Professional Documents
Culture Documents
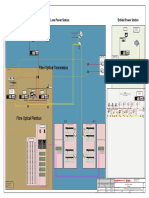
Industrial Network Security Monitoring - ICS - NSM - POSTER
Uploaded by
Ani MOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Industrial Network Security Monitoring - ICS - NSM - POSTER
Uploaded by
Ani MCopyright:
Available Formats
Industrial Network Security Monitoring
TAP vs. SPAN: The decision as to which method to use for NSM Collection may
depend on budget, maintenance windows, existing technology, and production
network architecture.
NSM Collection
Pros Cons
Method
TAP Hardware • Capture also includes network • ICS network outage required
This poster offers guidance on setting up and performing Network Security Monitoring (NSM) with freely available, no-cost •
errors – malformed packets, etc.
Dedicated hardware – TAP more
challenging to compromise than
• Additional hardware
equired
tools to carry out active cyber defense in industrial control system (ICS) environments. Several traditional concepts are
a switch SPAN configuration
adapted to provide an “ICS aspect” to further cybersecurity efforts in control networks.
SPAN Configuration • Deploys on existing fully • May miss or drop mirrored
managed switches in phased-in packets if switch is
approach overloaded
• No ICS network outage required • May not capture network
error communications
NETWORK SECURITY MONITORING • ite Name
S • IP and MAC address CRITICAL ICS ASSETS EtherNetIP/CIP SPAN Configuration Example: Commands differ across switch manufacturers. The
• Site location • Operating ICS protocols used Port: UDP 2222, TCP 44818 example below shows pseudo commands for setting up a SPAN configuration on a
NSM (Network Security Monitoring) is a human driven proactive repeatable process • Facility type • Model/manufacturer, serial number Critical industrial assets can be targeted with malware. Also, human adversaries tshark/Wireshark filter “enip” switch to create a local SPAN session 1 to monitor bi-directional traffic from port 1
of Collection, Detection, and Analysis. While not specific to ICS (Industrial Control • Asset type and ID tag • Firmware version can target the control system to cause negative impacts on the process through Application: EtherNetIP/CIP is commonly observed in manufacturing facilities, to port 2, and to verify that the change is applied:
Systems), NSM excels in control system networks as the environment is usually • Asset location: room, cabinet, rack • Applications installed and versions directly interacting with the control environment using legitimate operational using both UDP and TCP. UDP is used for I/O data transfers, while TCP is used for
more static and has less users than in traditional IT (Information Technology) • Description of asset function software with malicious intent. Several critical ICS assets are below. At a minimum, set points to be set or read. # monitor session 1 source interface gigabitethernet1/1 both
environments. NSM is most effective with an established ICS asset inventory and is • Impact to operations if unavailable access control, network traffic and system integrity should be protected and # monitor session 1 destination interface gigabitethernet1/2
an active approach in detecting threats in early phases of an attack. regularly monitored for these assets. DNP3 # show monitor all
Augment physical inspection with passive network packet captures on critical Port: TCP 20000
network segments that have critical ICS assets by using either a SPAN configuration Data Historian – This is a database that stores operational process records. Can be tshark/Wireshark filter “dnp3” NETWORK SECURITY MONITORING – ICS-COMPATIBLE
ICS ASSET INVENTORY off a fully managed switch or utilize a hardware TAP. abused to act as a pivot point from a compromised asset in IT to an asset in the ICS Application: Distributed Network Protocol version 3 is commonly observed in
TOOLS
network. water and electricity power utilities, and occasionally in gas pipeline operations.
Having an established ICS asset inventory of operational technology devices and Common host and network commands to discover data to help build the ICS asset It is used for communications between control centers and field devices such as
engineering assets will drastically improve industrial network security monitoring inventory with built-in operating system and network tools and capabilities. LLDP Engineering Workstation - The engineering workstation has software to program Remote Terminal Units (RTUs) or Intelligent Electronic Devices (IEDs). Many no-cost, open-source tools are available to assist organizations as they
efforts and assist in ICS Incident Response scenarios. (Link Layer Discovery Protocol), is a Layer 2 discovery protocol which is vendor- and change PLC and other field device settings/configurations. mature their ICS security program and ICS NSM capabilities. Several tools have
neutral and can be used to identify network assets and their capabilities. tshark IEC 60870-5-104 built-in or ICS-specific features or plugin modules.
