Professional Documents
Culture Documents
LGI SetUp
Uploaded by
Lakshmanan KuppanCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
LGI SetUp
Uploaded by
Lakshmanan KuppanCopyright:
Available Formats
1
LGI SetUp
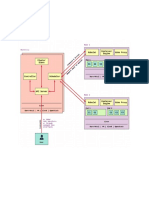
Fig: LGI Test Bed.
Test Bed Description:
Objective:
Test Bed diagram demonstrates the PoC to develop the Test Environment as well simulate the
Customer infrastructure within where the test cases of SDN controllers will be executed.
Accomplishment:
Both, the development of Test environment as well as the simulation of Customer infrastructure like
CSR – in particular the DHCP servers, is simulated using the infamous virtualization concept of Linux
Kernel - Linux Namespace, using which Linux Containers are created.
Linux Containers:
is created by isolating required Linux namespace(s) and thereby allowing the applications to execute
in these isolated namespaces.
In our context, most of the containers are created by isolating the Linux Network Namespace,
meaning isolating a separate network stack - consequence of which all the applications executing in
this namespace will be using separate network stack – in particular separate TCP/IP stack which will
be different from the host’s Network stack.
TEL Confidential LGI Setup Prabhunath G
2
This network stack will have its own virtual network interface and with its own unique IP address
separated from the host network interface and host IP address.
For a lay man, it gives the impression of the separate host, because a host in a networked
environment is uniquely identified through IP address.
A network application like sshd running on the newly created container with a separate network
stack can be used to login from the remote host.
Now, a user working remotely can access this host machine with 2 IP addresses, one with the host’s
IP address and other with the container’s IP address.
Stats: We can create 100s of Linux containers with Linux Network Namespace isolation, each having
its own IP address and can run sshd server on all the 100s of containers. This means I can simulate
100s of hosts in a decent (dual core processor and 4 GB RAM) hardware configuration of single host
machine.
This is the profundity of Linux Namespace.
Anything in this world, simpler in its design and usage, profound in its application, will become
popular.
So, is the idea of Linux Namespace and its profound application - Linux Containers, which we are
using in our Test Setup.
Abstract:
With this we are convinced that we will see the Linux containers with isolated Linux network
namespace as separate hosts.
We will create 2 sets of 4 + 1 containers each set configured to be in a separate collision domain,
a.k.a vlans, say vlan 10 and vlan 20. 1 container in each vlan will be running dhcp server to provide IP
address dynamically to all the other containers within that vlan.
Then Test Engineers will be logging into the containers to execute test cases.
The whole effort and exercise in this document is to do the following
1. Demonstrate the creation of Linux containers within two GNU/Linux host machines.
2. Group them into separate vlans,
3. Execute dhcp server in one container of each vlan.
4. Allow the containers within a vlan to dynamically fetch IP address from its corresponding
DHCP servers executing in the same vlan
5. Allow the users to log in to the containers from the host machine to execute testcases.
Detailed Description:
This test bed consists of both physical as well as virtual components. To be more specific there are
less number of physical components and more number of virtual components.
To begin with let me introduce to the reader, the physical and virtual components in this Test Bed.
Physical Components in this setup:
1. GNU/Linux of Ubuntu 16.04 64-bit version is used on Host machines (Desktops or Laptops).
(Here after this host machine is referred as Linux host)
a. Linux Host 1
b. Linux Host 2
c. Linux Host 3
2. Managed Switch
a. Layer 2 switch
3. Three Ethernet cables marked as blue line.
TEL Confidential LGI Setup Prabhunath G
3
Virtual Components in this Setup:
1. 2 OVS Bridges
2. 4 Linux Bridges
3. 20 virtual cables each having a pair of virtual interfaces.
4. 8 Linux containers with only Network Namespace isolation and shares other namespaces with
the host system.
5. 2 Linux containers (C10 and C20) with both Network Namespace and mount namespace
isolation and will share the other namespaces with the host system.
How to get Physical Components:
With the prior approval of the Manager or domain head, physical components must be
procured from IT
Inter-Connecting Physical Components:
1. Physical interface enp1s0 of Linux Host 1 is connected to the port 1 of the Managed Switch
2. Physical interface enp7s0 of Linux Host 2 is connected to the port 2 of the Managed Switch
3. Physical interface enp1s0 of Linux Host 3 is connected to the port 11 of the Managed Switch
How to get Virtual Components:
Unlike Physical Components Virtual components cannot be procured, but, must be created using
tools provided by the OS distributor, in this case Ubuntu 16.04.
