Professional Documents
Culture Documents
802-1x Intro-Compressed
Uploaded by
Syazwan M. DhiyaulhaqOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
802-1x Intro-Compressed
Uploaded by
Syazwan M. DhiyaulhaqCopyright:
Available Formats
Introduction to 802.
1x for enterprise network
Mukhammad Andri Setiawan, PhD
andri.setiawan@uii.ac.id
andri@idnic.net
Presented at IDNIC workshop, 27-28 November 2018
(part of the 1st Annual Member Meeting, IDNIC)
Manhattan Hotel, JAKARTA, INDONESIA
VALUES INNOVATION PERFECTION
Hello, I’m Andri Setiawan
• Training & Community, IDNIC
• CIO, Universitas Islam Indonesia
• Lecturer, Informatics Department, Universitas Islam Indonesia
• Administrator, eduroam Indonesia, a free wifi roaming services for
research and education, available at 101 countries, with more than
12,000 institutions providing the eduroam WiFi
• “Gerilyawan” , Indonesia Research Education Network (IdREN)
• Instructor Trainer, CISCO Networking Academy (Netacad) INDONESIA
• Websites:
• https://andrisetiawan.com
• https://ideas.andrisetiawan.com
VALUES INNOVATION PERFECTION
Disclaimer:
This workshop is ONLY an INTRODUCTION i.e. to give you the big concept or rough idea of
how 802.1x works. You can’t simply copy and paste and have your network 802.1x ready.
However, we strive to explain how 802.1x protocol works as much as possible. Some
technical jargons will be explained, some won’t. Some configurations will be explained, some
won’t. A further reading and lots of experiments are needed.
VALUES INNOVATION PERFECTION
Agenda
• Introduction to 802.1x protocol
• Why 802.1x
• Study case of 802.1x in WiFi network
• Study case of 802.1x in Windows Domain environment (wired network)
VALUES INNOVATION PERFECTION
802.1x – what is it?
• IETF defines 802.1X as port-based network access control
• It is a mechanism by which devices connecting to a local area network are
authenticated
• 802.1x uses Extensible Authentication Protocol (EAP) over LAN (EAPoL) that
is a network port authentication protocol PNAC (Port Based Network Access
Control) to give a generic network sign-on to access network resources
VALUES INNOVATION PERFECTION
Parties involved
• a supplicant,
• an authenticator, and
• an authentication server
VALUES INNOVATION PERFECTION
EAPOL handshakes
VALUES INNOVATION PERFECTION
Why 802.1x
VALUES INNOVATION PERFECTION
Business Case 1: 802.1x in WiFi
VALUES INNOVATION PERFECTION
Business case 1: 802.1x in WiFi Network
• You must be already familiar
with this
• Yes, the notorious captive
portal
VALUES INNOVATION PERFECTION
Why Captive Portal is not good
• Unsecured network, it’s OPEN
• Problematics (often the portal did not show up)
• You will have all of your users in one big pool (one vlan)
• Association before Authentication
• You received IP address, then authenticate yourself using captive portal
• Prone to MAC Spoofing
VALUES INNOVATION PERFECTION
802.1x in WiFi
• Users need to authenticate themselves before associating to the
network
• That means, NO ip address before authentication
• It’s a SET and FORGET system
• Trust me, your users will love it, a lot!!!
• Some vendors allow Single SSID multiple VLAN
• especially those enterprise grade vendor e.g. Cisco, Aruba, Ruckus, etc.
