Professional Documents
Culture Documents
1: Scan A Single Host or An Ip Address (Ipv4) : Nmap 192.168.1.1 192.168.1.2 192.168.1.3 Nmap 192.168.1.1,2,3
Uploaded by
fallli0 ratings0% found this document useful (0 votes)
13 views4 pagescode
Original Title
1.doc
Copyright
© © All Rights Reserved
Available Formats
ODT, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this Documentcode
Copyright:
© All Rights Reserved
Available Formats
Download as ODT, PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
13 views4 pages1: Scan A Single Host or An Ip Address (Ipv4) : Nmap 192.168.1.1 192.168.1.2 192.168.1.3 Nmap 192.168.1.1,2,3
Uploaded by
falllicode
Copyright:
© All Rights Reserved
Available Formats
Download as ODT, PDF, TXT or read online from Scribd
You are on page 1of 4
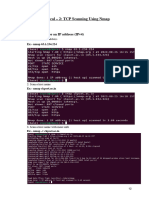
1: Scan a single host or an IP address (IPv4)
### Scan a single ip address ###
nmap 192.168.1.1
## Scan a host name ###
nmap server1.cyberciti.biz
## Scan a host name with more info###
nmap -v server1.cyberciti.biz
2: Scan multiple IP address or subnet (Ipv4)
nmap 192.168.1.1 192.168.1.2 192.168.1.3
nmap 192.168.1.1,2,3
scan a range of IP address too:
nmap 192.168.1.1-20
scan a range of IP address using a wildcard:
nmap 192.168.1.*
3: Read list of hosts/networks from a file (IPv4)
The -iL option allows you to read the list of target systems using a text file. This is useful to
scan a large number of hosts/networks. Create a text file as follows:
cat > /tmp/test.txt
nmap -iL /tmp/test.txt
4: Excluding hosts/networks (IPv4)
When scanning a large number of hosts/networks you can exclude hosts from a scan:
nmap 192.168.1.0/24 --exclude 192.168.1.5
nmap 192.168.1.0/24 --exclude 192.168.1.5,192.168.1.254
5: Turn on OS and version detection scanning script (IPv4)
nmap -A 192.168.1.254
nmap -v -A 192.168.1.1
nmap -A -iL /tmp/scanlist.txt
6: Find out if a host/network is protected by a firewall
nmap -sA 192.168.1.254
nmap -sA server1.cyberciti.biz
7: Scan a host when protected by the firewall
nmap -PN 192.168.1.1
nmap -PN server1.cyberciti.biz
8: Scan a network and find out which servers and devices are up and
running
This is known as host discovery or ping scan:
nmap -sP 192.168.1.0/24
9: perform a fast scan
nmap -F 192.168.1.1
10: Display the reason a port is in a particular state
nmap --reason 192.168.1.1
nmap --reason server1.cyberciti.biz
11: Only show open (or possibly open) ports
nmap --open 192.168.1.1
nmap --open server1.cyberciti.biz
12: Show all packets sent and received
nmap --packet-trace 192.168.1.1
nmap --packet-trace server1.cyberciti.biz
13:Show host interfaces and routes
nmap iflist
14: The fastest way to scan all your devices/computers for open ports
ever
nmap -T5 192.168.1.0/24
15: detect remote operating system
nmap -O 192.168.1.1
16: detect remote services (server / daemon) version numbers
nmap -sV 192.168.1.1
17: Scan a host using TCP ACK (PA) and TCP Syn (PS) ping
If firewall is blocking standard ICMP pings, try the following host discovery methods:
nmap -PS 192.168.1.1
nmap -PS 80,21,443 192.168.1.1
nmap -PA 192.168.1.1
nmap -PA 80,21,200-512 192.168.1.1
18: Scan a host using IP protocol ping
nmap -PO 192.168.1.1
19: saving output to a text file
The syntax is:
nmap 192.168.1.1 > output.txt
You might also like
- Etl Testing Real Time Interview QuestionsDocument20 pagesEtl Testing Real Time Interview QuestionsSai Vasu75% (16)
- Marketing Research Assignment: 11 Steps of Market ResearchDocument14 pagesMarketing Research Assignment: 11 Steps of Market ResearchSimbarashe MaringosiNo ratings yet
- Wireshark - Follow TCP StreamDocument7 pagesWireshark - Follow TCP StreamSundeel Bin Haleem100% (1)