Common methodologies to establish the inventory are below and can be filters can be used to reveal asset information from a packet capture using the lldp Human Machine Interface - The HMI is a visual interface between the physical Port: TCP 2404, 2405
combined for improved accuracy. For example, Physical Inspection will take filter. ARP (Address Resolution Protocol), the ‘arp’ tool is a simple tool available process and operators that is used to monitor, control, and change most any part tshark/Wireshark filter “iec60870_104” Security Onion: A no-cost, open-source Linux platform designed for intrusion
advantage of face-to-face security awareness and educational discussion on- in common operating systems to reveal ARP cache to show IP and MAC addresses of the industrial process. Application: The IEC 60870-5-104 Protocol is commonly observed in the electricity detection, network security monitoring, and event log management with many
site with engineering and operational teams. Augmented with Passive Network pairing in which that device knows about on the network. Start with the top critical sector to monitor power systems and has the capabilities to restart devices and supporting tools built in.
Captures can create and verify an inventory while having network traffic to sift ICS assets first. Programmable Logic Controllers – PLCs connect the physical hardware, run logic modify set points in the field.
through for threat detection. code to read the state, change the state or a process, and interfaces with devices Snort: Intrusion Detection System (IDS) with many ICS-specific preprocesses built
Discover LLDP compatible systems, their names and and network capabilities: that make physical changes in the real-world. IEC 61850 in to help detect ICS vulnerabilities and attack traffic in control networks. ICS
Asset identification information is available from several network devices such as tshark: tshark -Y lldp -T fields -e lldp.tlv.system.name -e Port:102 plugins available.
routers, switches, and firewalls. Beyond the network layer, asset information can be lldp.tlv.system.desc -e lldp.tlv.system_cap -r <ICS-Network_ tshark/Wireshark filter “goose”
discovered by extracting data directly from endpoints themselves such as the Data file.pcap> Application: IEC 61850 is a communications protocol commonly used for Tcpreplay: Command-line network tool to play packet capture files (pcap) against
historians, HMI etc.
INDUSTRIAL CONTROL NETWORK PROTOCOLS communications with Intelligent Electronic Devices (IEDs) at electric substations. a network interface card. Used in conjunction with Snort, or similar IDS systems,
Discovery asset IP and MAC addresses from ARP tables: to sift through network communication for known malicious activity and to test
Linux: arp -an Use common tshark/Wireshark filters to focus on industrial control network custom ICS network threat signatures.
Physical Inspection – Getting physically to industrial facilities, documenting the
communications to aid in engineering troubleshooting and security initiatives.
hardware seen in racks, cabinets, on plant floor, software and protocols used, etc. Windows: arp /a
There are many industrial protocols, the following are just some of the most NETWORK SECURITY MONITORING – SETUP Wireshark: Graphical user interface packet analysis tool with built-in dissectors
Time consuming, accurate, can be expensive if traveling to remote sites. There is Switches, Firewalls: show arp
common protocols in use in their related sectors. for many common industrial protocols. Also has capabilities to extract file objects
some potential physical risk, so PPE (Personal Protective Equipment) is required on There are two main methods to ensure that NSM Collection is established and
sites. Discover connections and their related IP addresses on an asset: from packet captures.
ModbusTCP serves as a critical step to improve any modern ICS security program: Network TAP
Linux: netstat -an and Network SPAN.
Windows: netstat /an Port: TCP 502 Tshark: Command-line packet analysis tool supporting Wireshark filters with many
Passive Network Packet Capture - Nonintrusive to ICS operations, accurate
tshark/Wireshark filter “mbtcp” of the same capabilities.
representation of natural network comms. Can be quick. Can output a visual Network TAP - A purpose-built hardware device
Managing the ICS Asset Inventory: Application: The TCP version of the serial protocol Modbus is an open industrial
network diagram that can be printed and used for engineering troubleshooting installed in-line in a network that copies network
The asset inventory is incredibly valuable for the organization, but also for protocol standard, the de facto standard, commonly used to communicate with GRASSMARLIN: An open-source network mapping tool created by the National
and ICS Incident Response. traffic. It typically requires a network outage to
attackers. Safeguard ICS asset inventory by storing it in a database that is: IP-connected field devices to/from HMIs and intelligent electronic devices across Security Agency’s Information Assurance Directorate specifically for ICS network
several industrial sectors, including the electricity sector. install. Always ensure that it is configured to fail packet captures. It will output information about devices, control network
Active Scanning - Intrusive to ICS operations, unnatural representation of network open, allowing traffic to flow through the device
comms., but very fast and very detailed information about devices, services, etc. Scalable - Databases can help ensure that site inventories can be updated or communications, and data extracted about the industrial protocols in use.
BACnet (Building Automation Controls) in the event of a failure. Otherwise, it will drop or GRASSMARLIN can also output a primitive network diagram from a live network
Should be tested in a development environment prior to scanning any production expanded, and back them up regularly. block legitimate control network communication.
Port: UDP 47808 collection from a tap, or offline traffic captured from a SPAN configuration into
environment. TAP installations in industrial control environments
Searchable - All fields should be indexed to enable quick searching across tshark/Wireshark filter “bacnet” pcap files.
