Professional Documents
Culture Documents
Secure Big Data Access Control Policies For Cloud Computing Environment
Uploaded by
Mahi MalikOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Secure Big Data Access Control Policies For Cloud Computing Environment
Uploaded by
Mahi MalikCopyright:
Available Formats
International Journal of Innovative Research in Computer Science & Technology (IJIRCST)
ISSN: 2347-5552, Volume-5, Issue-2, March 2017
DOI: 10.21276/ijircst.2017.5.2.8
Secure Big Data Access Control Policies for
Cloud Computing Environment
Taniya Jain (M.Tech Scholar), Asst. Prof. Javed Akhtar Khan
Abstract— As the term indicates the Big data it means supervise or organize the cloud infrastructure yet they have
we are work for the something big or can say something been in charge of on operating systems, applications,
large in the Amount, Data the high volume is known as storage space and probably their collection and components
the big data.Now a Day for storing the data file in the with the cloud computing key technology [2] . One of the
Computer Science Engineering we are used the Hard main apprehension in cloud computing is the possibility of
disk, some of the storage place , these storage device incursion of privacy. As cloud computing is achieving
may store the data in a Giga byte capability and augmented popularity, apprehension are being voiced about
Terabyte capability or many more, Now a day we are the safety issues bring in through the acceptance of this new
used the some new technology call the cloud model.description of this inventive deployment model, be
environment. So in this work I am study the big data different broadly from them of conventional architectures
storing process in the Cloud environment, big data [3]a new approach using redundancy technique with
fetching from the cloud in a securer manner. So in this improve security in cloud computing.
dissertation work I am also include the some
information about the existing work and some of the
algorithm that war already proposed by the researcher
in the various paper. My work is based on the
Attribute-Based Encryption(ABE) is promising
technique to ensure the end-to-end security of big data
in the cloud However, the policy updating has always
been a challenging issue when ABE is used to construct
access control schemes.
Index Terms— ABE, Big Data, cloud, Cipher Text,
Plain Text
I. INTRODUCTION CLOUD COMPUTING
Cloud Computing refers to manipulating, accessing and
configuring the applications online. It offers online data
storage, infrastructure & cloud application. Cloud
computing is an IT operation form, based on virtualization,
where resources, in terms of infrastructure, appliance and
data are deployed via the internet as a distributed service by
one or some service providers[1] Data integrity Evaluation
Figure 1: Cloud Computing Data Integrity [1]
in cloud Database –as-a – service is explore the data
integrity for the cloud environment . These services are . Cloud computing means that instead of all
scalable on require and can be valued on a pay per use basis. the computer hardware and software you're using sitting on
Cloud infrastructure provides extensive facilities for the your desktop, or somewhere inside your
client such as process, storage, power, networks, space and company's network, it's provided for you as a service by
other computational possessions, so that the customer can another company and accessed over the Internet, usually in
set and perform their convention software as well as a completely seamless way. Most of us use cloud computing
applications and operating system. Client does not all day long without realizing it. The same applies to
Web-based email. Once upon a time, email was something
you could only send and receive using a program running
on your PC (sometimes called a mail client). But then
Manuscript received March 14, 2017 Web-based services such as Hotmail came along and
Taniya Jain (M.Tech Scholar), Asst. Prof. Javed Akhtar Khan Department carried email off into the cloud. Preparing documents over
of Computer Science & Engineering, Takshshila Group of Institute, INDIA
the Net is a newer example of cloud computing. Simply log
Copyright © 2017. Innovative Research Publications. All Rights Reserve 253
Electronic copy available at: https://ssrn.com/abstract=3533276
Secure Big Data Access Control Policies for Cloud Computing Environment
on to a web-based service such as Google Documents and and give performance measurements. Fully secure
you can create a document, spreadsheet, presentation, or functional encryption schemes: a fully secure
whatever you like using Web-based software. Instead of attribute-based encryption (ABE)[4]scheme and a fully
typing your words into a program like Microsoft Word or secure (attribute-hiding) predicate encryption (PE) scheme
Open Office, running on your computer, you're using for inner-product predicates. In both cases, previous
similar software running on a PC at one of Google's constructions were only proven to be selectively secure.
world-wide data centers. Both results use novel strategies to adapt the dual system
II CLOUD COMPUTING IMPORTANCE encryption methodology introduced by Waters. Author
construct our ABE scheme in composite order bilinear
Cloud Computing has several recompense. Some of them
groups, and prove its security from three static assumptions.
are listed below:
ABE scheme supports arbitrary monotone access formulas.
