Professional Documents
Culture Documents
Security Strategies in Windows Platforms and Applications
Uploaded by
Shreya KasturiaOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Security Strategies in Windows Platforms and Applications
Uploaded by
Shreya KasturiaCopyright:
Available Formats
Security Strategies in Windows
Platforms and Applications
Lesson 14
Microsoft Windows and the
Security Life Cycle
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Learning Objective and Key
Concepts
Learning Objective
Include security concerns as early as possible in the
software development process.
Key Concepts
Trends in software change management
Windows system and application security
management
The application security life cycle
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
Security Strategies in Windows Platforms and Applications www.jblearning.com Page 2
All rights reserved.
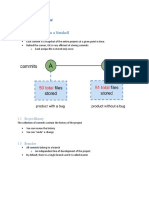
Secure Software Development
Strategies
Software Development Life Cycle – SDLC
Agile Development
Security Development Lifecycle – SDL
Building Security in Maturity Model – BSIMM
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
Security Strategies in Windows Platforms and Applications www.jblearning.com Page 3
All rights reserved.
An SDLC with 10 Phases
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
Security Strategies in Windows Platforms and Applications www.jblearning.com Page 4
All rights reserved.
SDLC
Initiate
Dispose Define
Operate Design
Roll out Build
Test
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
Security Strategies in Windows Platforms and Applications www.jblearning.com Page 5
All rights reserved.
Agile Development Cycle
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
Security Strategies in Windows Platforms and Applications www.jblearning.com Page 6
All rights reserved.
Microsoft Software Development
Lifecycle
Training
Response
Requirement
s
Release
Design
Verification
Implementati
on
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
Security Strategies in Windows Platforms and Applications www.jblearning.com Page 7
All rights reserved.
The Software Security
Framework (SSF)
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
Security Strategies in Windows Platforms and Applications www.jblearning.com Page 8
All rights reserved.
Testing
The purpose of formal testing is to evaluate how
well your application meets overall performance,
functionality, and security goals.
Every goal from the original specification should
have at least one corresponding testing scenario.
The testing scenario evaluates whether the
application satisfies the goal.
Testing activities can be manual or and
automated.
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
Security Strategies in Windows Platforms and Applications www.jblearning.com Page 9
All rights reserved.
Secure Software Development
Fewer defects
• Fewer vulnerabilities
Proper training is crucial
• Development
• Testing
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
Security Strategies in Windows Platforms and Applications www.jblearning.com Page 10
All rights reserved.
Secure Software Development
(Continued)
Security starts with requirements and
design
• Too many applications added delay security
• Rework is always more expensive
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
Security Strategies in Windows Platforms and Applications www.jblearning.com Page 11
All rights reserved.
Application Software Development/
Revision
Software
Software
Configuration
Development Software Control
Management
Areas of Difficulty
(SCM)
Phase Baseline Configuration
Identification Identification Identification
Configuration
Change Control
Control
Phase Transition
Configuration
Communication
Auditing
Activity Repeatable Configuration
Coordination Processes Status Accounting
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
Security Strategies in Windows Platforms and Applications www.jblearning.com Page 12
All rights reserved.
Best Practices
Think of security early and often.
Adopt a software development model to help
define your organization’s development activities
and flow.
Define activities for each phase in your model.
Ensure all developers are trained to develop
secure applications.
Look for developer training.
Validate your software product at the end of every
phase.
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
Security Strategies in Windows Platforms and Applications www.jblearning.com Page 13
All rights reserved.
Best Practices (Cont.)
Create separate software projects for each
related group of programs or program changes.
Do not begin a software development project by
writing code—plan and design first.
Keep the three SDL core concepts in focus—
education, continuous improvement, and
accountability.
Develop tests to ensure each component of your
application meets security requirements.
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
Security Strategies in Windows Platforms and Applications www.jblearning.com Page 14
All rights reserved.
Summary
Software development and its strategies
Process of developing secure software
Key roles in software change management
Questions and answers on emerging
trends
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
Security Strategies in Windows Platforms and Applications www.jblearning.com Page 15
All rights reserved.
