Professional Documents
Culture Documents
Lecture 8 IP Security NPTEL
Uploaded by
AK The Tuber's Cafe0 ratings0% found this document useful (0 votes)
4 views25 pagesCopyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
4 views25 pagesLecture 8 IP Security NPTEL
Uploaded by
AK The Tuber's CafeCopyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You are on page 1of 25
IP Security
Dr. Neminath Hubballi
Indian Institute of Technology Indore
Overview
q Background
q IPSec features
q Deployment scenarios
q Components
q Methods
q Security Association
Indian Institute of Technology Indore
IPSec Features
q Encrypt and authenticate network traffic at the IP layer
q Several networked applications can be secured
q Data origin authentication: Each IP datagram was originated by the
claimed sender.
q Data integrity: IP datagram was not modified in transit
q Data confidentiality: Conceals the content of a message, typically by using
encryption.
q Replay protection: Capture and retransmit is not allowed
q Automated management of cryptographic keys and security associations:
Ensures that your VPN policy can be used throughout the extended
network with little or no manual configuration.
Indian Institute of Technology Indore
one reciever gets P1 attacker cannot send P1 again
full form of vpn -> virtual private network
Use cases (VPN)
q Secure branch office connectivity over Internet
q Secure remote access over the Internet
q Secure connections with partner organizations
Indian Institute of Technology Indore
Where to Implement IPSec Methods ?
q End host or
q Middlebox
Indian Institute of Technology Indore
middle box
IPSec -Two Methods
not provide confidentiality
q Authentication Header (AH): Provides authentication through an
extended/extra header.
qDeprecated as ESP provides both confidentiality and authentication
q Encapsulating Security Payload(ESP): Provides confidentiality and
confidentiality along with authentication.
Indian Institute of Technology Indore
IPSec Modes Both of those methods can operate in two diff modes
q Transport Mode: Secure the data given by a protocol above IP
q IPSec header is inserted into the original IP header
q Tunnel Mode: Original IP packet is encrypted and sent
q A new IP header is inserted at the beginning
Indian Institute of Technology Indore
original packet is not modified only
a new IPsec header is inserted
protocol identifies which entity is actually carried.
6 for TCP
17 for UDP
IPv4 Header Format 4 for IP header
50 for ESP header
51 for authentication header
(authentication header provides only the authentication of datagram )
protocol field is actually carrying this number
meaning that it is actually identifying what is
the next header type.
so it is actually in some sense it's actually
pointing to the next header
Indian Institute of Technology Indore
Authentication Header and IPv4
Courtesy: tcpguide.com
Indian Institute of Technology Indore
Authentication Header Format
who is recipient who is sender and what
cryptographic algo we are using are identified
4 bits
16 bits
Next Header Payload Length Reserved
Security Parameter Index
Sequence Number
Authentication Data (ICV)
32 bits
sequence number originally identifies the ip packet
Indian Institute of Technology Indore
Encapsulating Security Payload
Courtesy: tcpguide.com
Indian Institute of Technology Indore
Encapsulating Security Payload
Security Parameter Index
Sequence Number
Data
Padding Pad length Next Header
Integrity Check Value
ESP authentication data
padded data acc to the
how many bytes are
requirement of encryption algo
added to orig data
Indian Institute of Technology Indore
Indian Institute of Technology Indore
IPSec Components
q Encryptions and Hashing Algorithms
q DES, AES
q MD5, SHA-1
