Professional Documents
Culture Documents
Introduction - Cont'd: Computer Network Security
Uploaded by
Timo AlexOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Introduction - Cont'd: Computer Network Security
Uploaded by
Timo AlexCopyright:
Available Formats
Faculty of Computing and Informatics
COMPUTER NETWORK SECURITY
Succeed We Must
Computer Security Research Group
Lecture 2
Introduction – Cont’d
07/12/22 Fred Kaggwa 1
Faculty of Computing and Informatics
Lecture 2
Succeed We Must
Overview
Computer Security Research Group
The history and current events in
“computer network security”
Security Violations (Examples)
Computer Security Objectives
Challenges of Computer security
07/12/22 Fred Kaggwa 2
Faculty of Computing and Informatics
Introduction: The history and current events in “computer network
Succeed We Must security”
How can you define computer security?
Computer Security Research Group
“The protection afforded to an automated
information system in order to attain the
applicable objectives of preserving the
integrity, availability and confidentiality of
information system resources (This
includes hardware, software, firmware,
information/data and
telecommunications)”
(NIST)
07/12/22 Fred Kaggwa 3
Faculty of Computing and Informatics
What do we need to know?
Succeed We Must
For Computer security, we need to know that:
Computer Security Research Group
Software is not secure
Networks are not secure
Trust infrastructures are not secure
And users too are not secure!...someone will tell
you....I think I might have a bank in Nigeria to sell
to you
Internet is not secure
07/12/22 Fred Kaggwa 4
Faculty of Computing and Informatics
What about in those days?
Succeed We Must
Before wide spread use of data processing
equipment
Computer Security Research Group
Security of valuable and very sensitive/private
information could be provided by Physical &
Administrative means. E.g (physical) cabinets/Shelves
with a combination lock, (Administrative) Thorough
research on people before recruitment/hiring.
This is still common in our country…just try to visit
some sensitive organizations.
People are still rigid and resistant to deploy current
security mechanisms.
Organizations still believe “Askaris” (Security Guards)
can do it best!
07/12/22 Fred Kaggwa 5
Faculty of Computing and Informatics
How about in these days?
Succeed We Must
There is a wide spread use of data processing
equipment (mainly in terms of computing
Computer Security Research Group
Computers, Mobile Phones , Automobile etc.
These however need to be interconnected through
networks (public telephone networks, data networks,
and or the internet) to allow easy access.
There is therefore a need for tools that can provide
adequate security of the valuable and very
sensitive/private information stored on these computing
resources.
The collection of such tools that aid in data protection
and impeding hackers is usually called computer
security.
07/12/22 Fred Kaggwa 6
Faculty of Computing and Informatics
So, what is for this course?
Succeed We Must
The wide spread use of computing resources
has brought about:
Computer Security Research Group
The introduction of distributed/shared systems
The use of networks and
The use of communication facilities
All to carry data between user terminals and
computers, and between computers &
computers
There is therefore a need for computer network
security measures/tools that can provide
adequate security & protection during this kind of
transmission.
07/12/22 Fred Kaggwa 7
Faculty of Computing and Informatics
So, what is for this course?
Succeed We Must
NOTE
Computer Security Research Group
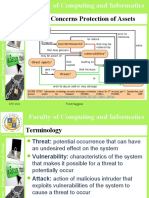
Security is about protecting assets.
Computer Security generally concerns assets of
computer systems: the information and services
they provide .
Computer Network Security focuses on the
protection of assets on computers that are
connected and can be accessed remotely
This course therefore focuses on measures to
deter, prevent ,detect, and correct any security
violations that involve transmission of
information.
07/12/22 Fred Kaggwa 8
Faculty of Computing and Informatics
Some Examples of Security Violations
Succeed We Must
Example 1
Computer Security Research Group
Ali (A) transmits a file to his concubine Beth (B).
The file contains very sensitive information (they
want to go out for a trip-but Ali wants to verbally
lie to the wife that he has a business trip). The
information in the file is to be protected from
disclosure. His wife Cathy (C), who is not
authorized to read the file is able to monitor the
transmission and capture a copy of the file during
its transmission.