VALUES INNOVATION PERFECTION
802.1x in actions
VALUES INNOVATION PERFECTION
802.1x in Wi-Fi, the scenario
• We broadcast an SSID called eduroam
• This SSID will be a single SSID but with multiple VLAN
• Users will be distinguished by their directory’s group (we are using
Active Directory), each group will represent a single VLAN
• We assume Active Directory has been set up
VALUES INNOVATION PERFECTION
802.1x in Wi-Fi, the topology
VALUES INNOVATION PERFECTION
The topology explained
• All APs are within the same VLAN
• The beauty of CAPWAP (centralised protocol for WLC) is that it can tunnel
VLANs within a VLAN (just like Q-in-Q) i.e 802.11ad
• WLC connect with NAT Router with a trunk mode
• You can refer to: Router on a stick concept
• freeRADIUS uses Active Directory as the backend
• I will show the example of accessing AD with both AD protocol and LDAP
protocol, but for different purposes: Authentication and VLAN allocation
VALUES INNOVATION PERFECTION
The implementation
• Client uses smartphone (can be Android or iPhone)
• Cisco WLC 5500 series, Cisco Aironet Access Points
• freeRADIUS 3.0
• Active Directory (Windows Server 2012)
• NAT Router – Mikrotik CCR
VALUES INNOVATION PERFECTION
Settings in WLC
• Setup SSID eduroam
• Set Authentication Security
• Set dynamic VLAN allocation
VALUES INNOVATION PERFECTION
SSID eduroam
VALUES INNOVATION PERFECTION
SSID eduroam
VALUES INNOVATION PERFECTION
WLC Interfaces
(dynamic VLAN)
VALUES INNOVATION PERFECTION
RADIUS authentication (IP + secret)
VALUES INNOVATION PERFECTION
freeRADIUS settings
• Assumptions:
• freeRADIUS 3 is installed in Linux machine
• there is connectivity between freeRADIUS and Active Directory
• Steps involved:
• Join freeRADIUS machine with AD with Samba
• Setup RADIUS machine clients.conf (to allow communication between WLC and RADIUS)
• Enable these modules:
• eap
• ntlm_auth – Auth Users
• ldap – allocate groups for dynamic VLAN
• Tag vlan with vendor attributes in post-auth
VALUES INNOVATION PERFECTION
freeRADIUS + AD
• Details: https://wiki.freeradius.org/guide/freeradius-active-directory-
integration-howto
// JOIN DOMAIN
#net join –U Administrator
// TEST AUTH
// We will use this command in the ntlm_auth module of freeRADIUS
#ntlm_auth –-request-nt-key –-domain=XYZDOM –-username=example_user
VALUES INNOVATION PERFECTION
freeRADIUS, first thing first
• To authenticate WLC to freeRADIUS, we need:
• IP address of our WLC
• Secret i.e. the password
client wlc {
ipaddr = 10.x.x.x
secret = myRADIUS
}
VALUES INNOVATION PERFECTION
freeRADIUS configuration
• Types of EAP authentication method
• EAP-TLS, EAP-TTLS, EAP-MD5, EAP-IKEv2, EAP-FAST, EAP-SIM
• Types of EAP encapsulation
• EAP-PEAP (it’s actually TTLS but with added improvement from Microsoft,
CISCO, etc, hence it is encapsulation, not simply an authentication)
• In our case, we will use EAP-PEAP
VALUES INNOVATION PERFECTION
Authentication: Enable EAP-PEAP
• To enable such authentication (as per previous slides), we need to enable few
modules
• In freeRADIUS 3, they are under /etc/freeradius/mods-enabled
• In our case:
• /etc/freeradius/mods-enabled/eap – and enable PEAP (FYI: peap ONLY if you are using
AD, but if you are using other than AD e.g. LDAP, you can’t use PEAP, but EAP-TTLS
eap {
default_eap_type = peap
}
VALUES INNOVATION PERFECTION
Authentication: Enable MSCHAPv2
• Available at /etc/freeradius/mods-enabled/mschap
mschap {
ntlm_auth = "/usr/bin/ntlm_auth
--request-nt-key --domain=%{%{mschap:NT-Domain}:-myDOMAIN}
--username=%{%{Stripped-User-Name}:-%{%{User-Name}:-None}}
--challenge=%{%{mschap:Challenge}:-00}
--nt-response=%{%{mschap:NT-Response}:-00}
--require-membership-of='myDOMAIN\\eduroam'”
}
VALUES INNOVATION PERFECTION
Authorization: inner-tunnel
• Once our users are successfully authenticated, we need to authorize them to our
