Professional Documents
Culture Documents
Kubernetes Flannel Networking. This Article Explains How
Uploaded by
OpenSource DevelopmentOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Kubernetes Flannel Networking. This Article Explains How
Uploaded by
OpenSource DevelopmentCopyright:
Available Formats
Firefox https://blog.laputa.
io/kubernetes-flannel-networking-6a1cb1f8ec7c
This article explains how flannel network works in Kubernetes
Kubernetes is an excellent tool for managing containerized applications at scale. But as
you may know, working with kubernetes is not an easy road, especially the backend
networking implementation. I have met many problems in networking and it cost me
much time to figure out how it works.
In this article, I want to use the most simple implementation as an example, to explain
kubernetes networking works. Hope this article can help those people like me who are
studying kubernetes as a beginner.
Kubernetes networking model
The following graph shows a simple image of a kubernetes cluster:
Pods in Kubernetes
Kubernetes manages a cluster of Linux machines(might be cloud VM like AWS EC2 or
physical servers), on each host machine, kubernetes runs any number of Pods, in each
Pod there can be any number of containers. User’s application is running in one of
those containers.
For kubernetes, Pod is the minimum management unit, and all containers inside one
Pod shares the same network namespace, which means they have same network
interface and can connect each other by using localhost
1 von 8 28.11.2021, 00:56
Firefox https://blog.laputa.io/kubernetes-flannel-networking-6a1cb1f8ec7c
The official documentation says kubernetes networking model requires:
• all containers can communicate with all other containers without NAT
• all nodes can communicate with all containers (and vice-versa) without NAT
• the IP that a container sees itself as is the same IP that others see it as
We can replace all containers to Pods in above requirements, as containers share with
Pod network.
Basically it means all Pods should be able to freely communicate with any other Pods in
the cluster, even they are in different Hosts, and they recognized each other with their
own IP address, just as the underlying Host does not exists. Also the Host should also
be able to communicate with any Pod with it’s own IP address, without any address
translation.
Kubernetes does not provide any default network implementation, rather it only
defines the model and leaves to other tools to implement it. There are many
implementations nowadays, flannel is one of them and one of the simplest. In the
following sections, I will explain the Flannel’s UDP mode impelmentations.
The Overlay Network
Flannel is created by CoreOS for Kubernetes networking, it also can be used as a
general software defined network solution for other purpose.
To achieve kubernetes' network requirements, flannel’s idea is simple: create another
flat network which runs above the host network, this is the so-called overlay network.
All containers(Pod) will be assigned one ip address in this overlay network, they
communicate with each other by calling each other’s ip address directly.
To help explain, I use a small testing kubernetes cluster on AWS, there are 3 Kubernetes
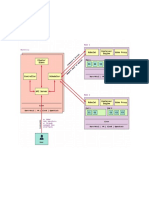
nodes in the cluster. Here is how the network looks like:
2 von 8 28.11.2021, 00:56
Firefox https://blog.laputa.io/kubernetes-flannel-networking-6a1cb1f8ec7c
Flannel overlay network
There are three networks in this cluster:
AWS VPC network: all instances are in one VPC subnet 172.20.32.0/19 . They have been
assigned ip addresses in this range, all hosts can connect to each other because they are
in same LAN.
Flannel overlay network: flannel has created another network 100.96.0.0/16 , it’s a
bigger network which can hold 2¹⁶(65536) addresses, and it’s across all kubernetes
nodes, each pod will be assigned one address in this range, later we will see how
flannel achieves this.
In-Host docker network: inside each host, flannel assigned a 100.96.x.0/24 network to
all pods in this host, it can hold 2⁸(256) addresses. The docker bridge interface docker0
will use this network to create new containers.
By this design, each container has it’s own IP address, all fall into the overlay subnet
100.96.0.0/16 . The containers inside the same host can communicate with each other
by the docker bridge docker0 , which is simple so I will skip in this article. To
communicate across hosts with other containers in the overlay network, flannel uses
kernel route table and UDP encapsulation to achieve it, the following sections explain
this.
