Professional Documents
Culture Documents
Notes - Secret Key Cryptography: Benjamin Fenster
Uploaded by
vidhya_bineesh0 ratings0% found this document useful (0 votes)
18 views6 pagessecret key cryptography
Original Title
CS266-02
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this Documentsecret key cryptography
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
18 views6 pagesNotes - Secret Key Cryptography: Benjamin Fenster
Uploaded by
vidhya_bineeshsecret key cryptography
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You are on page 1of 6
Benjamin Fenster
CS-266 (Ling)
19 December 2005
Notes – Secret Key Cryptography
I. Introduction
a. Take some fixed-size block (broken off the message, maybe 128 bits worth) and a fixed-
size key, and turn it into another block.
b. A longer key means more secure
c. Generic Block Encryption
i. One-to-one, so block sizes are the same (can reliably encrypt / decrypt)
ii. Keys need to be long enough to discourage a known-plaintext attack (needs to
be longer by about 2 bits every year)
iii. Done with substitutions, permutations
1. Substitute: Swap any value with any other
2. Permute: Swap individual bits in the message
3. Combine
iv. Want the probability of possible outputs to be distributed randomly: if the
opponent doesn’t know the key there’s no direct way to learn it.
v. Bit Spreading: A 1 in position 23 may result in a 1 in any position of the output
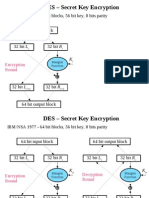
II. DES: Data Encryption Standard
a. Used 56-bit keys originally, perhaps because the government could break that level of
encryption
b. Keys are just eight ASCII characters
c. Blocks are 64 bits
d. Designed to be hard to attack with software, but easier to break with specialized
hardware
e. It’s not a big deal if it’s slow in software, since legitimate users only need to do one
encryption / decryption (instead of 256 of them)
f. Algorithm
i. Initial Permutation
1. Swap the bits in a fixed (publicly known) way
2. Adds nothing to security
3. The point: it’s easy to do in hardware but harder in software.
ii. Break the message into two 32-bit pieces
iii. To each piece, apply a key
iv. Will do 16 rounds, applying a 48-bit key to each (generated from the original 56-
bit key)
v. Then perform a final permutation that’s the inverse of the initial permutation
g. How to Generate Keys
i. Keys are originally 64 bits with 1/8 of those for parity
ii. We just discard the parity bits for the encryption
iii. Generate C0, D0 by permutations of the 56-bit key (each will be 28 bits)
iv. Will rotate left by 1 bit for round 1, 2, 9, 16 and by 2 bits for all other rounds. That
way we end up using all 28 bits of each key
v. So we have 28 + 28 bits; we only need 24 + 24.
vi. Take a permutation of Ci for the left half of Ki and a permutation of Di for the right
half of Ki.
vii. Thus we’ve constructed a key for round i.
h. Rounds
i. Move the right half fo the left half (Ln+1 = Rn)
ii. Rn + 1 = Ln ⊕ m(Rn, Kn) where m() is the “mangler function” (more later)
iii. Ln+1 = Rn
i. Decryption
i. Rn+1 = Ln ⊕ m(Ln+1, Kn)
ii. Rn+1 ⊕ m(Ln+1, Kn) = Ln⊕ m(Ln+1, Kn) ⊕ m(Ln+1, Kn)
iii. The underlined part is all zeros, so Rn+1 ⊕ m(Ln+1, Kn) = Ln
iv. Ln = Rn+1 ⊕ m(Ln+1, Kn)
v. Rn = Ln+1
vi. Decryption is the same as encryption, but swapped
j. Mangler Function
i. Takes the 32-bit Rn, 48-bit key
ii. Doesn’t affect the ability to encrypt/decrypt. This function just adds security
iii. Need to expand Rn to 48 bits by expanding each 4 bits into 6.
