Professional Documents
Culture Documents
A Dependable Sharing Approach With Creation of Encrypted Database
Uploaded by
Azmi AbdulbaqiOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
A Dependable Sharing Approach With Creation of Encrypted Database
Uploaded by
Azmi AbdulbaqiCopyright:
Available Formats
ISSN No.
0976-5697
Volume 2, No. 4, July-August 2011
International Journal of Advanced Research in Computer Science
RESEARCH PAPER
Available Online at www.ijarcs.info
A Dependable sharing approach with creation of Encrypted database
Monika Sharma* Meenakshi Sharma
Lecturer in Information Technology Assistant Professor in CSE
SDDIET, H.C.T.M,
Barwala, India Kaithal, India
Monikamtech123@gmail.com minnyk@gmail.com
Abstract: Database security is important for every organization to protect their data from unauthorized users. In this dissertation
Encryption plays a major role for protecting the data and securely sharing the data in the database. Encrypting the whole data in the database is
not advisable because of the time it takes to encrypt the data. So only the sensitive data is encrypted and stored in the database. Whenever
any malicious attacks happen on the database even if he opens the database the data in the database is encrypted which that malicious user
/ unauthorized user can’t understand.[1] So any attacks on the database become useless for those who are attacking. There are different
kinds of users out of which administrator is one of the user and the administrator can give permissions to the other users. Whenever any
authorized user enters with his valid id and password to view data according to the permissions given by administrator the data is decrypted
then retrieved and shown to the user.[4],[6]. Even the user who is the owner of his details can give permissions on his details which he
wishes to other users. So sharing also becomes more secure because only the owner and the administrator have the right to give different
combination of permissions. In this paper we have discussed the dependable sharing approach of encrypted database.
Keywords: Database, Encryption, Database Security, Data Encryption
polices and governmental regulations. Database security is
I. INTRODUCTION the system, processes, and procedures that protect a
database from unintended activity. Unintended activity can
There are many database security techniques but be categorized as authenticated misuse, malicious attacks
each of them having their own vulnerabilities. Many or inadvertent mistakes made by authorized individuals or
organizations are suffering from these vulnerabilities and processes. Information security means protecting
are in immediate need of some database security information and information systems f r o m unauthorized
technique that can ensure both data privacy and should be access, use, disclosure, disruption, modification, or
able to protect the database from the attacks caused by
intruders and malicious users. Encryption is the only
technique that provides both data privacy and protects the
database from the attacks caused by intruders and malicious
users. So there is an immediate need for the organization
for a database security technique that can defend all kinds
of attacks. Time also plays an important role in the
organizations so encryption of the whole data is also not
advisable and only data that is confidential / sensitive is
encrypted [1]. Sharing of the data should also be secure
only the authorized persons who are permitted should only
view the data. This is technique that provides both the
protection from malicious user keeping the time constraint
in mind and secure sharing of data
destruction.
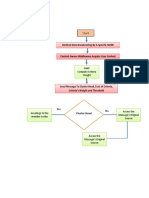
II. DATABASE SECURITY
Figure 1. Components of Information Security
Databases have been protected from external
connections by firewalls or routers on the network perimeter III. ENCRYPTION
with the database environment existing on the internal
network opposed to being located within a demilitarized In cryptography, encryption is the process of
zone. Additional network security devices that detect and transforming information (referred to as plaintext) using an
alert on malicious database protocol traffic include network algorithm (called cipher) to make it unreadable to anyone
intrusion detection systems along with host-based intrusion except those possessing special knowledge, usually referred
detection systems. Database security can begin with the to as a key. The result of the process is encrypted
process of creation and publishing of appropriate security information (in cryptography, referred to as cipher text). In
standards for the database environment. The standards may many contexts, the word encryption also implicitly refers to
include specific controls for the various relevant database the reverse process, decryption (e.g. “software for
platforms; a set of best practices that cross over the encryption” can typically also perform decryption), to make
platforms; and linkages of the standards to higher level
© 2010, IJARCS All Rights Reserved 116
Monika Sharma et al, International Journal of Advanced Research in Computer Science, 2 (4), July-August, 2011,116-118
the encrypted information readable again (i.e. to make it
unencrypted). Encryption has long been used by
militaries and governments to facilitate secret
communication. Encryption is now used in protecting
information within many kinds of civilian systems, such as
computers, networks (e.g. the Internet e-commerce),
mobile telephones, wireless microphones, wireless
intercom systems, Bluetooth devices and bank automatic
teller machines. Encryption is also used in digital rights
management to prevent unauthorized use or reproduction of
copyrighted material and in software also to protect against
reverse engineering.