Before using the tools, let us peep through the software packages which provides the tools required
for our usage.
• iproute2 (contains ip utility)
• bridge-utils (Contains brctl utility)
• openvswitch-switch (Contains ovs-vsctl utility)
• net-tools (contains ifconfig utility)
• iputils-ping (Contains ping)
• isc-dhcp-client (Contains dhclient)
Creating Virtual Components
1. OVS bridge is created by using ovs-vsctl command
a. $ sudo ovs-vsctl add-br <bridge-name>
2. Linux bridge is created by using brctl command
a. $ sudo brctl addbr <bridge-name>
3. A virtual cable having a pair of virtual ports is created using ip command
a. $ sudo ip link add <veth-port1> type veth peer name <veth-port2>
4. Linux Containers with network namespace isolation is created using ip command
a. $ sudo ip netns add <container name>
5. Linux Containers with both network namespace isolation and mount namespace
isolation is created by a Docker
a. Please find below the steps involved in installing docker and launching docker
container with dhcp package.
TEL Confidential LGI Setup Prabhunath G
4
Interconnecting Virtual components
Interconnecting virtual components is all about plugging the virtual ports to the Linux bridge or ovs
bridge or Linux containers.
1. Connecting a port to the ovs bridge is accomplished using ovs-vsctl command
a. $ ovs-vsctl add-port <bridge name> <port no.>
2. Connecting a port to the Linux Bridge is accomplished using brctl command
a. $ brctl addif <bridge name> <port no.>
3. Connecting a port to the Linux container is accomplished using ip command
a. $ ip link set <veth port> netns <container name>
Before we go to the details of wiring the virtual network components, let us understand the role of
the physical and virtual components
1. Linux Hosts: To house the virtual hosts named Linux containers and to house the virtual
network elements like Linux Bridges and OVS Bridges.
2. Managed Switch: To interconnect the two hosts and to allow vlan traffic from one host to
the other host. Also, it aids in interconnecting the Management host to the Two linux hosts
housing the Linux Containers.
3. Linux Bridges: To logically separate the Linux Containers into vlans
4. OVS Bridges: To technically separate the Linux Containers into vlans.
5. Pair of virtual ports: Used to wire the virtual network elements.
Setting up Virtual Network components on Linux Host 1
1. Create 1 OVS-bridge named br0
2. Create 2 Linux Bridges named br1 and br2
3. Create 4 Linux Containers named CR11, CR12, CR21 and CR22
4. Create 4 virtual cables each having a pair of virtual ports to interconnect Containers and
Linux Bridges. {(v100,v101), (v102,v103), (v200,v201), (v202,v203)}
5. Create 2 virtual cables each having a pair of virtual ports to interconnect Linux Bridges and
OVS-Bridge. {(veth0, veth1), (veth2, veth3)}
6. Create 3 virtual cables each having a pair of virtual ports to interconnect OVS-Bridge and
Linux Host or Global NameSpace. {(v0,v1), (v2,v3), (v4,v5)}
7. Configure ports {v2, veth0} as vlan10 access ports
8. Configure ports {v4, veth2} as vlan20 access ports
9. Configure ports{v1} as vlan 1 access ports
10. Configure the phy port enp1s0 as trunk port carrying vlan1, vlan10 and vlan20 tagged frames
Sequence of commands to execute the above 10 steps is described in the script file
host_1_setup_1.sh. Also sequence of commands to undo the above 10 steps is described in the