Cross host container communication
Assume the container(let’s call it container-1) in Node 1 which has the IP address
3 von 8 28.11.2021, 00:56
Firefox https://blog.laputa.io/kubernetes-flannel-networking-6a1cb1f8ec7c
100.96.1.2 wants to connect to the container(let’s call it container-2) in Node 2 with
the IP address 100.96.2.3 , let’s see how the overlay network enables the packets
passing.
Cross host communication
First container-1 creates an IP packet with src: 100.96.1.2 -> dst: 100.96.2.3 , the
packet will go to the docker0 bridge as it’s the container’s gateway.
In each host, flannel runs a daemon process called flanneld , it creates some route
rules in kernel’s route table, here is what Node 1’s route table looks like:
admin@ip-172-20-33-102:~$ ip route
default via 172.20.32.1 dev eth0
100.96.0.0/16 dev flannel0 proto kernel scope link src 100.96.1.0
100.96.1.0/24 dev docker0 proto kernel scope link src 100.96.1.1
172.20.32.0/19 dev eth0 proto kernel scope link src 172.20.33.102
As we can see, the packet’s destination address 100.96.2.3 falls in the bigger overlay
network 100.96.0.0/16 , so it matches the second rule, now kernel knows it should send
the packet to flannel0 .
flannel0 is a TUN device also created by our flanneld daemon process, TUN is a
software interface implemented in linux kernel, it can pass raw ip packet between user
4 von 8 28.11.2021, 00:56
Firefox https://blog.laputa.io/kubernetes-flannel-networking-6a1cb1f8ec7c
program and the kernel. It works in two directions:
• when it write IP packet to the flannel0 device, the packet will be send to kernel
directly, and kernel will route the packet according to its route table
• when an IP packet arrives to the kernel, and the route tables says it should be
routed to flannel0 device, kernel will send the packet directly to the process which
created this device, which is the flanneld daemon process
As kernel sends packet to the TUN device, it will directly goes to the flanneld process,
it sees the destination address is 100.96.2.3 , though we can see from the diagram that
this address belongs to a container who runs on Node 2, but how does flanneld know
this?
It so happens that flannel stores some information in a key-value storage service called
etcd, if you know kubernetes you should not be suprised. In flannel case, we can just
think it as a general key-value store.
flannel stores the subnet to host mapping information into the etcd service, we can see
it by using etcdctl command:
admin@ip-172-20-33-102:~$ etcdctl ls /coreos.com/network/subnets
/coreos.com/network/subnets/100.96.1.0-24
/coreos.com/network/subnets/100.96.2.0-24
/coreos.com/network/subnets/100.96.3.0-24
admin@ip-172-20-33-102:~$ etcdctl get /coreos.com/network/subnets
/100.96.2.0-24
{"PublicIP":"172.20.54.98"}
so each flanneld process queries etcd to know each subnet belongs to which host, and
compares the destination ip address with all subnets key stored in etcd. In our case, the
address 100.96.2.3 will match the subnet 100.96.2.0-24 , and as we see the value
stored in this keys says the Node ip is 172.20.54.98 .
Now flanneld knows the destination address, it then wraps the original IP packet into
5 von 8 28.11.2021, 00:56
Firefox https://blog.laputa.io/kubernetes-flannel-networking-6a1cb1f8ec7c
a UDP packet, with it’s own host’s ip as source address, and the target host’s IP as
destination address. In each host, the flanneld process will listen on a default UDP
port :8285 . So it just need to set the UDP packet’s destination port to 8285 , and send it
on the wire.
After the UDP packet arrives at the destination host, the kernel’s IP stack will send the
packet to the flanneld process because that’s the user process who listens on UDP port
:8285 . Then flanneld will get the payload of the UDP packet, which is the original IP
packet generated by the originate container, it simply write this packet to the TUN
device flannel0 , then the packet will directly pass to kernel as that’s how TUN works.