One can right of entry applications as utilities, over the
Predicate encryption scheme is constructed via a new
Internet.
approach on bilinear pairings using the notion of dual
Stage-manage and configure the relevance online at pairing vector spaces proposed by Okamoto and Takashima
any time. . A party can simply act as an ABE authority by creating a
It does not necessitate installing a explicit piece of public key and issuing private keys to different users that
software to right to use or manipulating cloud reflect their attributes. A user can encrypt data in terms of
application. any Boolean formula over attributes issued from any chosen
Cloud computing propose online progress and set of authorities. Finally, our system does not require any
deployment tools, programming runtime surroundings central authority. In this system, our largest technical
through Platform as a Service model. hurdle is to make it collusion resistant. Prior
Cloud resources are accessible over the network in a Attribute-Based Encryption systems achieved collusion
method that provides platform independent right of resistance when the ABE system authority “tied” together
entry to any type of clients. different components (representing different attributes) of a
Cloud computing put forward on-demand self-service. user’s private key by randomizing the key. However, in this
The resources can be used lacking interaction with system each component will come from a potentially
cloud service contributor. different authority, where no coordination between such
Cloud Computing is extremely cost effective since it authorities. Researcher create new techniques to tie key
operates at higher efficiencies with larger utilization. It components together and prevent collusion attacks between
just has need of an Internet connection. users with different global identifiers. In this access control
Cloud Computing offers load comparison that makes scheme is constructed based on the Decentralized -ABE
it more reliable. method is introduce by the researcher primer group order
(CP-ABE) in reference number [5][8], which is proved to
III LITERATURE SURVEY be secure under generic bilinear group model and random
As more sensitive data is shared and stored by third-party oracle model. At an intuitive level, this means that if there
sites on the Internet, there will be a need to encrypt data are any vulnerabilities in the scheme, then these
stored at these sites. One drawback of encrypting data, is vulnerabilities must exploit specific mathematical
that it can be selectively shared only at a coarse-grained properties of elliptic curve groups or cryptographic hash
level (i.e., giving another party your private key). In this functions used when instantiating the scheme has emerged
paper author develop a new cryptosystem for fine-grained as a promising technique to ensure the end-to-end data
sharing of encrypted data that is called Key-Policy security in cloud storage system. It allows data owners to
Attribute-Based Encryption[6] (KP-ABE). In our define access policies and encrypt the data under the
cryptosystem, cipher texts are labeled with sets of attributes policies, such that only users whose attributes satisfying
and private keys are associated with access structures that these access policies can decrypt the data. When more and
control which cipher texts a user is able to decrypt. In more organizations and enterprises outsource data into the
several distributed systems a user should only be able to cloud, the policy updating becomes a significant issue as
access data if a user posses a certain set of credentials or data access policies may be changed dynamically and
attributes. Currently, the only method for enforcing such frequently by data owners. However, this policy updating
policies is to employ a trusted server to store the data and issue has not been considered in existing attribute-based
mediate access control. If any server storing the data is access control schemes [9] in this paper author are
compromised, then the confidentiality of the data will be proposed the secure scalable and fine –grained data acecess
compromised. Previous Attribute Based Encryption[7] control for the cloud computing environment .Author
systems used attributes to describe the encrypted data and Liang –Ao Zhang et.al[10] are proposed the ABE based
built policies into user’s keys; in this system attributes are Access control with the Authentication and proposed the
used to describe a user’s credentials, and a party encrypting policy for the Cloud . In this paper Researcher are introduce
data determines a policy for who can decrypt. This methods the ABE that is attribute based Encryption technique and
are conceptually closer to traditional access control used this technique for the providing the securizaion data
methods such as Role-Based Access Control (RBAC). In cloud , In this paper author are focus on the data owner’s
addition, Author provides an implementation of our system authentication in the ABE system and proposed a new
Copyright © 2017. Innovative Research Publications. All Rights Reserve 254
Electronic copy available at: https://ssrn.com/abstract=3533276
International Journal of Innovative Research in Computer Science & Technology (IJIRCST)
ISSN: 2347-5552, Volume-5, Issue-2, March 2017
DOI: 10.21276/ijircst.2017.5.2.8
scheme for the data access . In this paper author are do the Table 1: Analysis of Data
work for Zero Knowledge Proof of Knowledge (ZKPK) to
realize the anonymous authentication of the owner’s policy
updating key without increasing any secret information to
the owner side. So authors are propose an access control
system with authenticated dynamic policy updating for the
cloud storage and our ideas could also be applied to other
ABE systems.
