Professional Documents
Culture Documents
Lab 6 - MITM With Ettercap - ARP Poisoning
Uploaded by
Pratham PandeyCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Lab 6 - MITM With Ettercap - ARP Poisoning
Uploaded by
Pratham PandeyCopyright:
Available Formats
Lab 6 - MITM with Ettercap - ARP Poisoning
Description: In this lab, we will do Man in the middle attack (MITM) using Ettercap. Ettercap is
a comprehensive suite for man in the middle attacks. It features sniffing of live connections,
content filtering on the fly and many other interesting tricks. It supports active and passive
dissection of many protocols and includes many features for network and host analysis.
Requirements for the lab: Attacker Machine - Kali Linux / Parrot OS. Victim / target Machine –
Windows Machine (Win 7/ Win 8)
Step 1: Launch your attacker machine (Parrot virtual machine) and log in
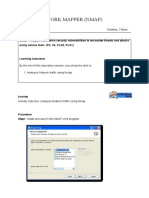
Step 2: Go to Applications -> Pentesting -> Sniffing & Spoofing and then launch Ettercap-
graphical
Step 3: At the prompt, it will ask for the adapter that you want to choose, you may choose unified
or bridged sniffing and then click on start.
Step 4: Once this is done, scan for the hosts, it will list you the IP address of the default gateway
as well as the IP address of the target machine. Make sure that your target machine is up and
running before this step.
Step 5: Now, from the lists of the hosts add the targets, add IP address of gateway as target 1
and IP address of victim as the target 2.
Step 6: Now, from MITM Menu select the ARP Poisoning, and make sure that Sniff remote
connections option is checked.
Step 7: Now, Ettercap has poisoned the ARP tables of the gateway and the target. Now, you
can perform the MITM and can sniff the traffic going from the target machine.
Step 8: Now, you can launch any network sniffer like tcpdump or wireshark on the attacker
machine. I am using tcpdump, I will open a separate terminal and type:
Sudo tcpdump –I eth0 port 80 and host IP_Address_of_target
Step 9: Now, the MITM attack is performed, any network activity on the target machine can be
observed with the tcpdump.
Note: It will take several minutes to run the scan.
Question 1: Do you see any network traffic after performing MITM on tcpdump?
If yes, please write some of them below:
Question 2: Do you see any other active hosts after scanning the hosts on Ettercap-graphical?
If yes, please write some of them below:?
You might also like
- Arp Poison Lab 2011Document17 pagesArp Poison Lab 2011Tứ Vũ VănNo ratings yet
- Lab Sheet 2Document9 pagesLab Sheet 2api-2414180090% (1)
- Wireless and Mobile Hacking and Sniffing TechniquesFrom EverandWireless and Mobile Hacking and Sniffing TechniquesNo ratings yet
- How To Perform A Man-In-The-middle (MITM) Attack With Kali Linux - Our Code World-man-In-The-middleDocument7 pagesHow To Perform A Man-In-The-middle (MITM) Attack With Kali Linux - Our Code World-man-In-The-middleHenry PaipiNo ratings yet
- Packet Sniffing and Spoofing Lab - FinalDocument26 pagesPacket Sniffing and Spoofing Lab - FinalKhalil Ullah67% (3)
- Network Security Lab Manual DraftDocument29 pagesNetwork Security Lab Manual DraftShraddha PatilNo ratings yet
- Vulnarability Scan With NMAP & Intrusion Attacks With and MetasploitDocument17 pagesVulnarability Scan With NMAP & Intrusion Attacks With and MetasploitRania BenamaraNo ratings yet
- How Hackers Use Your IP Address To Hack Your Computer & How To Stop ItDocument4 pagesHow Hackers Use Your IP Address To Hack Your Computer & How To Stop ItAnonymous rKtpSR3No ratings yet