iv. Each 4 bits borrows a bit from either side (shifting around the ends),
1. Have, say, 0100 1110 1000 1101 … to start
2. Becomes: 101001 011101 010001 011010
v. Now we have the input and key the same length (each 48 bits)
vi. Have 8 chunks of 6 bits in each
vii. xor together for each chunk, then treat them separately
1. Rn 101001 011101 010001 011010
2. Kn 111111 111111 111111 111111
3. 101001 ⊕ 111111 = 010110
viii. Turn each six-bit chunk back into 4 using an S-box
1. Take 010110, output 1100
2. Basically a conversion “function” from 6-bit inputs into 4-bit outputs
ix. That yields a 32-bit output (eight chunks of 4 bits)
x. Then apply a permutation to the result, that’s the final mangler function result
k. Weak Keys
i. Some keys should be avoided (for C0, D0)
ii. 0000…0000
iii. 1111…1111
iv. 0101…
v. 1010…
III. IDEA: International Data Encryption Algorithm
a. 64-bit blocks, 128-bit keys (more secure)
b. All primitive operations map two 16-bit things into one 16-bit thing. In examples here
we’ll use four-bit values to make it easier to write.
c. Three Operations
i. a ⊕ b = c (xor)
1. If you know any two, you can compute the third.
2. b = c ⊕ a
3. a = b ⊕ c
4. 1100 ⊕ 0100 = 1001
5. 0110 ⊕ 0110 = 0000
6. With ⊕, any value is its own additive inverse
ii. a + b = c
16
1. But mod 2 at the end (ignore the carrying bit)
16
2. (a + b) mod 2 = a + b
16
3. If a + b = c, b = c – a (mod 2 )
4. May get a negative difference, but will always have a positive remainder
5. 10 + 1 = 11
6. 9 + 8 = 1
iii. a ⊗ b = a x b mod (2 + 1)
16
1. Re-encode using the values 1 to 216 since 0 is boring in multiplication
2. 9 ⊗ 12 = 6 (multiply 9 and 12, divide by 17, take the remainder)
3. 7 ⊗ 14 = 13
4. Zero is boring, so eliminate it, then encode 16 as 0 since it won’t fit into
the 4 bits available anyway.
5. a ⊗5 = 11, a ⊗ 5 ⊗ 7 = 11 ⊗ 7, a = 9
6. Given any number a, there’s a unique inverse b such that a ⊗ b = 1
d. Per-Round Keys
i. 17 rounds, with nine of them odd and eight even
ii. Need a total of 52 keys (generated from the 128-bit key)
iii. Get eight keys just by breaking K into eight 16-bit pieces
iv. Now shift K by 25 bits (rotating around as you do)
v. Break that into 8 more 16-bit keys.
vi. Shift by 25 again and repeat until all 52 keys are generated
vii. There will be four extra keys on the last set; just ignore them
e. Odd Rounds
i. Take four per-round keys Ka, Kb, Kc, Kd
ii. Split the 64-bit message into Xa, Xb, Xc, Xd
iii. Xa’ = Xa⊗ Ka
iv. Xb’ = Xc + Kc
v. Xc’ = Xb + Kb
vi. Xd’ = Xd ⊗ Kd
vii. Can decrypt; just use the multiplicative / additive inverses
f. Even Rounds
i. Take two per-round keys Ke, Kf
ii. Compute YIN = XA ⊕ XB, ZIN = XC ⊕ XD
iii. Send YIN, ZIN, Ke, Kf into the mangler function
iv. Xa’ = Xa ⊕ YOUT
v. Xb’ = Xb ⊕ YOUT
vi. Xc = Xc ⊕ ZOUT
vii. Xd = Xd ⊕ ZOUT
g. Mangler Functions
i. YOUT = ((Ke ⊗ YIN) + ZIN) ⊗ Kf
ii. ZOUT = (Ke ⊗ YIN) + YOUT
IV. AES
a. History
i. Key length of 56 bits in DES doesn’t seem secure enough for current technology
