Professional Documents
Culture Documents
NMap Commands KungFu
Uploaded by
Janny YogaCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
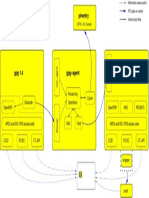
NMap Commands KungFu
Uploaded by
Janny YogaCopyright:
Available Formats
Offensive Counterintelligence | OffensiveCI
-f/-ff (Use Fragmented IP Packets)
--mtu <databytes>(Maximum Transmission Unit)
--ttl <value> (Time To Live)
Cloak A Scan With Decoys -D <decoy1,decoy2[,ME],...> (Create Decoys) -PE/-PI (ICMP Echo Request Ping)
Spoof Source Address -S <IP_Address> (Source Address) -PN/-PD/-P0 (Don't Ping)
Use Specified Interface -e <iface> (Interface) -PS (TCP SYN Ping)
Use Given Port Number -g/--source-port (Source Port Scan) -PU (UDP Ping)
--proxies <url1,[url2],...>(Relay Connections Through HTTP/SOCKS4 Proxies) -PY (SCTP Ping)
Append Random Data to Sent Packets --data-length <databytes> (Data Length) -PO (IP Protocol Ping)
MAC Spoofing --spoof-mac <mac address/prefix/vendor name> -PP (ICMP Timestamp Ping)
Ping Options
Send Packets With a Bogus TCP/UDP/SCTP Checksum --badsum (Bogus Packet) -PM (ICMP Address Mask Ping)
Host Timeout --host-timeout <milliseconds> -R (Require Reverse)
--initial-rtt-timeout <milliseconds> (Initial Round Trip Timeout) -n (Disable Reverse DNS)
Specifies Probe Round Trip Time --min-rtt-timeout <milliseconds> (Minimum Round Trip Timeout) Firewall/IDS Evasion and Spoofing --dns-servers (Specify DNS Servers)
--max-rtt-timeout <milliseconds> (Maximum Round Trip Timeout) Timing, Tunning & Performance Options
--max-hostgroup <number> (Maximum Parallel Hosts per Scan)
Parallel Host Scan Group Sizes -O (OS Fingerprinting)
--min-hostgroup <number> (Minimum Parallel Hosts per Scan)
-A (Aggressive, Additional & Advanced Detection) Guess OS More Aggressively
--max-parallelism <number> (Maximum Parallel Port Scans)
Probe Parallelization --osscan-limit (Limit System Scanning)
--min-parallelism <number> (Minimum Parallel Port Scans)
OS Detection --osscan-guess, --fuzzy (More Guessing Flexibility)
--scan-delay <milliseconds> (Minimum Delay Between Probes)
Delay Time Between Probes
--max-scan-delay <milliseconds> (Maximum Delay Between Probes)
Paranoid (T0)|Sneaky (T1)|Polite (T2)|Normal (T3)|Aggressive (T4)|Insane (T5) --timing/-T<0|1|2|3|4|5> (Timing Policies) -sV (Version Scan)
Send Packets No Slower Than <Number> Per Second --min-rate <number> (Minimum Slower Packet Send) --allports (Don’t Exclude Any Ports)
Send Packets No Faster Than <Number> Per Second --max-rate <number> (Maximum Faster Packet Send) --version-intensity <Level> (Set Version Intensity) Set from 0 (light) to 9 (Try all Probes)
--version-light (Enable Version Scanning Light)
Version Detection --version-all (Enable Version Scan All)
Verbose Mode -v/--verbose/-vv (Increase Verbosity Level)
--version-trace (For Debugging) Show Detailed Version Scan Activity Version Trace
Debug Mode -d/--debug/-dd (Increase Debugging Level)
--interactive (Interactive Mode)
--noninteractive (Noninteractive Mode) -sS (TCP SYN Scan) Half Open Scan | Stealth Scan
Display The Reason a Port is in a Particular State --reason (Port Reason) -sT (TCP Connect() Scan) Vanila Scan
Only Show Open (or Possibly Open) Ports --open (Open Port) -sA (ACK Scan)
Packet Trace Show All Packets Sent and Received --packet-trace (Packet Status) -sW (Window Scan)
Print Host Interfaces and Routes (For Debugging) -iflist (List Interfaces) -sM (Uriel/Maimon Scan)
Log Errors/Warnings To The Normal-Format Output File --log-errors (Logs Status) -sU (UDP Scan)
--append-output (Append Outputs) NMap Commands KungFu -sN (Null Scan)