You might also like
- Textnow - Mon, 28 Feb 2022 13 - 39 - 00 GMT - LogDocument18 pagesTextnow - Mon, 28 Feb 2022 13 - 39 - 00 GMT - Logry twiggNo ratings yet
- CISA - Domain 3 - IS Acquisition, Development and ImplementationDocument153 pagesCISA - Domain 3 - IS Acquisition, Development and ImplementationPremdeepakHulagbali100% (1)
- Proposal For Dedicated Internet BandwidthDocument3 pagesProposal For Dedicated Internet Bandwidthjsri100% (1)
- 1 Devops and Git in A NutshellDocument30 pages1 Devops and Git in A NutshellsadoNo ratings yet
- The Secure Software Development Lifecycle at SAPDocument12 pagesThe Secure Software Development Lifecycle at SAPHelderNo ratings yet
- Security Policies and Implementation Issues: Week 6 - Chapter 8 IT Security Policy Framework ApproachesDocument37 pagesSecurity Policies and Implementation Issues: Week 6 - Chapter 8 IT Security Policy Framework ApproachesSrinivas AdityaNo ratings yet
- E-Book App Development Cybersecurity With The APP SolutionsDocument17 pagesE-Book App Development Cybersecurity With The APP SolutionsViet Nguyen TrongNo ratings yet
- Deepak Kumar: ObjectiveDocument4 pagesDeepak Kumar: Objectiveabhishek kumarNo ratings yet
- Reynolds PPT Ch07Document24 pagesReynolds PPT Ch07Phillip GardnerNo ratings yet
- Ram KapoorDocument4 pagesRam KapoorAbhishek RajpootNo ratings yet
- Secure Coding Webinar3Document42 pagesSecure Coding Webinar3Ashok Siva Kumar PoojalaNo ratings yet
- Data Sheet Appscan EnterpriseDocument8 pagesData Sheet Appscan EnterpriseMohannad DawoudNo ratings yet
- Security Policies and Implementation Issues Lesson 1 Information Systems Security Policy ManagementDocument23 pagesSecurity Policies and Implementation Issues Lesson 1 Information Systems Security Policy ManagementSrinivas AdityaNo ratings yet
- SB SoftSec16 03 Security Software EngineeringDocument62 pagesSB SoftSec16 03 Security Software EngineeringShreya KasturiaNo ratings yet
- Resume NewDocument8 pagesResume Newbala govindamNo ratings yet
- 1574158341-Resume AjayLanjewar QA 8YrsExp1Document7 pages1574158341-Resume AjayLanjewar QA 8YrsExp1ragunath90No ratings yet
- Consultant Profile TemplateDocument4 pagesConsultant Profile TemplateAnil ChiplunkarNo ratings yet
- Echnologies: The Next Level of Competitive AdvantageDocument18 pagesEchnologies: The Next Level of Competitive AdvantageNilesh PatkarNo ratings yet
- Echnologies: The Next Level of Competitive AdvantageDocument18 pagesEchnologies: The Next Level of Competitive AdvantageNilesh PatkarNo ratings yet
- CSSLP Insights: Why Become A CSSLPDocument6 pagesCSSLP Insights: Why Become A CSSLPudara86No ratings yet
- Risk Software IMDSDocument21 pagesRisk Software IMDSrnyaboke90No ratings yet
- Seven Steps To Software Security - UpdatedDocument8 pagesSeven Steps To Software Security - UpdatedAbdul Razak KamaruddinNo ratings yet
- F Secure Security Comes As Standard WhitepaperDocument24 pagesF Secure Security Comes As Standard WhitepaperArnaldo CanelasNo ratings yet
- OSMAP - Course OutlineDocument2 pagesOSMAP - Course OutlinejerryhamstersgNo ratings yet
- SecAppDev2013 - SDLC Session Bart de Win v1.0Document57 pagesSecAppDev2013 - SDLC Session Bart de Win v1.0Mera KaramNo ratings yet
- Re Fi ZonDocument5 pagesRe Fi ZonTamarakuro Simon AlaleNo ratings yet
- Srikanth 154797Document6 pagesSrikanth 154797Usha TNo ratings yet
- CH04 - Part1Document17 pagesCH04 - Part1entsar11 entsarNo ratings yet
- 1.lyallpur Khalsa College Jalandhar, 2.guru Nanak Dev University, AmritsarDocument15 pages1.lyallpur Khalsa College Jalandhar, 2.guru Nanak Dev University, AmritsarsuzanalupuNo ratings yet
- SAFECode Dev Practices1108Document22 pagesSAFECode Dev Practices1108Sakthi T VelNo ratings yet
