Professional Documents
Culture Documents
CSF Semester III IV
Uploaded by
John DikoOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
CSF Semester III IV
Uploaded by
John DikoCopyright:
Available Formats
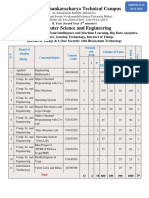
School of Computing Science and Engineering
Department of Computer Science and Engineering
B. Tech CSE (with specialization in Cyber Security and Forensics)
Semester – III
Teaching Scheme
(Hrs./Week) Examination Scheme
Sr. Formative Total
Summative Marks
Core Course Code Course Name
No. Assessment Assessment
L T P C CIA ESE
Course Lab Course Lab
Discrete Mathematics and
1 UC 17YBS304 3 -- -- 3 50 -- 50 -- 100
Logic
Digital Design and Computer
2 PC 17YCF301 3 -- -- 3 50 -- 50 -- 100
Organization
3 PC 17YCF302 Object Oriented Programming 3 -- -- 3 50 -- 50 -- 100
4 PC 17YCF303 Data Structures 3 -- -- 3 50 -- 50 -- 100
5 PC 17YCF304 IT Systems Security 3 -- -- 3 50 -- 50 -- 100
Object Oriented Programming
6 PC 17YCF311 -- -- 2 1 -- 25 -- 25 50
Lab
7 PC 17YCF312 Data Structure Lab -- -- 4 2 -- 25 -- 25 50
8 PC 17YCF313 IT System Security Lab -- -- 2 1 -- 25 -- 25 50
Dynamic Paradigm in Cyber
9 PC 17YCF314 -- -- 2 1 -- 50 -- - 50
Security and Forensics 1
10 UC 17YCF315 Industry Internship -- 1 -- 1 -- 50 -- -- 50
TOTAL 15 01 8 21 250 175 250 75 750
CIA: Continuous Internal Assessment #: Internship for 15 days. CIA Weight age Description
L: Theory Lecture *: Oral Examination CIA 1 10% Home Assignment
CIA 2 20% Mid-Term Exam (MTE)
T: Tutorial UC: University Core
CIA 3 10% Seminar Presentation
P: Practical PC: Programme Core CIA 4 10% Research Based Activity
TH: Theory Exam. PE: Programme Elective TOTAL 50%
Note:
17YCF314 – Seminar and Webinars conducted by IBM Experts (Student must submit a Report on the same technical topic)
17YCF315 – Applicable for Natural growth students only, Maximum Two weeks, Students will submit report for the same
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – III
Course: Discrete Mathematics and Logic Course Code: 17YBS304
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA)
Examination Total
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3 CIA-4 Lab Theory Lab
3 1 0 3 10 20 10 10 -- 50 -- 100
Max. Time, End Semester Exam (Theory) -3 Hrs. End Semester Exam (Lab) - 0Hrs.
Prerequisites:
Basic Mathematics
Objectives:
Students are able to:-
1 To impart fundamentals of discrete mathematical structures useful in studying, analyzing
and solving problems in Computer Science.
2 To sharpen the mathematical skills by practicing problem solving, logical reasoning and
writing precise proofs.
3 To impart skills for applying ideas from discrete mathematics to real world problems.
Unit
Details Hours
No
Module 1:Need of Set, Representation of Sets, Subsets, Venn Diagrams, 3
complements, Cartesian products, Operations on sets, Laws of Set Theory, Power
Sets and Products, cardinality and countability (Countable and Uncountable sets),
1 Partition of sets, Multisets, The Principle of Inclusion - Exclusion.
Module 2: Propositions and Logical operations, Truth tables, Equivalence, 4
Implications, Laws of Logic, Normal forms, Predicates and quantifiers,
Mathematical Induction.
Module 1: Relations and their properties, n-array relations and their applications, 3
representing relations, closure of relations, equivalence of relations, partial
orderings, Hasse Diagram, Lattices, Chains and Anti-Chains, Transitive Closure
2
and Warshall‘s Algorithm.
Module 2: Surjective, Injective and Bijective functions, Inverse Functions and 4
Compositions of Functions, The Pigeonhole Principle.
Module 1:Basic terminology, representation of a graph in computer memory, 3
multi-graphs and weighted graphs, Sub graphs, Isomorphic graphs, Complete,
regular and bipartite graphs, operations on graph.
3
Module 2:Paths and circuits, Euler paths and circuits, Hamiltonian paths and 3
circuits, Planner graphs, shortest path in weighted graphs (Dijkstra’s algorithm),
coloring graphs, Isomorphism of Graphs.
Module 1: Basic terminology and characterization of trees, rooted trees and path 4
4 length in rooted trees, binary search trees, Tree traversal, Fundamental Trees and
cut sets.
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Module 2: Spanning tree and Minimal Spanning tree, Isomorphism of trees, 4
Weighted trees and Prefix Codes, The Max flow- Min Cut Theorem (Transport
network).
Module 1:Algebraic structures with one binary operation - semi groups, monoids 4
and groups, Isomorphism, homomorphism, automorphism, Cyclic groups,
5 Module 2:Normal sub group, codes and group codes, Algebraic structures with 4
two binary operations - rings, integral domains and fields. Ring homomorphism
and Isomorphism.
Outcomes:
At the end of this course students will be able to:-
1 Solve real world problems logically using appropriate set, function, and relation models and
interpret the associated operations and terminologies in context.
2 Analyze and synthesize the real world problems using discrete mathematics.
Text Books
1. C L Liu, “Elements of Discrete Mathematics”, Tata McGraw-Hill, ISBN 10:0-07-066913-9.
2. K.H. Rosen, “Discrete Mathematics and its application”, 7th edition, Tata McGraw Hill, ISBN
978-0-07-338309-5.
3. B. Kolman, Robert C. Busby, Sharon Ross, “Discrete Mathematical Structure”, 6th edition,
Pearson/Prentice Hall, ISBN 9780132078450.
Reference Book
1. Kenneth H. Rosen, “Discrete Mathematics and its Applications”, 6th edition, McGraw-Hill,
2007, ISBN 978-0-07-288008-3.
2. Tremblay J. P. and R. Manohar, Discrete Mathematical Structures with Applications to
Computer Science, Tata McGraw-Hill, 1997.
3. Bernard Kolman, Robert C. Busby and Sharon Ross, Discrete Mathematical Structures, Prentice-
Hall of India /Pearson, ISBN: 0132078457, 9780132078450.
4. N. Biggs, “Discrete Mathematicsǁ”, 3rd Edition, Oxford University Press, ISBN 0-19 850717 – 8.
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – III
Course: Digital Design and Computer Organization Course Code: 17YCF301
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA)
Examination Total
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3 CIA-4 Lab Theory Lab
3 -- -- 3 10 20 10 10 -- 50 -- 100
Max. Time, End Semester Exam (Theory) -3Hrs. End Semester Exam (Lab) - 0Hrs.
Prerequisites:
Fundamentals of Programming Languages., Basics of Electronics Engineering
Objectives:
Students are able to:-
1 To understand the structure, function and characteristics of computer systems & Number
System.
2 To understand the various computer systems and logic gates.
3 To understand combinational and sequential logic circuits.
4 To understand memory concept.
5 To understand I/O devices and instruction sets.
Unit
Details Hours
No
Module 1:Basic Organization of Computers, Classification Micro, Mini, 3
Mainframe and Super Computer. System Bus and Interconnection, Computer
Function, Interrupt and Class of Interrupts.
1
Module 2: Number systems, Decimal Number system, Binary number system, 4
Octal &Hexa decimal number system,1's & 2's complement, Binary Fixed Point
Representation.
Module 1:Von-Neumann M/c: Structure of IAS. Fundamental Concepts: Fetching 3
and storing a word in Memory, Register Transfer, Performing an Arithmetic &
Logic Operation, Execution of Instruction.
2
Module 2: Arithmetic operation on Binary numbers, Overflow & under f low. 4
Logic Gates, AND, OR, NOT GATES and their Truth tables, NOR, NAND &
XOR gates.
Module-1 Half Adder, Full Adder, 4-bit binary adder, multiplexer-2:1, 4:1, 8:1, 3
Demultiplexer-1:2, 1:4, 1:8.
3 Module 2 Latch, Flip Flop-SR FF, D FF, JK FF, Race around condition, T FF, 3
MSJK FF. Shift Registers-SISO, SIPO, PISO,PIPO, Counter-Asynchronous and
asynchronous.
Module 1:Cache memory- Computer Memory system Overview, Memory 4
4 hierarchy, Cache memory principles, Elements of cache design.
Module 2:Internal Memory-Semiconductor main memory, Error correction. 4
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
External Memory-Magnetic Disk, RAID.
Module 1:I/O-External Devices, I/O Modules, Programmed I/O, Interrupt Driven 4
I/O, DMA.
5 Module 2: Instruction Sets-Machine Instruction Characteristics, types of operands, 4
types of operations, Addressing Modes-Instruction Formats. Processor
Organization, Register Organization.
Outcomes:
At the end of this course students will be able to:-
1 Understand the structure, function and characteristics of computer systems & Number
System.
2 Understand the various computer systems and logic gates.
3 Understand combinational and sequential logic circuits.
4 Understand memory concept.
5 Understand I/O devices and instruction sets.
Text Books
1. Stephen Brown, Zvonko Vranesic, ―Fundamentals of Digital Logic with VHDL Designǁ,
McGraw-Hill, ISBN–13:978-1-25-902597-6.
2. R.P. Jain, ―Modern Digital Electronicsǁ, TMH, 2012, ISBN–13: 978-0-07- 066911-6.
3. W. Stallings, ―Computer Organization and Architecture: Designing for performanceǁ, Pearson
Education/ Prentice Hall of India, 2003, ISBN 978-93-325-1870-4, 7th Edition.
4. Zaky S, Hamacher, ―Computer Organizationǁ, 5th Edition, McGraw-Hill Publications, 2001,
ISBN- 978-1-25-900537-5, 5th Edition.
Reference Book
1. John Yarbrough, ―Digital Logic applications and Designǁ, Cengage Learning, ISBN – 13: 978-
81-315-0058-3
2. John P Hays, ―Computer Architecture and Organizationǁ, McGraw-Hill Publication, 1998,
ISBN:978-1-25-902856-4, 3rd Edition.
3. A.Tanenbaum, ―Structured Computer Organizationǁ, Prentice Hall of India, 1991 ISBN: 81 –
203 – 1553 – 7, 4th Edition of India /Pearson, ISBN: 0132078457, 9780132078450.
4. N. Biggs, “Discrete Mathematicsǁ”, 3rd Edition, Oxford University Press, ISBN 0-19 850717 – 8.
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – III
Course: Object Oriented Programming Course Code: 17YCF302
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA)
Examination Total
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3 CIA-4 Lab Theory Lab
3 - - 3 10 20 10 10 -- 50 -- 100
Max. Time, End Semester Exam (Theory) -3Hrs. End Semester Exam (Lab) – 0 Hrs.
Prerequisites:
Fundamentals of Programming Languages
Objectives:
Students are able to:-
1 To study the object-oriented programming principles and techniques.
2 To understand fundamental concepts of OOP such as data abstraction, encapsulation,
inheritance, dynamic binding and polymorphism.
