Professional Documents
Culture Documents
IPsec PDF
IPsec PDF
Uploaded by
Chester ConnollyOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
IPsec PDF
IPsec PDF
Uploaded by
Chester ConnollyCopyright:
Available Formats
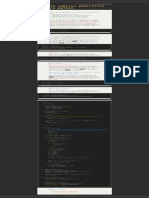
IPSEC
packetlife.net
Protocols
Encryption Algorithms
Internet Security Association and Key Management
Protocol (ISAKMP)
A framework for the negotiation and management of
security associations between peers (traverses UDP/500)
Internet Key Exchange (IKE)
Responsible for key agreement using asymmetric
cryptography
Encapsulating Security Payload (ESP)
Provides data encryption, data integrity, and peer
authentication; IP protocol 50
Authentication Header (AH)
Provides data integrity and peer authentication, but not data
encryption; IP protocol 51
L2
IP
TCP/UDP
Transport
Mode
L2
IP
ESP/AH
Tunnel
Mode
L2
New IP
ESP/AH
Strength
56
Weak
168
Medium
AES Symmetric
128/192/256
Strong
RSA Asymmetric
1024+
Strong
DES Symmetric
3DES Symmetric
Hashing Algorithms
Length (Bits)
MD5 128
Strength
Medium
SHA-1 160
Strong
IKE Phases
Phase 1.5 (optional)
Xauth can optionally be implemented to enforce
user authentication
TCP/UDP
IP
TCP/UDP
Transport Mode
The ESP or AH header is inserted behind the IP header; the
IP header can be authenticated but not encrypted
Tunnel Mode
A new IP header is created in place of the original; this
allows for encryption of the entire original packet
Configuration
crypto isakmp policy 10
encryption aes 256
hash sha
authentication pre-share
group 2
lifetime 3600
Key Length (Bits)
Phase 1
A bidirectional ISAKMP SA is established
between peers to provide a secure management
channel (IKE in main or aggressive mode)
IPsec Modes
Original
Packet
Type
ISAKMP Policy
Phase 2
Two unidirectional IPsec SAs are established for
data transfer using separate keys (IKE quick
mode)
Terminology
Data Integrity
Secure hashing (HMAC) is used to ensure data
has not been altered in transit
Data Confidentiality
Encryption is used to ensure data cannot be
intercepted by a third party
Data Origin Authentication
Authentication of the SA peer
ISAKMP Pre-Shared Key
crypto isakmp key 1 MySecretKey address 10.0.0.2
IPsec Transform Set
crypto ipsec transform-set MyTS esp-aes 256 esp-sha-hmac
mode tunnel
IPsec Profile
crypto ipsec profile MyProfile
set transform-set MyTS
Virtual Tunnel Interface
interface Tunnel0
ip address 172.16.0.1 255.255.255.252
tunnel source 10.0.0.1
tunnel destination 10.0.0.2
tunnel mode ipsec ipv4
tunnel protection ipsec profile MyProfile
Anti-replay
Sequence numbers are used to detect and
discard duplicate packets
Hash Message Authentication Code (HMAC)
A hash of the data and secret key used to
provide message authenticity
Diffie-Hellman Exchange
A shared secret key is established over an
insecure path using public and private keys
Troubleshooting
show crypto isakmp sa
show crypto isakmp policy
show crypto ipsec sa
show crypto ipsec transform-set
debug crypto {isakmp | ipsec}
by Jeremy Stretch
v2.0
You might also like
- BGP CheatSheet Version 2Document2 pagesBGP CheatSheet Version 2Cynthia Indah FebriyantiNo ratings yet
- PKI Interview QuestionsDocument18 pagesPKI Interview QuestionsSouthpaw Conor McGregor100% (3)
- Information Security Question BankDocument5 pagesInformation Security Question BankstiffleradamNo ratings yet