q Security Associations
q Key Exchange Methods
security association defines what kind of the cryptographic algorithm or hash algorithm to be used
Indian Institute of Technology Indore
IP Security Policy
q Security Association Database (SAD)
qA security association is uniquely identified by
q Security Parameter Index (SPI)- a bit string added to IP packet
q Destination IP Address
q Security Protocol Identified – AH or ESP
qSecurity Association is One-Way connections
q Security Policy Database (SPD)- Determines a SA for a subset of IP traffic
qRemote IP address
qLocal IP address
qHigher layer protocol
qName
qPort numbers
Indian Institute of Technology Indore
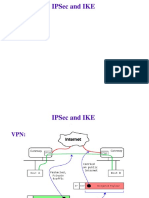
IPSec Architecture
Security Policy
AH ESP IKE
internet key exchange
Indian Institute of Technology Indore
Establishing a Security Association
q Manually
q On each node configuration
q Who are the participants of communication
q Mode of IPSec
q Key to be used
q Internet Key Exchange (IKE)
q Automatic configuration
Indian Institute of Technology Indore
IP Packet Processing: Outbound
Courtesy: Network Security Essentials
By William Stallings
Indian Institute of Technology Indore
IP Packet Processing: Inbound
Courtesy: Network Security Essentials
By William Stallings
Indian Institute of Technology Indore
You might also like
- Ipsec and VPN: Ali Bodden Joseph Gonya Miguel MendezDocument30 pagesIpsec and VPN: Ali Bodden Joseph Gonya Miguel MendezshahrianNo ratings yet
- CCDE BookDocument54 pagesCCDE BookVikasNo ratings yet
- IpsecDocument38 pagesIpseckstu1112No ratings yet
- IpsecDocument18 pagesIpsecRahul SaiNo ratings yet
- Ipsec Ike PDFDocument26 pagesIpsec Ike PDFPushpendra KumarNo ratings yet
- NetEngine AR600 AR6000 Series Routers IPSec VPN Delivery GuideDocument49 pagesNetEngine AR600 AR6000 Series Routers IPSec VPN Delivery GuideEDWIN GREGORIO MARIN VARGASNo ratings yet
- Computer Networks: CMPE 466Document38 pagesComputer Networks: CMPE 466foofoof123No ratings yet
- Unit 4Document70 pagesUnit 4Raj PaliwalNo ratings yet
- Unit IV Security Requirements ICSDocument55 pagesUnit IV Security Requirements ICSSakshi ChoudharyNo ratings yet
- IP Security: Web Security: Network LevelDocument23 pagesIP Security: Web Security: Network LevelnattychNo ratings yet
- IpsecDocument38 pagesIpsecMd. Asaduzzaman TaifurNo ratings yet
- 18CS744 Module5 NotesDocument23 pages18CS744 Module5 Notesakashroshan17No ratings yet
- BCA 4th Sem : Assignment File Introduction To Internet TechnologiesDocument23 pagesBCA 4th Sem : Assignment File Introduction To Internet TechnologiesvjagarwalNo ratings yet
- Lec 11Document34 pagesLec 11Areeba NawazNo ratings yet
- Unit 4 (Part 1)Document64 pagesUnit 4 (Part 1)Akshay UtaneNo ratings yet
- CNS Unit-ViDocument47 pagesCNS Unit-VinandanNo ratings yet
- CNS Chapter 4Document17 pagesCNS Chapter 4Divya shreeNo ratings yet
- Lecture 11 - IPSecDocument36 pagesLecture 11 - IPSecArslan RiazNo ratings yet
- Design and Implementation of IPsec VPN S PDFDocument5 pagesDesign and Implementation of IPsec VPN S PDFYves BlaNo ratings yet
- C&NS Unit-6 R16Document29 pagesC&NS Unit-6 R16Geethanjali KotaruNo ratings yet
- 11 IP Sec Services 02 Mar 2021material I 02 Mar 2021 IPSECDocument36 pages11 IP Sec Services 02 Mar 2021material I 02 Mar 2021 IPSECSharath KumarNo ratings yet
- Week 14 SVDocument25 pagesWeek 14 SVthanhtin2109No ratings yet
- HC110110029 Securing Data With IPSec VPNDocument17 pagesHC110110029 Securing Data With IPSec VPNjscansinoNo ratings yet
- IpsecDocument42 pagesIpsechalo.sidiqNo ratings yet
- 6-2 Comparative Analysis of Wireless Security ProtocolsDocument10 pages6-2 Comparative Analysis of Wireless Security ProtocolsMukul SharmaNo ratings yet