3 To create base of cutting-edge programming.
Unit
Details Hours
No
Module 1:Principles of OOP: Software crisis, Software evolution, OOP paradigm, 3
Basic Concepts of OOP, Benefits & applications of OOP. Functions: Function,
function prototype, accessing function and utility function.
1 Module 2:Moving from C to C++: Declaration of variable, Reference variables, 4
Scope resolution operator, Member dereferencing operator, memory management
operators. Beginning with C++: What is C++, Applications of C++, A Simple C++
Program.
Module 1: Class, Object, class and data abstraction, class scope and accessing 3
class members, Controlling access to members, Objects and Memory
requirements, Defining member functions, A C++ program with class, Making an
outside function inline, Nesting of member function, Private member function,
2 Arrays within class, Member allocation for objects, Arrays of objects, Objects as
function arguments. Static Class members, Static Functions, inline function, Friend
Function.
Module 2: Constructors, Parameterized constructors, Multiple constructors in a 4
class, Constructors with default arguments, Destructors.
Module 1: Three Address, Two Address, One Address and Zero Address 3
Instruction, Addressing Modes: Types of Addressing modes, Numerical Examples,
Program Relocation, Compaction, Data Transfer & Manipulation: Data transfer,
3 Data Manipulation, Arithmetic, Logical & Bit Manipulation Instruction.
Module 2: Program Control: Conditional Branch Instruction, Subroutine, Program 3
Interrupt, Types of Interrupt, RISC & CISC Characteristic. Control Unit
Operation: Hardware Control & Micro Programmed Control.
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Module 1: Pointers- indirection Operators, Memory Management: new and delete, 4
Pointers to Objects, accessing Arrays using pointers, Function pointers, Pointers to
4 Pointers, this Pointer, virtual function, dynamic binding, Virtual destructor.
Module 2: function templates, Function overloading, overloading Function 4
templates, class templates, class template and Nontype parameters.
Module 1: Fundamentals of exception handling techniques, simple exception 4
handling- Divide by Zero, rethrowing an exception, exception specifications.
Module 2: Data hierarchy, Stream and files, Stream Classes, Stream Errors, Disk 4
5
File I/O with Streams, File Pointers, and Error Handling in File I/O, File I/O with
Member Functions, Standard Template Library: Introduction to STL, Containers,
algorithms and iterators.
Outcomes:
At the end of this course students will be able to:-
1 Apply standards and principles to write executable code.
2 Take a problem and develop the structures to represent the solution in the form of objects
and the algorithms.
3 Check the program and, if necessary, find errors in the program and rectify them.
Text Books
1. Balagurusamy, “Object Oriented Programming with C++” Sixth Edition, McGrawHill
Publication, ISBN 13:978-1-25-902993-6.
2. BjarneStroustrup, ―The C++ Programming languageǁ, Third edition, Pearson Education. ISBN
9780201889543.
Reference Book
1. Robert Lafore, ―Object-Oriented Programming in C++, fourth edition, Sams Publishing,
ISBN:0672323087 (ISBN 13: 9780672323089).
2. Herbert Schildt, ―C++ The complete referenceǁ, Eighth Edition, McGraw Hill Professional,
2011, ISBN:978-00-72226805.
3. Cox Brad, Andrew J. Novobilski, ―Object –Oriented Programming: An Evolutionary
Approachǁ, Second Edition, Addison–Wesley, ISBN:13:978-020-1548341.
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – III
Course: Data Structures Course Code: 17YCF303
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA)
Examination Total
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3 CIA-4 Lab Theory Lab
3 - - 3 10 20 10 10 -- 50 -- 100
Max. Time, End Semester Exam (Theory) - 03 Hrs. End Semester Exam (Lab) – 00
Hrs.
Prerequisites:
C, C++, Data Structures and algorithms
Objectives:
The course will enables students to:-
1 To develop a logic for graphical modeling of the real life problems.
2 To suggest appropriate data structure and algorithm for graphical solutions of the problems.
3 To understand advanced data structures to solve complex problems in various domains.
4 To operate on the various structured data
5 To build the logic to use appropriate data structure in logical and computational solutions.
Unit
Details Hours
No
Module 1: Introduction to Data Structures: Concept of data, Data object, Data
structure, Abstract Data Types, realization of ADT in 'C'. Concept of Primitive and
non-primitive, linear and Non-linear, static and dynamic, persistent and ephemeral
data structures. Analysis of algorithm: frequency count and its importance in 4
analysis of an algorithm, Time complexity & Space complexity of an algorithm,
Big 'O', ‘Ω' and 'Θ' notations, Best, Worst and Average case analysis of an
1
algorithm
Module 2: Search Techniques, Sequential search, variant of sequential search-
sentinel search, Binary search, Fibonacci search.
Types of sorting-Internal and external sorting, General sort concepts-sort order, 4
stability, efficiency, number of passes, Sorting methods- Bubble sort, Insertion
sort, Selection sort, Quick sort, Heap sort, Shell sort
Module 1: Introduction of stack, Operations on stacks: Push & Pop, Array
representation of stack, Linked representation of stack, Application of stack,
Conversion of infix to prefix and postfix expressions, Evaluation of the postfix 4
expression using a stack. Iteration and recursion with examples such as binary
2
search, Fibonacci numbers, Use of stack in backtracking
Module 2: Array and linked representation, Operations on queue, Types of queue:
Circular queues, Advantages of Circular queue. Multiqueues, Dequeues and 3
Priority queue, Linked Queue & operations, Applications of Queue.
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Module 1: Basic concept, Representation of linked lists, Comparison of sequential
& linked organizations, Operations on linked list, linked list as ADT, Linked list
4
using dynamic memory management, Types of linked list: Linear, Circular linked
3 list, Doubly linked list and operations,
Module 2: Applications of linked list: Polynomial representation and addition,
Polynomial addition & Multiplication using linked list, Generalized Linked 4
list(GLL) concept, polynomial representation
Module 1: Tree- basic terminology, General tree and its representation,
representation using sequential and linked organization, Binary tree- properties,
converting tree to binary tree, binary tree traversals- inorder, preorder, post 4
order, level wise -depth first and breadth first, Operations on binary tree. Binary
4 Search Tree (BST), BST operations, Threaded binary tree- concepts, threading,
Module 2: Graph- Basic Concepts, Storage representation, Adjacency matrix,
adjacency list, Traversals-depth first and breadth first. Minimum spanning Tree,
3
Prims and Kruskal Algorithms, Dikjtra's Single source shortest path, Topological
ordering.
Module 1: Symbol Table-Representation of Symbol Tables- Static tree table and
Dynamic tree table, Height Balanced Tree- AVL tree.
4
Indexing and Multiway Trees-Indexing, indexing techniques, Types of search tree-
Multiway search tree, B-Tree, B+Tree
5 Module 2: Hash Table- Concepts-hash table, hash function, bucket, collision,
probe, synonym, overflow, open hashing, closed hashing, perfect hash function,
load density, full table, load factor, rehashing, issues in hashing, hash functions 4
properties of good hash function. Heap-Basic concepts, realization of heap and
operations
Outcomes:
On completion of the course, student will be able to–
1 To apply appropriate advanced data structure and efficient algorithms to approach the
problems of various domain.
2 To design the algorithms to solve the programming problems.
3 To use effective and efficient data structures in solving various Computer Engineering
domain problems.
4 To analyze the algorithmic solutions for resource requirements and optimization.
Text Books
1. Horowitz, Sahani, Dinesh Mehata, “Fundamentals of Data Structures in C++”, Galgotia
Publisher, ISBN: 8175152788, 9788175152786.
2. M Folk, B Zoellick, G. Riccardi, “File Structures, Pearson Education”, ISBN:81-7758-37-5.
3. Peter Brass, “Advanced Data Structuresǁ”, Cambridge University Press, ISBN:978-1-107-
43982-5
Reference Book
1. Aho, J. Hopcroft, J. Ulman, ―Data Structures and Algorithmsǁ, Pearson Education, 1998,
ISBN-0-201-43578-0.
2. Michael J Folk, ―File Structures an Object Oriented Approach with C++ǁ, Pearson Education,
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
ISBN: 81-7758-373-5.
3. G A V Pai, ―Data Structures and Algorithmsǁ, The McGraw-Hill Companies, ISBN -
9780070667266.
4. Goodrich, Tamassia, Goldwasser, ―Data Structures and Algorithms in Javaǁ, Wiley Publication,
ISBN: 9788126551903.
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – III
Course: IT Systems Security Course Code: 17YCF304
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA)
Examination Total
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3 CIA-4 Lab Theory Lab
3 - - 3 10 20 10 10 -- 50 -- 100
Max. Time, End Semester Exam (Theory) - 03 Hrs. End Semester Exam (Lab) – 00
Hrs.
Prerequisites:
DDCO
Objectives:
The course will enables students to:-
1 Understand data storage technique
2 Understand the authentication problems
Unit
Details Hours
No
Module 1: Tree- Introduction, 4
1
Module 2: Network security 4
Module 1: Hardware/Downloadable devices/Data storage, 4
2
Module 2: Physical security. 3
Module 1:Software updates to reduces vulnerabilities, 4
3
Module 2: Firewall. 4
Module 1: Account Management - One Time passwords . 4
4
Module 2: Account Management - Authentication. 3
Module 1: System Threats - Antivirus software, Worms, Trojan horse, Root kits, 4
5 Module 2: Port Scanning, Denial of service attack, Distributed Denial of Service
4
attack.
Outcomes:
On completion of the course, student will be able to–
1 Implementation of passwords
2 Know system threats
Text Books
IT Systems security (IBM ICE Publication)
Reference Book
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – III
Course: Object Oriented Programming Lab Course Code:17YCF311
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA) Total
Examination
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3
CIA- Lab Theory Lab
4
0 0 2 1 -- -- -- -- 25 0 25 50
Max. Time, End Semester Exam (Theory) -00 Hrs. End Semester Exam (Lab) – 03
Hrs.
Prerequisites:
C Programing
Objectives:
Students are able to:-
1 Have successful technical and professional careers in their chosen fields such as circuit
theory, Field theory, control theory and computational platforms.
2 Engross in life long process of learning to keep themselves abreast of new developments in
the field of Electronics and their applications in power engineering.
Guidelines for Assessment
Continuous assessment of laboratory work is done based on overall performance and lab
assignments performance of student. Each lab assignment assessment will assign grade/marks
based on parameters with appropriate weightage. Suggested parameters for overall assessment as
well as each lab assignment assessment include- timely completion, performance, innovation,
efficient codes, punctuality and neatness.
Guidelines for Laboratory Conduction
The instructor is expected to frame the assignments by understanding the prerequisites,
technological aspects, utility and recent trends related to the topic. The assignment framing policy
need to address the average students and inclusive of an element to attract and promote the
intelligent students. The instructor may set multiple sets of assignments and distribute among
batches of students. It is appreciated if the assignments are based on real world
problems/applications. Encourage students for appropriate use of Hungarian notation, Indentation
and comments. Use of open source software is encouraged.
In addition to these, instructor may assign one real life application in the form of a mini-project
based on the concepts learned. Instructor may also set one assignment or mini-project that is
suitable to respective branch beyond the scope of syllabus.