- Aps Push Service Via Soap v1.8 enDocument61 pagesAps Push Service Via Soap v1.8 enSNo ratings yet
- ELearnSecurity ECPPT Notes ExamDocument157 pagesELearnSecurity ECPPT Notes ExamAngel CabralesNo ratings yet
- Lab 2 Scanning NetworksDocument143 pagesLab 2 Scanning Networksfawas hamdiNo ratings yet
- Project ReportDocument48 pagesProject ReportMona GoyalNo ratings yet
- Top 32 Nmap Command Examples For SysNetwork AdminsDocument16 pagesTop 32 Nmap Command Examples For SysNetwork AdminswizunuNo ratings yet
- Experiment - 1: #1: Scan A Single Host or An Ip Address (Ipv4)Document17 pagesExperiment - 1: #1: Scan A Single Host or An Ip Address (Ipv4)Hardik MehtaNo ratings yet
- Nmap CommandDocument3 pagesNmap CommandKrishna ForuNo ratings yet
- Craft: Top 30 Nmap Command Examples For Sys/Network AdminsDocument27 pagesCraft: Top 30 Nmap Command Examples For Sys/Network AdminsJoerdy LianuryNo ratings yet
- Top 30 Nmap Command ExamplesDocument12 pagesTop 30 Nmap Command ExamplesvictorpetriniNo ratings yet
- Top 30 Nmap Command Examples For SysAdminsDocument8 pagesTop 30 Nmap Command Examples For SysAdminsYamabushiNo ratings yet
- Da 02Document18 pagesDa 02Kumar RajaNo ratings yet
- NmapDocument55 pagesNmapyogesh2377No ratings yet
- N Map CommandDocument12 pagesN Map CommandMakarius YuwonoNo ratings yet
- NMAP Cheat Sheet and Tutorial GuideDocument8 pagesNMAP Cheat Sheet and Tutorial Guidehoadi100% (2)
- Task-4 Scanning and Enumeration TechniquesDocument28 pagesTask-4 Scanning and Enumeration TechniquesVenkat KarthikNo ratings yet
- NMAP Commands Cheat Sheet and Tutorial With Examples (Download PDFDocument10 pagesNMAP Commands Cheat Sheet and Tutorial With Examples (Download PDFjaveeed0401No ratings yet
- Vulnerability Assessment Using NmapDocument10 pagesVulnerability Assessment Using NmapKavisha SolankiNo ratings yet
- Network Scanning Using NmapDocument6 pagesNetwork Scanning Using Nmapmillanu6275No ratings yet
- TCP Scanning Using NmapDocument12 pagesTCP Scanning Using Nmapprat jariwalaNo ratings yet
- Name Synopsis Description: Nmap (Scan Type... ) (Options) (Target Specification)Document42 pagesName Synopsis Description: Nmap (Scan Type... ) (Options) (Target Specification)aNo ratings yet
- NmapDocument14 pagesNmapayeshashafeeqNo ratings yet
- Rajasthan Technical University, Kota Cyber Security Assignment NMAP CommandsDocument17 pagesRajasthan Technical University, Kota Cyber Security Assignment NMAP CommandsAbhishekNo ratings yet
- Nmap Command Examples in LinuxDocument13 pagesNmap Command Examples in LinuxHakim Samiul Hossain MunnaNo ratings yet
- Ex - No: 1 Study of Basic Network CommandsDocument6 pagesEx - No: 1 Study of Basic Network CommandsAnto ShybinNo ratings yet
- Ana Chanaba Robert HuyloDocument18 pagesAna Chanaba Robert HuyloAkshay ChoudharyNo ratings yet
- Fire Up Cpan On UbuntuDocument17 pagesFire Up Cpan On UbuntuHarguilar NhangaNo ratings yet
- Copy of CS_Pr2Document24 pagesCopy of CS_Pr2muskanbandariaNo ratings yet
- NMAPDocument60 pagesNMAPSrdjan DrazovicNo ratings yet
- Cybersecurity Practical JAINIDocument43 pagesCybersecurity Practical JAINIkhaabishayarNo ratings yet
- NMAP Command Guide SheetDocument5 pagesNMAP Command Guide SheetRafoo MGNo ratings yet
- Nmap CommandDocument14 pagesNmap CommandFrancis Densil RajNo ratings yet
- IT Systems Security: Submitted By: Submitted To: Ayush Sharma Dr. Adarsh Kumar 500061524 R134217045 Cse-Csf (Vi) B1Document15 pagesIT Systems Security: Submitted By: Submitted To: Ayush Sharma Dr. Adarsh Kumar 500061524 R134217045 Cse-Csf (Vi) B1Mansi BishtNo ratings yet
- Pen Testing Tools Cheat SheetDocument39 pagesPen Testing Tools Cheat Sheetsetyahangga3No ratings yet
