Professional Documents
Culture Documents
Questions Q: Q:: 9.2.4 Configure Interfaces and Security Levels
Uploaded by
rajesh tenetOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Questions Q: Q:: 9.2.4 Configure Interfaces and Security Levels
Uploaded by
rajesh tenetCopyright:
Available Formats
Null Dummy
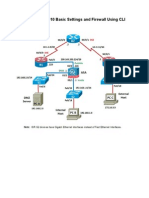
The Cisco PIX and ASA firewall devices are hardware devices built specifically for firewalling, unlike
the firewall software running on routers which we have encountered in previous labs. The device
(or
being simulated) in this lab is a PIX 525, a medium to large enterprise device, with up to eight
10/100
Fast Ethernet interfaces, or three Gigabit interfaces.
Display the list of commands available in Privilege mode using ?
View the PIX configuration file with the command show running-config
Questions
Q: Which version of the ASA firewall Operating System is running?
Q: Compared to a router, which extra attributes can be defined for each interface of the ASA?
9.2.4 Configure Interfaces and Security Levels
ASA security devices use an algorithm called the Adaptive Security Algorithm (ASA), which allows
traffic to flow between the interfaces depending on the security level set on the interfaces
(related
to the trust levels for each attached network). The security trust level value can be set from 0 (the
lowest) to 100) the highest). By default the inside interface (trusted network) is set to 100, and the
outside interface (untrusted Internet) is set to 0. Other networks, such as DMZs are set to values
of
1-99.
By default, the ASA allows traffic to flow from a higher security level to a lower one, and between
levels with the same value, but blocks traffic flowing from a lower level to a higher one, as shown
in
the figure below.
Configure the Interfaces
Certain attributes must be set on the interfaces, and then the default security behaviour can be
observed.
Set up the outside interface, which is connected to the internet, using the following commands.
ciscoasa(config)# interface gigabitEthernet 0
ciscoasa(config-if)# nameif outside
INFO: Security level for "outside" set to 0 by default.
ciscoasa(config-if)# ip address 10.1.Y.254 255.255.255.0
Additionally configure the MAC Address on the interfaces with the following command, using the
format <ca0 module code grpno 0 intno> such as the following for module csn11118 group 99:
ciscoasa(config-if)# mac-address 0001.1118.9900
ciscoasa(config-if)# no shutdown
Set up the inside interface, which is connected to the trusted internal network:
ciscoasa(config)# interface gigabitEthernet 1
ciscoasa(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
ciscoasa(config-if)# ip address 192.168.X.254 255.255.255.0
ciscoasa(config-if)# mac-address 000p.pppp.qq0r
ciscoasa(config-if)# no shutdown
Set up the DMZ interface, which is connected to the DMZ network:
ciscoasa(config)# interface Ethernet2
ciscoasa(config-if)# nameif dmz
ciscoasa(config-if)# security-level 50
ciscoasa(config-if)# ip address 192.168.Z.254 255.255.255.0
ciscoasa(config-if)# mac-address 000p.pppp.qq0r
ciscoasa(config-if)# no shutdown
Annotate your diagram/notes with the security trust levels for each interaface/connected network.
You might also like
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3From EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3No ratings yet
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationFrom EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationNo ratings yet
- Cisco ASA Firewall Commands Cheat SheetDocument10 pagesCisco ASA Firewall Commands Cheat SheetTuan Pham100% (1)
- Cisco ASA Firewall Best Practices For Firewall DeploymentDocument10 pagesCisco ASA Firewall Best Practices For Firewall Deploymentmichoco911No ratings yet