Set of suggested assignment list is provided in three groups. Each student must perform at least 13
assignments as at 05 compulsory from group A, 07 from group B and 01 from group C
Operating System recommended : 64-bit Open source Linux or its derivative
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Programming tools recommended: Open Source C Programming tool like GCC
Suggested List of Laboratory Assignments
Group A (Compulsory Assignments)
1. Create class Student having Roll No. and Name member variable and get_data () and put_data()
member functions. Take values for member variables through member functions and print those
values by calling member functions through object.
2. Create any one class and demonstrate the use of static member variable and static member
functions.
3. Write a program to display name and age of five managers using array of objects.
4. Write a program to demonstrate the use of friend function within class.
5. Write a program containing Default Constructor, Parameterized Constructor, and Destructor.
Group B (Any 7)
1. Write a program to sort the numbers in an array using separate functions for read, display, sort
and swap.
2. Write a program to perform addition, subtraction, multiplication and division operations on
complex numbers.
3. Write a program to implement database of persons using inheritance which have different
profession e,g. engineer, doctor, student, laborer etc.
4. Write a program to perform addition, subtraction, multiplication and division operations on
complex numbers using operator overloading.
5. Write a program using Constructors and destructors to implement Stack. Design the class for
stack and the operations to be performed on stack.
6. Write a program in C++ to handle the “Divide by zero” exception.
7. Write a program in C++ using the open (), eof() and getline() member functions to open and
read file content line by line.
8. Write a program in C++having class Number which has inline function mult() and cube() for
calculating the multiplication of 2 double numbers given and cube of the integer number given.
9. Write a program in C++ for bubble sort using function template.
10. Write a program in Java with class Rectangle with the data field’s width, length, area and
colour. The length, width and area are of double type and colour is of string type. The methods
are get_length(), get_width(), get_colour() and find_area(). Create two objects of Rectangle and
compare their area and colour. If the area and colour both are the same for the objects then
display “Matching Rectangles”, otherwise display “Non-matching Rectangle”.
Group C (Any 1)
1. Write a program to store roll numbers of student in array who attended training program in
random order. Write function for- a) Searching whether particular student attended training
program or not using linear search and sentinel search. b) Searching whether particular student
attended training program or not using binary search and Fibonacci search.
2. Write program to implement a priority queue in C++ using an inorder List to store the items in
the queue. Create a class that includes the data items (which should be template) and the priority
(which should be int) Theinorder list should contain these objects, with operator <= overloaded
so that the items with highest priority appear at the beginning of the list (which will make it
relatively easy to retrieve the highest item.)
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – III
Course: Data Structure Lab Course Code: 17YCF312
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA) Total
Examination
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3 CIA-4 Lab Theory Lab
- - 4 1 -- -- -- -- 25 0 25 50
Max. Time, End Semester Exam (Theory) -00 Hrs. End Semester Exam (Lab) – 03 Hrs.
Prerequisites:
Basic Programming Language
Objectives:
Students are able to:-
1 To perform different c operations.
2 To understand searching and sorting.
Guidelines for Assessment
Continuous assessment of laboratory work is done based on overall performance and lab
assignments performance of student. Each lab assignment assessment will assign grade/marks
based on parameters with appropriate weightage. Suggested parameters for overall assessment as
well as each lab assignment assessment include- timely completion, performance, innovation,
efficient codes, punctuality and neatness.
Guidelines for Laboratory Conduction
The instructor is expected to frame the assignments by understanding the prerequisites,
technological aspects, utility and recent trends related to the topic. The assignment framing policy
need to address the average students and inclusive of an element to attract and promote the
intelligent students. The instructor may set multiple sets of assignments and distribute among
batches of students. It is appreciated if the assignments are based on real world
problems/applications. Encourage students for appropriate use of Hungarian notation, Indentation
and comments. Use of open source software is encouraged.
In addition to these, instructor may assign one real life application in the form of a mini-project
based on the concepts learned. Instructor may also set one assignment or mini-project that is
suitable to respective branch beyond the scope of syllabus.
Set of suggested assignment list is provided in three groups. Each student must perform at least 13
assignments as at 05 compulsory from group A, 07 from group B and 01 from group C
Operating System recommended : 64-bit Open source Linux or its derivative
Programming tools recommended: Open Source C Programming tool like GCC
Suggested List of Laboratory Assignments
Group A (Compulsory Assignments)
1. Write a program to perform Set operations - Union, Intersection, Difference, Symmetric
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Difference etc.
2. Write a program to perform various string operations such as Copy, Length, Reversing,
Palindrome, and Concatenation and to find occurrence substring etc with and without using
library functions.
3. Write a program to perform following operations on any database: Add, Delete, Modify, Display,
Search & Sort etc.
4. Implement Sorting Methods using functions- Bubble Sort, Selection Sort and Insertion Sort.
5. Implement Searching Methods-Sequential Search and Binary Search.
Group B (Any 7)
1. Implement Sorting Methods using recursion- Quick Sort and Merge Sort.
2. Represent polynomial using structures and write a menu driven program to perform Addition,
Multiplication and Evaluation.
3. Write a menu driven program to perform following operations on SLL/CDLL: Create, Insert –
Start, end, between, Search & delete, Reverse, Display etc.
4. Create two Singly Linked lists, sort one after creation and one while creation using Pointer
manipulation. Merge these two lists into one list without creating a new node or swapping of the
data.
5. Represent a polynomial using Circular Linked List and write a menu driven program to perform
Addition, Multiplication and Evaluation.
6. Implement Stack as an ADT using Array. Use this ADT to perform expression conversion and
evaluation (infix to postfix, infix to prefix, prefix to infix, prefix to postfix, postfix to infix and
postfix to prefix).
7. Represent Circular Queue using Linked List and write a program to perform operations like
Insert, Delete, Finding front and rear element.
8. Write a program for simulating job queue. Write functions to add job and delete job from queue.
9. Pizza parlor accepting maximum M orders. Orders are served in first come first served basis.
Order once placed cannot be cancelled. Write C++ program to simulate the system using
circular queue using array.
10. Write a program to perform various operation on Binary Tree
11. Write a program to perform various operation on Binary Search Tree
12. Write a program to perform various operation on Heap using linear probing
13. Write a program to perform various operation on Sequential file
Group C (Any 1)
1. Write a program to store roll numbers of student in array who attended training program in
random order. Write function for- a) Searching whether particular student attended training
program or not using linear search and sentinel search. b) Searching whether particular student
attended training program or not using binary search.
2. Write a program to perform various operation on index file
3. Write a C Program to implement hashing.
4. C Program to Implement Hash Tables chaining with Singly Linked Lists.
5. C Program for the Implementation of a Symbol Table with functions to create, insert, modify,
search and display
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – III
Course: IT System Security Lab Course Code: 17YCF313
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA) Total
Examination
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3
CIA- Lab Theory Lab
4
- - 2 1 -- -- -- -- 25 -- 25 50
Max. Time, End Semester Exam (Theory) -00 Hrs. End Semester Exam (Lab) – 03
Hrs.
Prerequisites:
Computer Organization
Objectives:
Students are able to:-
1 Understand data storage technique
2 Understand the authentication problems
Guidelines for Assessment
Continuous assessment of laboratory work is done based on overall performance and lab
assignments performance of student. Each lab assignment assessment will assign grade/marks
based on parameters with appropriate weightage. Suggested parameters for overall assessment as
well as each lab assignment assessment include- timely completion, performance, innovation,
efficient codes, punctuality and neatness.
Guidelines for Laboratory Conduction
The instructor is expected to frame the assignments by understanding the prerequisites,
technological aspects, utility and recent trends related to the topic. The assignment framing policy
need to address the average students and inclusive of an element to attract and promote the
intelligent students. The instructor may set multiple sets of assignments and distribute among
batches of students. It is appreciated if the assignments are based on real world
problems/applications. Encourage students for appropriate use of Hungarian notation, Indentation
and comments. Use of open source software is encouraged.
In addition to these, instructor may assign one real life application in the form of a mini-project
based on the concepts learned. Instructor may also set one assignment or mini-project that is
suitable to respective branch beyond the scope of syllabus.
Operating System recommended : 64-bit Open source Linux or its derivative
Programming tools recommended: Open Source C Programming tool like GCC
Suggested List of Laboratory Assignments
Assignment list will be given by IBM ICE trainer
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – III
Course: Dynamic Paradigm Cyber Security Course Code: 17YCF314
and Digital Forensics1
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA) Total
Examination
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3
CIA- Lab Theory Lab
4
- - 2 1 -- -- -- -- 50 -- -- 50
Max. Time, End Semester Exam (Theory) -00 Hrs. End Semester Exam (Lab) – 00 Hrs.
Prerequisites:
Computer Organization
Objectives:
The course will enables students to:-
1 Learn how to analyze multidimensional data properly.
2 Understand the role of formal statistical theory and informal data warehouse methods.
Guidelines for Assessment
Continuous assessment of laboratory work is done based on overall performance and lab
assignments performance of student. Each lab assignment assessment will assign grade/marks
based on parameters with appropriate weightage. Suggested parameters for overall assessment as
well as each lab assignment assessment include- timely completion, performance, innovation,
efficient codes, punctuality and neatness.
Guidelines for Laboratory Conduction
The instructor is expected to frame the assignments by understanding the prerequisites,
technological aspects, utility and recent trends related to the topic. The assignment framing policy
need to address the average students and inclusive of an element to attract and promote the
intelligent students. The instructor may set multiple sets of assignments and distribute among
batches of students. It is appreciated if the assignments are based on real world
problems/applications. Encourage students for appropriate use of Hungarian notation, Indentation
and comments. Use of open source software is encouraged.
In addition to these, instructor may assign one real life application in the form of a mini-project
based on the concepts learned. Instructor may also set one assignment or mini-project that is
suitable to respective branch beyond the scope of syllabus.
Operating System recommended : 64-bit Open source Linux or its derivative
Programming tools recommended: Open Source C Programming tool like GCC
Suggested List of Laboratory Assignments
Seminars and Webinars conducted by IBM ICE trainer
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – III
Course: Industry Internship Course Code: 17YCF315
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA)
Examination Total
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3 CIA-4 Lab Theory Lab
-- 1 -- 1 -- -- -- -- 50 -- -- 50
Max. Time, End Semester Exam (Theory) -00 Hrs. End Semester Exam (Lab) – 00 Hrs.
Objectives:
Students are able to:-
1 To expose students to the 'real' working environment and get acquainted with the
organization structure, business operations and administrative functions.
2 To set the stage for future recruitment by potential employers.
Unit
Details Hours
No
Course (catalog) description: As a part of the B. Tech Curriculum, Industry
Internship is a Practical course, in which the students of CSE are trained for
technical skills.
Grading:
The Course is graded based on:
Presentation : 50%
Student’s reports : 50%
Employers Expectations:
Source of highly motivated pre professionals.
1 Students bring new perspectives to old problems.
Visibility of your organization is increased on campus.
Quality candidates for temporary or seasonal positions and projects.
Freedom for professional staff to pursue more creative projects.
Flexible, cost effective work force not requiring a long term employer
commitment.
