Professional Documents
Culture Documents
Self-Quiz Unit 4 Attempt Review Home3
Uploaded by
habupazelOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Self-Quiz Unit 4 Attempt Review Home3
Uploaded by
habupazelCopyright:
Available Formats
Wednesday, 28 February 2024, 8:24 AM
Finished
Wednesday, 28 February 2024, 8:24 AM
6 secs
out of 10.00 ( %)
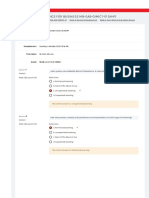
What kind of Access Control method can be used instead of RBAC without losing any functionality?
Not answered Select one:
Marked out of a. Mnemonic Access Control
1.00
b. Mannerism Access Control
c. Manifested Access Control
d. Mandatory Access Control
e. Maximal Access Control
Maximal Access Control
Your answer is incorrect.
The correct answer is: Mandatory Access Control
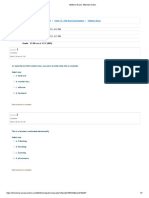
What is the function of access control?
Not answered Select one:
Marked out of a. It provides 100% database security.
1.00
b. It ensures an error-free data quality.
c. It controls the access of the database to the user.
d. It enables a regular backup of the database.
Your answer is incorrect.
The correct answer is: It controls the access of the database to the user.
If you wish to observe a database to ensure nothing strange happens with user access and the data,
what do you best do as a �rst step?
Not answered
Marked out of
Select one:
1.00
a. You shut down the database.
b. You delete the data.
c. You contact the users.
d. You run a database audit.
e. You do nothing.
Your answer is incorrect.
The correct answer is: You run a database audit.
What is achieved by restricting values of data and operations on data?
Not answered Select one:
Marked out of a. Identity Control
1.00
b. Integrity Control
c. Access Control
d. Performance Control
e. Control Logic
Your answer is incorrect.
The correct answer is: Integrity Control
What happens if you turn on Native Audit for databases?
Not answered Select one:
Marked out of a. Security may be reduced but performance is enhanced.
1.00
b. Performance may be reduced but security is enhanced.
c. Security and performance are both enhanced.
d. Security and performance are both reduced.
e. None of the above.
Your answer is incorrect.
The correct answer is: Performance may be reduced but security is enhanced.
In a three-tier application model, which level is responsible for authentication?
Not answered
Marked out of
Select one:
1.00
a. Web server
b. Application server
c. Database server
d. All of the above
e. None of the above
Your answer is incorrect.
The correct answer is: Application server
What is the meaning of the acronym LBAC?
Not answered Select one:
Marked out of a. Logic Based Access Control
1.00
b. Logic Bound Access Control
c. List Based Access Control
d. List Bound Access Control
e. Label Based Access Control
Your answer is incorrect.
The correct answer is: Label Based Access Control
LBAC means Label-based Access Control. Regarding databases, an additional and more recent
meaning of the same acronym has been established. What is it?
Not answered
Marked out of
Select one:
1.00
a. Least Bytes Access Control
b. Lossless Bias Access Control
c. Lattice-based Access Control
d. List-based Access Control
e. Least Bad Access Control
Your answer is incorrect.
The correct answer is: Lattice-based Access Control
What is LDAP?
Not answered Select one:
Marked out of a. Less Data with Active Problems
1.00
b. Little Density Accumulated Permutation
c. Lightweight Directory Access Protocol
d. Loss and Discovery Announcement Protocol
e. List Doctoring Allure Procedure
Your answer is incorrect.
The correct answer is: Lightweight Directory Access Protocol
What needs to happen as �rst step to connect to a database?
Not answered
Marked out of
Select one:
1.00
a. Automatization
b. Authentication
c. Authorization
d. Data Dumping
e. Enhancement
Your answer is incorrect.