Resume An Aborted Scan --resume <logfilename> (Resume Scan) -sF (FIN Scan) Stealth Scan
OffensiveCI@Prawez Samani
XSL Style Sheet To Transform XML Output To HTML --stylesheet <path/URL> (Style Sheet) Run Time Interaction & Reporting Options -sX (Xmas Tree Scan)
Reference Style Sheet From Nmap.Org For More Portable XML --webxml (Reference Style Sheet) --scanflags <Flags> (Customize TCP Scan Flags)
Prevent Associating Of XSL Style Sheet w/XML Output --no-stylesheet (No Style Sheet) -sP (Ping Scan)
Output In The Three Major Formats At Once -oA (All Format) Scan Techniques -sO (IP Protocol Scan)
-oN <logfilename> (Normal Format) -sR (RPC Scan) Remote Procedure Call
-oX <logfilename> (XML Format) -sP (Ping Scan)
-oG <logfilename> (Grepable Format) -sn (Ping Scan) Disable Port Scan
-oS <logfilename> (Script Kiddie Format) -sL (List Scan) Simply List Targets To Scan
-sI (Idle Scan) Zombie Scan
-b (FTP Bounce Attack)
-sC/--script <Lua Script> (Using Script)
-sY (SCTP Init Scan)
--script-args <n1=v1,[n2=v2,...]> (Script Argument)
-sZ (Cookie-Echo Scans)
--script-args-file=filename (Script Argument Into File)
Show All Data Sent and Received --script-trace (Data Status)
--script-updatedb (Update Script Database) --exclude (Exclude Target) Exclude Hosts/Networks
--script-help <Lua Script> (Show About Script) --excludefile (Exclude Target File)
-h/--help (Quick Reference Screen) -iR (Random Target)
-V/--version (Nmap Version) --randomize_hosts/-rH (Randomize Hosts)
--datadir <directory_name> (Data Directory) Scripts & Miscellaneous Options -iL (Read Target from File) Input From List of Hosts/Networks (Manual Scanning)
-q (Quash Argument Vector) -Pn (Treat All Hosts As Online) Skip Host Discovery
-6 (IPv6 Support) --system-dns (Use OS's DNS Resolver)
--privileged (Fully Privileged) --traceroute (Trace Hop Path To Each Host)
Host & Port Options
--unprivileged (Lacks Raw Socket Privileged) -p <Port Range> (Only Scan Specified Ports)
--send-eth/--send-ip (Send Using Raw Ethernet Frames Or IP Packets) -F (Fast Scan) Scan Fewer Ports Than The Default Scan
-r (Scan Ports Consecutively) Don't Randomize
--top-ports (Scan Most Common Ports)
--port-ratio (Scan ports more common than ratio)
You might also like
- NMap KungFu MindMap v2022.1Document1 pageNMap KungFu MindMap v2022.1anamariaoliveira1919No ratings yet
- Linux CheatsheetDocument2 pagesLinux CheatsheetrjkojasNo ratings yet
- DJF EnumerationDocument2 pagesDJF EnumerationElyar SafarovNo ratings yet
- Ringkasan OpsiDocument3 pagesRingkasan OpsiJamal SyarifNo ratings yet
- Akirasett - Nmap Basics Cheat SheetDocument1 pageAkirasett - Nmap Basics Cheat SheetSergeo ArmaniNo ratings yet
- Target specification and service/version detection with NmapDocument1 pageTarget specification and service/version detection with NmapmarcusburghardtNo ratings yet
- Nmap6 Cheatsheet Eng v1 PDFDocument1 pageNmap6 Cheatsheet Eng v1 PDFJhon Darío Montoya García100% (1)
- Nessus Cheat SheatDocument1 pageNessus Cheat Sheatbashwork100% (12)
- Lab Hacking1 10Document21 pagesLab Hacking1 10tvm1318022002No ratings yet
- Command Sheet Cheat - NmapDocument6 pagesCommand Sheet Cheat - NmapEdgar FerreiraNo ratings yet
- 1694000474061Document18 pages1694000474061Chinmay GhateNo ratings yet
- Nmap Cheet Sheet PDFDocument4 pagesNmap Cheet Sheet PDFnomo100% (1)
- Nmap Cheat Sheet: Target Specification Scan TechniquesDocument6 pagesNmap Cheat Sheet: Target Specification Scan TechniquesAmeur HedNo ratings yet
- Tamaranth Cisco Device Configuration Commands Net 126Document3 pagesTamaranth Cisco Device Configuration Commands Net 126Felicidade paulo KunkuNo ratings yet