IV. ENCRYPTION ALGORITHM
A mathematical procedure of performing encryption
on data through the use of an algorithm, information is
made into meaningless cipher text and requires the use of a
key to transform the data back into its original form. In this
dissertation the encryption algorithm used is Data
Encryption Standard (DES).
A. Data Encryption Standard (Des) Algorithm
The Data Encryption Standard (DES) is a cipher (a
method for encrypting information) that was selected by
NBS as an official Federal Information Processing
Standard (FIPS) for the United States in 1976 and Figure 2: Data Encryption Standards Algorithm
which has subsequently enjoyed widespread use
internationally. It is based on a symmetric key algorithm VI. CONCLUSION
that uses a 56-bit key. DES consequently came under
intense academic scrutiny which motivated the modern Encryption by itself can protect the confidentiality of
understanding of block ciphers and their cryptanalysis [9]. messages, but other techniques are still needed to protect
DES is now considered to be insecure for many the integrity and authenticity of a message. But if all the
applications. This is chiefly due to the 156-bit key size data in the database is encrypted then it reduces the
being too small. The algorithm is believed to be practically performance. Therefore, only the sensitive/personal data is
secure in the form of Triple DES, although there are encrypted. For retrieval that data is decrypted. The no
theoretical attacks. In recent years, the cipher has been sensitive/common data is not encrypted and is retrieved
superseded by the Advanced Encryption Standard (AES). immediately while authorized user requests for it
according to the permissions given to them. Encryption is
V. WORKING OF DES the only technique that provides both data privacy and
protects the database from the attacks caused by intruders
Encryption of a block of the message takes place in and malicious users. So there is a immediate need for the
16 stages or rounds. From the input key, sixteen 48 bit organization for a database security technique that can
keys are generated, one for each round. In each round, defend all kinds of attacks. Time also plays an important
eight so-called S-boxes are used. These S-boxes are role in the organizations so encryption of the whole data is
fixed in the specification of the standard. Using the S- also not advisable and only data that is confidential /
boxes, groups of six bits are mapped to groups of four bits. sensitive is encrypted. Even sharing of the data is also
The contents of these S-boxes have been determined by the secure because only Administrator has right to give
U.S. National Security Agency (NSA). The figure in the permissions and owner has the right to change the
next page should hopefully make this process a bit more permissions. This increases the performance of the system.
clear. In the figure, the left and right halves are denotes as In this paper the encryption algorithm used is D.E.S (Data
L0 and R0, and in subsequent rounds as L1, R1, L2, R2 and Encryption Standard) for encrypting the data. The mo d el
so on. The function f is responsible for all the mappings can be extended fo r different kind s of encryption
described above. DES is the archetypal block cipher an algorithms such as AES (Advanced Encryption System)
algorithm that takes a fixed- length string of plaintext encryption algorithm, RSA (Rivest- Shamir- Adelman)
bits and transforms it through a series of complicated encryption algorithm.
operations into another cipher text bit string of the same
length. In the case of DES, the block size is 64 bits. DES VII. REFERENCES:
also uses a key to customize the transformation, so that
decryption can supposedly only be performed by those [1] Sesai S, Yang Z, Chen J and Du Xu, “A Secure Database
who know the particular keyused to encrypt. Encryption Scheme”, Proceedings of IEEE, pp 49-53,
26, Nov 2004.
[2] Lihua Yu,Chen G, Ke Chen,Dong J, “Securely Sharing
© 2010, IJARCS All Rights Reserved 117
Monika Sharma et al, International Journal of Advanced Research in Computer Science, 2 (4), July-August, 2011,116-118
th [13] Horst Feistel, Block Cipher Cryptographic System, US
Data in Encrypted databases”, Proceedings of the 10
Patent 3,798,359, March 19, 1974.
International Conference on Computer Supported
[14] Whitfield Daffier and Martin E. Hellman, Exhaustive
Cooperative work in Design, 2003.
Cryptanalysis of the NBS Data Encryption Standard,
[3] Yong Zhang, Wei-Xin Li, Xia-Mu Niu, “A Secure
Computer 10 (6), 74-84 (1977).