script file host_1_unset.1.sh
Setting up Virtual Network components on Linux Host 2
1. Creating 1 OVS-bridge named br0
2. Creating 2 Linux Bridges named br1 and br2
3. Create 2 Linux Containers named C10 and C11 hosting DHCP servers.
4. Create 4 Linux Containers named CR13, CR14, CR23 and CR24
5. Create 4 virtual cables each having a pair of virtual ports to interconnect Containers and
Linux Bridges. {(v104, v105), (v106, v107), (v204, v205), (v206, v207)}
TEL Confidential LGI Setup Prabhunath G
5
6. Creating 2 virtual cables each having a pair of virtual ports to interconnect 2 containers
hosting DHCP containers and OVS-Bridge. {(v300, v301), (v302, v303)}
7. Creating 2 virtual cables each having a pair of virtual ports to interconnect Linux Bridges and
OVS-Bridge. {(veth10, veth11), (veth12, veth13)}
8. Creating 3 virtual cables each having a pair of virtual ports to interconnect OVS-Bridge and
Linux Host or Global NameSpace. {(v10, v11), (v12,v13), (v14,v15)}
9. Configure ports {v12, veth10, v300} as vlan10 access ports
10. Configure ports {v14, veth12, v302} as vlan20 access ports
11. Configure ports{v1} as vlan 10 access ports
12. Configure the phy port enp7s0 as trunk port carrying vlan1, vlan10 and vlan20 tagged frames
Sequence of commands to execute the above 10 steps is described in the script file
host_2_setup_1.sh and host_2_setup_2.sh. Also sequence of commands to undo the above 10 steps
is described in the script file host_2_unset.1.sh and host_2_unset.2.sh
Configuration of Static IP addresses
It is essential to configure static IP addresses for few interfaces
1. Configuring Management IP addresses
a. 172.16.1.1 on phy interface enp2s0 on Linux host 3
b. 172.16.1.10 on virtual interface v1 on Linux host 1
c. 172.16.1.20 on virtual interface v11 on Linux host 2
2. Configuring IP addresses on Linux Containers DHCP Servers
a. 192.168.1.1 on virtual interface eth0 on Linux Container C10
b. 192.168.2.1 on virtual interface eth0 on Linux Container C20
With this the setup is ready for us to launch the applications in respective containers.
Launching of Applications
1. Launch DHCP server (/usr/bin/dhcpd) application in Linux container C10
2. Launch DHCP server (/usr/bin/dhcpd) application in Linux container C11
3. Execute dhcp client on all the containers except C10 and C11 to dynamically obtain IP
addresses for their virtual interface eth0
4. Execute ssh server (/usr/sbin/sshd) on all the containers except C10 and C11
Logging into the Containers
1. Note down the the IP addresses all the containers before logging in.
2. Logging into the container through ssh command (ssh username@ip-address)
Disclaimer:
Every time a virtual interface is created and associated to the Container, Linux gives
a different MAC address. Hence DHCP server will assign a new IP address. If there is
frequent act of creating and deleting the Containers, there is high chance of depleting the IP
address from the DHCP server. Hence it is recommended that the lease time of the IP
address assigned by the DHCP server should be as less as possible and the leasing
information should be
TEL Confidential LGI Setup Prabhunath G
6
Diagnostics
Following are the few diagnostics which will help you to diagnose the anatomy and physiology of
the Test bed
1. $ ip a show (Gives the statistics about all the bridge ports, virtual ports and physical ports)
2. $ sudo ovs-vsctl show ( Gives the statistics about all the ovs-bridges and its ports)
3. $ ping <ip-address> ( Helps in figuring out the connectivity of the remote host)
4. $ sudo tcpdump -i <interface-name> (Captures the packets flowing through the interface
name)
Following are the steps involved in installing Docker and starting Docker container
1. Install Docker