- IPsec 221112 111952Document2 pagesIPsec 221112 111952nguyenbaviet89No ratings yet
- Ipsec Components and Ipsec VPN FeaturesDocument45 pagesIpsec Components and Ipsec VPN FeaturesrajkumarlodhNo ratings yet
- Ipsec: 4 Key Functions or Services of Ipsec Are As FollowsDocument9 pagesIpsec: 4 Key Functions or Services of Ipsec Are As FollowsRohit KumarNo ratings yet
- MindCert Cisco IPsec MindMapDocument1 pageMindCert Cisco IPsec MindMapcpawan_69No ratings yet
- 91 IPSec+ProtocolsDocument8 pages91 IPSec+ProtocolsalbahithNo ratings yet
- 32-08 Site-to-Site Virtual Private NetworksDocument13 pages32-08 Site-to-Site Virtual Private Networksabhinaskari1No ratings yet
- Apnic Elearning:: Ipsec BasicsDocument34 pagesApnic Elearning:: Ipsec BasicsRajkumar WaghmodeNo ratings yet
- VPNDocument109 pagesVPNPitendra GulpadiyaNo ratings yet
- Cryptography and Network SecurityDocument23 pagesCryptography and Network SecurityPavithra AnandhNo ratings yet
- IP SecurityDocument22 pagesIP SecurityBruno BlayNo ratings yet
- 11 IP Sec Services 02 Mar 2021material I 02 Mar 2021 IPSECDocument36 pages11 IP Sec Services 02 Mar 2021material I 02 Mar 2021 IPSECSharath KumarNo ratings yet
- 9.3 Ipsec: 1 © 2016 Cisco And/Or Its Affiliates. All Rights Reserved. Cisco ConfidentialDocument11 pages9.3 Ipsec: 1 © 2016 Cisco And/Or Its Affiliates. All Rights Reserved. Cisco ConfidentialSyifa FauziahNo ratings yet
- Ipsec: Authentication Header (Ah) : The Ah Protocol Provides A Mechanism ForDocument2 pagesIpsec: Authentication Header (Ah) : The Ah Protocol Provides A Mechanism ForGaurav SharmaNo ratings yet
- Network Security Protocols: Anisha RaghuDocument53 pagesNetwork Security Protocols: Anisha RaghuMuktesh MukulNo ratings yet
- Extra Notes On IPsec VPNsDocument21 pagesExtra Notes On IPsec VPNsAlex MohNo ratings yet
- IpsecDocument25 pagesIpsecsunnyNo ratings yet
- OK 68-IPSec+ProtocolsDocument6 pagesOK 68-IPSec+ProtocolsrjuniorcasNo ratings yet
- CISSP CryptographyDocument1 pageCISSP CryptographyonlysubasNo ratings yet
- IPSecDocument22 pagesIPSecEswin AngelNo ratings yet
- Internet Protocol SecurityDocument19 pagesInternet Protocol SecurityJill_xyinz14589No ratings yet
- IPSecDocument25 pagesIPSecAMMAN ASAD (RA2011030030031)No ratings yet
- IPSec Basics HandoutsDocument20 pagesIPSec Basics HandoutsJame JameNo ratings yet
- Chapter 08Document27 pagesChapter 08willy muhammad fauziNo ratings yet
- Mikrotik IpsecDocument13 pagesMikrotik IpsecMertol SerbanNo ratings yet
- Mikrotik IpsecDocument13 pagesMikrotik IpsecMertol SerbanNo ratings yet
- IPsec Quick and DirtyDocument4 pagesIPsec Quick and Dirtysgopal7No ratings yet
- 4.U5 M1 T4 IP SecurityDocument41 pages4.U5 M1 T4 IP SecurityGuru PrasathNo ratings yet
- ch19 IPDocument27 pagesch19 IPDuttaUdayaVenkataChegondiNo ratings yet
- Ipsec SSLDocument35 pagesIpsec SSLAniesha Holy-chic ScottNo ratings yet
- IP SecurityDocument10 pagesIP Securitypray71No ratings yet
- Chapter 8: Implementing Virtual Private NetworksDocument168 pagesChapter 8: Implementing Virtual Private NetworksRyanb378No ratings yet
- IPsec OverviewDocument54 pagesIPsec OverviewRafa Alcaide AlcaideNo ratings yet
- Virtual Private Network (VPN) : IpsecDocument4 pagesVirtual Private Network (VPN) : Ipsecabhineet sharmaNo ratings yet
