Professional Documents
Culture Documents
Tech Tip: Figure 40 Ipsec Tunnel With FVRF Aggregation
Uploaded by
Priscila FloresOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Tech Tip: Figure 40 Ipsec Tunnel With FVRF Aggregation
Uploaded by
Priscila FloresCopyright:
Available Formats
Appendix B: Technical Feature Supplement
The advertisement of a default route to the hub router (with an existing default route) is problematic. This route
requires a better administrative distance to become the active default, which then overrides the default route that
is supporting the peer-peer IPsec tunnel connection. This routing advertisement breaks the tunnel as shown in
section B in the previous figure.
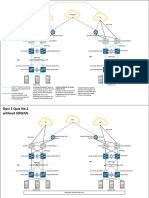
Through the introduction of an external VRF INET-PUBLIC (shown in red), the hub router can support multiple
default routes. The internal network remains in the global VRF. This is shown in section A of the following figure.
Tech Tip
Most additional features on the hub router do not require VRF-awareness.
Figure 40 IPsec tunnel with FVRF aggregation
A B
WAN WAN
Distribution Distribution
Default Default
vrf global vrf INET-PUBLIC vrf global vrf INET-PUBLIC
Inside Inside
Internet Internet
Default Edge Default Edge
Block Block
VPN-DMZ VPN-DMZ
Default Default
Default
Outside Outside
RP
EIG 0)
(20 Default
Internet Internet
Default
DMVPN DMVPN
Spoke Spoke
Router Router
Default Route
2036F
Default Route (vrf INET-PUBLIC)
This configuration is referred to as FVRF, because the Internet is contained in a VRF. FVRF is sometimes referred
to as Front Side VRF. The alternative to this design is Inside VRF (IVRF), where the internal network is in a VRF on
the VPN hub and the Internet remains in the global VRF. This method is not documented in this guide.
It is now possible to reestablish the IPsec tunnel to the remote peer router. Because the remote-site policy
requires central Internet access for end users, a default route is advertised through the tunnel. This advertise-
ment causes a similar default routing issue on the remote router; the tunnel default overrides the Internet-pointing
default and the tunnel connection breaks as shown in section B of the previous figure.
This configuration requires using FVRF on the remote-site router as well. The primary benefits of using this solution are:
•• Simplified default routing and static default routes in the INET-PUBLIC VRFs.
•• Ability to support default routing for end-users traffic through VPN tunnels.
•• Ability to use dynamic default routing for sites with multiple WAN transports.
•• Ability to build spoke-to-spoke tunnels with DMVPN with end-user traffic routed by default through VPN tun-
nels.
Cisco Validated Design page 277
Appendix B: Technical Feature Supplement
The final design that uses FVRF at both the WAN-aggregation site and a WAN remote-site is shown in the follow-
ing figure.
Figure 41 FVRF: Final configuration
WAN Distribution
Default
vrf global vrf INET-PUBLIC
Inside
DMVPN Hub Router
Default Internet
Edge
Default VPN-DMZ
Default
RP
EIG 00) Outside
(2
Internet
Default Route
Default Route (vrf INET-PUBLIC)
Default
DMVPN Spoke Router vrf global vrf INET-PUBLIC
2037F
Cisco Validated Design page 278
Appendix C: Common Procedures
Appendix C: Common Procedures
The procedure in this Appendix is common to all routers.
Procedure 1 Configure the platform base features
Step 1: Configure the device host name. Make it easy to identify the device.
hostname [Hostname]
Step 2: Configure local login and password.
The local login account and password provide basic access authentication to a router, which provides only limited
operational privileges. The enable password secures access to the device configuration mode. By enabling pass-
word encryption, you prevent the disclosure of plain text passwords when viewing configuration files.
username admin secret c1sco123
enable secret c1sco123
service password-encryption
aaa new-model
By default, https access to the router will use the enable password for authentication.
Step 3: (Optional) Configure centralized user authentication.
As networks scale in the number of devices to maintain, it poses an operational burden to maintain local user
accounts on every device. A centralized AAA service reduces operational tasks per device and provides an audit
log of user access for security compliance and root cause analysis. When AAA is enabled for access control, AAA
controls all management access to the network infrastructure devices (SSH and HTTPS).