$ curl https://get.docker.com > /tmp/install.sh
$ chmod a+x /tmp/install.sh
$ /tmp/install.sh
# Add the user to the docker group
$ sudo usermod -aG docker `echo $USER`
2. Load the Ubuntu's dhcp image in the form of tarball (The link is
supplied in the Reference Section)
$ docker load -i ubuntu_dhcpd.tar.gz
3. Verify the image in the local repository
$ docker images # You should see the image tagged dhcpd in
# the REPOSITORY ubuntu
4. Create docker container named dhcp-server-1 with the above listed
image
$ docker run -it --name=dhcp-server-1 --net=none ubuntu:dhcpd
/bin/bash
5. Create docker container named dhcp-server-2 with the above listed
image
$ docker run -it --name=dhcp-server-2 --net=none ubuntu:dhcpd
/bin/bash
6. Following configuration has to be done within the container
7. Create a file /var/lib/dhcp/dhcpd.leases in both the containers
# touch /var/lib/dhcp/dhcpd.leases
8. Edit the dhcp configuration file /etc/dhcp/dhcpd.conf in both the
containers to edit the pool profile. A sample pool profile named
LGI is already present in the configuration
TEL Confidential LGI Setup Prabhunath G
7
Reference:
1. Here is the link to download ubuntu_dhcpd.tar.gz
https://tataelxsi-
my.sharepoint.com/personal/prabhunath_g_tataelxsi_co_in/_layouts/15/
guestaccess.aspx?guestaccesstoken=o21LgDstoQwd4P100EiBq%2fwxHWE3HTFd
%2bugENiwbba0%3d&docid=2_103a082df9f454ed0a585a40e7f84b5a5&rev=1
TEL Confidential LGI Setup Prabhunath G
You might also like
- HhmKIe9pRWaZiiHvaUVm0Q NFV-workshop1Document3 pagesHhmKIe9pRWaZiiHvaUVm0Q NFV-workshop1rabulNo ratings yet
- Lvs TutorialDocument32 pagesLvs TutorialRajshekar ShivanagoudarNo ratings yet
- Mini NetDocument8 pagesMini NetDung Viet NgoNo ratings yet
- Kubernetes Flannel Networking. This Article Explains HowDocument8 pagesKubernetes Flannel Networking. This Article Explains HowOpenSource DevelopmentNo ratings yet
- Lesson 8 DNS Networking CoreDNS and CNIDocument54 pagesLesson 8 DNS Networking CoreDNS and CNIHamdi GharsalliNo ratings yet
- Develop Ingelligence - Docker Docker NetworkingDocument7 pagesDevelop Ingelligence - Docker Docker Networkingsaphana9800No ratings yet
- Kubernets NetworkingDocument30 pagesKubernets NetworkingSenthilkumar MuthusamyNo ratings yet
- Tutorial Mininet POXDocument8 pagesTutorial Mininet POXPaolo FrankoneriNo ratings yet
- SDN Controller and Implementation PDFDocument63 pagesSDN Controller and Implementation PDFhadje benilhaNo ratings yet
- LXC Conf ParamsDocument52 pagesLXC Conf Paramsxeyog51371No ratings yet
- Diving Deep Into Kubernetes Networking 1667510323Document71 pagesDiving Deep Into Kubernetes Networking 1667510323Stoyan IlievNo ratings yet
- CSE3035-Principles of Coud Computing Lab Assignment-4Document41 pagesCSE3035-Principles of Coud Computing Lab Assignment-4ShadowNo ratings yet
- Making Docker and Consul Get Along - Zendesk Engineering - MediumDocument11 pagesMaking Docker and Consul Get Along - Zendesk Engineering - MediumasdfsdfsdfdsfNo ratings yet
- Building Your Own Call of Duty 2 Linux Dedicated ServerDocument4 pagesBuilding Your Own Call of Duty 2 Linux Dedicated ServerguidokrNo ratings yet
- VPN Lab: The Container VersionDocument12 pagesVPN Lab: The Container VersionAwabdeh 97No ratings yet
- DevOps Lab Assignment-2Document3 pagesDevOps Lab Assignment-2sakshi gaikwadNo ratings yet
- How To Configure Two Node High Availability Cluster On RHELDocument18 pagesHow To Configure Two Node High Availability Cluster On RHELslides courseNo ratings yet
- Networking in Kubernetes-2-2-3Document23 pagesNetworking in Kubernetes-2-2-3m.asif.muzammilNo ratings yet
- Z/VM & Rhel KVM On Linuxone With Racf Implementation Services Project Planning & PreparationDocument5 pagesZ/VM & Rhel KVM On Linuxone With Racf Implementation Services Project Planning & PreparationVen NatNo ratings yet
