Professional Documents
Culture Documents
IBM Security Verify Privilege
Uploaded by
Youssif HassanCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
IBM Security Verify Privilege
Uploaded by
Youssif HassanCopyright:
Available Formats
PAM Implementation Documentation
Prepared for:
National Bank of Egypt (NBE)
ITS – NBE-EGY Confidential 1
INFORMATION TECHNOLOGY SOLUTIONS – ITS
26 ADEN ST., MOHANDESEEN, CAIRO, EGYPT
TEL: +202 37493773
FAX: +202 37493736
EMAIL: info@egypt-its.com
WEBSITE: HTTP://WWW.EGYPT-ITS.COM/
ITS – NBE-EGY Confidential 2
Contents
1. Installation............................................................................................................................. 4
2. Upload Licenses................................................................................................................... 17
3. Clustering ............................................................................................................................ 22
4. Rabbit MQ ........................................................................................................................... 42
5. Edit General Configurations ................................................................................................ 55
6. Active Directory Integration & sync with the groups ......................................................... 62
7. Enable Discovery ................................................................................................................. 70
8. Enable Heartbeat, Remote Password Changing ................................................................. 71
9. Unix Platform ...................................................................................................................... 72
11. Oracle Platform .................................................................................................................... 101
12. SQL Platform ......................................................................................................................... 131
11. Synchronize Secret Passwords During RPC .......................................................................... 162
12. Windows Platform ................................................................................................................ 145
13. Create Role & Assign it to users ............................................................................................ 171
14. Create Secret Policy to folders .............................................................................................. 174
15. Share secrets ......................................................................................................................... 176
16. Create Password Policy ......................................................................................................... 178
17. Upgrade Secret server & Privilege Manager Without Outbound Access ............................. 181
ITS – NBE-EGY Confidential 3
1. Installation
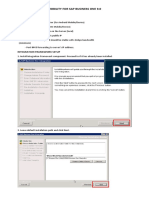
- Download the latest version of privilege vault.
- It is suggested that you run the setup.exe file as an administrator.
- Click next.
ITS – NBE-EGY Confidential 4
- Choose Connect to an existing SQL Server then click next.
ITS – NBE-EGY Confidential 5
- The Pre-Requisites page ensures that every prerequisite is set up
correctly.
- Listed prerequisites can be installed outside of the installer, but if
not, the installer can install and configure them by clicking fix Issues.
ITS – NBE-EGY Confidential 6
- Waiting until the required prerequisites installed.
- Click close.
ITS – NBE-EGY Confidential 7
- The tests run again with only two fails.
- Restart the server.
- Run setup.exe again then follow the above steps (until prerequisites
page).
ITS – NBE-EGY Confidential 8
- Click next.
ITS – NBE-EGY Confidential 9
- Enter server name or IP of SQL Server.
- Enter database name that created for PAM.
- Choose windows authentication using service account.
ITS – NBE-EGY Confidential 10
- Enter credentials of service account, click validate credentials.
- After validation is success, click next.
ITS – NBE-EGY Confidential 11
- Enter Username, Display name, Email, Password of the user that
will administer secret server.
- Click next.
ITS – NBE-EGY Confidential 12
- Click Skip Email. (we will edit email configuration from SS).
ITS – NBE-EGY Confidential 13
- Most settings are set to user defaults and they can still choose to
modify those settings.
- Click install.
ITS – NBE-EGY Confidential 14
- Waiting to finish install, click finish.
ITS – NBE-EGY Confidential 15
- Installation is complete and you can start by using both Secret and
Privilege Manager.
ITS – NBE-EGY Confidential 16
2. Upload Licenses
- Go to login page (https://plz-pamapp-v02.nbe.ahly.bank/secretserver).
- From Admin tab choose licenses.
- Click install new license.
- Click Bulk Entry Mode.
ITS – NBE-EGY Confidential 17
- Copy licenses & paste them here.
- Click Add multiple licenses.
- Click license activation.
ITS – NBE-EGY Confidential 18
- Enter name, email & phone number.
- Click Activate offline.
- Copy license request.
- Go to activation center.
ITS – NBE-EGY Confidential 19
- Paste in the activation request.
- Click activate.
ITS – NBE-EGY Confidential 20
- Copy the following activation confirmation.
- Paste it into corresponding screen within your secret server
instance.
- Click activate.
- Click continue.
ITS – NBE-EGY Confidential 21
3. Clustering
- From admin tab All.
- Click server nodes.
- Enable clustering.
ITS – NBE-EGY Confidential 22
- Go to path of secret server & copy inetpub folder from first node.
- Paste it in the second node & open IIS.
ITS – NBE-EGY Confidential 23
- Right click on application pool.
- Choose application pool.
- Enter name (SecretServerAppPool).
- Click ok.
ITS – NBE-EGY Confidential 24
- From sites default web site.
- Click add virtual directory.
- Enter alias (SecretServer).
- Enter physical path (D:\inetpub\wwwroot\SecretServer).
- Click ok.
ITS – NBE-EGY Confidential 25
- Right click on created directory (SecretServer).
- Click convert to application.
- Click select.
- From application pool, choose (SecretServerAppPool).
- Click connect as.
- Specific user then enters credentials of service account.
- Click ok.
ITS – NBE-EGY Confidential 26
- Click ok.
- Right click on SecretServerAppPool Advanced settings.
ITS – NBE-EGY Confidential 27
- Double click on application pool identity.
- Select custom account and click set.
ITS – NBE-EGY Confidential 28
- Enter username, password of service account.
- Click ok.
- The second node added successfully but disabled.
- Click on edit.
ITS – NBE-EGY Confidential 29
- Enable the in cluster, background worker, engine worker & session
recording worker.
- Click save.
- For TMS:
On the primary server, decrypt the connectionStrings.config file by
running the following command:
- Run CMD with as administrator:
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\aspnet_regiis.exe
-pd "connectionStrings" -app "/Tms"
- Select and copy all contents of the Privilege Manager web
application folder at:
D:\inetpub\wwwroot\TMS\
- Including the unencrypted connectionStrings.config file.
- On the secondary server, create the same folder path.
- Paste the entire contents of the Privilege Manager web application
folder from the primary web server to the similar location on the
secondary web server.
ITS – NBE-EGY Confidential 30
- Open Internet Information Services Manager (IIS).
- Under your local server, right-click Application Pools and select Add
Application Pool…
- Add three new application pools.
TMS
TMSAgent
TMSWorker.
- Make the same step for to create (TMS, TMSAgent & TMSWorker)
application pool.
ITS – NBE-EGY Confidential 31
- For each of the 3 app pools (TMS, TMSAgent & TMSWorker),
o right-click on each app pool,
o select Advanced Settings…
o then the Identity box in the “Process Model” section,
o click the three dots on the right of the box.
o Select the Custom Account radio button,
o Click Set, enter your service account’s name and password.