- LAb 1Document9 pagesLAb 1Siti AisyahNo ratings yet
- Network Scanning TechniquesDocument17 pagesNetwork Scanning TechniquesjangdiniNo ratings yet
- Refresher Guide NmapDocument7 pagesRefresher Guide NmapmalinaNo ratings yet
- Perform An Experiment For Port Scanning With Nmap, Superscan or Any Other Equivalent SoftwareDocument4 pagesPerform An Experiment For Port Scanning With Nmap, Superscan or Any Other Equivalent SoftwaresangeetadineshNo ratings yet
- Tutorial 4 - ARP AttackDocument11 pagesTutorial 4 - ARP Attacklaytonchetty27No ratings yet
- NmapDocument14 pagesNmapamird12No ratings yet
- TCPIPDocument7 pagesTCPIPdgk84_idNo ratings yet
- Walkthrough 1866Document7 pagesWalkthrough 1866rivoluzioneaiNo ratings yet
- Man in The Middle Attacks ARP Poisoning: Redirect Packets To and From Any Client To Our DeviceDocument19 pagesMan in The Middle Attacks ARP Poisoning: Redirect Packets To and From Any Client To Our DevicemarkopvNo ratings yet
- How To Use EttercapDocument18 pagesHow To Use EttercapmajeedsterNo ratings yet
- Lab 6 - StudentDocument24 pagesLab 6 - StudentsalwaNo ratings yet
- Network Security Lab ManualDocument71 pagesNetwork Security Lab ManualSankalp Balannavar100% (1)
- 3 NetworkSecurity LABManualDocument33 pages3 NetworkSecurity LABManualdahiyalkNo ratings yet
- Lab Experiment #08 - Network & Host Detection ScansDocument3 pagesLab Experiment #08 - Network & Host Detection ScansAnoop DasNo ratings yet
- Operation Sheet 3.1: Man-In-The-Middle Attack Using EttercapDocument19 pagesOperation Sheet 3.1: Man-In-The-Middle Attack Using Ettercapኣስፋ ሙሉNo ratings yet
- Lab 5Document4 pagesLab 5Derick cheruyotNo ratings yet
- Man-In-The-Middle Attack Using Ettercap: Group 4: Linh, Manish, Mario and MeiDocument37 pagesMan-In-The-Middle Attack Using Ettercap: Group 4: Linh, Manish, Mario and Meiismail oualidNo ratings yet
- 35 Resource - Network Pentesting - Post Connection AttacksDocument20 pages35 Resource - Network Pentesting - Post Connection AttacksPetreaca MihaiNo ratings yet
- Arp Spoofing Windows PDFDocument0 pagesArp Spoofing Windows PDFalsamixersNo ratings yet
- Attacking Metasploitable2 VM Server Cameron WDocument20 pagesAttacking Metasploitable2 VM Server Cameron Wapi-502019278No ratings yet
- IP Address and Port ScanningDocument4 pagesIP Address and Port Scanningreddy ramya sri ghantasalaNo ratings yet
- Top 32 Nmap Command Examples For SysNetwork AdminsDocument16 pagesTop 32 Nmap Command Examples For SysNetwork AdminswizunuNo ratings yet
- NetwoxDocument4 pagesNetwoxbhikkhusirinNo ratings yet
- 7 CNDocument11 pages7 CNAdfar RashidNo ratings yet
- Enumeration Lab 4.1: Services Enumeration Using Nmap: StepsDocument7 pagesEnumeration Lab 4.1: Services Enumeration Using Nmap: StepsJoel JohnNo ratings yet
- How To Use Ettercap - KaliTutDocument21 pagesHow To Use Ettercap - KaliTutمحمد القحطانيNo ratings yet
- Module 6Document13 pagesModule 6Apurva KeskarNo ratings yet
- Lab 1Document2 pagesLab 1MahlikBrown100% (4)
- Lab 13Document4 pagesLab 13Сейфолла БаяндыNo ratings yet
- Wireless PDFDocument25 pagesWireless PDFBhuvneshwar VishwakarmaNo ratings yet
- VAPT Mooc Course NotesDocument10 pagesVAPT Mooc Course NotesFatema TahaNo ratings yet
- Learning Nmap: The Basics: Rajesh Deodhar How-Tos Tools / Apps 1 CommentDocument5 pagesLearning Nmap: The Basics: Rajesh Deodhar How-Tos Tools / Apps 1 Commentksenthil77No ratings yet