Cipher Index over Encrypted Character Data in
[15] Electronic Frontier Foundation, Cracking DES: Secrets
Database”, Proceedings of the Seventh International
of Encryption Research, Wiretap Politics and Chip
Conference on Machine Learning and Cybernetics,
Design, O’Reilly & Associates, Inc., Sebastopol, CA
Kunming, pp 1111-1116,12-15 July 2008,
(1998).
[4] Ian Somesville, “Software Engineering Pearson
[16] Miles E .Smid& Deniss. K. Brantstad, “Data
Education Asia”, Sixth edition 2001.
Encryption Standard (DES), Federal Information
[5] Raghu Ramakrishna, Johannes Gehrke, “Database
Processing”, Proceeding of IEEE, vol.76, pp.550-559,
Management Systems”, McGraw Hill International
May, 1988.
Editions, Second Edition 2000.
[17] Gobinath, Subramaniam, Kalyani Subramanian, Senthil
[6] Java Server Pages Technology, ”Sun Developer
Raja Balakrishnan,Baskaran Kaliaperumal, “DES
Network”,1994, [online document] Available at:
Enabled Fingerprint System”, Proceedings of the
http://java.sun.com/products/jsp/index.jsp
International Conference on Man-Machine Systems
[7]] http://en.wikipedia.org/wiki/HTML
(ICOMMS), , Batu Ferringhi, Penang, Malaysia, 11 –
[8] Apache Tomcat,“WIKIPEDIA”, June 2009, [online
13, October, 2009.
document]Available
[18] Amit, Dhir, “Data Encryption using DES/Triple-DES
at:http://en.wikipedia.org/wiki/Apache_Tomcat
Functionality in Spartan-II FPGAs” , White Paper-115
[9] Data Encryption Standard, “WIKIPEDIA”, June 2009,
(v1.0), March 9, 2000.
[online document] Available
[19] Paul. A.J, Varghese Paul, P. Mythili, “ A Fast and
at:http://en.wikipedia.org/wiki/Data_Encryption_Standa
secure encryption for message communication”, IET-
rd
UK International Conference on Information and
[10] Data Encryption Standard, Federal Information
Communication Technology in Electrical Sciences
Processing Standards Publication (FIPS PUB) 46,
(ICTES 2007),Dr. M.G.R. University, Chennai, Tamil
National Bureau of Standards, Washington, DC (1977).
Nadu, India. pp. 629-634, Dec. 20-22, 2007.
[11] Data Encryption Algorithm (DEA), ANSI X3.92-1981,
[20] Abdel-Karim Al Tamimi, “Performance Analysis of
American National Standards Institute, New York.
Data Encryption Algorithms”,
[12] Horst Feistel, Cryptography and Computer Privacy, Sci.
http://www.cse.wustl.edu/~jain/cse567-
Am. 228 (5), 15-23 (1973).
06/ftp/encryption_perf/index.html.
© 2010, IJARCS All Rights Reserved 118
You might also like
- CEH: Certified Ethical Hacker v11 : Exam Cram Notes - First Edition - 2021From EverandCEH: Certified Ethical Hacker v11 : Exam Cram Notes - First Edition - 2021No ratings yet
- Wazuh-Elastic Stack Training: Deck 2Document61 pagesWazuh-Elastic Stack Training: Deck 2Eric MartinezNo ratings yet
- Singh G. Cisco Certified CyberOps Associate 200-201.guide - .2021Document1,029 pagesSingh G. Cisco Certified CyberOps Associate 200-201.guide - .2021JuanCarlosArias100% (1)
- Database Security PDFDocument23 pagesDatabase Security PDFUmesh Hengaju0% (1)
- CYBER SECURITY HANDBOOK Part-2: Lock, Stock, and Cyber: A Comprehensive Security HandbookFrom EverandCYBER SECURITY HANDBOOK Part-2: Lock, Stock, and Cyber: A Comprehensive Security HandbookNo ratings yet
- Light Cruiser: Performance Alarms MonitoringDocument31 pagesLight Cruiser: Performance Alarms MonitoringYasir KhanNo ratings yet
- Data Security Enhancement Using Number SystemDocument31 pagesData Security Enhancement Using Number Systemmarshal robertNo ratings yet
- Database Security Attacks Threats and Challenges IJERTCONV5IS10008Document4 pagesDatabase Security Attacks Threats and Challenges IJERTCONV5IS10008Hussein AbdullahNo ratings yet