Same as in Node 1, the route table will decide where this packet should go, let’s see
Node 2’s route table:
admin@ip-172-20-54-98:~$ ip route
default via 172.20.32.1 dev eth0
100.96.0.0/16 dev flannel0 proto kernel scope link src 100.96.2.0
100.96.2.0/24 dev docker0 proto kernel scope link src 100.96.2.1
172.20.32.0/19 dev eth0 proto kernel scope link src 172.20.54.98
the destination address of the IP packet is 100.96.2.3 , kernel will take the most precise
match, which is the third rule. The packet will be send to docker0 device. As docker0 is
a bridge device, and all containers in this host are connected to this bridge, the packet
will finnaly be seen and received by the destination container-2.
Finally our packet finished the one way pass to the target, when contianer-2 sends
packet back to container-1, the reverse route will work exactly the same way. That’s
how cross host container communication works.
Configuring with docker network
In the above explanation, we have missed one point. That’s how we configure docker to
use the smaller subnet like 100.96.x.0/24 ?
It happens that flanneld will write it’s subnet information into a file in the host:
6 von 8 28.11.2021, 00:56
Firefox https://blog.laputa.io/kubernetes-flannel-networking-6a1cb1f8ec7c
admin@ip-172-20-33-102:~$ cat /run/flannel/subnet.env
FLANNEL_NETWORK=100.96.0.0/16
FLANNEL_SUBNET=100.96.1.1/24
FLANNEL_MTU=8973
FLANNEL_IPMASQ=true
This information will be used to configure the docker daemon’s option, so docker can
use the FLANNEL_SUBNET as its bridge network, then the in-host container network will
work:
dockerd --bip=$FLANNEL_SUBNET --mtu=$FLANNEL_MTU
Packet copy and performance
The newer version of flannel does not recommend to use UDP encapsulation for
production, says it should be only used for debugging and testing purpose. One reason
is the performance.
Though the flannel0 TUN device provides a simple way to get and send packet through
the kernel, it has a performance penalty: the packet has to be copied back and forth
from the user space to kernel space:
packet copy
as the above, from the original container process send packet, it has to be copied 3
7 von 8 28.11.2021, 00:56
Firefox https://blog.laputa.io/kubernetes-flannel-networking-6a1cb1f8ec7c
times between user space and kernel space, this will increase network overhead in a
significant way, so you should avoid using UDP in production if you can.
Conclusion
Flannel is one of the simplest implementation of kubernetes network model. It uses the
existing docker bridge network and an extra Tun device with a daemon process to do
UDP encapsulation. I explained the details of the core part: cross host container
communication, and briefly mentioned the performance penalty. I hope this article
helps people to understand the basics of kuberentes networking, with this knowledge
you can start exploring the more interesting world of kubernetes networking, and
figure out many
Kubernetes advanced
Flannel implementations
Networking Docker like Calico, WeaveNet, Romana.
Container
References
https://coreos.com/blog/introducing-rudder.html
http://backreference.org/2010/03/26/tuntap-interface-tutorial/
About Write Help Legal
Get the Medium app
8 von 8 28.11.2021, 00:56
You might also like
- Kubernetes Flannel NetworkDocument6 pagesKubernetes Flannel Networksuhashis acharyaNo ratings yet
