0% found this document useful (0 votes)
388 views119 pagesBlock Cipher Fundamentals
The document discusses block ciphers and stream ciphers, explaining that block ciphers encrypt fixed-size blocks of plaintext into ciphertext, while stream ciphers encrypt digital data streams on a bit-by-bit or byte-by-byte basis. It also describes the Feistel cipher structure, which is used in many symmetric block encryption algorithms, and examines the design principles of Feistel ciphers including diffusion, confusion, substitution boxes, and permutation boxes.
Uploaded by
Tanvir Khasru AdnanCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PPTX, PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
388 views119 pagesBlock Cipher Fundamentals
The document discusses block ciphers and stream ciphers, explaining that block ciphers encrypt fixed-size blocks of plaintext into ciphertext, while stream ciphers encrypt digital data streams on a bit-by-bit or byte-by-byte basis. It also describes the Feistel cipher structure, which is used in many symmetric block encryption algorithms, and examines the design principles of Feistel ciphers including diffusion, confusion, substitution boxes, and permutation boxes.
Uploaded by
Tanvir Khasru AdnanCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PPTX, PDF, TXT or read online on Scribd
- Introduction: Overview and significance of block encryption algorithms in current use, focusing on Feistel block cipher.
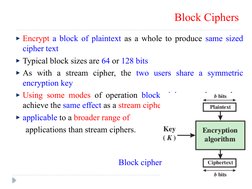
- Block Ciphers: Details on block ciphers and their operation, including modes and characteristics compared to stream ciphers.
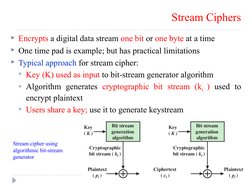
- Stream Ciphers: Explains the encryption of data streams one bit at a time, with reference to practical applications.
- Feistel Structure Motivation: Insights into reversible and irreversible mappings in Feistel Cipher Structure and its importance.
- Ideal Block Cipher: Discusses the concept of ideal block cipher and its problems related to block sizes.
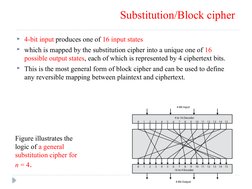
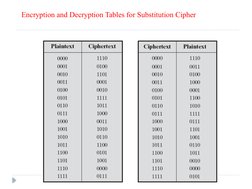
- Substitution/Block Cipher: Covers the operation of substitution ciphers and their relation to block ciphers.
- Substitution-Permutation Networks: Overview of substitution-permutation networks as a basis for block ciphers, emphasizing Shannon's contribution.
- Diffusion and Confusion: Detailed discussion on diffusion and confusion techniques used in enhancing encryption strength.
- Components of Modern Block Cipher: Examines the roles of permutation boxes (P-boxes) in modern block cipher structures.
- S-Boxes: Introduction to substitution boxes and their application in ciphers for security enhancement.
- Exclusive-Or Operation: Describes the role of the exclusive-OR operation in block ciphers and their characteristics.
- Circular Shift: Covers the circular shift operation used in some modern block ciphers.
- Product Ciphers: Introduction to product ciphers combining substitution and permutation principles.
- Classes of Product Ciphers: Divides product ciphers into Feistel and Non-Feistel classes, detailing their attributes.
- Feistel Cipher Structure: Articulates Feistel cipher logic, its importance, and dual application in encryption and decryption.
- Symmetric Block Cipher Algorithms: Overview of common symmetric block cipher algorithms such as DES, 3DES, and AES.
- Data Encryption Standard (DES): Explains the Data Encryption Standard, its history, and its transformation processes.
- Triple DES: Describes the Triple DES encryption standard and its enhancements over the original DES.
- Concerns of DES: Details concerns about DES, including potential vulnerabilities in its design and key management.
- Cryptanalysis on Block Ciphers: Overview of cryptanalysis methods applicable to block ciphers including brute force and meet-in-the-middle attacks.