- Network SecurityDocument11 pagesNetwork SecurityAshu ChauhanNo ratings yet
- New Comparative Study Between DES, 3DES and AES Within Nine FactorsDocument6 pagesNew Comparative Study Between DES, 3DES and AES Within Nine FactorsKashish GuptaNo ratings yet
- Cns-Unit I IntroductionDocument39 pagesCns-Unit I IntroductionRamyaNo ratings yet
- Cybr Security - LatestDocument40 pagesCybr Security - LatestboyaraghavendraNo ratings yet
- Transparent Data Encryption - Solution For Security of Database ContentsDocument4 pagesTransparent Data Encryption - Solution For Security of Database ContentsEditor IJACSANo ratings yet
- DSM Assignment 1Document15 pagesDSM Assignment 1Malik GoharNo ratings yet
- Irjet V5i4919Document5 pagesIrjet V5i4919ghada sayedNo ratings yet
- Privacy Preserving Methodology For Anonymous Data SharingDocument2 pagesPrivacy Preserving Methodology For Anonymous Data SharingInternational Journal of Innovative Science and Research TechnologyNo ratings yet
- Chapter Goals: Security TechnologiesDocument12 pagesChapter Goals: Security TechnologiesDheeraj MishraNo ratings yet
- Ixia-VS-BR-Guide - Network - Security - Terms - AcronymsDocument5 pagesIxia-VS-BR-Guide - Network - Security - Terms - AcronymsErnesto MorenoNo ratings yet
- Data SecurityDocument5 pagesData Securitymunashe francisNo ratings yet
- 192 CryptographyDocument16 pages192 CryptographyTanjil AhmedNo ratings yet
- NF Lecture 14Document10 pagesNF Lecture 14Ayesha nawazNo ratings yet
- VTU Network Security (10ec832) Unit-6 NotesDocument24 pagesVTU Network Security (10ec832) Unit-6 Notesjayanthdwijesh h p0% (2)
- (IJCST-V5I2P61) :irene Getzi SDocument5 pages(IJCST-V5I2P61) :irene Getzi SEighthSenseGroupNo ratings yet
- Paper 8659Document5 pagesPaper 8659IJARSCT JournalNo ratings yet
- A Study of Cryptographic AlgorithmsDocument14 pagesA Study of Cryptographic AlgorithmsIJRASETPublicationsNo ratings yet
- CryptographyDocument77 pagesCryptographyDominic LouiseNo ratings yet
- Pros and Cons of Cryptography, Steganography and Perturbation TechniquesDocument6 pagesPros and Cons of Cryptography, Steganography and Perturbation Techniquesparitosh chandrakapureNo ratings yet
- Information System Assignments 26Document48 pagesInformation System Assignments 26Morgan OkothNo ratings yet
- Security of Data Science and Data Science For Security: IjarsctDocument5 pagesSecurity of Data Science and Data Science For Security: IjarsctLab George BrownNo ratings yet
- FINAL TERM Topic Understanding Cybersecurity. BSA - BSMADocument7 pagesFINAL TERM Topic Understanding Cybersecurity. BSA - BSMAynoxtaikoNo ratings yet
- Chapter One ProjectDocument8 pagesChapter One ProjectHabiba MuhdNo ratings yet
- Database Security Threats and Challenges - 2020 PDFDocument5 pagesDatabase Security Threats and Challenges - 2020 PDFDanyer Valencia LlamocaNo ratings yet
- Cyber PresentationDocument5 pagesCyber Presentationceedosk1No ratings yet
- Cyber Security EssayDocument5 pagesCyber Security EssayBilly BaginzNo ratings yet
- OS-Chapter 6 - Security and ProtectionDocument14 pagesOS-Chapter 6 - Security and ProtectionDesalegn Asefa100% (3)
- 126 It0017Document5 pages126 It0017JoseMarianoTomayTeranNo ratings yet
- Privacy Preserving: Slicer Based SchemeDocument3 pagesPrivacy Preserving: Slicer Based SchemeIJSTENo ratings yet
- SSRN Id3319251Document5 pagesSSRN Id3319251Hòa Nguyễn Lê MinhNo ratings yet
- Absolute Data Security SchemeDocument6 pagesAbsolute Data Security Scheme517wangyiqiNo ratings yet