Application: The Building Automation Controls protocol enables communications are usually added as a task as part of a scheduled
Configuration Analysis - Many control system and network devices may have to be inventories for all sites. operational maintenance window when operations
for building automation and controls for Heating Ventilation Air Conditioning NetworkMiner: A protocol-aware network tool. A no-cost version is available that
accessed to review configuration settings. Switch and firewall configurations can are scheduled to be down.
Secure - Standard data protection and security practices, including authentication (HVAC) systems. can extract objects from packet captures such as credentials and several file types.
reveal IP address and MAC address pairings through ARP tables to indicate devices
allowed or denied access on the network. Traffic and port information at a 5-tuple and network segmentation, should be used to protect this sensitive data.
OPC (Open Platform Communications) Zeek: An open-source IDS and NSM tool for Linux. It has some ICS capabilities
level could reveal general protocols in use. Network SPAN - Also known as port mirroring, this
A practical approach - Use threat intelligence to drive searches across an Port: <several>, sometimes TCP 135 and DCE/RPC ports built in and can be expanded further with additional ICS plugins from the
tshark/Wireshark filter “opcua” or “dcerpc” may be available on already-deployed managed community. Zeek also has features such as network flow analysis and others.
A practical approach - Start by reviewing any already created network diagrams. established inventory database to understand which ICS assets have identified switches in a control network. No network outage
vulnerabilities. Identify vulnerable industrial assets for proactive defense changes Application: Open Platform Communications can be implemented in several ways,
Use an encrypted laptop with at least a basic spreadsheet application to start is required to implement it. SPAN configurations
starting with the most critical assets first. Combine asset inventory knowledge with which determines the ports that will be utilized when the communications are
cataloging and storing ICS asset information during a physical site walkthrough. can be phased in. Phase VLANs, network segments,
ICS Network Security Monitoring to monitor for traffic anomalies that may lead to deployed. Observing Distributed Computing Environment/Remote Procedure
At a minimum, record the following attributes from the commonly targeted critical into the SPAN configuration one or two at a time
NSM Detection and NSM Analysis phases. Call (DCE/RPC) traffic can help identify OPC in use. OPC is used to enable
assets such as Data Historians, HMI, PLCs, Engineering Workstations, core network to ensure the switch CPU and memory can manage
communications from different vendor devices in a vendor-natural way.
devices, and active Safety Instrumented Systems (SIS) used. the SPAN load copying packets to a mirror port.
COLLECT DETECT NETWORK SECURITY
MO N I TO R I N G – I N
NETWORK SECURITY MONITORING – COLLECTION
A properly segmented ICS network following the Purdue network architecture model has enforcement boundaries, naturally creating chokepoints for network data collection. It also
NETWORK SECURITY MONITORING – DETECTION
Network detection is about discovering potentially malicious and/or abnormal activity, including detecting unusual
PRACTICE
doubles as control points for containment in industrial incident response. Collect ICS traffic at Purdue Levels 0-3 at a minimum – communications to and from the HMIs, PLCs,
inbound or outbound connections, network events linked to known IP addresses to threat campaigns, and other
RTUs, and other IEDs in critical network segments. Common network collection points would be on internal edge or zone industrial firewalls, or core control network switches.
network anomalies.
Use fully managed network switches to passively collect data via SPAN, or from hardware TAP devices that would be installed in-line.
NSM Collection Platform
Leverage threat intel from the applicable ICS sector and tools such as tcpreplay and Snort, with built-in ICS
ICS ASPECT - COLLECTION: Collect the 5-tuple data at a minimum, where full-packet collection would be ideal to ensure that industrial protocol rulesets, and pseudocode rules below, to start network detection specific to a control environment. Known IP
communications and data are also captured. Beyond just security events, ICS NSM can uncover general networking and engineering system addresses associated with attack campaigns can be used to search across network flow data or packet captures First, phase in NSM Collection around the most critical and vulnerable ICS assets. Start with
from intrusion detection systems monitoring network communications. Expand and change pseudo rules and the most important IP-connected engineering operation or facility and deploy one network
misconfigurations to improve overall industrial network efficiency and resilience.
logic to suit the organizations’ control network and setup. segment at a time.
The 5-tuple Capture: Consists of the source and destination IP addresses, source and destination ports, and protocols observed.
