Professional Documents
Culture Documents
Dvanced Etwork Ecurity: M Z Q D C S F, I
Uploaded by
Zee Shan0 ratings0% found this document useful (0 votes)
8 views17 pagesOriginal Title
ANS-Lecture-5-BlockCiphers-ModesOfOperations
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
8 views17 pagesDvanced Etwork Ecurity: M Z Q D C S F, I
Uploaded by
Zee ShanCopyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You are on page 1of 17
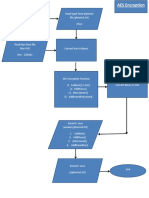
ADVANCED NETWORK SECURITY
Lecture 5 – Block Ciphers Modes of Operations
M UHAMMAD Z ESHAN Q URASHI
D EPARTMENT OF C OMPUTER S CIENCE
F UUAST,I SLAMABAD
Lecture Agenda
To show how modern standard ciphers, such as DES or AES, can be used to encipher long
messages
To discuss five modes of operation designed to be used with modern block ciphers
To define which mode of operation creates stream ciphers out of the underlying block ciphers
ADVANCED NETWORK SECURITY 2
Message Padding
The plaintext message is broken into blocks, P1, P2, P3, ...
The last block may be short and may needs padding
Possible padding:
◦ Known non-data values (e.g. NULLS)
◦ Or a number indicating the size of the pad
◦ Or a number indicating the size of the plaintext
◦ The last two schemes may require an extra block.
ADVANCED NETWORK SECURITY 3
Modes of Operations
ADVANCED NETWORK SECURITY 4
Electronic Code Book - ECB
The simplest mode of operation - ECB
For a given key, this mode behaves like we have a gigantic codebook, in which each plaintext block
has an entry, hence the name Electronic Code Book is used.
ADVANCED NETWORK SECURITY 5
About ECB
Strength: it’s simple.
No Error Propagation
Weakness:
◦ Repetitive information contained in the plaintext may show in the ciphertext
◦ If the same message (e.g., an CNIC) is encrypted (with the same key) and sent twice, their ciphertexts are the same.
Typical application
◦ Secure transmission of short pieces of information (e.g. a temporary encryption key)
ADVANCED NETWORK SECURITY 6
Error Propagation?
A single bit error in transmission can create errors in several in the corresponding block.
However, the error does not, in ECB, have any effect on the other blocks.
ADVANCED NETWORK SECURITY 7
ECB Weakness
Assume that Eve works in a company a few hours per month (her monthly payment is very low).
She knows that the company uses several blocks of information for each employee in which the
seventh block is the amount of money to be deposited in the employee’s account.
Eve can intercept the ciphertext sent to the bank at the end of the month, replace the block with
the information about her payment with a copy of the block with the information about the
payment of a full-time colleague.
Each month Eve can receive more money than she deserves.
This is known as Replay attack
ADVANCED NETWORK SECURITY 8
ECB Weakness
ECB can leave plaintext data patterns in the ciphertext, as can be seen when ECB mode is used to
encrypt a bitmap image which uses large areas of uniform color. Although each individual pixel is
encrypted, the overall image may still be discerned as the pattern of identically colored pixels in the
original remains in the encrypted version.
ADVANCED NETWORK SECURITY 9
Cipher Block Chaining - CBC
In CBC mode, each plaintext block is XOR-ed with the previous ciphertext block before being
encrypted. Invented by IBM in 1976
ADVANCED NETWORK SECURITY 10
Cipher Block Chaining - CBC
CBC has been the most commonly used mode of operation.
The initialization vector (IV) should be known by the sender and the receiver.
Disadvantages
◦ Encryption is sequential (i.e., it cannot be parallelized)
◦ A single bit error in ciphertext block during transmission may create error in most bits in
plaintext block
◦ The message must be padded to a multiple of the cipher block size.
Decrypting with the incorrect IV causes the first block of plaintext to be corrupt but subsequent
plaintext blocks will be correct.