- Cryptography and Network SecurityDocument158 pagesCryptography and Network SecuritySivarajan RamachandranNo ratings yet
- Faculty e Notes Unit 1Document20 pagesFaculty e Notes Unit 1deepakraj0192No ratings yet
- Securtiy Is Essential For Sensitive MaterialsDocument10 pagesSecurtiy Is Essential For Sensitive MaterialsToby Nixon100% (2)
- CybersecurityDocument9 pagesCybersecurityAnisa NdociNo ratings yet
- Abdu Gusau Polytechnic Talata Mafara Zamfara State: TopicDocument12 pagesAbdu Gusau Polytechnic Talata Mafara Zamfara State: TopicSOMOSCONo ratings yet
- The Effectiveness of The Port Knocking Method in Computer SecurityDocument8 pagesThe Effectiveness of The Port Knocking Method in Computer SecurityNOORNo ratings yet
- Cryptography in ITDocument48 pagesCryptography in ITFego OgwaraNo ratings yet
- A Novel Framework For Database Security Based On MDocument9 pagesA Novel Framework For Database Security Based On MGourvankit singh BhatiNo ratings yet
- Secured and Encrypted Data Transmission Over The Web Using CryptographyDocument5 pagesSecured and Encrypted Data Transmission Over The Web Using CryptographyEditor IJTSRDNo ratings yet
- Hybrid Cryptosystem For Secure Data StorageDocument4 pagesHybrid Cryptosystem For Secure Data StorageIJIRIS - INTERNATIONAL JOURNAL OF INNOVATIVE RESEARCH IN INFORMATION SECURITYNo ratings yet
- Unit - 2: Infrastructure of Network Security: StructureDocument44 pagesUnit - 2: Infrastructure of Network Security: StructureSreeprada VNo ratings yet
- Paper of CryptographyDocument3 pagesPaper of CryptographySuinNo ratings yet
- Design and Implementation of Security Management Using Data Encryption and Decryption Techniquesfjo1nr4mfDocument12 pagesDesign and Implementation of Security Management Using Data Encryption and Decryption Techniquesfjo1nr4mfjamessabraham2No ratings yet
- Database Security and Encryption: A Survey Study: International Journal of Computer Applications May 2012Document8 pagesDatabase Security and Encryption: A Survey Study: International Journal of Computer Applications May 2012iyelNo ratings yet
- 20BCA1335 Ashish-Yadav AssinmentDocument4 pages20BCA1335 Ashish-Yadav AssinmentimyadashuNo ratings yet
- Resilient Security Against Hackers Using Enchanced Encryption Techniques: Blowfish and Honey EncryptionDocument5 pagesResilient Security Against Hackers Using Enchanced Encryption Techniques: Blowfish and Honey EncryptionEditor IJRITCCNo ratings yet
- A Review On Network SecurityDocument4 pagesA Review On Network SecuritylujainmohammedNo ratings yet
- Network Security and CryptographyDocument8 pagesNetwork Security and CryptographyKPNo ratings yet
- Alert System For New User To Find Safe Area Using BlockchainDocument5 pagesAlert System For New User To Find Safe Area Using BlockchainInternational Journal of Innovative Science and Research TechnologyNo ratings yet
- 10 1109@icoei48184 2020 9143004Document6 pages10 1109@icoei48184 2020 9143004Udhaya kumar PNo ratings yet
- Oprating Systems: College of Natural and Computational Sciences Department of Computer ScienceDocument5 pagesOprating Systems: College of Natural and Computational Sciences Department of Computer ScienceSEMAHAGN ADAMUNo ratings yet
- Encryption Techniques To Protect The Patient Privacy in Health CareDocument11 pagesEncryption Techniques To Protect The Patient Privacy in Health CareSachin KhandareNo ratings yet
- IEEE 2017 Enhanced RSA Algorithm With Varying Key Sizes For Data Security in CloudDocument4 pagesIEEE 2017 Enhanced RSA Algorithm With Varying Key Sizes For Data Security in Cloudakash rawatNo ratings yet
