Professional Documents
Culture Documents
Flow Diagram-Methodology V3.drawio
Uploaded by
GG GEOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Flow Diagram-Methodology V3.drawio
Uploaded by
GG GECopyright:
Available Formats
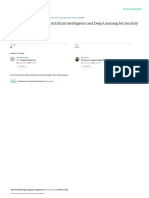
IoT Security 1. Knowledge Base Creation 2.
Deriving Security Rules
Standards
Extracting Security Elaborated Security Summarizing Extracting Values Deriving Security
Controls Standard Security Controls utilizing NER Rules
Annotating Data Labelled Corpus
Step: 1.1
NIST SP 800-53r5 Expert Inspection
Technical Building Structural Device 1
Specification Knowledge Device 2 Step 2.1 Deriving Security Rules
IoT Devices API Device 3
MUDGEE
Documentation Building Functional
Configuration Knowledge Instantiating Security Interpreting in
Device N
Rules Formal Language
Step: 1.2 Step: 2.2 Rules Instantiation
3. Application to IoT Security Auditing
Identifying Policy Collecting & Processing Converting into Formal Conducting Formal Generating Audit
Specific Data Sources run-time Data Language Verification Report
You might also like
- Flow Diagram-Methodology V3.drawioDocument1 pageFlow Diagram-Methodology V3.drawioGG GENo ratings yet
- 2022 Qatar CSF Mapping Guide - IDDocument27 pages2022 Qatar CSF Mapping Guide - IDAjmul IndiaNo ratings yet
- CSX Practitioner 1-IdentifyProtectDocument2 pagesCSX Practitioner 1-IdentifyProtectMithun LomateNo ratings yet
- Network Management in Organisations: Ethical Issues Associated With Various TechnologiesDocument5 pagesNetwork Management in Organisations: Ethical Issues Associated With Various TechnologiesOxford AssignmentNo ratings yet
- Isc-V1 2024Document310 pagesIsc-V1 2024Roshan SNo ratings yet
- 2024 Becker CPA Information Systems & Controls (ISC) NotesDocument43 pages2024 Becker CPA Information Systems & Controls (ISC) NotescraigsappletreeNo ratings yet
- Nozomi Networks Asset Intelligence Data SheetDocument4 pagesNozomi Networks Asset Intelligence Data SheetMauricio CalderónNo ratings yet
- Introduction To Iot and Its Security: Mr. Avinash KumarDocument42 pagesIntroduction To Iot and Its Security: Mr. Avinash KumarFiroz HussainNo ratings yet
- Keysight Network Packet Broker v5.3.0 CC Guide 1.0Document20 pagesKeysight Network Packet Broker v5.3.0 CC Guide 1.0Laurent SchirckNo ratings yet
- Network Access Control (NAC) Target Recommended SolutionDocument20 pagesNetwork Access Control (NAC) Target Recommended Solutiongeorges succar100% (1)
- NIS2 Versus ISO27001 - 2022 Versus CIS v8Document5 pagesNIS2 Versus ISO27001 - 2022 Versus CIS v8Vagabond PakistanNo ratings yet
- It Audit ChecklistDocument3 pagesIt Audit ChecklistSai DatlaNo ratings yet
- Cybersecurity Framework vPA 092813Document299 pagesCybersecurity Framework vPA 092813holamundo123No ratings yet
- Course of Study Application Development - Programmer (It-010-2) Module 1: Evaluate System SpecificationDocument5 pagesCourse of Study Application Development - Programmer (It-010-2) Module 1: Evaluate System SpecificationGevita GvNo ratings yet
- Miller AuditingDocument52 pagesMiller AuditingSyed NoumanNo ratings yet
- Nozomi Networks Guardian Data Sheet A4Document16 pagesNozomi Networks Guardian Data Sheet A4parpausNo ratings yet
- As 801 Fundamentals of DotNET Application SecurityDocument109 pagesAs 801 Fundamentals of DotNET Application SecurityAustin Louis AndradeNo ratings yet
- SEC502 IT Security Audit StandardDocument12 pagesSEC502 IT Security Audit StandardpmdrnoraNo ratings yet
- Internet of Things-Lecture 8: Dr. Rashmi SahayDocument6 pagesInternet of Things-Lecture 8: Dr. Rashmi SahaySONY DEEKSHITHANo ratings yet
- Add Structure and Credibility To Your Security Portfolio With CIS Controls v8 Cybersecurity FrameworkDocument55 pagesAdd Structure and Credibility To Your Security Portfolio With CIS Controls v8 Cybersecurity FrameworkLâm Hữu TiếnNo ratings yet
- Iot Security - Executing An Effective Security Testing ProcessDocument38 pagesIot Security - Executing An Effective Security Testing Processthato69No ratings yet
- IoT Sec 1.1 Fundamentals - IoT Security Final Exam AnswersDocument29 pagesIoT Sec 1.1 Fundamentals - IoT Security Final Exam AnswersRama IsveganNo ratings yet
- OPS239006 NCE-T Basic NE Configuration ISSUE19Document72 pagesOPS239006 NCE-T Basic NE Configuration ISSUE19randydooks100% (2)
- COCU 5 - Basic Data EntryDocument5 pagesCOCU 5 - Basic Data EntryMuhammad nazrien NizamNo ratings yet
- Cyber Vision - Knovledge Transfer v1.0Document45 pagesCyber Vision - Knovledge Transfer v1.0ranjeetNo ratings yet
- SANS ICS Assessment Quick Start Guide v1.2 09.30.21Document2 pagesSANS ICS Assessment Quick Start Guide v1.2 09.30.21Akhilesh SoniNo ratings yet
