Professional Documents
Culture Documents
Mobile Security Whitepaper 2021
Uploaded by
Gregory ZwirnCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Mobile Security Whitepaper 2021
Uploaded by
Gregory ZwirnCopyright:
Available Formats
Microsoft 365 mobile apps with
Security, Compliance, & Identity
The lowdown of locking down secure mobile productivity
Introduction
Mobile technology has transformed the business landscape. Workers rely on multiple screens to
manage work and personal pursuits throughout the day. They are taking Teams calls and web surfing
on their phones in the kitchen, reviewing spreadsheets and PowerPoints on tablets at a local cafe,
and deftly moving between business and personal projects on their laptops. But as the lines between
work and personal use have blurred, new security risks have arisen. The challenge: How can
organizations support employees who want to use their mobile devices for both work and personal
reasons while securing corporate data?
Users want—and expect—the ability to access their work and personal data anytime, anywhere, on
any device, using the apps they know and love. However, the very features that users love also leave
devices vulnerable. An SMS (text) or social media posting may include a legit link—or a phishing lure.
A free game download in the app store may be malware in disguise. Attackers use these (and other)
schemes to get into the user's device in pursuit of the real target: their corporate network.
Security from the ground up
At Microsoft, we spend more than $1 billion per year on cybersecurity research and development.
What differentiates Microsoft from other security companies is our approach. We take a truly holistic
approach to the technology that safeguards identities, data, applications, and mobile devices end-to-
end. The goal: protect sensitive data no matter where it's created, where it lives, or where it travels.
Microsoft 365 was developed with both the mobile-end user and corporate security experience in
mind. This combination of Office 365, Windows, security, endpoint management, and enhanced data
management incorporates the mobile apps and solutions that are loved by IT, loved by users, and
trusted by all. Workers get one-stop shopping for the apps and tools they already know and use
daily, tailored to ensure they feel at home on their preferred iOS and Android devices. IT teams value
Microsoft 365 for its deep integration with the Azure ecosystem, familiar toolset, and strong security.
Plus, Microsoft security intelligence capabilities can be used to accurately identify and evaluate
threats captured from user activity.
In the event a threat is identified, the information is extracted and fed in real-time to Microsoft
Security teams who use powerful tools including AI, audits, and ediscovery to investigate
compromised accounts and help better understand the scope of a breach. Having this broad view of
user activity and potential threats enables risk-based assessments for protecting identities, data,
applications, and mobile device end-to-end benefits for all users, and protects SMB and enterprise
customers.
In this paper, we'll review the critical components of mobile security—identity, device, and data
protection—and discuss how Microsoft 365 can help prevent attackers from breaching the network
via mobile device usage.
Microsoft 365 mobile apps with Security, Compliance, & Identity 2
Figure 1: Microsoft Zero Trust architecture
Identity protection
The explosion of iOS and Android devices, apps, and users outside of the corporate network creates
identity challenges for today's IT teams. Identity attacks, particularly on mobile devices, are on the
rise—yet organizations lack visibility (and control) over their workers' personal devices. The
foundation of Microsoft 365 security and compliance is based on user identity; In other words,
ensuring that the person accessing corporate data is authorized to do so. Before a user is allowed on
the network, they must be authenticated to ensure they are a trusted user. This involves:
Confirming the user's identity
Identifying previous network activity (what they have been allowed to do in the past)
Determining what they’ve attempted to do (e.g., previous failed authentication attempts)
Evaluating what they are attempting to do now
Microsoft has been working to develop identity management options that can be plugged into an
organization's existing security solution with minimal impact on the end user. In this section, we'll
take a brief look at how Microsoft can help organizations manage, strengthen, and simplify users’
identity for their mobile workforce.
Implement conditional access policies
Users may try to access corporate resources from anywhere. Therefore, Microsoft recommends
moving from a traditional, perimeter-based network defense to an identity-driven security model.
Microsoft 365 mobile apps with Security, Compliance, & Identity 3
Azure Active Directory Conditional Access policies use a combination of user, location, device, app,
and other risk factors to protect Microsoft service endpoints such as Microsoft 365. The policies
define which authentication attempts in Azure Active Directory (Azure AD) will be subject to which
access controls. For example, organizations can enforce multifactor authentication (MFA) for all users
outside the network perimeter or require a password reset if a user's risk level is elevated.