Sift through collected data for indicators of compromise starting with IP addresses. Use threat
ICS ASPECT - DETECTION: An Intrusion Detection System (IDS) is preferred for threat detection
intel to drive searches across an established inventory database to identify vulnerabilities in
5
in ICS environments over an Intrusion Prevention System (IPS). IDS systems are used to targeted assets that could be flagged for proactive defense changes.
prioritize safety, that is, to reduce false positives that could cause legitimate control
commands causing operational disruptions. The Detection phase of NSM is primarily Control network traffic can be collected by purpose-built ICS NSM technology. Alternatively,
Source IP
address 1 about understanding what is “normal” for the industrial operations to be better at
even the no-cost Linux Security Onion distribution on a laptop with external storage, using
built-in tools such as tcpdump or Wireshark, can be used to start ICS NSM Collection. For
4
spotting “abnormal” activity. These tools and filters can get a program started. Detection and Analysis, Wireshark, which has several built-in packet dissectors for common
Source
industrial protocols, can be helpful in determining the assets, protocols in use, and
Port
2
Destination Replay packet captures against a listening network IDS such as Snort: communication patterns in an industrial environment. The tools discussed here can also be
sudo tcpreplay --intf1=<nic_for_snort > --mbps=topspeed <ICS-
COLLECT
IP address used to extract objects for further analysis to assist with ICS Incident Response efforts.
Network_file.pcap>
5 Destination
Port THE NETWORK Alert on communications to PLC that is not HMI: Passive ICS Network Traffic Capture Window
3
Protocol 5 TUPLE alert tcp !$Modbus_HMI any -> $Modbus_PLC any (msg:“TCP comms
DETECT
used to PLC which is not the HMI”;) Passive control network capture times could be as short as several hours for point-in-
time assessments. This would depend on the objective, storage, and size of the control
Alert on possible recon scan or mapping if ModbusTCP is not normally used: environment. Point-in-time assessment for full-packet captures is commonly between 1 and
alert tcp any any -> any 502 (msg:“Scan or usage of 24 hours.
ANALIZE
ModbusTCP on network without it”;)
Full-Packet Capture: Consists of the entire packet - including the 5-tuple data as well as the full packet payload,
such as the query and response data, industrial commands, function codes, and other artifacts. Even files in the Alert on possible TCP connection to known malicious command and Control System Network Capture Considerations
packet payload may be extracted for analysis during incident response cases, such as malware samples. Full-packet control server:
capture does consume significantly more storage space than just capturing 5-tuple data. alert tcp any any -> <evil_C2_ip> any Note that the control system could be in several operational states, which can affect network
(msg:“Connection attempt to known evil C2 IP collection output. If the system is in a safe-shutdown, maintenance, or emergency procedure,
address”;) devices that do not normally communicate will be visible, and the more active devices may be
invisible. The most effective captures will be during the industrial process start-up and during
5
normal operations.
ICS Threat Detection Concepts for 5-TUPLE
Unusual spikes
in traffic Start and repeat the NSM Collection,
Detection, and Analysis phases
while applying these tips to
ANALIZE
prioritize the safety and reliability
THE NETWORK of ICS operations. Add additional
5 TUPLE Top talker IP
addresses
engineering knowledge for more
specific industrial control system
1
protection. High confidence
Indicator of Compromise matches
NETWORK SECURITY MONITORING – ANALYSIS Asset names from DNS that could be assets performing Internet checks: and the discovery of anomalous
tshark: tshark -T fields -e ip.src -e dns.qry.name -Y “dns.flags.response eq 0” -r <ICS- Devices talking network patterns will call industrial
Use triggered signatures, which match on malicious activity such as IP addresses from attack Network_file.pcap> | sort | uniq that should not incident response steps into action.
Response: Trans: 6; Unit: 255, Func: 4: Read Input Registers
campaigns. From the Detection phase on these triggers, pivot to the Analysis phase. With Traffic going to external addresses by internal source IP to external IP:
Query: Trans: 10; Unit: 255, Func: 4: Read Input Registers an understanding of which assets on the network are critical for safety and operations, work tshark: tshark -T fields -e ip.src -e ip.dst -r <ICS-Network_file.pcap> “not ip.dst in
to identify anomalous network connections around them to help determine when ICS Incident {192.168.0.0/16 172.16.0.0/12 10.0.0.0/8}” | sort | uniq
Query: Trans: 1435; Unit: 255, Func: 15: Write Multiple Coils Response is needed. Expand or change the tshark or Wireshark filters below to suit the hunt for Matches on known
malicious network activity. Encrypted communications, less common in ICS, which could be covert channels: malicious IPs
Query: Trans: 12062; Unit: 255, Func: 15: Write Multiple Coils tshark: tshark -Y tls -T fields -e ip.src -e ip.dst -e tcp.port -e _ws.col.Info -r
ICS ASPECT - ANALYSIS: ICS environments have far less connectivity to the Internet and use <ICS-Network_file.pcap> | sort | uniq
Response: Trans: 12062; Unit: 255, Func: 15: Write Multiple Coils
much less encrypted communications inside control networks than in traditional IT environments. Protocols in use on the control network: ICS Threat Detection Concepts ICS Threat Detection
Query: Trans: 20308; Unit: 255, Func: 1: Read Coils
In addition, ICS attack techniques can abuse legitimate native industrial control protocols. These tshark: tshark -T fields -e frame.protocols -r <ICS-Network_file.pcap> | sort | uniq | for Deep Packet Analysis Based on ICS Behavior
Response: Trans: 20308; Unit: 255, Func: 1: Read Coils types of network communications should be flagged for analysis to rule out suspicious activity. cut -d : -f 2-20
Discover and analyze information, assets, protocols, files, and commands from the control network by
IP addresses of devices having ModbusTCP conversations: Are there files moving Abnormal ICS protocols
using these tools and filters. Furthermore, file transfers to or from critical assets such as the HMI, Data tshark: tshark -Y “mbtcp” -T fields -e ip.dst -e ip.src -r <ICS-Network_file.pcap> | sort across the network or command patterns
Historian, or engineering workstations are critical to flag for analysis. | uniq
Wireshark: Wireshark > Statistics > Endpoints All ModbusTCP Function Codes in use on the control network:
2 3
Provides statistics about logical addresses on the network, including asset IP address and MAC address. Displays number tshark: tshark -Y mbtcp -T fields -e _ws.col.Info -r <ICS-Network_file.pcap> | sort | signs for unexpected Unexpected remote
of packets, total bytes, bytes received and transmitted, and attempts to perform DNS name resolution, which can help with uniq | cut -d “:” -f 5,6 | sort | uniq encryption access to HMI
asset identification. Record the expected and potentially anomalous polling rate and direction of traffic between the HMI and
field devices (varies by vendor equipment and protocol). Record and analyze each IP address and associated ports to identify all All DNP3 Function Codes in use and IP addresses using them:
active assets. tshark: tshark -n -Y dnp3 -T fields -e ip.src -e ip.dst -e dnp3.al.func -e _ws.col.Info
-r <ICS-Network_file.pcap> | sort | uniq Newly registered Connection attempts to
Wireshark: Wireshark > Statistics > Conversations devices on the network Internet addresses
Provides statistics about conversations in the traffic between endpoints, displayed as IP addresses. Information such as the start, stop, IP addresses of devices using BACnet and BACnet control commands:
and duration of the conversations is notable. Record the devices that are communicating and note their communication patterns. A tshark: tshark -Y bacnet -T fields -e ip.src -e ip.dst -e bacnet.control -e _ws.col.
single device having conversations with multiple devices could indicate the HMI in the network. Info -r <ICS-Network_file.pcap> | sort | uniq
Wireshark: Wireshark > Statistics > Protocol Hierarchy Discover and analyze possible HTTP downloads, including filename and URI:
Provides statistics about observed protocols on the network. Protocols are displayed in a tree layout with bar graphs indicating the percent tshark: tshark -n -T fields -e http.request.method -e http.host -e http.request.uri -r SANS ICS COMMUNITY FORUM
of the protocol seen as a share of the overall protocols in the capture. Record the list to determine which protocols are expected and further <ICS-Network_file.pcap> | sort | uniq