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityFrom EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityNo ratings yet
- EC-Council: Exam Questions 312-50v11Document20 pagesEC-Council: Exam Questions 312-50v11Lê Huyền MyNo ratings yet
- Cisco ASA Firewall Commands - Cheat SheetDocument8 pagesCisco ASA Firewall Commands - Cheat SheetAsifNo ratings yet
- Securing Communication of Legacy Applications with IPSec: Step-by-Step Guide to Protecting “Data in Transit” without Changes in Your Existing SoftwareFrom EverandSecuring Communication of Legacy Applications with IPSec: Step-by-Step Guide to Protecting “Data in Transit” without Changes in Your Existing SoftwareNo ratings yet
- ASA Step by StepDocument10 pagesASA Step by StepWondwossen DebalkieNo ratings yet
- Ch08 Implementing The Bastion HostDocument46 pagesCh08 Implementing The Bastion HostPumarunaNo ratings yet
- PPT ch06Document50 pagesPPT ch06kvsrvzmNo ratings yet
- Cisco ASADocument6 pagesCisco ASAsrk_ukNo ratings yet
- CCNP Sec LabsDocument210 pagesCCNP Sec LabsLalo ZúñigaNo ratings yet
- Cisco Router Switch Security HardeningDocument9 pagesCisco Router Switch Security HardeningEuribiades Jose GomezNo ratings yet
- R12.2 DMZ Url Not Working: Appsdba Oracle Dba R12.2 No CommentsDocument28 pagesR12.2 DMZ Url Not Working: Appsdba Oracle Dba R12.2 No CommentsSyed NoumanNo ratings yet
- This Lab Deals With A Basic Configuration of The Cisco ASADocument15 pagesThis Lab Deals With A Basic Configuration of The Cisco ASARaveenaNo ratings yet
- Ccnasv1.1 Chp10 Lab-A Asa-Fw-Cli Instructor 8.25.37 Am 8.25.57 AmDocument35 pagesCcnasv1.1 Chp10 Lab-A Asa-Fw-Cli Instructor 8.25.37 Am 8.25.57 Amclearmoon247100% (2)
- Asa Lab 1Document5 pagesAsa Lab 1Adil Raza SiddiquiNo ratings yet
- DDOS Attack & Mitigation SImulationDocument19 pagesDDOS Attack & Mitigation SImulationJaved Shaik100% (3)
- Configuring ASA 5510 Basic Settings and Firewall Using CLIDocument18 pagesConfiguring ASA 5510 Basic Settings and Firewall Using CLIIrfee75% (8)
- Ccnasv1.1 Chp10 Lab D Asa Isr s2s VPN StudentDocument36 pagesCcnasv1.1 Chp10 Lab D Asa Isr s2s VPN Studentmuscle260% (1)
- Computer Science Textbook Solutions - 18Document31 pagesComputer Science Textbook Solutions - 18acc-expertNo ratings yet
- Basic Cisco ASA 5506-x Configuration Example PDFDocument7 pagesBasic Cisco ASA 5506-x Configuration Example PDFAnton AlexandruNo ratings yet
- Ccnasv1.1 Chp10 Lab-B Asa-fw-Asdm Instructor 8.25.37 Am 8.25.57 AmDocument52 pagesCcnasv1.1 Chp10 Lab-B Asa-fw-Asdm Instructor 8.25.37 Am 8.25.57 Amclearmoon247No ratings yet
- SAP Ariba CIG For Buyers FAQDocument8 pagesSAP Ariba CIG For Buyers FAQShekhar GuptaNo ratings yet
- Packet Tracer DMZ ASA LabDocument3 pagesPacket Tracer DMZ ASA LabHenrry Josué Villanueva Bazan100% (1)
- CCNP SecDocument210 pagesCCNP SecThien Nhan Vo Nguyen100% (2)
- CCNA Security 1.1 Laboratorios Instructor Part 2Document181 pagesCCNA Security 1.1 Laboratorios Instructor Part 2Ricardo Castro TenorioNo ratings yet
- Gns 3Document18 pagesGns 3Raveena MathurNo ratings yet
- ASA Firewall Interview Questions and Answers Vol 1.0Document14 pagesASA Firewall Interview Questions and Answers Vol 1.0Syed MoNo ratings yet
- Lab05 - Configuring ASA Basic Settings and Firewall Using CLIDocument26 pagesLab05 - Configuring ASA Basic Settings and Firewall Using CLIAdrián ChóezNo ratings yet
- Configuring ASA Basic Settings and Firewall Using CLIDocument7 pagesConfiguring ASA Basic Settings and Firewall Using CLIMilošKovačevićNo ratings yet
- Basic Cisco ASA 5506-x Configuration ExampleDocument7 pagesBasic Cisco ASA 5506-x Configuration ExampleMarselNo ratings yet
