Professional Documents
Culture Documents
IS & F Lecture # 11 - Classification of Security Attacks
Uploaded by
Sadiholic0 ratings0% found this document useful (0 votes)
14 views6 pagesOriginal Title
IS & F Lecture # 11 -- Classification of Security Attacks
Copyright
© © All Rights Reserved
Available Formats
DOCX, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
© All Rights Reserved
Available Formats
Download as DOCX, PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
14 views6 pagesIS & F Lecture # 11 - Classification of Security Attacks
Uploaded by
SadiholicCopyright:
© All Rights Reserved
Available Formats
Download as DOCX, PDF, TXT or read online from Scribd
You are on page 1of 6
Information Security and Forensics
Lecture # 11
Classify Security Attacks as
Passive attacks
o -eavesdropping on, or monitoring of, transmissions to;
o -obtain message content, or
o -monitor traffic flows
Active attacks-
o Modification of data steam to:
o masquerade of one entity as some other
o reply previous messages
o modify messages in transit
o denial of services
Passive Attacks: Release of Message contents
Traffic Analysis
Observe pattern from bob to Alice
Masquerade
Message from Darth that appear to be from Bob
Replay
Capture message, later reply message to alice
Modification of Message
Darth modifies message from Bob to Alice
Denial of Service
Darth disrupts service provided by server
Passive Threats Active Threats
Traffic analysis
Release of masquerade reply Modification Denial of series
Message contents
Active and Passive threats
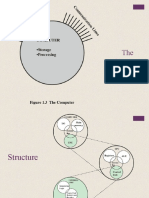
Model for network security
Model for Network Security
Using this model require us to
1. : design a suitable algorithm for the security transformation
2. : generate the secret information used by the algorithm
3. : develop methods to distribute and share the secret information
4. : specify a protocol enabling the principals to use the transformation and secret
information for a security service
Model for Network Access Security
Model for Network Access Security
Using this model requires us to
1. 1: Select appropriate gatekeeper function to identify users
2. 2: implement security controls to ensure only authorized users access designated
information or resources
Trusted Computer System can be used to implements this model
Methods of Defense
Encryption
Software controls(access limitation in a database, in os protect each user from other
users)
Hardware controls(smart card)
Policies(frequent changes of password)
Physical controls
You might also like
- IS & F Lecture # 10 - Classification of Security AttacksDocument6 pagesIS & F Lecture # 10 - Classification of Security AttacksSadiholicNo ratings yet
- IS364 - Lecture 01 - Introduction ITSECDocument34 pagesIS364 - Lecture 01 - Introduction ITSECsamwel sittaNo ratings yet
- Network Security: Presented By: Dr. Munam Ali ShahDocument25 pagesNetwork Security: Presented By: Dr. Munam Ali ShahNadeem ShoukatNo ratings yet
- Active Attack Passive Attack: Disabling Unused ServicesDocument5 pagesActive Attack Passive Attack: Disabling Unused ServicesMohamad MansourNo ratings yet
- Cryptography NotesDocument9 pagesCryptography Notespranjal palNo ratings yet
- Datacenter and Cloud Security - Unit 3Document43 pagesDatacenter and Cloud Security - Unit 3Ujjawal TripathiNo ratings yet
- 6 THDocument14 pages6 THOMKAR BateNo ratings yet
- Chapter 2-Computer Security Attacks and ThreatsDocument40 pagesChapter 2-Computer Security Attacks and ThreatsYohannes DerejeNo ratings yet
- Lecture 3Document27 pagesLecture 3Farhan Nasir AliNo ratings yet
- Nework Security-3Document19 pagesNework Security-3mahtab mahtabNo ratings yet
- Wireless Communication Systems Wireless SecurityDocument19 pagesWireless Communication Systems Wireless Securitynabeel hasanNo ratings yet