ITS – NBE-EGY Confidential 32
o Click ok.
o Right-click Default Web Site in IIS and select Add Virtual
Directory.
ITS – NBE-EGY Confidential 33
o Select an alias for your Privilege Manager. The alias is what will
be appended to the website.
For instance, “TMS” in http://myserver/TMS.
o Enter the physical directory where you unzipped Privilege
Manager (i.e., ‘D:\inetpub\wwwroot\TMS').
o Click OK.
o In the tree, right-click the new virtual directory and select Convert
to Application.
Set the Application Pool to the one called TMS.
Click OK.
ITS – NBE-EGY Confidential 34
o In the virtual directory expand the new TMS site,
Right click the Agent Subfolder and select Convert to
Application.
Set the Application Pool to the one called TMSAgent, click
OK.
o In the virtual directory navigate to the ServiceBus Subfolder.
Right-click and select Convert to Application.
Set the Application Pool to the one called TMSWorker you
created earlier, click OK.
o In the virtual directory select the Services Subfolder,
Right-click the new virtual directory and select Convert to
Application.
Ensure that the Application Pool is set to the one called TMS,
click OK.
o In the virtual directory select the Setup Subfolder,
Right-click the new virtual directory and select Convert to
Application.
Ensure that the Application Pool is set to the one called TMS,
click OK.
ITS – NBE-EGY Confidential 35
o In the virtual directory select the Worker Subfolder,
Right-click the new virtual directory and select Convert to
Application.
Set the Application Pool to the one called TMSWorker, click
OK.
o Select your TMS virtual directory.
Double-click Authentication in the features pane.
Make sure that only Anonymous Authentication is set to
Enabled. Everything else should be set to disabled.
ITS – NBE-EGY Confidential 36
o Select the Setup directory.
Double click Authentication in the features pane.
Make sure that Anonymous Authentication and Windows
Authentication are both set to Enabled and everything else is
disabled.
o Select the Worker.
Double-click Authentication in the features pane and make
sure that Anonymous Authentication and Windows
Authentication are both set to Enabled and everything else is
disabled.
ITS – NBE-EGY Confidential 37
o Folder Permissions to C:\Windows\Temp
Navigate to the C:\Windows\TEMP folder.
Right-click the folder and select Properties | Security |
Advanced.
Click Add and Select a principal.
Ensure the domain machine is listed as the Location and type
the service account into the Enter the object name to select
field.
Click Check Names and Enter network credentials for
accessing your domain machine.
Click OK.
Under Basic permissions, select the Modify checkbox.
ITS – NBE-EGY Confidential 38
Verify your service account has Modify, Read & execute, List
folder contents, Read, and Write permissions for the
C:\Windows\TEMP folder.
Click OK, then Apply.
o Folder Permissions to the Privilege Manager Application Folder
Navigate to the Privilege Manager application folder at
C:\inetpub\wwwroot\TMS.
Right-click the folder and select Properties | Security |
Advanced.
Select principal.
Ensure the domain machine is listed as the Location and type
the service account into the Enter the object name to select
field.
Click Check Names and Enter network credentials for
accessing your domain machine.
Click OK.
ITS – NBE-EGY Confidential 39
o Under Basic permissions, select the Modifycheckbox
Verify your service account has Modify, Read & execute, List
folder contents, Read, and Write permissions for the
C:\Windows\TEMP folder.
Click OK, then Apply.
o Note: The application folder only needs Write and Modify
permissions during the installation or during an upgrade. You can
remove these once the installation process is complete.
ITS – NBE-EGY Confidential 40
o Verify Login on Secondary Node
Navigate to Privilege Manager, ex: http://localhost/TMS.
You should be able to authenticate to Privilege Manager.
After logging in, all policies and all data accessible on the
primary node should be accessible on the secondary node.
o Re-encrypt ConnectionStrings.config
On the primary node, run the following command to re-
encrypt the connectionStrings.config file:
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\aspnet_regiis.exe
-pe "connectionStrings" -app "/Tms"
On the secondary node, run the same command to re-
encrypt the connectionStrings.config file:
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\aspnet_regiis.exe
-pe "connectionStrings" -app "/Tms"
ITS – NBE-EGY Confidential 41
4. Rabbit MQ
- From admin tab Distributed Engine.
- Click manage Site Connectors.
- Click New Site Connector
ITS – NBE-EGY Confidential 42
- Click to select Rabbit MQ in the Queue Type dropdown list.
- Type a name for your new site connector in the Name text box.
- Click to select the Active check box.
- Type the host name of the machine where you plan to install
RabbitMQ in the Host Name text box.
- Click to select Use SSL.
- Click the View Credentials.
- Click the copy icons to copy both the Username and Password and
store them for use in the next section.
- Click the OK button.
ITS – NBE-EGY Confidential 43
- Download the Thycotic RabbitMQ Helper.
- Install the Thycotic RabbitMQ helper by running the downloaded
MSI.
- Copy file of RabbitMQ to offline file.
ITS – NBE-EGY Confidential 44
- Go to RabbitMQ install location and open application.
- Run the below commands.
- $path = "$env:programfiles\Thycotic Software Ltd\RabbitMq Helper\Examples";
-
- $cred = Get-Credential -Message "Enter the initial RabbitMq user username and
password";
ITS – NBE-EGY Confidential 45
- Enter username and password which we have saved before.
- Enter fully qualified domain name in the PFX.
ITS – NBE-EGY Confidential 46
- Save location in attribute.
- Run mmc to get certificate.
ITS – NBE-EGY Confidential 47
- Select computer account.
- Export certificate in “cer” type.
ITS – NBE-EGY Confidential 48
- Export certificate in “PFX”.
- Enter password and confirm password.
ITS – NBE-EGY Confidential 49
- Click next.
- Click finish.
ITS – NBE-EGY Confidential 50
- Copy certificates to RabbitMQ location.
- Run this command to save certificate password
$pfxCred = Get-Credential -UserName PfxUserName -Message "Enter the PFX
password. Username is ignored";
- Enter the password.
ITS – NBE-EGY Confidential 51
- Run the RabbitMQ installation commands.
Install-Connector `
-Hostname $fqdn `
-Credential $cred `
-UseTls `
-CaCertPath "$certpath\localhostca.cer" `
-PfxPath "$certpath\localhost.pfx" `
-PfxCredential $pfxCred `
-OfflineErlangInstallerPath "$path\Offline\o-erlang.exe" `
-OfflineRabbitMqInstallerPath "$path\Offline\o-rabbitMq.exe" `
-Verbose
ITS – NBE-EGY Confidential 52
- Return to SS and go to the site connector you created in the
previous section.
- Click the site connector’s link. The Site Connector Details page
appears.
- Click the Validate Connectivity button.
- If everything is set up correctly, you will see “Validation Succeeded.”
ITS – NBE-EGY Confidential 53
- Close non-SSL connection
• Add “,{rabbit,[{tcp_listeners, []} ]} ” in file advanced.config as the
below.
