Professional Documents
Culture Documents
Bug Bounty
Uploaded by
Alan VikramCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Bug Bounty
Uploaded by
Alan VikramCopyright:
Available Formats
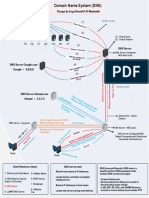
SCOPE Domain Seeds / Root domains = *.example.
com
whoxy.com
Tools
DOMLink (Vincent Yiu)
Reverse Whois
shows the ownership of the organisation (past
and present)
crunchbase.com
Acquisations
after obtaining the acquisation orgs digginf for
them is acceptable
Subdomain Enumeration
bgp.he.net
Tools metabigor (j3ssiejjj)
asnlookup.py (Yassine Aboukir)
campuses all of the known IP to the
ASN Enumeration
organisation
with the asn numbers, `amass` can be used to
obtain more domains which can be again go command: `amass intel -asn {}` {number
through the recon processes followed by asnxxxxx}
masscan -p1-65535 -iL IPFILE --max-rate 1800 -
masscan oG output file
RECON
Port Analysis
dnsmasscan domainList.txt outputFile.txt -p
dnmasscan ports -oG masscan.log
Privacy Policy
"copy rights" site: target.com Copyrights
Terms of Services
Google
Through dorks, multiple domains and
subdomains can be identified
SHODAN
Github Dorking
EyeWitness
ScreenShotting Aquatone
httpscreenshot
Tesla.com on budcrowd Working
can i takeover xyz
Verizon Media on hackerone Huge Scope Domains
Subdomain Takeover SubOver
nuclei
builtwith.com
Bug Hunting
Ad/Analytics Relationships Framework interlace
Tech Profiles and Relationship profiles Application Analysis
Methodology v4 Turn Off PassiveScanning
Keep Track of Everything (Mindmap, notes Set Forms to auto submit
etc..,)
Burp Scope to Advanced control and enter regex (!
Recon = Discover as many as assests as
possible
Recon NO FULLY QUALIFIED DOMAIN NAME)
Visit -> Sipder -> Sipder the output of the
Linked Discovery Spider Recursively spider
Gospider (j3ssiejjj)
Linked and JavaScript Discovery hakrawler (hakluke)
Subdomainizer (Neeraj Edwards)
subscraper (Cillian-Collins)
Google site:exampl.org -www.example.org
amass amass enum -d example.com
subfinder subfinder -d example.com
Subdomain Scraping python3 github-subdomains.py -t "target.
github-subdomains.py com" -d ? | tee out.txt
shosubgo (inc0gbyt3) shosubgo -d 'example.com' -s "shodan-key"
SUB-DOMAIN Enumeration curl 'https://tls.bufferover.run/dns?q=.website.
cloud ranges com' 2>/dev/null | jq .Results
massdns
amass amass enum -brute -d example.com -srv
Subdomain BruteForce shuffledns -d example.com -w words.txt -r
shuffleDNS resolver-list.txt
all.txt
wordlists for bruteforce lists
github.com/assetnote/commonspeak2
altdns
Misc Alteration Scanning
amass
You might also like
- DNS Design and OperationDocument1 pageDNS Design and OperationsiouxinfoNo ratings yet
- Bug Hunter Methodology V4 (@jhaddix) : Finding SeedsDocument1 pageBug Hunter Methodology V4 (@jhaddix) : Finding SeedshsenNo ratings yet
- RDBMS Genealogy V6 PrintDocument1 pageRDBMS Genealogy V6 Printamit_post2000No ratings yet
- pdf-section6-stimulation-equipment_compress_17Document1 pagepdf-section6-stimulation-equipment_compress_17Mohamed MamdouhNo ratings yet
- Red Team Ops - Mind MapDocument1 pageRed Team Ops - Mind Map0xt3stNo ratings yet
- Mobile Web Serverless RADocument2 pagesMobile Web Serverless RAradius.airflowNo ratings yet
- Operation Contracts Detail System Behavior ChangesDocument13 pagesOperation Contracts Detail System Behavior ChangesNandha KishoreNo ratings yet
