Professional Documents
Culture Documents
Spotlight Process
Spotlight Process
Uploaded by
Dương Dương0 ratings0% found this document useful (0 votes)
3 views1 pageCopyright
© © All Rights Reserved
Available Formats
DOCX, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
© All Rights Reserved
Available Formats
Download as DOCX, PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
3 views1 pageSpotlight Process
Spotlight Process
Uploaded by
Dương DươngCopyright:
© All Rights Reserved
Available Formats
Download as DOCX, PDF, TXT or read online from Scribd
You are on page 1of 1
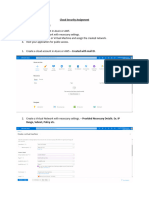
Spotlight Process
1. Configure Connections and Data Sources
a. Set up connections:
i. Active Directory
ii. PAM
iii. SIEM
b. Define the assets and domains to be covered by Spotlight
2. Define Crown Jewels
a. Crown Jewels = any critical system
b. Must have an IP address, host name, or URL
3. Write Policies
a. Create a default rule to collect data
b. Create additional rules later if needed
4. Data Collection and Analysis
a. ITDR queries Active Directory and PAM
b. ITDR deploys self-dissolving binary to endpoints
c. Spotlight IDI server analyzes and prioritizes risk findings
5. Remediation
a. Spotlight performs cleaning based on auto-hygiene rules created
b. Spotlight administrators triage remaining risk findings
You might also like
- Business Email Compromise Response PlaybookDocument7 pagesBusiness Email Compromise Response PlaybookFrank GulmayoNo ratings yet
- Oracle Infrastructure Architect Associate All One PDFDocument663 pagesOracle Infrastructure Architect Associate All One PDFtimirkantaNo ratings yet
- SEcurity+ QuestionsDocument17 pagesSEcurity+ QuestionsEnock AndersonNo ratings yet
- Exam Ref 70-532 Developing Microsoft Azure Solutions (PDFDrive)Document633 pagesExam Ref 70-532 Developing Microsoft Azure Solutions (PDFDrive)grndarubioNo ratings yet
- People and Organisational DocumentDocument11 pagesPeople and Organisational DocumentRavi RamanNo ratings yet
- Web Application Compromise Response PlaybookDocument7 pagesWeb Application Compromise Response PlaybookFrank GulmayoNo ratings yet
- Obiee 12c Course ContentDocument6 pagesObiee 12c Course ContentKhaled MohammedNo ratings yet
- Computer Forensics ProjectsDocument4 pagesComputer Forensics Projectszaid khattakNo ratings yet
- CND Exam (Answer)Document23 pagesCND Exam (Answer)Foodbank Jatibening100% (1)
- Privacy Manager Certification: Examination Blueprint For The Certified Information Privacy Manager (CIPM)Document2 pagesPrivacy Manager Certification: Examination Blueprint For The Certified Information Privacy Manager (CIPM)MatthewNo ratings yet
- Computer System Servicing NCII Pointers To ReviewDocument2 pagesComputer System Servicing NCII Pointers To ReviewEviok Anfone ZosaNo ratings yet
- SQL Server Installation Checklist2Document3 pagesSQL Server Installation Checklist2praveenmpkNo ratings yet
- Ibm Datapower Gateway V7.6 Solution Implementation Sample TestDocument4 pagesIbm Datapower Gateway V7.6 Solution Implementation Sample TestAnudeep PolamarasettyNo ratings yet
- Django Unleashed: Building Web Applications with Python's FrameworkFrom EverandDjango Unleashed: Building Web Applications with Python's FrameworkNo ratings yet