ii. Triple DES
1. Given a 112-bit key (2 keys, still 56 bits each)
2. Encrypt with K1, decrypt with K2, encrypt with K1
3. If you use double DES there’s a fairly easy attack against it. Details later
4. Triple DES is much more secure, but is also much too slow.
iii. IDEA
1. Good, secure, efficient
2. Patented! Nobody wants to pay royalties
3. Want a royalty-free standard
iv. AES
1. NISI proposes something to replace DES
2. Makes a public call on 12 September 1997 to create a publicly-designed
cryptosystem
3. People need to believe it’s secure, so it should be done in public
4. Want a block length of 128 bits
5. Want key length to be variable: 128, 192, 256 bits
6. Want world-wide availability without royalties
7. 21 proposals submitted, 15 met the criteria 5 chosen as finalists
8. MARS, RC6, Rijndael, Serpent, Twofish
9. Rijndael became AES based on efficiencies, memory use, politics, et
cetera
10. All five finalists were secure
b. Description
i. Both block length and key length are variable (128, …, 256)
ii. More general than the requirements demanded
iii. The number of rounds NR depends on the key length
iv. Given plaintext X (128 bits), create a state (4 x 4 array), put 1 byte in each cell
v. All operations happen on this state. For example: Round Key ⊕ State
(ADDROUNDKEY)
vi. For the first NR – 1 rounds, do:
1. SUBBYTES substitution
2. SHIFTROWS permutation
3. MIXCOLUMNS
4. ADDROUNDKEY
vii. On the last round, don’t do MIXCOLUMNS
viii. Then the ciphertext is just what’s left in the state.
c. Algorithm
i. Initialize state
ii. SUBBYTES: Use an S-box (specifically chosen for security)
iii. SHIFTROW: Shift the ith row left by i bytes (not bits!)
iv. MIXCOLUMN
1. Applied independently to each column
2. Lookup column of four bytes for each element in the original column
3. result1 = a1 ⊕ b4 ⊕ c3 ⊕ d2
4. result2 = a2 ⊕ b1 ⊕ c4 ⊕ d3
5. result3 = a3 ⊕ b2 ⊕ c1 ⊕ d4
6. result4 = a4 ⊕ b3 ⊕ c2 ⊕ d1
7. Now you have a new column
V. Modes of Operation
a. These algorithms only describe how to encrypt really short messages (we’ve been
measuring in bits)
b. We need a way to break a large message up into pieces, encrypt the pieces, and put it
back together to get the final ciphertext
c. Electronic Code Book (ECB)
i. Break the message into 64-bit or 128-bit chunks (depending on which algorithm
you’re using)
ii. Encrypt each chunk individually
iii. Encryption: ci = Ek(mi) for all i
iv. Decryption: mi = Dk(ci) for all i
v. So a given block of ciphertext is obtained by just encrypting the corresponding
block of the message
vi. Very simple!
vii. The Rub: It’s easy to change the message
1. Could swap two blocks and change the meaning, undetected by the
recipient
2. In salary data, for example, could swap two salaries to your own benefit,
and you wouldn’t have to know the key to do it.
viii. Due to this problem, this scheme is rarely used.
ix. The benefit: Changing one bit only affects one block of the message (each is
independent)
d. Cipher Block Chaining
i. Generate some r1r2…rk
ii. Encryption: ci = Ek(mi ⊕ ri)
iii. Decryption: Dk(ci) ⊕ ri = mi
iv. So we need to have access to these random ri’s in both steps.
v. This doubles the message length if ri is generated randomly
vi. Let’s generate ri from the message:
1. ri+1 = ci
2. Now there’s no need to send ri AND nobody can rearrange the blocks
3. Choose ri= IV (some initialization vector). You’ll still need to send that
much, but that’s tiny compared to a long message.
vii. Set c0= r1 for notation purposes.
viii. Encryption: ci= Ek(mi ⊕ ci-1)
ix. Decryption: mi = Dk(ci) ⊕ ci-1
x. If one block is altered, the following block is affected too, but that effect does not
propagate further since each block depends only on one other block.