IV PROBLEM DESCRIPTION
The policy updating is a difficult issue in attribute-based
access control systems, because once the data owner
outsourced data into the cloud, it would not keep a copy in
local systems. When the data owner wants to change the
access policy, it has to transfer the data back to the local site
from the cloud, Re-encrypt the data under the new access
policy, and then move it back to the cloud server. By doing
so, it incurs a high communication overhead and heavy
computation burden on data owners. This motivates us to
develop a new method to outsource the task of policy
updating to cloud server. The grand challenge of
outsourcing policy updating to the cloud is to guarantee the
following requirements:
i) Correctness: Users who possess sufficient attributes
should still be able to decrypt the data encrypted under new
access policy by running the original decryption algorithm.
ii) Completeness: The policy updating method should be
able to update any type of access policy.
iii) Security: The policy updating should not break the
security of the access control system or introduce any new
security problems.
V. OVERVIE OF THE EXISTING SYSTEM
Attribute-Based Encryption (ABE) has emerged as a
promising technique to ensure the end-to-end data security
in cloud storage system. It allows data owners to define
access policies and encrypt the data under the policies, such
that only users whose attributes satisfying these access
policies can decrypt the data. The policy updating problem
has been discussed in key policy structure and cipher
text-policy structure.
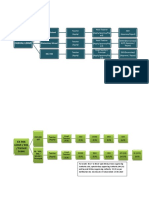
ARCHITECTURAL DIAGRAM
Figure 3: Data Owner File in Big Data
Figure 2: System Architecture
Copyright © 2017. Innovative Research Publications. All Rights Reserve 255
Electronic copy available at: https://ssrn.com/abstract=3533276
Secure Big Data Access Control Policies for Cloud Computing Environment
[6] B. Waters, “Key-policy attribute-based
encryption(KP-ABE) An expressive, efficient, and
provably secure realization,” in KC’11. Springer, 2011, pp.
53–70.
[7] A. B. Lewko, T. Okamoto, A. Sahai, K. Takashima, and
B. Waters,“Fully secure functional encryption:
Attribute-based Encryption and (hierarchical) inner
product encryption(RBAC)” in EUROCRYPT’10.
Springer, 2010, pp. 62–91.
[8] A. B. Lewko and B. Waters, “Decentralizing
attribute-based encryption,”in EUROCRYPT’11. Springer,
2011, pp. 568–588.
[9] S. Yu, C. Wang, K. Ren, and W. Lou, “Achieving
secure, scalable, and fine-grained data access control in
cloud computing,” in INFOCOM’10.IEEE, 2010, pp.
534–542.
[10] Liang-Ao Zhang et al. “ ABE based Access Control
with Authenticated Dynamic Policy Updating in Clouds”
International Journal of Security and Its Applications
Vol.9, No.8 (2015), pp.95-110
Figure 4: Login Form after polices update Big Data
http://dx.doi.org/10.14257/ijsia.2015.9.8.08
VI CONCLUSION Taniya Jain has published review research
papers in International Journal of Innovative
It is more efficient for data owners to only generate an Research in Engineering & Management
update key than generate a cipher text component for each (IJIREM),ISSN: 2350-0557, Volume-3,
attribute. Attribute-based access control schemes were Issue-4, July-2016.
Our research work on “On Secure Big Data
proposed to ensure the data confidentiality in the cloud. It Access Control Policy for Cloud Computing
allows data owners to define an access structure on Environment”. In other word, I analysis policy
attributes and encrypt the data under this access structure, updating technique in cloud environment.
such that data owners can define the attributes that the user
needs to possess in order to decrypt the cipher text.
However, the policy updating becomes a difficult issue
when applying ABE methods to construct access control
schemes, because once data owner outsource the data into
cloud, they won’t store in local systems.
REFERENCES
[1]Puya Ghazizadeh, Ravi Mukkamala & Stephan Olariu,
2013,“Data Integrity Evaluation in Cloud
Database-as-a-Service”, IEEE Ninth World Congress on
Services,978-0-7695-5024-4/13, DOI
0.1109/SERVICES.2013.40, pp.280-285.