TACACS+ is the primary protocol used to authenticate management logins on the infrastructure devices to the
AAA server. A local AAA user database is also defined (in Step 2) on each network infrastructure device in order
to provide a fallback authentication source in case the centralized TACACS+ server is unavailable.
tacacs server TACACS-SERVER-1
address ipv4 10.4.48.15
key SecretKey
aaa group server tacacs+ TACACS-SERVERS
server name TACACS-SERVER-1
aaa authentication login default group TACACS-SERVERS local
aaa authorization exec default group TACACS-SERVERS local
aaa authorization console
ip http authentication aaa
Cisco Validated Design page 279
Appendix C: Common Procedures
Step 4: Configure device management protocols.
Secure HTTPS and SSH are secure replacements for the HTTP and Telnet protocols. They use SSL and TLS in
order to provide device authentication and data encryption.
Secure management of the network device is enabled through the use of the SSH and HTTPS protocols. Both
protocols are encrypted for privacy and the nonsecure protocols, Telnet and HTTP, are turned off. SCP is en-
abled, which allows the use of code upgrades using Prime Infrastructure via SSH-based SCP protocol.
Specify the transport preferred none on vty lines in order to prevent errant connection attempts from the CLI
prompt. Without this command, if the ip name-server is unreachable, long timeout delays may occur for mistyped
commands.
ip domain-name cisco.local
ip ssh version 2
no ip http server
ip http secure-server
ip scp server enable
line vty 0 15
transport input ssh
transport preferred none
When synchronous logging of unsolicited messages and debug output is turned on, console log messages are
displayed on the console after interactive CLI output is displayed or printed. With this command, you can continue
typing at the device console when debugging is enabled.
line con 0
transport preferred none
logging synchronous
Enable SNMP in order to allow the network infrastructure devices to be managed by an NMS. SNMPv2c is con-
figured both for a read-only and a read-write community string.
snmp-server community cisco RO
snmp-server community cisco123 RW
snmp-server ifindex persist ! IOS Classic Only
snmp ifmib ifindex persist ! IOS XE Only
Step 5: (Optional) In networks where network operational support is centralized, you can increase network secu-
rity by using an access list to limit the networks that can access your device. In this example, only devices on the
10.4.48.0/24 network will be able to access the device via SSH or SNMP.
access-list 55 permit 10.4.48.0 0.0.0.255
line vty 0 15
access-class 55 in
snmp-server community cisco RO 55
snmp-server community cisco123 RW 55
Cisco Validated Design page 280
Appendix C: Common Procedures
Tech Tip
If you configure an access-list on the vty interface you may lose the ability to use ssh to login from
one router to the next for hop-by-hop troubleshooting.
Step 6: Configure a synchronized clock.
NTP is designed to synchronize a network of devices. An NTP network usually gets its time from an authoritative
time source, such as a radio clock or an atomic clock attached to a time server. NTP then distributes this time
across the organizations network.
You should program network devices to synchronize to a local NTP server in the network. The local NTP server
typically references a more accurate clock feed from an outside source. By configuring console messages, logs,
and debug output to provide time stamps on output, you can cross-reference events in a network.
ntp server 10.4.48.17
clock timezone PST -8
clock summer-time PDT recurring
service timestamps debug datetime msec localtime
service timestamps log datetime msec localtime
Step 7: Configure an in-band management interface.
The loopback interface is a logical interface that is always reachable as long as the device is powered on and any
IP interface is reachable to the network. Because of this capability, the loopback address is the best way to man-
age the router in-band. Layer 3 process and features are also bound to the loopback interface to ensure process
resiliency.
The loopback address is commonly a host address with a 32-bit address mask. Allocate the loopback address
from the IP address block that the router summarizes to the rest of the network.
interface Loopback 0
ip address [ip address] 255.255.255.255
ip pim sparse-mode
Bind the device processes for SNMP, SSH, PIM, TACACS+ and NTP to the loopback interface address for optimal
resiliency:
snmp-server trap-source Loopback0
ip ssh source-interface Loopback0
ip pim register-source Loopback0
ip tacacs source-interface Loopback0
ntp source Loopback0
Cisco Validated Design page 281
Appendix D: Changes
Appendix D: Changes
This appendix summarizes the changes Cisco made to this guide since its last edition.
