Professional Documents
Culture Documents
Mapa de Procesos Itil 2011
Mapa de Procesos Itil 2011
Uploaded by
Milagros Campos RamirezCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Mapa de Procesos Itil 2011
Mapa de Procesos Itil 2011
Uploaded by
Milagros Campos RamirezCopyright:
Available Formats
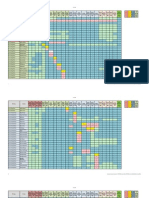
7 Steps improvement process
Continual Service Improvement
Service Measurement
Service Reporting
Service Design
Define policies and methods Plan design resources and capabilities Coordinate design activities Manage design risks and issues Improve service design
ITIL 2011
Plan individual designs Coordinate individual designs Monitor individual designs Review designs and handover SDP
Design Coordination
SKMS
SLA/ OLA
Service Level Management
Planning Maintain catalogue
Capacity Management
Business/Service/ Component capacity Capacity Plan
Availability Management
Service/Component availability Requirements Risk assessment and management Vital Business Functions (VBF) Plan and design for availability Implement Monitor, adjust & maintain Report & Improve
SKMS AMIS
IT Service Continuity Management
ITSCM and the BCM Business Impact Analysis (BIA) Risk assessment and management Countermeasures Requirements and strategy Plan recovery (DRP) and continuity Implement Test and review On going operation and maintain Invoke
Risk Management
Security Policies
Information Security management
Risk assessment and management Countermeasures Define & enforce information security policies Requirements & plans Document & implement security controls Monitor & manage security breach/ incidents/problems Improvement of security controls
SKMS
SCMIS UC
Capture Service Level Requirements Review and update OLA (and UC) Negotiate & establish SLA Produce and present service reports
SKMS CMIS
Technical Business
Service Catalogue Management
Define service and service package Produce service catalogues
Supplier Management
Strategies & policies Requirements Evaluation of new suppliers Establish contract Performance Renew/terminate suppliers and contracts Maintain SCMIS
10% 30% 20%
Requirements Plan, design and model for performance Demand Management Application sizing Monitor, adjust & maintain Report & Improve
Projected Service Unavailability Performance reports
Continuity Plan Availability Plan
Descripti on Servic Suppor e t Hours
SLA
Duratio n Signatur e
SLA
Align with service Portfolio and CMS
SKMS
Service Portfolio
Service Strategy
Strategy Management for IT Services Standards Support business vision and mission Architecture Identify customers Prioritize investments Identify market space Governance
SKMS ISMS
Service Design Package (SDP)
SLA
SKMS
Service Catalogues
Publish and update Maintain service catalogues
Demand Management
Business activities and patterns
Service Transition
3
CAB Change Management
Log, review and categorize Assess and authorize build and test Plan and coordinate build and test Authorize deployment Coordinate deployment Measure and report Post Implementation Review Emergency change
Discovery tools
10% 30%
Service Operation
IT Operations Management function Applications Management function Technical Management function Service Desk function Self serve
Service portfolio Management Define Analyse Authorise Charter
Business relationship Management Customer Portfolio Customer Agreements Portfolio Customer Satisfaction Service Requirements
IT Financial Management
Service Cost Structure Evaluate services Funding Charge-back Return On Investment
Asset and Configuration Management
Financial Plan Definitive Media Library Mon 27 Tue 28
SKMS
Plan and Identify Maintain and control Status report Verification and audit Inventory and licence management Spares CMS CMDBs
Organization and RACI Charts
Change Schedule
SKMS
Service Requests Events and alerts
Request fulfillment