[2] Ling Lang & Lin wang, 2012, “Research on cloud
computing and key technologies”, IEEE International
Conference on Computer Science and Information
Processing (CSIP), 978-1-4673-1411-4/12, pp.863-866
[3] Mohammed A. AlZain & Ben Soh and Eric Pardede,
2013, “A New Approach Using Redundancy Technique to
Improve Security in Cloud Computing”, pp. 230-235.
[4] V. Goyal, O. Pandey, A. Sahai, and B. Waters,
“Attribute-based encryption for fine-grained access control
of encrypted data,” in CCS’06. ACM, 2006, pp. 89–98.
[5] J. Bethencourt, A. Sahai, and B. Waters,
“Ciphertext-policy attributebased encryption,” in S&P’07.
IEEE, 2007, pp. 321–334.
Copyright © 2017. Innovative Research Publications. All Rights Reserve 256
Electronic copy available at: https://ssrn.com/abstract=3533276
You might also like
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Postprint: International 2018, Las Vegas, NV, USA, July 15-20, 2018.Document20 pagesPostprint: International 2018, Las Vegas, NV, USA, July 15-20, 2018.Mahi MalikNo ratings yet
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5794)
- 10, Mohallah Qazian Fazilpur, FAZILPUR, Rajanpur Rajanpur Parveen AkhtarDocument4 pages10, Mohallah Qazian Fazilpur, FAZILPUR, Rajanpur Rajanpur Parveen AkhtarMahi MalikNo ratings yet
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- Final Leave ModuleDocument5 pagesFinal Leave ModuleMahi MalikNo ratings yet
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (587)
- Vaccination CertificateDocument1 pageVaccination CertificateMahi MalikNo ratings yet
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- Arslan Aslam - Muhammad Aslam - 618891-SDA-2020 3240308399601 - 08-11-2005 3240342598151 Appearing StatusDocument3 pagesArslan Aslam - Muhammad Aslam - 618891-SDA-2020 3240308399601 - 08-11-2005 3240342598151 Appearing StatusMahi MalikNo ratings yet
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (895)
- Framing The Issues of Cloud Computing & Sustainability: A Design PerspectiveDocument6 pagesFraming The Issues of Cloud Computing & Sustainability: A Design PerspectiveMahi MalikNo ratings yet
- Q:1 Discuss in Details Classical and Modern Philosophies in Relation To EducationDocument7 pagesQ:1 Discuss in Details Classical and Modern Philosophies in Relation To EducationMahi MalikNo ratings yet
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- What Exactly Is A Classical Education?: Solution # 01Document9 pagesWhat Exactly Is A Classical Education?: Solution # 01Mahi MalikNo ratings yet
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- Sumaira MalikDocument1 pageSumaira MalikMahi MalikNo ratings yet
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- Silo - Tips - Environmental Conditions Big Data Management and Cloud Computing Analytics For Sustainable AgricultureDocument9 pagesSilo - Tips - Environmental Conditions Big Data Management and Cloud Computing Analytics For Sustainable AgricultureMahi MalikNo ratings yet
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (266)
- Allama Iqbal Open University, Islamabad ROLL # BX613798 Course Code: 8609 Student Name: Rana Saqib AminDocument6 pagesAllama Iqbal Open University, Islamabad ROLL # BX613798 Course Code: 8609 Student Name: Rana Saqib AminMahi MalikNo ratings yet
- Environmental Conditions' Big Data Management and Cloud Computing Analytics For Sustainable AgricultureDocument9 pagesEnvironmental Conditions' Big Data Management and Cloud Computing Analytics For Sustainable AgricultureMahi MalikNo ratings yet
- Hounor Boards of PRINCIPAL, DEO, CEO RAJANPURDocument4 pagesHounor Boards of PRINCIPAL, DEO, CEO RAJANPURMahi MalikNo ratings yet
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- Allama Iqbal Open UniversityDocument1 pageAllama Iqbal Open UniversityMahi MalikNo ratings yet
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- List of The Main Computer Science Research AreasDocument4 pagesList of The Main Computer Science Research AreasMahi MalikNo ratings yet