•• We upgraded IOS software.
•• We updated the QoS settings.
•• We updated the EIGRP settings.
•• We updated the NHRP settings.
•• We updated the PfR policy settings.
•• We simplified the IOS CA configuration.
•• We added a virtual router hub master controller.
•• We added hub master controller high availability.
•• We added hub border router scalability.
•• We added a second data center as a transit site.
•• We added Prime Infrastructure for IWAN monitoring.
Cisco Validated Design page 282
Appendix E: Device Configuration Files
Appendix E: Device Configuration Files
To view the configuration files from the CVD lab devices that were used to test this guide, go to the following
URL: http://cvddocs.com/fw/201i-16a
Cisco Validated Design page 283
Please use the feedback form to send comments and
suggestions about this guide.
Americas Headquarters Asia Pacific Headquarters Europe Headquarters
Cisco Systems, Inc. Cisco Systems (USA) Pte. Ltd. Cisco Systems International BV Amsterdam,
San Jose, CA Singapore The Netherlands
Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco Website at www.cisco.com/go/offices.
ALL DESIGNS, SPECIFICATIONS, STATEMENTS, INFORMATION, AND RECOMMENDATIONS (COLLECTIVELY, “DESIGNS”) IN THIS MANUAL ARE PRESENTED “AS
IS,” WITH ALL FAULTS. CISCO AND ITS SUPPLIERS DISCLAIM ALL WARRANTIES, INCLUDING, WITHOUT LIMITATION, THE WARRANTY OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT
SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION,
LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THE DESIGNS, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN
ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. THE DESIGNS ARE SUBJECT TO CHANGE WITHOUT NOTICE. USERS ARE SOLELY RESPONSIBLE FOR
THEIR APPLICATION OF THE DESIGNS. THE DESIGNS DO NOT CONSTITUTE THE TECHNICAL OR OTHER PROFESSIONAL ADVICE OF CISCO, ITS SUPPLIERS
OR PARTNERS. USERS SHOULD CONSULT THEIR OWN TECHNICAL ADVISORS BEFORE IMPLEMENTING THE DESIGNS. RESULTS MAY VARY DEPENDING ON
FACTORS NOT TESTED BY CISCO.
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and figures included
in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and coincidental.
© 2015 Cisco Systems, Inc. All rights reserved.
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go
to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not
imply a partnership relationship between Cisco and any other company. (1110R)
Cisco Validated Design B-000200i-1 02/16
You might also like
- PETITION For Declaration of NullityDocument7 pagesPETITION For Declaration of NullityKira Jorgio100% (3)
- Untitled PresentationDocument23 pagesUntitled Presentationapi-543394268No ratings yet
- VRF, MPLS and MP-BGP FundamentalsDocument55 pagesVRF, MPLS and MP-BGP FundamentalsIVAN TANEV100% (2)
- Mobile DevGuide 13 - Gulde For Mobile DeveloperDocument258 pagesMobile DevGuide 13 - Gulde For Mobile DevelopersmaliscribdNo ratings yet
- Financial Management Full Notes at Mba FinanceDocument44 pagesFinancial Management Full Notes at Mba FinanceBabasab Patil (Karrisatte)86% (7)
- Quantum PauseDocument5 pagesQuantum Pausesoulsearch67641100% (2)
- Cloud Native 5G Core Samsung 5G Core Volume 2Document16 pagesCloud Native 5G Core Samsung 5G Core Volume 2ALEXANDRE JOSE FIGUEIREDO LOUREIRO100% (1)