- Edddas 11223344Document8 pagesEdddas 11223344Azmi AbdulbaqiNo ratings yet
- Edddas 11223344Document7 pagesEdddas 11223344Azmi AbdulbaqiNo ratings yet
- TGGTDocument3 pagesTGGTAzmi AbdulbaqiNo ratings yet
- TGGTDocument3 pagesTGGTAzmi AbdulbaqiNo ratings yet
- Homogeneous (Or Balanced) .: Example 1: Scale RectangleDocument3 pagesHomogeneous (Or Balanced) .: Example 1: Scale RectangleAzmi AbdulbaqiNo ratings yet
- Edddas 11223344Document3 pagesEdddas 11223344Azmi AbdulbaqiNo ratings yet
- Edddas 11223344Document11 pagesEdddas 11223344Azmi AbdulbaqiNo ratings yet
- 3 2D Transformation ROTATIONDocument3 pages3 2D Transformation ROTATIONAzmi AbdulbaqiNo ratings yet
- TGGTDocument3 pagesTGGTAzmi AbdulbaqiNo ratings yet
- Computer Graphics - LectureDocument5 pagesComputer Graphics - LectureAzmi AbdulbaqiNo ratings yet
- 3 2D Transformation ROTATIONDocument3 pages3 2D Transformation ROTATIONAzmi AbdulbaqiNo ratings yet
- Quality Assessment Tool For Performance Measurement of Image Contrast Enhancement MethodsDocument10 pagesQuality Assessment Tool For Performance Measurement of Image Contrast Enhancement MethodsAzmi AbdulbaqiNo ratings yet
- 3 2D Transformation ROTATIONDocument3 pages3 2D Transformation ROTATIONAzmi AbdulbaqiNo ratings yet
- 2-Circle Drawing AlgorithmsDocument4 pages2-Circle Drawing AlgorithmsAzmi AbdulbaqiNo ratings yet
- Computer Graphics - Lecture (1)Document6 pagesComputer Graphics - Lecture (1)Azmi AbdulbaqiNo ratings yet
- Computer Graphics: Line and Circle 1-Line Drawing AlgorithmsDocument4 pagesComputer Graphics: Line and Circle 1-Line Drawing AlgorithmsAzmi AbdulbaqiNo ratings yet
- Blockiness Estimation in Reduced Reference Mode For Image Quality AssessmentDocument4 pagesBlockiness Estimation in Reduced Reference Mode For Image Quality AssessmentAzmi AbdulbaqiNo ratings yet
- Files 112Document1 pageFiles 112Azmi AbdulbaqiNo ratings yet
- Files 112Document1 pageFiles 112Azmi AbdulbaqiNo ratings yet
- Building A Reduced Reference Video Quality Metric With Very Low Overhead Using Multivariate Data AnalysisDocument6 pagesBuilding A Reduced Reference Video Quality Metric With Very Low Overhead Using Multivariate Data AnalysisAzmi AbdulbaqiNo ratings yet
- Enhanced Image No-Reference Quality Assessment Based On Colour Space DistributionDocument11 pagesEnhanced Image No-Reference Quality Assessment Based On Colour Space DistributionAzmi AbdulbaqiNo ratings yet
- Neurocomputing: Sergio Decherchi, Paolo Gastaldo, Rodolfo Zunino, Erik Cambria, Judith RediDocument12 pagesNeurocomputing: Sergio Decherchi, Paolo Gastaldo, Rodolfo Zunino, Erik Cambria, Judith RediAzmi AbdulbaqiNo ratings yet
- Chen2012 Chapter ReducedReferenceImageQualityAsDocument8 pagesChen2012 Chapter ReducedReferenceImageQualityAsAzmi AbdulbaqiNo ratings yet
- Files 112Document1 pageFiles 112Azmi AbdulbaqiNo ratings yet
- Neurocomputing: Lin Ma, Xu Wang, Qiong Liu, King Ngi NganDocument11 pagesNeurocomputing: Lin Ma, Xu Wang, Qiong Liu, King Ngi NganAzmi AbdulbaqiNo ratings yet
- Files 112Document1 pageFiles 112Azmi AbdulbaqiNo ratings yet
- Files 112Document1 pageFiles 112Azmi AbdulbaqiNo ratings yet
- Files 112Document1 pageFiles 112Azmi AbdulbaqiNo ratings yet
- Neurocomputing: Xu Wang, Qiong Liu, Ran Wang, Zhuo ChenDocument9 pagesNeurocomputing: Xu Wang, Qiong Liu, Ran Wang, Zhuo ChenAzmi AbdulbaqiNo ratings yet
- J. Vis. Commun. Image R.: Saeed Mahmoudpour, Peter SchelkensDocument13 pagesJ. Vis. Commun. Image R.: Saeed Mahmoudpour, Peter SchelkensAzmi AbdulbaqiNo ratings yet