network
• /etc/freeradius/sites-enabled/inner-tunnel
authorize {
mschap
}
authenticate {
ntlm_auth
Auth-Type MS-CHAP {
mschap
}
eap
}
VALUES INNOVATION PERFECTION
Authorization: LDAP module
• We use LDAP to assign the VLAN of each group, so we need to make sure that ldap module is enabled
• /etc/freeradius/mods-enabled/ldap
ldap {
server = '10.254.254.101’
port = 389
identity = 'CN=Administrator,CN=Users,DC=uii,DC=ac,DC=id’
password = thisIsAVeryLongPasswordDoNotForgetIt
base_dn = 'OU=Accounts,DC=uii,DC=ac,DC=id’
user {
base_dn = "${..base_dn}”
filter = "(samaccountname=%{%{Stripped-User-Name}:-%{User-Name}})”
}
}
VALUES INNOVATION PERFECTION
Pre / Post Auth
• In freeRADIUS, depends on your company policies, users action can be
arranged e.g. they are on different networks
VALUES INNOVATION PERFECTION
Authorization: inner-tunnel
post-auth { ##STAFF-REKTORAT
##reject user from group alumni if ((Ldap-Group == "CN=STAFF-
REKTORAT,OU=Group,OU=Accounts,DC=uii,DC=ac,DC=i
if (Ldap-Group ==
d")) {
"CN=ALUMNI,OU=Group,OU=Accounts,DC=uii,DC=ac,DC
=id") { update reply {
update reply { Tunnel-Type = VLAN
Reply-Message = "reject user Tunnel-Medium-Type = IEEE-802
from group ALUMNI"
Tunnel-Private-Group-Id = 400
}
}
reject
}
}
}
VALUES INNOVATION PERFECTION
DHCP Allocation (CCR Mikrotik)
VALUES INNOVATION PERFECTION
Case 1: Recap
• WiFi (and WLC) part: • freeRADIUS:
• Setup SSID • Join freeRADIUS machine with AD
• Setup WPA Enterprise (enable 802.1x (using samba)
Authentication) • Setup clients.conf (connect RADIUS
• Setup RADIUS as 802.1x security and WLC)
backend • Setup authentication part
• Setup VLAN allocation (give VLAN ID • Setup authorisation part
number)
VALUES INNOVATION PERFECTION
Business Case 1: 802.1x in wired
VALUES INNOVATION PERFECTION
Scenario
• Business wants every user need to logged-in to the workstation they are
using with their own credentials
• The environment is Windows Domain
• Authentication is against Windows Server 2012 with Active Directory
• However, different group of people has different roles and permissions,
hence we need to put them on different VLAN
• We are going to use 802.1x, dynamic VLAN will be delivered using
Catalyst CISCO 2960X
VALUES INNOVATION PERFECTION
Assumptions
• Windows Domain Controller is being used, and all machines already
joined the Domain
• AD has been set up, as directory backend
• We are going to use Windows NPS (built-in RADIUS in Windows Server
2012)
• One workstation can be used by multiple users who might have different
roles i.e. different group in Active Directory
VALUES INNOVATION PERFECTION
Topology
VALUES INNOVATION PERFECTION
Setting client in NPS
VALUES INNOVATION PERFECTION
Attributes Settings
VALUES INNOVATION PERFECTION
Settings in NPS
VALUES INNOVATION PERFECTION
Catalyst’s Config
!-- DEFAULT MANAGEMENT --- !--- CONSOLE LOKAL (biar tetep bisa login ssh dengan user yg
ada di lokal switch)
vlan <vid-mgmt>
int vlan <vid-mgmt> conf t
ip address <ip-mgmt> <mask-ip-mgmt> aaa authentication login console local
no sh aaa authorization exec default local
ip default-gateway <ip-gw-mgmt>
interface range GigabitEthernet0/23 - 24 line con 0
login authentication console
description TRUNK
switchport mode trunk
!-- for VLAN definition, we simply use VTP
!--- APPLY DOT1X ON PORT on g0/1 to g0/10
!--- AAA must enable
conf t interface range g0/1 – 10
conf t switchport mode access
aaa new-model dot1x pae authenticator
aaa authentication dot1x default group radius authentication port-control auto
aaa authorization network default group radius if-
authenticated end
aaa accounting dot1x default start-stop group radius
aaa session-id common
dot1x system-auth-control
radius server <radius-name>
address ipv4 <ip-radius> auth-port 1812 acct-port 1813
key 0 <key-secret-radius>
VALUES INNOVATION PERFECTION
So what happen now?