- BRKDCN 2458Document123 pagesBRKDCN 2458Oscar PinedaNo ratings yet
- ASBSC OverviewDocument32 pagesASBSC Overviewdeepakkumar10038No ratings yet
- Api 4G PDFDocument12 pagesApi 4G PDFAluosh AluoshNo ratings yet
- BRKDCN 3378Document135 pagesBRKDCN 3378Khaan MonzaNo ratings yet
- VOSS82 Segmented MGMT StackDocument28 pagesVOSS82 Segmented MGMT StackcobobeNo ratings yet
- BRKDCN 3040Document109 pagesBRKDCN 3040trinity9876No ratings yet
- Using FlowSpec For Diverting Traffic To A TMSDocument30 pagesUsing FlowSpec For Diverting Traffic To A TMSIvan Popov100% (1)
- Vxlan Bgp-Evpn: Vinit Jain Twitter - @vinugenieDocument25 pagesVxlan Bgp-Evpn: Vinit Jain Twitter - @vinugeniechienkmaNo ratings yet
- Enterprise Data Center EVPN-VXLAN ArchitectureDocument60 pagesEnterprise Data Center EVPN-VXLAN ArchitectureAqsa ArshadNo ratings yet
- VXLANDocument75 pagesVXLANxploreNo ratings yet
- 04 RN30034EN40GLA0 CRNC Iu Planning PDFDocument108 pages04 RN30034EN40GLA0 CRNC Iu Planning PDFsuratno mukinNo ratings yet
- 5G Arc HLD V1Document25 pages5G Arc HLD V1Harjeetsingh GillNo ratings yet
- Nexus Operation and Maintenance - BRKDCT-2458Document111 pagesNexus Operation and Maintenance - BRKDCT-2458praveen100% (1)
- 5G CoreDocument18 pages5G CoreHa ThanhNo ratings yet
- Using Open-Ended Tools in Facilitating Mathematics and Science LearningDocument59 pagesUsing Open-Ended Tools in Facilitating Mathematics and Science LearningDomina Jayne PagapulaanNo ratings yet
- ONAP SD-WAN Proposal Use Case v0.9Document23 pagesONAP SD-WAN Proposal Use Case v0.9Danni NovandriNo ratings yet
- Cisco Intelligent WAN (IWAN) - 1Document15 pagesCisco Intelligent WAN (IWAN) - 1Priscila FloresNo ratings yet
- NFV Management and OrchestrationDocument14 pagesNFV Management and OrchestrationMasood SabriNo ratings yet
- QuizDocument4 pagesQuizHafidHariyadhiNo ratings yet
- Cgnat On VSM in 5.1.1Document24 pagesCgnat On VSM in 5.1.1Marco López ZeledónNo ratings yet
- Other Aspects - Discussions - HWDocument5 pagesOther Aspects - Discussions - HWsakshi agarwalNo ratings yet
- WhiteBoard 23 VPC Part 3Document1 pageWhiteBoard 23 VPC Part 3amarmudirajNo ratings yet
- Solution Overview. Motorola Solutions Dimetra IP Micro Automatic Failover PDFDocument8 pagesSolution Overview. Motorola Solutions Dimetra IP Micro Automatic Failover PDFdroyoNo ratings yet
- ZXSDR Nodeb Data Configuration: Zte UniversityDocument42 pagesZXSDR Nodeb Data Configuration: Zte UniversityThakurNo ratings yet
- Reiri Adapter Selection Guide (DHOS CS AG 2110 001)Document13 pagesReiri Adapter Selection Guide (DHOS CS AG 2110 001)crisma tariNo ratings yet
- BRKRST 2091Document75 pagesBRKRST 2091boythanhdatNo ratings yet
- GIBNv2 Routing Architecture and Pilot Phase Presentation V1 0Document37 pagesGIBNv2 Routing Architecture and Pilot Phase Presentation V1 0Rikul Raj GuptaNo ratings yet
- WAN ConfigurationDocument2 pagesWAN ConfigurationGIL ENGINEERNo ratings yet
- Service Provider CCIE Advanced Technologies Class: © 2007 Internetwork Expert, IncDocument5 pagesService Provider CCIE Advanced Technologies Class: © 2007 Internetwork Expert, Incoamal2001No ratings yet
- Extending Wi-Fi - AVForumsDocument3 pagesExtending Wi-Fi - AVForumsjohndo3No ratings yet
- 1-1-1 Reyee Router ProductDocument9 pages1-1-1 Reyee Router ProductSindu WinantoNo ratings yet