xi. Since the IV is random, the encrypted message will be different each time. One
cannot detect if the message has changed if it’s sent twice.
xii. A Problem: Say you want to change m7 from 5 to 7. You can’t change c7 without
knowing the key. You CAN change c6 by ⊕ing it with something (000000010) to
turn what was 1012 to 1112. This would screw up m6 in an unpredictable way
though.
e. One-Time Pad
i. Genreate ri randomly
ii. ci= mi ⊕ ri
iii. Note that there’s no encryption function here; it’s just ⊕ing.
iv. This is completely secure, though it’s very hard to generate truly random
numbers.
f. Output Feedback Mode
i. Generate IV = b0
ii. Generate b1 = Ek(b0) using a shared key
iii. Then ci = mi ⊕ bi
iv. Decryption:
1. Receive c plus b0
2. Generate all bi using the same encryption
3. Then mi = ci ⊕ bi
4. No decryption function is needed
5. Since you don’t need decryption, you could use a hash function.
v. A problem: If a bad guy knows both mi and ci s/he can compute bi easily without
ever knowing the key (and then can create a new message)
vi. A benefit: Changing one bit in ci affects only one bit of mi
g. Cipher Feedback Mode
i. Want to generate bi so we can do ci= mi ⊕ bi again
ii. bi+1 = Ek(Ci), with b1 random
iii. ci = mi ⊕ bi = mi ⊕ Ek(ci-1)
iv. mi = ci ⊕ Ek(ci-1)
h. Why is this strategy secure?
i. Assume bi is generated randomly
ii. We want to know the probability of mi being some message given ci. P(mi | ci)
iii. Each bi you choose leads to a different mi
1 64
iv. P(mi | ci) = P(bi) = ( /2)
v. As long as you don’t know bi, this is perfectly secure
vi. We want P(mi = 000) = P(mi = 0001) = … = P(mi = 1111)
VI. Preserving Integrity
a. Want to compute something like a checksum from a message such that it can’t be altered
without knowing the key
b. Send only the last block of CBC (called CBC Residue)
c. Security and Integrity
i. Want to use CBC to encrypt and to generate a hash, since it requires a total of
one pass
ii. Compute hash: one pass
iii. Then compute CBC (message | hash) and transmit it
iv. Using a hash function is more efficient than encrypting
VII. Multiple Encryption DES
a. Could be used for other cryptosystems
b. Have two keys
c. c = Ek1(Dk2(Ek1(m)))
d. Why two keys? If we used the same key you’d just end up encrypting once in the end
because of ⊕.
e. Why not encrypt with the same key twice? Because finding the key by brute force is just
as hard that way as if you’d only done it once.
f. Why not just encrypt with k1, then with k2
i. Suppose the bad guy knows (m1, c2), (m2, c2), and (m3, c3)
ii. For each possible key, encrypt m1 and decrypt c1
iii. Find cases where the results are the same: those are potential matches.
iv. There are 248 possible (k1, k2) pairs that encrypt this way, and even though it’s
not really feasible to brute force that it’s still less secure than single DES
v. If there are two intermediate steps (by encrypting, decrypting, and encrypting
again), this attack isn’t possible
g. CBC
i. Could treat Triple DES as a single algorithm and do CBC at the end
ii. Could take the intermediate result and xor, but this means it’s no longer
protected from transmission errors the way it was before.