• Whenever user logged-in to the workstation, he/she will received a
specific VLAN according to his/her roles
• One workstation might be in one VLAN at one time, and different VLAN
at other time, depends on who logged-in to the workstation i.e. different
group provides different VLAN
VALUES INNOVATION PERFECTION
Q&A?
VALUES INNOVATION PERFECTION
You might also like
- Ezekiel The End Time Prophet - Gerald Flurry PDFDocument162 pagesEzekiel The End Time Prophet - Gerald Flurry PDFNeilGWilsonNo ratings yet
- How To FingerDocument18 pagesHow To FingerAgiabAbera100% (1)
- 2018 BlackHat Arsenal - PowerUpSQL - A PowerShell Toolkit For Hacking SQL Servers On ScaleDocument82 pages2018 BlackHat Arsenal - PowerUpSQL - A PowerShell Toolkit For Hacking SQL Servers On Scalekoltkolt579No ratings yet
- Common Ipsec TroubleDocument51 pagesCommon Ipsec Troublejama99No ratings yet
- OCI Fast Track Tutorial-OCIDocument52 pagesOCI Fast Track Tutorial-OCIobuguenoNo ratings yet
- Cisco ISE Design and ArchitectureDocument69 pagesCisco ISE Design and ArchitectureMike Van Kleef100% (1)
- Configuration and Evaluation of Some Microsoft and Linux Proxy Servers, Security, Intrusion Detection, AntiVirus and AntiSpam ToolsFrom EverandConfiguration and Evaluation of Some Microsoft and Linux Proxy Servers, Security, Intrusion Detection, AntiVirus and AntiSpam ToolsNo ratings yet
- 1908 The Watchower and Herald of Christ's PresenceDocument193 pages1908 The Watchower and Herald of Christ's PresenceTimothy RichesNo ratings yet
- Practical Deployment of Cisco Identity Services Engine (ISE): Real-World Examples of AAA DeploymentsFrom EverandPractical Deployment of Cisco Identity Services Engine (ISE): Real-World Examples of AAA DeploymentsRating: 5 out of 5 stars5/5 (2)
- Demystifying 802.1x PDFDocument9 pagesDemystifying 802.1x PDFoic-ad-agNo ratings yet
- Identity Services Engine (ISE)Document33 pagesIdentity Services Engine (ISE)Vk VNo ratings yet
- Implementing 8021x AuthenticationDocument30 pagesImplementing 8021x Authenticationhari525No ratings yet
- Deploying Wired 802.1XDocument120 pagesDeploying Wired 802.1Xchico_xtrNo ratings yet
- PESTEL Analysis of MoroccoDocument2 pagesPESTEL Analysis of Moroccoethernalx67% (15)
- Unit 5 and 6Document2 pagesUnit 5 and 6Leo GonellNo ratings yet
- Ise Lab Guide For 9-11th WorkshopDocument237 pagesIse Lab Guide For 9-11th WorkshopKamalNo ratings yet
- 802.1x + LLADP + RadiusDocument30 pages802.1x + LLADP + RadiusHermawan KemisNo ratings yet
- ISE Slides PDFDocument134 pagesISE Slides PDFPablo Piriwenho Godoy0% (1)
- OpenStack NVM 2021Document120 pagesOpenStack NVM 2021AtharvaNo ratings yet
- Natural Remedies For Gout (High Uric Acid) - Natural Gout TreatmentDocument12 pagesNatural Remedies For Gout (High Uric Acid) - Natural Gout Treatmentkapoor_mukesh4uNo ratings yet