The correct answer is: Authentication
You might also like
- Self-Quiz Unit 4 Attempt Review HomeDocument4 pagesSelf-Quiz Unit 4 Attempt Review HomehabupazelNo ratings yet
- Self-Quiz Unit 4 Attempt Review Home5Document4 pagesSelf-Quiz Unit 4 Attempt Review Home5habupazelNo ratings yet
- Self-Quiz Unit 4 Attempt Review Home2Document4 pagesSelf-Quiz Unit 4 Attempt Review Home2habupazelNo ratings yet
- Self-Quiz Unit 4 Attempt Review Home4Document4 pagesSelf-Quiz Unit 4 Attempt Review Home4habupazelNo ratings yet
- Key IIS Final VIP David Hai 1Document443 pagesKey IIS Final VIP David Hai 1Hi LightNo ratings yet
- Câu hỏiontapatttDocument117 pagesCâu hỏiontapatttnguyen toanNo ratings yet
- Model Exam 2 Click Here To Attempt - Attempt ReviewDocument51 pagesModel Exam 2 Click Here To Attempt - Attempt RevieworsangobirukNo ratings yet
- Quiz 1 - Attempt ReviewDocument7 pagesQuiz 1 - Attempt ReviewAditya SinghNo ratings yet
- Day 5 Quiz - Attempt ReviewDocument7 pagesDay 5 Quiz - Attempt ReviewĐỗ Đức AnhNo ratings yet
- Midterm Test 1 (Page 1 of 4)Document1 pageMidterm Test 1 (Page 1 of 4)nhox sokNo ratings yet
- UntitledDocument46 pagesUntitledNguyen Duc TaiNo ratings yet
- Prelim Exam - Attempt Review 2Document6 pagesPrelim Exam - Attempt Review 2Jomer LunarNo ratings yet
- CS6303 - Load Testing - Prelim Lab Quiz 1 - Attempt ReviewDocument3 pagesCS6303 - Load Testing - Prelim Lab Quiz 1 - Attempt ReviewLolita CrebilloNo ratings yet
- Day 4 Quiz - Attempt ReviewDocument8 pagesDay 4 Quiz - Attempt ReviewĐỗ Đức AnhNo ratings yet
- Artificial Intelligence MCQSDocument22 pagesArtificial Intelligence MCQSMUHAMMAD KHUBAIBNo ratings yet
- Review Quiz - Attempt Review-1Document12 pagesReview Quiz - Attempt Review-1Z MO4s ZNo ratings yet
- IT MTU Model ExamDocument181 pagesIT MTU Model Examaschalew tsehomeNo ratings yet
- Kuis - Pertemuan 1 - Attempt ReviewDocument6 pagesKuis - Pertemuan 1 - Attempt ReviewLukdalam 0No ratings yet
- Prelim Exam - Principles of Operating SystemDocument12 pagesPrelim Exam - Principles of Operating SystemYolanda RiguerNo ratings yet
- Network Security Prelim ExamDocument19 pagesNetwork Security Prelim ExamAlec BrentNo ratings yet
- (Update) Post Test Week 7 - Attempt ReviewDocument5 pages(Update) Post Test Week 7 - Attempt ReviewDita NoviyantiNo ratings yet
- UGRD-CS6306 Unified Functional TestingDocument71 pagesUGRD-CS6306 Unified Functional TestingApril John BurgosNo ratings yet
- Information Assurance and Security 1 MIdtermDocument23 pagesInformation Assurance and Security 1 MIdtermjusipragasNo ratings yet
- Oed 2,0 2022Document139 pagesOed 2,0 2022Ellish ErisNo ratings yet
- Self-Quiz Unit 3 - Attempt Review5Document6 pagesSelf-Quiz Unit 3 - Attempt Review5Reem Reem (Reem Castro)No ratings yet
- Database MGT System Prelim ExamDocument12 pagesDatabase MGT System Prelim Examjulius obregonNo ratings yet
- Final Exam - Attempt Review IntegDocument25 pagesFinal Exam - Attempt Review IntegTon LazaroNo ratings yet
- Midterm Lab Exam - Principles of OSDocument10 pagesMidterm Lab Exam - Principles of OSYolanda RiguerNo ratings yet
- Self-Quiz Unit 3 - Attempt Review4Document6 pagesSelf-Quiz Unit 3 - Attempt Review4Reem Reem (Reem Castro)No ratings yet
- Prelim Exam - Attempt Review 1Document6 pagesPrelim Exam - Attempt Review 1Jomer LunarNo ratings yet