- Big Data Overview & Hadoop For DBA's: Satyendra PasalapudiDocument92 pagesBig Data Overview & Hadoop For DBA's: Satyendra PasalapudivnairajNo ratings yet
- Special: U.S. Ghess Gatalog and NIC Yearbook Vol 1/1984 chess title collectionDocument84 pagesSpecial: U.S. Ghess Gatalog and NIC Yearbook Vol 1/1984 chess title collectionOscar Estay T.No ratings yet
- Massive Transformative Purpose: Organization Date Done byDocument1 pageMassive Transformative Purpose: Organization Date Done byGiovanna Arzamendia TrinidadNo ratings yet
- System Design Blueprint: The Ultimate GuideDocument1 pageSystem Design Blueprint: The Ultimate GuideSathiamoorthy DuraisamyNo ratings yet
- Deep analysis of malware behavior and codeDocument2 pagesDeep analysis of malware behavior and codedonoNo ratings yet
- Act460-Scholar ch4 Part 1Document6 pagesAct460-Scholar ch4 Part 1Anfal KankouniNo ratings yet
- Cmsc420 Spring2021 SlidesDocument54 pagesCmsc420 Spring2021 SlidesĐạt NguyễnNo ratings yet
- WTG Site PlanDocument1 pageWTG Site PlanDaina OliverNo ratings yet
- Proceedings of Spie: "Fast" Is Not "Real-Time": Designing Effective Real-Time AI SystemsDocument10 pagesProceedings of Spie: "Fast" Is Not "Real-Time": Designing Effective Real-Time AI SystemsbassbngNo ratings yet
- Ethics - Short NotesDocument29 pagesEthics - Short NotesasrdawfhfNo ratings yet
- Pgcrypto Avast!: A Study in Django's Password HashersDocument52 pagesPgcrypto Avast!: A Study in Django's Password Hasherskrishna.setwinNo ratings yet
- Data structures and algorithms overviewDocument1 pageData structures and algorithms overviewrashed44No ratings yet
- Data structures and algorithms overviewDocument1 pageData structures and algorithms overviewrashed44No ratings yet
- CompositesWorkshop ANSYS DAFDocument22 pagesCompositesWorkshop ANSYS DAFDavid Acosta100% (1)
- (Soiirce: City of Chicago) (Source: City of Chicago) : ArcgisDocument13 pages(Soiirce: City of Chicago) (Source: City of Chicago) : ArcgispedroNo ratings yet
- malicious programsDocument1 pagemalicious programstrxjtckfn2No ratings yet
- Betradar Cashout APIDocument1 pageBetradar Cashout APIsiyakinNo ratings yet
- Big Data Dataset Categories Pattern IdentificationDocument1 pageBig Data Dataset Categories Pattern IdentificationpietropesNo ratings yet
- Opensource ML Frameworks On Amazon SageMakerDocument40 pagesOpensource ML Frameworks On Amazon SageMakerAnx xNo ratings yet
- ZT JVM Options Cheat SheetDocument1 pageZT JVM Options Cheat SheetnenjamsNo ratings yet
- Proposed Assets Class Names:: ConveyanceDocument2 pagesProposed Assets Class Names:: ConveyancePrabhat SrivastavaNo ratings yet
- Blue Bank Story MappingDocument1 pageBlue Bank Story MappingVikin Jain100% (1)
- Amassive Leap in Host DiscoveryDocument23 pagesAmassive Leap in Host DiscoverytestNo ratings yet
- React Learning Path 2020Document1 pageReact Learning Path 2020Java ManNo ratings yet
- Ultimate Web Development Roadmap 2021+: Start HereDocument1 pageUltimate Web Development Roadmap 2021+: Start Heregodway BOKA100% (1)
- 8-Data Driven MPCDocument94 pages8-Data Driven MPChinsermuNo ratings yet
- V10 Mes PDFDocument5 pagesV10 Mes PDFBrian MelNo ratings yet
- V10 MesDocument5 pagesV10 Mesvela vanNo ratings yet
- Sharao's PDF ResumeDocument1 pageSharao's PDF ResumeSrinivas Rao GunjaNo ratings yet
