Professional Documents
Culture Documents
Nmap Commands
Uploaded by
aniket kasturi0 ratings0% found this document useful (0 votes)
38 views2 pagescommands
Original Title
Nmap commands
Copyright
© © All Rights Reserved
Available Formats
TXT, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this Documentcommands
Copyright:
© All Rights Reserved
Available Formats
Download as TXT, PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
38 views2 pagesNmap Commands
Uploaded by
aniket kasturicommands
Copyright:
© All Rights Reserved
Available Formats
Download as TXT, PDF, TXT or read online from Scribd
You are on page 1of 2
IP scan:
Scan a single IP nmap 192.168.1.1
Scan a host nmap www.testhostname.com
Scan a range of IPs nmap 192.168.1.1-20
Scan a subnet nmap 192.168.1.0/24
Nmap Port Selection
Scan a single Port nmap -p 22 192.168.1.1
Scan a range of ports nmap -p 1-100 192.168.1.1
Scan all 65535 ports nmap -p- 192.168.1.1
Scan 100 most common ports (Fast) nmap -F 192.168.1.1
Nmap Port Scan types
Scan using TCP connect nmap -sT 192.168.1.1
Scan using TCP SYN scan (default) nmap -sS 192.168.1.1
Scan UDP ports nmap -sU -p 123,161,162 192.168.1.1
Scan selected ports - ignore discovery nmap -Pn -F 192.168.1.1
Service and OS Detection
Detect OS and Services nmap -A 192.168.1.1
Standard service detection nmap -sV 192.168.1.1
More aggressive Service Detectio nmap -sV --version-intensity 5 192.168.1.1
Lighter banner grabbing detection nmap -sV --version-intensity 0 192.168.1.1
Nmap Output Formats
Save default output to file nmap -oN outputfile.txt 192.168.1.1
Save results as XML nmap -oX outputfile.xml 192.168.1.1
Save results in a format for grep nmap -oG outputfile.txt 192.168.1.1
Save in all formats nmap -oA outputfile 192.168.1.1
Digging deeper with NSE Scripts
Scan using default safe scripts nmap -sV -sC 192.168.1.1
Get help for a script nmap --script-help=ssl-heartbleed
Scan using a specific NSE script nmap -sV -p 443 �script=ssl-heartbleed.nse
192.168.1.1
Scan with a set of scripts nmap -sV --script=smb* 192.168.1.1
Scan for UDP DDOS reflectors nmap �sU �A �PN �n �pU:19,53,123,161 �script=ntp-
monlist,dns-recursion,snmp-sysdescr 192.168.1.0/24
Gather page titles from HTTP services nmap --script=http-title 192.168.1.0/24
Get HTTP headers of web services nmap --script=http-headers 192.168.1.0/24
Find web apps from known paths nmap --script=http-enum 192.168.1.0/24
Heartbleed Testing nmap -sV -p 443 --script=ssl-heartbleed 192.168.1.0/24
IP Address information
Find Information about IP address nmap --script=asn-query,whois,ip-geolocation-
maxmind 192.168.1.0/24
You might also like
- Nmap KomandeDocument1 pageNmap KomandeEmir HasanbegovićNo ratings yet
- Nmap Commands CollectionDocument7 pagesNmap Commands Collectionhammad.khan.4440kNo ratings yet
- NmapDocument5 pagesNmapPriyanshu UpadhyayNo ratings yet
- Kali LinuxDocument1 pageKali LinuxFiaz Ahmed LoneNo ratings yet
- Nmap Cheat SheetDocument8 pagesNmap Cheat SheetPauloNo ratings yet
- Nmap:The Network MapperDocument13 pagesNmap:The Network MapperNahid MajumderNo ratings yet
- NmapDocument20 pagesNmapjayshreeNo ratings yet
- Nmap Cheat SheetDocument16 pagesNmap Cheat SheetHarshitaBhatiaNo ratings yet