Conditional Access policies also let organizations block email access from undesired apps such as
native OS clients, unknown networks, or devices that may be non-compliant with corporate security
policies. For example, if a company only allows modern authentication or OAuth, Conditional Access
can be used to block Exchange Active Sync (EAS) clients on iOS and Android devices that use basic
authentication to access Exchange Online.
Move to passwordless authentication
Passwords have been a staple of identity management for decades—and a common source of
vulnerability. End-user fatigue may lead to unsafe practices such as repeating passwords or using
ones that are easy to guess. Passwordless authentication methods replace a password requirement
with something the user has, plus something they know.
Microsoft offers passwordless authentication options that integrate directly with Azure AD, including
the Microsoft Authenticator app. Workers with Android and iOS devices can use biometrics (e.g.,
their face or thumbprint) to verify their identity through the app. Organizations can also add a
secondary verification requirement such as a password, PIN, or time-based, one-time passcode (also
known as TOTP or OTP).
As an added benefit, putting workers' identification into Azure AD enables organizations to manage
laptop authentication with Windows Hello for Business and FIDO2 security keys (e.g., an external
security key or platform key).
Implement endpoint compliance
Organizations are under intense pressure to ensure all mobile devices used to handle company data
are secure and compliant. That extends to vendors and service providers hired to assist with projects
using their own (or company-owned) mobile devices. Microsoft Endpoint Manager helps
organizations modernize IT processes and increase security posture for all devices while utilizing
existing technology investment. Endpoint Manager can be used to help onboard PCs, Macs, and
mobile devices. Windows Server can be used for security management, device management, and
device monitoring on all devices both in the cloud and on-premises. It has built-in integration with
Azure Active Directory Conditional Access to verify endpoint compliance status using device, app,
and risk-based policies evaluation. The device compliance dashboard helps ensure update readiness,
deploying and managing apps, operating system, and software updates, as well as up-to-date
security and compliance policies.
Microsoft 365 mobile apps with Security, Compliance, & Identity 4
For more information
For more information about identity management, please see these resources:
Azure Active Directory Universal identity and access management solution
Azure Active Directory Identity Protection
Identity and device access configurations
Endpoint Manager Compliance Policies
Device protection
Personal phones and tablets are more than productivity devices; they entertain, inform, and connect
people to each other. Allowing workers to use personal mobile devices and protecting the network
are not mutually exclusive goals; with the right apps, both can be achieved. Microsoft provides
protection on the mobile apps that users already know and love, including Edge and Office, so
workers can enjoy everything mobile has to offer while minimizing their device’s vulnerability to
attack. In this section, we'll take a brief look at how Microsoft can help ensure workers’ devices will
be protected.
Deliver protected mobile experiences
Microsoft Endpoint Manager, which includes Microsoft Intune, is a unified endpoint management
solution that provides the tools required to securely support employees who want to work on the
devices and apps they choose. There are multiple ways of managing mobile devices and apps. These
include mobile device management (MDM), which allows configuration and compliance for the
entire device and requires device enrollment and mobile application management (MAM), which
applies data protection controls on applications to protect the corporate data on personal (non-
corporate-owned) or corporate-owned devices.
Intune's MAM solution includes mobile app protection policies (APP) and app configuration settings
and may be deployed with or without device enrollment (MDM). The primary difference: MDM
ensures the device is managed and compliant, while the APP solution focuses on ensuring
compliance with respect to the data. A fuller scope of APP capabilities also includes enabling data
transfer, encryption, access, and conditional launch capabilities.
Microsoft 365 mobile apps with Security, Compliance, & Identity 5
Figure 2: Sample device showing corporate and personal profiles
For Android device users, Intune supports the configuration of Android Enterprise work and personal
containers enabling both personal and corporate-owned devices to be configured with a set of
features and services that separate personal apps and data from work apps and data. The work
profile can be set-up with Intune and Azure Active Directory (using an Active Directory join) with IT
administrators making the determinations regarding what apps will be allowed and how they will be
configured by way of enrollment options for managing device, data and app security. When work
profile authorized apps are configured and installed, they are easily identified by a lock icon such as
for Microsoft Authenticator. Note that Intune only manages the corporate apps and data, the user is
responsible for managing the personal side of the device and personal profile which are not
accessible by corporate IT. Admins should be aware that Android Enterprise devices aren’t
preconfigured for capabilities such as forcing the user to encrypt so utilizing Conditional Access
policies and compliance settings to protect organizational resources is highly recommended.
