Professional Documents
Culture Documents
How It Works (All Steps)
Uploaded by
Anas Toufeeq0 ratings0% found this document useful (0 votes)
10 views11 pagesOriginal Title
How It Works ( All Steps)
Copyright
© © All Rights Reserved
Available Formats
DOCX, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
© All Rights Reserved
Available Formats
Download as DOCX, PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
10 views11 pagesHow It Works (All Steps)
Uploaded by
Anas ToufeeqCopyright:
© All Rights Reserved
Available Formats
Download as DOCX, PDF, TXT or read online from Scribd
You are on page 1of 11
Chapter 3 – Exercise: Enabling Multifactor Authentication
Chapter 3 – Exercise: Creating a User with Read-Only Rights
Chapter 4 – Exercise: Enabling Storage Container Encryption
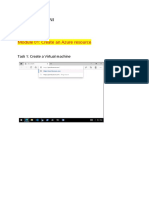
Chapter 4 – Exercise: Enabling VM Disk Encryption
You might also like
- Nbu82adm Les09Document72 pagesNbu82adm Les09Christopher MeyerweckNo ratings yet
- Nbu82adm Les10Document78 pagesNbu82adm Les10Christopher MeyerweckNo ratings yet
- Secure CRT Scripting Essentials PDFDocument122 pagesSecure CRT Scripting Essentials PDFputakoNo ratings yet
- Oracle Infrastructure Architect Associate All One PDFDocument663 pagesOracle Infrastructure Architect Associate All One PDFtimirkantaNo ratings yet
- Cloud+ Certification Chapters 3 and 4 Labs DocumentationDocument4 pagesCloud+ Certification Chapters 3 and 4 Labs DocumentationAnas ToufeeqNo ratings yet
- 07 VirtualMachinesDocument101 pages07 VirtualMachinessrabgroupNo ratings yet
- We Have Credentials To Log In. Let's Use Them To Login and Check For Vulnerable Input FieldsDocument4 pagesWe Have Credentials To Log In. Let's Use Them To Login and Check For Vulnerable Input FieldscontactNo ratings yet
- 70 412.moac - Lab.manualDocument304 pages70 412.moac - Lab.manualTakeshi Onikawara100% (2)
- VS5ICM M10 ResourceMonitoring PDFDocument70 pagesVS5ICM M10 ResourceMonitoring PDFMadhav KarkiNo ratings yet
- EDU EN VS Optimize Scale 7 LAB IE PDFDocument127 pagesEDU EN VS Optimize Scale 7 LAB IE PDFIsmail BarbourNo ratings yet
- Commvault - v11 PDFDocument106 pagesCommvault - v11 PDFMuhammad BurhanNo ratings yet
- Vmware Vsphere Icm 67 Lab ManualDocument142 pagesVmware Vsphere Icm 67 Lab ManualJavier Mariani0% (1)
- Kaspersky Endpoint Security and Management. Fundamentals: ID KL-002.11.1 Price On Request Duration 3 DaysDocument2 pagesKaspersky Endpoint Security and Management. Fundamentals: ID KL-002.11.1 Price On Request Duration 3 DaysSoufianeSaiDarNo ratings yet
- Modulo 4 VDC Storage CloudDocument41 pagesModulo 4 VDC Storage CloudChelashia RoshiniNo ratings yet
- Security Computing-4-AuthenticationDocument36 pagesSecurity Computing-4-Authenticationmqarwa2No ratings yet
- CIS Module 4 VDC StorageDocument34 pagesCIS Module 4 VDC StorageyoonghanNo ratings yet
- JasperReports Server Security GuideDocument92 pagesJasperReports Server Security GuideRafael Maiorali Agostino Leão ErenoNo ratings yet
- KVM ManagementDocument5 pagesKVM ManagementMangesh AbnaveNo ratings yet
- Dev m9 Demodoc2 v1 Xao z36sf3wDocument4 pagesDev m9 Demodoc2 v1 Xao z36sf3wShishanki KushwahNo ratings yet
- FortiClient EMS 6.2 Lab Guide-OnlineDocument85 pagesFortiClient EMS 6.2 Lab Guide-OnlineDarko SpunkyNo ratings yet
- Fortinet Zero Trust Access Lab Guide For FortiOS 7.2 (Fortinet Training Institute)Document247 pagesFortinet Zero Trust Access Lab Guide For FortiOS 7.2 (Fortinet Training Institute)Sérgio Peres100% (1)