07/12/22 Fred Kaggwa 9
Faculty of Computing and Informatics
Some Examples of Security Violations
Succeed We Must
Example 2
Computer Security Research Group
A network manager transmits a message to a
computer under his management. The message
instructs the computer to update an authorization
file to include the identities of a number of new
users who are to be given access to that
computer. A certain user intercepts the message,
alters its contents to add or delete entries and
then forwards the message to the computer,
which accepts the message as coming from the
network manager and updates its authorization
file accordingly.
07/12/22 Fred Kaggwa 10
Faculty of Computing and Informatics
Some Examples of Security Violations
Succeed We Must
Example 3
Computer Security Research Group
An employee is fired without a warning. The
personnel manager sends a message to a server
system to invalidate the employee’s account. When
the invalidation is accomplished, the server is to
post a notice to the employee’s file as confirmation
of action. The employee is able to intercept the
message and delay it long enough to make a final
access to the server to retrieve sensitive information.
The message is then forwarded, the action taken,
and the confirmation posted. The employee’s action
may go unnoticed for some considerable time.
07/12/22 Fred Kaggwa 11
Faculty of Computing and Informatics
Some Examples of Security Violations
Succeed We Must
Example 4
Computer Security Research Group
A message is sent from a certain
customer to a stock broker in Uganda with
instructions for various transactions.
Subsequently, the investments loose value
and the customer denies sending the
message.
07/12/22 Fred Kaggwa 12
Faculty of Computing and Informatics
Reminder: Computer Security
Succeed We Must
Computer Security Research Group
“The protection afforded to an automated
information system in order to attain the
applicable objectives of preserving the integrity,
availability and confidentiality of information
system resources (This includes hardware,
software, firmware, information/data and
telecommunications)”
(NIST)
07/12/22 Fred Kaggwa 13
Faculty of Computing and Informatics
Key Computer Security Objectives
Succeed We Must
You realize that the definition we have just had introduces
the key objectives that are at the heart of computer security.
Computer Security Research Group
1. Confidentiality: This term covers two related concepts
Data confidentiality: Assures that private or confidential
information is not made available or disclosed to
unauthorized individuals
Privacy: Assures that individuals control or influence what
information related to them may be collected and stored and
by whom and to whom that information may be disclosed
07/12/22 Fred Kaggwa 14
Faculty of Computing and Informatics
Key Computer Security Objectives
Succeed We Must
2. Integrity: This term also covers two related concepts
Computer Security Research Group
Data Integrity: Assures that information and programs are
changed only in a specified and authorized manner
System Integrity: Assures that a system performs its
intended function in an unimpaired manner, free from
deliberate or inadvertent unauthorized manipulation of the
system
3. Availability: Assures that systems work promptly and
service is not denied to authorized users.
These three are commonly referred to as the CIA
07/12/22 Fred Kaggwa 15
Faculty of Computing and Informatics
Key Computer Security Objectives (CIA)
Succeed We Must
1. Confidentiality: Preserving authorized restrictions on
Computer Security Research Group
information access and disclosure, including means for
protecting personal privacy and proprietary information A loss
of confidentiality is the unauthorized disclosure of
information.
2. Integrity: Guarding against improper information
modification or destruction, including ensuring information
nonrepudiation and authenticity. A loss of integrity is the
unauthorized modification or destruction of information
3. Availability: Ensuring timely an reliable access to and use
of information. A loss of availability is the disruption of access
to or use of information or an information system
07/12/22 Fred Kaggwa 16
Faculty of Computing and Informatics
Other Computer Security Objectives
Succeed We Must
1. Authenticity: The property of being genuine and being able to be
verified and trusted; confidence in the validity of a transmission, a
Computer Security Research Group
message, or message originator. This means verifying that user are
who they say they are and that each input arriving at the system came
from a trusted source .
2. Accountability: The security goal that generates the requirement
for actions of an entity to be traced uniquely to that entity. This
supports nonrepudiation, deterrence, fault isolation, intrusion
detection and prevention and after-action recovery and legal action.