Companies can use app protection policies with or without MDM. For example, consider an
employee who uses both a company-issued phone and their own personal tablet for work. The
corporate asset (phone) would be enrolled in MDM and protected by app protection policies. The
Microsoft 365 mobile apps with Security, Compliance, & Identity 6
personal device (tablet) would be protected solely by app protection policies. On either device, the
employee would login to access work data using the same Azure AD credentials and the right set of
policies will be applied based on IT configuration.
Endpoint protection for mobile device users
Microsoft Defender ATP helps protect personal devices against malware and phishing attacks by
blocking unsafe connections, scanning for malware, and blocking access to sensitive data on both
enrolled and unenrolled devices. In addition, it offers a unified security experience through the
Microsoft Defender Security Center, where security teams can get a centralized view of alerts,
incidents, and the additional context required to remediate threats across all endpoints. It is now
available for both Android and iOS devices.
Implement best practices
It is critical that all companies, vendors, and service providers clearly define and enforce device
policies for enrolled devices or workers who opt to use personal devices for work. Organizations can
use Microsoft Defender ATP to configure anti-phishing policies to protect devices. This policy also
includes anti-impersonation settings to protect users and domains. Organizations can also use the
spoof intelligence policy to allow (or block) specific spoofed internal and external email senders.
For more information
For more information, please see these resources:
Enforce Compliance for Microsoft Defender for Endpoint with Conditional Access in Intune
Microsoft Endpoint Manager
Android Enterprise Security Configuration Framework
Microsoft 365 mobile apps with Security, Compliance, & Identity 7
Data protection
Despite efforts to educate and inform, people can (and do) still make mistakes. Organizations can't
stop users from surfing the web, texting, or downloading apps. However, it is possible to prevent
those bad decisions from becoming a data leak. In this section, we'll take a brief look at how
Microsoft can help ensure organizational data will be safe on workers' personal devices.
Implement app protection policies
Workers are multitasking on their devices, managing work, conducting personal business, and
enjoying leisure activities. Microsoft recommends implementing Intune app protection policies (APP)
to help ensure employees can use their preferred devices to stay productive while preventing
accidental (or intentional) data loss. Intune APPs can be used to restrict access to company resources
for enrolled—and unenrolled—devices accessing the network. From the end user perspective, they
keep using the protected apps just as they always did, comfortable in the knowledge that their data
is safe from leaving the corporate environment.
Protect documents in the cloud
Workers may need to share files with clients or vendors outside of the network. OneDrive for
Business can help protect data outside the firewall by requiring a password to access a shared link.
This prevents unauthorized users from accessing the file in the event the link is intercepted or
forwarded. If Microsoft detects a ransomware attack, the OneDrive user will receive an email or
notification.
Add protection through data compliance
Microsoft Information Protection (MIP) for Microsoft 365 helps organizations better protect sensitive
information across devices, apps, cloud services, and on-premises. MIP provides a consistent and
comprehensive approach to discovering, classifying, labeling, and protecting sensitive data to help
prevent accidental sharing of sensitive data. The built-in labeling experiences are integrated
directly—there's no need for any special plugins or add-ins. And as the experience is consistent
across Office apps, it's easy and familiar for users to apply sensitivity labels while working in
Microsoft 365 on the Android or iOS device.
For more information
For more information about data protection and classification functionality, please see these
resources:
Microsoft Information Protection (MIP)
Information Protection and Governance
Microsoft 365 mobile apps with Security, Compliance, & Identity 8
Microsoft Intune App lifecycle
APP data protection framework
Intune App Protection Policies (APP)
App Protection Policies for unmanaged devices (iOS, Android)
In conclusion
Personal device use is here to stay—and so are mobile-centric attacks. Combatting these attacks
requires planning and vigilance. Organizations can help protect their network by tailoring a security
plan that incorporates identity management, device management, and data protection and utilizes
the Microsoft apps that are loved by IT, loved by users, and trusted by all.