- Kubernetes Networking: Marian Babik, Spyridon Trigazis CernDocument19 pagesKubernetes Networking: Marian Babik, Spyridon Trigazis CernArun SomashekarNo ratings yet
- Sample Exam Qs Config Netwks Srvrs Auth DNS PHP MariaDB iSCSI SMBDocument4 pagesSample Exam Qs Config Netwks Srvrs Auth DNS PHP MariaDB iSCSI SMBnodi.chad713No ratings yet
- Containers Kubernetes Helm Ingress 2018nov21Document97 pagesContainers Kubernetes Helm Ingress 2018nov21fqchinaNo ratings yet
- k8s PrimerDocument40 pagesk8s Primersunil kalvaNo ratings yet
- Configure High Availability Cluster in Centos 7 (Step by Step Guide)Document9 pagesConfigure High Availability Cluster in Centos 7 (Step by Step Guide)HamzaKhanNo ratings yet
- kubernetes orchestration toolDocument61 pageskubernetes orchestration toolSree Harsha Ananda RaoNo ratings yet
- VMware NSX T Data Center - 4Document60 pagesVMware NSX T Data Center - 4Yohan De SilvaNo ratings yet
- Kubernetes For World PDFDocument9 pagesKubernetes For World PDFcumar2014No ratings yet
- Docker ContainersDocument22 pagesDocker ContainersWafa KhalidNo ratings yet
- ACTION Lab HPC Install MannulDocument10 pagesACTION Lab HPC Install MannulMandoiu StefanNo ratings yet
- KubernatiesDocument36 pagesKubernatiesAslam AnsariNo ratings yet
- 12 13 14 15 16Document34 pages12 13 14 15 16maira buttNo ratings yet
- VMware NSX T Data Center - 3Document83 pagesVMware NSX T Data Center - 3Yohan De SilvaNo ratings yet
- Kubernetes NetworkingDocument91 pagesKubernetes NetworkingDodo winyNo ratings yet
- Kubernetes Simple DocumentDocument22 pagesKubernetes Simple Documentafzal100% (1)
- Creating and Using Docker Like BossDocument39 pagesCreating and Using Docker Like BossabhinavsrivastavNo ratings yet
- Free Lab Friday - Part 6 Implementing IP Addressing SchemesDocument3 pagesFree Lab Friday - Part 6 Implementing IP Addressing SchemeshoadiNo ratings yet
- Technical Assessment For Deployment Support Engineer - Hery MunanzarDocument6 pagesTechnical Assessment For Deployment Support Engineer - Hery MunanzarMuhammad HafizNo ratings yet
- KubernetesDocument2 pagesKubernetesRajesh ChaudharyNo ratings yet
- Pra-Test Modul DDocument11 pagesPra-Test Modul Dyogi pranataNo ratings yet
- Kubernetes Flannel NetworkDocument6 pagesKubernetes Flannel Networksuhashis acharyaNo ratings yet
- Kubernetes in the Docker platformDocument23 pagesKubernetes in the Docker platformazureNo ratings yet
- LKSN2023 ITNSA MC Actual enDocument10 pagesLKSN2023 ITNSA MC Actual enRizan Abki C.No ratings yet
- Install LXC On CentOSDocument3 pagesInstall LXC On CentOSgplgpNo ratings yet
- Ultra Monkey AsteriskDocument11 pagesUltra Monkey AsteriskHenryNo ratings yet
- Docker 21.10.22Document50 pagesDocker 21.10.2220C134-SRIKRISHNA MNo ratings yet
- OS-Lab-Manual (Final Print)Document158 pagesOS-Lab-Manual (Final Print)Faseeh Ahmad0% (1)
- Troubleshooting Network IssuesDocument3 pagesTroubleshooting Network IssuescarlosNo ratings yet
- Docker Networking With Linux: Guillaume Urvoy-KellerDocument58 pagesDocker Networking With Linux: Guillaume Urvoy-KellerSafidy RazafindrabenjaminaNo ratings yet
- Building Your Own Call of Duty 4: Modern Warfare Linux Dedicated ServerDocument9 pagesBuilding Your Own Call of Duty 4: Modern Warfare Linux Dedicated Serverguidokr100% (2)
- DockerDocument62 pagesDockerStephen YovanNo ratings yet
- VPC Lab Configuration and Hands-OnDocument23 pagesVPC Lab Configuration and Hands-Onhanuman challisaNo ratings yet
- Build your own Call of Duty 2 Linux Dedicated ServerDocument4 pagesBuild your own Call of Duty 2 Linux Dedicated ServerVedran GavranNo ratings yet