You might also like
- Assembly x86 Exam1 SolutionDocument5 pagesAssembly x86 Exam1 Solutionkhayat_samirNo ratings yet
- Cys535 Lecture03Document70 pagesCys535 Lecture03Waseem LaghariNo ratings yet
- C3-Cryptography Block Cipher and Modes of OperationsDocument29 pagesC3-Cryptography Block Cipher and Modes of OperationsTrần HiếuNo ratings yet
- Chapter 3Document51 pagesChapter 3Abduu MizaabNo ratings yet
- Analog vs Digital Quantities GuideDocument2 pagesAnalog vs Digital Quantities GuidechistoracinNo ratings yet
- Course Id 23311 Course Title - Digital LogicDocument3 pagesCourse Id 23311 Course Title - Digital LogicICIS CollegeNo ratings yet
- Recall from last lecture: Cryptography fundamentalsDocument39 pagesRecall from last lecture: Cryptography fundamentalsAlexis Marcano PradaNo ratings yet
- March 2008 Paper 2Document2 pagesMarch 2008 Paper 2many1tothe11No ratings yet
- Lecture 4 Block Ciphers, DES, AESDocument82 pagesLecture 4 Block Ciphers, DES, AESMohammad BangeeNo ratings yet
- Chapter 3 AUDocument56 pagesChapter 3 AUYididiya TilahunNo ratings yet
- DLD Assignment - 1Document2 pagesDLD Assignment - 1gokulNo ratings yet
- Secret Key CryptographyDocument32 pagesSecret Key Cryptographyvidhya_bineeshNo ratings yet
- Rutgers CCPD / The Beacon Institute For Learning: TCP/IP Address ClassesDocument4 pagesRutgers CCPD / The Beacon Institute For Learning: TCP/IP Address ClassesshamramiNo ratings yet
- Mini Advanced Encryption Standard (Mini-AES) : A Testbed For Cryptanalysis StudentsDocument19 pagesMini Advanced Encryption Standard (Mini-AES) : A Testbed For Cryptanalysis StudentsAhmad ZulhilmiNo ratings yet
- Crptography Exam Questions and SolutionsDocument36 pagesCrptography Exam Questions and SolutionsRajeswari Purushotham100% (1)
- LOC Bca 1st YearDocument7 pagesLOC Bca 1st YearKhushbooNo ratings yet
- Contest 1007Document15 pagesContest 1007Ivan YevtushenkoNo ratings yet
- Data Encryption Standard (DES)Document53 pagesData Encryption Standard (DES)resky_12No ratings yet
- Loc I 2020Document3 pagesLoc I 2020singlamuskaan2002No ratings yet
- Number Theory & Cryptography: Secret Key CryptographyDocument18 pagesNumber Theory & Cryptography: Secret Key CryptographyPrateek ParashariNo ratings yet
- Data Encryption Standard (DES)Document63 pagesData Encryption Standard (DES)Snehal SolankeNo ratings yet
- Unit2: Data Encryption StandardDocument78 pagesUnit2: Data Encryption StandardAbhishek RaoNo ratings yet
- Deber 7Document2 pagesDeber 7chistoracinNo ratings yet
- Digital Logic Design More Number Systems/ComplementsDocument76 pagesDigital Logic Design More Number Systems/Complementslovely personNo ratings yet
- DES Encryption Standards ExplainedDocument8 pagesDES Encryption Standards Explainedmame Magnaw0% (1)
- Mini AES: Tingkat Ii Teknik Rancang Bangun 2013-2014Document22 pagesMini AES: Tingkat Ii Teknik Rancang Bangun 2013-2014andini85No ratings yet
- Shahzad AkbarDocument9 pagesShahzad Akbarmalihajabbar519No ratings yet
- Archeologists ProblemDocument15 pagesArcheologists ProblemСмурф СмурфовичNo ratings yet
- Computer Network Homework HelpDocument9 pagesComputer Network Homework HelpComputer Network Assignment HelpNo ratings yet
- Cryptography and Network SecurityDocument34 pagesCryptography and Network Securityvaishakh gargNo ratings yet