January 2021
Microsoft 365 mobile apps with Security, Compliance, & Identity 9
You might also like
- Active Directory Migrations A Complete Guide - 2020 EditionFrom EverandActive Directory Migrations A Complete Guide - 2020 EditionNo ratings yet
- Microsoft IntuneDocument8 pagesMicrosoft IntunePenny worthNo ratings yet
- Intune Privacy and Data Protection OverviewDocument13 pagesIntune Privacy and Data Protection OverviewFelicianoNo ratings yet
- Mobile Device Managment at Microsoft TCS W10Document13 pagesMobile Device Managment at Microsoft TCS W10Julio Espirito SantoNo ratings yet
- Endpoint DLP OverviewDocument25 pagesEndpoint DLP Overviewavinashsharma.inNo ratings yet
- Intune ImplementationDocument61 pagesIntune Implementationdev KumarNo ratings yet
- Requirements For Azure Information Protection - AIP - Microsoft DocsDocument5 pagesRequirements For Azure Information Protection - AIP - Microsoft DocssjmpakNo ratings yet
- Intune ComanagementDocument20 pagesIntune ComanagementVIVEKNo ratings yet
- Conversational Azure Backup Best Practices PDFDocument28 pagesConversational Azure Backup Best Practices PDFCoordinacion TIC ExtrusionesNo ratings yet
- Device Features and Settings in Microsoft Intune PDFDocument551 pagesDevice Features and Settings in Microsoft Intune PDFAmardeep KumarNo ratings yet
- Measuring Efficiency of Cloud Computing-1-1Document7 pagesMeasuring Efficiency of Cloud Computing-1-1rajasekarkalaNo ratings yet
- M365 Security Administration Guia MS 500Document8 pagesM365 Security Administration Guia MS 500Roberto LopezNo ratings yet
- Cloud-enabled platform for unified and secure endpoint managementDocument2 pagesCloud-enabled platform for unified and secure endpoint managementionNo ratings yet
- Information Protection For Office 365Document1 pageInformation Protection For Office 365javiyahooNo ratings yet
- Deploy An Endpoint Detection and Response (EDR) Solution With MicrosoftDocument6 pagesDeploy An Endpoint Detection and Response (EDR) Solution With Microsofthai TrầnNo ratings yet
- IT Project Planning Guide For Intel (R) AMTDocument36 pagesIT Project Planning Guide For Intel (R) AMTYimmyQuispeYujraNo ratings yet
- Enterprise Mobility ManagementDocument12 pagesEnterprise Mobility ManagementSharath ChandraNo ratings yet
- Deploy A Modern and Secure Desktop With Microsoft: Windows 10 Office 365 ProplusDocument5 pagesDeploy A Modern and Secure Desktop With Microsoft: Windows 10 Office 365 ProplusakdreamscapeNo ratings yet
- Manage Desktops Using Group PolicyDocument13 pagesManage Desktops Using Group PolicyparitaNo ratings yet
- Mobile Cloud ComputingDocument10 pagesMobile Cloud ComputingHobikNo ratings yet
- Enrolling An Android Device in InTuneDocument15 pagesEnrolling An Android Device in InTuneRai DuNo ratings yet
- Modern Work User Subscription Plan Comparison For Enterprise - 27 Jan 2022Document9 pagesModern Work User Subscription Plan Comparison For Enterprise - 27 Jan 2022Pavan RajeshNo ratings yet
- Office 365 and Microsoft 365 Price ComparisonDocument4 pagesOffice 365 and Microsoft 365 Price ComparisonIndumati YadavNo ratings yet
- Protegrity Application Protector Data SheetDocument2 pagesProtegrity Application Protector Data SheetManish BajpaiNo ratings yet
- Pim PPTDocument3 pagesPim PPTNavneetGuptaNo ratings yet
- SOW IT Management Services IT Security PDFDocument36 pagesSOW IT Management Services IT Security PDFblackghostNo ratings yet
- Cloud Computing GuideDocument217 pagesCloud Computing Guideikram1984No ratings yet
- 7 Keys To Delivering Secure Remote AccessDocument3 pages7 Keys To Delivering Secure Remote AccessmaryamNo ratings yet
- Microsoft End-Point ManagerDocument25 pagesMicrosoft End-Point ManagermaazNo ratings yet