- Dynamic Memory Allocation: PTR (Cast-Type ) Malloc (Byte-Size)Document4 pagesDynamic Memory Allocation: PTR (Cast-Type ) Malloc (Byte-Size)JonathanNo ratings yet
- A. Increase B. Decrease C. Can't Say D. None of The Above AnswerDocument50 pagesA. Increase B. Decrease C. Can't Say D. None of The Above AnswerMukulNo ratings yet
- NC3200S CircuitDocument17 pagesNC3200S CircuitHector PerezNo ratings yet
- ZKTeco+Fingerprint+Scanner+SDK+Selection+Guide Ver3.0Document1 pageZKTeco+Fingerprint+Scanner+SDK+Selection+Guide Ver3.0Dracon KnightNo ratings yet
- Assignment 1Document7 pagesAssignment 1julyhopingNo ratings yet
- IP Project Covid-19 ImpactDocument24 pagesIP Project Covid-19 ImpactextreammartialgamingNo ratings yet
- Securityplus 2020 720 PagesDocument721 pagesSecurityplus 2020 720 PagesSolomonNo ratings yet
- Brain Gate - Program To Connect Human Brains To ComputerDocument20 pagesBrain Gate - Program To Connect Human Brains To ComputerShreya SachanNo ratings yet
- Wired System CatalogueDocument8 pagesWired System CatalogueMuaz HaşaneNo ratings yet
- Rohit Kumar Resume (Photo) PDFDocument1 pageRohit Kumar Resume (Photo) PDFBhashkar JhaNo ratings yet
- Zuber Resume Aug23Document1 pageZuber Resume Aug23rajendrasNo ratings yet
- Group 4 - Using DFDDocument26 pagesGroup 4 - Using DFDZakyaNo ratings yet
- Annamalai UniversityDocument41 pagesAnnamalai UniversityGreen ZoneNo ratings yet
- Online Deal Project ReportDocument167 pagesOnline Deal Project ReportSuvendu Sekhar SahooNo ratings yet
- Mod Menu Crash 2023 11 19-09 41 10Document2 pagesMod Menu Crash 2023 11 19-09 41 10РАВАНNo ratings yet
- Parallel Computing Based Distribution Network - Reliability Evaluation Technology ResearchDocument6 pagesParallel Computing Based Distribution Network - Reliability Evaluation Technology ResearchSudiharyantoLikaNo ratings yet
- DIALux Setup LogDocument2 pagesDIALux Setup LogACES ENGINEERINGNo ratings yet
- Downloading and Installing Db2 Developer-C On Ubuntu Linux: 1 Introduction: What Is Db2?Document23 pagesDownloading and Installing Db2 Developer-C On Ubuntu Linux: 1 Introduction: What Is Db2?Marco JimenezNo ratings yet
- When Saving A FileDocument3 pagesWhen Saving A FileAhmad Hadi Mashuri HadiNo ratings yet
- DPSD 20-21 Notes Unit-3Document138 pagesDPSD 20-21 Notes Unit-3Karthick Sivakumar ChellamuthuNo ratings yet
- CST 232 Operating Systems Tutorial 1 (Week 3 25-9-2017 To 29-9-2017)Document1 pageCST 232 Operating Systems Tutorial 1 (Week 3 25-9-2017 To 29-9-2017)Chua ZheNo ratings yet
- Spru 187 oDocument229 pagesSpru 187 oprageNo ratings yet
- Tech Summit 2021 Autoupgrade Deep DiveDocument86 pagesTech Summit 2021 Autoupgrade Deep DivemghomriNo ratings yet
- i-PRO - UDE - BWC4000 - ICV4000 - IDGuard - 2021-11-30Document68 pagesi-PRO - UDE - BWC4000 - ICV4000 - IDGuard - 2021-11-30Ted DetNo ratings yet
- Robotic Process Automation: Mrs. Leena A Deshpande Leena - Deshpande@viit - Ac.inDocument25 pagesRobotic Process Automation: Mrs. Leena A Deshpande Leena - Deshpande@viit - Ac.inMIRELLE MARTISNo ratings yet
- Kv-29fq76e, 29FQ76KDocument24 pagesKv-29fq76e, 29FQ76KBouhaja SalahNo ratings yet
- Learning Deep Python Network Progamming Learn Network Programming in Simple and Easy Steps (Etc.)Document113 pagesLearning Deep Python Network Progamming Learn Network Programming in Simple and Easy Steps (Etc.)doolalosNo ratings yet
- Blockchain ShardingDocument6 pagesBlockchain ShardingVIVA-TECH IJRINo ratings yet