- IP SecurityDocument3 pagesIP SecurityDigital NikhilNo ratings yet
- 01-04 IPSec ConfigurationDocument270 pages01-04 IPSec Configurationfetah baghdadNo ratings yet
- 5th ModuleDocument22 pages5th Moduleashishsingh18022002No ratings yet
- Crypto 5th ModulenotesDocument22 pagesCrypto 5th ModulenotesShazNo ratings yet
- IpsecDocument25 pagesIpsecsunnyNo ratings yet
- J 1417-Information Security (2014 Admn OnwardsDocument10 pagesJ 1417-Information Security (2014 Admn OnwardsLeslie QwerNo ratings yet
- ch19 IPDocument27 pagesch19 IPDuttaUdayaVenkataChegondiNo ratings yet
- CNS Unit-IVDocument54 pagesCNS Unit-IVRadha RaniNo ratings yet
- IpsecDocument81 pagesIpsecBharath SriramNo ratings yet
- Chapter 08Document27 pagesChapter 08willy muhammad fauziNo ratings yet
- CCNP Certification CoursewareDocument70 pagesCCNP Certification CoursewareOsama100% (1)
- Chapter 5 Network SecurityDocument62 pagesChapter 5 Network Securitycarraa DestaNo ratings yet
- Unit 5 - IP SecurityDocument47 pagesUnit 5 - IP Securitygadidheerajreddy.20.itNo ratings yet
- Hitkarni College of Engg. and Tech.: Internet Protocol SecurityDocument33 pagesHitkarni College of Engg. and Tech.: Internet Protocol SecurityramujagirsinghNo ratings yet
- 5.1 Ip Security OverviewDocument22 pages5.1 Ip Security OverviewDragon ModeNo ratings yet
- IP Security (IPSEC) and Internet Key Exchange (IKE)Document39 pagesIP Security (IPSEC) and Internet Key Exchange (IKE)Deepak KhatriNo ratings yet
- Levis-CS144 Lecture 1-3-Ip Service ModelDocument8 pagesLevis-CS144 Lecture 1-3-Ip Service ModelMaharshiMishraNo ratings yet
- Internet Security: How The Internet Works and Some Basic VulnerabilitiesDocument39 pagesInternet Security: How The Internet Works and Some Basic Vulnerabilitiessalim ucarNo ratings yet
- Cryptography and Network Security: Fifth Edition by William StallingsDocument27 pagesCryptography and Network Security: Fifth Edition by William Stallingsspm1379No ratings yet
- SCCS 420 CH 32 (Internet Security)Document10 pagesSCCS 420 CH 32 (Internet Security)api-3738694No ratings yet
- CNS Unit-6Document15 pagesCNS Unit-6pihadar269No ratings yet
- Wa0004.Document9 pagesWa0004.umang JadhavNo ratings yet
- Presented By: Kulwinder Priyanka PriyaDocument70 pagesPresented By: Kulwinder Priyanka PriyaPriya RainaNo ratings yet
- Introduction To IoT PlatformDocument17 pagesIntroduction To IoT PlatformPrasanth VarasalaNo ratings yet
- ET4280 ACN-06 Security Internet ProtocolDocument40 pagesET4280 ACN-06 Security Internet ProtocolHưng NguyễnNo ratings yet
- DCN Unit 7Document40 pagesDCN Unit 7RazinNo ratings yet
- Module Name: Dept. of ISE, SJBITDocument45 pagesModule Name: Dept. of ISE, SJBITShaikh faisalNo ratings yet
- The Idea To Encrypt and Seal The Transport and Application Layer Data During Transmission Also Offer Integrity Protection Is Called IP SecurityDocument18 pagesThe Idea To Encrypt and Seal The Transport and Application Layer Data During Transmission Also Offer Integrity Protection Is Called IP Securityrh_rathodNo ratings yet
- Understanding IPSec (Modo de Compatibilidad)Document42 pagesUnderstanding IPSec (Modo de Compatibilidad)cordon162No ratings yet
- An toàn hệ thốngDocument35 pagesAn toàn hệ thốngnhiNo ratings yet
- Module 10 - Ipsec: Ing. Rayner Durango E. Msig Mcse, MCTDocument19 pagesModule 10 - Ipsec: Ing. Rayner Durango E. Msig Mcse, MCTJhono BassNo ratings yet
- Enterprise Networking, Security, and Automation - IPsecDocument7 pagesEnterprise Networking, Security, and Automation - IPsecZulkifliNo ratings yet
- Cryptography and Network Security: UNIT-5Document12 pagesCryptography and Network Security: UNIT-5Aravind ValugondaNo ratings yet
- Ip Security Overview: Applications of IpsecDocument14 pagesIp Security Overview: Applications of IpsecDivyaThalankiVenkataNo ratings yet