- Module 04 - Endpoint ManagementDocument37 pagesModule 04 - Endpoint ManagementManuel Felipe PortelaNo ratings yet
- Intune Enrollment MethodsDocument2 pagesIntune Enrollment MethodsVIVEKNo ratings yet
- Trusted Information Protection: On-Premises. On Devices. in The Cloud. at All TimesDocument20 pagesTrusted Information Protection: On-Premises. On Devices. in The Cloud. at All TimesferNo ratings yet
- Implementing & Managing Microsoft 365 - Mobility & Security Exam PrepDocument2 pagesImplementing & Managing Microsoft 365 - Mobility & Security Exam PrepJyothi PrakashNo ratings yet
- Managing Cloud Security & Risk ExposureDocument4 pagesManaging Cloud Security & Risk ExposureCisco ITNo ratings yet
- QRadar SIEM 7.0 Data SheetDocument4 pagesQRadar SIEM 7.0 Data Sheetmehak_3274516No ratings yet
- Achieving Secure, Scalable and Fine-Grained Data Access Control in Cloud ComputingDocument47 pagesAchieving Secure, Scalable and Fine-Grained Data Access Control in Cloud Computingpssumi2No ratings yet
- SCCM FeaturesDocument25 pagesSCCM FeaturesMO1101100% (1)
- Microsoft Teams BackupDocument24 pagesMicrosoft Teams BackupJuan Tomas OrtizNo ratings yet
- Windows Intune at A GlanceDocument2 pagesWindows Intune at A GlanceAndréia CostaNo ratings yet
- Windows 10 Commercial ComparisonDocument1 pageWindows 10 Commercial Comparisonmyodlac9k874zlwdegkcNo ratings yet
- Unified Endpoint Management and Security 2022Document5 pagesUnified Endpoint Management and Security 2022Mathieu LEROYNo ratings yet
- Microsoft Endpoint Manager OverviewDocument4 pagesMicrosoft Endpoint Manager OverviewionNo ratings yet
- EndUser Backup PolicyDocument3 pagesEndUser Backup Policyaami6No ratings yet
- Microsoft 365 Security: Bourseaud Laurent Architecte Microsoft 365Document51 pagesMicrosoft 365 Security: Bourseaud Laurent Architecte Microsoft 365Kevin LmrNo ratings yet
- Thycotic Denver PresentationDocument41 pagesThycotic Denver PresentationuakarsuNo ratings yet
- Managing Windows 10 Devices With Microsoft IntuneDocument5 pagesManaging Windows 10 Devices With Microsoft IntuneAmardeep KumarNo ratings yet
- Why Use Azure Cloud OriginalDocument16 pagesWhy Use Azure Cloud OriginalPride4444 NobleNo ratings yet
- MS-101 Microsoft 365 Mobility and Security Al 01-Sept-2022Document615 pagesMS-101 Microsoft 365 Mobility and Security Al 01-Sept-2022Andy Roberto Dixon GutiérrezNo ratings yet
- Desktop Architect in Philadelphia PA Resume Mark MelansonDocument4 pagesDesktop Architect in Philadelphia PA Resume Mark MelansonMarkMelanson1No ratings yet
- Modern Work & Security For SMB and ScaleDocument25 pagesModern Work & Security For SMB and ScalecursurilemeleNo ratings yet
- Office 365 Deployment Patterns and PracticesDocument24 pagesOffice 365 Deployment Patterns and PracticesRiki Rinaldo100% (1)
- Module 03 - Windows 365Document47 pagesModule 03 - Windows 365Manuel Felipe PortelaNo ratings yet
- Windows Azure Security Technical Insights Feb 2014Document41 pagesWindows Azure Security Technical Insights Feb 2014RaphaelCPNo ratings yet
- Microsoft Endpoint Manager - MEMDocument86 pagesMicrosoft Endpoint Manager - MEMNsrk KrishnaNo ratings yet
- Active Directory Security Assessment (EN) PDFDocument2 pagesActive Directory Security Assessment (EN) PDFTalal AnwarNo ratings yet
- McAfee DLP 9.0.1 Product Guide PDFDocument238 pagesMcAfee DLP 9.0.1 Product Guide PDFJavier HernanzNo ratings yet
- Microsoft - Examcollectionpremium.70 416.v2015!10!15.by - Rabz.90qDocument85 pagesMicrosoft - Examcollectionpremium.70 416.v2015!10!15.by - Rabz.90qPazNo ratings yet
- Web Application Compromise Response PlaybookDocument7 pagesWeb Application Compromise Response PlaybookFrank GulmayoNo ratings yet