Because truly secure systems are not yet achievable, we must be able
to trace a security breach to a responsible party. System must keep
records of their activities to permit later forensic analysis to trace
security breaches or to aid in transaction disputes
07/12/22 Fred Kaggwa 17
Faculty of Computing and Informatics
Challenges of Computer Network Security
Succeed We Must
There are a number of reasons that make computer network
security fascinating and complex:
Computer Security Research Group
Security is not as simple as it might first appear to the novice.
Major requirements for security services seem straight
forward (confidentiality, authentication, non-repudiation,
integrity)
However, the mechanisms to implement the mentioned
requirements, can be complex and not easy to
understand.
07/12/22 Fred Kaggwa 18
Faculty of Computing and Informatics
Challenges of Computer Network Security
Succeed We Must
If you are to design a certain security mechanism or
algorithm, it is important to always consider possible
Computer Security Research Group
attacks on the designed security features.
The challenge here is in explicitly exploiting all the
possible unexpected weaknesses in the
mechanism/algorithm
This then makes the design of security
algorithms/mechanisms complex.
07/12/22 Fred Kaggwa 19
Faculty of Computing and Informatics
Challenges of Computer Network Security
Succeed We Must
The placement of the designed various security
mechanisms can also be challenging. It is not easy to
Computer Security Research Group
explicitly decide on where to use these mechanisms.
For example in physical security placement, it is not easy
to know (decide) where (at what points) to place
particular security mechanisms on a network
Also, it can be challenging for the logical security for
example at what layer of the architecture like TCP/IP can
the security mechanisms be placed.
07/12/22 Fred Kaggwa 20
Faculty of Computing and Informatics
Challenges of Computer Network Security
Succeed We Must
The various security mechanisms typically involve more
than one particular algorithm or protocol. They also require
Computer Security Research Group
that participants be in possession of some secret
information (eg. An encryption key). This itself raises
questions on how the secret information is created,
distributed and protected.
There can also be reliance on other communication
protocols of which we may not be sure of their security or
even how to integrate our designed security mechanism
with them.
07/12/22 Fred Kaggwa 21
Faculty of Computing and Informatics
Challenges of Computer Network Security
Succeed We Must
Computer Network security is simply a battle between the
“bad guys” who want to find security holes and the security
Computer Security Research Group
officers (designers or administrators) who try to close these
security holes.
Now, the biggest challenge here is that, the “bad guys”
need only to find one single weakness and then plan on
exploiting it, BUT the designer has to find and eliminate
all weaknesses to achieve perfect security.
07/12/22 Fred Kaggwa 22
Faculty of Computing and Informatics
Challenges of Computer Network Security
Succeed We Must
The other challenge is that, users and system managers
have some natural instinct that makes them perceive
Computer Security Research Group
little benefit from security investment until when a
security failure occurs.
To have an almost good security, it requires regular,
even constant, monitoring and this is difficult in today’s
short-term and overloaded environment (people have
other more “important things” to do than monitoring
security).
System designers still make security an after-thought to
be added to the system, rather than being an integral
part of the design process (very evident in todays
systems)
07/12/22 Fred Kaggwa 23
Faculty of Computing and Informatics
Challenges of Computer Network Security
Succeed We Must
Many users and also security administrators perceive
strong security as a barrier to efficient and user-friendly
Computer Security Research Group
operation of an information system or even the use of
information.
This is deadly, because the organization ends up not
implementing stronger security mechanisms and hence
security challenges
07/12/22 Fred Kaggwa 24
Faculty of Computing and Informatics
Breach of Security: Levels of Impact
Succeed We Must
There can be three levels of impact on either the organizations or
individuals when there is any kind of breach of security (by this we
Computer Security Research Group
mean, a loss of confidentiality, integrity or availability).
LOW: Here, the loss could be expected to have a limited adverse effect
on the organizational operations, organizational assets, or individuals.
By this we mean that, a loss in confidentiality, integrity or availability
might:
Cause a degradation in mission capability to an extent and
duration that the organization is able to perform its primary
functions but the effectiveness of the functions is noticeably
reduced.