ITS – NBE-EGY Confidential 54
5. Edit General Configurations
- Edit email configuration.
o Go to admin tab configuration email tab.
o Click edit.
o Enter email server & email address that will used by secret server
for notifications.
o Click save.
ITS – NBE-EGY Confidential 55
- Edit database backup configurations.
o Go to admin tab all setup & system maintenance.
o Click backup.
ITS – NBE-EGY Confidential 56
o Edit the paths of backup files.
o Click save.
o Enable backup to schedule & repeat every 1 day.
ITS – NBE-EGY Confidential 57
- Enable & edit session recording configurations.
o Go to admin tab configuration session recording tab.
o Click edit.
o Check the box of enable session recording.
ITS – NBE-EGY Confidential 58
o Edit the configuration as the above screenshots.
o Click save.
ITS – NBE-EGY Confidential 59
- Edit X-Forwarded-For (load balancer).
o Open IIS Manager.
o On server, site or application level, double click “Logging”.
ITS – NBE-EGY Confidential 60
o Click “Select Fields”.
o In “W3C Logging Fields” window, click “Add Field“.
o In the “Add Custom Field” window, fill out the following fields:
Field Name: X-Forwarded-For
Source type: Request Header
Source: X-Forwarded-For.
o Click “OK” in both open windows.
o Click “Apply” in the actions pane.
- Go to https://<SecretServerAddress>/ConfigurationAdvanced.aspx.
- Scroll to the bottom and click Edit.
- Locate the IP Address Header text box, type X-Forwarded-For.
- Click the Save button.
ITS – NBE-EGY Confidential 61
6. Active Directory Integration & sync with the groups
First, we need to create a secret to use it in synchronization.
- Choose secrets in the left panel.
- Click on (+) in the top right.
- Click new secret.
- Click on active directory account.
ITS – NBE-EGY Confidential 62
- Choose folder.
- Enter secret name, domain, username & password.
- Click create secret.
ITS – NBE-EGY Confidential 63
Second, enable active directory to integration & add a domain:
- From admin tab Active directory.
- Click edit.
- Enable Active directory integration.
- Enable sync. of active directory.
- From user account options choose user status mirror active
directory.
- Click save.
ITS – NBE-EGY Confidential 64
- Click edit domains.
- Click new.
ITS – NBE-EGY Confidential 65
- Enter fully qualified domain name & friendly/NETBIOS name.
- Check active & allow logins from domain.
- Add secret that we have created above.
- Form site drop list, select local.
- Click save & validate.
ITS – NBE-EGY Confidential 66
Third, Synchronize group of PAM users:
- From admin Active Directory.
- Edit synchronization.
- Choose your domain from drop list.
- Search for the groups.
- Can preview users of each group from left panel.
ITS – NBE-EGY Confidential 67
- Select the groups & then bring it to left panel.
- Click save.
- Click synchronize now.
ITS – NBE-EGY Confidential 68
- Go to users from admin tab.
- You can see the users that synchronized from the group.
ITS – NBE-EGY Confidential 69
7. Enable Discovery
- From admin Discovery.
- Click edit.
- Enable discovery.
- Click save.
ITS – NBE-EGY Confidential 70
8. Enable Heartbeat, Remote Password Changing
- From admin remote password changer.
- Click edit.
- Check the box of enable remote password changing.
- Check the box of heartbeat.
- Click save.
ITS – NBE-EGY Confidential 71
9. Unix Platform
1. Create folder structure from adaption strategy.
o Choose secrets in the left panel.
o Click on (+) in the top right.
o Click on new folder.
o Enter name of the folder.
o Click create new folder.
ITS – NBE-EGY Confidential 72
o Click right button on root folder (Unix Platform).
o Choose add subfolder.
o Enter the name of subfolder.
o Click create new folder.
Note: Follow the above steps to create the folder structure as adaption
strategy.
ITS – NBE-EGY Confidential 73
2. Create a secret with user credentials that have permissions to
discovery & takeover accounts on the target server.
o Choose secrets in the left panel.
o Click on (+) in the top right.
o Click new secret.
o Click change.
ITS – NBE-EGY Confidential 74
o Choose the folder where you want to create secret in it.
ITS – NBE-EGY Confidential 75
o Choose the UNIX Account as a secret template.
o Enter the secret name, machine address & credentials of the user
that will be used in the discovery & takeover.
o Click create secret.
ITS – NBE-EGY Confidential 76
3. Add new UNIX discovery source & run discovery.
o From admin tab discovery.
o Click edit discovery sources.
o Click create new.
o Choose UNIX discovery source.
o Click ok.
ITS – NBE-EGY Confidential 77
o Click next.
o Enter the discovery source name.
o Click next.
ITS – NBE-EGY Confidential 78
o Click add secret.
o Choose the created secret that will used to discover accounts.
ITS – NBE-EGY Confidential 79
o After the secret added.
o Click finish.
o Then from admin tab discovery.
o Click run now.
o Then go to discovery network view.
ITS – NBE-EGY Confidential 80
o Click on the discovery source to view accounts that found on the
target machine.
4. Create new RPC for takeover.
o From admin tab remote password change.
o Click configure password changers.
ITS – NBE-EGY Confidential 81
o Click new.
o Choose base password changer as UNIX Account custom.
o Enter the name of the password changer.
o Click save.
ITS – NBE-EGY Confidential 82
o Enter the fields of username & passwords in verify password
changed commands section then click save.
o Enter the fields of username & passwords in password change
commands section then click save.
o Enter the above commands.
ITS – NBE-EGY Confidential 83
5. Create new secret templates of UNIX platform.
o From admin tab secret template.
o Click create new.
o Enter the name of the secret template.
o Click create.
ITS – NBE-EGY Confidential 84
o In the fields section we need to add the fields as the below.
o Click configure extended mappings.
ITS – NBE-EGY Confidential 85
o Choose the extended mapping to use SSH private key.
o Choose the fields of private key & private key passphrase.
o Click save.
Note: we need to do all the above steps to create the secret templates
that found in the adaption strategy for UNIX platform.
ITS – NBE-EGY Confidential 86
6. Assign the custom RPC to the created secret template.
o From secret template (for example: service_Accounts)
o Click configure password changing.
ITS – NBE-EGY Confidential 87
o Click edit.
o Choose the RPC from password type drop list.
o Click save.
ITS – NBE-EGY Confidential 88
7. Create UNIX team launchers.
o From admin tab secret templates.
o Configure launchers.
o Click new.
o Use the below configurations for the required launchers for UNIX
teams.
ITS – NBE-EGY Confidential 89
o Kitty
o SuperPutty
ITS – NBE-EGY Confidential 90
o WinSCP
o Mobaxterm
ITS – NBE-EGY Confidential 91
8. Configure launchers to secret template.
o From admin tab secret templates.
o Choose the secret templates that you want to add launchers to it.
o Click edit.
o Click configure launcher.