- Vulnerabilities and Attacks: Msc. Vuong Thi Nhung Faculty of Information Technology Hanoi UniversityDocument50 pagesVulnerabilities and Attacks: Msc. Vuong Thi Nhung Faculty of Information Technology Hanoi Universityrooney ngôNo ratings yet
- Distributed Systems Course: SecurityDocument42 pagesDistributed Systems Course: SecurityLouis XavierNo ratings yet
- Notes CryptographyDocument68 pagesNotes CryptographyShubhamKhanduriNo ratings yet
- Networking Final 2Document6 pagesNetworking Final 2Askall ThapaNo ratings yet
- 3 Computer Security (CSE 17514) Model Answer Practice TestDocument34 pages3 Computer Security (CSE 17514) Model Answer Practice TestashaNo ratings yet
- Final Interviw PreparDocument4 pagesFinal Interviw Preparsandeep singhNo ratings yet
- Introduction To Information SecurityDocument9 pagesIntroduction To Information SecuritymohamedNo ratings yet
- M.C.a. (Sem - IV) Paper - III - Network SecurityDocument197 pagesM.C.a. (Sem - IV) Paper - III - Network SecurityBalaji RamNo ratings yet
- Cybersecurity Overview: Network SecurityDocument18 pagesCybersecurity Overview: Network SecuritysubishsNo ratings yet
- Students - Unit - 1 - Network SecurityDocument60 pagesStudents - Unit - 1 - Network SecurityDr M JayanthiNo ratings yet
- Defensepro: Ddos Protection and Attack MitigationDocument6 pagesDefensepro: Ddos Protection and Attack MitigationJagjeet SinghNo ratings yet
- Radware DefensePro Data Sheet 2018Document6 pagesRadware DefensePro Data Sheet 2018PDFZalNo ratings yet
- Defensepro: Ddos Protection and Attack MitigationDocument6 pagesDefensepro: Ddos Protection and Attack MitigationJagjeet SinghNo ratings yet
- Radware DefensePro DatasheetDocument6 pagesRadware DefensePro DatasheetJagjeet SinghNo ratings yet
- Radware DefensePro Datasheet UpdatedDocument6 pagesRadware DefensePro Datasheet UpdatedJagjeet SinghNo ratings yet
- Types of AttacksDocument5 pagesTypes of AttacksAkansha UniyalNo ratings yet
- Chapter 1 2 AUDocument80 pagesChapter 1 2 AUYididiya TilahunNo ratings yet
- Chapter 4 - Network Security Concepts and MechanismsDocument74 pagesChapter 4 - Network Security Concepts and MechanismsMebruka Abdul RahmanNo ratings yet
- "MY APPS"-Android Application Security Software Using Grid Security Infrastructure (GSI)Document51 pages"MY APPS"-Android Application Security Software Using Grid Security Infrastructure (GSI)Prabu RajsekarNo ratings yet
- CNS-R16-UNIT-1 NotesDocument24 pagesCNS-R16-UNIT-1 NotesSiva TummaNo ratings yet
- Network SecurityDocument10 pagesNetwork SecurityDivya SharmaNo ratings yet
- Security Cram Notes PLUSDocument12 pagesSecurity Cram Notes PLUSNick Van HalenNo ratings yet
- Information SecurityDocument8 pagesInformation Securitysmartclass2022jknNo ratings yet
- Week 6 - WatermarkDocument146 pagesWeek 6 - Watermarkshailesh karthikNo ratings yet
- Security2 1Document42 pagesSecurity2 1Broot KalNo ratings yet
- ECS401: Cryptography and Network Security: Module 1: IntroductionDocument24 pagesECS401: Cryptography and Network Security: Module 1: IntroductionShabnam SmileNo ratings yet
- Is Unit-IDocument13 pagesIs Unit-IPrakruti KrishnanNo ratings yet
- Cyber Security Sem6Document38 pagesCyber Security Sem6thirstyeulerNo ratings yet
- Threats in Network: Anonymity Many Points of Attack Sharing Complexity of SystemDocument14 pagesThreats in Network: Anonymity Many Points of Attack Sharing Complexity of SystemJack KimaniNo ratings yet
- Network & Security PPDocument7 pagesNetwork & Security PPBharath KumarNo ratings yet
- NS Yst Em: Gagandeep AP in CSE Deptt. PPIMT, HisarDocument69 pagesNS Yst Em: Gagandeep AP in CSE Deptt. PPIMT, HisarAnkur MittalNo ratings yet
- Ebook - CISSP - Domain - 04 - Communication and Network SecurityDocument160 pagesEbook - CISSP - Domain - 04 - Communication and Network SecurityAb ParvizeNo ratings yet
- Attacks Information SecurityDocument7 pagesAttacks Information Securitysanamanand3300No ratings yet