- Lab Exercises - XFSC-7021-MC1 - Network Security Kali Linux - 49070 - OnlineDocument2 pagesLab Exercises - XFSC-7021-MC1 - Network Security Kali Linux - 49070 - Onlinegojan39660No ratings yet
- Cloudera VM Machine Setup Guide+Document4 pagesCloudera VM Machine Setup Guide+nadiaNo ratings yet
- Control 2 CC 202 - HAITAM ELJOUNI PDFDocument25 pagesControl 2 CC 202 - HAITAM ELJOUNI PDFHaitam El JouniNo ratings yet
- MS Azure: Online, Classroom, Corporate Mr. Khaja 45 DaysDocument15 pagesMS Azure: Online, Classroom, Corporate Mr. Khaja 45 DaysKranti KumarNo ratings yet
- VMware VSphere ICM 6.7 Lab ManualDocument142 pagesVMware VSphere ICM 6.7 Lab Manualitnetman93% (29)
- CCP User Guide 2 1 0 - Chapter - 0111Document6 pagesCCP User Guide 2 1 0 - Chapter - 0111Marius StefanNo ratings yet
- B Ve Inst UserDocument154 pagesB Ve Inst UserJlinx Jebm JebmNo ratings yet
- Module 2.3 Shared Folder in VMWare-583007a61ff9Document10 pagesModule 2.3 Shared Folder in VMWare-583007a61ff9AbhinandNo ratings yet
- Fireware Essentials Student Guide (En US) v11 12Document504 pagesFireware Essentials Student Guide (En US) v11 12Gleidson CamposNo ratings yet
- Risk Assesment Report 1Document4 pagesRisk Assesment Report 1Rohit ParchuriNo ratings yet
- B Msgs FCM PDFDocument598 pagesB Msgs FCM PDFJavier GonzalezNo ratings yet
- Lotus Notes 8.5.1 Administration (DSCA851)Document4 pagesLotus Notes 8.5.1 Administration (DSCA851)marializaestellaNo ratings yet
- Deploying With JrubyDocument220 pagesDeploying With JrubyAri OseiasNo ratings yet
- Privileged Remote Access For Administrators: Powered by BomgarDocument2 pagesPrivileged Remote Access For Administrators: Powered by BomgarneoaltNo ratings yet
- The Version 4 Authentication Dialogue: Network SecurityDocument24 pagesThe Version 4 Authentication Dialogue: Network SecurityAbdullah ShahidNo ratings yet
- Troubleshooting Hyper V First AidDocument55 pagesTroubleshooting Hyper V First AidwsedcNo ratings yet
- Configuring and Troubleshooting Network File and Print ServicesDocument31 pagesConfiguring and Troubleshooting Network File and Print ServicesAlecs DenisNo ratings yet
- Penetration Testing With Kali Linux (PWK)Document6 pagesPenetration Testing With Kali Linux (PWK)DF QWERTNo ratings yet
- Vmware Vsphere: Install, Configure, Manage: Lab Manual Esxi 6.7 and Vcenter Server 6.7Document144 pagesVmware Vsphere: Install, Configure, Manage: Lab Manual Esxi 6.7 and Vcenter Server 6.7Dharmesh BNo ratings yet
- Vmware Data Recovery 1.0 Evaluator'S GuideDocument25 pagesVmware Data Recovery 1.0 Evaluator'S GuideBuy SellNo ratings yet
- FULLTEXT01Document92 pagesFULLTEXT01sasif0007No ratings yet
- Chapter 01Document4 pagesChapter 01Amin KhozaeiNo ratings yet
- OCI IAM ServiceDocument14 pagesOCI IAM ServiceHarish NaikNo ratings yet
- Firecracker microVMDocument4 pagesFirecracker microVMbalzofayeNo ratings yet
- Linux System Administration Part-2Document1 pageLinux System Administration Part-2AtaurRahmanNo ratings yet
- Edu en Vskdm7 Lab IeDocument104 pagesEdu en Vskdm7 Lab IeRaju NNo ratings yet
- Bản sao của Technology Infographics by SlidesgoDocument9 pagesBản sao của Technology Infographics by Slidesgojellie jNo ratings yet
- Powering On A VM ConfiguredDocument3 pagesPowering On A VM ConfiguredMohd AyoobNo ratings yet
- VM Resource Management: Vmware Infrastructure 3: Install and Configure - Rev BDocument61 pagesVM Resource Management: Vmware Infrastructure 3: Install and Configure - Rev Bsurkal100% (2)
- V Sphere Security@nettrainDocument428 pagesV Sphere Security@nettrainelahi elahiNo ratings yet