Note: Decryption can be parallelized
ADVANCED NETWORK SECURITY 11
Cipher Feedback (CFB) Mode
The previous block’s ciphertext is re-
encrypted and XOR-ed with plain text.
Note that encryption algorithm is used in
both CFB Encryption and Decryption
ADVANCED NETWORK SECURITY 12
CFB as Stream Cipher
ADVANCED NETWORK SECURITY 13
Output Feedback (OFB) Mode
The output feedback (OFB) mode makes a block cipher into a synchronous stream cipher.
ADVANCED NETWORK SECURITY 14
Counter (CTR) Mode
In the counter (CTR) mode, there is no feedback. The pseudorandomness in the key stream is
achieved using a counter.
ADVANCED NETWORK SECURITY 15
Counter (CTR) Mode as a Stream Cipher
ADVANCED NETWORK SECURITY 16
Summary
ADVANCED NETWORK SECURITY 17
You might also like
- Part 1Document36 pagesPart 1Farhan SjNo ratings yet
- Introduction to Smart Cards and Quantum CryptographyDocument11 pagesIntroduction to Smart Cards and Quantum CryptographyayanthakNo ratings yet
- ECEG-6530 Computer (And Network) Security: Private-Key Encryption Schemes, Modes of EncryptionDocument30 pagesECEG-6530 Computer (And Network) Security: Private-Key Encryption Schemes, Modes of EncryptionYekeber AddisNo ratings yet
- Ch02 BlockCipher StreamCipher ModesOp DESDocument67 pagesCh02 BlockCipher StreamCipher ModesOp DESVIDIT SHAHNo ratings yet
- Is CH4Document13 pagesIs CH4Dhruv SojitraNo ratings yet
- Information Secuirity AssDocument6 pagesInformation Secuirity Assproductsample183No ratings yet
- Information Secuirity AssDocument6 pagesInformation Secuirity Assproductsample183No ratings yet
- Cryptography Week4 Assessment: KEY: 0123456789ABCDEF Input Data: Hi Hello WelcomeDocument7 pagesCryptography Week4 Assessment: KEY: 0123456789ABCDEF Input Data: Hi Hello WelcomeHarismita NagrajNo ratings yet
- DNS PP Short QuestionDocument13 pagesDNS PP Short Question13 Samia farnazNo ratings yet
- Module 2 - Symmetric and asymmetric key cryptography and key management block cipher modesDocument37 pagesModule 2 - Symmetric and asymmetric key cryptography and key management block cipher modes04 KHUSHBU BHATIA SE ANo ratings yet
- Ma Chan Myae Thu (For Third Seminar)Document47 pagesMa Chan Myae Thu (For Third Seminar)Dr. Myat Mon KyawNo ratings yet
- Modes of Encryption and DecryptionDocument26 pagesModes of Encryption and DecryptionFatima SyedNo ratings yet
- How To Choose AES ModeDocument16 pagesHow To Choose AES Modeاليزيد بن توهاميNo ratings yet
- Block Cipher Operation: Nauman H. Ansari Spring 2019 - MAJUDocument8 pagesBlock Cipher Operation: Nauman H. Ansari Spring 2019 - MAJUkaka shipaiNo ratings yet
- 01204427-Modes of OperationDocument38 pages01204427-Modes of OperationSwati SharmaNo ratings yet
- Information Security CRlsDocument49 pagesInformation Security CRls2OO11AO513No ratings yet
- Experiment 2 ICSDocument7 pagesExperiment 2 ICSritika sahuNo ratings yet
- CNS Unit - 2Document17 pagesCNS Unit - 2logeshwaran1725No ratings yet
- Opportunistic EncryptionDocument13 pagesOpportunistic EncryptionMichael FirmanNo ratings yet
- CryptographyDocument21 pagesCryptographyinamdaramena4No ratings yet