ITS – NBE-EGY Confidential 92
o Add new launcher.
o Choose the launcher type you want (example: kitty).
o Click save.
Note: you will need to do all the above steps to all needed launchers for
UNIX platform.
ITS – NBE-EGY Confidential 93
9. Create secret policies of UNIX platform.
o From admin tab secret policy.
o Click create new.
o Use the below configurations for the secret policies of UNIX
teams.
ITS – NBE-EGY Confidential 94
o NBE_ROOT_UNIX_Policy
o NBE_Service_accounts_Policy
ITS – NBE-EGY Confidential 95
o NBE_UNIX_Admin_Department
ITS – NBE-EGY Confidential 96
10. Takeover an account
o From admin discovery.
o Click on discovery network source.
o Click on the discovery source where the user that you want to
takeover.
o Search for the user you want to takeover.
o Select the user then click import.
ITS – NBE-EGY Confidential 97
o Choose the secret type from the drop list.
o Select the folder where you want to create this secret.
o Click next.
o Check (I want to change the password on the account & I want a
new random password for each created secret).
o Click next.
ITS – NBE-EGY Confidential 98
o Choose the password type from drop list.
o Select the secret to be used for taking over the account.
o Click next.
ITS – NBE-EGY Confidential 99
o Select the secret to be used for future password changing.
o Click finish.
o Secret created successfully.
ITS – NBE-EGY Confidential 100
11. Oracle Platform
1. Create folder structure from adaption strategy.
o Choose secrets in the left panel.
o Click on (+) in the top right.
o Click on new folder.
o Enter name of the folder.
o Click create new folder.
ITS – NBE-EGY Confidential 101
o Click right button on root folder (Oracle Platform).
o Choose add subfolder.
o Enter the name of subfolder.
o Click create new folder.
Note: Follow the above steps to create the folder structure as adaption
strategy.
ITS – NBE-EGY Confidential 102
2. Create a secret with user credentials that have permissions to
discovery & takeover accounts on the target server.
o Choose secrets in the left panel.
o Click on (+) in the top right.
o Click new secret.
o Click change.
ITS – NBE-EGY Confidential 103
o Choose the folder where you want to create secret in it.
o Choose the Oracle Account as a secret template.
o Enter the secret name, machine address & credentials of the user
that will be used in the discovery & takeover.
o Click create secret.
ITS – NBE-EGY Confidential 104
3. Create a custom discovery for oracle accounts.
o From admin scripts.
o Create new.
o Enter name & description.
o Choose dependency from category drop list.
o Paste the script-to-script field.
ITS – NBE-EGY Confidential 105
o From admin tab discovery extensible discovery.
o Click configure discovery scanners.
o Click on accounts.
o Click create new scanner.
ITS – NBE-EGY Confidential 106
o Use the above setting to add new scanner.
o Click ok.
ITS – NBE-EGY Confidential 107
4. Create custom scan template for oracle.
o From admin discovery extensible discovery.
o Click configure scan templates.
o Click accounts tab.
o Click create new scan templates.
ITS – NBE-EGY Confidential 108
o Enter the name of scan type.
o Add the above fields.
o Click save.
ITS – NBE-EGY Confidential 109
5. Create new discovery source & run discovery.
o From admin tab discovery.
o Click edit discovery sources.
o Click create new.
o Choose UNIX discovery source.
o Click ok.
ITS – NBE-EGY Confidential 110
o Click next.
o Enter name of discovery source.
o Click next.
ITS – NBE-EGY Confidential 111
o Enter IP of target machine.
o Click next.
o Click add secret.
ITS – NBE-EGY Confidential 112
o Choose the created secret that will used to discover accounts.
o After the secret added.
o Click finish.
ITS – NBE-EGY Confidential 113
o Click on the created discovery source.
o Remove the Unix Non-Daemon User.
o Click add new account scanner.
ITS – NBE-EGY Confidential 114
o Choose oracle by database scanner.
o Choose:
First secret (user that can run script on the server).
Second secret (user that have permissions for discovery).
o Then from admin tab discovery.
ITS – NBE-EGY Confidential 115
o Click run now.
o Then go to discovery network view.
o Click on the discovery source to view accounts that found on the
target machine.
ITS – NBE-EGY Confidential 116
6. Create new secret templates of Oracle platform.
o From admin tab secret template.
o Click create new.
o Enter the name of the secret template.
o Click create.
ITS – NBE-EGY Confidential 117
o In the fields section we need to add the fields as the below.
o The secret template created successfully.
Note: we need to do all the above steps to create the secret templates
that found in the adaption strategy for Oracle platform.
ITS – NBE-EGY Confidential 118
7. Create Oracle team launchers.
o From admin tab secret templates.
o Click edit.
o Configure launchers.
o Use the below configurations for the required launchers for UNIX
teams.
ITS – NBE-EGY Confidential 119
o SQL-Plus
o PL-SQL Developer
ITS – NBE-EGY Confidential 120
o SQL Developer
o CMD
ITS – NBE-EGY Confidential 121
o PowerShell
ITS – NBE-EGY Confidential 122
8. Configure launchers to secret template.
o From admin tab secret templates.
o Choose the secret templates that you want to add launchers to it.
o Configure launchers.
o Click add new launcher.
ITS – NBE-EGY Confidential 123
o Choose the launcher type you want (example: sql-plus).
o Click save.
Note: you will need to do all the above steps to all needed launchers for
Oracle platform.
ITS – NBE-EGY Confidential 124
9. Create secret policies of Oracle platform.
o From admin tab secret policy.
o Click create new.
o Use the below configurations for the secret policies of Oracle
teams.
ITS – NBE-EGY Confidential 125
o NBE_SYS_DBA_Recording_Policy.
o NBE_Service_accounts_Policy
ITS – NBE-EGY Confidential 126
10. Takeover an account
o From admin discovery.
o Click on discovery network source.
o Click on the discovery source where the user that you want to
takeover.
o Search for the user you want to takeover.
o Select the user then click import.
ITS – NBE-EGY Confidential 127
o Choose the secret type from the drop list.
o Select the folder where you want to create this secret.
o Click next.
o Check (I want to change the password on the account & I want a
new random password for each created secret).
o Click next.
ITS – NBE-EGY Confidential 128
o Choose the password type from drop list.
o Select the secret to be used for taking over the account.
o Click next.
ITS – NBE-EGY Confidential 129
o Select the secret to be used for future password changing.
o Click finish.
ITS – NBE-EGY Confidential 130
12. SQL Platform
1. Create folder structure from adaption strategy.
o Choose secrets in the left panel.
o Click on (+) in the top right.
o Click on new folder.
o Enter name of the folder.
o Click create new folder.
ITS – NBE-EGY Confidential 131
o Click right button on root folder (MS-SQL Platform).
o Choose add subfolder.
o Enter the name of subfolder.
o Click create new folder.