- Flannel Network KubernetesDocument6 pagesFlannel Network KubernetesDavid SofitaNo ratings yet
- LGI SetUpDocument7 pagesLGI SetUpLakshmanan KuppanNo ratings yet
- Diving Deep Into Kubernetes Networking 1667510323Document71 pagesDiving Deep Into Kubernetes Networking 1667510323Stoyan IlievNo ratings yet
- Docker Networking On Detail - ExamplesDocument35 pagesDocker Networking On Detail - ExamplesJuancaNo ratings yet
- Lvs TutorialDocument32 pagesLvs TutorialRajshekar ShivanagoudarNo ratings yet
- WWW Akadia Com Services Ora - Rac HTML PDFDocument20 pagesWWW Akadia Com Services Ora - Rac HTML PDFZakir HossenNo ratings yet
- HhmKIe9pRWaZiiHvaUVm0Q NFV-workshop1Document3 pagesHhmKIe9pRWaZiiHvaUVm0Q NFV-workshop1rabulNo ratings yet
- KubernetesDocument27 pagesKubernetesJason GomezNo ratings yet
- Kubernetes Notes 1708954446Document33 pagesKubernetes Notes 1708954446Satyanarayana SureNo ratings yet
- Kubernetes Networking Explained - IntroductionDocument13 pagesKubernetes Networking Explained - IntroductionRpl MarseilleNo ratings yet
- Tutorial Mininet POXDocument8 pagesTutorial Mininet POXPaolo FrankoneriNo ratings yet
- Develop Ingelligence - Docker Docker NetworkingDocument7 pagesDevelop Ingelligence - Docker Docker Networkingsaphana9800No ratings yet
- Making Docker and Consul Get Along - Zendesk Engineering - MediumDocument11 pagesMaking Docker and Consul Get Along - Zendesk Engineering - MediumasdfsdfsdfdsfNo ratings yet
- Promox 2Document101 pagesPromox 2Rodrigo PinzonNo ratings yet
- Containerizing Docker On Kubernetes !! - L..Document7 pagesContainerizing Docker On Kubernetes !! - L..Tej SharmaNo ratings yet
- What Is Docker NetworkingDocument6 pagesWhat Is Docker NetworkingBoris MamićNo ratings yet
- ProxmoxDocument27 pagesProxmoxjust4lmgameNo ratings yet
- Introduction To Docker - PACKT Books: Rajdeep Dua, The Author of The Book Learning DockerDocument4 pagesIntroduction To Docker - PACKT Books: Rajdeep Dua, The Author of The Book Learning DockerRahmi YıldızNo ratings yet
- Devops CIA 2 QB FinalDocument15 pagesDevops CIA 2 QB FinalLRG Govt. Arts College for Women TiruppurNo ratings yet
- ACTION Lab HPC Install MannulDocument10 pagesACTION Lab HPC Install MannulMandoiu StefanNo ratings yet
- Kubernetes Networking: Marian Babik, Spyridon Trigazis CernDocument19 pagesKubernetes Networking: Marian Babik, Spyridon Trigazis CernArun SomashekarNo ratings yet
- Kubernates Cluster On Centos 8Document28 pagesKubernates Cluster On Centos 8chandrashekar_ganesanNo ratings yet
- M5 - T-GCPFCI-B - Core Infrastructure v5.1.0 - ILTDocument27 pagesM5 - T-GCPFCI-B - Core Infrastructure v5.1.0 - ILTSandy LinNo ratings yet
- 38-Kubernetes Io Docs Concepts Services Networking Topology AwaDocument6 pages38-Kubernetes Io Docs Concepts Services Networking Topology AwaArmstrong NoriscaNo ratings yet
- Mininet ActivityDocument17 pagesMininet ActivitySanthosh MenonNo ratings yet
- k8s1 PDFDocument61 pagesk8s1 PDFSree Harsha Ananda RaoNo ratings yet
- No SDN KubernetesDocument6 pagesNo SDN KubernetesudNo ratings yet
- How To Configure Two Node High Availability Cluster On RHELDocument18 pagesHow To Configure Two Node High Availability Cluster On RHELslides courseNo ratings yet
- Network TroubleshootingDocument5 pagesNetwork Troubleshootingdandaniel3000No ratings yet
- Setting A Private CloudDocument15 pagesSetting A Private CloudVasanth RajNo ratings yet