- Digital Encryption StandardDocument30 pagesDigital Encryption StandardManoj SunchauriNo ratings yet
- The Application Layer: Algorithms)Document19 pagesThe Application Layer: Algorithms)VinayKumarSinghNo ratings yet
- سوالات فصل دوم.pdf 2Document5 pagesسوالات فصل دوم.pdf 2shadab BenawarNo ratings yet
- Number SystemsDocument44 pagesNumber SystemsRuby BartNo ratings yet
- Binary Numbers and Storage Units WorksheetDocument2 pagesBinary Numbers and Storage Units WorksheetAziz Alusta OmarNo ratings yet
- DES Encryption Explained - 40 Char TitleDocument14 pagesDES Encryption Explained - 40 Char TitleRock GamerNo ratings yet
- Ex2 SecretDocument8 pagesEx2 Secretl namikazeNo ratings yet
- DLD BankDocument16 pagesDLD BankHarshad ThiteNo ratings yet
- CS 61C Number Representation Spring 2020: 1 Unsigned IntegersDocument3 pagesCS 61C Number Representation Spring 2020: 1 Unsigned IntegersEric JiaNo ratings yet
- 18 State AssignDocument30 pages18 State AssignSushant MandalNo ratings yet
- Invitation To Computer Science 6th Edition Schneider Solutions Manual 1Document9 pagesInvitation To Computer Science 6th Edition Schneider Solutions Manual 1stephan100% (47)
- Invitation To Computer Science 6Th Edition Schneider Solutions Manual Full Chapter PDFDocument30 pagesInvitation To Computer Science 6Th Edition Schneider Solutions Manual Full Chapter PDFvirginia.romo181100% (11)
- Info Assign 1Document2 pagesInfo Assign 1sastivelNo ratings yet
- Dwnload Full Computer Organization and Architecture Themes and Variations 1st Edition Alan Clements Solutions Manual PDFDocument36 pagesDwnload Full Computer Organization and Architecture Themes and Variations 1st Edition Alan Clements Solutions Manual PDFeliasfosterhs6r100% (15)
- Computer Organization and Architecture Themes and Variations 1st Edition Alan Clements Solutions ManualDocument36 pagesComputer Organization and Architecture Themes and Variations 1st Edition Alan Clements Solutions Manualkeeling.grownzqrhqv100% (32)
- HW 1Document4 pagesHW 1MohammadChharchhodawalaNo ratings yet
- Chap 02Document70 pagesChap 02Ranjan Kumar H SNo ratings yet
- Introduction To Cryptography: Matt Mahoney Florida TechDocument66 pagesIntroduction To Cryptography: Matt Mahoney Florida TechJboy EspinolaNo ratings yet
- MATC16 Cryptography and Coding Theory Final Exam SolutionsDocument4 pagesMATC16 Cryptography and Coding Theory Final Exam SolutionsMostafa Mahmoud HasseibNo ratings yet
- 8 Modern Blockciphers 20-01-2022Document29 pages8 Modern Blockciphers 20-01-2022vigneshreddy1430No ratings yet
- A SIMPLIFIED IDEA ALGORITHM: UNDERSTANDING THE KEY CONCEPTSDocument16 pagesA SIMPLIFIED IDEA ALGORITHM: UNDERSTANDING THE KEY CONCEPTSKéké DocteurNo ratings yet
- OperatorsDocument65 pagesOperatorsSujay MusaleNo ratings yet
- SCM, CSU 201430 ITC161/411 Instruction Set ArchitecturesDocument4 pagesSCM, CSU 201430 ITC161/411 Instruction Set ArchitecturesSaimo MghaseNo ratings yet
- Simplified DESDocument52 pagesSimplified DESshahenaaz3No ratings yet
- Question & Answer PDFDocument10 pagesQuestion & Answer PDFKalyan DasNo ratings yet
- ICT 5301 Lecture3Document36 pagesICT 5301 Lecture3voccubdNo ratings yet
- Assignment 3Document1 pageAssignment 3ibrahimango3No ratings yet
- Macro Preprocessors m5Document53 pagesMacro Preprocessors m5vidhya_bineeshNo ratings yet