- Reklamobil-Mobile Ad Industry 2009 by MobileraDocument1 pageReklamobil-Mobile Ad Industry 2009 by Mobileraasliguel_aktasNo ratings yet
- System Tables DiagramDocument1 pageSystem Tables Diagramhansom1029No ratings yet
- System Design BlueprintDocument1 pageSystem Design BlueprintyashNo ratings yet
- Advanced Javascript: Interpreter/ Compiler/ JIT CompilerDocument1 pageAdvanced Javascript: Interpreter/ Compiler/ JIT CompilerJamshid AzizovNo ratings yet
- Advanced Javascript: Interpreter/ Compiler/ JIT Compiler Writing Optimized CodeDocument1 pageAdvanced Javascript: Interpreter/ Compiler/ JIT Compiler Writing Optimized CodeRonNo ratings yet
- Advanced JavascriptDocument1 pageAdvanced Javascriptsttv2727No ratings yet
- Ergodic Rate Analysis of Reconfigurable Intelligent Surface-Aided Massive MIMO Systems With ZF DetectorsDocument5 pagesErgodic Rate Analysis of Reconfigurable Intelligent Surface-Aided Massive MIMO Systems With ZF DetectorspratirajNo ratings yet
- Machine Learning Quick Start GuideDocument1 pageMachine Learning Quick Start GuideHammad RiazNo ratings yet
- SmartBabyincub DrawioDocument1 pageSmartBabyincub DrawioYOSEF AbdoNo ratings yet
- For Zoe Guys-1Document2 pagesFor Zoe Guys-1zjsxf8tptzNo ratings yet
- Captura de Pantalla 2023-10-05 A La(s) 8.32.40 P.M.Document1 pageCaptura de Pantalla 2023-10-05 A La(s) 8.32.40 P.M.hannasophiacuteNo ratings yet
- V91MESDocument4 pagesV91MESdhinojahimeshNo ratings yet
- Aws Innovate Q4T3S3Document33 pagesAws Innovate Q4T3S3man.sinh.leeNo ratings yet
- An Advanced Logistics Platform For Smes & Enterprises: NimbuspostDocument1 pageAn Advanced Logistics Platform For Smes & Enterprises: NimbuspostHimanshu SinghalNo ratings yet
- Flyer 3Document1 pageFlyer 3Himanshu SinghalNo ratings yet
- Constructing Sobol Sequences With Better Two-Dimensional ProjectionsDocument20 pagesConstructing Sobol Sequences With Better Two-Dimensional ProjectionsA BNo ratings yet
- VolteDocument1 pageVoltemohamed100% (1)
- Future of Making MapDocument2 pagesFuture of Making MapSean NessNo ratings yet
- Bhandari 2016Document13 pagesBhandari 2016Bryan Alexis MendezNo ratings yet
- Home WorkDocument3 pagesHome WorkDaoud ElalouanyNo ratings yet
- Penetration Testing ToolsDocument1 pagePenetration Testing ToolsJulián GonzálezNo ratings yet
- SD Blueprint MergedDocument160 pagesSD Blueprint MergedHrithik VemparalaNo ratings yet
- MODULE 3 and 4Document40 pagesMODULE 3 and 4Alan VikramNo ratings yet
- SSRF - Server Side Request Forgery (Types and Ways To Exploit It) Part-1 - by SaN ThosH - MediumDocument8 pagesSSRF - Server Side Request Forgery (Types and Ways To Exploit It) Part-1 - by SaN ThosH - MediumAlan VikramNo ratings yet
- CPT 1Document184 pagesCPT 1Alan VikramNo ratings yet
- Threat Hunting, Hacking, and Intrusion DetectionDocument121 pagesThreat Hunting, Hacking, and Intrusion DetectionAlan VikramNo ratings yet
- Kali Linux 64 Bit Link: Kali Linux 64 Bit Alternative Link: Kali Linux 32 Bit LinkDocument1 pageKali Linux 64 Bit Link: Kali Linux 64 Bit Alternative Link: Kali Linux 32 Bit LinkAlan VikramNo ratings yet
- DUMPDocument294 pagesDUMPAlan VikramNo ratings yet
- Introduction to DisastersDocument51 pagesIntroduction to DisastersAlan VikramNo ratings yet
- BF PP 2017Document4 pagesBF PP 2017Revatee HurilNo ratings yet
- Operation - Manual Cubase 5Document641 pagesOperation - Manual Cubase 5Samiam66682% (17)