Modeling
Request Models
Patch Management
Problem Management
Detect and log Categorise and prioritize Investigate and diagnose Workaround Validation and Tests Plans Deployment Plans
Release and Deployment Management Plan Prepare Build and test cycles Pilot and tests Deployment planning Execute deployment, transfer, retire Early life support Release review
Work order
Incident Management
Identifiy and log Categorize & prioritize Initial support
Transition Planning and Support
Setup Transition Strategy Lifecycle stages Prepare transition Transition policies release policies Support transition
Access Management
Log request Receive request Automate workflow Request verification Fulfillment Closure
Event Management
Design for event management Configure system Notification/ Detection/Log Filter/correlation/ significance Alert and response Respond and close Revise and tuning
And asset
Diagnose Provide access rights Log and track access Remove-restrict access rights Maintain groups and roles Resolve and recover Close Follow up & communicate
3
Release packages
Plan and coordinate Transition
SKMS
Incident records Known error records Problem records
Raise known error Resolve Close Major problem review
Service Validation and Testing
Service and quality assurance
Change Evaluation
Evaluation plan Expected and unexpected effects of change Evaluation of expected performance Evaluation of real performance Risk management Test plan and results
Service Knowledge Management
Knowledge management strategy Knowledge transfer Manage data, information, knowledge Using SKMS
1
Request Models
Test policies Test strategy Test levels and models Test approach and technique
SKMS
Roles and groups
User satisfaction survey
Service Improvement proposals
Version 2011/11/07
Organizational Change
Deming Cycle
Ownership
Service review and improvement planning
Process review and compliance
CSI Register
CSI Framework and Quality System
IT Governance
You might also like
- Quality Manual, IsO 13485 and MDR, Free TemplateDocument13 pagesQuality Manual, IsO 13485 and MDR, Free TemplateNADJAH YOUSFINo ratings yet
- ITSM Roles by Process MatrixDocument4 pagesITSM Roles by Process MatrixWarnher100% (5)
- ITIL v3 Service Lifecycle ChartDocument1 pageITIL v3 Service Lifecycle Chartdardenne_tNo ratings yet
- Materna ITIL Poster v4.0.0Document2 pagesMaterna ITIL Poster v4.0.0desertedtweek93% (15)
- ITSM Gap Analysis - TemplateDocument57 pagesITSM Gap Analysis - TemplateAnuradha Lipare86% (7)
- SolutionsDocument47 pagesSolutionsPerry Si100% (1)
- ITIL Service Strategy Poster PDFDocument1 pageITIL Service Strategy Poster PDFDominic Benedito100% (4)
- Itsm and Itil Capability Assessment ChecklistDocument1 pageItsm and Itil Capability Assessment ChecklistFarina James0% (1)
- ITIL Foundation Overview v5 4 FINALDocument2 pagesITIL Foundation Overview v5 4 FINALKhaled KittanaNo ratings yet
- Itil Poster The Big Picture CFN PeopleDocument1 pageItil Poster The Big Picture CFN PeopleFabrizio MachadoNo ratings yet
- ITIL Process Maturity FrameworkDocument2 pagesITIL Process Maturity FrameworkpdsramaraoNo ratings yet
- ITSM Assessment Artifacts-1Document1 pageITSM Assessment Artifacts-1Murali PvNo ratings yet
- Optimizing Tableau Aws Redshift WhitepaperDocument33 pagesOptimizing Tableau Aws Redshift WhitepaperweNo ratings yet
- SmartCare Strategy Roadmap PDFDocument31 pagesSmartCare Strategy Roadmap PDFuxunNo ratings yet
- InternshipDocument15 pagesInternshipPrince PraveenNo ratings yet
- ITIL Process Map WallchartDocument2 pagesITIL Process Map Wallchartphilmeyer100% (3)
- ITIL 2011 Process Maps Visio-3 Service TransitionDocument1 pageITIL 2011 Process Maps Visio-3 Service Transitionjesus_yustasNo ratings yet
- RFP For ISO 20000 Service Desk Implementation-Final-backupDocument53 pagesRFP For ISO 20000 Service Desk Implementation-Final-backupwmolinariNo ratings yet