- C1000-156 QRadar SIEM V7.5 Administrator Sample TestDocument19 pagesC1000-156 QRadar SIEM V7.5 Administrator Sample TestheineckennNo ratings yet
- Integration of Cisco - ISE - With - cnPilot-AP'sDocument19 pagesIntegration of Cisco - ISE - With - cnPilot-AP'slacerdatomNo ratings yet
- Incident Response Playbooks 1687937708Document21 pagesIncident Response Playbooks 1687937708macNo ratings yet
- Syllabus Ccna Security IinsDocument11 pagesSyllabus Ccna Security IinsHrm SaifullahNo ratings yet
- Test-Exam - S1000-001 IBM Cloud Pak For Security 1.xDocument10 pagesTest-Exam - S1000-001 IBM Cloud Pak For Security 1.xshadNo ratings yet
- Cloud Security AssignmentDocument10 pagesCloud Security Assignmentmsaif213010No ratings yet
- Hypatia FinalDocument8 pagesHypatia FinalAssem MakhyounNo ratings yet
- Collibra DIC Data Privacy 2022.05Document185 pagesCollibra DIC Data Privacy 2022.05Host MomNo ratings yet
- Managing Network SourcesDocument4 pagesManaging Network Sourcessss pppNo ratings yet
- Wordpress - HA - Environment - Setup GuideDocument3 pagesWordpress - HA - Environment - Setup GuideWordpress MediaExplorerNo ratings yet
- Sample Questions For: Test C1000-026, Ibm Qradar Siem V7.3.2 Fundamental AdministrationDocument4 pagesSample Questions For: Test C1000-026, Ibm Qradar Siem V7.3.2 Fundamental AdministrationKirenji RyuseiNo ratings yet
- Architecture Diagram: Social Networks UsersDocument1 pageArchitecture Diagram: Social Networks UsersReddy SumanthNo ratings yet
- Slide STM AccountingDocument18 pagesSlide STM AccountingTika LarasatiNo ratings yet
- S1103612GC21 Ag CLS-Lab-05Document10 pagesS1103612GC21 Ag CLS-Lab-05ahmadNo ratings yet
- Athena ChuongTrinhDayMCSA ISA 70 350Document2 pagesAthena ChuongTrinhDayMCSA ISA 70 350Kha TrinhNo ratings yet
- McAfee SIEM Course ContentDocument2 pagesMcAfee SIEM Course ContentJohn ManniNo ratings yet
- Prisma Certified Cloud Security Engineer (PCCSE) BlueprintDocument4 pagesPrisma Certified Cloud Security Engineer (PCCSE) BlueprintJohn LinNo ratings yet
- Aws Crist PDFDocument3 pagesAws Crist PDFPranav KashyapNo ratings yet
- Samc1000 066Document4 pagesSamc1000 066Mahendran BaluNo ratings yet
- CH4 ReviewDocument5 pagesCH4 ReviewNick Benz100% (1)
- Sow It InfraDocument3 pagesSow It Infradev KumarNo ratings yet
- IP Assignment Using An External Server On ACS 5Document9 pagesIP Assignment Using An External Server On ACS 5tberner666No ratings yet
- PCI ComplianceDocument18 pagesPCI ComplianceHusseni MuzkkirNo ratings yet
- 300 735 SAUTO v1.1Document2 pages300 735 SAUTO v1.1elmenorNo ratings yet
- Full Ebook of Google Cloud Certified Associate Cloud Engineer All in One Exam Guide 1St Edition Hyman Online PDF All ChapterDocument69 pagesFull Ebook of Google Cloud Certified Associate Cloud Engineer All in One Exam Guide 1St Edition Hyman Online PDF All Chaptercolettespell207923100% (2)
- Sample Exam 250-315: Administration of Symantec Endpoint Protection 12.1Document5 pagesSample Exam 250-315: Administration of Symantec Endpoint Protection 12.1simardeepsingh3No ratings yet
- Lab 6 Rules PDFDocument8 pagesLab 6 Rules PDFPradeep KumarNo ratings yet