Note: Follow the above steps to create the folder structure as adaption
strategy.
ITS – NBE-EGY Confidential 132
2. Create a secret with user credentials that have permissions to
discovery & takeover accounts on the target server.
o Choose secrets in the left panel.
o Click on (+) in the top right.
o Click new secret.
o Click change.
ITS – NBE-EGY Confidential 133
o Choose the folder where you want to create secret in it.
o Choose the Active Directory Account as a secret template.
ITS – NBE-EGY Confidential 134
o Enter the secret name, machine address & credentials of the user
that will be used in the discovery & takeover.
o Click create secret.
ITS – NBE-EGY Confidential 135
3. Create a custom discovery for SQL accounts.
o From admin scripts.
o Create new.
o Enter name & description.
o Choose dependency from category drop list.
o Paste the script-to-script field.
ITS – NBE-EGY Confidential 136
o From admin tab discovery extensible discovery.
o Click configure discovery scanners.
o Click on accounts.
o Click create new scanner.
ITS – NBE-EGY Confidential 137
o Use the above setting to add new scanner.
o Click ok.
ITS – NBE-EGY Confidential 138
4. Create new discovery source & run discovery.
o From admin tab discovery.
o Click edit discovery sources.
o Choose active directory discovery source.
o Choose scanner settings.
- Click add new account scanner.
- Then choose the SQL Local Accounts.
- Click run now.
ITS – NBE-EGY Confidential 139
5. Configure launchers to secret template.
o From admin tab secret templates.
o Choose the secret templates that you want to add launchers to it.
o Click edit.
o Configure launcher.
ITS – NBE-EGY Confidential 140
o Click add new launcher.
o Choose the launcher type you want (example: RDP).
o Click save.
Note: you will need to do all the above steps to all needed launchers for
Windows platform.
ITS – NBE-EGY Confidential 141
6. Create secret policies of SQL platform.
o From admin tab secret policy.
o Click create new.
o Use the below configurations for the secret policies of SQL
teams.
o NBE_SQL_SA_Policy
ITS – NBE-EGY Confidential 142
o NBE_SQL_SYS_ADMIN_Policy
o NBE_Service_accounts_Policy
ITS – NBE-EGY Confidential 143
7. Takeover an account
o From admin discovery.
o Click on discovery network source.
o Click on the discovery source where the user that you want to
takeover.
o Search for the user you want to takeover.
o Select the user then click import.
o Choose the secret type from the drop list (Active Directory
Account).
o Select the folder where you want to create this secret.
o Click next.
o Check (I want to change the password on the account & I want a
new random password for each created secret).
o Click next.
o Choose the password type from drop list (Active Directory
Account).
o Select the secret to be used for taking over the account.
o Click next.
o Select the secret to be used for future password changing.
o Click finish.
ITS – NBE-EGY Confidential 144
12. Windows Platform
1. Create folder structure from adaption strategy.
o Choose secrets in the left panel.
o Click on (+) in the top right.
o Click on new folder.
o Enter name of the folder.
o Click create new folder.
ITS – NBE-EGY Confidential 145
o Click right button on root folder (Windows Platform).
o Choose add subfolder.
o Enter the name of subfolder.
o Click create new folder.
Note: Follow the above steps to create the folder structure as adaption
strategy.
ITS – NBE-EGY Confidential 146
2. Create a secret with user credentials that have permissions to
discovery & takeover accounts on the target server.
o Choose secrets in the left panel.
o Click on (+) in the top right.
o Click new secret.
o Click change.
ITS – NBE-EGY Confidential 147
o Choose the folder where you want to create secret in it.
o Choose the Active Directory Account as a secret template.
ITS – NBE-EGY Confidential 148
o Enter the secret name, machine address & credentials of the user
that will be used in the discovery & takeover.
o Click create secret.
ITS – NBE-EGY Confidential 149
3. Create new discovery source & run discovery.
o From admin tab discovery.
o Click edit discovery sources.
o Create new.
ITS – NBE-EGY Confidential 150
o Choose Active Directory Discovery Source.
o Click next.
ITS – NBE-EGY Confidential 151
o Choose windows local accounts.
o Click next.
o Enter fully qualified domain name.
o Choose the created secret.
o Click next.
ITS – NBE-EGY Confidential 152
o Click finish.
- Click run now.
- Go to discovery network view.
ITS – NBE-EGY Confidential 153
o You can see your discovery sources and the users of each one.
o Search for specific user from search indexer.
ITS – NBE-EGY Confidential 154
4. Configure launchers to secret template.
o From admin tab secret templates.
o Choose the secret templates that you want to add launchers to it.
o Click edit.
o Configure launchers.
ITS – NBE-EGY Confidential 155
o Click add new launcher.
o Choose the launcher type you want (example: RDP).
o Click save.
Note: you will need to do all the above steps to all needed launchers for
Windows platform.
ITS – NBE-EGY Confidential 156
5. Create secret policies of Windows platform.
o From admin tab secret policy.
o Click create new.
o Use the below configurations for the secret policies of Oracle
teams.
o NBE_Domain_Recording_Policy
ITS – NBE-EGY Confidential 157
o NBE_Service_Accounts_Policy
ITS – NBE-EGY Confidential 158
6. Takeover an account
o From admin discovery.
o Click on discovery network source.
o Click on the discovery source where the user that you want to
takeover.
o Search for the user you want to takeover.
o Select the user then click import.
o Choose the secret type from the drop list.
o Select the folder where you want to create this secret.
o Click next.
ITS – NBE-EGY Confidential 159
o Check (I want to change the password on the account & I want a
new random password for each created secret).
o Click next.
o Choose the password type from drop list.
o Select the secret to be used for taking over the account.
o Click next.
ITS – NBE-EGY Confidential 160
o Select the secret to be used for future password changing.
o Click finish.
ITS – NBE-EGY Confidential 161
11. Synchronize Secret Passwords During RPC
- Download this tool from
“http://updates.thycotic.net/tools/powershell.wellnesschecker.zip”.
- Extract it.
- Open a command window in the extracted directory and run this
command “PowerShell.WellnessChecker.exe –fixerrors”.
- From Admin Scripts.
- Click create new.
ITS – NBE-EGY Confidential 162
- Enter name & description.
- Choose dependency from category drop list.
- Put the below script in the script field.