- SE Quiz 3 - Attempt ReviewDocument5 pagesSE Quiz 3 - Attempt ReviewHansu MalviyaNo ratings yet
- Dashboard Software Engineering Concepts Software Maintenance Pre-QuizDocument2 pagesDashboard Software Engineering Concepts Software Maintenance Pre-QuizPrakash Hegde67% (3)
- Artificial Intelligence For Business Mb-Gab-Oimict-01 (Ahp) : The Correct Answer Is: Free From ErrorsDocument8 pagesArtificial Intelligence For Business Mb-Gab-Oimict-01 (Ahp) : The Correct Answer Is: Free From ErrorsZaenal HediansahNo ratings yet
- اسئلة ميدتيرم مادة اساسيات الامن السيبرانيDocument8 pagesاسئلة ميدتيرم مادة اساسيات الامن السيبرانيjfaa5lanNo ratings yet
- Prelim Lab Exam - Attempt Review 1Document5 pagesPrelim Lab Exam - Attempt Review 1Jomer LunarNo ratings yet
- Artificial Intelligence For Business Mb-Gab-Oimict-01 (Ahp) : Started On Tuesday, 5 October 2021, 12:00 PMDocument5 pagesArtificial Intelligence For Business Mb-Gab-Oimict-01 (Ahp) : Started On Tuesday, 5 October 2021, 12:00 PMZaenal HediansahNo ratings yet
- Network Security Source 4Document7 pagesNetwork Security Source 4John Llucastre CortezNo ratings yet
- 1st Quarter Exam PROG3112Document10 pages1st Quarter Exam PROG3112Jonathan23d100% (4)
- Thuong mai dien tu - Nhom 05: Câu hỏiDocument16 pagesThuong mai dien tu - Nhom 05: Câu hỏiĐức Hữu100% (1)
- Quiz 001 - Attempt Review PDFDocument6 pagesQuiz 001 - Attempt Review PDFPeter Eclevia100% (1)
- Database Mid ExamDocument26 pagesDatabase Mid ExamGian Sonny ObraNo ratings yet
- 3RD YEAR Network SecurityDocument53 pages3RD YEAR Network SecurityMelanie BuñalesNo ratings yet
- Midterm Test 1 - Attempt Review (Page 1 of 4)Document1 pageMidterm Test 1 - Attempt Review (Page 1 of 4)nhox sokNo ratings yet
- Kuis 01 - Attempt ReviewDocument10 pagesKuis 01 - Attempt ReviewAdinda MaharaniNo ratings yet
- IT Application Tools in Business Prelim Qiuz 2.2Document4 pagesIT Application Tools in Business Prelim Qiuz 2.2lj parrenoNo ratings yet
- Final Lab Exam - UGRD-IT6201C Principles of Operating SystemsDocument30 pagesFinal Lab Exam - UGRD-IT6201C Principles of Operating Systemsyhu FULNo ratings yet
- Artificial Intelligence McqsDocument173 pagesArtificial Intelligence McqsMUHAMMAD KHUBAIBNo ratings yet
- IT Application Tools in Business Prelim Qiuz 2.1Document4 pagesIT Application Tools in Business Prelim Qiuz 2.1lj parrenoNo ratings yet
- Quiz 4 - Attempt ReviewDocument5 pagesQuiz 4 - Attempt ReviewHansu MalviyaNo ratings yet
- Software Engineering 1 Prelim ExamDocument31 pagesSoftware Engineering 1 Prelim ExamAlec BrentNo ratings yet
- Finals Exam System IntegDocument28 pagesFinals Exam System IntegMark RosellNo ratings yet
- MidtermDocument31 pagesMidtermLiliam LuqueNo ratings yet
- Midterm Exam - Attempt Review CS6303Document7 pagesMidterm Exam - Attempt Review CS6303Ton LazaroNo ratings yet
- PEXAM Network Security - Attempt Review25-30Document6 pagesPEXAM Network Security - Attempt Review25-30mark gonzalesNo ratings yet
- Network Security MidtermDocument21 pagesNetwork Security Midtermarriesgadoicerry09172002No ratings yet
- Principles of Operating Systems Prelim LabDocument85 pagesPrinciples of Operating Systems Prelim Labdarwin armadoNo ratings yet
- CS6306-Prelim Exam - Attempt ReviewDocument20 pagesCS6306-Prelim Exam - Attempt ReviewHarvey MendozaNo ratings yet