- CiscoDataCenterCertificatione Guide 2017Document40 pagesCiscoDataCenterCertificatione Guide 2017Fayyaz AhmedNo ratings yet
- Broad Band VSAT Network PresentationDocument18 pagesBroad Band VSAT Network Presentationprateek_bahal5931No ratings yet
- Building and Using Policies With Cisco SD-WAN - BRKRST-2791Document129 pagesBuilding and Using Policies With Cisco SD-WAN - BRKRST-2791Aaron Reyes SanchezNo ratings yet
- HCIP-WLAN-POEW Planning and Optimization V1.0 Lab Guide-31-40Document10 pagesHCIP-WLAN-POEW Planning and Optimization V1.0 Lab Guide-31-40Test TestNo ratings yet
- SDN For ISPsDocument41 pagesSDN For ISPsmikeNo ratings yet
- Peplink Balance 30 Pro: SD-WAN Branch Router With LTE FailoverDocument3 pagesPeplink Balance 30 Pro: SD-WAN Branch Router With LTE FailoverMichael GillisNo ratings yet
- MP-BGP L2VPN EVPN With FRRDocument3 pagesMP-BGP L2VPN EVPN With FRRSimanta HazraNo ratings yet
- FusionCompute V100R005C00 Network VirtualizationDocument66 pagesFusionCompute V100R005C00 Network VirtualizationAlexNo ratings yet
- BRKDCN 1645Document62 pagesBRKDCN 1645Chafik KaNo ratings yet
- BRKDCN-3378 - VxlanDocument165 pagesBRKDCN-3378 - VxlanChafik KaNo ratings yet
- BRKINI-2005 - Engineering Fast IO To The NetworkDocument72 pagesBRKINI-2005 - Engineering Fast IO To The Network윤덕광No ratings yet
- Model EDS 3000 PR EDS 3000 PS EDS4100 Eds-Md SGX™ 5150 MD SGX™ 5150Document2 pagesModel EDS 3000 PR EDS 3000 PS EDS4100 Eds-Md SGX™ 5150 MD SGX™ 5150eversonfrancaNo ratings yet
- Configuring NAT: Understanding Network Address TranslationDocument4 pagesConfiguring NAT: Understanding Network Address TranslationAkash JosephNo ratings yet
- BRK-134T VPNs SimplifiedDocument37 pagesBRK-134T VPNs Simplifiedbekhedda kaouterNo ratings yet
- DGTL BRKDCN 1645Document40 pagesDGTL BRKDCN 1645Khaan MonzaNo ratings yet
- Intelligent WAN Configuration Files Guide: Cisco Validated DesignDocument30 pagesIntelligent WAN Configuration Files Guide: Cisco Validated DesignTerry ZhaoNo ratings yet
- Topology: Created by NRU Untuk Pelanggan Merapi Utama PharmaDocument10 pagesTopology: Created by NRU Untuk Pelanggan Merapi Utama PharmaArham Sofyan PLINo ratings yet
- KMPL-2143 - EVPN Migration From Legacy To Modern ArchDocument32 pagesKMPL-2143 - EVPN Migration From Legacy To Modern ArchquintaNo ratings yet
- DTP Notes Cheat Sheet Network WalksDocument1 pageDTP Notes Cheat Sheet Network WalksYe Zeiya SheinNo ratings yet
- Brkcrt-2601 - VRF, Mpls and MP-BGP FundamentalsDocument57 pagesBrkcrt-2601 - VRF, Mpls and MP-BGP FundamentalsIvan MachuzaNo ratings yet
- VLAN 150 Public Web DMZ 10.200.1.0/24: Edge AggregationDocument3 pagesVLAN 150 Public Web DMZ 10.200.1.0/24: Edge AggregationNova JosephNo ratings yet
- Example: Secondary WAN in The Hybrid Design Model: Step 2Document20 pagesExample: Secondary WAN in The Hybrid Design Model: Step 2Priscila FloresNo ratings yet
- Intelligent Wan Configuration Files Guide: Cisco Validated DesignDocument38 pagesIntelligent Wan Configuration Files Guide: Cisco Validated DesignTerry ZhaoNo ratings yet
- Introduction To The BSC6900 V900R014 Feature Transmission Resource Pool in RNC BSCDocument64 pagesIntroduction To The BSC6900 V900R014 Feature Transmission Resource Pool in RNC BSCsamNo ratings yet