- Nmap Cheat SheetDocument9 pagesNmap Cheat SheetDraKon GamingNo ratings yet
- Switch Example Description: Target SpecificationDocument3 pagesSwitch Example Description: Target SpecificationKD TricksNo ratings yet
- Nmap Cheat SheetDocument8 pagesNmap Cheat Sheetkalesh shaikNo ratings yet
- Nmap Cheet Sheet PDFDocument4 pagesNmap Cheet Sheet PDFnomo100% (1)
- Nmap Cheat Sheet: Target Specification Scan TechniquesDocument6 pagesNmap Cheat Sheet: Target Specification Scan TechniquesAmeur HedNo ratings yet
- Nmap E7Document9 pagesNmap E7Игорь КнопкинNo ratings yet
- Nmap Cheat Sheet 2023Document11 pagesNmap Cheat Sheet 2023ketix20201No ratings yet
- ELearnSecurity ECPPT Notes ExamDocument157 pagesELearnSecurity ECPPT Notes ExamAngel CabralesNo ratings yet
- NMAP Command Guide SheetDocument5 pagesNMAP Command Guide SheetRafoo MGNo ratings yet
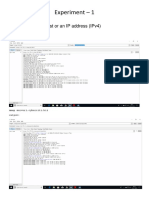
- Experiment - 1: #1: Scan A Single Host or An Ip Address (Ipv4)Document17 pagesExperiment - 1: #1: Scan A Single Host or An Ip Address (Ipv4)Hardik MehtaNo ratings yet
- Nmap Cheat Sheet and TutorialDocument8 pagesNmap Cheat Sheet and Tutorialhoadi100% (2)
- NMAP Commands Cheat Sheet and Tutorial With Examples (Download PDFDocument10 pagesNMAP Commands Cheat Sheet and Tutorial With Examples (Download PDFjaveeed0401No ratings yet
- ScanningDocument15 pagesScanningtestetesteciteNo ratings yet
- Active Directory-1Document67 pagesActive Directory-1JorgeNo ratings yet
- By Gopalsamy RajendranDocument19 pagesBy Gopalsamy RajendranrmknecNo ratings yet
- Cybersecurity Practical JAINIDocument43 pagesCybersecurity Practical JAINIkhaabishayarNo ratings yet
- Network Enumeration With Nmap Module Cheat SheetDocument3 pagesNetwork Enumeration With Nmap Module Cheat Sheetskttoan1223No ratings yet
- NMAP SyntaxDocument2 pagesNMAP SyntaxPrasad DhondNo ratings yet
- 1: Scan A Single Host or An Ip Address (Ipv4) : Nmap 192.168.1.1 192.168.1.2 192.168.1.3 Nmap 192.168.1.1,2,3Document4 pages1: Scan A Single Host or An Ip Address (Ipv4) : Nmap 192.168.1.1 192.168.1.2 192.168.1.3 Nmap 192.168.1.1,2,3fallliNo ratings yet
- Complete Guide To NMAPDocument7 pagesComplete Guide To NMAPPulkit R AggarwalNo ratings yet
- Cyber Security For Beginners PDFDocument28 pagesCyber Security For Beginners PDFVenkat KarthikNo ratings yet
- NMap Cheat Sheet 1688314900Document18 pagesNMap Cheat Sheet 1688314900Bikash kumar ShowNo ratings yet
- Nmap Cheat SheetDocument18 pagesNmap Cheat SheetJesse VazquezNo ratings yet
- Top 30 Nmap Command Examples For SysAdminsDocument8 pagesTop 30 Nmap Command Examples For SysAdminsYamabushiNo ratings yet
- Nmap CheatDocument1 pageNmap CheatKrishna ForuNo ratings yet
- Nmap CommandDocument3 pagesNmap CommandKrishna ForuNo ratings yet
- Nmap CommandsDocument21 pagesNmap Commandsramya.gNo ratings yet
- Top 32 Nmap Command Examples For SysNetwork AdminsDocument16 pagesTop 32 Nmap Command Examples For SysNetwork AdminswizunuNo ratings yet
- Nmap Openssl Snmpget-Walk Ldapsearch Dig Cisco IOS Tcpdump Ssldump Iptables NC (Netcat) Ruby Mysql-OnE LINERSDocument48 pagesNmap Openssl Snmpget-Walk Ldapsearch Dig Cisco IOS Tcpdump Ssldump Iptables NC (Netcat) Ruby Mysql-OnE LINERSmitrasamrat20026085No ratings yet