Result in minor damage to organizational assets
Result in minor financial loss
Result in minor harm to individuals
07/12/22 Fred Kaggwa 25
Faculty of Computing and Informatics
Breach of Security: Levels of Impact
Succeed We Must
MODERATE: Here, the loss could have a serious
adverse effect on the organizational operations,
Computer Security Research Group
organizational assets, or individuals. By this we mean
that, a loss in confidentiality, integrity or availability might:
Cause a significant degradation in mission capability to
an extent and duration that the organization is able to
perform its primary functions but the effectiveness of the
functions is significantly reduced.
Result in significant damage to organizational assets
Result in significant financial loss
Result in significant harm to individuals that does not
involve loss of life or serious life-threatening injuries.
07/12/22 Fred Kaggwa 26
Faculty of Computing and Informatics
Breach of Security: Levels of Impact
Succeed We Must
HIGH: Here, the loss could be expected to have a severe or
catastrophic adverse effect on the organizational
Computer Security Research Group
operations, organizational assets, or individuals. By this we
mean that, a loss in confidentiality, integrity or availability
might:
Cause a severe degradation in or loss of mission
capability to an extent and duration that the organization is
not able to perform one or more of its primary functions.
Result in major damage to organizational assets
Result in major financial loss
Result in severe or catastrophic harm to individuals
involving loss of life or serious life-threatening injuries.
07/12/22 Fred Kaggwa 27
Faculty of Computing and Informatics
Succeed We Must
Computer Security Research Group
Any Questions?
07/12/22 Fred Kaggwa 28
You might also like
- Etical HackingDocument60 pagesEtical HackingraniNo ratings yet
- The Ultimate CISSP Study PlanDocument63 pagesThe Ultimate CISSP Study PlanLakshmi Kiran AtthuluriNo ratings yet
- Solution Manual For Computer Networking A Top Down Approach 6 e 6th EditionDocument38 pagesSolution Manual For Computer Networking A Top Down Approach 6 e 6th Editionbrookemaxwellfhfpy100% (10)
- Va PT ReportDocument16 pagesVa PT ReportRobinNo ratings yet
- Cyber Security Operations Centre A User-Cantered Machine Learning FrameworkDocument6 pagesCyber Security Operations Centre A User-Cantered Machine Learning FrameworkIJRASETPublicationsNo ratings yet
- Injection and Broken Access ControlDocument4 pagesInjection and Broken Access ControlSiyabongaNo ratings yet
- Lecture 4: Physical Security: Succeed We MustDocument43 pagesLecture 4: Physical Security: Succeed We MustTimo AlexNo ratings yet
- CNS Lecture1-Introduction A1 - BCSDocument20 pagesCNS Lecture1-Introduction A1 - BCSTimo AlexNo ratings yet
- Ijcsrtv1is050024 PDFDocument6 pagesIjcsrtv1is050024 PDFIJERT.ORGNo ratings yet
- A Summary and Review of The Current Trends in Database SecurityDocument3 pagesA Summary and Review of The Current Trends in Database SecurityInternational Journal of Innovative Science and Research TechnologyNo ratings yet
- Introduction - Cont'd: Computer Network SecurityDocument36 pagesIntroduction - Cont'd: Computer Network SecurityTimo AlexNo ratings yet
- Cyber Security of Critical InfrastructuresDocument4 pagesCyber Security of Critical InfrastructurescheintNo ratings yet
- Attack Detection in IoT Critical Infrastructures A Machine Learning and Big Data Processing ApproachDocument8 pagesAttack Detection in IoT Critical Infrastructures A Machine Learning and Big Data Processing ApproachCarlosNo ratings yet