- ITIL 2011 - The Big Picture v.2.0 - CFN PeopleDocument1 pageITIL 2011 - The Big Picture v.2.0 - CFN PeopleChristian Feldbech NissenNo ratings yet
- ITIL V3 Lifecycle OverblikDocument1 pageITIL V3 Lifecycle OverblikDavid RovsingNo ratings yet
- CMC PresentationDocument34 pagesCMC PresentationSandeep Kumar Sinha100% (3)
- Itil Cobit Mapping TemplateDocument6 pagesItil Cobit Mapping Templategobits100% (3)
- Itil V3 - at A Glance: Service DesignDocument1 pageItil V3 - at A Glance: Service DesignAleksandr TsirkunovNo ratings yet
- ITIL Service Design PosterDocument1 pageITIL Service Design PosterDominic Benedito100% (6)
- Example Configuration Management System Diagram PDFDocument1 pageExample Configuration Management System Diagram PDFmartid58No ratings yet
- Itil v3 Process ModelDocument2 pagesItil v3 Process ModelMahya Bagheri100% (1)
- Process To PraticesDocument3 pagesProcess To PraticesAndrea GiulianiNo ratings yet
- ITIL KPIs and The IT Balanced ScorecardDocument37 pagesITIL KPIs and The IT Balanced Scorecardtobitobsen_20013953100% (11)
- Checklist of Recommended ITIL Documents For Processes and Functions enDocument18 pagesChecklist of Recommended ITIL Documents For Processes and Functions enFeleke AfeworkNo ratings yet
- ITIL v.3 Processes & FunctionsDocument5 pagesITIL v.3 Processes & FunctionsAndrea GiulianiNo ratings yet
- Itil Cobit v4Document4 pagesItil Cobit v4Catherine Niwagaba100% (1)
- ITIL PresentationDocument29 pagesITIL PresentationRoger Alexander100% (1)
- Process Improvement Calculations ToolsDocument65 pagesProcess Improvement Calculations ToolsNevets Nonnac100% (1)
- IT Service ManagementDocument21 pagesIT Service ManagementSreedhar Dachepalli100% (1)
- ITIL Capacity Management: Much More Than Charts Over CoffeeDocument44 pagesITIL Capacity Management: Much More Than Charts Over CoffeeGary Reynolds100% (1)
- ITIL Cobit MappingDocument16 pagesITIL Cobit Mappingapi-383689667% (3)
- 03 Derek Gillard - Service Catalogue JourneyDocument28 pages03 Derek Gillard - Service Catalogue Journeyarsman1100% (1)
- It Service Management: Improvement Plan: BY Uday Mishra, Global It Service Operation ManagerDocument31 pagesIt Service Management: Improvement Plan: BY Uday Mishra, Global It Service Operation Managerrajesh.j162763No ratings yet
- Asset Management For ITSMF Nicole Conboy, NCADocument14 pagesAsset Management For ITSMF Nicole Conboy, NCAAtish JadhavNo ratings yet
- IT Service Management (ITSM)Document4 pagesIT Service Management (ITSM)Saikat BanerjeeNo ratings yet
- Mountainview-ITIL V3 Process Poster v3Document1 pageMountainview-ITIL V3 Process Poster v3Martin Leck100% (1)
- Continual Service Improvement (ITIL CSI) v3 - Definition of CSI InitiativesDocument1 pageContinual Service Improvement (ITIL CSI) v3 - Definition of CSI InitiativesAndrea GiulianiNo ratings yet
- Continual Service Improvement (ITIL CSI) v3 - Process EvaluationDocument1 pageContinual Service Improvement (ITIL CSI) v3 - Process EvaluationAndrea GiulianiNo ratings yet
- Visual CMDB Overview & SetupDocument13 pagesVisual CMDB Overview & SetupLuis RizoNo ratings yet
- ITIL ConceptDocument57 pagesITIL Conceptsumanpk133100% (1)
- IT Service Management: OwnershipDocument22 pagesIT Service Management: OwnershipchandrukanthNo ratings yet
- CHG Mindmap v4Document1 pageCHG Mindmap v4Paul James BirchallNo ratings yet
- Itil CartoonDocument43 pagesItil CartoonAstro Victor100% (1)
- ITIL - Foundation NewDocument155 pagesITIL - Foundation NewAnonymous zWUrYoc2VNo ratings yet
- FIN Mindmap v4Document1 pageFIN Mindmap v4Paul James BirchallNo ratings yet
- Dynamics 365 Enterprise Edition Licensing GuideDocument43 pagesDynamics 365 Enterprise Edition Licensing GuideNVNo ratings yet
- ISO 20000-1 2011 Audit ChecklistDocument10 pagesISO 20000-1 2011 Audit Checklistjoelc5840% (1)