- Name Synopsis Description: Nmap (Scan Type... ) (Options) (Target Specification)Document42 pagesName Synopsis Description: Nmap (Scan Type... ) (Options) (Target Specification)aNo ratings yet
- NMap - Network MappingDocument35 pagesNMap - Network MappingFaisal AR100% (3)
- Da 02Document18 pagesDa 02Kumar RajaNo ratings yet
- Oscp Notes Active Directory 1Document70 pagesOscp Notes Active Directory 1Talha KhanNo ratings yet
- NmapDocument55 pagesNmapyogesh2377No ratings yet
- Top 16 Nmap Commands To Scan Remote HostsDocument10 pagesTop 16 Nmap Commands To Scan Remote Hostsmindhackers161No ratings yet
- Top 30 Nmap Command ExamplesDocument12 pagesTop 30 Nmap Command ExamplesvictorpetriniNo ratings yet
- 10 Practical Nmap CommandsDocument2 pages10 Practical Nmap CommandsB.JayNo ratings yet
- Tutorial 3 - Network and Port ScanningDocument3 pagesTutorial 3 - Network and Port ScanningJimmy BooNo ratings yet
- Lab Hacking1 10Document21 pagesLab Hacking1 10tvm1318022002No ratings yet
- TCP Scanning Using NmapDocument12 pagesTCP Scanning Using Nmapprat jariwalaNo ratings yet
- Cyber Security Lab ManualDocument19 pagesCyber Security Lab ManualadiradityasinghNo ratings yet
- CS - Pr2Document24 pagesCS - Pr2muskanbandariaNo ratings yet
- Ringkasan OpsiDocument3 pagesRingkasan OpsiJamal SyarifNo ratings yet
- Network Reconnaissance and Port Scanning Using NmapDocument6 pagesNetwork Reconnaissance and Port Scanning Using NmapAbdulrhman AlshameriNo ratings yet
- 6 T 7 y 7 y 7 y 8Document3 pages6 T 7 y 7 y 7 y 8govebNo ratings yet
- DJF EnumerationDocument2 pagesDJF EnumerationElyar SafarovNo ratings yet
- NmapDocument14 pagesNmapayeshashafeeqNo ratings yet
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkFrom EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo ratings yet
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityFrom EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityNo ratings yet
- Overview of Some Windows and Linux Intrusion Detection ToolsFrom EverandOverview of Some Windows and Linux Intrusion Detection ToolsNo ratings yet
- Experiment No.11A: NAME-ANIKET - I2 - 39Document4 pagesExperiment No.11A: NAME-ANIKET - I2 - 39aniket kasturiNo ratings yet
- Networks Pre Connection Attacks PDFDocument15 pagesNetworks Pre Connection Attacks PDFaniket kasturiNo ratings yet
- Experiment No. 6 Aim Theory:: Name - Aniket.K - I2-39Document3 pagesExperiment No. 6 Aim Theory:: Name - Aniket.K - I2-39aniket kasturiNo ratings yet
- NAME - ANIKET.K-I2-39 POST LAB Assignment Aim:: Packet TracerDocument2 pagesNAME - ANIKET.K-I2-39 POST LAB Assignment Aim:: Packet Traceraniket kasturiNo ratings yet
- NAME - ANIKET.K - I2 - 39 : Experiment No.11 BDocument3 pagesNAME - ANIKET.K - I2 - 39 : Experiment No.11 Baniket kasturiNo ratings yet
- NAME-ANIKET.K - I2-39 Experiment No.: 11 C Aim: Program CodeDocument4 pagesNAME-ANIKET.K - I2-39 Experiment No.: 11 C Aim: Program Codeaniket kasturiNo ratings yet
- NAME - ANIKET.K - I2-39 Experiment No. 12 Aim: TCP Socket Programming: Program CodeDocument3 pagesNAME - ANIKET.K - I2-39 Experiment No. 12 Aim: TCP Socket Programming: Program Codeaniket kasturiNo ratings yet
- Push Down AutomataDocument23 pagesPush Down Automataaniket kasturiNo ratings yet