Professional Documents
Culture Documents
ATARC AIDA Guidebook - FINAL e
Uploaded by
dfgluntOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
ATARC AIDA Guidebook - FINAL e
Uploaded by
dfgluntCopyright:
Available Formats
Artificial Intelligence and Data Analytics (AIDA) Guidebook
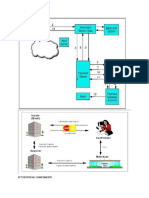
order to increase security of data transfer. This is particularly important when users transmit
sensitive data, such as by logging into a bank account, email service, or health insurance
provider. Any website, especially those that require login credentials, often uses HTTPS. A
primary use case of TLS is encrypting the communication between web applications and
servers, such as web browsers loading a website. TLS can also be used to encrypt other
communications such as email, messaging, and voice over IP (VoIP). FTPS is a secure file
transfer protocol that allows businesses to connect securely with their trading partners, users,
and customers. Sent files are exchanged through FTPS and authenticated by FTPS supported
applications such as client certificates and server identities.
When compared to the data in transit, data at rest is generally harder to access, which means
that oftentimes private information, such as health records, are stored this way. Making the
interception of this data more valuable to hackers and more consequential for victims of cyber-
attacks. Despite the greater security, there is still a risk of this data being intercepted by
hackers through cyber-attacks, potentially causing private information such as addresses and
financial records to be released, putting an individual’s safety at risk. Protecting all sensitive
data, whether in motion or at rest, is imperative for modern enterprises as attackers find
increasingly innovative ways to compromise systems and steal data.
If the data must be protected for many years, one should make sure that the encryption
scheme used is quantum-safe. Current publically available quantum computers are not
powerful enough to threaten current encryption methods. However, as quantum processors
advance, this could change. Most current public-key encryption methods (where different keys
are used for encryption and decryption) could be broken with a powerful enough quantum
computer. On the other hand, most current symmetric cryptographic algorithms (where the
encryption and decryption keys are the same) are not susceptible to quantum attacks,
assuming the keys are sufficiently long.11
For applications where confidentiality of the data in use is of utmost importance, additional
technologies could be used. When one wants to keep the data private even while it is being
processed, there are a number of technologies that can be employed independently or, in some
cases, even together. These include homomorphic encryption, differential privacy, federated
computing, and synthetic data. Homomorphic encryption is a technique that allows operations
to be performed on encrypted data without decrypting it.12 This permits the confidential
processing of data on a system that is untrusted. The results of the computation can only be
only decrypted with the original key. The biggest barrier to widespread use of homomorphic
encryption has been its poor performance. It is significantly slower than performing the
11
http://www.pqcrypto.org/www.springer.com/cda/content/document/cda_downloaddocument/9783540887010
-c1.pdf
12
See https://eprint.iacr.org/2015/1192 for an overview of homomorphic encryption and related technologies
Page 19
You might also like
- ATARC AIDA Guidebook - FINAL KDocument3 pagesATARC AIDA Guidebook - FINAL KdfgluntNo ratings yet
- New Frontiers in Cryptography: Quantum, Blockchain, Lightweight, Chaotic and DNAFrom EverandNew Frontiers in Cryptography: Quantum, Blockchain, Lightweight, Chaotic and DNANo ratings yet
- Cloud Cryptography and Data Security IJERTV10IS110100Document2 pagesCloud Cryptography and Data Security IJERTV10IS110100techieNo ratings yet
- A Definition of Data EncryptionDocument8 pagesA Definition of Data EncryptionSameen KhanNo ratings yet
- Cryptography Benefits & DrawbacksDocument2 pagesCryptography Benefits & Drawbackstracy keitaNo ratings yet