- Mini NetDocument8 pagesMini NetDung Viet NgoNo ratings yet
- VPN Lab: The Container VersionDocument12 pagesVPN Lab: The Container VersionAwabdeh 97No ratings yet
- TP SDN-2022Document6 pagesTP SDN-2022Elhem MansourNo ratings yet
- GNS3 Bridge To ESXi Environment Using GNS3 v1.0Document6 pagesGNS3 Bridge To ESXi Environment Using GNS3 v1.0darrenNo ratings yet
- k8s PrimerDocument40 pagesk8s Primersunil kalvaNo ratings yet
- HOWTO Congure A High Available Firewall Cluster With FwbuilderDocument15 pagesHOWTO Congure A High Available Firewall Cluster With FwbuilderJosé María CopadoNo ratings yet
- Green Networks: Introduction To MininetDocument6 pagesGreen Networks: Introduction To MininetnshivegowdaNo ratings yet
- DCA - Section 3 NetworkingDocument5 pagesDCA - Section 3 NetworkingValiS1234No ratings yet
- DCA - Section 3 NetworkingDocument5 pagesDCA - Section 3 Networkingsrikanth ganjiNo ratings yet
- How To Install and Use Kubernetes On Ubuntu 20.04 - CloudSigmaDocument15 pagesHow To Install and Use Kubernetes On Ubuntu 20.04 - CloudSigmaAymenNo ratings yet
- Lab7 OpensflowDocument11 pagesLab7 OpensflowAllan Pitter PressiNo ratings yet
- SSH X11 ForwardingDocument4 pagesSSH X11 ForwardingJunkOh GradyNo ratings yet
- KUBERNETESDocument6 pagesKUBERNETESjyotiNo ratings yet
- Beowulf ClusterDocument4 pagesBeowulf ClusterkiritmodiNo ratings yet
- DevNet Associate (Version 1.0) - Module 5 Exam Answers PDFDocument12 pagesDevNet Associate (Version 1.0) - Module 5 Exam Answers PDFsamar zantourNo ratings yet
- Command and Control Cheat SheetDocument70 pagesCommand and Control Cheat SheetcptraavanNo ratings yet
- Clustering Unikernel Microservices in Networking: Myungho - Jung@utah - Edu University of UtahDocument4 pagesClustering Unikernel Microservices in Networking: Myungho - Jung@utah - Edu University of UtahAnonymous iTV3WVbsNo ratings yet
- Clustering DocumentationDocument15 pagesClustering DocumentationNazifa KazimiNo ratings yet
- Free Lab Friday - Part 6 Implementing IP Addressing SchemesDocument3 pagesFree Lab Friday - Part 6 Implementing IP Addressing SchemeshoadiNo ratings yet
- Packet Sniffing and Spoofing LabDocument12 pagesPacket Sniffing and Spoofing LabTal ZichNo ratings yet
- Packet Sniffing and Spoofing LabDocument12 pagesPacket Sniffing and Spoofing LabZihao MiaoNo ratings yet
- Sniffing SpoofingDocument12 pagesSniffing SpoofingMulugeta Tesfaye TadesseNo ratings yet
- TCP ProtocolDocument19 pagesTCP ProtocolVandana DulaniNo ratings yet
- OCFS2 - Frequently Asked QuestionsDocument18 pagesOCFS2 - Frequently Asked QuestionsJosneiNo ratings yet
- KuberneteDocument4 pagesKuberneteTuấn Nguyễn ThúcNo ratings yet
- How To Expose Multiple Containers On The Same PortDocument16 pagesHow To Expose Multiple Containers On The Same PortLuc ChantelNo ratings yet
- Kubernetes: Build and Deploy Modern Applications in a Scalable Infrastructure. The Complete Guide to the Most Modern Scalable Software Infrastructure.: Docker & Kubernetes, #2From EverandKubernetes: Build and Deploy Modern Applications in a Scalable Infrastructure. The Complete Guide to the Most Modern Scalable Software Infrastructure.: Docker & Kubernetes, #2No ratings yet
- Connecting To A Server in A Different Network Via SapGuiDocument2 pagesConnecting To A Server in A Different Network Via SapGuisony209No ratings yet