analyze protocols that are unexpected. Note, however, that legitimate protocols could be abused in attack scenarios, so it is important to record Join the ICS Community Forum. Tips, tricks and Q&A to secure your ICS:
and analyze protocol patterns and source devices sending commands, in particular to field devices. Export data for analysis – HTTP downloads, including filename and URI:
tshark: tshark -r <ICS-Network_file.pcap> --export-objects http,<OutputDir> | sort | https://ics-community.sans.org/signup
Wireshark: Wireshark > Export Objects > <type> > Save uniq
ICSPS_v1.0_09-21 - This poster was Extract files from a packet capture using this feature. File hashes can be obtained then searched against threat intelligence or malware databases. Or,
created by Dean C. Parsons. ©2021 files can be executed in an isolated malware analysis sandbox to determine threat behaviors in order to develop defensive countermeasures. Export data for analysis – SMB file transfers, including filename and file data: SANS INDUSTRIAL CONTROL SYSTEM SECURITY CURRICULUM
Dean C. Parsons. All Rights Reserved. tshark: tshark --export-objects smb,<OutputDir> -r <ICS-Network_file.pcap>
General statistics about logical addresses on the network: ICS410: ICS/SCADA Security Essentials
tshark: tshark -qz ip_hosts,tree -r <ICS-Network_file.pcap> Discover files transferred via SMB with remote hostname, account name, file(s) accessed:
tshark: tshark -n -Y ‘frame.number == 189’ -T fields -e smb2.filename -e smb2.tree -e Global Industrial Cyber Security Professional (GICSP)
Asset names from NetBIOS communications: smb2.acct -e smb2.host -r <ICS-Network_file.pcap>
tshark: tshark -Y nbns -T fields -e nbns.name -r <ICS-Network_file.pcap> ICS456: Essentials for NERC Critical Infrastructure
Protection
GIAC Critical Infrastructure Protection (GCIP)
ICS515: ICS Visibility, Detection, and Response
SANS ICS RESOURCES ics.sans.org ics-community.sans.org/signup @SANSICS Free and open-source tools for ICS available at ControlThings.io GIAC Response and Industrial Defense (GRID)
ICS612: ICS Cybersecurity In-Depth
SANS ICS Security SANS ICS
You might also like
- VPDM Pin LayoutDocument1 pageVPDM Pin LayoutBernardo OlivaNo ratings yet
- Functional Safety With Iec62061 and Iso13849Document1 pageFunctional Safety With Iec62061 and Iso13849최재호0% (1)
- Instant Assessments for Data Tracking, Grade 3: MathFrom EverandInstant Assessments for Data Tracking, Grade 3: MathRating: 5 out of 5 stars5/5 (2)
- FINAL CHEAT SHEET Industrial Network Security Monitoring Incident ResponseDocument2 pagesFINAL CHEAT SHEET Industrial Network Security Monitoring Incident ResponseAni MNo ratings yet
- Wa0007Document1 pageWa0007bhavyaNo ratings yet
- Siemens: PSS®SINCAL Platform Price ListDocument1 pageSiemens: PSS®SINCAL Platform Price ListJohnDoeNo ratings yet
- With Intel Xeon Processors: Cisco Unif Ied Computing SystemDocument2 pagesWith Intel Xeon Processors: Cisco Unif Ied Computing SystemPavan NavNo ratings yet
- Competitor PresentationDocument6 pagesCompetitor PresentationRangarajan SrinivasaNo ratings yet
- ABB UNO DM 1.2 5.0 TL PLUS Quick Installation GuideDocument2 pagesABB UNO DM 1.2 5.0 TL PLUS Quick Installation GuideFlorin FlorinNo ratings yet
- 5G Architecture and SpecificationsDocument1 page5G Architecture and Specificationshrga hrgaNo ratings yet
- Exfo - Reference Poster - Full Network 5g - v1 enDocument2 pagesExfo - Reference Poster - Full Network 5g - v1 enGennady ShenkerNo ratings yet
- System ConfigurationDocument1 pageSystem ConfigurationCristi CrseNo ratings yet
- System ConfigurationDocument1 pageSystem ConfigurationCristi CrseNo ratings yet
- Achievement Chart Computer Systems Servicing NC IiDocument3 pagesAchievement Chart Computer Systems Servicing NC IiSer Crz JyNo ratings yet
- Progress Review Report-CniDocument6 pagesProgress Review Report-Cnirbdubey2020No ratings yet
- PVI-GSM - GPRS Quick Installation Guide - AADocument2 pagesPVI-GSM - GPRS Quick Installation Guide - AAroscribNo ratings yet
- Chin Her-10. SLD Inv 21-25Document1 pageChin Her-10. SLD Inv 21-25uzair rosdiNo ratings yet
- Safety Integrity Level (SIL)Document1 pageSafety Integrity Level (SIL)UKNo ratings yet
- AWS Periodic TableDocument1 pageAWS Periodic Tabledouglas.dvferreiraNo ratings yet
- Message No. 2 - Format Infrastructure Data Collection 30.01.2019Document1 pageMessage No. 2 - Format Infrastructure Data Collection 30.01.2019Bhaskar Victor DasNo ratings yet