- Kubernetes Networking Made Easy With Open Vswitch and OpenFlow Péter Megyesi LeanNet Ltd.Document84 pagesKubernetes Networking Made Easy With Open Vswitch and OpenFlow Péter Megyesi LeanNet Ltd.M_ahmed81No ratings yet
- Manual Calculadora IpDocument7 pagesManual Calculadora IpGeorge DiazNo ratings yet
- Practical Guide RacDocument63 pagesPractical Guide RacJames AndersonNo ratings yet
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkFrom EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo ratings yet
- Set Up Your Own IPsec VPN, OpenVPN and WireGuard Server: Build Your Own VPNFrom EverandSet Up Your Own IPsec VPN, OpenVPN and WireGuard Server: Build Your Own VPNRating: 5 out of 5 stars5/5 (1)
- Netconf: in This ChapterDocument54 pagesNetconf: in This ChapterLakshmanan KuppanNo ratings yet
- Netconf: in This ChapterDocument54 pagesNetconf: in This ChapterLakshmanan KuppanNo ratings yet
- Casa To ARRIS Command Reference: For Commands Contained in The C100G LabDocument26 pagesCasa To ARRIS Command Reference: For Commands Contained in The C100G LabMarioArielGuerraNo ratings yet
- Authorization Form: Data Partner Easy NutsDocument2 pagesAuthorization Form: Data Partner Easy NutsLakshmanan KuppanNo ratings yet
- Python Cheat Sheet PDFDocument26 pagesPython Cheat Sheet PDFharishrnjic100% (2)
- Authorization Form: Data Partner Easy NutsDocument2 pagesAuthorization Form: Data Partner Easy NutsLakshmanan KuppanNo ratings yet
- Python Cheat Sheet PDFDocument26 pagesPython Cheat Sheet PDFharishrnjic100% (2)
- EVE Comm BOOK 1.09 2020 PDFDocument165 pagesEVE Comm BOOK 1.09 2020 PDFKevin JaraNo ratings yet
- Casa To ARRIS Command Reference: For Commands Contained in The C100G LabDocument26 pagesCasa To ARRIS Command Reference: For Commands Contained in The C100G LabMarioArielGuerraNo ratings yet
- c181 S2i PingDocument1 pagec181 S2i PingLakshmanan KuppanNo ratings yet
- Open Source Tool Tool Name CategoryDocument5 pagesOpen Source Tool Tool Name CategoryLakshmanan KuppanNo ratings yet
- List of JIRA issues and details from multiple vendorsDocument2 pagesList of JIRA issues and details from multiple vendorsLakshmanan KuppanNo ratings yet
- IPAddressDocument1 pageIPAddressLakshmanan KuppanNo ratings yet
- User details report with names, IDs and contact infoDocument4 pagesUser details report with names, IDs and contact infoLakshmanan KuppanNo ratings yet
- Client C141 S2S IPERF CUSTOMDocument2 pagesClient C141 S2S IPERF CUSTOMLakshmanan KuppanNo ratings yet
- Server C241 S2S IPERF CUSTOMDocument1 pageServer C241 S2S IPERF CUSTOMLakshmanan KuppanNo ratings yet
- C181 S2i PingDocument1 pageC181 S2i PingLakshmanan KuppanNo ratings yet
- 1.txt Test Lakshmanan Tsts SDFKDSFDSSD 1 SDDocument1 page1.txt Test Lakshmanan Tsts SDFKDSFDSSD 1 SDLakshmanan KuppanNo ratings yet
- Client C11 S2IDocument1 pageClient C11 S2ILakshmanan KuppanNo ratings yet
- 1.txt Show Service Group Show Interface Docsis-Mac Show Interface Ofdma Show Interface UpstreaDocument1 page1.txt Show Service Group Show Interface Docsis-Mac Show Interface Ofdma Show Interface UpstreaLakshmanan KuppanNo ratings yet
- Python Cheat Sheet PDFDocument26 pagesPython Cheat Sheet PDFharishrnjic100% (2)
- c181 S2i PingDocument1 pagec181 S2i PingLakshmanan KuppanNo ratings yet
- 1.txt Test Lakshmanan Tsts SDFKDSFDSSD 1 SdasdfdssdfdsDocument1 page1.txt Test Lakshmanan Tsts SDFKDSFDSSD 1 SdasdfdssdfdsLakshmanan KuppanNo ratings yet
- 789Document1 page789Lakshmanan KuppanNo ratings yet
- 1.txt Test Lakshmanan Tsts SDFKDSFDSSD 1 Sdasdfdssdfds SSDFDGHH FdsDocument1 page1.txt Test Lakshmanan Tsts SDFKDSFDSSD 1 Sdasdfdssdfds SSDFDGHH FdsLakshmanan KuppanNo ratings yet
- 567Document1 page567Lakshmanan KuppanNo ratings yet
- Lakshmanan TestDocument1 pageLakshmanan TestLakshmanan KuppanNo ratings yet