$url = 'http://MySecretServerURL/webservices/sswebservice.asmx';
$username = $Args[0]
$password = $Args[1]
$newpassword = $Args[2]
$secretIdArray = $Args[3]
$domain = $Args[4]
$proxy = New-WebServiceProxy -uri $url -UseDefaultCredential
$result1 = $proxy.Authenticate($username, $password, '', $domain)
if ($result1.Errors.length -gt 0){
$errors = $result1.Errors[0]
Write-Debug "Errors result1: $errors"
exit
} else {
$token = $result1.Token
}
$secretIds = $secretIdArray -split ","
foreach($secretId in $secretIds){
$result2 = $proxy.GetSecret($token, $secretId, $false, $null)
if ($result2.Errors.length -gt 0){
$errors = $result2.Errors[0]
Write-Debug "Errors result2: $errors"
} else {
$secretName = $result2.Secret.Name
Write-Debug "Updating Secret: $secretName"
foreach ($item in $result2.Secret.Items) {
if($item.IsPassword) {
$item.Value = $newpassword
}
}
$secret = $result2.Secret
$result3 = $proxy.UpdateSecret($token, $secret)
if ($result3.Errors.length -gt 0) {
$errors = $result3.Errors[0]
ITS – NBE-EGY Confidential 163
Write-Debug "Errors result3: $errors"
} else {
Write-Debug "Updated Secret: $secretName"
}
}
}
- Click ok.
- Admin Configuration and set Enable Webservices to Yes.
ITS – NBE-EGY Confidential 164
- Create user account as Application Account.
- Create role for API_Account user.
ITS – NBE-EGY Confidential 165
- Assign role to user.
- Create a secret with the Secret Server credentials for the new
API User Account (template works well as Active Directory or Web
Password).
ITS – NBE-EGY Confidential 166
- On each of the child Secrets grant the API User Account Edit
Permission on the Secrets.
- From admin tab remote password changer.
- Click the Configure Dependency Changers button.
ITS – NBE-EGY Confidential 167
- Create a new changer using the below settings.
- For the Arguments field, paste the following:
$[1]$USERNAME $[1]$PASSWORD $PASSWORD $NOTES $[1]$DOMAIN
- Click save.
ITS – NBE-EGY Confidential 168
- Go the Primary Account Secret and on the Dependencies tab.
- Click create add New Dependency Group.
ITS – NBE-EGY Confidential 169
- Choose your template, and under Service/Machine name put
"default". Select a Privileged Account (active directory account
secret able to run PowerShell on the Server).
Notes:
- Ensure that the Child Secret IDs are listed comma separated in your
Parent Secret's Notes field.
- Now the Dependency has been added and the full process can be
tested by kicking a Password Change off on the Primary Account
Secret.
ITS – NBE-EGY Confidential 170
13. Create Role & Assign it to users
- From admin tab Roles.
- Click Create New
ITS – NBE-EGY Confidential 171
- Enter Role Name for example:
o “NBE_Uinux_Admins_SSH”.
- Select form left panel (permissions unassigned) to right panel
(permission assigned) for example :
o “View Folders ,View Secrets”.
- Click save.
- Then assign the role to user.
- Click assign roles.
ITS – NBE-EGY Confidential 172
- Select role name in Role.
- Click edit.
- Select users from right panel (unassigned) to left panel (assigned).
- Click save changes.
ITS – NBE-EGY Confidential 173
14. Create Secret Policy to folders
- From admin folders.
- Choose the folder that you will assign the secret policy to.
- Click edit.
ITS – NBE-EGY Confidential 174
- Select secret policy from drop list.
- Click save.
ITS – NBE-EGY Confidential 175
15. Share secrets
- Go to any secret that you want to share it.
- Click on sharing tab.
- In shared with section, you can see the users which the secret
shared with. (to edit in it, you must disable inherit from folder option)
- Also, can see that the secret inherits permissions from folder.
- To edit in these properties, click edit.
ITS – NBE-EGY Confidential 176
- After we click edit & uncheck box of inherit permissions from folder.
- We can search for the user that you want to share secret with.
- Click save.
ITS – NBE-EGY Confidential 177
16. Create Password Policy
- Form admin Secret Templates.
- Click A Character Sets.
- Enter name of the list of characters that you will use in password
policy.
- Enter the characters in CHARACTER SET field.
- Click in add icon to save.
- Click back.
ITS – NBE-EGY Confidential 178
- Click the Password Requirements.
- Click the Create New
- Type the name and description.
- If you want the requirement to become the new default, click to
select the Is Default check box.
- Set the general options for the requirement in the Generate
Password section.
- Add one or more password rules:
• Click to select the type of rule in the first dropdown list in the
Password Rules section.
• Set that type’s parameter in the following text box.
• Click to select the character set from the “from” dropdown list.
• Click the + icon to save the rule.
- Click save.
ITS – NBE-EGY Confidential 179
- To set a custom password requirement for a specific secret, use the
“Customize Password Requirement” in the Security tab of a secret.
- You can enable or disable the validation of manually entered
passwords at the secret template level via the “Validate Password
Requirements on Create” and “Validate Password Requirements on
Edit” settings.
ITS – NBE-EGY Confidential 180
17. Upgrade Secret server & Privilege Manager Without Outbound Access
- Stop the application pool on the second node.
- From a computer that does have outbound network access and Secret Server
access, go to the Secret Server Upgrade page by browsing to:
http://<yourinstance>/Installer.aspx?patch=true (filling in your Secret Server
URL for <yourinstance>). The wizard appears:
- Click enable maintenance mode.
- Click backup.
- Click the Continue button. The next page appears:
ITS – NBE-EGY Confidential 181
- Download the latest version .zip file by clicking the Download Latest Version
button on the installer page. The file name will appear something like
Version_10_2_000000.zip. Note where you save it.
- Click the Choose File button & select the Secret Server .zip file you just
downloaded.
- Click the Upload Upgrade File button.
ITS – NBE-EGY Confidential 182
- Click install this version.
- After installation done, the above screenshot appears.
ITS – NBE-EGY Confidential 183
- Navigate to the TMS web folder (D:\inetpub\wwwroot\TMS\).
- Open web.config file with Notepad with Administrator.
Update the “value” field of this item :
<add key="nuget:source:SolutionCentre" value="http://tmsnuget.thycotic.com/nuget/" />
to C:\ProgramData\NugetCache\, such as:
<add key="nuget:source:SolutionCentre"value="C:\ProgramData\NugetCache\" />
- Save the web.config file.
- Recycle the TMS app pools.
- Navigate to https://<webserver>/TMS/Setup/ProductOptions/ShowProducts.
- Click the Install/Upgrade Products button.
- Wait until installation finished.
ITS – NBE-EGY Confidential 184
- Once upgraded and working, copy the SecretServer folder (without the
database.config or the encryption.config files) & TMS Folder (without the
connectionstrings.config file) to all secondary servers, and replace the content
of the existing Web application folder with the new.
- Without the database.config or the encryption.config files.
ITS – NBE-EGY Confidential 185
- Without the connectionstrings.config file.
- Disable maintenance mode.
- Start application pool in the second node.
- Upgrade done.