Proven, cost effective way to recruit and evaluate potential employees.
Your image in the community is enhanced as you contribute your expertise to the
educational enterprise
Outcomes:
On completion of the course, student will be able to–
1 An ability to work in actual working environment.
2 An ability to utilize technical resources.
3 An ability to write technical documents and give oral presentations related to the work
completed.
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
STUDENT EVALUATION OF INDUSTRY INTERNSHIP
Please respond to the following questions regarding your internship experience.
The purpose of this form is to provide opportunity for an honest appraisal of the internship site
and supervisor.
Organization: ___________________________________________
Semester/Year:_____________
Location: ___________________________________
Supervisor: _________________________________
1. Please rate the following aspects of your internship placement on the basis of this scale:
(0) No Observation, (1) Poor, (2) Fair, (3) Good, (4) Excellent
• Work experience relates to my career goals
• Adequacy of employer supervision
• Helpfulness of supervisor
• Acceptance by fellow workers
• Opportunity to use my training
• Opportunity to develop my human relations skills
• Provided levels of responsibility consistent with my ability and growth
• Opportunity to develop my communication skills
• Opportunity to develop my creativity
• Cooperativeness of fellow workers
• Opportunity to problem solve
• Opportunity to develop critical thinking skills
• Provided orientation to the organization
• Attempt to offer feedback on my progress and abilities
• Effort to make it a learning experience for me
Feel free to explain any of your responses to the above criteria here (use other side if
necessary):
2. Would you work for this supervisor again? ___ Yes ___ No ___ Uncertain
3. Would you work for this organization again? ___ Yes ___ No
Uncertain
4. Would you recommend this organization to other students? ___ Yes ___ No ___ Uncertain
Why or why not?
5. Your Name: _________________________________________ Date: ______________
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
B. Tech CSE (with specialization in Cyber Security and Forensics)
Semester – IV
Teaching Scheme
(Hrs./Week) Examination Scheme
Sr. Formative Total
Summative Marks
Core Course Code Course Name
No. Assessment Assessment
L T P C CIA ESE
Course Lab Course Lab
1 UC 17YBS401 Modern Mathematics 3 1 -- 4 50 -- 50 -- 100
Object Oriented Programming
2 PC 17YCF401 3 -- -- 3 50 -- 50 -- 100
in Java
3 PC 17YCF402 Database Management System 3 -- -- 3 50 -- 50 -- 100
4 PC 17YCF403 IT Application Security 3 -- -- 3 50 -- 50 -- 100
5 UC 17YHS401 Professional Ethics 3 -- -- 3 50 -- 50 -- 100
Object Oriented Programming
6 PC 17YCF411 -- -- 2 1 -- 25 -- 25 50
in Java Lab
Database Management System
7 PC 17YCF412 -- -- 2 1 -- 25 -- 25 50
Lab
8 PC 17YCF413 IT Application Security Lab -- -- 2 1 -- 25 -- -- 25
Dynamic Paradigm in Cyber
9 PC 17YCF414 -- -- 2 1 -- 25 -- -- 25
Security and Forensics 2
English Communication and
10 UC 17YFE411 2 -- 2 3 -- 50 -- 50* 100
Soft Skill 1
17YFF401/ Foreign Language (French I /
11 UC 17YFG402
2 -- -- 2 50 -- 50 -- 100
German I)
TOTAL 19 01 10 25 300 150 300 100 850
CIA: Continuous Internal Assessment #: Internship for 15 days.
CIA Weight age Description
L: Theory Lecture *: Oral Examination
CIA 1 10% Home Assignment
T: Tutorial UC: University Core
CIA 2 20% Mid-Term Exam (MTE)
P: Practical PC: Programme Core
CIA 3 10% Seminar Presentation
TH: Theory Exam. PE: Programme Elective
CIA 4 10% Research Based Activity
TOTAL 50%
Note:
17YCF414 – Seminar and Webinars conducted by IBM Experts (Student must submit a Report on the same technical topic)
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – IV
Course: Modern Mathematics Course Code: 17YBS401
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA)
Examination Total
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3 CIA-4 Lab Theory Lab
3 1 0 3 10 20 10 10 -- 50 -- 100
Max. Time, End Semester Exam (Theory) - 03 Hrs. End Semester Exam (Lab) – 00 Hrs.
Prerequisites:
Basic Mathematics
Objectives:
The course will enables students to:-
1 To solve order linear differential equations.
2 To find the roots of polynomial equations by using numerical methods and to learn the
concepts of interpolation.
3 To understand the basic concepts of probability distributions, correlation, regression and
fitting of curves.
4 To understand the basic concepts of linear Programing problems.
5 To find the optimal solution of LPP by using simplex and dual simplex method
Unit
Details Hours
No
Module 1: Linear Differential Equations with constant coefficients, Homogeneous
4
1 Linear differential equations,
Module 2: Applications of LDE with constant coefficients to Electrical systems. 4
Module 1: Zeroes of transcendental and polynomial equation using Bisection
method, Secant method, Regulafalsi method and Newton Raphson method, Rate of 4
convergence of above methods.
2
Module 2:Interpolation: Finite differences, difference tables, Newton’s forward
and backward interpolation, Lagrange’s and Newton’s divided difference formula 3
for unequal intervals.
Module 1 Probability: Random variable, Binomial, Poisson, and Normal
4
distributions.
3
Module 2: Fitting of curves: Coefficient of correlation and lines of regression of
4
bivariate data, Fitting of Curves by method of Least squares.
Module 1: Formulation of Linear Optimization Problems, constraints, Graphical
4
method to solve LPP,
4
Module 2: Standard and Canonical forms, basic solutions and feasible solutions,
3
optimal solutions by simplex method.
Module 1: Artificial Variables, Duality concept, formulation of dual problems,
5 4
duality principle,
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Module 2: Relation between Primal and Dual L.P.P., Dual simplex method. 4
Outcomes:
On completion of the course, student will be able to–
1 Solve linear differential equation using appropriate techniques.
2 Apply statistical methods like correlation, regression analysis and probability theory for
analysis and prediction of a given data as applied to machine intelligence.
3 Solve Linear Programming Problems.
Text Books
1. B. S. Grewal, Higher Engineering Mathematics, 43rd edition, Khanna Publishers.
2. A text book of Applied Mathematics: Vol. I, II and III by J. N. Wartikar& P. N. Wartikar ,
VidyarthiGrihaPrakashan, Pune.
3. Operations Research by T. A. Taha.
Reference Book
1. Ervin Kreyszig, Advanced Engineering Mathematics, 10th edition, John Wiley and Sons.
2. Peter V. O'Neil, Advanced Engineering Mathematics, 7th edition, Cengage Learning.
3. Operations Research by S. D. Sharma.
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – IV
Course: Object Oriented Programming in Java Course Code: 17YCF401
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA)
Examination Total
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3 CIA-4 Lab Theory Lab
3 - - 3 10 20 10 10 -- 50 -- 100
Max. Time, End Semester Exam (Theory) -3Hrs. End Semester Exam (Lab) – 0 Hrs.
Prerequisites:
Fundamentals of Programming Languages
Objectives:
Students are able to:-
1 Object oriented programming is the most proven technique for developing reliable programs. It
helps in increased productivity, reusability of code, decrease in the development time, and reduces
cost of production to an extent.
2 The cost of maintaining such systems have also considerably decreased. There are many languages
which used the object oriented concepts and techniques. Some of them are C++, Java, Smalltalk,
Objective-C, etc. Java is a purely object oriented language.
3 Systems/applications created using java programming language reduces the need for developing and
maintain complex and space consuming applications
Unit
Details Hours
No
Module 1: History, Overview of Java, Object Oriented Programming, A simple 3
Programme, Two control statements - if statement, for loop, using Blocks of codes,
Lexical issues - White space, identifiers, Literals, comments, separators, Java Key words.
Data types: Integers, Floating point, characters, Boolean, A closer look at Literals,
Variables, Type conversion and casting, Automatic type promotion in Expressions Arrays.
1
Module 2:Operators: Arithmetic operators, The Bit wise operators, Relational 4
Operators, Boolean Logical operators, Assignment Operator, Operator Precedence.
Control Statements: Selection Statements - if, Switch: Iteration Statements - While, Do-
while, for Nested loops, Jump statements.
Module 1:Class Fundamentals, Declaring objects, Assigning object reference variables, 4
Methods, constructors, “this” keyword, finalize ( ) method A stack class, Over loading
methods, using objects as parameters, Argument passing, Returning objects, Recursion,
2 Access control, Introducing final, understanding static
Module 2:Introducing Nested and Inner classes, Using command line arguments. 4
Inheritance: Inheritance basics, Using super, method overriding, Dynamic method
Dispatch, using abstract classes, using final with Inheritance.
Module 1:Definition, Access protection importing packages, Interfaces: Definition 4
3 implementing interfaces.
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Exception Handling: Fundamental, Exception types
Module 2:Using try and catch, Multiple catch clauses, Nested try Statements, throw, 4
throws, finally, Java’s Built - in exception, using Exceptions.
Module 1:The Java thread model, The main thread, Creating a thread, Creating multiple 4
thread, Creating a thread, Creating multiple threads, Using isalive() and Join(),Thread -
Priorities, Synchronization, Inter thread communication, suspending, resuming and
4 stopping threads, using multi-threading
Module 2:I/O basics, Reading control input, writing control output, Reading and Writing 4
files, Applet Fundamentals, the AWT package, AWT Event handling concepts The
transient and volatile modifiers, using instance of using assert.
Module 1: Database connectivity: JDBC architecture, JDBC Drivers, the JDBC API: 4
loading a driver, connecting to a database, Creating and executing JDBC statements,
5 Handling SQL exceptions
Module 2:Accessing result sets: Types of result sets, Methods of result set interface. An 3
example JDBC application to query a database.
Outcomes:
At the end of this course students will be able to:-
1 Apply standards and principles to write executable code.
2 Take a problem and develop the structures to represent the solution in the form of objects and the
algorithms.
3 Check the program and, if necessary, find errors in the program and rectify them.
4 Students will learn how to write Programs using Java
Text Books
1. The complete reference Java –2: V Edition By Herbert Schildt Pub. TMH
Reference Book
1. SAMS teach yourself Java – 2: 3rd Edition by Rogers Cedenhead and Leura Lemay Pub.
Pearson Education.
Web Reference:
1. http://www.geeksforgeeks.org/java/
2. https://docs.oracle.com/javase/tutorial/java/concepts/
3. https://www.tutorialspoint.com/java/
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – IV
Course: Database Management System Course Code: 17YCF402
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA)
Examination Total
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3 CIA-4 Lab Theory Lab
3 - - 3 10 20 10 10 -- 50 -- 100
Max. Time, End Semester Exam (Theory) - 03 Hrs. End Semester Exam (Lab) – 00 Hrs.