- Oracle Cloud Infrastructure - Associate Architect - Notes: IAM - Identity and Access ManagementDocument32 pagesOracle Cloud Infrastructure - Associate Architect - Notes: IAM - Identity and Access Managementsss pppNo ratings yet
- 81819-ISE Posture Configuration ExerciseDocument81 pages81819-ISE Posture Configuration ExerciseNguyen LeNo ratings yet
- OpenStack Networking TopicsDocument38 pagesOpenStack Networking TopicsJeffery Padgett100% (2)
- IDNIC 802-1x Intro-CompressedDocument54 pagesIDNIC 802-1x Intro-Compressedakun1994No ratings yet
- AAA ServersDocument25 pagesAAA ServersKalyan SannedhiNo ratings yet
- Aruba Excellence Program Aruba Instant: Presented by Michael Owen January 2015Document47 pagesAruba Excellence Program Aruba Instant: Presented by Michael Owen January 2015Sam KolaNo ratings yet
- AAWC Class 5.1r1 RevfDocument487 pagesAAWC Class 5.1r1 RevfChow Kok KeeNo ratings yet
- Rest Youtube 4Document34 pagesRest Youtube 4Abdelhak AcharqiNo ratings yet
- Breaking SAP Portal Dmitry ChastukhinDocument68 pagesBreaking SAP Portal Dmitry ChastukhinfaizquadriNo ratings yet
- What Is 802.1X - How Does It WorkDocument13 pagesWhat Is 802.1X - How Does It WorkvatcheNo ratings yet
- SISAS Student Guide Vol 1Document423 pagesSISAS Student Guide Vol 1ALINo ratings yet
- Unit-2 Working With Private CloudDocument56 pagesUnit-2 Working With Private CloudSnehal MedidarNo ratings yet
- Network As A Service in Openstack: Ilya AlekseyevDocument30 pagesNetwork As A Service in Openstack: Ilya AlekseyevImen Khabou AbidNo ratings yet
- Cybersecurity Pentesing ExpertDocument34 pagesCybersecurity Pentesing ExpertSMNo ratings yet
- Quantum Ovirt DiscussionDocument44 pagesQuantum Ovirt DiscussionkollathodiNo ratings yet
- 10190-Move and Improve With Oracle Analytics Cloud-Presentation - 287Document69 pages10190-Move and Improve With Oracle Analytics Cloud-Presentation - 287hunt4nothingNo ratings yet
- Slide-5 (AWS - IAM)Document28 pagesSlide-5 (AWS - IAM)worksukainaNo ratings yet
- Configure IEEE 802.1x Authentication With Catalyst 6500/6000 Running Cisco IOS Software................ 1Document9 pagesConfigure IEEE 802.1x Authentication With Catalyst 6500/6000 Running Cisco IOS Software................ 1Miamin RizzoNo ratings yet
- Aljaz+Mali+-+Secure+your+APEX+application Final HROUGDocument148 pagesAljaz+Mali+-+Secure+your+APEX+application Final HROUGDiganta Kumar GogoiNo ratings yet
- Developer Day - 7/21/2012 Will Chan - Director of EngineeringDocument83 pagesDeveloper Day - 7/21/2012 Will Chan - Director of EngineeringMehdi Chouikh SkalliNo ratings yet
- (Ccna) Cisco Certified Network Associate:: CCNA Examination Eligibility CriteriaDocument6 pages(Ccna) Cisco Certified Network Associate:: CCNA Examination Eligibility CriteriaRonyRoyNo ratings yet