- Razberi Monitor™: Remote Monitoring and Management For Physical Security SystemsDocument2 pagesRazberi Monitor™: Remote Monitoring and Management For Physical Security SystemsLeonardo AravenaNo ratings yet
- Getting To Know Cisco DNA Center PDFDocument27 pagesGetting To Know Cisco DNA Center PDFdemouserNo ratings yet
- Getting To Know Cisco DNA Center PDFDocument27 pagesGetting To Know Cisco DNA Center PDFdemouserNo ratings yet
- Intel Secure Device Onboard Product Brief PDFDocument4 pagesIntel Secure Device Onboard Product Brief PDFsmithm007No ratings yet
- Guidelines For Application Security Management Design, Development, and TestingDocument16 pagesGuidelines For Application Security Management Design, Development, and TestingRamya LoganathanNo ratings yet
- Security Testing SDLC: Prepare The Organization (PO)Document5 pagesSecurity Testing SDLC: Prepare The Organization (PO)sin masterNo ratings yet
- Fortigate FirewallDocument4 pagesFortigate FirewallAnataTumongloNo ratings yet
- Exprivia Apulia IoT Security Cisco DR StangalinoDocument51 pagesExprivia Apulia IoT Security Cisco DR StangalinoFernando ArmendarizNo ratings yet
- Nozomi Networks Guardian Data SheetDocument16 pagesNozomi Networks Guardian Data SheetMunawar BhuttoNo ratings yet
- NIST Cybersecurity For IOTDocument30 pagesNIST Cybersecurity For IOTAice WareNo ratings yet
- 3.4.3 Manageble Network Plan FactsDocument2 pages3.4.3 Manageble Network Plan FactsleovaldanNo ratings yet
- 1 - Monitoring and Diagnosing Networks TerminologyDocument17 pages1 - Monitoring and Diagnosing Networks TerminologyAntonio SodréNo ratings yet
- Sebi3 PDFDocument5 pagesSebi3 PDFNAGARAJU MOTUPALLINo ratings yet
- Sebi1 PDFDocument5 pagesSebi1 PDFNAGARAJU MOTUPALLINo ratings yet
- Sebi2 PDFDocument5 pagesSebi2 PDFNAGARAJU MOTUPALLINo ratings yet
- In Ra Sebi Circular On Cyber Security Noexp1 PDFDocument5 pagesIn Ra Sebi Circular On Cyber Security Noexp1 PDFNAGARAJU MOTUPALLINo ratings yet
- Security Testing Services SciencesoftDocument17 pagesSecurity Testing Services SciencesoftWondachew WoldeyesusNo ratings yet
- Ise Device Compliance AagDocument2 pagesIse Device Compliance AagsiamuntulouisNo ratings yet
- 5 IOM - Idirect NMS Ibuilder Module, v6.0, 030106Document90 pages5 IOM - Idirect NMS Ibuilder Module, v6.0, 030106jangoNo ratings yet
- Chapter 4 Connectivity Power Management For IoT - ENDocument120 pagesChapter 4 Connectivity Power Management For IoT - ENNyamsuren PurevsurenNo ratings yet
- SOC FundamentalsDocument21 pagesSOC Fundamentalssiouxinfo100% (2)
- Nozomi Networks Smart Polling Data SheetDocument4 pagesNozomi Networks Smart Polling Data SheetFlávio Camilo CruzNo ratings yet
- Configuration Manager Microca: Operation ManualDocument18 pagesConfiguration Manager Microca: Operation ManualFabian Andres Diaz MalpikNo ratings yet
- CSS NC II Self CheckDocument8 pagesCSS NC II Self CheckJanice Conde PelaezNo ratings yet
- Creating A Portable Biometric Authentication DeviceDocument11 pagesCreating A Portable Biometric Authentication Devicenetra.r.tarteNo ratings yet
- Weapon Detection Using Artificial Intelligence and Deep Learning For Security ApplicationsDocument7 pagesWeapon Detection Using Artificial Intelligence and Deep Learning For Security ApplicationsKiran KumarNo ratings yet
- Chapter 4 - Audit in An Automated Environment by CA - Pankaj GargDocument4 pagesChapter 4 - Audit in An Automated Environment by CA - Pankaj GargAnjali P ANo ratings yet
- CCNA Security v2.0 Practice Skills Assesement Part 1 - Packet Tracer - Implementing Network SecurityDocument16 pagesCCNA Security v2.0 Practice Skills Assesement Part 1 - Packet Tracer - Implementing Network SecurityYuliani FitryNo ratings yet
- BalaBit Comply ISO 27011Document6 pagesBalaBit Comply ISO 27011ziaire.natanaelNo ratings yet
- Datasheet - Netwrix Auditor For Network DevicesDocument2 pagesDatasheet - Netwrix Auditor For Network Devicesolakunle abiodunNo ratings yet
- (PDF) Network Access Control Technology-Proposition To Contain New Security ChallengesDocument1 page(PDF) Network Access Control Technology-Proposition To Contain New Security Challengeskwame AyewNo ratings yet
- Reusable Verification Environment For Verification of Ethernet Packet in Ethernet IP Core, A Verification Strategy-An AnalysisDocument12 pagesReusable Verification Environment For Verification of Ethernet Packet in Ethernet IP Core, A Verification Strategy-An AnalysisNithin DevangNo ratings yet
- Implementing Database Security and AuditingFrom EverandImplementing Database Security and AuditingRating: 4.5 out of 5 stars4.5/5 (3)