- System Software Modules and FunctionsDocument21 pagesSystem Software Modules and Functionsvidhya_bineeshNo ratings yet
- Module 1 Part3Document12 pagesModule 1 Part3vidhya_bineeshNo ratings yet
- NFA - NFA - DFA EquivalenceDocument14 pagesNFA - NFA - DFA EquivalenceRahul SinghNo ratings yet
- System Software Module 3: Machine-Dependent Assembler FeaturesDocument28 pagesSystem Software Module 3: Machine-Dependent Assembler Featuresvidhya_bineeshNo ratings yet
- Computer Science and EngineeringDocument358 pagesComputer Science and Engineeringvidhya_bineeshNo ratings yet
- Sree Narayana Gurukulam College of Engineering: Answer All Questions, Each Carries 3 MarksDocument3 pagesSree Narayana Gurukulam College of Engineering: Answer All Questions, Each Carries 3 Marksvidhya_bineeshNo ratings yet
- CS404 Embedded Systems: Eighth Semester B.Tech Degree Supplementary Examination August 2021Document2 pagesCS404 Embedded Systems: Eighth Semester B.Tech Degree Supplementary Examination August 2021Jinu ThomasNo ratings yet
- Module 3 (Part2)Document68 pagesModule 3 (Part2)vidhya_bineeshNo ratings yet
- Apj Abdul Kalam Technological University: Seventh Semester B.Tech Examinations (S), September 2020Document2 pagesApj Abdul Kalam Technological University: Seventh Semester B.Tech Examinations (S), September 2020vidhya_bineeshNo ratings yet
- Floyd WarshallDocument6 pagesFloyd Warshallvidhya_bineeshNo ratings yet
- Unit: 1 Complex Numbers: Department of MathematicsDocument4 pagesUnit: 1 Complex Numbers: Department of Mathematicsvidhya_bineeshNo ratings yet
- A 1Document4 pagesA 1vidhya_bineeshNo ratings yet
- Quantum CryptographyDocument7 pagesQuantum Cryptographyvidhya_bineeshNo ratings yet
- Embedded C Programming With Keil LanguageDocument25 pagesEmbedded C Programming With Keil Languagevidhya_bineeshNo ratings yet
- Embedded Firmware Development Environment Unit Iii: Mr. S. Vinod Assistant Professor Eee DepartmentDocument46 pagesEmbedded Firmware Development Environment Unit Iii: Mr. S. Vinod Assistant Professor Eee Departmentvidhya_bineeshNo ratings yet
- CS 404 Embedded SystemsDocument32 pagesCS 404 Embedded Systemsvidhya_bineeshNo ratings yet
- TYPES OF MALICIOUS SOFTWAREDocument11 pagesTYPES OF MALICIOUS SOFTWAREvidhya_bineeshNo ratings yet
- ESDocument50 pagesESNamitha GopanNo ratings yet
- ESDocument50 pagesESNamitha GopanNo ratings yet
- Question BankDocument3 pagesQuestion Bankvidhya_bineeshNo ratings yet
- Mod 5ES Part2Document6 pagesMod 5ES Part2vidhya_bineeshNo ratings yet
- Mod 5ES Part1Document32 pagesMod 5ES Part1vidhya_bineeshNo ratings yet
- Module 3 ESDocument46 pagesModule 3 ESvidhya_bineeshNo ratings yet
- RelationsDocument22 pagesRelationsvidhya_bineeshNo ratings yet
- ES Model Question Paper With Solution KeyDocument10 pagesES Model Question Paper With Solution Keyvidhya_bineeshNo ratings yet
- Module 3Document63 pagesModule 3vidhya_bineeshNo ratings yet
- Module 3 ESDocument46 pagesModule 3 ESvidhya_bineeshNo ratings yet
- IMAGE COMPRESSION AND DECOMPRESSION SYSTEM USING RUN LENGTH ENCODING ALGORITHM (Chapter 1-3)Document18 pagesIMAGE COMPRESSION AND DECOMPRESSION SYSTEM USING RUN LENGTH ENCODING ALGORITHM (Chapter 1-3)femiNo ratings yet
- Analytics Prepbook Laterals 2019-2020Document40 pagesAnalytics Prepbook Laterals 2019-2020Surabhi Sharma100% (1)