- What Are Data Encryption Solutions?Document4 pagesWhat Are Data Encryption Solutions?Shaban MahekulaNo ratings yet
- IT Security AssignmentDocument2 pagesIT Security Assignmentsimon sylvesterNo ratings yet
- Why Everyone Should Use Encryption Systems.: Technology of Information SecurityDocument4 pagesWhy Everyone Should Use Encryption Systems.: Technology of Information SecurityParamjit SinghNo ratings yet
- API Security: A guide to building and securing APIs from the developer team at OktaFrom EverandAPI Security: A guide to building and securing APIs from the developer team at OktaNo ratings yet
- Ist hw3Document3 pagesIst hw3Amaltas SinghNo ratings yet
- Security in e - CommerceDocument4 pagesSecurity in e - CommerceAlex T BinoyNo ratings yet
- Security TechnologiesDocument13 pagesSecurity TechnologiesAjay Krishna NNo ratings yet
- Question 4bDocument4 pagesQuestion 4bRamesh JiNo ratings yet
- Data Security Enhancement Using Number SystemDocument31 pagesData Security Enhancement Using Number Systemmarshal robertNo ratings yet
- Basics of Encryption andDocument4 pagesBasics of Encryption andShruti JainNo ratings yet
- Master of Business Administration-MBA Semester IV MI0026 Computer Networks - 2 Credits (Book ID: B1041) Assignment Set-1 (30 Marks)Document5 pagesMaster of Business Administration-MBA Semester IV MI0026 Computer Networks - 2 Credits (Book ID: B1041) Assignment Set-1 (30 Marks)Tenzin KunchokNo ratings yet
- 5 WpiDocument15 pages5 WpiDIAN SURGAWIWAHANo ratings yet
- Best Practices For Securing Your Enterprise:: 10 Things You Need To KnowDocument10 pagesBest Practices For Securing Your Enterprise:: 10 Things You Need To KnowShubham GuptaNo ratings yet
- Application Layer: Network SecurityDocument16 pagesApplication Layer: Network SecuritySunanda BansalNo ratings yet
- (IJCST-V5I2P61) :irene Getzi SDocument5 pages(IJCST-V5I2P61) :irene Getzi SEighthSenseGroupNo ratings yet
- "Palladium Cryptography": 1: AbstractDocument4 pages"Palladium Cryptography": 1: AbstractSandeep Singh RajawatNo ratings yet
- Document 4Document2 pagesDocument 4Last SummerNo ratings yet
- CryptographyDocument8 pagesCryptographySadia Islam ShefaNo ratings yet
- Final RSA DocumentationDocument125 pagesFinal RSA DocumentationKishore PinnintiNo ratings yet
- UntitledDocument13 pagesUntitledBhumika MhatreNo ratings yet
- EncryptionDocument14 pagesEncryptionSyeda Ashifa Ashrafi PapiaNo ratings yet
- Enabling Public Auditability For Cloud Data Storage SecurityDocument5 pagesEnabling Public Auditability For Cloud Data Storage SecurityRakeshconclaveNo ratings yet
- Ieee Research Papers On Cryptography and Network SecurityDocument5 pagesIeee Research Papers On Cryptography and Network Securityfvgxy2ha100% (1)
- IS AssignmentDocument24 pagesIS Assignmentyuvanpgr-wm20No ratings yet
- Confidentiality in CyberspaceDocument8 pagesConfidentiality in CyberspaceZakiyya RasheedNo ratings yet
- Net Zeros and Ones: How Data Erasure Promotes Sustainability, Privacy, and SecurityFrom EverandNet Zeros and Ones: How Data Erasure Promotes Sustainability, Privacy, and SecurityNo ratings yet
- Pros and Cons of Cryptography, Steganography and Perturbation TechniquesDocument6 pagesPros and Cons of Cryptography, Steganography and Perturbation Techniquesparitosh chandrakapureNo ratings yet
- Revolution of Computer Networks and Modern Computer NetworksDocument2 pagesRevolution of Computer Networks and Modern Computer NetworksAdithyaNo ratings yet
- Blockchain in Cyber Security: Blockchainexpert - UkDocument8 pagesBlockchain in Cyber Security: Blockchainexpert - UkSuganthi Ganesan GNo ratings yet
- Security in E-CommerceDocument29 pagesSecurity in E-CommerceAlex T BinoyNo ratings yet
- Data Protection and the Cloud: Are the risks too great?From EverandData Protection and the Cloud: Are the risks too great?Rating: 4 out of 5 stars4/5 (1)
- SSL Decryption - Uncovering The New Infrastructure Blind Spot - Gigamon WhitepaperDocument6 pagesSSL Decryption - Uncovering The New Infrastructure Blind Spot - Gigamon WhitepaperGigamonNo ratings yet
- Data Encryption Best Practices For Edge EnvironmentsDocument7 pagesData Encryption Best Practices For Edge Environmentspk bsdkNo ratings yet
- Card Payment Security Using RSADocument23 pagesCard Payment Security Using RSAKaataRanjithkumar100% (1)