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (73)
- Directorate of Admission, Block 4 Allama Iqbal Open University, H-8 IslamabadDocument3 pagesDirectorate of Admission, Block 4 Allama Iqbal Open University, H-8 IslamabadMahi MalikNo ratings yet
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- Application FormDocument1 pageApplication FormMahi MalikNo ratings yet
- Board of IntermediateDocument1 pageBoard of IntermediateMahi MalikNo ratings yet
- Vacant Posts (GHSS Fazilpur)Document1 pageVacant Posts (GHSS Fazilpur)Mahi MalikNo ratings yet
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- Part-I Title of File: Form To Be Attached On Every File Cover Muhammad IzharDocument1 pagePart-I Title of File: Form To Be Attached On Every File Cover Muhammad IzharMahi MalikNo ratings yet
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- Exam Entrance Slip: Student ID: PasswordDocument1 pageExam Entrance Slip: Student ID: PasswordMahi MalikNo ratings yet
- ProjectDocument5 pagesProjectMahi MalikNo ratings yet
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2219)
- Final Research Paper (NCBA&E)Document13 pagesFinal Research Paper (NCBA&E)Mahi MalikNo ratings yet
- Result Gazette PSDF Programme (Industrial Training Programme 2018)Document41 pagesResult Gazette PSDF Programme (Industrial Training Programme 2018)Mahi MalikNo ratings yet
- Book 1Document3 pagesBook 1Mahi MalikNo ratings yet
- D.M SBDocument4 pagesD.M SBMahi MalikNo ratings yet
- Result & Discussion SectionDocument20 pagesResult & Discussion SectionMahi MalikNo ratings yet
- Wa0009 PDFDocument5 pagesWa0009 PDFMahi MalikNo ratings yet
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (119)
- Status of Water Filteration Plants Is District RajanpurDocument2 pagesStatus of Water Filteration Plants Is District RajanpurMahi MalikNo ratings yet
- Fast SSHDocument38 pagesFast SSHOcha PitalokaNo ratings yet
- Identity-Based Encryption With CloudDocument4 pagesIdentity-Based Encryption With CloudPidikiti Surendra BabuNo ratings yet
- Phrack Magazine Issue 65Document635 pagesPhrack Magazine Issue 65jmuzz100% (10)
- Java ProgramDocument6 pagesJava ProgramZuhadMahmoodNo ratings yet
- RFC 5996Document139 pagesRFC 5996karthik_chordzNo ratings yet
- Discrete Mathematics: Unit-I-Chapter-2 Algorithms-Integers-MatricesDocument100 pagesDiscrete Mathematics: Unit-I-Chapter-2 Algorithms-Integers-MatricesKhaja AhmedNo ratings yet
- STES SINHGAD INSTITUTE SHA1 ALGORITHM IMPLEMENTATION JAVADocument5 pagesSTES SINHGAD INSTITUTE SHA1 ALGORITHM IMPLEMENTATION JAVANIRANJAN KALENo ratings yet
- CTJV801 A Practical Public Key Encryption Scheme Based On Learning Parity With NoiseDocument11 pagesCTJV801 A Practical Public Key Encryption Scheme Based On Learning Parity With NoisebhasutkarmaheshNo ratings yet
- Paasch Week8 Isys406casestudyDocument2 pagesPaasch Week8 Isys406casestudyapi-502523030No ratings yet
- The VPN Menu - Endian UTM Appliance 2Document12 pagesThe VPN Menu - Endian UTM Appliance 2amelchorNo ratings yet
- Transmission Security Overview (SRAN11.1 - 02)Document21 pagesTransmission Security Overview (SRAN11.1 - 02)waelq2003No ratings yet
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
- Nod Serial NumberDocument6 pagesNod Serial NumberFirdha TaqiyyaNo ratings yet
- FDP 25-8-2020 - Avnk-SrinidhiDocument26 pagesFDP 25-8-2020 - Avnk-Srinidhisravan kodemNo ratings yet
- HIPAADocument69 pagesHIPAADucTriNo ratings yet
- Password Generator Visual Cryptography: UsingDocument13 pagesPassword Generator Visual Cryptography: Usingrao raoNo ratings yet
- Access ControlDocument40 pagesAccess ControlRamai Azami100% (4)
- MPESA API Test CasesDocument56 pagesMPESA API Test Casesoliro AmuriNo ratings yet
- Ticketing System Using AES Encryption Based QR CodeDocument6 pagesTicketing System Using AES Encryption Based QR Codeizralaimin02No ratings yet
- Mathematical Foundations of Public-Key CryptographyDocument27 pagesMathematical Foundations of Public-Key CryptographyKoukou MedNo ratings yet