Prerequisites:
Data Structures
Objectives:
The course will enables students to:-
1 To understand the fundamental concepts of database management
2 To learn databases and applications software primarily in the relational model
3 To use querying languages, primarily SQL, and other database supporting software
4 To understand the basic issues of transaction processing and concurrency control
5 To implement security and integrity policies relating to databases
Unit
Details Hours
No
Module 1: Database Concepts, Database System Architecture, Data Modelling:
Data Models, Basic Concepts, entity, attributes, relationships, constraints, keys, 4
users and architecture of DBA
1
Module 2: Components of E-R Model, conventions, converting E-R diagram into
tables, EER Model components, converting EER diagram into tables, legacy 4
system model
Module 1: Basic concepts, Attributes and Domains, Codd's Rules, Relational
Integrity: Domain, Entity, Referential Integrities, Enterprise Constraints, Views, 4
Schema Diagram, Database Design : Functional Dependency, Directives
2 Module 2: Purpose of Normalization, Data Redundancy and Update Anomalies,
Normalization: 1NF, 2NF, 3NF, BCNF. Decomposition: lossless join
3
decomposition and dependency preservation, Multi valued Normalization (4NF),
Join Dependencies and the Fifth Normal Form
Module 1: Introduction to SQL: Characteristics and advantages, SQL Data Types
and Literals, DDL, DML, DCL, TCL,SQL Operators, Tables: Creating,
4
Modifying, Deleting, Views: Creating, Dropping, Updating using Views, Indexes,
Nulls
3
Module 2: SELECT Query and clauses, Set Operations, Predicates and Joins, Set
membership, Tuple Variables, Set comparison, Ordering of Tuples, Aggregate
4
Functions, Nested Queries, Database Modification using SQL Insert, Update and
Delete Queries, MongoDB
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Module 1: Stored Procedures, Cursors, Triggers, assertions, roles and privileges
4
Programmatic SQL: Embedded SQL, Dynamic SQL
4 Module 2: Basic concept of a Transaction, Transaction Management, Properties
of Transactions, Concept of Schedule, Serial Schedule, Serializability: Conflict 3
and View, Cascaded Aborts, Recoverable and Non- recoverable Schedules
Module 1: Need, Locking Methods, Deadlocks, Time-stamping Methods,
Optimistic Techniques, Recovery methods : Shadow-Paging and Log-Based 4
Recovery, Checkpoints
Module 2: Centralized and Client-Server Architectures, 2 Tier and 3 Tier
5
Architecture,Introduction to Parallel Databases, Key elements of Parallel Database
Processing, Architecture of Parallel Databases,Introduction to Distributed 4
Databases, Architecture of Distributed Databases, Distributed Database Design,
Internet Databases, Database Connectivity using Mongo databases
Outcomes:
On completion of the course, student will be able to–
1 Learn fundamental concepts of database management
2 Analyze database models & entity relationship models
3 Apply the basics of database languages and construct queries using SQL, PLSQL
4 Design cost effective transaction queries for databases.
Text Books
1. Silberschatz A., Korth H., Sudarshan S., "Database System Concepts", 6thEdition, McGraw Hill
Publishers, ISBN 0-07-120413-X
Reference Book
1. S.K.Singh, Database Systems : Concepts, Design and Application , 2nd Edition, Pearson, 2013,
2. Connally T., Begg C., "Database Systems", 3rd Edition, Pearson Education, 2002, ISBN 81-
7808-X
3. P. S. Deshpande, “SQL & PL / SQL for Oracle 11g Black Book”, DreamTech Publication
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – IV
Course: IT Application Security Course Code: 17YCF403
Teaching
Scheme End Semester
Continuous Internal Assessment (CIA)
(Hrs. Examination Total
/Week)
L T P C CIA-1 CIA-2 CIA-3 CIA-4 Lab Theory Lab
3 -- -- 3 10 20 10 10 -- 50 -- 100
Max. Time, End Semester Exam (Theory) - 03 Hrs. End Semester Exam (Lab) – 00 Hrs.
Prerequisites:
IT System Security
Objectives:
The course will enables students to:-
1 This course is a study within the Information Assurance discipline of Application Security
as it relates to security assessments and secures deployment.
Unit
Details Hours
No
Module 1: Application Security, Authentication & Authorization
Input Validation - Buffer overflow; cross-site scripting; SQL injection;
4
canonicalization, Sensitive information Access sensitive data in storage; network
1 eavesdropping; data tampering.
Module 2: Network eavesdropping; Brute force attack; dictionary attacks; cookie
replay; credential theft. Elevation of privilege; disclosure of confidential data; data 4
tampering; luring attacks; Phishing
Module 1: Configuration management & Session management
Unauthorized access to administration interfaces; unauthorized access to
configuration stores; retrieval of clear text configuration data; lack of individual 4
2
accountability; over-privileged process and service accounts.
Module 2: Hijacking; session replay; man in the middle 3
Module 1: Cryptography, Parameter manipulation & Exception Management
Cryptography Poor key generation or key management; weak or custom
4
encryption. Parameter manipulation Query string manipulation; form field
3
manipulation; cookie manipulation
Module 2: HTTP header manipulation Exception Management Information
4
disclosure; denial of service
Module 1: Auditing and logging, Countermeasures
4
Auditing and logging User denies performing an operation
4
Module 2: attacker exploits an application without trace; attacker covers his or her
3
tracks, Countermeasures
5 Module 1: Introduction to code analysis 4
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Module 2: Introduction to code analysis using IBM Rational AppScan 4
Outcomes:
On completion of the course, student will be able to–
1 Understand the role of IT Physical Security in transactions
2 Describe social networking and evaluate associated risks
3 Evaluate web application security vulnerabilities
4 Identify IT Physical Security controls and risk mitigation techniques
5 Develop a security strategy and solution for securing web based applications
6 Assess web application security compliance requirements and objectives.
Text Books
IT Application security (IBM ICE Publication)
Reference Book
----
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – IV
Course: Professional Ethics Course Code: 17YHS401
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA)
Examination Total
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3 CIA-4 Lab Theory Lab
3 - - 3 10 20 10 10 -- 50 -- 100
Max. Time, End Semester Exam (Theory) - 03 Hrs. End Semester Exam (Lab) – 00 Hrs.
Prerequisites:
Soft Skills and Language.
Objectives:
The course will enables students to:-
1 To enable the students to imbibe and internalize the Values and Ethical Behavior in the
personal and Professional lives.
Unit
Details Hours
No
Module 1: Basic Concepts, Governing Ethics, Personal & Professional Ethics,
Ethical Dilemmas, Life Skills, Emotional Intelligence, Thoughts of Ethics, Value 4
Education.
1
Module 2: Dimensions of Ethics, Profession and professionalism, Professional
Associations, Professional Risks, Professional Accountabilities, Professional 4
Success, Ethics andProfession.
Module 1: Basic Ethical Principles, Moral Developments, Deontology,
Utilitarianism, Virtue Theory, Rights Theory, Casuist Theory, Moral Absolution. 4
2
Module 2: Moral Rationalism, Moral Pluralism, Ethical Egoism, Feminist
3
Consequentialism, Moral Issues, Moral Dilemmas, MoralAutonomy.
Module 1: Professions and Norms of Professional Conduct, Norms of
Professional Conduct vs. Profession; Responsibilities, Obligations and Moral
Values in Professional Ethics, Professional codes of ethics, the limits of 4
3 predictability and responsibilities of the engineering profession.
Module 2: Central Responsibilities of Engineers - The Centrality of
Responsibilities of Professional Ethics; lessons from 1979 American Airlines DC- 4
10 Crash and Kansas City Hyatt Regency Walk awayCollapse.
Module 1: Work Place Rights & Responsibilities, Ethics in changing domains of
Research, Engineers and Managers; Organizational Complaint Procedure,
4
difference of Professional Judgment within the Nuclear Regulatory Commission
4
(NRC), the Hanford Nuclear Reservation.
Module 2: Ethics in changing domains of research - The US government wide
3
definition of research misconduct, research misconduct distinguished from
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
mistakes and errors, recent history of attention to research misconduct, the
emerging emphasis on understanding and fostering responsible conduct,
responsible authorship, reviewing & editing.
Module 1:Introduction – Current Scenario, Technology Globalization of MNCs,
International Trade, World Summits, Issues, Business Ethics and Corporate 4
Governance.
5
Module 2:Sustainable Development Ecosystem, Energy Concerns, Ozone
Deflection, Pollution, Ethics in Manufacturing and Marketing, Media Ethics; War 4
Ethics; Bio Ethics, Intellectual Property Rights.
Outcomes:
On completion of the course, student will be able to–
1 The students will understand the importance of Values and Ethics in their personal lives
and professional careers. The students will learn the rights and responsibilities as an
employee, team member and a global citizen.
Text Books
1. Professional Ethics: R. Subramanian, Oxford University Press, 2015.
2. Ethics in Engineering Practice & Research, Caroline Whit beck, 2e, Cambridge University Press
2015.
Reference Book
1. Engineering Ethics, Concepts Cases: Charles E Harris Jr., Michael S Pritchard, Michael J
Rabins, 4e, Cengagelearning, 2015.
2. Business Ethics concepts & Cases: Manuel G Velasquez, 6e, PHI, 2008.
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester –IV
Course: Object Oriented Programming in Java Lab Course Code:17YCF411
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA) Total
Examination
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3
CIA- Lab Theory Lab
4
0 0 2 1 -- -- -- -- 25 0 25 50
Max. Time, End Semester Exam (Theory) -00 Hrs. End Semester Exam (Lab) – 03 Hrs.
Prerequisites:
Java Programing
Objectives:
Students are able to:-
1 Object oriented programming is the most proven technique for developing reliable programs. It
helps in increased productivity, reusability of code, decrease in the development time, and reduces
cost of production to an extent.
2 There are many languages which use the object oriented concepts and techniques. Some of them are
C++, Java, Smalltalk, Objective-C, etc. Java is a purely object oriented language
3 Systems/applications created using java programming language reduces the need for developing and
maintain complex and space consuming applications. Nowadays java is also found in the mobile
phones
Guidelines for Assessment
Continuous assessment of laboratory work is done based on overall performance and lab
assignments performance of student. Each lab assignment assessment will assign grade/marks
based on parameters with appropriate weightage. Suggested parameters for overall assessment as
well as each lab assignment assessment include- timely completion, performance, innovation,
efficient codes, punctuality and neatness.
Guidelines for Laboratory Conduction
The instructor is expected to frame the assignments by understanding the prerequisites,
technological aspects, utility and recent trends related to the topic. The assignment framing policy
need to address the average students and inclusive of an element to attract and promote the
intelligent students. The instructor may set multiple sets of assignments and distribute among
batches of students. It is appreciated if the assignments are based on real world
problems/applications. Encourage students for appropriate use of Hungarian notation, Indentation
and comments. Use of open source software is encouraged.
In addition to these, instructor may assign one real life application in the form of a mini-project
based on the concepts learned. Instructor may also set one assignment or mini-project that is
suitable to respective branch beyond the scope of syllabus.
Set of suggested assignment list is provided in three groups. Each student must perform at least 13
assignments as at 05 compulsory from group A, 07 from group B and 01 from group C
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Operating System recommended : 64-bit Open source Linux or its derivative
Programming tools recommended: Open Source C Programming tool like GCC
Suggested List of Laboratory Assignments
Group A (Compulsory Assignments)
1. Write a program to check whether two strings are equal or not.
2. Write a program to display reverse string.
3. Write a program to find the sum of digits of a given number.
4. Write a program to display a multiplication table.
5. Write a program to display all prime numbers between 1 to 1t000.
6. Write a program to insert element in existing array.
7. Write a program to sort existing array.
8. Write a program to create object for Tree Set and Stack and use all methods.
9. Write a program to check all math class functions.
10. Write a program to execute any Windows 95 application (Like notepad, calculator etc)
11. Write a program to find out total memory, free memory and free memory after executing
garbage Collector (gc).