- Information and Network Security Lab: Lab Mannual FOR VII SEMESTER Computer Science & EngineeringDocument30 pagesInformation and Network Security Lab: Lab Mannual FOR VII SEMESTER Computer Science & EngineeringAnitha McNo ratings yet
- Network Security LAB Manual For DiplomaDocument31 pagesNetwork Security LAB Manual For DiplomaIrshad Khan50% (2)
- Lab 2 Scanning NetworksDocument143 pagesLab 2 Scanning Networksfawas hamdiNo ratings yet
- IT20232504Document14 pagesIT20232504Thilin ThungeeshaNo ratings yet
- 3.3.1.9 Lab - Detecting Threats and VulnerabilitiesDocument5 pages3.3.1.9 Lab - Detecting Threats and Vulnerabilitieskarenozelleb88No ratings yet
- Practice Exercises 4Document2 pagesPractice Exercises 4Tran TranNo ratings yet
- Lab - Detecting Threats and Vulnerabilities: ObjectivesDocument3 pagesLab - Detecting Threats and Vulnerabilities: ObjectivesObaid AnwerNo ratings yet
- Lab 06 TaskDocument2 pagesLab 06 TaskZuraiz QureshiNo ratings yet
- 4.2.2.5 Lab - Port Scanning An IoT DeviceDocument6 pages4.2.2.5 Lab - Port Scanning An IoT Devicemahin BhuiyanNo ratings yet
- NetworkSecurity LABManualDocument33 pagesNetworkSecurity LABManualvenkatdhanNo ratings yet
- CEH NotesDocument12 pagesCEH NotesshavadpesseNo ratings yet
- Lab 8 - Gaining Access of Metasploitable Machine Using Metasploit FrameworkDocument1 pageLab 8 - Gaining Access of Metasploitable Machine Using Metasploit FrameworkPratham PandeyNo ratings yet
- Lab IiiDocument14 pagesLab IiiKumar JiNo ratings yet
- Security & Ethical Hacking p2Document29 pagesSecurity & Ethical Hacking p2Vipin NarangNo ratings yet
- PES2UG22CS397CNLABWEEK1Document15 pagesPES2UG22CS397CNLABWEEK1Ashish GuptaNo ratings yet
- Packet Sniffer ImplementationDocument19 pagesPacket Sniffer ImplementationnassmahNo ratings yet
- ETHICAL HACKING GUIDE-Part 2: Comprehensive Guide to Ethical Hacking worldFrom EverandETHICAL HACKING GUIDE-Part 2: Comprehensive Guide to Ethical Hacking worldNo ratings yet
- Footprinting, Reconnaissance, Scanning and Enumeration Techniques of Computer NetworksFrom EverandFootprinting, Reconnaissance, Scanning and Enumeration Techniques of Computer NetworksNo ratings yet
- Lab 5 - DNS Enumeration and NetBIOS EnumerationDocument3 pagesLab 5 - DNS Enumeration and NetBIOS EnumerationPratham PandeyNo ratings yet
- Lab 8 - Gaining Access of Metasploitable Machine Using Metasploit FrameworkDocument1 pageLab 8 - Gaining Access of Metasploitable Machine Using Metasploit FrameworkPratham PandeyNo ratings yet
- Lab 4 - Scanning Using NMAPDocument2 pagesLab 4 - Scanning Using NMAPPratham PandeyNo ratings yet
- Lab 9 - Automated SQL Injection Using SQLMapDocument1 pageLab 9 - Automated SQL Injection Using SQLMapPratham PandeyNo ratings yet
- Lab 2 - Footprinting Using Metagoofil and MaltegoDocument2 pagesLab 2 - Footprinting Using Metagoofil and MaltegoPratham PandeyNo ratings yet
- Lab 1 - Footprinting Using NIKTO and TheharvesterDocument2 pagesLab 1 - Footprinting Using NIKTO and TheharvesterPratham PandeyNo ratings yet
- Lab 7 - Vulnerability Assessment - NessusDocument1 pageLab 7 - Vulnerability Assessment - NessusPratham PandeyNo ratings yet
- Lab 3 - Google HackingDocument1 pageLab 3 - Google HackingPratham PandeyNo ratings yet
- Ethics in Eng Lec1 F2012Document58 pagesEthics in Eng Lec1 F2012AchuNo ratings yet
- 1-Unit Introduction To Human Values & Ethics Course Session 1Document17 pages1-Unit Introduction To Human Values & Ethics Course Session 1Pratham PandeyNo ratings yet
- 1-Unit Exploring The Self Session-2Document44 pages1-Unit Exploring The Self Session-2Pratham PandeyNo ratings yet