- Card Payment Security Using RSADocument23 pagesCard Payment Security Using RSAKaataRanjithkumar100% (2)
- Embedded Systems Security: Practical Methods for Safe and Secure Software and Systems DevelopmentFrom EverandEmbedded Systems Security: Practical Methods for Safe and Secure Software and Systems DevelopmentRating: 4.5 out of 5 stars4.5/5 (2)
- Review On Credible Internet Sites Related To Security Issues - EditedDocument9 pagesReview On Credible Internet Sites Related To Security Issues - EditedAbednego AliiNo ratings yet
- Tresorit Encryption WhitepaperDocument6 pagesTresorit Encryption WhitepapereminentzNo ratings yet
- Using Public Key Cryptography in Mobile PhonesDocument9 pagesUsing Public Key Cryptography in Mobile PhonesAnkitaRawalNo ratings yet
- 6 Dr. Amit Sharma P61-66Document6 pages6 Dr. Amit Sharma P61-66amittechnosoftNo ratings yet
- Data Exfiltration During Ransomware AttacksDocument5 pagesData Exfiltration During Ransomware Attacksanthony jassoNo ratings yet
- Private Key Encryption: and Network SecurityDocument19 pagesPrivate Key Encryption: and Network SecurityAditya MathurNo ratings yet
- Ecure Client Server Message Integrity Verification Using Robust Encrypted TechniqueDocument5 pagesEcure Client Server Message Integrity Verification Using Robust Encrypted Techniquesurendiran123No ratings yet
- A Seminar ReportDocument39 pagesA Seminar ReportNutan BhorNo ratings yet
- Cryptography and Network Security 1Document11 pagesCryptography and Network Security 1Srini VasuluNo ratings yet
- LoRaWAN Crypto Chips v1 0Document13 pagesLoRaWAN Crypto Chips v1 0VaisakhMohanNo ratings yet
- Evaluation of The Role of Encryption Techniques in E CommerceDocument10 pagesEvaluation of The Role of Encryption Techniques in E CommerceLame Segokgo100% (2)
- Security: Table of ContentDocument5 pagesSecurity: Table of ContentMihir PatelNo ratings yet
- It SecurityDocument6 pagesIt Securitydhirender testNo ratings yet
- The Use of Elliptic Curves in Cryptography: Aster S Hesis in AthematicsDocument76 pagesThe Use of Elliptic Curves in Cryptography: Aster S Hesis in AthematicsTeodoraNo ratings yet
- Module 1eDocument14 pagesModule 1ezackaryaskingNo ratings yet
- BlueCoat Decrypting SSLDocument15 pagesBlueCoat Decrypting SSLRichardNo ratings yet
- Forum Systems: Presidio FTP Gateway For Managed File TransferDocument4 pagesForum Systems: Presidio FTP Gateway For Managed File TransferForum SystemsNo ratings yet
- What Is CryptographyDocument8 pagesWhat Is CryptographyahmadkamalNo ratings yet
- CloudComputing ResearchPaperDocument8 pagesCloudComputing ResearchPaperPrachi BansalNo ratings yet
- ATARC AIDA Guidebook - FINAL 96Document7 pagesATARC AIDA Guidebook - FINAL 96dfgluntNo ratings yet
- ATARC AIDA Guidebook - FINAL 92Document6 pagesATARC AIDA Guidebook - FINAL 92dfgluntNo ratings yet
- ATARC AIDA Guidebook - FINAL 99Document6 pagesATARC AIDA Guidebook - FINAL 99dfgluntNo ratings yet
- ATARC AIDA Guidebook - FINAL 76Document5 pagesATARC AIDA Guidebook - FINAL 76dfgluntNo ratings yet
- ATARC AIDA Guidebook - FINAL 83Document1 pageATARC AIDA Guidebook - FINAL 83dfgluntNo ratings yet
- ATARC AIDA Guidebook - FINAL 94Document8 pagesATARC AIDA Guidebook - FINAL 94dfgluntNo ratings yet
- ATARC AIDA Guidebook - FINAL 84Document1 pageATARC AIDA Guidebook - FINAL 84dfgluntNo ratings yet
- ATARC AIDA Guidebook - FINAL 65Document5 pagesATARC AIDA Guidebook - FINAL 65dfgluntNo ratings yet
- ATARC AIDA Guidebook - FINAL 74Document3 pagesATARC AIDA Guidebook - FINAL 74dfgluntNo ratings yet
- ATARC AIDA Guidebook - FINAL 72Document1 pageATARC AIDA Guidebook - FINAL 72dfgluntNo ratings yet
- ATARC AIDA Guidebook - FINAL 70Document1 pageATARC AIDA Guidebook - FINAL 70dfgluntNo ratings yet
- ATARC AIDA Guidebook - FINAL 77Document6 pagesATARC AIDA Guidebook - FINAL 77dfgluntNo ratings yet
- ATARC AIDA Guidebook - FINAL 62Document6 pagesATARC AIDA Guidebook - FINAL 62dfgluntNo ratings yet
- ATARC AIDA Guidebook - FINAL 58Document7 pagesATARC AIDA Guidebook - FINAL 58dfgluntNo ratings yet
- Artificial Intelligence - Using Artificial Intelligence To Advance The State of Multiple Industries-6Document2 pagesArtificial Intelligence - Using Artificial Intelligence To Advance The State of Multiple Industries-6dfgluntNo ratings yet