ITS – NBE-EGY Confidential 186
You might also like
- IBM WebSphere Application Server Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesFrom EverandIBM WebSphere Application Server Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesNo ratings yet
- Setting Up The VMWare ImageDocument26 pagesSetting Up The VMWare ImageNikolaNo ratings yet
- IMS-ZXUN CG-BC-EN-Installation and Commissioning-Software Installation Guide-1-201011-PPT-102Document102 pagesIMS-ZXUN CG-BC-EN-Installation and Commissioning-Software Installation Guide-1-201011-PPT-102BSSNo ratings yet
- Siemonster v4 Demo Build Guide v12Document14 pagesSiemonster v4 Demo Build Guide v12Amine NedjadiNo ratings yet
- Tutorial 5Document8 pagesTutorial 5Nam BuiNo ratings yet
- Sir Padampat Singhania University: Server Administration Lab FileDocument11 pagesSir Padampat Singhania University: Server Administration Lab FileIndrasena ReddyNo ratings yet
- SiemensDocument8 pagesSiemenskhaldoun samiNo ratings yet
- ZKBioSecurity Installation GuideV1.1 - 20160222Document17 pagesZKBioSecurity Installation GuideV1.1 - 20160222Srinivas ChanderNo ratings yet
- IMS-ZXUN CG-BC-EN-Installation and Commissioning-Software Installation-1-201010-PPT-98newDocument98 pagesIMS-ZXUN CG-BC-EN-Installation and Commissioning-Software Installation-1-201010-PPT-98newBSSNo ratings yet
- Sir Padampat Singhania University: Server Administration Lab FileDocument11 pagesSir Padampat Singhania University: Server Administration Lab FileIndrasena ReddyNo ratings yet
- HF Security Smart-Pass - Installation Instructions - 1.5.9 - 20220304Document28 pagesHF Security Smart-Pass - Installation Instructions - 1.5.9 - 20220304Kristoffer OrdonaNo ratings yet
- Av InstallationDocument39 pagesAv InstallationNILESHNo ratings yet
- 3 - 0-Software-Ver2 0Document14 pages3 - 0-Software-Ver2 0Ismael VaiNo ratings yet
- Ansys Licensing FaqDocument11 pagesAnsys Licensing Faqadmin GRNNo ratings yet
- Complete Pangya Setup Guide v1.2Document24 pagesComplete Pangya Setup Guide v1.2BananaspiltNo ratings yet
- WWW Pingtrip Com Weblog 2008 09 Installing-hacme-bank-On-xp-proDocument4 pagesWWW Pingtrip Com Weblog 2008 09 Installing-hacme-bank-On-xp-proCeles NubesNo ratings yet
- License With Server DongleDocument10 pagesLicense With Server DongleEmerson GrossNo ratings yet
- IBM Maximo Asset Management Installation GuideDocument76 pagesIBM Maximo Asset Management Installation Guideerick_coNo ratings yet
- SOP For HYPER-VDocument11 pagesSOP For HYPER-Vpavan4india8381No ratings yet
- Mobility For Sap Business One 9.0: Integration Framework SetupDocument13 pagesMobility For Sap Business One 9.0: Integration Framework SetupRobeth John BacalanNo ratings yet
- KS2008 Harrington-Training With Celerra SimulatorDocument26 pagesKS2008 Harrington-Training With Celerra SimulatorMinhajuddin MohammedNo ratings yet
- Deep Security - DS - 8.0 - PSTL - v1.9Document74 pagesDeep Security - DS - 8.0 - PSTL - v1.9Massimo GampoliNo ratings yet
- Project CCIT 1Document32 pagesProject CCIT 1Setyo Aji WibowoNo ratings yet
- How To Install and Gather Logs On Windows Systems With SupportAssist EnterpriseDocument11 pagesHow To Install and Gather Logs On Windows Systems With SupportAssist EnterpriseVicente JuniorNo ratings yet
- SCCM NotesDocument6 pagesSCCM NotesasegunloluNo ratings yet
- Extra - Exercises Unistall InformixDocument14 pagesExtra - Exercises Unistall InformixМихаи БонцалоNo ratings yet
- DM600 - TranSend II Installation GuideDocument12 pagesDM600 - TranSend II Installation GuideSergio BuenoNo ratings yet
- SL 10317Document22 pagesSL 10317emcviltNo ratings yet
- Network and Security Lab Report: Lab 4.1: Installing Certificate ServicesDocument67 pagesNetwork and Security Lab Report: Lab 4.1: Installing Certificate Serviceslucifer thomasNo ratings yet
- Installation IsoDocument18 pagesInstallation IsoSam SwitchNo ratings yet
- Install and Configure EMC SMI-S Provider and Solutions EnablerDocument9 pagesInstall and Configure EMC SMI-S Provider and Solutions EnablerallanonNo ratings yet
- Sci A Install Manu AllDocument1 pageSci A Install Manu AllBelak1No ratings yet
- SPP 10.1.3 Hands-On Lab Guide Eng.r2 PDFDocument53 pagesSPP 10.1.3 Hands-On Lab Guide Eng.r2 PDFAndres HerediaNo ratings yet
- Vsphere ICM7 Lab 19Document20 pagesVsphere ICM7 Lab 19AlvinMoralesNo ratings yet
- SCCM NotesDocument6 pagesSCCM NotesNsrk KrishnaNo ratings yet
- 1 Setup Azure VPN ClientDocument20 pages1 Setup Azure VPN ClientskmillosNo ratings yet
- Netapp Simulator InstallDocument6 pagesNetapp Simulator InstallManish MauryaNo ratings yet
- VCP 6 5 TrainingDocument15 pagesVCP 6 5 TrainingRoel MagistradoNo ratings yet
- Install SAP Gateway on Windows NTDocument6 pagesInstall SAP Gateway on Windows NTWilder Ortiz VelasquezNo ratings yet
- Eltek Multisite Monitor 2.3.1 Installation ManualDocument4 pagesEltek Multisite Monitor 2.3.1 Installation ManualAsif Majeed MalikNo ratings yet
- Installing Guardium in A Virtual MachineDocument6 pagesInstalling Guardium in A Virtual MachineMohsin AliNo ratings yet
- Install and Configure SUSE Linux and SAP NetWeaverDocument49 pagesInstall and Configure SUSE Linux and SAP NetWeaverrajesh98765No ratings yet
- Window ServerDocument25 pagesWindow ServersohaibchNo ratings yet
- CA Identity Suite 14.x: Implementation - Install The Components 200Document44 pagesCA Identity Suite 14.x: Implementation - Install The Components 200Steven AvilaNo ratings yet
- Examen Password SafeDocument17 pagesExamen Password SafeheisembergNo ratings yet
- Dot1x ISE Lab Book ProDocument40 pagesDot1x ISE Lab Book ProswtNo ratings yet
- VPN Tunnel: We Can Build A Tunnel in Check Point Firewall AsDocument47 pagesVPN Tunnel: We Can Build A Tunnel in Check Point Firewall AsBHARATH S RNo ratings yet
- Windows 2016Document59 pagesWindows 2016Alfred SalazarNo ratings yet