- Cryptography and Network Security Module 2 QuestionsDocument8 pagesCryptography and Network Security Module 2 QuestionsSubhadip MajiNo ratings yet
- Jaypractical 14Document6 pagesJaypractical 14Dhruv SojitraNo ratings yet
- InfoSec Lect 6Document30 pagesInfoSec Lect 6Taha AhmedNo ratings yet
- Lab02 - Block Ciphers DES - AESDocument13 pagesLab02 - Block Ciphers DES - AESEllieNo ratings yet
- AES ModesDocument9 pagesAES Modespaul diNo ratings yet
- Chapter 6: Block Cipher OperationDocument6 pagesChapter 6: Block Cipher OperationOmnia GalalNo ratings yet
- Block Cipher Modes Strengths and WeaknessesDocument3 pagesBlock Cipher Modes Strengths and WeaknesseseshanNo ratings yet
- 01204427-Modes of OperationDocument38 pages01204427-Modes of OperationAngel KirubaNo ratings yet
- Unit 4Document23 pagesUnit 4Andualem BegunoNo ratings yet
- Outline: Chris Karlof, Naveen Sastry, and David WagnerDocument22 pagesOutline: Chris Karlof, Naveen Sastry, and David Wagnermarchelo_cheloNo ratings yet
- Cryptography and Network SecurityDocument16 pagesCryptography and Network SecuritysuryakasiNo ratings yet
- Cryptography Lecture 5 NotesDocument11 pagesCryptography Lecture 5 NotesShivend MenonNo ratings yet
- Ebook Cryptography and Network Security Principles and Practice 6Th Edition William Stallings Test Bank Full Chapter PDFDocument29 pagesEbook Cryptography and Network Security Principles and Practice 6Th Edition William Stallings Test Bank Full Chapter PDFMrScottPowelltgry100% (10)
- Block Cipher ModesDocument10 pagesBlock Cipher ModesMohamed MohamedNo ratings yet
- Cryptography An Introduction Continued : Shon Harris Cissp, 5 EditionDocument24 pagesCryptography An Introduction Continued : Shon Harris Cissp, 5 EditionMuhammad Bilal MukhtarNo ratings yet
- Encipherment Using Modern Symmetric-Key Ciphers-Block CiphersDocument48 pagesEncipherment Using Modern Symmetric-Key Ciphers-Block Cipherssatish naikawadiNo ratings yet
- Difference Between Symmetric and Asymmetric Key Encryption: Block Cipher Modes of OperationDocument15 pagesDifference Between Symmetric and Asymmetric Key Encryption: Block Cipher Modes of OperationUchiha SasukeNo ratings yet
- Chapter 4 PPTDocument31 pagesChapter 4 PPTKotireddy vinthaNo ratings yet
- An Overview of CryptographyDocument65 pagesAn Overview of CryptographyNguyễn Tuấn AnhNo ratings yet
- CS6701 CNS Unit-Ii NotesDocument23 pagesCS6701 CNS Unit-Ii Notesgayathri baskarNo ratings yet
- 137 - CS8792, CS6701 Cryptography and Network Security - 2 Marks With Answers 2Document17 pages137 - CS8792, CS6701 Cryptography and Network Security - 2 Marks With Answers 2Lionel Bharath RazerNo ratings yet
- Modes of OperationDocument32 pagesModes of Operation19Z205 Bala Bharat RaajNo ratings yet
- PR7__AES_Java_FinalDocument3 pagesPR7__AES_Java_FinalprafullaNo ratings yet
- Fachpraktikum 5. / 6. Semester Studiengang Elektrotechnik Is 1: CryptofunDocument13 pagesFachpraktikum 5. / 6. Semester Studiengang Elektrotechnik Is 1: CryptofunNeelu RanganathNo ratings yet
- Modes of OperationDocument17 pagesModes of OperationAyush JainNo ratings yet