- Discover Network Services with NmapDocument35 pagesDiscover Network Services with NmapFaisal AR100% (3)
- Windows 7 Host Port ScanDocument7 pagesWindows 7 Host Port Scan123456789No ratings yet
- CIT 480: Securing Computer Systems Lab #7: Network Scanning NameDocument4 pagesCIT 480: Securing Computer Systems Lab #7: Network Scanning NameManzu PokharelNo ratings yet
- CN PracticalDocument9 pagesCN PracticalJui BhanushaliNo ratings yet
- Perform An Experiment For Port Scanning With Nmap, Superscan or Any Other Equivalent SoftwareDocument4 pagesPerform An Experiment For Port Scanning With Nmap, Superscan or Any Other Equivalent SoftwaresangeetadineshNo ratings yet
- Modul Praktikum NmapDocument31 pagesModul Praktikum NmapJabang Aru SaputroNo ratings yet
- NmapDocument14 pagesNmapamird12No ratings yet
- Cyber SecurityDocument73 pagesCyber SecuritymuskanbandariaNo ratings yet
- Nmap Is The Definitive Port Scanner. It Is A Network Discovery Tool Used by Ethical Hackers On A DailyDocument2 pagesNmap Is The Definitive Port Scanner. It Is A Network Discovery Tool Used by Ethical Hackers On A DailymibaNo ratings yet
- SampleDocument8 pagesSampleBryle DrioNo ratings yet
- Enumeration Using NmapDocument7 pagesEnumeration Using NmapFatema TahaNo ratings yet
- 20bit0428 VL2022230101456 Ast02Document19 pages20bit0428 VL2022230101456 Ast02Kumar RajaNo ratings yet
- PTDocument5 pagesPThsaekjakNo ratings yet
- Lab Experiment #08 - Network & Host Detection ScansDocument3 pagesLab Experiment #08 - Network & Host Detection ScansAnoop DasNo ratings yet
- Nmap:The Network MapperDocument13 pagesNmap:The Network MapperNahid MajumderNo ratings yet
- Nmap Network Discovery and Port ScanningDocument11 pagesNmap Network Discovery and Port ScanningAdfar RashidNo ratings yet
- PES2UG22CS397CNLABWEEK1Document15 pagesPES2UG22CS397CNLABWEEK1Ashish GuptaNo ratings yet
- CDIS CV PL.2 ScoutingDocument33 pagesCDIS CV PL.2 ScoutingIvanildo CostaNo ratings yet
- Comprehensive Nmap Scanning TechniquesDocument2 pagesComprehensive Nmap Scanning Techniquesaniket kasturiNo ratings yet
- Nmap Cheat SheetDocument18 pagesNmap Cheat SheetJesse VazquezNo ratings yet
- Network CommandsDocument21 pagesNetwork Commandsivica77No ratings yet
- CN Lab Manual-2-60Document59 pagesCN Lab Manual-2-60alps2coolNo ratings yet
- Nmap ManualDocument65 pagesNmap ManualMastNo ratings yet
- Wireshark and Nmap: 19Bct0021 Swayam Shresth Mohapatra Cse-3501 Isaa L55+56Document8 pagesWireshark and Nmap: 19Bct0021 Swayam Shresth Mohapatra Cse-3501 Isaa L55+56Swayam Mohapatra100% (1)
- CN LAB ManualDocument72 pagesCN LAB Manualraghu atluriNo ratings yet
- CN Lab ManualDocument74 pagesCN Lab Manualraghu atluriNo ratings yet
- Lab 03 Scanning NetworksDocument116 pagesLab 03 Scanning NetworksErnesto Galvan PapelNo ratings yet
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkFrom EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo ratings yet
- JAVA Socket Programming: 2003.3.19 Joonbok Lee KaistDocument30 pagesJAVA Socket Programming: 2003.3.19 Joonbok Lee Kaistdev_okNo ratings yet
- StanleyDocument30 pagesStanleycrankycoderNo ratings yet
- Sorting Algorithms - Strand Sort - Rosetta CodeDocument41 pagesSorting Algorithms - Strand Sort - Rosetta CodefallliNo ratings yet
- Sorting Algorithms - Strand Sort - Rosetta CodeDocument41 pagesSorting Algorithms - Strand Sort - Rosetta CodefallliNo ratings yet
- Information and Network Security: 1. StatementDocument3 pagesInformation and Network Security: 1. StatementfallliNo ratings yet
- Computer Engineer Falgun Patel ResumeDocument2 pagesComputer Engineer Falgun Patel ResumefallliNo ratings yet