- Lakshmanan TestDocument1 pageLakshmanan TestLakshmanan KuppanNo ratings yet
- 1.txt TestDocument1 page1.txt TestLakshmanan KuppanNo ratings yet
- Update Manjaro - Buscar Con GoogleDocument9 pagesUpdate Manjaro - Buscar Con GoogleHéctor PérezNo ratings yet
- Linux Operating System Components and ServicesDocument36 pagesLinux Operating System Components and ServicesAnish A RNo ratings yet
- Junos Containerized Routing Protocol Daemon: Product OverviewDocument3 pagesJunos Containerized Routing Protocol Daemon: Product Overviewchandrashekar_ganesanNo ratings yet
- Join Linux to Active Directory with Samba 3Document3 pagesJoin Linux to Active Directory with Samba 3Diego FiliceNo ratings yet
- RHCSA Course DatasheetDocument1 pageRHCSA Course DatasheetsalmanpkplusNo ratings yet
- CamScanner Document ScansDocument191 pagesCamScanner Document ScansIzabela CătălinaNo ratings yet
- IT Project Manager / Web Developer / Pentester: Page 1 of 5Document5 pagesIT Project Manager / Web Developer / Pentester: Page 1 of 5Lili SopiandiNo ratings yet
- Kaspersky Security for Virtualization 5.2 Light Agent DocumentationDocument810 pagesKaspersky Security for Virtualization 5.2 Light Agent DocumentationLam Khê PhạmNo ratings yet
- Presentation On Utility ProgramsDocument21 pagesPresentation On Utility ProgramsAiman Fatima100% (2)
- Freebeer-1 2Document189 pagesFreebeer-1 2Neil EspinozaNo ratings yet
- Symantec Scan Engine 5.1Document14 pagesSymantec Scan Engine 5.1Farhan JavaidNo ratings yet
- تفسیر حکمت القران اتم جلدDocument604 pagesتفسیر حکمت القران اتم جلدکتابخانه آشنا کتابتونNo ratings yet
- 15 Command Line Tools To Monitor Linux Performance PDFDocument25 pages15 Command Line Tools To Monitor Linux Performance PDFVictor L Wamukoya100% (1)
- Red Hat Enterprise Virtualization-3.3-User Portal Guide-En-USDocument33 pagesRed Hat Enterprise Virtualization-3.3-User Portal Guide-En-USRakesh SinghNo ratings yet
- Red Hat Satellite-6.4-Quick Start Guide-en-USDocument32 pagesRed Hat Satellite-6.4-Quick Start Guide-en-USytdscdzngysygubzwsNo ratings yet
- Why CDocument9 pagesWhy CMuhammedNo ratings yet
- GROMACS Installation and Simulation GuideDocument10 pagesGROMACS Installation and Simulation GuideKaka TsaiNo ratings yet
- Operating Systems Comparison and FunctionalityDocument17 pagesOperating Systems Comparison and Functionalityabhinav yadavNo ratings yet
- XAMPP Memcache ExtensionDocument2 pagesXAMPP Memcache ExtensionKrisnaNo ratings yet
- ProCAST 2021-5 InstallationGuideDocument34 pagesProCAST 2021-5 InstallationGuideMariano PinheiroNo ratings yet
- Raspberry Pi IP Camera Surveillance SystemDocument40 pagesRaspberry Pi IP Camera Surveillance SystemMANISH TRIPATHINo ratings yet
- E Mail Marketing With OpenEMMDocument22 pagesE Mail Marketing With OpenEMMnomanNo ratings yet
- C PDFDocument151 pagesC PDFJohn Michael ParcoNo ratings yet
- IBM System Storage DS8000 - A QuickDocument10 pagesIBM System Storage DS8000 - A Quickmuruggan_aNo ratings yet
- Install Builder UserguideDocument231 pagesInstall Builder UserguideRodrigo Axl OlivaNo ratings yet
- Operating System: Operating Systems: Internals and Design PrinciplesDocument86 pagesOperating System: Operating Systems: Internals and Design PrinciplesJeremiah FerrerNo ratings yet
- Mount points and filesystemsDocument5 pagesMount points and filesystemsJedar DoskiNo ratings yet
- Curriculum - Programming and Systems Administration AssistantDocument36 pagesCurriculum - Programming and Systems Administration AssistantSayantan MajhiNo ratings yet
- AppStudio - Workshop - UserDocument80 pagesAppStudio - Workshop - UserzamanNo ratings yet
- Ansible Playbook Bundle Development GuideDocument59 pagesAnsible Playbook Bundle Development GuidePoola Satish KumarNo ratings yet