- Ian Alfred Orozco CV - Latest PDFDocument9 pagesIan Alfred Orozco CV - Latest PDFJohnPaulChristopherPabloNo ratings yet
- Resume Rahul Goyal B/205 Sheetal Tower Venkatesh Park Opp MTNLDocument4 pagesResume Rahul Goyal B/205 Sheetal Tower Venkatesh Park Opp MTNLKasey CaseyNo ratings yet
- 10 Things To Get Right For Successful DevSecOpsDocument15 pages10 Things To Get Right For Successful DevSecOpsyns100% (1)
- Hemant Singh: Experience SummaryDocument8 pagesHemant Singh: Experience SummaryLokesh MakwaneNo ratings yet
- Surya CVDocument4 pagesSurya CVvivekNo ratings yet
- Selenium 2yrs Experience ResumeDocument4 pagesSelenium 2yrs Experience Resumek varmaNo ratings yet
- Sap Hana Security WhitepaperDocument10 pagesSap Hana Security WhitepaperMaximo MavenusNo ratings yet
- Selenium 2yrs Experience ResumeDocument4 pagesSelenium 2yrs Experience Resumeaaditya aroraNo ratings yet
- Aditi Ahuja Global Business Services: EducationDocument4 pagesAditi Ahuja Global Business Services: EducationvishalbhtNo ratings yet
- Sandeep Reddy: ObjectiveDocument4 pagesSandeep Reddy: ObjectiveAdhe IdhiNo ratings yet
- CSSLP Brochure ForPDFDocument6 pagesCSSLP Brochure ForPDFjoekkuNo ratings yet
- Resumee 2018Document5 pagesResumee 2018SURBHI KUMARNo ratings yet
- Ibm Appscan Source DatasheetDocument12 pagesIbm Appscan Source DatasheetAnonymous G1iPoNOKNo ratings yet
- Servicenow Certified Application Developer Exam SpecificationDocument8 pagesServicenow Certified Application Developer Exam SpecificationChandra SekharNo ratings yet
- Ramakrishna Marella: Soft Skill Profile SummaryDocument5 pagesRamakrishna Marella: Soft Skill Profile SummaryRamakrishna MarellaNo ratings yet
- Guidelines For Secure Application Design, Development, Implementation & OperationsDocument15 pagesGuidelines For Secure Application Design, Development, Implementation & OperationsVatsal ThackerNo ratings yet
- OffSec Web Application Security060320Document12 pagesOffSec Web Application Security060320shakawathNo ratings yet
- OffSec Web Application Security060320Document12 pagesOffSec Web Application Security060320Llauca Xavier0% (2)
- Website Pen ProjectDocument65 pagesWebsite Pen ProjectshivNo ratings yet
- DC Neotalent en Maicon NunesDocument4 pagesDC Neotalent en Maicon NunesFernando DiasNo ratings yet
- QA Principles Day 2Document48 pagesQA Principles Day 2Aseel AlomariNo ratings yet
- 02 Software SecurityDocument31 pages02 Software SecurityCristobal QuispeNo ratings yet
- 05 Handout 1 (Pre-Finals)Document2 pages05 Handout 1 (Pre-Finals)Emmanuel DelarosaNo ratings yet
- Curriculum Vitae Suresh Yallambatla Mobile: 91-9060638739 Shanthi Nagar, Bangalore. ProfileDocument5 pagesCurriculum Vitae Suresh Yallambatla Mobile: 91-9060638739 Shanthi Nagar, Bangalore. Profileruben_thalakotturNo ratings yet
- Résumé: Mobile: +91 9620840711Document6 pagesRésumé: Mobile: +91 9620840711Nagachetan SPNo ratings yet
- Resume-Ankit AgrawalDocument2 pagesResume-Ankit AgrawalAbhishek SharmaNo ratings yet
- Gopi D Mobile No: +91-9908496530 EmailDocument3 pagesGopi D Mobile No: +91-9908496530 EmailNagaraju kNo ratings yet
- QA PrinciplesDocument108 pagesQA PrinciplesAseel AlomariNo ratings yet
- Software Engineering M1Document47 pagesSoftware Engineering M1Ilechukwu MichelleNo ratings yet
- Education: Name Mobile Number Email IdDocument6 pagesEducation: Name Mobile Number Email Idmail4moorthyNo ratings yet
- SkillFront Certification ExaminationDocument9 pagesSkillFront Certification Examinationrangel24No ratings yet
- Software Testing Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesFrom EverandSoftware Testing Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesNo ratings yet