- Network Security Essentials: Fourth Edition by William StallingsDocument27 pagesNetwork Security Essentials: Fourth Edition by William StallingsXozanNo ratings yet
- Cryptography and Network Security: Vivek Verma CSE DeptDocument23 pagesCryptography and Network Security: Vivek Verma CSE Deptviv_vNo ratings yet
- Cryptography and Network SecurityDocument23 pagesCryptography and Network SecurityVivek VermaNo ratings yet
- Ipsec: Tcp/IpDocument12 pagesIpsec: Tcp/IpSaptarshi BhattacharjeeNo ratings yet
- Demystifying Ipsec VPN'S 1Document21 pagesDemystifying Ipsec VPN'S 1David MaasNo ratings yet
- Web SecurityDocument17 pagesWeb SecurityUchiha SasukeNo ratings yet
- CS6004 CF Unit I Revision IIIDocument12 pagesCS6004 CF Unit I Revision IIId_k_joseNo ratings yet
- Unit 1-1Document52 pagesUnit 1-1Vaishnavi DhimateNo ratings yet
- 18CS744 Module5 NotesDocument23 pages18CS744 Module5 Notesakashroshan17No ratings yet
- Ipsec: Security Across The Protocol Stack: Brad Stephenson Csci NetprogDocument27 pagesIpsec: Security Across The Protocol Stack: Brad Stephenson Csci NetprogAnkita BaidNo ratings yet
- Updated - IPSec VPN Using Cisco Packet TracerDocument9 pagesUpdated - IPSec VPN Using Cisco Packet TracerAnvesh PenkeNo ratings yet
- Security Associations (Sas) : VPN OverviewDocument7 pagesSecurity Associations (Sas) : VPN OverviewfxtrendNo ratings yet
- Unit 4Document70 pagesUnit 4Raj PaliwalNo ratings yet
- Ipsec: Ipsec, and Ipsec Over Gre TunnelDocument9 pagesIpsec: Ipsec, and Ipsec Over Gre Tunnelaboubakeriam djibirldararNo ratings yet
- Presented By: Kulwinder Priyanka PriyaDocument70 pagesPresented By: Kulwinder Priyanka PriyaPriya RainaNo ratings yet
- Cryptography and Network Security: Fifth Edition by William StallingsDocument27 pagesCryptography and Network Security: Fifth Edition by William Stallingsspm1379No ratings yet
- SECS04L01 - Introducing IPsecDocument13 pagesSECS04L01 - Introducing IPsecKhoa Huynh DangNo ratings yet
- Apnic Elearning:: Ipsec VPN DesignDocument34 pagesApnic Elearning:: Ipsec VPN DesignJC CastilloNo ratings yet
- Ipsec (Ip Security) : Advanced Computer Networks Ss2004Document28 pagesIpsec (Ip Security) : Advanced Computer Networks Ss2004Saba WasimNo ratings yet
- Module 3 NSDocument40 pagesModule 3 NSjahnavi.dmNo ratings yet
- IPSecDocument25 pagesIPSecDinesh ParasharNo ratings yet
- SecurityDocument78 pagesSecuritypriyeshb13No ratings yet
- The Concise Guide to SSL/TLS for DevOpsFrom EverandThe Concise Guide to SSL/TLS for DevOpsRating: 4.5 out of 5 stars4.5/5 (2)
- Securing Communication of Legacy Applications with IPSec: Step-by-Step Guide to Protecting “Data in Transit” without Changes in Your Existing SoftwareFrom EverandSecuring Communication of Legacy Applications with IPSec: Step-by-Step Guide to Protecting “Data in Transit” without Changes in Your Existing SoftwareNo ratings yet
- Spanning TreeDocument2 pagesSpanning TreealhersalNo ratings yet
- Physical Terminations PDFDocument1 pagePhysical Terminations PDFYacine A. MezianeNo ratings yet
- Ipv6 PDFDocument1 pageIpv6 PDFYacine A. MezianeNo ratings yet
- Vlans PDFDocument1 pageVlans PDFYacine A. MezianeNo ratings yet
- Mpls PDFDocument1 pageMpls PDFYacine A. Meziane100% (1)
- Cisco Ios Versions PDFDocument1 pageCisco Ios Versions PDFYacine A. MezianeNo ratings yet