- Business Update and Outlook 2021: February 15, 2021Document19 pagesBusiness Update and Outlook 2021: February 15, 2021sdsddNo ratings yet
- Ilovepdf MergedDocument43 pagesIlovepdf MergedRaul SteelNo ratings yet
- Access Bank PPMC Eleme PHC Atp DocumentDocument3 pagesAccess Bank PPMC Eleme PHC Atp DocumentOnyekachi JackNo ratings yet
- CVD IWANDesignGuide FEB16 5Document20 pagesCVD IWANDesignGuide FEB16 5Priscila FloresNo ratings yet
- NGFW in FW/VPN Role and Clustering TechnologyDocument37 pagesNGFW in FW/VPN Role and Clustering TechnologyomarptcNo ratings yet
- CVD IWANDesignGuide FEB16 13Document20 pagesCVD IWANDesignGuide FEB16 13Priscila FloresNo ratings yet
- Example: Secondary WAN in The Hybrid Design Model: Step 2Document20 pagesExample: Secondary WAN in The Hybrid Design Model: Step 2Priscila FloresNo ratings yet
- Step 4: Step 5: Step 6:: Table 72 Private DMZ Firewall Network ObjectsDocument20 pagesStep 4: Step 5: Step 6:: Table 72 Private DMZ Firewall Network ObjectsPriscila FloresNo ratings yet
- CVD IWANDesignGuide FEB16 1Document20 pagesCVD IWANDesignGuide FEB16 1Priscila FloresNo ratings yet
- Cisco Validated Design: Deploying IWAN Performance RoutingDocument20 pagesCisco Validated Design: Deploying IWAN Performance RoutingPriscila FloresNo ratings yet
- Figure 27 IWAN Dual Router Remote-Site: Connection To Distribution LayerDocument20 pagesFigure 27 IWAN Dual Router Remote-Site: Connection To Distribution LayerPriscila FloresNo ratings yet
- (Profile Name) (VRF Name) (IP Address) (Loopback IP Address of This Router)Document20 pages(Profile Name) (VRF Name) (IP Address) (Loopback IP Address of This Router)Priscila FloresNo ratings yet
- Applying Qos Configurations To Remote Site RoutersDocument20 pagesApplying Qos Configurations To Remote Site RoutersPriscila FloresNo ratings yet
- Iwan-Eigrp 400 Tunnel20 (Summary Network) (Summary Mask) : Procedure 10 Configure IP Multicast RoutingDocument20 pagesIwan-Eigrp 400 Tunnel20 (Summary Network) (Summary Mask) : Procedure 10 Configure IP Multicast RoutingPriscila FloresNo ratings yet
- Procedure 1 Verify IP Connectivity To Remote Site Loopback InterfacesDocument20 pagesProcedure 1 Verify IP Connectivity To Remote Site Loopback InterfacesPriscila FloresNo ratings yet
- Cisco Intelligent WAN (IWAN) - 5Document15 pagesCisco Intelligent WAN (IWAN) - 5Priscila FloresNo ratings yet
- Intelligent Path Control: Application Recognition 287Document15 pagesIntelligent Path Control: Application Recognition 287Priscila FloresNo ratings yet
- CVD IWANDesignGuide FEB16 5Document20 pagesCVD IWANDesignGuide FEB16 5Priscila FloresNo ratings yet
- Procedure 3 Configure Network Address Translation: Table 15 DMVPN NAT Address MappingDocument20 pagesProcedure 3 Configure Network Address Translation: Table 15 DMVPN NAT Address MappingPriscila FloresNo ratings yet
- Data Redundancy Elimination (DRE) Technology To Identify: Secure ConnectivityDocument15 pagesData Redundancy Elimination (DRE) Technology To Identify: Secure ConnectivityPriscila FloresNo ratings yet
- Option 1: MPLS WAN Physical WAN InterfaceDocument20 pagesOption 1: MPLS WAN Physical WAN InterfacePriscila FloresNo ratings yet
- CVD IWANDesignGuide FEB16 2Document20 pagesCVD IWANDesignGuide FEB16 2Priscila FloresNo ratings yet
- Cisco Intelligent WAN (IWAN) - 3Document15 pagesCisco Intelligent WAN (IWAN) - 3Priscila FloresNo ratings yet