- Active Directory Migration Strategy A Complete Guide - 2020 EditionFrom EverandActive Directory Migration Strategy A Complete Guide - 2020 EditionNo ratings yet
- TNG UPDATE InstructionsDocument10 pagesTNG UPDATE InstructionsDiogo Alexandre Crivelari CrivelNo ratings yet
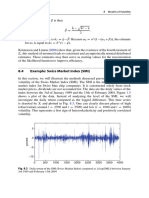
- 8.4 Example: Swiss Market Index (SMI) : 188 8 Models of VolatilityDocument3 pages8.4 Example: Swiss Market Index (SMI) : 188 8 Models of VolatilityNickesh ShahNo ratings yet
- Sample QuestionsDocument70 pagesSample QuestionsBushra MaryamNo ratings yet
- C11 Strategy DevelopmentDocument30 pagesC11 Strategy DevelopmentPARTI KEADILAN RAKYAT NIBONG TEBALNo ratings yet
- 2 Druid StreetDocument4 pages2 Druid StreetthamestunnelNo ratings yet
- Organic Chem Diels-Alder Reaction LabDocument9 pagesOrganic Chem Diels-Alder Reaction LabPryanka BalleyNo ratings yet
- Grace Lipsini1 2 3Document4 pagesGrace Lipsini1 2 3api-548923370No ratings yet
- Why Islam Is The True Religion in Light of The Quran and SunnahDocument7 pagesWhy Islam Is The True Religion in Light of The Quran and SunnahAsmau DaboNo ratings yet
- State of Education in Tibet 2003Document112 pagesState of Education in Tibet 2003Tibetan Centre for Human Rights and DemocracyNo ratings yet
- 2 5 Marking ScheduleDocument6 pages2 5 Marking Scheduleapi-218511741No ratings yet
- S06 - 1 THC560 DD311Document128 pagesS06 - 1 THC560 DD311Canchari Pariona Jhon AngelNo ratings yet
- Lesson 4Document13 pagesLesson 4Annie Mury SantiagoNo ratings yet
- Business StrategiesDocument2 pagesBusiness Strategiesthristanlexter694No ratings yet
- CP Mother's Day Lesson PlanDocument2 pagesCP Mother's Day Lesson PlanAma MiriNo ratings yet
- Organizational Behaviour Group Assignment-2Document4 pagesOrganizational Behaviour Group Assignment-2Prateek KurupNo ratings yet
- Final Annotated BibiliographyDocument4 pagesFinal Annotated Bibiliographyapi-491166748No ratings yet
- Interesting Facts (Compiled by Andrés Cordero 2023)Document127 pagesInteresting Facts (Compiled by Andrés Cordero 2023)AndresCorderoNo ratings yet
- CHEMICAL ANALYSIS OF WATER SAMPLEDocument5 pagesCHEMICAL ANALYSIS OF WATER SAMPLEAiron Fuentes EresNo ratings yet
- British Isles Composition GuideDocument4 pagesBritish Isles Composition GuidesonmatanalizNo ratings yet
- 16 Week Mountain Marathon Training Plan: WWW - Brutalevents.co - UkDocument2 pages16 Week Mountain Marathon Training Plan: WWW - Brutalevents.co - UkCristina CrsNo ratings yet
- Airs-Lms - Math-10 - q3 - Week 3-4 Module 3 Rhonavi MasangkayDocument19 pagesAirs-Lms - Math-10 - q3 - Week 3-4 Module 3 Rhonavi MasangkayRamil J. Merculio100% (1)
- Load Frequency Control of Hydro and Nuclear Power System by PI & GA ControllerDocument6 pagesLoad Frequency Control of Hydro and Nuclear Power System by PI & GA Controllerijsret100% (1)
- Admisibility To Object EvidenceDocument168 pagesAdmisibility To Object EvidenceAnonymous 4WA9UcnU2XNo ratings yet
- Marulaberry Kicad EbookDocument23 pagesMarulaberry Kicad EbookPhan HaNo ratings yet
- Siga-Cc1 12-22-2010Document6 pagesSiga-Cc1 12-22-2010Felipe LozanoNo ratings yet
- Building and Enhancing New Literacies Across The CurriculumDocument119 pagesBuilding and Enhancing New Literacies Across The CurriculumLowela Kasandra100% (3)
- Handbook of Zen, Mindfulness and Spiritual Health PDFDocument324 pagesHandbook of Zen, Mindfulness and Spiritual Health PDFMatthew Grayson100% (3)
- Agilent Cool On-Column Operation ManualDocument42 pagesAgilent Cool On-Column Operation Manualdmcevoy1965No ratings yet
- Fehniger Steve-Pump VibrationDocument35 pagesFehniger Steve-Pump VibrationSheikh Shoaib100% (1)
- Ahu, Chiller, Fcu Technical Bid TabulationDocument15 pagesAhu, Chiller, Fcu Technical Bid TabulationJohn Henry AsuncionNo ratings yet