- Block Cipher OperationsDocument36 pagesBlock Cipher OperationsAarindam RainaNo ratings yet
- Block Cipher and Modes of CipherDocument10 pagesBlock Cipher and Modes of CipherJOSHUA CECIL L URK20AI1061No ratings yet
- Modern Symmetric Key EncryptionDocument23 pagesModern Symmetric Key EncryptionEr Niraj SinghNo ratings yet
- AES Encryption: Modes and StructureDocument22 pagesAES Encryption: Modes and StructureveenadivyakishNo ratings yet
- Block Cipher FundamentalsDocument6 pagesBlock Cipher FundamentalsanandhacNo ratings yet
- Lab01 - Symmetric CryptographyDocument13 pagesLab01 - Symmetric Cryptography21522672No ratings yet
- Part 3Document18 pagesPart 3Farhan SjNo ratings yet
- Unit 1 AnsDocument39 pagesUnit 1 AnsVikramadityaNo ratings yet
- NS Two MarksDocument17 pagesNS Two MarksSankari SoniNo ratings yet
- Block Cipher Modes and Triple DesDocument30 pagesBlock Cipher Modes and Triple Desash 3No ratings yet
- 07-Block Cipher Operation+stream CipherDocument37 pages07-Block Cipher Operation+stream Cipher6alal UshNo ratings yet
- IS364 - Lecture 09 - Symmetric EncryptionDocument41 pagesIS364 - Lecture 09 - Symmetric Encryptionsamwel sittaNo ratings yet
- Network Security 2Document57 pagesNetwork Security 2DarshanNo ratings yet
- 214 Naef AesDocument8 pages214 Naef AesMrunali BarapatreNo ratings yet
- AES Example - Input (128 bit key and messageDocument17 pagesAES Example - Input (128 bit key and messageVikas PsNo ratings yet
- Cyber-Laws Part IDocument19 pagesCyber-Laws Part IZee ShanNo ratings yet
- CS2110: Hashing Practice QuestionsDocument3 pagesCS2110: Hashing Practice QuestionsNithyasri ArumugamNo ratings yet
- Instructions About Online Exam Only For CCN-5 B (Morning)Document1 pageInstructions About Online Exam Only For CCN-5 B (Morning)Zee ShanNo ratings yet
- Dvanced Etwork Ecurity: M Z Q D C S F, IDocument26 pagesDvanced Etwork Ecurity: M Z Q D C S F, IZee ShanNo ratings yet
- Dvanced Etwork Ecurity: M Z Q D C S F, IDocument27 pagesDvanced Etwork Ecurity: M Z Q D C S F, IZee ShanNo ratings yet
- Dvanced Etwork Ecurity: M Z Q D C S F, IDocument27 pagesDvanced Etwork Ecurity: M Z Q D C S F, IZee ShanNo ratings yet
- Chapter 1: Introduction: Muhammad Zeshan Qurashi Fuuast, Islamabad Spring, 2020Document77 pagesChapter 1: Introduction: Muhammad Zeshan Qurashi Fuuast, Islamabad Spring, 2020Zee ShanNo ratings yet
- Lab Tech 26 Sep 2019Document1 pageLab Tech 26 Sep 2019Zee ShanNo ratings yet
- Almiraj Sufi & Islamic Study Centre, Inc. 2009 Page 58Document8 pagesAlmiraj Sufi & Islamic Study Centre, Inc. 2009 Page 58Zee ShanNo ratings yet
- Caesar CipherDocument5 pagesCaesar CipherS ANo ratings yet
- Substitution CipherDocument7 pagesSubstitution CipherphaulusNo ratings yet
- 1402 Columnar TranspositionDocument8 pages1402 Columnar TranspositionKrish ParekhNo ratings yet
- SmartEVSEv2 2Document1 pageSmartEVSEv2 2anetoNo ratings yet
- Atbash CipherDocument5 pagesAtbash CipherLouwella RamosNo ratings yet
- AES AlgorithmDocument25 pagesAES AlgorithmAhmad ShdifatNo ratings yet
- CodeDocument13 pagesCodeshiloh velascoNo ratings yet
- Playfair CipherDocument5 pagesPlayfair CiphermourinaNo ratings yet