- Unit - 1Document96 pagesUnit - 1Akshit PrajapatiNo ratings yet
- Security of Communication Networks, InDP3 (IST, IRES, RSM)Document27 pagesSecurity of Communication Networks, InDP3 (IST, IRES, RSM)AhmedAzriNo ratings yet
- Network Security: Presented By: Dr. Munam Ali ShahDocument25 pagesNetwork Security: Presented By: Dr. Munam Ali ShahNadeem ShoukatNo ratings yet
- Unit-1 Cryptography and HashingDocument73 pagesUnit-1 Cryptography and HashingNishil ShahNo ratings yet
- INS 6th SemDocument66 pagesINS 6th SemVinay JaiprakashNo ratings yet
- MCE Cybersecurity ForensicDocument105 pagesMCE Cybersecurity Forensicgowdanischith03No ratings yet
- Cryptography & Network Security - 2Document5 pagesCryptography & Network Security - 2junaid MalikNo ratings yet
- 192 CryptographyDocument16 pages192 CryptographyTanjil AhmedNo ratings yet
- Chapter 04 - Network SecurityDocument25 pagesChapter 04 - Network SecurityJaye 99No ratings yet
- Information Security Unit - 1Document11 pagesInformation Security Unit - 1Lokesh Sai Kumar DasariNo ratings yet
- Calculus Cheat Sheet Limits PDFDocument23 pagesCalculus Cheat Sheet Limits PDFVijayprakashreddy BvprNo ratings yet
- Network Security Issue 1.0 qsCh0SRDocument33 pagesNetwork Security Issue 1.0 qsCh0SRYaniko DimasNo ratings yet
- Memory Tables Answer Key: Appendix DDocument19 pagesMemory Tables Answer Key: Appendix Daquey1No ratings yet
- Cloud Security AssessmentDocument18 pagesCloud Security Assessmentraju mahtreNo ratings yet
- Eh - Unit-1Document33 pagesEh - Unit-1vgfwky2nypNo ratings yet
- Lecture 14 - External Memory 1Document17 pagesLecture 14 - External Memory 1SadiholicNo ratings yet
- Lecture 03 - Computer Evolution and Performance 01Document21 pagesLecture 03 - Computer Evolution and Performance 01SadiholicNo ratings yet
- Y 2017 P 5 Q 5Document1 pageY 2017 P 5 Q 5SadiholicNo ratings yet
- 08 - Operating System SupportDocument65 pages08 - Operating System SupportSadiholicNo ratings yet
- Lecture 02 - Introduction 02Document7 pagesLecture 02 - Introduction 02SadiholicNo ratings yet
- 07 - Input OutputDocument22 pages07 - Input OutputSadiholicNo ratings yet
- Lecture 01 - Introduction 01Document10 pagesLecture 01 - Introduction 01SadiholicNo ratings yet
- Lecture 2Document37 pagesLecture 2SadiholicNo ratings yet
- Lecture 3Document11 pagesLecture 3SadiholicNo ratings yet
- 10 - Instruction Sets CharacteristicsDocument19 pages10 - Instruction Sets CharacteristicsSadiholicNo ratings yet
- Lecture 4Document5 pagesLecture 4SadiholicNo ratings yet
- Lecture 1Document20 pagesLecture 1SadiholicNo ratings yet
- IS & F Lecture #29 30 - Computer Forensics-Data AcquisitionDocument17 pagesIS & F Lecture #29 30 - Computer Forensics-Data AcquisitionSadiholicNo ratings yet
- IS & F Lecture 2-3 Introduction To Information SecurityDocument31 pagesIS & F Lecture 2-3 Introduction To Information SecuritySadiholicNo ratings yet
- Is & F Lecture# 24 - Classicla Encryption TechniquesDocument14 pagesIs & F Lecture# 24 - Classicla Encryption TechniquesSadiholicNo ratings yet
- Is & F Lecture 11 - Description of Network ProtocolsDocument26 pagesIs & F Lecture 11 - Description of Network ProtocolsSadiholicNo ratings yet
- Is & F Lecture 15 16 17 18 19 - Firewalls and Their Security ConfigurationsDocument22 pagesIs & F Lecture 15 16 17 18 19 - Firewalls and Their Security ConfigurationsSadiholicNo ratings yet
- IS & F Lecture 7 8 9 10 - MaliciousSoftware & Security AttacksDocument29 pagesIS & F Lecture 7 8 9 10 - MaliciousSoftware & Security AttacksSadiholicNo ratings yet
- IS & F Lecture 4-5-6 Software Engineering and Information SecurityDocument32 pagesIS & F Lecture 4-5-6 Software Engineering and Information SecuritySadiholicNo ratings yet
- DBA PaperDocument7 pagesDBA PaperSadiholicNo ratings yet
- CS87 Spring 2010 Readings 7Document5 pagesCS87 Spring 2010 Readings 7SadiholicNo ratings yet