- Cisco ASA DMZ Configuration ExampleDocument12 pagesCisco ASA DMZ Configuration ExampleopcrisNo ratings yet
- Lab 8: Firewalls - ASA Firewall Device: 8.1 DetailsDocument24 pagesLab 8: Firewalls - ASA Firewall Device: 8.1 Detailsrajesh tenetNo ratings yet
- Lab 8Document24 pagesLab 8RapacitorNo ratings yet
- Cisco ASADocument5 pagesCisco ASAShrijendra ShakyaNo ratings yet
- Scope: Configuration Guide: Juniper Networks Branch SRX Series Services GatewaysDocument8 pagesScope: Configuration Guide: Juniper Networks Branch SRX Series Services GatewaysAlcides ChanaNo ratings yet
- DMZ: Demilitarized ZoneDocument6 pagesDMZ: Demilitarized Zonemohamedarsathkhan045No ratings yet
- How To Configure Cisco PIX Firewall Part II: The Simple Network DiagramDocument4 pagesHow To Configure Cisco PIX Firewall Part II: The Simple Network Diagramabbass512No ratings yet
- Report - Chapter 6: FirewallDocument11 pagesReport - Chapter 6: FirewallDaniel PonsNo ratings yet
- Configurar VPN ASA PIX CiscoDocument23 pagesConfigurar VPN ASA PIX CiscoMauro GuañoNo ratings yet
- How To Configure Firewall PIXDocument4 pagesHow To Configure Firewall PIXHarjanto Handi KusumoNo ratings yet
- Ipsec Pix70 NatDocument28 pagesIpsec Pix70 NatRicardo Cien FuegosNo ratings yet
- Cisco Pix 515E Firewall ConfigurationDocument7 pagesCisco Pix 515E Firewall Configurationmicorina100% (2)
- Site To Site IPsec VPNDocument27 pagesSite To Site IPsec VPNRasakiRraskiNo ratings yet
- C C C C!C C C: C CCCCCCCCC CCCCC CC C CCDocument3 pagesC C C C!C C C: C CCCCCCCCC CCCCC CC C CCAnil ShelarNo ratings yet
- PIX/ASA: Establish and Troubleshoot Connectivity Through The Cisco Security ApplianceDocument7 pagesPIX/ASA: Establish and Troubleshoot Connectivity Through The Cisco Security AppliancetsibiNo ratings yet
- How To Configure Cisco Firewall - Part IDocument5 pagesHow To Configure Cisco Firewall - Part IMannem NireeshareddyNo ratings yet
- Configuring ASA On GNS3 Allow ICMP PacketDocument5 pagesConfiguring ASA On GNS3 Allow ICMP PacketYawar AzizNo ratings yet
- 21.7.6 Optional Lab Configure Asa Network Services Routing and DMZ With Acls Using CliDocument14 pages21.7.6 Optional Lab Configure Asa Network Services Routing and DMZ With Acls Using CliJuan Carlos BolivarNo ratings yet
- Cisco ASA As DHCP Server With Multiple Internal LANs (Configuration)Document1 pageCisco ASA As DHCP Server With Multiple Internal LANs (Configuration)mohamedzerhouniNo ratings yet
- Security Hardening Checklist Guide For Cisco RoutersDocument7 pagesSecurity Hardening Checklist Guide For Cisco RoutersFaouzi MaddouriNo ratings yet
- Dokumen - Tips CCNP SecurityDocument232 pagesDokumen - Tips CCNP SecuritySanjayNo ratings yet
- 21.9.5 Lab Configure Asa Basic Settings and Firewall Using AsdmDocument13 pages21.9.5 Lab Configure Asa Basic Settings and Firewall Using AsdmJuan Carlos BolivarNo ratings yet
- 9.4.1.5 Packet Tracer - Configuring ASA Basic Settings and Firewall Using CLIDocument7 pages9.4.1.5 Packet Tracer - Configuring ASA Basic Settings and Firewall Using CLIPouetteNo ratings yet
- 5506x-Quick-Start 2022Document16 pages5506x-Quick-Start 2022Tsiry AndrianantenainaNo ratings yet
- FirewallDocument26 pagesFirewallLekshmi BibinNo ratings yet
- Ccnasv1.1 Chp10 Lab-E Asa5510-Fw-cli StudentDocument22 pagesCcnasv1.1 Chp10 Lab-E Asa5510-Fw-cli StudentHarrison HayesNo ratings yet
- How To Configure A Cisco ASA 5510 FirewallDocument4 pagesHow To Configure A Cisco ASA 5510 FirewallHamami InkaZoNo ratings yet
- InteropDocument6 pagesInteropSaurav LodhNo ratings yet
- Cli Commands For ASADocument26 pagesCli Commands For ASAEmmet HearonNo ratings yet
- 21.2.10 Optional Lab - Configure ASA Basic Settings Using The CLI - ILMDocument19 pages21.2.10 Optional Lab - Configure ASA Basic Settings Using The CLI - ILMnetgame76No ratings yet