- Security Concerns Protection of Assets: Succeed We MustDocument10 pagesSecurity Concerns Protection of Assets: Succeed We MustTimo AlexNo ratings yet
- Research Paper On Private SecurityDocument4 pagesResearch Paper On Private Securitywonopwwgf100% (1)
- IoT Based Smart Cities-1Document7 pagesIoT Based Smart Cities-1Meenachi SundaramNo ratings yet
- Optimal Performance of Security by Fragmentation and Replication of Data in CloudDocument6 pagesOptimal Performance of Security by Fragmentation and Replication of Data in CloudIJRASETPublicationsNo ratings yet
- Materi - Presentasi - Kegiatan - Bimtek - Kesiapsiagaan - Teknis - PenangananDocument30 pagesMateri - Presentasi - Kegiatan - Bimtek - Kesiapsiagaan - Teknis - Penangananportal datanyaNo ratings yet
- Cyber Security - Iot: 4. Unauthorized Access or ControlDocument4 pagesCyber Security - Iot: 4. Unauthorized Access or ControlKhushal SinghNo ratings yet
- A Trusted Feature Aggregator Federated Learning For Distributed Malicious Attak Detection-14Document15 pagesA Trusted Feature Aggregator Federated Learning For Distributed Malicious Attak Detection-14Canada OlympiadNo ratings yet
- Iot WP Iot Security 1Document12 pagesIot WP Iot Security 1ravinab999No ratings yet
- Webcast 124110Document139 pagesWebcast 124110hadini.jamaleddineNo ratings yet
- 2 IJAEST Volume No 2 Issue No 2 Analysis of Information Security Algorithm Based On Network Business Security 124 131Document8 pages2 IJAEST Volume No 2 Issue No 2 Analysis of Information Security Algorithm Based On Network Business Security 124 131iserpNo ratings yet
- V2i410 PDFDocument4 pagesV2i410 PDFIJCERT PUBLICATIONSNo ratings yet
- Cyber Security PaperDocument4 pagesCyber Security PaperHimanshu GoelNo ratings yet
- Managing The Risk of IoT - Joa - Eng - 0517 HugoDocument8 pagesManaging The Risk of IoT - Joa - Eng - 0517 HugoHugo Oswaldo Alonzo RamírezNo ratings yet
- A Review: Artificial Intelligence and Expert Systems For Cyber SecurityDocument5 pagesA Review: Artificial Intelligence and Expert Systems For Cyber SecuritybijejournalNo ratings yet
- Hardware and Embedded Security in The Context of Internet of ThingsDocument5 pagesHardware and Embedded Security in The Context of Internet of ThingsTeddy IswahyudiNo ratings yet
- Enterprise Iot Security and Scalability: How Unikernels Can Improve The Status QuoDocument6 pagesEnterprise Iot Security and Scalability: How Unikernels Can Improve The Status QuoDjango BoyeeNo ratings yet
- How Intrinsic Security Protects Against Education DisruptionDocument9 pagesHow Intrinsic Security Protects Against Education DisruptionsepthydwijayanthyNo ratings yet
- Research Paper Topics in Computer SecurityDocument4 pagesResearch Paper Topics in Computer Securitynlaxlvulg100% (1)
- Thomas Case StudyreportDocument11 pagesThomas Case Studyreport21UCS152 J.MICHEAL AUGUSTINNo ratings yet
- Intrusion Detection System Through Advance Machine Learning For The Internet of Things NetworksDocument7 pagesIntrusion Detection System Through Advance Machine Learning For The Internet of Things NetworksMuhammad Junaid KhalidNo ratings yet
- Network SecurityDocument54 pagesNetwork SecurityfiromsaNo ratings yet
- Leveraging Centralized Threat IntelligenceDocument16 pagesLeveraging Centralized Threat Intelligenceknow_idea8867No ratings yet
- Synopsis Junaid V2.2Document14 pagesSynopsis Junaid V2.2Muhammad Junaid KhalidNo ratings yet