- Digital Signals Lab #01Document6 pagesDigital Signals Lab #01Zohaib KhanNo ratings yet
- CSF-429 - L7 Word Vectors - GloveDocument24 pagesCSF-429 - L7 Word Vectors - GloveManan PopatNo ratings yet
- Recursion Explained: Examples of Recursive Methods and Problem SolvingDocument33 pagesRecursion Explained: Examples of Recursive Methods and Problem SolvingАмирхан ГульназNo ratings yet
- Time Frequency Representation of Digital Signals and Systems Based On Short TimeDocument15 pagesTime Frequency Representation of Digital Signals and Systems Based On Short TimeNorozKhanNo ratings yet
- A Disease Prediction by Machine Learning Over Bigdata From Healthcare CommunitiesDocument3 pagesA Disease Prediction by Machine Learning Over Bigdata From Healthcare CommunitiesHarikrishnan ShunmugamNo ratings yet
- Digital Oscillator: Final Mini Project Report OnDocument10 pagesDigital Oscillator: Final Mini Project Report OnNagendra KumarNo ratings yet
- DNN-Based Smart Attendance SystemDocument18 pagesDNN-Based Smart Attendance SystemNaren DranNo ratings yet
- Efficient Estimation of Word Representations in Vector Space - Meghana BDocument2 pagesEfficient Estimation of Word Representations in Vector Space - Meghana BMeghana BezawadaNo ratings yet
- Artificial Sequences and Complexity MeasuresDocument27 pagesArtificial Sequences and Complexity MeasuresCao Hoang VuNo ratings yet
- Assignment2-NIT CALICUT DSADocument10 pagesAssignment2-NIT CALICUT DSAJ AnanthakrishnanNo ratings yet
- On Probability Theory &stochastic ProcessDocument101 pagesOn Probability Theory &stochastic ProcessmohanNo ratings yet
- 01 ASAP TimeSeriesForcasting Day1 2 IntroductionDocument62 pages01 ASAP TimeSeriesForcasting Day1 2 IntroductionGeorge MathewNo ratings yet
- Fixed-Radius Near NeighborsDocument2 pagesFixed-Radius Near Neighborswatson191No ratings yet
- Grp7 ProjectReportDocument26 pagesGrp7 ProjectReportPHANTOME FFNo ratings yet
- HabijabiDocument21 pagesHabijabiTanvir Shahrier MahmudNo ratings yet
- Ann PsoDocument8 pagesAnn PsoselcukcankurtNo ratings yet
- Designing Robust Force Control Of: by Navid Niksefat and Nariman SepehriDocument12 pagesDesigning Robust Force Control Of: by Navid Niksefat and Nariman SepehriMiguel Andres Duran AlvarezNo ratings yet
- Algorithms Illuminated Part3Document230 pagesAlgorithms Illuminated Part3Abdullah Al Umari100% (5)
- 2ND Code CoverageDocument5 pages2ND Code CoveragejanakikunalNo ratings yet
- Unit 12 - Week 11Document3 pagesUnit 12 - Week 11sanjay.diddeeNo ratings yet
- R5210101 Mathametics - IIDocument1 pageR5210101 Mathametics - IIsivabharathamurthyNo ratings yet
- Ejemplo de Diagrama Pert en ExcelDocument7 pagesEjemplo de Diagrama Pert en Excelhector eduardo perez carhuapomaNo ratings yet
- Midterm 2006Document11 pagesMidterm 2006Muhammad MurtazaNo ratings yet
- A Genetic Approach To Solving Sudoku SDocument26 pagesA Genetic Approach To Solving Sudoku SPrashant SoniNo ratings yet
- Factoring MazeDocument2 pagesFactoring MazeJo-Amver Valera Manzano100% (1)
- Dijkstra's AlgorithmDocument21 pagesDijkstra's AlgorithmSaurabh Agarwal100% (2)
- Essentials of ML, VITOL Course DA1Document5 pagesEssentials of ML, VITOL Course DA1Abey SebastianNo ratings yet
- The DSP For FPGA PrimerDocument2 pagesThe DSP For FPGA PrimervonguyenphuongNo ratings yet