- Lab Setup Guide 98 367Document9 pagesLab Setup Guide 98 367Morfeo MunitaNo ratings yet
- VM Meterial1234Document14 pagesVM Meterial1234Krishna ManoharNo ratings yet
- Load iDirect iDX 3.3 Software on Evolution ModemsDocument5 pagesLoad iDirect iDX 3.3 Software on Evolution ModemsAhmadHambaliNo ratings yet
- Informatica Installation and DAC Configuration in 17 StepsDocument42 pagesInformatica Installation and DAC Configuration in 17 Stepseasymoney user1No ratings yet
- Implement Failover Clustering for Hyper-V VMsDocument9 pagesImplement Failover Clustering for Hyper-V VMslucasNo ratings yet
- Instructions For Configuring Remote Working V0.1 - Updated-200426Document21 pagesInstructions For Configuring Remote Working V0.1 - Updated-200426BRajesh ReddyNo ratings yet
- PPI MiddlewareManualDocument63 pagesPPI MiddlewareManualjahanzaibiNo ratings yet
- Terminal ServerDocument3 pagesTerminal ServerAmandeep Singh BirdiNo ratings yet
- Windows Server 2016 Installation and ConfigurationDocument47 pagesWindows Server 2016 Installation and ConfigurationAziz LbaibiNo ratings yet
- CP E80.50 SecuRemoteClient UserGuideDocument16 pagesCP E80.50 SecuRemoteClient UserGuideGabino PampiniNo ratings yet
- Kepserverex Wonderware Suitelink Di ObjectDocument12 pagesKepserverex Wonderware Suitelink Di ObjectfhahzfNo ratings yet
- Win Server ChecklistDocument10 pagesWin Server ChecklistEduardo MorenoNo ratings yet
- Thycotic Database Sizing Guide for Transactional WorkloadsDocument18 pagesThycotic Database Sizing Guide for Transactional WorkloadsYoussif HassanNo ratings yet
- Secret Server - Creating A Database Maintenance PlanDocument10 pagesSecret Server - Creating A Database Maintenance PlanYoussif HassanNo ratings yet
- PAM Install Lab Guide-V12-1Document142 pagesPAM Install Lab Guide-V12-1Youssif HassanNo ratings yet
- PAM Install Lab Guide-V12-1Document142 pagesPAM Install Lab Guide-V12-1Youssif HassanNo ratings yet
- Documentation Guide - Upgrade Steps - 083708Document17 pagesDocumentation Guide - Upgrade Steps - 083708Youssif HassanNo ratings yet
- Sentry Study Guide - 2021Document4 pagesSentry Study Guide - 2021Youssif HassanNo ratings yet
- SCOPEDocument5 pagesSCOPEYoussif HassanNo ratings yet
- Quick Start Guide For WOWDocument3 pagesQuick Start Guide For WOWMegamar50 Servicios caNo ratings yet
- The 8255 Programmable Peripheral InterfaceDocument3 pagesThe 8255 Programmable Peripheral InterfaceMANIKANDANNo ratings yet
- AISDocument9 pagesAISBima AdetyaNo ratings yet
- Quick Reference AIX Journaled File Systems and Veritas File SystemDocument16 pagesQuick Reference AIX Journaled File Systems and Veritas File SystemR D Sandeep100% (1)
- Project Title: Ambo University Woliso Campus School of Technology and InformaticsDocument5 pagesProject Title: Ambo University Woliso Campus School of Technology and InformaticsDagim Fekadu Amenu100% (1)
- Active DatabaseDocument30 pagesActive DatabaseNamrata91No ratings yet
- Database Significance and TrendsDocument5 pagesDatabase Significance and TrendsNamiNo ratings yet
- Networking and Internetworking Devices: 21.1 Review QuestionsDocument3 pagesNetworking and Internetworking Devices: 21.1 Review QuestionsOso PolNo ratings yet
- c2763720 - System Administration Guide - v9 PDFDocument130 pagesc2763720 - System Administration Guide - v9 PDFClaudio Akira EndoNo ratings yet
- FYBSC ComputerDocument21 pagesFYBSC ComputerJS vinesNo ratings yet
- Galaxy Database Manager User's GuideDocument8 pagesGalaxy Database Manager User's GuidesimbamikeNo ratings yet
- MoteView Users Manual 7430-0008-04 BDocument64 pagesMoteView Users Manual 7430-0008-04 BAnushree RastogiNo ratings yet
- Language Fundamentals-JavaDocument8 pagesLanguage Fundamentals-JavasycuneNo ratings yet
- PrintSuperVision 4.0 Installation GuideDocument197 pagesPrintSuperVision 4.0 Installation GuideSenaNo ratings yet
- Introduction to AS/400 System OperationsDocument82 pagesIntroduction to AS/400 System Operationssri100% (2)
- 3gp ConverterDocument1 page3gp ConverterandreasbayuNo ratings yet
- Get Quick and Easy Access To The Wealth of Knowledge, Resources, Tools, Support and Services That Are Available To All SAP CustomersDocument4 pagesGet Quick and Easy Access To The Wealth of Knowledge, Resources, Tools, Support and Services That Are Available To All SAP CustomersKathrynTrinkaButterfuss100% (1)
- Storage Huawei AllDocument268 pagesStorage Huawei AllНиколай ГалановNo ratings yet
- Distributed File SystemDocument7 pagesDistributed File SystemMahamud elmogeNo ratings yet
- The Python Tutorial: Saciando Tu ApetitoDocument114 pagesThe Python Tutorial: Saciando Tu Apetitotvboxsmart newNo ratings yet
- Introduction To File Input and OutputDocument7 pagesIntroduction To File Input and OutputLyle Andrei SotozaNo ratings yet
- Unit 2 DBMSDocument35 pagesUnit 2 DBMS21131A4232 CHUKKALA PRUDHVI RAJNo ratings yet
- SOP On Data Sharing & DLP - User - Policy Creation FormDocument16 pagesSOP On Data Sharing & DLP - User - Policy Creation FormGuruprasad100% (2)
- Java Media Framework API Guide: November 19,1999 JMF 2.0 FcsDocument265 pagesJava Media Framework API Guide: November 19,1999 JMF 2.0 FcsranevesNo ratings yet
- WS 2 PythonDocument28 pagesWS 2 PythonNandhiniNo ratings yet
- (HUAWEI) Poster-GPON TechnologyDocument1 page(HUAWEI) Poster-GPON TechnologyCutui MariusNo ratings yet
- PeopeSoft REN Server ConfigurationDocument19 pagesPeopeSoft REN Server ConfigurationRajNo ratings yet
- Telecommunication ProcessorsDocument11 pagesTelecommunication ProcessorsJeannand Marcial100% (1)
- OSELAS - BSP Pengutronix Mini2440 QuickstartDocument62 pagesOSELAS - BSP Pengutronix Mini2440 QuickstartCarlos TipánNo ratings yet
- Machine Level Representation of Data Character RepresentationDocument14 pagesMachine Level Representation of Data Character RepresentationRenchie GonzalesNo ratings yet