- HCSP-Presales-Campus Network Planning and Design V1.0 Training Material-With RemarksDocument1,108 pagesHCSP-Presales-Campus Network Planning and Design V1.0 Training Material-With RemarksMuhamad Ibnu Sani El-ChusainyNo ratings yet
- All You Need To Know About Bluecoat ProxyDocument107 pagesAll You Need To Know About Bluecoat ProxyJennifer Nieves100% (2)
- 6231B 01Document28 pages6231B 01dfrr2000No ratings yet
- Developing Real World Applications in The Cloud: Joseph Acero, JSA Solutions Gina Haub, STPDocument41 pagesDeveloping Real World Applications in The Cloud: Joseph Acero, JSA Solutions Gina Haub, STPRajendran SureshNo ratings yet
- Ale Switch CheatsheetDocument1,046 pagesAle Switch Cheatsheetrakyat mataramNo ratings yet
- Cloud - Training 19 10 2019Document41 pagesCloud - Training 19 10 2019Riyas MohamedNo ratings yet
- Omnivista 2500 Nms & Omniaccess - Alcatel-Lucent EnterpriseDocument716 pagesOmnivista 2500 Nms & Omniaccess - Alcatel-Lucent EnterprisejghiNo ratings yet
- Cisco ACS EduroamDocument43 pagesCisco ACS EduroamNalin SinghNo ratings yet
- Cisco and Open Stack PresentationDocument17 pagesCisco and Open Stack PresentationManoj SamtaniNo ratings yet
- Implementing and Administering Cisco Solutions (CCNA) : Related Certificate Course ID Related Exam Audience HoursDocument6 pagesImplementing and Administering Cisco Solutions (CCNA) : Related Certificate Course ID Related Exam Audience HoursChristina FingtonNo ratings yet
- Introduction To SQL Server® 2012 and Its ToolsetDocument28 pagesIntroduction To SQL Server® 2012 and Its ToolsetDip Madav100% (1)
- Cloud Foundation - PresentationDocument68 pagesCloud Foundation - PresentationRiyas MohamedNo ratings yet
- The History of DevOps & NetDevOpsDocument8 pagesThe History of DevOps & NetDevOpsCyber PunkNo ratings yet
- Openstack Brief and DemoDocument40 pagesOpenstack Brief and DemoDede PratamaNo ratings yet
- OPENSTACK (Cloud Computing)Document32 pagesOPENSTACK (Cloud Computing)nikitaNo ratings yet
- Cisco Virtualized Application Container Services 2-0 v1 Lab GuideDocument34 pagesCisco Virtualized Application Container Services 2-0 v1 Lab GuideDennisse MierNo ratings yet
- 3.4 Introduction To Private Clouds and OpenStackDocument13 pages3.4 Introduction To Private Clouds and OpenStack22mt0045No ratings yet
- Session 08Document8 pagesSession 08bouzid.salim47No ratings yet
- Intro To Openstack & SDN Meetup 1 SDNRG ITB: Ady Saputra - Ady@comlabs - Itb.ac - IdDocument22 pagesIntro To Openstack & SDN Meetup 1 SDNRG ITB: Ady Saputra - Ady@comlabs - Itb.ac - Idno07No ratings yet
- Chapter 01Document26 pagesChapter 01hadiqhusnainNo ratings yet
- Openstack Neutron and SDNDocument26 pagesOpenstack Neutron and SDNdileepNo ratings yet
- (640-802) CCNA (Blueprint) : Course DescriptionDocument5 pages(640-802) CCNA (Blueprint) : Course DescriptionbnhamzNo ratings yet
- The Adventist Perspective of Unity With CatholicismDocument12 pagesThe Adventist Perspective of Unity With Catholicismfortyniner85No ratings yet