- (IJCST-V6I6P22) :prof. Sudhir Morey, Prof. Sangpal SarkateDocument7 pages(IJCST-V6I6P22) :prof. Sudhir Morey, Prof. Sangpal SarkateEighthSenseGroupNo ratings yet
- 1 s2.0 S016740482200445X MainDocument27 pages1 s2.0 S016740482200445X MainAkashah ArshadNo ratings yet
- Database Security and Encryption: A Survey Study: International Journal of Computer Applications May 2012Document8 pagesDatabase Security and Encryption: A Survey Study: International Journal of Computer Applications May 2012iyelNo ratings yet
- Energies 15 08692 v3Document22 pagesEnergies 15 08692 v3Андрей ШнукалоNo ratings yet
- Network Security Research Papers IeeeDocument6 pagesNetwork Security Research Papers Ieeejppawmrhf100% (1)
- A System Architecture For The Detection of Insider Attacks in Big Data SystemsDocument14 pagesA System Architecture For The Detection of Insider Attacks in Big Data SystemsAbhishek DasNo ratings yet
- Cyber SecurityDocument7 pagesCyber SecurityVINCENT MUHARINo ratings yet
- Danish Javeed, Muhammad Shahid Saeed, Ijaz Ahmad, Muhammad Adil, Prabhat Kumar, and A K M Najmul Islam Affiliation Not Available December 14, 2023Document27 pagesDanish Javeed, Muhammad Shahid Saeed, Ijaz Ahmad, Muhammad Adil, Prabhat Kumar, and A K M Najmul Islam Affiliation Not Available December 14, 2023Dr. V. Padmavathi Associate ProfessorNo ratings yet
- Network SecurityDocument66 pagesNetwork SecurityTariqul IslamNo ratings yet
- 1 s2.0 S1084804518300419 MainDocument11 pages1 s2.0 S1084804518300419 Maindodol garutNo ratings yet
- 1 s2.0 S2542660519301957 Main PDFDocument19 pages1 s2.0 S2542660519301957 Main PDFArunNo ratings yet
- Review: Deep Learning Methods For Cybersecurity and Intrusion Detection SystemsDocument6 pagesReview: Deep Learning Methods For Cybersecurity and Intrusion Detection SystemsChaima BelhediNo ratings yet
- Internet of Things Security Research PaperDocument6 pagesInternet of Things Security Research Papergvzz4v44100% (1)
- Study On Security and Prevention Strategies of Computer NetworkDocument3 pagesStudy On Security and Prevention Strategies of Computer NetworkArfan AfandyNo ratings yet
- A Comparative Study of Using Boosting-Based Machine Learning Algorithms For Iot Network Intrusion DetectionDocument15 pagesA Comparative Study of Using Boosting-Based Machine Learning Algorithms For Iot Network Intrusion DetectionHeather WinNo ratings yet
- An Ensemble Deep Learning Based Ids For Iot Using Lambda ArchitectureDocument17 pagesAn Ensemble Deep Learning Based Ids For Iot Using Lambda ArchitectureHatim LakhdarNo ratings yet
- What Is Zero Trust? CISA Zero Trust Maturity ModelDocument2 pagesWhat Is Zero Trust? CISA Zero Trust Maturity ModelVijay Anandhan TDNo ratings yet
- Zero Trust Security Model 1703007366Document2 pagesZero Trust Security Model 1703007366mohammed benhmammouchNo ratings yet
- Security Tactics For People, Processes, and TechnologyDocument6 pagesSecurity Tactics For People, Processes, and TechnologyAleir PinsalaNo ratings yet
- Cyber CrimesDocument2 pagesCyber Crimesnyoikeian0No ratings yet
- 154-Article Text-229-3-10-20230813Document24 pages154-Article Text-229-3-10-20230813lailamohd33No ratings yet
- Article 2Document16 pagesArticle 2ked25482No ratings yet
- Cipher Home A Smart Home With Network Level Security To IoT DevicesDocument5 pagesCipher Home A Smart Home With Network Level Security To IoT DevicesInternational Journal of Innovative Science and Research TechnologyNo ratings yet
- Live Vs Dead Computer Forensic Image AcquisitionDocument3 pagesLive Vs Dead Computer Forensic Image AcquisitionSon NguyenNo ratings yet