- Certificate Validation Using BlockchainDocument4 pagesCertificate Validation Using BlockchainHarshikantNo ratings yet
- Security+ SY0-501 Exam ObjectivesDocument20 pagesSecurity+ SY0-501 Exam ObjectiveskasimNo ratings yet
- ABAP Connectivity - Web Services ABAPDocument18 pagesABAP Connectivity - Web Services ABAProsavilacaNo ratings yet
- VIKASHDocument1 pageVIKASHVivek PanwarNo ratings yet
- Intruders and intrusion techniquesDocument18 pagesIntruders and intrusion techniquesNikhil NerkarNo ratings yet
- Governance and Security Essentials in AWS: Telefonica - Eleven PathsDocument37 pagesGovernance and Security Essentials in AWS: Telefonica - Eleven PathspablogarlandeiraNo ratings yet
- Key Management LifecycleDocument55 pagesKey Management LifecycleSherif SalamaNo ratings yet
- Exemplary Logs To Identify BGP FailureDocument4 pagesExemplary Logs To Identify BGP FailuremandeepmailsNo ratings yet
- MCQ Question Bank-IS-1Document7 pagesMCQ Question Bank-IS-1Narender KumarNo ratings yet
- Enhancing Data Security Using Video Steganography (Advanced Encryption Standard Algorithm)Document21 pagesEnhancing Data Security Using Video Steganography (Advanced Encryption Standard Algorithm)R vinodNo ratings yet
- Thiết kế phần cứng xử lý giải thuật mã CRYSTALS-KyberDocument29 pagesThiết kế phần cứng xử lý giải thuật mã CRYSTALS-KyberThi PhamNo ratings yet
- Excel 2023: A Comprehensive Quick Reference Guide to Master All You Need to Know about Excel Fundamentals, Formulas, Functions, & Charts with Real-World ExamplesFrom EverandExcel 2023: A Comprehensive Quick Reference Guide to Master All You Need to Know about Excel Fundamentals, Formulas, Functions, & Charts with Real-World ExamplesNo ratings yet
- Learn Power BI: A beginner's guide to developing interactive business intelligence solutions using Microsoft Power BIFrom EverandLearn Power BI: A beginner's guide to developing interactive business intelligence solutions using Microsoft Power BIRating: 5 out of 5 stars5/5 (1)
- ChatGPT Millionaire 2024 - Bot-Driven Side Hustles, Prompt Engineering Shortcut Secrets, and Automated Income Streams that Print Money While You Sleep. The Ultimate Beginner’s Guide for AI BusinessFrom EverandChatGPT Millionaire 2024 - Bot-Driven Side Hustles, Prompt Engineering Shortcut Secrets, and Automated Income Streams that Print Money While You Sleep. The Ultimate Beginner’s Guide for AI BusinessNo ratings yet
- ChatGPT Side Hustles 2024 - Unlock the Digital Goldmine and Get AI Working for You Fast with More Than 85 Side Hustle Ideas to Boost Passive Income, Create New Cash Flow, and Get Ahead of the CurveFrom EverandChatGPT Side Hustles 2024 - Unlock the Digital Goldmine and Get AI Working for You Fast with More Than 85 Side Hustle Ideas to Boost Passive Income, Create New Cash Flow, and Get Ahead of the CurveNo ratings yet
- Change Management for Beginners: Understanding Change Processes and Actively Shaping ThemFrom EverandChange Management for Beginners: Understanding Change Processes and Actively Shaping ThemRating: 4.5 out of 5 stars4.5/5 (3)
- Designing Data-Intensive Applications: The Big Ideas Behind Reliable, Scalable, and Maintainable SystemsFrom EverandDesigning Data-Intensive Applications: The Big Ideas Behind Reliable, Scalable, and Maintainable SystemsRating: 5 out of 5 stars5/5 (6)
- Fundamentals of Data Engineering: Plan and Build Robust Data SystemsFrom EverandFundamentals of Data Engineering: Plan and Build Robust Data SystemsRating: 5 out of 5 stars5/5 (1)
- Excel for Beginners 2023: A Step-by-Step and Quick Reference Guide to Master the Fundamentals, Formulas, Functions, & Charts in Excel with Practical Examples | A Complete Excel Shortcuts Cheat SheetFrom EverandExcel for Beginners 2023: A Step-by-Step and Quick Reference Guide to Master the Fundamentals, Formulas, Functions, & Charts in Excel with Practical Examples | A Complete Excel Shortcuts Cheat SheetNo ratings yet