- Cisco Device Configuration Commands (NET-126) Cheat SheetDocument2 pagesCisco Device Configuration Commands (NET-126) Cheat Sheetheroh909No ratings yet
- Nmap Openssl Snmpget-Walk Ldapsearch Dig Cisco IOS Tcpdump Ssldump Iptables NC (Netcat) Ruby Mysql-OnE LINERSDocument48 pagesNmap Openssl Snmpget-Walk Ldapsearch Dig Cisco IOS Tcpdump Ssldump Iptables NC (Netcat) Ruby Mysql-OnE LINERSmitrasamrat20026085No ratings yet
- Nmap Cheat SheetDocument16 pagesNmap Cheat SheetHarshitaBhatiaNo ratings yet
- MY Arbor Best Practices - v1Document71 pagesMY Arbor Best Practices - v1Nguyen Huy HoangNo ratings yet
- GX-CS - Cheat Sheet - Hping3Document2 pagesGX-CS - Cheat Sheet - Hping3bogeybogey6891No ratings yet
- FJJFNVDocument21 pagesFJJFNVRehman ZamanNo ratings yet
- Quick Reference Guide To NMAPDocument2 pagesQuick Reference Guide To NMAPMarcelo Alexandre de FreitasNo ratings yet
- Alexanderhd27 IptablesDocument1 pageAlexanderhd27 IptablesSergeo ArmaniNo ratings yet
- 22 (&!Document24 pages22 (&!Rehman ZamanNo ratings yet
- Dns-Zone-Transfer:: Scripting Engine Notable ScriptsDocument2 pagesDns-Zone-Transfer:: Scripting Engine Notable ScriptshamzaNo ratings yet
- Hping3 Cheat SheetDocument1 pageHping3 Cheat Sheetmuna cliffNo ratings yet
- NmapDocument2 pagesNmapIgnacio CorreaNo ratings yet
- PingDocument7 pagesPingricardoso5549No ratings yet
- ReteleDocument2 pagesReteleAndrei-Alexandru IoniţăNo ratings yet
- Nmap - Tabela e Guia Rapido PDFDocument2 pagesNmap - Tabela e Guia Rapido PDFbugatti_alienNo ratings yet
- Nmap Cheat SheetDocument9 pagesNmap Cheat SheetDraKon GamingNo ratings yet
- Tcpip PRGDocument2 pagesTcpip PRGindorateNo ratings yet
- Tutorial 3 - Network and Port ScanningDocument3 pagesTutorial 3 - Network and Port ScanningJimmy BooNo ratings yet
- Juniper Netscreen - VPN TroubleshootingDocument8 pagesJuniper Netscreen - VPN TroubleshootingrubinbrittoNo ratings yet
- NmapDocument55 pagesNmapyogesh2377No ratings yet
- Manual - IP - Firewall - Connection Tracking - MikroTik WikiDocument4 pagesManual - IP - Firewall - Connection Tracking - MikroTik WikiachainyaNo ratings yet
- TSR 2900 10Document6 pagesTSR 2900 10scada.wupptclNo ratings yet
- BRKSEC-3172 Advanced IOS XR SecurityDocument70 pagesBRKSEC-3172 Advanced IOS XR Securityreferenceref31No ratings yet
- 1.IOS XR - Intro-UseDocument68 pages1.IOS XR - Intro-Useagus kurniawanNo ratings yet
- Ping CommandDocument8 pagesPing CommandJEEVITHANo ratings yet
- Pinentry: Gluecode Private Key Operations CacheDocument1 pagePinentry: Gluecode Private Key Operations CacheetetNo ratings yet
- Nmap Commands Cheat SheetDocument1 pageNmap Commands Cheat SheetSaidu Haruna musaNo ratings yet
- Scanning: Slides (C) 2015 Based On Hacking ExposedDocument24 pagesScanning: Slides (C) 2015 Based On Hacking Exposedsirajudeen HNo ratings yet
- Active Directory-1Document67 pagesActive Directory-1JorgeNo ratings yet
- 1 BorghelloDocument18 pages1 BorghellojuanNo ratings yet
- Pentest Command Tools Gpen Based Cheat SheetDocument10 pagesPentest Command Tools Gpen Based Cheat Sheetlbb1987No ratings yet
- UE Attach ProcedureDocument6 pagesUE Attach ProcedureLalit Kumar ChoudharyNo ratings yet
- Ethical Hacking Python Tools GuideDocument66 pagesEthical Hacking Python Tools Guidekorab korabNo ratings yet
- Nmap Cheat SheetDocument18 pagesNmap Cheat SheetJesse VazquezNo ratings yet
- ASR CTF Cheatsheet PDFDocument9 pagesASR CTF Cheatsheet PDFcristina9209No ratings yet
- Vuln WebDocument3 pagesVuln WebsandraNo ratings yet
- IPsec Tools ChecklistDocument3 pagesIPsec Tools ChecklistMerab TavartkiladzeNo ratings yet