- 210 255 Secops v2Document5 pages210 255 Secops v2vjjmirasNo ratings yet
- DWDM Final Lab SyllabusDocument2 pagesDWDM Final Lab Syllabussaisimba99No ratings yet
- F5 201 NotesDocument13 pagesF5 201 NotesPuneet GuptaNo ratings yet
- EX NO 6 Riyaz New'11Document5 pagesEX NO 6 Riyaz New'11sam881343No ratings yet
- Semester VI Subject Name: Ethical Hacking Name: Mohammed Raza Haqiqullah Khan Class: T.Y. B.Sc. Computer ScienceDocument35 pagesSemester VI Subject Name: Ethical Hacking Name: Mohammed Raza Haqiqullah Khan Class: T.Y. B.Sc. Computer ScienceRaza khanNo ratings yet
- AZ First 6 Mod 5Document24 pagesAZ First 6 Mod 5jharajnish30No ratings yet
- Checkpoint Test-Inside 156-215 80 v2020-09-23 by Mila 320q - QOnlyDocument65 pagesCheckpoint Test-Inside 156-215 80 v2020-09-23 by Mila 320q - QOnlyMirza CerimNo ratings yet
- ISO 27701 WhitepaperDocument30 pagesISO 27701 WhitepaperJohnNo ratings yet
- Question 1Document4 pagesQuestion 1YoSalinasNo ratings yet
- AZ First 6 Mod 3Document22 pagesAZ First 6 Mod 3jharajnish30No ratings yet
- Module 8: Administering and Troubleshooting Compliance and Security in Office 365 Lab: Configuring and Troubleshooting Compliance and SecurityDocument11 pagesModule 8: Administering and Troubleshooting Compliance and Security in Office 365 Lab: Configuring and Troubleshooting Compliance and SecurityBen Aissa TaherNo ratings yet
- Module 8: Administering and Troubleshooting Compliance and Security in Office 365 Lab: Configuring and Troubleshooting Compliance and SecurityDocument11 pagesModule 8: Administering and Troubleshooting Compliance and Security in Office 365 Lab: Configuring and Troubleshooting Compliance and SecurityBen Aissa TaherNo ratings yet
- Cipm Ebp 2.0.1 2022Document2 pagesCipm Ebp 2.0.1 2022blackdogpkNo ratings yet
- CCNA Security SyllabusDocument5 pagesCCNA Security SyllabuszoyaNo ratings yet
- Ebffiledoc - 707download PDF Infrastructure As Code 2Nd Edition Early Access Kief Morris Ebook Full ChapterDocument53 pagesEbffiledoc - 707download PDF Infrastructure As Code 2Nd Edition Early Access Kief Morris Ebook Full Chapterdan.marrero822100% (1)
- QRadar SIEM V7.5 Deployment Exam C1000-153 Sample QuestionsDocument9 pagesQRadar SIEM V7.5 Deployment Exam C1000-153 Sample QuestionsPauloNo ratings yet
- CS552 Object-Oriented Design Project Mahender Kasarla, Pramod Reddy Dharma Rivier UniversityDocument37 pagesCS552 Object-Oriented Design Project Mahender Kasarla, Pramod Reddy Dharma Rivier UniversitySanjog PathakNo ratings yet
- Tomcat Penetration Testing 1714147419Document22 pagesTomcat Penetration Testing 1714147419Dương DươngNo ratings yet
- How To Demo CASB-9-2-21-Partner UseDocument8 pagesHow To Demo CASB-9-2-21-Partner UseDương DươngNo ratings yet
- Tenableio and CyberArk Enterprise Password Vault Integration GuideDocument71 pagesTenableio and CyberArk Enterprise Password Vault Integration GuideDương DươngNo ratings yet
- Requir MentDocument1 pageRequir MentDương DươngNo ratings yet
- L1Document2 pagesL1Dương DươngNo ratings yet
- Samsung Group Purchases From Imarketkorea: Online File W5.5Document1 pageSamsung Group Purchases From Imarketkorea: Online File W5.5Dương DươngNo ratings yet