- Processing) and Non-Real-Time Analytics (Batch Data Processing)Document1 pageProcessing) and Non-Real-Time Analytics (Batch Data Processing)Shreya KasturiaNo ratings yet
- SB SoftSec16 03 Security Software EngineeringDocument62 pagesSB SoftSec16 03 Security Software EngineeringShreya KasturiaNo ratings yet
- A Survey On Design Methods For Secure Software DevelopmentDocument19 pagesA Survey On Design Methods For Secure Software DevelopmentShreya KasturiaNo ratings yet
- Hadoop QuestionsDocument14 pagesHadoop QuestionsShreya KasturiaNo ratings yet
- Top 6 Technology Trends That Affect Software Security: 1. Everything Is MobileDocument5 pagesTop 6 Technology Trends That Affect Software Security: 1. Everything Is MobileShreya KasturiaNo ratings yet
- Turtorial Real TimeDocument19 pagesTurtorial Real TimeShreya KasturiaNo ratings yet
- Design and Implementation of A Mobile Based Transcript Request Processing System Mbts IJERTV4IS070001Document5 pagesDesign and Implementation of A Mobile Based Transcript Request Processing System Mbts IJERTV4IS070001chisom aneneNo ratings yet
- Lic ProjectDocument80 pagesLic ProjectMahavira DesaiNo ratings yet
- OODB and Previllage For LabDocument146 pagesOODB and Previllage For LabzerihunNo ratings yet
- PlantPAx™ Logix Batch & Sequence ManagerDocument4 pagesPlantPAx™ Logix Batch & Sequence ManagerYang Gul LeeNo ratings yet
- DaknetDocument19 pagesDaknetSowMya VeeraMachaneniNo ratings yet
- Business Communication Assignment 02Document9 pagesBusiness Communication Assignment 02Aiou MSCNo ratings yet
- Mizoram State Data CenterDocument264 pagesMizoram State Data Centervijayabhaskar83No ratings yet
- Setting Up Od I Form Q SeriesDocument7 pagesSetting Up Od I Form Q SeriesaliNo ratings yet
- Sy0 601 12Document32 pagesSy0 601 12MEN'S ARENANo ratings yet
- Big Data Challenges: 1. Dealing With Data GrowthDocument4 pagesBig Data Challenges: 1. Dealing With Data GrowthAkhila Shaji100% (1)
- SIM7000X-PCIE Series SPEC 20220210Document3 pagesSIM7000X-PCIE Series SPEC 20220210bflizardoNo ratings yet
- Vel Tech SympDocument9 pagesVel Tech SympSandeep_Ojha_2033No ratings yet
- Things To Know About Wifi6Document1 pageThings To Know About Wifi6Treasurer MykonosNo ratings yet
- User Story Writing: Samuel LohDocument9 pagesUser Story Writing: Samuel LohSamuel LohNo ratings yet
- Manual Linksys WAP54GDocument5 pagesManual Linksys WAP54GJUAN ESCOBARNo ratings yet
- Section 1 QuizDocument4 pagesSection 1 QuizAnca Vochescu100% (1)
- Basic QNX Neutrino CommandsDocument2 pagesBasic QNX Neutrino CommandsdobNo ratings yet
- Website Development Company in London - Idiosys UKDocument8 pagesWebsite Development Company in London - Idiosys UKIdiosysNo ratings yet
- ETHIOPIAN HIGHER UNIVERSITY PLACEMENT SYSTEM Final ProposalDocument15 pagesETHIOPIAN HIGHER UNIVERSITY PLACEMENT SYSTEM Final ProposalIbrãhîm MõWdät100% (1)
- TOR IT ConsultantDocument5 pagesTOR IT ConsultantJasim's BhaignaNo ratings yet
- Apparent Software EngineeringDocument70 pagesApparent Software EngineeringShaller Taye100% (1)
- Normalization: UpdateslDocument20 pagesNormalization: UpdateslBarinder SinghNo ratings yet
- Serverless Computing For IoTDocument12 pagesServerless Computing For IoTYishamu YihunieNo ratings yet
- NPTEL SyllabusDocument1 pageNPTEL SyllabusRam DinNo ratings yet
- Pts000109 Ihe Integration Statement Mylab f11xx 01.3 04Document1 pagePts000109 Ihe Integration Statement Mylab f11xx 01.3 04dssdvNo ratings yet
- Dns Server: Phd. Alcides Montoya Canola, Est. Carlos Andres Ballesteros Universidad Nacional de Colombia - Sede MedellinDocument4 pagesDns Server: Phd. Alcides Montoya Canola, Est. Carlos Andres Ballesteros Universidad Nacional de Colombia - Sede MedellinDanielColoradoGaviriaNo ratings yet