- Artificial Intelligence - Using Artificial Intelligence To Advance The State of Multiple Industries-1Document2 pagesArtificial Intelligence - Using Artificial Intelligence To Advance The State of Multiple Industries-1dfgluntNo ratings yet
- ATARC AIDA Guidebook - FINAL 45Document9 pagesATARC AIDA Guidebook - FINAL 45dfgluntNo ratings yet
- ATARC AIDA Guidebook - FINAL 60Document10 pagesATARC AIDA Guidebook - FINAL 60dfgluntNo ratings yet
- ATARC AIDA Guidebook - FINAL 37Document5 pagesATARC AIDA Guidebook - FINAL 37dfgluntNo ratings yet
- ATARC AIDA Guidebook - FINAL 40Document8 pagesATARC AIDA Guidebook - FINAL 40dfgluntNo ratings yet
- Tutorial Letter 203/0/2020: Information SecurityDocument10 pagesTutorial Letter 203/0/2020: Information SecurityEarnest KeteloNo ratings yet
- Lecture 9Document6 pagesLecture 9waleedNo ratings yet
- BE COMP - Block Chain TechnologyDocument1 pageBE COMP - Block Chain Technologyyash patilNo ratings yet
- Eras of CipherDocument47 pagesEras of CipherRhea Mae Simacio100% (1)
- Pseudo Random Bit GeneratorDocument54 pagesPseudo Random Bit Generatorsiddharth07334No ratings yet
- Cryptography: 11/16/2011 Indian Institute of Technology Delhi Donkeshwaram Harahari, Srishti BhaduriDocument48 pagesCryptography: 11/16/2011 Indian Institute of Technology Delhi Donkeshwaram Harahari, Srishti BhaduriHarahari DonkeshwaramNo ratings yet
- Creating RSA Keys Using OpenSSLDocument10 pagesCreating RSA Keys Using OpenSSLflorindoNo ratings yet
- Information and Network SecurityDocument36 pagesInformation and Network SecuritySarah Al-FayoumiNo ratings yet
- The Question Paper Contains 40 Multiple Choice Questions With Four Choices and Student Will Have To Pick The Correct One. (Each Carrying Marks.)Document6 pagesThe Question Paper Contains 40 Multiple Choice Questions With Four Choices and Student Will Have To Pick The Correct One. (Each Carrying Marks.)A.K. BNo ratings yet
- Bitcoin - CryptocurrencyDocument65 pagesBitcoin - CryptocurrencyrunnyNo ratings yet
- Rules Which Restrict Access Only To Those Who Need To KnowDocument10 pagesRules Which Restrict Access Only To Those Who Need To Knowclyde bautistaNo ratings yet
- Research Proposal On Vanet SecurityDocument6 pagesResearch Proposal On Vanet SecurityMd Habibur RahmanNo ratings yet
- Module 2 Chat LogDocument14 pagesModule 2 Chat Logkasun kalharaNo ratings yet
- An Implementation of WEP/WPA/WPA2 Password Cracking Using FluxionDocument16 pagesAn Implementation of WEP/WPA/WPA2 Password Cracking Using FluxionHoàng HảiNo ratings yet
- Exp Arif SirDocument5 pagesExp Arif Sirrafiqul.aiblNo ratings yet
- Image Masking and Compression Using User Private Key GenerationDocument5 pagesImage Masking and Compression Using User Private Key GenerationInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- CNS Module IIDocument111 pagesCNS Module IISashank ANo ratings yet
- SHA-512 Overall StructureDocument5 pagesSHA-512 Overall StructureRAMI RAMINo ratings yet
- Isc Chapter 5Document55 pagesIsc Chapter 5Cristina Joy CruzNo ratings yet
- Introduction To WPADocument3 pagesIntroduction To WPAshailesh_rathour07No ratings yet
- Transport Layer Security (TLS)Document14 pagesTransport Layer Security (TLS)svmc bcaNo ratings yet
- Cluster Based Data-Aggregation Using Lightweight CryptographicDocument8 pagesCluster Based Data-Aggregation Using Lightweight CryptographickeneneNo ratings yet
- Chapter 3: Block Ciphers and The Data Encryption Standard True or FalseDocument6 pagesChapter 3: Block Ciphers and The Data Encryption Standard True or FalseOmnia GalalNo ratings yet
- Uetion Descibe Toos: CybercaimeDocument3 pagesUetion Descibe Toos: CybercaimeDraxNo ratings yet
- Os Mini Project ReportDocument19 pagesOs Mini Project ReportCherry YNo ratings yet
- Crypto 2Document10 pagesCrypto 2John QuintalNo ratings yet
- Smime and PGPDocument19 pagesSmime and PGPAndik SyafruddinNo ratings yet
- Cyber Warfare Espionage by FlameDocument6 pagesCyber Warfare Espionage by FlameyoghavelNo ratings yet
- Cryptography & Digital Signature: by Sreekanth .A Mba IbDocument12 pagesCryptography & Digital Signature: by Sreekanth .A Mba Ibsreekanth3x108No ratings yet
- Try Hack MeDocument2 pagesTry Hack Mefuck youNo ratings yet