- Motor Controller PIC2550 SchematicsDocument1 pageMotor Controller PIC2550 SchematicsRolando100% (2)
- Conventional Encryption AlgorithmsDocument41 pagesConventional Encryption AlgorithmsSwapna DollyNo ratings yet
- Java Product Cipher Encryption DecryptionDocument6 pagesJava Product Cipher Encryption DecryptionSudeep HegdeNo ratings yet
- Unit - 2: Onventional Ncryption PrinciplesDocument35 pagesUnit - 2: Onventional Ncryption PrincipleshafeezaNo ratings yet
- Traditional Symmetric-Key CiphersDocument74 pagesTraditional Symmetric-Key Cipherssatish naikawadiNo ratings yet
- CryptoDocument7 pagesCryptoPRINCE SHRIVASTAVANo ratings yet
- Lecture 3 Data Encryption Standard (DES) and Advanced Encrption StandardDocument62 pagesLecture 3 Data Encryption Standard (DES) and Advanced Encrption StandardNurdin YussufNo ratings yet
- A Format-Preserving Encryption FF1, FF3-1 Using Lightweight Block Ciphers LEA And, SPECKDocument7 pagesA Format-Preserving Encryption FF1, FF3-1 Using Lightweight Block Ciphers LEA And, SPECKPPP BBBNo ratings yet
- Chapter 2lecture02Document52 pagesChapter 2lecture02Tomas AgonaferNo ratings yet
- Unit1.2 MarksDocument7 pagesUnit1.2 MarksKarthic SundaramNo ratings yet
- 390 Codes, Ciphers, and Cryptography: Polygraphic Substitution Ciphers - Hill's SystemDocument25 pages390 Codes, Ciphers, and Cryptography: Polygraphic Substitution Ciphers - Hill's SystemShubhamKhanduriNo ratings yet
- Blowfish AlgorithmDocument11 pagesBlowfish AlgorithmMomtaj Hossain MowNo ratings yet
- Select Residence - Aptos 3 Dorm (Forte)Document3 pagesSelect Residence - Aptos 3 Dorm (Forte)Samuel LauppNo ratings yet
- Advanced Encryption StandardDocument3 pagesAdvanced Encryption Standardmahesh0291No ratings yet
- CH 2 Solutions - Network SecurityDocument9 pagesCH 2 Solutions - Network Securitykarthikc_625No ratings yet
- 1st Assignment of CSE 403Document8 pages1st Assignment of CSE 403Harjeet SinghNo ratings yet
- AES Algorithm Flow ChartDocument3 pagesAES Algorithm Flow Chartchernwei0% (1)
- Lecture 1 (Notes) : Confusion & DiffusionDocument5 pagesLecture 1 (Notes) : Confusion & DiffusionGauravNo ratings yet
- Cryptography and Network Security Unit - 2 Chapter 3 - Block Ciphers and The Data Encryption StandardDocument86 pagesCryptography and Network Security Unit - 2 Chapter 3 - Block Ciphers and The Data Encryption StandardAkshit PrajapatiNo ratings yet
- Advanced Encryption Standard ProgramDocument3 pagesAdvanced Encryption Standard ProgramChinamayi ChinmayiNo ratings yet
- Mod2 Classical EncryptionDocument17 pagesMod2 Classical EncryptionAmin SiddiqNo ratings yet
- Block Ciphers: Dr. Md. Mahbubur RahmnaDocument124 pagesBlock Ciphers: Dr. Md. Mahbubur RahmnaimtibdNo ratings yet
- Defensive Cyber Mastery: Expert Strategies for Unbeatable Personal and Business SecurityFrom EverandDefensive Cyber Mastery: Expert Strategies for Unbeatable Personal and Business SecurityRating: 5 out of 5 stars5/5 (1)
- The Internet Con: How to Seize the Means of ComputationFrom EverandThe Internet Con: How to Seize the Means of ComputationRating: 5 out of 5 stars5/5 (6)