Group B (Any 7)
12. Write a program to copy a file to another file using Java to package classes. Get the file names
at run time and if the target file is existed then ask confirmation to overwrite and take necessary
actions.
13. Write a program to get file name at runtime and display number f lines and words in that file.
14. Write a program to list files in the current working directory depending upon a
given pattern.
15. Create a textfileld that allows only numeric value and in specified length.
16. Create a Frame with 2 labels, at runtime display x and y command ordinate of mouse pointer in
the labels.
Group C (Any 1)
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – IV
Course: Database Management System Lab Course Code: 17YCF412
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA) Total
Examination
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3 CIA-4 Lab Theory Lab
0 0 2 1 -- -- -- -- 25 -- 25 50
Max. Time, End Semester Exam (Theory) -00 Hrs. End Semester Exam (Lab) – 03 Hrs.
Prerequisites:
Data Structures
Objectives:
Students are able to:-
1 To understand Database Programming Languages.
2 To learn and understand SQL, PL/SQL ,NoSQL
3 To learn Relational Database (Open source) such as MongoDB, MySQL
4 To learn and understand Database Project Life Cycle.
5 To understand Database Programming Languages.
Guidelines for Assessment
Continuous assessment of laboratory work is done based on overall performance and lab
assignments performance of student. Each lab assignment assessment will assign grade/marks
based on parameters with appropriate weightage. Suggested parameters for overall assessment as
well as each lab assignment assessment include- timely completion, performance, innovation,
efficient codes, punctuality and neatness.
Guidelines for Laboratory Conduction
The instructor is expected to frame the assignments by understanding the prerequisites,
technological aspects, utility and recent trends related to the topic. The assignment framing policy
need to address the average students and inclusive of an element to attract and promote the
intelligent students. The instructor may set multiple sets of assignments and distribute among
batches of students. It is appreciated if the assignments are based on real world
problems/applications. Encourage students for appropriate use of Hungarian notation, Indentation
and comments. Use of open source software is encouraged.
In addition to these, instructor may assign one real life application in the form of a mini-project
based on the concepts learned. Instructor may also set one assignment or mini-project that is
suitable to respective branch beyond the scope of syllabus.
Set of suggested assignment list is provided in three groups. Each student must perform at least 13
assignments as at 05 compulsory from group A, 07 from group B and 01 from group C
Operating System recommended : 64-bit Open source Linux or its derivative
Programming tools recommended: Open Source C Programming tool like GCC
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Suggested List of Laboratory Assignments
1. Study of Open Source Databases : MySQL/ MongoDB/CouchDBetc.
2. Design and Develop SQL DDL statements which demonstrate the use of SQL objects such
3. Design 10 SQL queries for suitable database application using SQL DML statements: Insert,
Select, Update, Delete with operators
4. Design at least 10 SQL queries for suitable database application using SQL DML statements:
all types of Join, Sub-Query and View
5. Use the relations below to write SQL queries to solve the business problems specified.
CLIENT (clientno#,name, client_referred_by#)
ORDER (orderno#, clientno#, order_date, empid#)
ORDER_LINE (orderno#, order line number#, item_number#, no_of_items, item_ cost,
shipping_date)
ITEM (item_number#, item_type, cost)
EMPLOYEE (empid#, emp_type#, deptno, salary, firstname, lastname)
6. Write a PL/SQL block to calculate the student grades.
7. Write a PL/SQL block to implement types of cursors.
8. Write a PL/SQL stored procedure and function.
9. Write a database Trigger.
10. Implement aggregation and indexing with suitable example using MongoDB
11. Implement Map reduces operation with suitable example using MongoDB.
12. Design and Implement any 5 query using MongoDB
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – IV
Course: IT Application Security Lab Course Code: 17YCF413
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA) Total
Examination
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3
CIA- Lab Theory Lab
4
0 0 2 1 -- -- -- -- 25 0 25 50
Max. Time, End Semester Exam (Theory) -00 Hrs. End Semester Exam (Lab) – 03
Hrs.
Prerequisites:
IT System security
Objectives:
Students are able to:-
1 Understands the different types of attack perform on system.
2 Understands the Unauthorized access to administration and confidential data in the system.
3 Understands application of cryptography in border sense.
4 Understands the different exploit perform without tracing.
5 Understands the application part of IBM Rational AppScan.
Guidelines for Assessment
Continuous assessment of laboratory work is done based on overall performance and lab
assignments performance of student. Each lab assignment assessment will assign grade/marks
based on parameters with appropriate weightage. Suggested parameters for overall assessment as
well as each lab assignment assessment include- timely completion, performance, innovation,
efficient codes, punctuality and neatness.
Guidelines for Laboratory Conduction
The instructor is expected to frame the assignments by understanding the prerequisites,
technological aspects, utility and recent trends related to the topic. The assignment framing policy
need to address the average students and inclusive of an element to attract and promote the
intelligent students. The instructor may set multiple sets of assignments and distribute among
batches of students. It is appreciated if the assignments are based on real world
problems/applications. Encourage students for appropriate use of Hungarian notation, Indentation
and comments. Use of open source software is encouraged.
In addition to these, instructor may assign one real life application in the form of a mini-project
based on the concepts learned. Instructor may also set one assignment or mini-project that is
suitable to respective branch beyond the scope of syllabus.
Operating System recommended : 64-bit Open source Linux or its derivative
Programming tools recommended: Open Source C Programming tool like GCC
Suggested List of Laboratory Assignments
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
1. Study practical on Application Security, Authentication & Authorization.
2. Perform Buffer Overflow and Input Validation.
3. Perform brute force attack on another machine.
4. Perform the on dictionary attacks.
5. Perform Phishing operation on another system.
6. Generate Cookies and transfer to it different machine.
7. Perform practical on to take unauthorized access to administration interfaces.
8. Perform the man in the middle attack.
9. Perform cryptography operation using cipher text.
10. Perform cryptography using public, private and symmetric key.
11. Perform different code analysis using IBM Rational AppScan.
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – IV
Course: English Communication and Soft Skill 1 Course Code: 17YFE411
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA)
Examination Total
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3 CIA-4 Lab Theory Lab
2 - 2 3 10 20 10 20 -- -- 50 100
Max. Time, End Semester Exam (Theory) - 00 Hrs. End Semester Exam (Oral) – 01 Hrs.
Prerequisite
2. Functional grammar-Parts of speech, Tenses, Sentence pattern
3. Formal letter
4. Fluency in reading and speaking
Objectives:
The course will enables students to:-
1 To help the students in building interpersonal skills.
2 To develop Emotional Intelligence to deal with difficult situations.
3 To create an open environment for Communication.
4 To inculcate employability skills among students.
Unit
Details Hours
No
Module 1: Study Skills
Communication: Importance, barriers to communication, effective communication.
4
Listening Skills: Listening for Comprehension
1 Reading Skills: passages from varied registers
Module 2:
Written Skills: Formal writing, Email writing, picture composition 4
Writing for Social Media
Module 1: English
Parts of Speech 4
Vocabulary Building
Module 2:
2
Basic Sentence Pattern
Antonyms and Synonyms- functional usage 3
Idioms, Phrases and Proverbs
Passive Voice
Module 1 : Soft Skills – I
4
Self-awareness: SWOT/SWOC, Perceptions and Attitudes, Positive ttitude
3 Module 2:
Body Language 4
Interpersonal Skills
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Module 1 :
Soft Skills – II 4
4 Presentation Skills
Module 2: Group Discussion
3
Interview Techniques.
Module 1:Reference & Study Skills
4
5 Use of Dictionary and Thesaurus
Module 2: Use of Articles, Journals and Reference booksWriting Reviews 4
Objectives:
Students should able to:
1. Students will acquire basic proficiency in English including reading and listening
comprehension, writing and speaking skills.
2. Students will be able to write formal letters effectively.
3. Students will be able to prepare, organize and deliver oral presentation.
4. Students will develop reading speed and build academic vocabulary.
5. Students will demonstrate behavior and attitudes appropriate to university environment.
Text Books
1. Communication Skills by Sanjay Kumar and PushpaLata, Oxford University Press.
2. Developing Communication Skill by Krishna Mohan, MeeraBanerji, McMillan India Ltd.
3. English for Business Communication by Simon Sweeney, Cambridge University Press.
Reference Book
1. Ethics in Engineering Practice and Research by Caroline &Whitbeck, Cambridge University
Press.
2. Personality Development and Group Discussions by Barun K. Mitra, Oxford University Press.
3. Group Discussions and Interview Skills by PriyadarshiPatnaik , Foundation Books , Cambridge
University Press.
4. The Power of Your Subconscious Mind by Dr Joseph Murphy MaanuGraphics , ISBN-13
9789381529560.
5. The 80/20 Principal by Richard Koch, Nicholas BrealeyPublishings , ISBN-13 9781857883992.
6. Time Management from Inside Out by Julie Morgenstern, Owl Books (NY), ISBN-13
9780805075908.
7. You can win by Shiv Khera, Macmillan, ISBN-139789350591932.
Web References
https://www.britishcouncil.in/sites/default/files/esfe_report.pdf
https://www.britishcouncil.org/sites/default/files/english-soft-skills-maghreb-research-report.pdf
http://nptel.ac.in/courses/109104030/references/references.pdf
http://promeng.eu/downloads/training-materials/ebooks/soft-skills/effective-communication-
skills.pdf
Journals
https://pdfs.semanticscholar.org/c1d3/e21ea8496e2d828678cde2981aac1bd4ce3e.pdf
http://www.iosrjournals.org/iosr-jhss/papers/Vol11-issue4/D01142022.pdf
https://www.tandfonline.com/doi/abs/10.1080/18186874.2016.1248061
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – IV
Course: Dynamic Paradigm in Cyber Security Course Code: 17YCF414
and Digital Forensics 2
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA) Total
Examination
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3
CIA- Lab Theory Lab
4
- - 2 1 -- -- -- -- 25 -- 25 50
Max. Time, End Semester Exam (Theory) -00 Hrs. End Semester Exam (Lab) – 00
Hrs.
Prerequisites:
Computer Organization
Objectives:
The course will enables students to:-
1 Learn how to analyze multidimensional data properly.
2 Understand the role of formal statistical theory and informal data warehouse methods.
Guidelines for Assessment
Continuous assessment of laboratory work is done based on overall performance and lab
assignments performance of student. Each lab assignment assessment will assign grade/marks
based on parameters with appropriate weightage. Suggested parameters for overall assessment as
well as each lab assignment assessment include- timely completion, performance, innovation,
efficient codes, punctuality and neatness.