- Network Security Essentials: Fourth Edition by William StallingsDocument27 pagesNetwork Security Essentials: Fourth Edition by William StallingsXozanNo ratings yet
- ENC28J60 Manual Source CodeDocument7 pagesENC28J60 Manual Source CodeFlávio CaetanoNo ratings yet
- SNMP Web Card+box-User ManualDocument17 pagesSNMP Web Card+box-User ManualJ.M.No ratings yet
- 10.1.1.4 Packet Tracer - Map A Network Using CDPDocument4 pages10.1.1.4 Packet Tracer - Map A Network Using CDPIon TemciucNo ratings yet
- Forti Recorder Handbook RevisionDocument225 pagesForti Recorder Handbook RevisioneffahpaulNo ratings yet
- Fortinet - Certshared.nse4 FGT 72.exam - Dumps.2023 Sep 17.by - Hugo.64q.vceDocument10 pagesFortinet - Certshared.nse4 FGT 72.exam - Dumps.2023 Sep 17.by - Hugo.64q.vceSaeed NasharNo ratings yet
- Access Control ListDocument17 pagesAccess Control ListMubarik Ali MuhumedNo ratings yet
- Studying The TCP Flow and Congestion ConDocument6 pagesStudying The TCP Flow and Congestion ConKhalid mohamedNo ratings yet
- Datasheet VseDocument2 pagesDatasheet VseoksjaerNo ratings yet
- 5.1.9 Packet Tracer - Investigate STP Loop PreventionDocument2 pages5.1.9 Packet Tracer - Investigate STP Loop PreventionHạnhNo ratings yet
- NF18ACV PlayStation Setup GuideDocument6 pagesNF18ACV PlayStation Setup GuideCraig TaylorNo ratings yet
- Manual Switch OverTek OT 3407SVW UXDocument22 pagesManual Switch OverTek OT 3407SVW UXKovalski AndersonNo ratings yet
- SSH Tunneling Control: SSH Decryption To Prevent Non SSH Applications Bypass FirewallDocument7 pagesSSH Tunneling Control: SSH Decryption To Prevent Non SSH Applications Bypass FirewallnandomironNo ratings yet
- Service Delivery Switch: Data SheetDocument6 pagesService Delivery Switch: Data Sheetsatyvan2003No ratings yet
- Introduction To Frame Relay, Atm, Isdn, PSTN, and X.25Document14 pagesIntroduction To Frame Relay, Atm, Isdn, PSTN, and X.25Faith MachukaNo ratings yet
- COIT20262 - Advanced Network Security, Term 2, 2017: Assignment 2Document8 pagesCOIT20262 - Advanced Network Security, Term 2, 2017: Assignment 2Karambir SinghNo ratings yet
- Web-Admin Configuration Manual: Altai C1N Series Wifi Ap/CpeDocument120 pagesWeb-Admin Configuration Manual: Altai C1N Series Wifi Ap/CpeosvaldoNo ratings yet
- Sample Exam QuestionsDocument6 pagesSample Exam QuestionsAnonymous njwTvCNo ratings yet
- PLC Quantum PLC NOE771xx User Manual v5.0Document306 pagesPLC Quantum PLC NOE771xx User Manual v5.0Irfan AshrafNo ratings yet
- Te Va A Servir en Cisco V2Document4 pagesTe Va A Servir en Cisco V2Bryant GamboaNo ratings yet
- Router AwDocument12 pagesRouter AwdesafiadoreNo ratings yet
- Netscaler Data SheetDocument11 pagesNetscaler Data SheetBalvinder Singh RawatNo ratings yet
- 640-802 CCNA Question Review PDFDocument77 pages640-802 CCNA Question Review PDFkdwillsonNo ratings yet
- CN Full Manual r2021Document44 pagesCN Full Manual r2021chandrakanth.bNo ratings yet
- Cek Node B Gpon HuaweiDocument4 pagesCek Node B Gpon Huaweijefri saniNo ratings yet
- DEFCON 21 Miu Lee Kill em All DDoS Protection Total Annihilation WP UpdatedDocument17 pagesDEFCON 21 Miu Lee Kill em All DDoS Protection Total Annihilation WP Updatedhotsync101No ratings yet
- TS 3GPP 23278-710Document153 pagesTS 3GPP 23278-710acer_7No ratings yet
- Welcome To Ccna: Lead by Eng AbyadDocument46 pagesWelcome To Ccna: Lead by Eng AbyadAbdifatah SaidNo ratings yet
- Red Hat Enterprise Security: Network Services: Course OutlineDocument3 pagesRed Hat Enterprise Security: Network Services: Course OutlineAlex SkolnickNo ratings yet
- William Stalling - Chapter 12xDocument26 pagesWilliam Stalling - Chapter 12xLê Đắc Nhường (Dac-Nhuong Le)No ratings yet