- Man BasketDocument1 pageMan BasketsantoshNo ratings yet
- QFD Assignment 2Document1 pageQFD Assignment 2salsid916No ratings yet
- Appendix - H Nascent Applied Methods & Endeavors Organizational Chart Structure & Semantic Network of Operational DutiesDocument26 pagesAppendix - H Nascent Applied Methods & Endeavors Organizational Chart Structure & Semantic Network of Operational DutiesWilliam E. FieldsNo ratings yet
- Network - Topology - RevaDocument1 pageNetwork - Topology - RevaJulio VeraNo ratings yet
- Case Studies and Tech. MeasuresDocument1 pageCase Studies and Tech. MeasuresMuhammad Wahaj ButtNo ratings yet
- GET - DDC Analysis 24-10Document4 pagesGET - DDC Analysis 24-10Ahmed Salah AliNo ratings yet
- Simatic S5: System Manual CPU 100/102/103Document512 pagesSimatic S5: System Manual CPU 100/102/103SanjeewaNo ratings yet
- Deep Learning-Based Semantic Segmentation in Autonomous DrivingDocument7 pagesDeep Learning-Based Semantic Segmentation in Autonomous Drivingprajna acharyaNo ratings yet
- Chin Her-7. SLD Inv 1-7Document1 pageChin Her-7. SLD Inv 1-7uzair rosdiNo ratings yet
- Schematic Diagram: 7-1 Circuit DescriptionDocument8 pagesSchematic Diagram: 7-1 Circuit Descriptionoppa BaruNo ratings yet
- BizTalk Server 2010 Runtime Architecture PosterDocument1 pageBizTalk Server 2010 Runtime Architecture PosterascsaNo ratings yet
- Handhelds - HandheldsDocument298 pagesHandhelds - HandheldsAlexandru StoianNo ratings yet
- EB+ Gen3 HALDEXDocument1 pageEB+ Gen3 HALDEXPiotr ZiąbkowskiNo ratings yet
- 966H and 972H Wheel Loader With Steel Mill Electrical SystemDocument6 pages966H and 972H Wheel Loader With Steel Mill Electrical SystemmohamedNo ratings yet
- 3 - Detection of ARP Spoofing Attacks in Software Defined Networks - 2023 IeeexploreDocument5 pages3 - Detection of ARP Spoofing Attacks in Software Defined Networks - 2023 IeeexploreMahmoud ElzoghbiNo ratings yet
- Electro 323Document2 pagesElectro 323Pușcă MartinNo ratings yet
- Triaxial Test CoggleDocument1 pageTriaxial Test CoggleAndika PerbawaNo ratings yet
- Epc Epcm ChartDocument1 pageEpc Epcm ChartjcerignaleNo ratings yet
- Continuous Assessments Results University College of Jaffna: 2018 Basic Engineering DrawingDocument1 pageContinuous Assessments Results University College of Jaffna: 2018 Basic Engineering DrawingAnonymous OvLcq0Z28hNo ratings yet
- Poster PA 2015 en A1Document1 pagePoster PA 2015 en A1Dalat TigonNo ratings yet
- A380 Family Maintenance ConceptDocument1 pageA380 Family Maintenance Conceptyazan999100% (1)
- 6hk Truck Cat 785BDocument2 pages6hk Truck Cat 785BSergio VelardeNo ratings yet
- Poster EuMW 2009 BackUpDocument2 pagesPoster EuMW 2009 BackUpAbdul Ali KakarNo ratings yet
- GVM ST300R User ManualDocument1 pageGVM ST300R User ManualPaco Jiménez BarbaNo ratings yet
- 2021 RoadmapDocument2 pages2021 RoadmapSathia ShekarNo ratings yet
- Folder EuromaxDocument2 pagesFolder EuromaxHugo de LimaNo ratings yet
- Installation Packages Content MapDocument5 pagesInstallation Packages Content MapkarimNo ratings yet
- DMM 1 e 007Document1 pageDMM 1 e 007mahesh reddy mNo ratings yet
- Internet: F.O - 50 Microns F.O - 50 MicronsDocument3 pagesInternet: F.O - 50 Microns F.O - 50 MicronsJavier CareagaNo ratings yet
- SIP To TCAP GatewayDocument2 pagesSIP To TCAP Gatewayrana_gpNo ratings yet
- Plakat FESTO CPX MPA VTSADocument2 pagesPlakat FESTO CPX MPA VTSAtadNo ratings yet
- AMTED107013EN (Print)Document2 pagesAMTED107013EN (Print)Luis EduardoNo ratings yet
- Pressure Test & Test Pack ManagementDocument43 pagesPressure Test & Test Pack ManagementStanley Alex100% (4)
- Java Technology Concept MapDocument1 pageJava Technology Concept Mapkostas.karis100% (2)
- 103 Mesh Exposed: Perimeter Installation External Retrofit To Brick ConstructionDocument1 page103 Mesh Exposed: Perimeter Installation External Retrofit To Brick Constructiondodgy emailNo ratings yet
- User Guide: CS-64A Installation Diagram Hardware ReviewDocument2 pagesUser Guide: CS-64A Installation Diagram Hardware ReviewAde Rachmad MulyanaNo ratings yet
- Phase 5 Block Grading Exhibit - COMPRESSEDDocument1 pagePhase 5 Block Grading Exhibit - COMPRESSEDLevi PackNo ratings yet
- Instant Assessments for Data Tracking, Grade 4: Language ArtsFrom EverandInstant Assessments for Data Tracking, Grade 4: Language ArtsRating: 5 out of 5 stars5/5 (1)
- Instant Assessments for Data Tracking, Grade 2: MathFrom EverandInstant Assessments for Data Tracking, Grade 2: MathNo ratings yet