- Snigdha Chaturvedi PDFDocument5 pagesSnigdha Chaturvedi PDFHitesh KohliNo ratings yet
- Kitimat JRP SummaryDocument17 pagesKitimat JRP SummaryNorthwest InstituteNo ratings yet
- Hostel Standard and Safety MeasuresDocument16 pagesHostel Standard and Safety MeasuresSadiya IqbalNo ratings yet
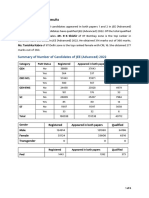
- Jeeadv 2022 Press ReleaseDocument6 pagesJeeadv 2022 Press ReleaseIzumiNo ratings yet
- Pms 500 - International Mechanics KitDocument0 pagesPms 500 - International Mechanics KitArsul RNo ratings yet
- DissertationDocument134 pagesDissertationAbbas AbbasiNo ratings yet
- James Rachels - What Is MoralityDocument26 pagesJames Rachels - What Is MoralityKiara Lagrisola100% (1)
- Particulate Ow at The Mouth of The Soummam Watershed (Algeria)Document9 pagesParticulate Ow at The Mouth of The Soummam Watershed (Algeria)bougheraraNo ratings yet
- AlerTox Sticks Soy PLUS ManualDocument8 pagesAlerTox Sticks Soy PLUS ManualLuis Miguel Matos OteroNo ratings yet
- The Human Body: Winston S. Abena, RMT, MD, DPASMAPDocument51 pagesThe Human Body: Winston S. Abena, RMT, MD, DPASMAPMinelli ArgonzaNo ratings yet
- The Dedicated - A Biography of NiveditaDocument384 pagesThe Dedicated - A Biography of NiveditaEstudante da Vedanta100% (2)
- Lesson 1 Exploring Indian LiteratureDocument5 pagesLesson 1 Exploring Indian LiteratureAthan MensalvasNo ratings yet
- Public Health LawsDocument16 pagesPublic Health Lawscharlene bermasNo ratings yet
- STEPOSOLMET10 UHousehold Cleaning Sales ToolDocument2 pagesSTEPOSOLMET10 UHousehold Cleaning Sales Toolpkh29No ratings yet
- SuperconductivityDocument13 pagesSuperconductivityprashanth68760100% (3)
- BDU-BIT-Electromechanical Engineering Curriculum (Regular Program)Document187 pagesBDU-BIT-Electromechanical Engineering Curriculum (Regular Program)beselamu75% (4)
- Cemont 2011 Chapter 3 Mig Mag Welding239619Document21 pagesCemont 2011 Chapter 3 Mig Mag Welding239619josechr6100% (1)
- TDS - 0121 - CapaCare Classic - 201912Document5 pagesTDS - 0121 - CapaCare Classic - 201912ayviwurbayviwurbNo ratings yet
- Node Name Ping Status Community IP Address: CAPSTONE - IT Infrastructure Monitoring SNMP WalkDocument4 pagesNode Name Ping Status Community IP Address: CAPSTONE - IT Infrastructure Monitoring SNMP WalkSpartacus CaesarNo ratings yet
- Wilkins Excel SheetDocument9 pagesWilkins Excel SheetYuvraj Aayush Sisodia100% (1)
- This Study Resource Was: Rizal Morga Lifestyle: LifestyleDocument2 pagesThis Study Resource Was: Rizal Morga Lifestyle: LifestyleMarjorie GawalaNo ratings yet
- 01 IKSP and Environmental MovementsDocument12 pages01 IKSP and Environmental MovementsGlister Diadem DolleraNo ratings yet
- 4194-Article Text-11162-1-10-20190903Document6 pages4194-Article Text-11162-1-10-20190903Akhsana SantosoNo ratings yet