- Cisco Intelligent WAN (IWAN) - 7Document15 pagesCisco Intelligent WAN (IWAN) - 7Priscila FloresNo ratings yet
- Number. Example 3-3 Displays Output From The CommandDocument15 pagesNumber. Example 3-3 Displays Output From The CommandPriscila FloresNo ratings yet
- Laboratorio Regresión Logística - Colaboratory Grupo 2Document7 pagesLaboratorio Regresión Logística - Colaboratory Grupo 2Priscila FloresNo ratings yet
- Strategi Penatalaksanaan Stomatitis Aftosa RekurenDocument11 pagesStrategi Penatalaksanaan Stomatitis Aftosa RekurenPRADNJA SURYA PARAMITHANo ratings yet
- AIKINS v. KOMMENDADocument6 pagesAIKINS v. KOMMENDAMENSAH PAULNo ratings yet
- FAN XR UP1 - E7Document26 pagesFAN XR UP1 - E7Mathieu MaesNo ratings yet
- Surimi Technology: Submitted To: Dr.A.K.Singh (Sr. Scientist) Submitted By: Rahul Kumar (M.Tech, DT, 1 Year)Document13 pagesSurimi Technology: Submitted To: Dr.A.K.Singh (Sr. Scientist) Submitted By: Rahul Kumar (M.Tech, DT, 1 Year)rahuldtc100% (2)
- Material Safety Data Sheet Visco WelDocument4 pagesMaterial Safety Data Sheet Visco Welfs1640No ratings yet
- Tinniuts Today March 1990 Vol 15, No 1Document19 pagesTinniuts Today March 1990 Vol 15, No 1American Tinnitus AssociationNo ratings yet
- Biology Project Asad AliDocument16 pagesBiology Project Asad Alisikander.a.khanixd26No ratings yet
- Marketing Communication I Assignment (Advertisement)Document13 pagesMarketing Communication I Assignment (Advertisement)Serene_98No ratings yet
- Simple Future TenseDocument14 pagesSimple Future TenseYupiyupsNo ratings yet
- A Freudian Look Into Roger Waters' True Expressions in "The Wall."Document5 pagesA Freudian Look Into Roger Waters' True Expressions in "The Wall."Jacob Ritteman100% (1)
- Indian Board of Alternative Medicine: Partner-Pub-1166 ISO-8859-1Document14 pagesIndian Board of Alternative Medicine: Partner-Pub-1166 ISO-8859-1vipinNo ratings yet
- People in OrganisationsDocument8 pagesPeople in OrganisationsBritney valladares100% (1)
- A Psychological Crusade by Fernando Sorrentino - Text 7Document2 pagesA Psychological Crusade by Fernando Sorrentino - Text 7Donnie DominguezNo ratings yet
- Housing Vocabulary TermsDocument3 pagesHousing Vocabulary TermslucasNo ratings yet
- Stock Market Prediction Using Machine Learning ProposalDocument10 pagesStock Market Prediction Using Machine Learning ProposalBilal AhmedNo ratings yet
- New Microsoft Office Word DocumentDocument3 pagesNew Microsoft Office Word DocumentVince Vince100% (1)
- H.P. Elementary Education Code Chapter - 4 - 2012 SMC by Vijay Kumar HeerDocument7 pagesH.P. Elementary Education Code Chapter - 4 - 2012 SMC by Vijay Kumar HeerVIJAY KUMAR HEERNo ratings yet
- Articles of IncorporationDocument2 pagesArticles of IncorporationLegal Forms100% (1)
- TLE10 - Q3 - Lesson 5Document17 pagesTLE10 - Q3 - Lesson 5Ella Cagadas PuzonNo ratings yet
- D245S 734046 Om enDocument90 pagesD245S 734046 Om enEndro Accoustic100% (1)
- Personal Details: Your Application Form Has Been Submitted Successfully. Payment Is SuccessfulDocument6 pagesPersonal Details: Your Application Form Has Been Submitted Successfully. Payment Is SuccessfulKanchanNo ratings yet
- Microwave Oven: Instructions & Cooking GuideDocument38 pagesMicrowave Oven: Instructions & Cooking GuidethomaselandNo ratings yet