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkFrom EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo ratings yet
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityFrom EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityNo ratings yet
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationFrom EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationNo ratings yet
- LEARN MPLS FROM SCRATCH PART-B: A Beginners guide to next level of networkingFrom EverandLEARN MPLS FROM SCRATCH PART-B: A Beginners guide to next level of networkingNo ratings yet
- The HACCP Plan Form The StepsDocument4 pagesThe HACCP Plan Form The StepsAnonymous qfCJwxib7No ratings yet
- 520 Um001 - en e PDFDocument244 pages520 Um001 - en e PDFAlanAvtoNo ratings yet
- Bill of Pipe ShedDocument6 pagesBill of Pipe ShedEntraspace ConsultantNo ratings yet
- CA ClarityPPM Integration Guide ENUDocument553 pagesCA ClarityPPM Integration Guide ENUvictorinovilaNo ratings yet
- ResumeDocument3 pagesResumedestroy0012No ratings yet
- CG Notes Unit5Document24 pagesCG Notes Unit5Rahul PatilNo ratings yet
- Wall Connector Installation Manual 80A en USDocument39 pagesWall Connector Installation Manual 80A en USdaks4u100% (1)
- Hazop Sil Study Report For 6 Buy Back Gas PipelineDocument32 pagesHazop Sil Study Report For 6 Buy Back Gas Pipelinealinor_tn100% (1)
- Convert number to words in VBScriptDocument5 pagesConvert number to words in VBScriptsazid99924No ratings yet
- Centri Fug ADocument5 pagesCentri Fug AKike MenesesNo ratings yet
- Trade Secret Complaint Against GoogleDocument24 pagesTrade Secret Complaint Against GoogleNitasha TikuNo ratings yet
- Chapter 8Document44 pagesChapter 8Syukri ZainuddinNo ratings yet
- Course Outline CEN 323 - Fall - 10Document4 pagesCourse Outline CEN 323 - Fall - 10Touhid AhamedNo ratings yet
- Networking EssentialsDocument16 pagesNetworking EssentialsSujin Sathianesan SNo ratings yet
- Colonie Findings With AttmtDocument130 pagesColonie Findings With AttmtTown of Colonie LandfillNo ratings yet
- Converter Faults & ProtectionDocument24 pagesConverter Faults & ProtectionrakeshNo ratings yet
- TRANSFORMER MVA SIZING IN ETAPDocument24 pagesTRANSFORMER MVA SIZING IN ETAPkhalidNo ratings yet
- GeoxdrawDocument12 pagesGeoxdrawWelsinsin Kevin SinNo ratings yet
- Erode TRB Mechanical Engineering Materials MCQDocument3 pagesErode TRB Mechanical Engineering Materials MCQsivakumarNo ratings yet
- 20-1-16 LS Dyna - SHPB Analysis FinalDocument7 pages20-1-16 LS Dyna - SHPB Analysis FinalJayDeep KhajureNo ratings yet
- Ebook - Panton ChairDocument68 pagesEbook - Panton Chairchemino76No ratings yet
- Soln p3 21Document5 pagesSoln p3 21Vinicius RamosNo ratings yet
- NIH FeeDocument111 pagesNIH FeemohdkhidirNo ratings yet
- Construction checklist for GI trunking installationDocument1 pageConstruction checklist for GI trunking installationMAZHALAI SELVANNo ratings yet
- Ground effects on pressure fluctuations in atmospheric boundary layersDocument21 pagesGround effects on pressure fluctuations in atmospheric boundary layersArchie PapNo ratings yet
- TutoDocument432 pagesTutotsf2012No ratings yet
- GP1850 Service Manual - FurunoDocument24 pagesGP1850 Service Manual - FurunoCarlos Proaño100% (1)
- Trials of A New Stirrer-Less Juice Sulphiter at Experimental Sugar FactoryDocument4 pagesTrials of A New Stirrer-Less Juice Sulphiter at Experimental Sugar FactoryInternational Journal of Innovative Science and Research TechnologyNo ratings yet
- Heideinhain MC420Document52 pagesHeideinhain MC420Roger RochaNo ratings yet
- AN 10-001 Thermal-Paste ENG PDFDocument6 pagesAN 10-001 Thermal-Paste ENG PDFClovis GajoNo ratings yet