- !poster - ICS Vs IT Security - 2022Document2 pages!poster - ICS Vs IT Security - 2022Ani MNo ratings yet
- ICS Security Solutions MapDocument2 pagesICS Security Solutions MapAni MNo ratings yet
- ICS Cyber Incident Response POSTERDocument2 pagesICS Cyber Incident Response POSTERAni MNo ratings yet
- Assessment MethodologyDocument2 pagesAssessment MethodologyAni MNo ratings yet
- AcronymsDocument2 pagesAcronymsAni MNo ratings yet
- !icss - SP800 5307 02 2008Document60 pages!icss - SP800 5307 02 2008Ani MNo ratings yet
- Practical Cybersecurity Architecture A Guide To Creating and Implementing Robust Designs For Cybersecurity Architects (Ed Moyle, Diana Kelley)Document418 pagesPractical Cybersecurity Architecture A Guide To Creating and Implementing Robust Designs For Cybersecurity Architects (Ed Moyle, Diana Kelley)Ani M100% (1)
- SANS - 5 Critical ControlsDocument19 pagesSANS - 5 Critical ControlsAni MNo ratings yet
- Quick Installation and Configuration Guide For Unified Expert AdvisorDocument67 pagesQuick Installation and Configuration Guide For Unified Expert Advisormky212No ratings yet
- Prueba 1Document88 pagesPrueba 1alphac10063No ratings yet
- Meer Zahid Khan: Ummary OF UalificationsDocument9 pagesMeer Zahid Khan: Ummary OF UalificationsAbrar_AshrafNo ratings yet
- Lesson 1 Quiz - CourseraDocument6 pagesLesson 1 Quiz - CourseraRupesh Kumar SahNo ratings yet
- Lzarus Database Programming ArticlesDocument10 pagesLzarus Database Programming ArticlesPradeep Hosadurga H KNo ratings yet
- Exploring Information Seeking Anxiety Among Research Students in PakistanDocument10 pagesExploring Information Seeking Anxiety Among Research Students in Pakistanumair aliNo ratings yet
- Types of Data BaseDocument10 pagesTypes of Data BaseFaisal Awan100% (1)
- MES Components2Document2 pagesMES Components2Labidi ZouhaierNo ratings yet
- Xegis Software User Manual IntroDocument13 pagesXegis Software User Manual IntroNikolay PenevNo ratings yet
- Anudeep SR Java1Document8 pagesAnudeep SR Java1Sainath AkulaNo ratings yet
- Amazon Passleader AWS-Solution-Architect-Associate Exam Question V2018-Mar-28 by Phillip 783q VceDocument45 pagesAmazon Passleader AWS-Solution-Architect-Associate Exam Question V2018-Mar-28 by Phillip 783q VceJayakrishna InjetiNo ratings yet
- At-05197 Hysys Study GuideDocument22 pagesAt-05197 Hysys Study Guidewf4sr4r100% (1)
- 74 - B.SC Syllabus..Document44 pages74 - B.SC Syllabus..Satish KumarNo ratings yet
- Ba Unit 3 and 4Document30 pagesBa Unit 3 and 4Mythili SNo ratings yet
- Rename Relocate Data Files and Resizing Log Files in DR Env PDFDocument15 pagesRename Relocate Data Files and Resizing Log Files in DR Env PDFG.R.THIYAGU ; Oracle DBA50% (4)
- Plugin Risk Management Plan SampleDocument12 pagesPlugin Risk Management Plan SampleMohammad Kanani ZadehNo ratings yet
- Discoverer Metadata Conversion AssistantDocument24 pagesDiscoverer Metadata Conversion AssistantmalliyadavaNo ratings yet
- Configure Instance Parameters and Modify Container Databases (CDB) and Pluggable Databases (PDB)Document2 pagesConfigure Instance Parameters and Modify Container Databases (CDB) and Pluggable Databases (PDB)Ahmed NagyNo ratings yet
- Binder 1Document291 pagesBinder 1vigneshtheguyNo ratings yet
- B Pharma Lab Experimets Bp210Document38 pagesB Pharma Lab Experimets Bp210Durgesh WadbudeNo ratings yet
- Oracle 11 GDocument5 pagesOracle 11 GsnekkalaNo ratings yet
- Microsoft FRX® To Management Reporter 2012 Migration GuideDocument14 pagesMicrosoft FRX® To Management Reporter 2012 Migration Guideobad2011No ratings yet
- Appsense Management Suite Architecture and Installation Guide PDFDocument76 pagesAppsense Management Suite Architecture and Installation Guide PDFsri2727No ratings yet
- Mobile Computing Data Management IssuesDocument31 pagesMobile Computing Data Management IssuesSanjay SrivastavaNo ratings yet
- SQL Injection Cheat SheetDocument7 pagesSQL Injection Cheat SheetThảo NguyễnNo ratings yet
- Name: Rijna Shrestha Roll No.: 36: 1.short Note On DDL and DMLDocument9 pagesName: Rijna Shrestha Roll No.: 36: 1.short Note On DDL and DMLrijna sthNo ratings yet
- Azure AD ConnectDocument5 pagesAzure AD ConnectmicuNo ratings yet
- Note Database Development ProcessDocument3 pagesNote Database Development ProcessRay Marvin GuevaraNo ratings yet
- TejaswiniGollamudi (4 8) 6Document3 pagesTejaswiniGollamudi (4 8) 6Bali TripNo ratings yet