- ASP Web Server Controls: Please Use Speaker Notes For Additional Information!Document20 pagesASP Web Server Controls: Please Use Speaker Notes For Additional Information!fallliNo ratings yet
- Introduction to ASP.NET - Understanding the .NET Framework ArchitectureDocument40 pagesIntroduction to ASP.NET - Understanding the .NET Framework ArchitectureDeep PatelNo ratings yet
- Check ProDocument1 pageCheck ProfallliNo ratings yet
- Transport LayerDocument106 pagesTransport LayerfallliNo ratings yet
- CH 04Document145 pagesCH 04fallliNo ratings yet
- CH 05Document103 pagesCH 05fallliNo ratings yet
- Dsa MCQDocument9 pagesDsa MCQbenaminsan100% (1)
- Leverage The Data Trapped in Unstructured Sources With Data ExtractionDocument27 pagesLeverage The Data Trapped in Unstructured Sources With Data ExtractionAstera SoftwareNo ratings yet
- Arrays in C PDFDocument32 pagesArrays in C PDFDj LouderhouseNo ratings yet
- CAPE INFORMATION TECHNOLOGY Unit 2 SO 1Document14 pagesCAPE INFORMATION TECHNOLOGY Unit 2 SO 1Shannoyia D'Neila ClarkeNo ratings yet
- Microproject ProformaDocument3 pagesMicroproject ProformaRushaliNo ratings yet
- Fs Mini Project ReportDocument25 pagesFs Mini Project Report9 New accountNo ratings yet
- RMAN CLONING DIRECTORY STRUCTURE IS DIFFERENT - SERVER TO SERVER (10g) PDFDocument14 pagesRMAN CLONING DIRECTORY STRUCTURE IS DIFFERENT - SERVER TO SERVER (10g) PDFG.R.THIYAGU ; Oracle DBANo ratings yet
- Ali Linux CommandsDocument17 pagesAli Linux CommandsrediNo ratings yet
- Chapter IDocument23 pagesChapter IPrecious UmingaNo ratings yet
- Efficient SQL StatementsDocument6 pagesEfficient SQL StatementsBodea FlorinNo ratings yet
- ch4 Notes (Security Part II-Auditing Database Systems)Document3 pagesch4 Notes (Security Part II-Auditing Database Systems)ziahnepostreliNo ratings yet
- BJMC 14 Block 04Document49 pagesBJMC 14 Block 04Kriti SinhaNo ratings yet
- DBMS ReviewerDocument8 pagesDBMS ReviewerPeyNo ratings yet
- Database Design Document TemplateDocument82 pagesDatabase Design Document Templaterockyloveu2100% (1)
- Effects of Mobile Games Mobile Legends TDocument9 pagesEffects of Mobile Games Mobile Legends Tgazer beam100% (3)
- Analisa Bangkitan Perjalanan Perumahan Villa Indah Permai Dan Villa Dago Permai Di Kecamatan Baturaja Timur Kabupaten Ogan Komering UluDocument10 pagesAnalisa Bangkitan Perjalanan Perumahan Villa Indah Permai Dan Villa Dago Permai Di Kecamatan Baturaja Timur Kabupaten Ogan Komering UluTYOCLALUGUANTENGNo ratings yet
- Cad - Notes Part IIDocument15 pagesCad - Notes Part IIAlfayo OmayioNo ratings yet
- Demystifying Strategy & Operations in Tech (by Herng Lee)Document61 pagesDemystifying Strategy & Operations in Tech (by Herng Lee)Thanh Nhan Nguyen ThiNo ratings yet
- Improving Students' Achievement in Writing by Using Movie PostersDocument16 pagesImproving Students' Achievement in Writing by Using Movie Postersfadhilah santriNo ratings yet
- On Data Handling Using Pandas-IDocument63 pagesOn Data Handling Using Pandas-Ianagha100% (2)
- SAP ABAP Programming OverviewDocument72 pagesSAP ABAP Programming Overviewanis habiballahNo ratings yet
- International Finance Literature ReviewDocument8 pagesInternational Finance Literature Reviewaflsodqew100% (1)
- IBM Data Virtualization Manager For z/OSDocument250 pagesIBM Data Virtualization Manager For z/OSrajneesh oshoNo ratings yet
- Oracle HRMS Question e BookDocument37 pagesOracle HRMS Question e BookSyed Farhan Ashraf100% (1)
- Practice Assessment For Exam DPDocument51 pagesPractice Assessment For Exam DPm3aistoreNo ratings yet
- Cassandra and Data HandlingDocument7 pagesCassandra and Data HandlingLynch GeorgeNo ratings yet