- Tcpdump PDFDocument1 pageTcpdump PDFYacine A. MezianeNo ratings yet
- Wireshark Display FiltersDocument2 pagesWireshark Display FiltersAnovar_ebooks100% (1)
- Weishaupt WL30 - WL40Document12 pagesWeishaupt WL30 - WL40Yacine A. Meziane100% (1)
- CISSP Domain 3 - 46 60Document15 pagesCISSP Domain 3 - 46 60Arifur RahmanNo ratings yet
- Design and Analysis of Cryptographic AlgrithmDocument273 pagesDesign and Analysis of Cryptographic AlgrithmToanNo ratings yet
- Anexos PDFDocument21 pagesAnexos PDFfelsuquiNo ratings yet
- A Novel Video EncryptionDocument4 pagesA Novel Video EncryptionSuganya SelvarajNo ratings yet
- IS3220 Lab 8Document6 pagesIS3220 Lab 8Damon MrFixit BakerNo ratings yet
- Anonymous and Non-Repudiation E-Cash Scheme With Partially Blind SignatureDocument5 pagesAnonymous and Non-Repudiation E-Cash Scheme With Partially Blind SignatureJournal of ComputingNo ratings yet
- Cgi WHPR 35 Pki eDocument12 pagesCgi WHPR 35 Pki emamk77No ratings yet
- Free To Open Password-Protected 7zip FileDocument11 pagesFree To Open Password-Protected 7zip FileantonioksdhNo ratings yet
- Turing Bombe TutorialDocument14 pagesTuring Bombe TutorialKamel BourasNo ratings yet
- Perform Cryptanalysis Using Various Cryptanalysis Tools-1Document23 pagesPerform Cryptanalysis Using Various Cryptanalysis Tools-1jsolaresrNo ratings yet
- PPTDocument26 pagesPPTSreejith PsNo ratings yet
- Cryptomafia 2nd Round QuestionsDocument2 pagesCryptomafia 2nd Round QuestionsKumar PranayNo ratings yet
- Attacking and Securing JWT: by @airman604 For @owaspvanouverDocument21 pagesAttacking and Securing JWT: by @airman604 For @owaspvanouverIvan RodrigoNo ratings yet
- UNIT 19 Lorenz Cipher Machine Teacher Resource Material: Key Stage: 4 / A-Level TargetDocument2 pagesUNIT 19 Lorenz Cipher Machine Teacher Resource Material: Key Stage: 4 / A-Level TargetOulfaNo ratings yet
- Cs6711 Security Laboratory Manual 2 PDFDocument66 pagesCs6711 Security Laboratory Manual 2 PDFrachanapatil123100% (1)
- Cyber Security Internship ReportDocument26 pagesCyber Security Internship ReportSARATH CHANDRANo ratings yet
- AP18110010172 CryptoDocument13 pagesAP18110010172 CryptoSRM AP armyNo ratings yet
- Ijdte 01 02 2016 P5Document8 pagesIjdte 01 02 2016 P5xtofsetNo ratings yet
- Cryptographic Hash FunctionDocument15 pagesCryptographic Hash FunctionIchitsukiNo ratings yet
- Digital SignatureDocument13 pagesDigital Signaturevart1992No ratings yet
- Master CyberOps Session 5Document80 pagesMaster CyberOps Session 5refka babouriNo ratings yet
- Message Authentication and Hash FunctionsDocument26 pagesMessage Authentication and Hash FunctionsMukeshNo ratings yet
- Audio Encryption PPT 8-7-2002240Document11 pagesAudio Encryption PPT 8-7-2002240Kuncham GeeteshNo ratings yet
- Three Types of EncryptionDocument18 pagesThree Types of Encryptionrocky2000097100% (3)
- Bitcoin Address Generation in Pure Python - OPSXCQ BlogDocument1 pageBitcoin Address Generation in Pure Python - OPSXCQ BlogMegan KosNo ratings yet
- Lecture 2Document36 pagesLecture 2AHMED DARAJNo ratings yet
- Network Security: A Note On The Use of These PPT SlidesDocument91 pagesNetwork Security: A Note On The Use of These PPT SlidesJanhviNo ratings yet
- Wi-Fi CERTIFIED WPA3 Technology OverviewDocument6 pagesWi-Fi CERTIFIED WPA3 Technology OverviewSANDEEP AGGARWALNo ratings yet