- ISU ITSM Tool RequirementsDocument106 pagesISU ITSM Tool RequirementsPrakash LakshmipathyNo ratings yet
- Disaster Recovery Service-Level Management Complete Self-Assessment GuideFrom EverandDisaster Recovery Service-Level Management Complete Self-Assessment GuideNo ratings yet
- Disaster Recovery As A Service A Complete Guide - 2020 EditionFrom EverandDisaster Recovery As A Service A Complete Guide - 2020 EditionNo ratings yet
- 09 Q7 ITIL 2011 Overview Diagram English 11012015Document1 page09 Q7 ITIL 2011 Overview Diagram English 11012015Khaled KittanaNo ratings yet
- Itil at A GlanceDocument1 pageItil at A Glancefernandomp100% (1)
- Itil MapDocument1 pageItil Mapmohd_qureshi_4100% (1)
- Stages and Processes ITILDocument6 pagesStages and Processes ITILHem Raj BhattaNo ratings yet
- CHART v.2.0 - ITSM - DRUCK PDFDocument1 pageCHART v.2.0 - ITSM - DRUCK PDFamirel80No ratings yet
- ITIL Winning FormulaDocument1 pageITIL Winning Formulagopi_4441100% (1)
- MC14500B Industrial Control Unit Handbook 1977Document113 pagesMC14500B Industrial Control Unit Handbook 1977FLAVIO100% (1)
- Ibm Utl Bomc 2.20 Anyos AnycpuDocument76 pagesIbm Utl Bomc 2.20 Anyos AnycpuPathoy PathicNo ratings yet
- Etika Dan Regulasi, UU ITE, HKIDocument23 pagesEtika Dan Regulasi, UU ITE, HKIFahan AdityaNo ratings yet
- Brake SystemDocument81 pagesBrake SystemRie ReiNo ratings yet
- Hydraulic Elevators Basic ComponentsDocument16 pagesHydraulic Elevators Basic ComponentsIkhwan Nasir100% (2)
- Manual Instalare Programare BFT VirgoDocument15 pagesManual Instalare Programare BFT Virgoanomin89No ratings yet
- Tesi Ufficiale Roberto Mario de StefanoDocument146 pagesTesi Ufficiale Roberto Mario de StefanoRoberto Mario De StefanoNo ratings yet
- UNIT I 1.6 Group-TechnologyDocument78 pagesUNIT I 1.6 Group-Technologyprof_panneerNo ratings yet
- Note 8 PLC IntroductionDocument23 pagesNote 8 PLC Introductionkandavel71No ratings yet
- Ts 7400 DatasheetDocument1 pageTs 7400 DatasheetmanteshbNo ratings yet
- en Quick Setup Guide VEGAPULS 6X Two Wire 4 20 MA HARTDocument28 pagesen Quick Setup Guide VEGAPULS 6X Two Wire 4 20 MA HARTSagetunov AryaNo ratings yet
- Ejot FDSDocument20 pagesEjot FDSJacobNo ratings yet
- SoftwareTutorial ZXT58Document17 pagesSoftwareTutorial ZXT58Luis Oscar Quispe ValeroNo ratings yet
- B GRADE 12 EMPOWERMENT TECHNOLOGY Q3M1 LearnerDocument25 pagesB GRADE 12 EMPOWERMENT TECHNOLOGY Q3M1 LearnerDanisse Casanova75% (8)
- Project Documentation - UMRR Serial Relay Option Data Sheet: Project Number: SMS Project NumberDocument12 pagesProject Documentation - UMRR Serial Relay Option Data Sheet: Project Number: SMS Project NumberCORAL ALONSONo ratings yet
- ASUG84403 - Implementation of Geographical Information SystemsDocument26 pagesASUG84403 - Implementation of Geographical Information SystemsabhishekNo ratings yet
- Grundfos Packaged Solutions: Grundfos Americas Brookshire, TX 77423 WWW - Grundfos.usDocument8 pagesGrundfos Packaged Solutions: Grundfos Americas Brookshire, TX 77423 WWW - Grundfos.usJhon Jairo Arango MarquezNo ratings yet
- Portaria 377 2021 Televisores Compulsoriedade - Pt.enDocument43 pagesPortaria 377 2021 Televisores Compulsoriedade - Pt.enSylvioAlvesNo ratings yet
- MC R20 - Unit-2Document43 pagesMC R20 - Unit-2Yadavilli VinayNo ratings yet
- Laptop Motherboard RepairDocument195 pagesLaptop Motherboard RepairAsadNo ratings yet
- SMP 4 Installation GuideDocument43 pagesSMP 4 Installation GuideSam AyodeleNo ratings yet
- QEI SCADA SystemsDocument1 pageQEI SCADA SystemsLee PearceNo ratings yet
- FO - FC3145 - E01 - 1 ZTE LR14 LTE FDD DL MIMO Feature Guide 35PDocument35 pagesFO - FC3145 - E01 - 1 ZTE LR14 LTE FDD DL MIMO Feature Guide 35PSasanka Chamara GamageNo ratings yet
- Resume Ibm San Storage EngineerDocument43 pagesResume Ibm San Storage Engineerakbisoi1No ratings yet