- A Semantic Study On Emerging Risk and Security Management in Cloud ComputingDocument11 pagesA Semantic Study On Emerging Risk and Security Management in Cloud ComputingIJRASETPublicationsNo ratings yet
- Database Security An Overview and Analysis of Current TrendDocument3 pagesDatabase Security An Overview and Analysis of Current TrendInternational Journal of Innovative Science and Research TechnologyNo ratings yet
- Performance Analysis of Data Security Using Cryptographic Policy With Instance Based Encryption in Cloud ComputingDocument6 pagesPerformance Analysis of Data Security Using Cryptographic Policy With Instance Based Encryption in Cloud ComputingEditor IJTSRDNo ratings yet
- Data Loss Prevention Technologies: (Manuscript Received April 14, 2009)Document9 pagesData Loss Prevention Technologies: (Manuscript Received April 14, 2009)bbdgei_tnpNo ratings yet
- Safe and Secure Cyber-Physical Systems and Internet-of-Things SystemsFrom EverandSafe and Secure Cyber-Physical Systems and Internet-of-Things SystemsNo ratings yet
- Pci DSSDocument32 pagesPci DSSKori Anthony SmithNo ratings yet
- Phases of The SDLCDocument5 pagesPhases of The SDLCAnnarathna ANo ratings yet
- Capricorn Authorisation LetterDocument1 pageCapricorn Authorisation LetterP S AnanthNo ratings yet
- Syllabus ptsv2Document7 pagesSyllabus ptsv2adam593No ratings yet
- En Cybersecurity Lab4Document4 pagesEn Cybersecurity Lab4Merveille josepha FokoNo ratings yet
- Devoir DSIDocument4 pagesDevoir DSIhenri victor bogmisNo ratings yet
- Key Loggers & SpywaresDocument29 pagesKey Loggers & SpywaresElit HakimiNo ratings yet
- Network SecurityDocument22 pagesNetwork Securitysalution technologyNo ratings yet
- h19084 Powerstore CybersecurityDocument18 pagesh19084 Powerstore CybersecuritybuyoloNo ratings yet
- MOSS: Your Monthly FLOSS Magazine: April 2010: Issue #04Document24 pagesMOSS: Your Monthly FLOSS Magazine: April 2010: Issue #04Luke SkywalkerNo ratings yet
- Lead Ethical Hacker - 4pDocument4 pagesLead Ethical Hacker - 4pAziz AzizNo ratings yet
- BRA Symmetric Encryption Algorithm: Remzi AKTAYDocument4 pagesBRA Symmetric Encryption Algorithm: Remzi AKTAYaijbmNo ratings yet
- Sha256 384 512Document50 pagesSha256 384 512Melanie WallaceNo ratings yet
- Cwna Security NotesDocument12 pagesCwna Security Notesvivek vermaNo ratings yet
- UTD-SASE-2.1 Workshop Guide-20231026Document109 pagesUTD-SASE-2.1 Workshop Guide-20231026angelgimNo ratings yet
- Hash List Percobaan 2Document1 pageHash List Percobaan 2Abdul HadiNo ratings yet
- Any Four FromDocument6 pagesAny Four FromHenryPDTNo ratings yet
- Computer Crime Homework 3 Protecting Personal DataDocument1 pageComputer Crime Homework 3 Protecting Personal DataSia DhimanNo ratings yet
- Materi Dan Soal Lengkap CpnsDocument9 pagesMateri Dan Soal Lengkap CpnsdeniNo ratings yet
- Network Security SUMSDocument9 pagesNetwork Security SUMSKaushal Prajapati0% (1)
- Google AssistantDocument121 pagesGoogle AssistantElmer III PelayoNo ratings yet
- ThreatMetrix Cybercrime Defender PlatformDocument3 pagesThreatMetrix Cybercrime Defender PlatformJoshua McAfeeNo ratings yet
- Secure Socket LayerDocument51 pagesSecure Socket LayerRaviNaganathanNo ratings yet
- Access Control Policy - V12Document6 pagesAccess Control Policy - V12Brian ThelwellNo ratings yet
- Diffie-Hellman Key Exchange Man-in-the-Middle Attack Elgamal Cryptographic SystemDocument24 pagesDiffie-Hellman Key Exchange Man-in-the-Middle Attack Elgamal Cryptographic SystemAbhijeet ThamakeNo ratings yet