- Bluetooth For Programmers: Albert HuangDocument4 pagesBluetooth For Programmers: Albert HuangYosephNo ratings yet
- FSX Shared Cockpit (1.2)Document14 pagesFSX Shared Cockpit (1.2)MihaiGurguNo ratings yet
- Ricoh Security Brochure PDFDocument18 pagesRicoh Security Brochure PDFR. EthierNo ratings yet
- SAP HA740 SetupGuide AWS Color enDocument84 pagesSAP HA740 SetupGuide AWS Color ens4 hanaNo ratings yet
- Zimbra OS Multi-Server Install 4-0-5Document48 pagesZimbra OS Multi-Server Install 4-0-5Keerthi Wijewardhane100% (3)
- CA4 KQSProg Guide Rev GDocument29 pagesCA4 KQSProg Guide Rev GTyler HiggsNo ratings yet
- ZXNVM S2000-WA-E Series: FeaturesDocument2 pagesZXNVM S2000-WA-E Series: FeaturesEvis SandovalNo ratings yet
- GGDocument53 pagesGGKelvin UtomoNo ratings yet
- Data-Linc Catalog 2012Document28 pagesData-Linc Catalog 2012QuantumAutomationNo ratings yet
- Cisco IOS Voice Troubleshooting and Monitoring - Voice Call Debug Filtering On Cisco Voice GatewaysDocument21 pagesCisco IOS Voice Troubleshooting and Monitoring - Voice Call Debug Filtering On Cisco Voice Gatewaysvipinco20030% (1)
- Week 5 Port Scanning Based On NMAPDocument23 pagesWeek 5 Port Scanning Based On NMAPBayu SamudraNo ratings yet
- MghelpDocument9 pagesMghelproger cyrNo ratings yet
- The Absolute Beginner S Guide To HTML and CSSDocument244 pagesThe Absolute Beginner S Guide To HTML and CSSBonus BNo ratings yet
- BMW OnlineTIS Site - InformationDocument30 pagesBMW OnlineTIS Site - InformationСтефан ЦаневNo ratings yet
- 7.2.1.8 Lab Using Wireshark To Observe The TCP 3 Way HandshakeDocument6 pages7.2.1.8 Lab Using Wireshark To Observe The TCP 3 Way HandshakePrinCesita Lily100% (1)
- HP Smart Update Manager Release NotesDocument22 pagesHP Smart Update Manager Release NotesManoj KumarNo ratings yet
- ZLAN9500 User Manual PDFDocument26 pagesZLAN9500 User Manual PDFSara CorreaNo ratings yet
- Oceanstor Dorado 5000V6: Hands-On / Transferência de ConhecimentoDocument617 pagesOceanstor Dorado 5000V6: Hands-On / Transferência de ConhecimentoLuis Fernando Lima DuarteNo ratings yet
- FR3004 TechreferenceDocument66 pagesFR3004 TechreferenceShadeTheif100% (2)
- SBC Advanced Teams Practical Exam Dec 2022Document19 pagesSBC Advanced Teams Practical Exam Dec 2022Ahmed Qunibi100% (1)
- DASABCIPDocument234 pagesDASABCIPericNo ratings yet
- 2.8-Inch Linux Visible Light Product Quick Start Guide V1.0-20190830Document10 pages2.8-Inch Linux Visible Light Product Quick Start Guide V1.0-20190830Guilherme VenturaNo ratings yet
- SonicWALL TELE3 SP Administrators GuideDocument210 pagesSonicWALL TELE3 SP Administrators GuideJeejan JosephNo ratings yet
- 07 CLPT en TrainerNotes V1.2.2 20151119GPDocument37 pages07 CLPT en TrainerNotes V1.2.2 20151119GPEssaïd Fassy FehryNo ratings yet
- Citrix Access Gateway Enterprise EditionDocument32 pagesCitrix Access Gateway Enterprise EditionAnonymous lCFzK9c2eNo ratings yet
- NSA XKeyscore Source Code Targets Tor and Tails UsersDocument3 pagesNSA XKeyscore Source Code Targets Tor and Tails UsersLeakSourceInfoNo ratings yet
- Nmodbus API Manual v1.2 enDocument35 pagesNmodbus API Manual v1.2 enAnonymous m8s2TWNo ratings yet
- ONVDocument16 pagesONVanh trinhNo ratings yet
- En Fanox Sicom Manual Comsoftware Sicom r009Document163 pagesEn Fanox Sicom Manual Comsoftware Sicom r009Cong TranNo ratings yet