- Medical Tourism A Look at How Medical Outsourcing Can Reshape Health Care - 2014Document18 pagesMedical Tourism A Look at How Medical Outsourcing Can Reshape Health Care - 2014avijitcu2007No ratings yet
- Growth of Luxury Market & Products in IndiaDocument60 pagesGrowth of Luxury Market & Products in IndiaMohammed Yunus100% (2)
- In-N-Out vs. DoorDashDocument16 pagesIn-N-Out vs. DoorDashEaterNo ratings yet
- Transmission Line4 PDFDocument46 pagesTransmission Line4 PDFRevathi PrasadNo ratings yet
- RidleyBoxManual1 17Document63 pagesRidleyBoxManual1 17Sergio Omar OrlandoNo ratings yet
- File System ImplementationDocument35 pagesFile System ImplementationSát Thủ Vô TìnhNo ratings yet
- Chapter 6 Game Theory TwoDocument9 pagesChapter 6 Game Theory TwoMextli BarritaNo ratings yet
- Illegitimate Child's Right to Support from FatherDocument1 pageIllegitimate Child's Right to Support from FatherrickmortyNo ratings yet
- Low Carb Diabetic RecipesDocument43 pagesLow Carb Diabetic RecipesDayane Sant'AnnaNo ratings yet
- Mil DTL 11891g EngDocument96 pagesMil DTL 11891g EngJohn DrakosNo ratings yet
- 2019 Book TheEBMTHandbookDocument688 pages2019 Book TheEBMTHandbook88tk6rccsmNo ratings yet
- EY ScandalDocument3 pagesEY ScandalAndrea RumboNo ratings yet
- 27 20130913 Kebijakan Inovasi Teknologi Untuk Pengelolaan Lahan Suboptimal Berkelanjutan-With-Cover-Page-V2Document12 pages27 20130913 Kebijakan Inovasi Teknologi Untuk Pengelolaan Lahan Suboptimal Berkelanjutan-With-Cover-Page-V2MeigimaesaNo ratings yet
- Solve A Second-Order Differential Equation Numerically - MATLAB SimulinkDocument2 pagesSolve A Second-Order Differential Equation Numerically - MATLAB Simulinkmohammedshaiban000No ratings yet
- Maluno Integrated School: Action Plan On Wins ProgramDocument1 pageMaluno Integrated School: Action Plan On Wins ProgramSherlymae Alejandro Avelino100% (2)
- Axe FX II Tone Match ManualDocument6 pagesAxe FX II Tone Match Manualsteven monacoNo ratings yet
- (Your Business Name Here) - Safe Work Procedure Metal LatheDocument1 page(Your Business Name Here) - Safe Work Procedure Metal LatheSafety DeptNo ratings yet
- Managing Digital Transformations - 1Document105 pagesManaging Digital Transformations - 1RamyaNo ratings yet
- Con Law Koppelman HugeDocument203 pagesCon Law Koppelman HugemrstudynowNo ratings yet
- Vehicle To Vehicle V2V Communication Scope Importa PDFDocument13 pagesVehicle To Vehicle V2V Communication Scope Importa PDFvahidinkormanNo ratings yet
- Dissertation Bowden PDFDocument98 pagesDissertation Bowden PDFmostafaNo ratings yet
- Satyam GargDocument2 pagesSatyam GargSatyam GargNo ratings yet
- Artificial Intelligence and Applications: Anuj Gupta, Ankur BhadauriaDocument8 pagesArtificial Intelligence and Applications: Anuj Gupta, Ankur BhadauriaAnuj GuptaNo ratings yet
- Manipulative and Interactive Media GuideDocument25 pagesManipulative and Interactive Media Guidetyron plandesNo ratings yet
- LabVIEW - Connect To MySQLDocument6 pagesLabVIEW - Connect To MySQLDavidleonardo GalindoNo ratings yet
- How The CBO Works: Jonathan Lewis WWW - Jlcomp.demon - Co.ukDocument37 pagesHow The CBO Works: Jonathan Lewis WWW - Jlcomp.demon - Co.ukomeratisNo ratings yet
- PMP Cheat SheetDocument9 pagesPMP Cheat SheetzepededudaNo ratings yet
- Factory Act Gujarat PDFDocument2 pagesFactory Act Gujarat PDFKeith100% (1)