Guidelines for Laboratory Conduction
The instructor is expected to frame the assignments by understanding the prerequisites,
technological aspects, utility and recent trends related to the topic. The assignment framing policy
need to address the average students and inclusive of an element to attract and promote the
intelligent students. The instructor may set multiple sets of assignments and distribute among
batches of students. It is appreciated if the assignments are based on real world
problems/applications. Encourage students for appropriate use of Hungarian notation, Indentation
and comments. Use of open source software is encouraged.
In addition to these, instructor may assign one real life application in the form of a mini-project
based on the concepts learned. Instructor may also set one assignment or mini-project that is
suitable to respective branch beyond the scope of syllabus.
Operating System recommended : 64-bit Open source Linux or its derivative
Programming tools recommended: Open Source C Programming tool like GCC
Suggested List of Laboratory Assignments
Seminars and Webinars conducted by IBM ICE trainer
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – IV
Course: French I Course Code:17YFF401
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA)
Examination Total
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3 CIA-4 Lab Theory Lab
2 - 2 10 20 10 10 -- 50 -- 100
Max. Time, End Semester Exam (Theory) - 03 Hrs. End Semester Exam (Lab) – 00
Hrs.
Objectives:
The course will enables students to:-
1 To be able to greet others formally and Informally ,say good bye and also frame and answer
W-questions about themselves and ask these questions to others
2 To be able to talk/write about their friends and their hobbies
3 To be able to talk about the city they live in, housing style, the important monuments and
the means of transport
4 To be able to talk about food habits and learn to communicate with the direct object.
5 To be able to talk about one’s family and relationships.
Unit
Details Hours
No
Module 1: Good Day!
Speech intentions: Greetings and Goodbyes, Introduce yourself and others, Speak
4
about yourself and others, Numbers till 20, To be able to say telephone, numbers
1 and email address, Spell it out, Speak about countries and their languages.
Module 2: Vocabulary: Numbers from 0-100, Countries and
Languages/nationalities Grammar: W- Questions (formal +informal / tuouvous), 4
Declarative sentences, Verbs, Personal pronouns Pronunciation, Alphabets.
Module 1: Friends, Colleagues and myself/S'ouvrir aux autres. Speech intentions:
Speak about hobbies, Arrange an informal meeting, State the days of the week,
4
telling the time in French /activity: dr. Appointment / speak work timings
Professions/le metier, Ordinal Numbers, Speak about seasons,
2 Module 2: Vocabulary, Hobbies, Days of the week, Numbers from70-
1000/practice date of birth, Professions, Months and seasons, Grammar, definite
articles ( Le,LA, les), for masculine, feminine gender agreement with gender. 3
verbs and personal pronouns 2, 3.Yes/ No questions, Plural, Verbs- to have and to
be ( avoir, etre)
Module 1In the city
Speech intentions:
1.State the names of places and buildings
3 4
2. Ask the address or directions to a place
3.Assign texts to a picture story/flashcards
4. Ask for things
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
5. State the names of various means of Transport
6. Ask for directions and to give directions
7. understand texts with international words and learn articles
Module 2: Grammar:
1. definite articles ( le LA Les)
2. indefinite articles (un, une,des) 4
3. negation with (ne---pas) (ne----pasde)
4. Formal imperative
Module 1: Goutera LA compagne(Enjoy your meal)
Speech intentions:
1. Speak about food
2. Make a shopping list
3. Converse while shopping
4. Understand texts using W- questions
4
5. Arrange the words and learn them
Vocabulary:
4
1. Meal timings
2.Grocery
3.Drinks
4. Shops
Module 2: Grammar:
1. Word order in sentences
3
2.Verbes acheter,payer, manger, boire
3. Usage of De, du, de la,des
Module 1: Family: Vocabulary related to family 4
5
Module 2: Film screening for all the lessons. 4
Internal Assessment:
CIA 1: Students will shoot a short introduction about themselves on the phone
CIA 2A: Receptive task: Read and understand a text
CIA 2B: Productive task: Write about 5-6 sentences about a friend/family member
CIA 3: Presentation on Nashik in the form of poster/picture post card according to the student's
choice/ monuments
CIA 4: The students will research into french food options inregionalzoneand make a presentation
on the topic in a format of their choice
Text Books
1. SaisonMETHODE DE FRANÇAIS A1
2. AlteregoA1
3. Apprenon le francais Niveau1-5
4. Jumelage
5. TRICOLOR
All books are published by GoyalsaabDelhi, We will be using SAISONA1 as the base for teaching.
Reference Book
All the audio available DELF ON didierfle.com/saison/www.didierfle.com/saison
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Year: Second Year Semester – IV
Course: German I Course Code: 17YFG402
Teaching
End Semester
Scheme Continuous Internal Assessment (CIA)
Examination Total
(Hrs. /Week)
L T P C CIA-1 CIA-2 CIA-3 CIA-4 Lab Theory Lab
2 - - 2 10 20 10 10 -- 50 -- 100
Max. Time, End Semester Exam (Theory) - 03 Hrs. End Semester Exam (Lab) – 00
Hrs.
Objectives:
The course will enables students to:-
1 To be able to greet others, say good bye and also frame and answer W-questions about
themselves and ask these questions to others.
2 To be able to talk/write about their friends and their hobbies.
3 To be able to talk/write about the city they live in, the important buildings there and the
means of transport.
4 To be able to talk/write about food habits and learn the accusative case in German.
5 To be able to talk/write about one’s family.
Unit
Details Hours
No
Module 1: Good Day!
Speech intentions:
Greetings and Goodbyes.
Introduce yourself and others
4
Speak about yourself and others
Numbers till 20
To be able to say telephone numbers and email address
Spell it out, Speak about countries and their languages.
Module 2:
1 Vocabulary:
Numbers from 0-100
Countries and Languages/nationalities
Grammar:
W- Questions (formal +informal / tuouvous) 4
Declarative sentences
Verbs
Personal pronouns Pronunciation
Alphabets.
Listening Comprehension
Module 1: Friends, Colleagues and myself/S'ouvrir aux autres.
2 Speech intentions: 4
Speak about hobbies
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
Arrange an informal meeting
State the days of the week
Speak about work, work timings ans Professions
Numbers From 20
Speak about seasons
Module 2: Vocabulary
Hobbies
Days of the week
Numbers from 20
Professions
Months and seasons
Grammar,
Definite articles (der , die , das): Nominative Case for masculine, feminine and 3
neutral.
Verbs and personal pronouns 2
Yes/ No questions
Plural
Verbs- to have and to be ( haben, sein)
Reading Comprehension, Write simple texts using the grammar that has been
taught
Module 1In the city
Speech intentions:
1.State the names of places and buildings
2. Ask the address or directions to a place
3.Assign texts to a picture story/flashcards
4
4. Ask for things
5. State the names of various means of Transport
6. Ask for directions and to give directions
3
7. understand texts with international words and learn articles
Module 2: Grammar:
1. definite articles (der, die, das)
2. indefinite articles (ein, eine, ein)
4
3. negation with (kein, keine, kein)
4. Formal imperative
Join the sentences using “aber’ (but) and “und” (and)
Module 1: GutenAppetit! (Enjoy your meal)
Speech intentions:
1. Speak about food
2. Make a shopping list
4 3. Converse while shopping 4
4. Understand texts using W- questions
5. Arrange the words and learn them
Vocabulary:
1. Meal timings
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
School of Computing Science and Engineering
Department of Computer Science and Engineering
2.Grocery
3.Drinks
4. Shops
Module 2: Grammar:
1. Word order in sentences
2. Accusative case
3
3. Verbs with Accusative
Form W-Questions, Statements and interrogative sentences and check the position
of the verb in the sentence
Module 1: Family: Vocabulary related to family
4
-Draw a family tree and describe one’s family
5
Module 2: , Film screening for all the lessons– Interactive session on films of the
4
units covered to understand the grasping of the vocabulary of all the 5 units
Outcomes:
CIA 1: Students will shoot a short introduction about themselves on the phone
CIA 2A: Internal exam
CIA 2B: Internal exam
CIA 3: Presentation on Nashik in the form of poster/picture post card according to the
student's choice
CIA 4: The students will research into food options in Nashik and make a presentation on
the topic in a format of their choice
Text Books
1. Netzwerk A1
2. Tangram A1
3. Studio D A1
4. Moment Mal A1
5. Themen 1
All books are published by Goyalsaab Delhi
We will be using Netzwerk A1 as the base for teaching.
Reference Book
www.youtube.com german150
https://www.youtube.com/channel/UC5ZnpdkQIit8TWhGVDiDnQQ
https://www.youtube.com/watch?v=PMj9kUPrnBk&t=46sMein Wegnach Deutschland
https://www.youtube.com/watch?v=X-J1t8q0wxMTypisch!