- Facing Cyber Threats Head On: Protecting Yourself and Your BusinessFrom EverandFacing Cyber Threats Head On: Protecting Yourself and Your BusinessRating: 4.5 out of 5 stars4.5/5 (27)
- Cybersecurity: The Hacker Proof Guide To Cybersecurity, Internet Safety, Cybercrime, & Preventing AttacksFrom EverandCybersecurity: The Hacker Proof Guide To Cybersecurity, Internet Safety, Cybercrime, & Preventing AttacksNo ratings yet
- Hackers & Painters: Big Ideas from the Computer AgeFrom EverandHackers & Painters: Big Ideas from the Computer AgeRating: 4.5 out of 5 stars4.5/5 (5)
- GDPR-standard data protection staff training: What employees & associates need to know by Dr Paweł MielniczekFrom EverandGDPR-standard data protection staff training: What employees & associates need to know by Dr Paweł MielniczekNo ratings yet
- Hacking Essentials - The Beginner's Guide To Ethical Hacking And Penetration TestingFrom EverandHacking Essentials - The Beginner's Guide To Ethical Hacking And Penetration TestingRating: 3 out of 5 stars3/5 (1)
- An Ultimate Guide to Kali Linux for BeginnersFrom EverandAn Ultimate Guide to Kali Linux for BeginnersRating: 3.5 out of 5 stars3.5/5 (4)
- Apple Card and Apple Pay: A Ridiculously Simple Guide to Mobile PaymentsFrom EverandApple Card and Apple Pay: A Ridiculously Simple Guide to Mobile PaymentsNo ratings yet
- (ISC)2 CCSP Certified Cloud Security Professional Official Study GuideFrom Everand(ISC)2 CCSP Certified Cloud Security Professional Official Study GuideRating: 5 out of 5 stars5/5 (1)
- IAPP CIPP/US Certification A Practical Study Guide to Master the Certified Information Privacy Professional ExamFrom EverandIAPP CIPP/US Certification A Practical Study Guide to Master the Certified Information Privacy Professional ExamNo ratings yet
- No Place to Hide: Edward Snowden, the NSA, and the U.S. Surveillance StateFrom EverandNo Place to Hide: Edward Snowden, the NSA, and the U.S. Surveillance StateRating: 4 out of 5 stars4/5 (250)
- Stay Anonymous Online:A Short and Simple Guide to Hide Yourself In The InternetFrom EverandStay Anonymous Online:A Short and Simple Guide to Hide Yourself In The InternetNo ratings yet
- Set Up Your Own IPsec VPN, OpenVPN and WireGuard Server: Build Your Own VPNFrom EverandSet Up Your Own IPsec VPN, OpenVPN and WireGuard Server: Build Your Own VPNRating: 5 out of 5 stars5/5 (1)
- Hacking With Kali Linux : A Comprehensive, Step-By-Step Beginner's Guide to Learn Ethical Hacking With Practical Examples to Computer Hacking, Wireless Network, Cybersecurity and Penetration TestingFrom EverandHacking With Kali Linux : A Comprehensive, Step-By-Step Beginner's Guide to Learn Ethical Hacking With Practical Examples to Computer Hacking, Wireless Network, Cybersecurity and Penetration TestingRating: 4.5 out of 5 stars4.5/5 (9)
- Social Engineering: The Science of Human HackingFrom EverandSocial Engineering: The Science of Human HackingRating: 3.5 out of 5 stars3.5/5 (44)
- Cybersecurity For Beginners: Learn How To Defend Against Online ThreatsFrom EverandCybersecurity For Beginners: Learn How To Defend Against Online ThreatsNo ratings yet