- Kaspersky Endpoint Security and Management: Duration 3 DaysDocument3 pagesKaspersky Endpoint Security and Management: Duration 3 DaysifowebbNo ratings yet
- Nbu 65 Unix CertificationDocument5 pagesNbu 65 Unix CertificationTeja VarmaNo ratings yet
- KPLABS CKA D7 - StorageDocument8 pagesKPLABS CKA D7 - StorageAmit KumarNo ratings yet
- VMware Vsphere Optimize and Scale v6 Lab GuideDocument150 pagesVMware Vsphere Optimize and Scale v6 Lab Guideemcvilt100% (4)
- KB Msp360 Com Standalone Backup General A Required Privilege Is Not Held by ClientDocument1 pageKB Msp360 Com Standalone Backup General A Required Privilege Is Not Held by ClientBmw004No ratings yet
- Module 2.4 Record VMs-c09ab99bc945Document7 pagesModule 2.4 Record VMs-c09ab99bc945AbhinandNo ratings yet
- Project Title Library Management System: SubjectDocument11 pagesProject Title Library Management System: SubjectraheeledNo ratings yet
- Unit 3 Assignment 1Document5 pagesUnit 3 Assignment 1Anas ToufeeqNo ratings yet
- Week 2 Lab Cyb 462Document7 pagesWeek 2 Lab Cyb 462Anas ToufeeqNo ratings yet
- Unit 3 AssignmentDocument6 pagesUnit 3 AssignmentAnas ToufeeqNo ratings yet
- Medical Supply CompanyDocument3 pagesMedical Supply CompanyAnas ToufeeqNo ratings yet
- Task 111Document2 pagesTask 111Anas ToufeeqNo ratings yet
- Unit 3 Assignment 1Document4 pagesUnit 3 Assignment 1Anas ToufeeqNo ratings yet
- Unit 4 Assignment 1 JB IT3225Document5 pagesUnit 4 Assignment 1 JB IT3225Anas ToufeeqNo ratings yet
- Invoice: FromDocument1 pageInvoice: FromAnas ToufeeqNo ratings yet
- ITEC 625 9042 Computer Systems ArchitectureDocument11 pagesITEC 625 9042 Computer Systems ArchitectureAnas ToufeeqNo ratings yet
- Week Two Lab AssignmentDocument1 pageWeek Two Lab AssignmentAnas ToufeeqNo ratings yet
- Part 2Document11 pagesPart 2Anas ToufeeqNo ratings yet
- The Auto RunsDocument4 pagesThe Auto RunsAnas ToufeeqNo ratings yet
- Denver International Airport (DIA)Document6 pagesDenver International Airport (DIA)Anas ToufeeqNo ratings yet
- CSCI 220 Operating Systems Lab Series #4Document3 pagesCSCI 220 Operating Systems Lab Series #4Anas ToufeeqNo ratings yet
- Process Explorer UtilityDocument13 pagesProcess Explorer UtilityAnas ToufeeqNo ratings yet
- IT FP2250 KellyTravis Assessment6 1Document6 pagesIT FP2250 KellyTravis Assessment6 1Anas ToufeeqNo ratings yet
- IT FP3225 McClainKathleen Assessment 1 Attempt 1Document3 pagesIT FP3225 McClainKathleen Assessment 1 Attempt 1Anas ToufeeqNo ratings yet
- IT2250 Unit 4 AssignmentDocument3 pagesIT2250 Unit 4 AssignmentAnas ToufeeqNo ratings yet
- PSDocument3 pagesPSAnas ToufeeqNo ratings yet
- Business Problem UpdatedDocument6 pagesBusiness Problem UpdatedAnas ToufeeqNo ratings yet
- Harvest CictyDocument8 pagesHarvest CictyAnas ToufeeqNo ratings yet
- Part 2Document12 pagesPart 2Anas ToufeeqNo ratings yet
- InstructionsDocument2 pagesInstructionsAnas ToufeeqNo ratings yet
- CSCI 220 Operating Systems Lab Series #3Document3 pagesCSCI 220 Operating Systems Lab Series #3Anas ToufeeqNo ratings yet
- Chapter 7 Exercise Creating A Web ApplicationDocument7 pagesChapter 7 Exercise Creating A Web ApplicationAnas ToufeeqNo ratings yet
- AssignmentDocument2 pagesAssignmentAnas ToufeeqNo ratings yet
- IT FP2250 KellyTravis Assessment6 1Document6 pagesIT FP2250 KellyTravis Assessment6 1Anas ToufeeqNo ratings yet
- CYB462Document3 pagesCYB462Anas ToufeeqNo ratings yet
- Cybr520week1week2printable PDFDocument11 pagesCybr520week1week2printable PDFAnas ToufeeqNo ratings yet