Dw.com/nico
www.vitaminde.de
Deutschtrainer A1 – Learning App from Google Store
Document Reference Revision No. / Date Prepared By Approved By
SUN/SOCSE/BTECH/CSF/2019 R3 / 23 October 2019
You might also like
- Managing the Testing Process: Practical Tools and Techniques for Managing Hardware and Software TestingFrom EverandManaging the Testing Process: Practical Tools and Techniques for Managing Hardware and Software TestingRating: 4 out of 5 stars4/5 (8)
- M.D. University Scheme of StudiesDocument52 pagesM.D. University Scheme of StudiesAryan RakhejaNo ratings yet
- Cse - 5thDocument46 pagesCse - 5thSakshi SharmaNo ratings yet
- Mumbai University BE IT Sem III Revised Syllabus 2020-21Document35 pagesMumbai University BE IT Sem III Revised Syllabus 2020-21Shaikh WasimaNo ratings yet
- SE COMP SEM III DSE 2020 21 - SyllabusDocument21 pagesSE COMP SEM III DSE 2020 21 - SyllabusPoonam PangarkarNo ratings yet
- Se Comp Sem-Iii-Dse-2020-21Document21 pagesSe Comp Sem-Iii-Dse-2020-21hewag82915No ratings yet
- 4 Semester: B.Tech (Computer Science and Engineering) Syllabus For Admission Batch 2015-16Document12 pages4 Semester: B.Tech (Computer Science and Engineering) Syllabus For Admission Batch 2015-16Samarjeet SahooNo ratings yet
- Httpsece - Gndec.ac - InsitesdefaultfilesSyllabus20Scheme EC20 20320to2082028920june202020292028429 PDFDocument5 pagesHttpsece - Gndec.ac - InsitesdefaultfilesSyllabus20Scheme EC20 20320to2082028920june202020292028429 PDFGurtej singhNo ratings yet
- Big DataDocument28 pagesBig DatajaijohnkNo ratings yet
- SyllabusDocument83 pagesSyllabusafreen babaNo ratings yet
- Diploma CS III SEMDocument18 pagesDiploma CS III SEMManik SinghNo ratings yet
- SRI SIDDHARTHA INSTITUTE OF TECHNOLOGY ECE DEPARTMENT VISION AND PROGRAM OUTCOMESDocument42 pagesSRI SIDDHARTHA INSTITUTE OF TECHNOLOGY ECE DEPARTMENT VISION AND PROGRAM OUTCOMESRoyal ClashNo ratings yet
- B.Tech IT 3 4 Semester Session 2021-22 Scheme SyllabusDocument28 pagesB.Tech IT 3 4 Semester Session 2021-22 Scheme Syllabuslakshyaraj Singh chundawatNo ratings yet
- B.Tech CSE 3rd YearDocument54 pagesB.Tech CSE 3rd YearJAIVINDERNo ratings yet
- 5th Semester Syllabus for B.Tech in ITDocument14 pages5th Semester Syllabus for B.Tech in ITturi puchhiNo ratings yet
- B.TECH CS II YearDocument20 pagesB.TECH CS II YearNavneet SharmaNo ratings yet
- COMPUTER Engineering - DEC2018 New-MinDocument163 pagesCOMPUTER Engineering - DEC2018 New-MinAdhara MukherjeeNo ratings yet
- Direct Second Year Engineering Students Admission CircularDocument37 pagesDirect Second Year Engineering Students Admission CircularMafia PathanNo ratings yet
- Hzu B.tech Syllabus (Cse) 07 Jan 2016Document95 pagesHzu B.tech Syllabus (Cse) 07 Jan 2016Rohit GoyalNo ratings yet
- Computer Engineering Syllabus - Sem VII & SEM VIII (Choice Based Credit and Grading System)Document56 pagesComputer Engineering Syllabus - Sem VII & SEM VIII (Choice Based Credit and Grading System)Saqlain BukhshNo ratings yet
- Chemical All 0Document187 pagesChemical All 0fact of factsNo ratings yet
- BamuDocument41 pagesBamujjkkNo ratings yet
- BCA Semester V SECs SyllabusDocument33 pagesBCA Semester V SECs SyllabusMadhuNo ratings yet
- 2.BS Computer EngineeringDocument14 pages2.BS Computer EngineeringEdgarNo ratings yet
- B.E.-Computer-Engg.Document27 pagesB.E.-Computer-Engg.Jai JindalNo ratings yet
- CSE 3 NotesDocument15 pagesCSE 3 NotesCSE SSGINo ratings yet
- T.Y. B. Sc. Computer Science SyllabusDocument29 pagesT.Y. B. Sc. Computer Science SyllabusVishal ParabNo ratings yet
- Computer Engineering - Final Year Semester 78Document72 pagesComputer Engineering - Final Year Semester 78glitched matrixNo ratings yet
- Batch 2017 4th Semester CSEDocument28 pagesBatch 2017 4th Semester CSEAzeem KhanNo ratings yet
- Syallbus B. Tech CSE First YearDocument12 pagesSyallbus B. Tech CSE First YearRishav RajNo ratings yet
- Secse 220915 215039Document41 pagesSecse 220915 215039jjkkNo ratings yet
- BTech CSE Course StructureDocument77 pagesBTech CSE Course StructureRohit GoyalNo ratings yet
- National Institute of Technology, RaipurDocument11 pagesNational Institute of Technology, RaipurAjeet KumarNo ratings yet
- B.Tech CSE 3 4 Semester Session 2021-22 Scheme SyllabusDocument28 pagesB.Tech CSE 3 4 Semester Session 2021-22 Scheme SyllabusDeepak KumarNo ratings yet
- Bachelor of Technology CseDocument8 pagesBachelor of Technology CseNaveen Kumar SharmaNo ratings yet
- 20240221104149-MR21 CSE B.tech Syllabus BookDocument210 pages20240221104149-MR21 CSE B.tech Syllabus BookSyamkumarDuggiralaNo ratings yet
- CSE Syllabus III-IV SemesterDocument32 pagesCSE Syllabus III-IV SemesterJatan TiwariNo ratings yet
- Handbook-M.E (CSE) Regulation 2019 (Students Admitted To Our Department From TheDocument84 pagesHandbook-M.E (CSE) Regulation 2019 (Students Admitted To Our Department From TheRaj sekharNo ratings yet
- MSD Bos CseDocument40 pagesMSD Bos Csepravin2mNo ratings yet
- Rajiv Gandhi Technological University, Bhopal (MP) : B.E. (EC) Electronics and Communication EnggDocument36 pagesRajiv Gandhi Technological University, Bhopal (MP) : B.E. (EC) Electronics and Communication EnggNikin KannolliNo ratings yet
- DJ 66555442525Document16 pagesDJ 66555442525AVHAD RUTIKNo ratings yet
- BTECH CSE 5th SemesterDocument18 pagesBTECH CSE 5th SemesterAdityaNo ratings yet
- Cse Btech III Yr V Sem Scheme Syllabus July 2022Document26 pagesCse Btech III Yr V Sem Scheme Syllabus July 2022Ved Kumar GuptaNo ratings yet
- Cse Syllabus 14Document75 pagesCse Syllabus 14sarthak nareshNo ratings yet
- MLDA SyllabusDocument20 pagesMLDA Syllabusmesevox663No ratings yet
- MCA - Syllabi Sem I and II 2019-2020Document28 pagesMCA - Syllabi Sem I and II 2019-2020BadboyNo ratings yet
- BTECH2022Document181 pagesBTECH2022faizan bariNo ratings yet
- Scheme of Instruction and Syllabi Of: Department of Computer Science & EngineeringDocument43 pagesScheme of Instruction and Syllabi Of: Department of Computer Science & Engineeringvineeth sagarNo ratings yet
- DATA SCIENCE SYLLABUS 2nd YearDocument58 pagesDATA SCIENCE SYLLABUS 2nd YearNEVER SETTLENo ratings yet
- r20 SchemeDocument8 pagesr20 SchemeVambaravelli HemanthNo ratings yet
- R V R & J C COLLEGE OF ENGINEERING, CHOWDAVARAM, GUNTUR-19 Semester I Course ScheduleDocument80 pagesR V R & J C COLLEGE OF ENGINEERING, CHOWDAVARAM, GUNTUR-19 Semester I Course ScheduleGirish SaiNo ratings yet
- CSBS 4 NotesDocument16 pagesCSBS 4 NotesCSE SSGINo ratings yet
- B Tech I Year 1Document24 pagesB Tech I Year 1Navneet SharmaNo ratings yet
- B.Tech 3rd Sem CSE Syllabus 2015-16Document72 pagesB.Tech 3rd Sem CSE Syllabus 2015-16Siddharth SekharNo ratings yet
- B.Tech Computer Science and Engineering: Study & Evaluation SchemeDocument5 pagesB.Tech Computer Science and Engineering: Study & Evaluation SchemesunnyiitvnsNo ratings yet
- CSE - Hand Book (RA15) 05-06-2017 PDFDocument210 pagesCSE - Hand Book (RA15) 05-06-2017 PDFRaghav MunnaNo ratings yet
- CSE 4 NotesDocument22 pagesCSE 4 NotesCSE SSGINo ratings yet
- M.tech 1st Year SyllabusDocument13 pagesM.tech 1st Year SyllabusarshiNo ratings yet
- 6th Sem Syllabus PDFDocument25 pages6th Sem Syllabus PDFsnehasish jenaNo ratings yet
- Regents Prep 4Document7 pagesRegents Prep 4api-24284785450% (2)
- Construction Engineering and ManagementDocument3 pagesConstruction Engineering and ManagementMica XDNo ratings yet
- MATHS Revision DPP No 1Document8 pagesMATHS Revision DPP No 1ashutoshNo ratings yet
- University of Waterloo Thesis RepositoryDocument5 pagesUniversity of Waterloo Thesis Repositoryafknkzkkb100% (2)
- Fine Art Estate - 2017 CatalogDocument386 pagesFine Art Estate - 2017 CatalogWeygers FoundationNo ratings yet
- Developing The Assessment Instrument of SpeakingDocument11 pagesDeveloping The Assessment Instrument of Speakingifdol pentagenNo ratings yet
- A Case Study On SchistosomiasisDocument154 pagesA Case Study On SchistosomiasisCarmellaDawn100% (1)
- Cainta Catholic College: Senior High School DepartmentDocument17 pagesCainta Catholic College: Senior High School DepartmentAllan Santos SalazarNo ratings yet
- Understanding Balance of PaymentsDocument8 pagesUnderstanding Balance of PaymentsMurtaza JamaliNo ratings yet
- National Study of 10 Years CurriculumDocument154 pagesNational Study of 10 Years CurriculumVIJAY KUMAR HEERNo ratings yet
- Understanding Application ReasoningDocument42 pagesUnderstanding Application ReasoningadeNo ratings yet
- Report of Lost, Stolen, Damaged or Destroyed Property: Appendix 75Document3 pagesReport of Lost, Stolen, Damaged or Destroyed Property: Appendix 75Knoll Viado100% (1)
- Evidence Law ProjectDocument20 pagesEvidence Law ProjectxyzNo ratings yet
- Conversation LaundryDocument2 pagesConversation Laundryvanni octavania88% (8)
- Jean Piaget's Theory On Child Language Development: Supporting Mtb-Mle Developmental Learning TheoriesDocument17 pagesJean Piaget's Theory On Child Language Development: Supporting Mtb-Mle Developmental Learning TheoriesFrancis Dave Villanova AriasNo ratings yet
- Review On Internal Combustion Engine Vibrations and MountingsDocument12 pagesReview On Internal Combustion Engine Vibrations and MountingsSanthosh KumarNo ratings yet
- Annotated BibliographyDocument6 pagesAnnotated BibliographyAnonymous 9VRu3ImiEQNo ratings yet
- 9601 Be Quiet George The ImperativeDocument1 page9601 Be Quiet George The Imperativeheoquay19311% (9)
- Meaning of Population EducationDocument28 pagesMeaning of Population Educationanon_896879459No ratings yet
- Chari Boru's - DR - Haasan Huseen - Microeconomics I PPT (PHD) ProgramDocument399 pagesChari Boru's - DR - Haasan Huseen - Microeconomics I PPT (PHD) ProgramCHARI BORUNo ratings yet
- Paper 6D - Appeals & Days Time Limits (By Khader)Document6 pagesPaper 6D - Appeals & Days Time Limits (By Khader)Khader MohammedNo ratings yet
- National Register of Large Dams -2019: Government of India Central Water CommissionDocument300 pagesNational Register of Large Dams -2019: Government of India Central Water CommissionPrabhjeet BaidNo ratings yet
- Understanding the Interdisciplinary Field of Cognitive ScienceDocument10 pagesUnderstanding the Interdisciplinary Field of Cognitive ScienceDoris TănaseNo ratings yet
- Maternal and Child PreboardDocument17 pagesMaternal and Child PreboardMichelle GambolNo ratings yet
- BCOM SyllabusDocument67 pagesBCOM SyllabusvjayarajuNo ratings yet
- Cy and JoyDocument6 pagesCy and JoyAlexander GreatNo ratings yet
- Introduction to Accounting BasicsDocument14 pagesIntroduction to Accounting BasicsJunaid IslamNo ratings yet
- Gods Revelation in Jesus and in His ChurchDocument13 pagesGods Revelation in Jesus and in His ChurchMerry DaceraNo ratings yet
- Diogenes The Cynic and Shakespeare's Bitter FoolDocument31 pagesDiogenes The Cynic and Shakespeare's Bitter FoolGEORGE FELIPE BERNARDES BARBOSA BORGESNo ratings yet
- The Flower of Services A Study On Private Universities in Sylhet CityDocument11 pagesThe Flower of Services A Study On Private Universities in Sylhet CityLatif AbdulNo ratings yet