0% found this document useful (0 votes)
281 views9 pagesOperating Systems Final Exam Guide
The document discusses several scenarios for establishing computer networks and systems and provides recommendations for each. For establishing connectivity between two computers, it recommends a peer-to-peer or small local area network. For utilizing physical data centers for daily operations, it recommends an enterprise data center with dedicated servers and storage. To interconnect multiple buildings for resource sharing, it suggests establishing a wide area network linking the buildings with local servers in each building.
Uploaded by
HarshCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
281 views9 pagesOperating Systems Final Exam Guide
The document discusses several scenarios for establishing computer networks and systems and provides recommendations for each. For establishing connectivity between two computers, it recommends a peer-to-peer or small local area network. For utilizing physical data centers for daily operations, it recommends an enterprise data center with dedicated servers and storage. To interconnect multiple buildings for resource sharing, it suggests establishing a wide area network linking the buildings with local servers in each building.
Uploaded by
HarshCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
- Scenario Setups: Provides recommended configurations for various operating system scenarios including network connectivity and resource interlinking.
- Question and Answer Section: Covers a series of true/false and multiple-choice questions related to operating system concepts and functionalities.
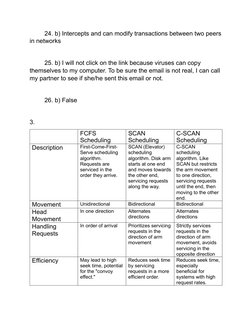
- Comparisons and Analysis: Provides comparative analyses of different scheduling methods used in operating systems.
- Security and Defense Enhancement: Outlines enhancements for security levels and methods to improve IT defense.
- Access Control Methods: Discusses different approaches to implementing access control within information systems, emphasizing the access matrix model.