- Manual Cisco ASA 5505Document2 pagesManual Cisco ASA 5505Marone MoraesNo ratings yet
- Next-Generation switching OS configuration and management: Troubleshooting NX-OS in Enterprise EnvironmentsFrom EverandNext-Generation switching OS configuration and management: Troubleshooting NX-OS in Enterprise EnvironmentsNo ratings yet
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkFrom EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo ratings yet
- ASA - LAB - Cisco 1 PDFDocument1 pageASA - LAB - Cisco 1 PDFrajesh tenetNo ratings yet
- ASA No 2 LabDocument2 pagesASA No 2 Labrajesh tenetNo ratings yet
- Questions Q: Q:: 9.2.4 Configure Interfaces and Security LevelsDocument2 pagesQuestions Q: Q:: 9.2.4 Configure Interfaces and Security Levelsrajesh tenetNo ratings yet
- Questions Q: Q:: 9.2.4 Configure Interfaces and Security LevelsDocument2 pagesQuestions Q: Q:: 9.2.4 Configure Interfaces and Security Levelsrajesh tenetNo ratings yet
- AsaDocument1 pageAsarajesh tenetNo ratings yet
- ASA 123 Network NukkDocument1 pageASA 123 Network Nukkrajesh tenetNo ratings yet
- 2.1 Firewalls and ACLsDocument16 pages2.1 Firewalls and ACLskxeNo ratings yet
- HG658 V2 Home Gateway: User GuideDocument54 pagesHG658 V2 Home Gateway: User Guiderdos14No ratings yet
- Billion 7402NX User ManualDocument128 pagesBillion 7402NX User Manualrees1098No ratings yet
- DVA-G3672B D2 Manual v1.20Document72 pagesDVA-G3672B D2 Manual v1.20Adi PermanaNo ratings yet
- Understanding The Next Generation Firewall and Its ArchitectureDocument21 pagesUnderstanding The Next Generation Firewall and Its ArchitecturehaydocNo ratings yet
- SC387 Solstice FireWall-1 v3.0 SG 0698Document370 pagesSC387 Solstice FireWall-1 v3.0 SG 0698Mok JackieNo ratings yet
- Connecting Audiocodes SBC To Microsoft Teams Direct Routing Hosting Model Configuration NoteDocument66 pagesConnecting Audiocodes SBC To Microsoft Teams Direct Routing Hosting Model Configuration NoteerikaNo ratings yet
- Router AwDocument12 pagesRouter AwdesafiadoreNo ratings yet
- ACL and SecurityDocument15 pagesACL and Securityatul1988No ratings yet
- Redes de Datos I: Class 21. FirewallsDocument53 pagesRedes de Datos I: Class 21. FirewallsLinux0ecNo ratings yet
- CompTIA Security+ SY0-301 Practice TestDocument28 pagesCompTIA Security+ SY0-301 Practice TestMichael RoseNo ratings yet
- DSL-2730U - U1 - User Manual - v1.00 (DME) PDFDocument81 pagesDSL-2730U - U1 - User Manual - v1.00 (DME) PDFiman nejatyNo ratings yet
- User Manual: 4G LTE™ Router With VoiceDocument61 pagesUser Manual: 4G LTE™ Router With Voicevadmanh100% (1)
- IT General Controls Audit Program - Template 1 - 0 - Rev 1-23-2020Document51 pagesIT General Controls Audit Program - Template 1 - 0 - Rev 1-23-2020kumusha123No ratings yet
- Ipcop Install en 1.4.21Document59 pagesIpcop Install en 1.4.21dvs_xdNo ratings yet
- Manual l1 Rw333Document71 pagesManual l1 Rw333Amilton MorillasNo ratings yet
- Australian Cyber Threat PerspectiveDocument18 pagesAustralian Cyber Threat PerspectiveRyalapeta Venu YadavNo ratings yet
- DSL-2730U User ManualDocument87 pagesDSL-2730U User Manualdeepak1438No ratings yet
- White Paper - PCI ComplianceDocument45 pagesWhite Paper - PCI ComplianceyosiserNo ratings yet
- Student Assessment Tasks 520 FinalDocument23 pagesStudent Assessment Tasks 520 FinalYayo MirandaNo ratings yet
- 10 - Ceh-Exam Test - Topic Iii FinalDocument23 pages10 - Ceh-Exam Test - Topic Iii FinalJannet OkechukwuNo ratings yet
- SAP Note 669848 - Unlocking The Administrator User On The J2EE Engine/AS JavaDocument22 pagesSAP Note 669848 - Unlocking The Administrator User On The J2EE Engine/AS JavaRamesh BandariNo ratings yet