- CISA Exam-Testing Concept-Knowledge of Logical Access ControlFrom EverandCISA Exam-Testing Concept-Knowledge of Logical Access ControlRating: 2.5 out of 5 stars2.5/5 (3)
- ISTQB Certified Tester Foundation Level Practice Exam QuestionsFrom EverandISTQB Certified Tester Foundation Level Practice Exam QuestionsRating: 5 out of 5 stars5/5 (1)
- Recommendation: Mix of BothDocument50 pagesRecommendation: Mix of Boththrowaway boiClaartiNo ratings yet
- MB 300Document12 pagesMB 300nikhil aroraNo ratings yet
- Hotel Management SystemDocument7 pagesHotel Management SystemManogya ChordiaNo ratings yet
- Visual Studio - Why Am I Getting - Cannot Connect To Server - A Network-Related or Instance-Specific Error - Stack OverflowDocument25 pagesVisual Studio - Why Am I Getting - Cannot Connect To Server - A Network-Related or Instance-Specific Error - Stack OverflowSuribabu VNo ratings yet
- Paper 14Document8 pagesPaper 14Daniel G Canton PuertoNo ratings yet
- IBM Data Science CapstoneDocument51 pagesIBM Data Science CapstonePeter Quoc88% (8)
- Dbms Session 2&3Document13 pagesDbms Session 2&3medhanshpro80No ratings yet
- Note On Data AnalyticsDocument21 pagesNote On Data AnalyticsLOOPY GAMINGNo ratings yet
- MLP Project - VarunDocument6 pagesMLP Project - VarunTangirala Ashwini100% (1)
- openSAP dsp1 Week 1 Unit 4 Joins PresentationDocument14 pagesopenSAP dsp1 Week 1 Unit 4 Joins Presentationfinance.panda.reportsNo ratings yet
- FAQ: SAP HANA Lock Analysis: SymptomDocument118 pagesFAQ: SAP HANA Lock Analysis: SymptomMaciel VierNo ratings yet
- Customer Presentation - Steelcentral Appresponse11Document39 pagesCustomer Presentation - Steelcentral Appresponse11AhmedNo ratings yet
- Product Opentext ResumeDocument2 pagesProduct Opentext ResumeVincenzo AngeliniNo ratings yet
- SAP HANA ODBC Connection Test Fails With (SAP AG) (LIBODBCHDB SO) (HDBODBC) General Error 10 Authentication Failed Error MessageDocument2 pagesSAP HANA ODBC Connection Test Fails With (SAP AG) (LIBODBCHDB SO) (HDBODBC) General Error 10 Authentication Failed Error Messagesanjubr21088No ratings yet
- Templates - YAGPDBDocument37 pagesTemplates - YAGPDBColin 8986No ratings yet
- Elasticsearch Quick Start: An Introduction To Elasticsearch in Tutorial FormDocument21 pagesElasticsearch Quick Start: An Introduction To Elasticsearch in Tutorial FormVinod KapoorNo ratings yet
- A Project Monitoring System Involves DeterminingDocument26 pagesA Project Monitoring System Involves DeterminingNayeem PashaNo ratings yet
- Meera Mainframe ResumeDocument3 pagesMeera Mainframe Resumemeeramf69No ratings yet
- IT326 - Ch1Document17 pagesIT326 - Ch1عبده شعوا100% (1)
- Name: Joseph Ascione Date: 4/10/2018: MET CS 669 Database Design and Implementation For Business Lab 4 SubmissionDocument21 pagesName: Joseph Ascione Date: 4/10/2018: MET CS 669 Database Design and Implementation For Business Lab 4 SubmissionIsrar AhmadNo ratings yet
- SAP ASE System Administration Guide Volume 1 enDocument156 pagesSAP ASE System Administration Guide Volume 1 enAmerica MedinaNo ratings yet
- Semester VIIDocument8 pagesSemester VIIsohaibchNo ratings yet
- Assignment 1 Se PDF CuszDocument20 pagesAssignment 1 Se PDF CuszBLACK WOLFNo ratings yet
- Dbms FinalDocument25 pagesDbms FinalSunny VarshneyNo ratings yet
- EBPro Manual All in One PDFDocument1,020 pagesEBPro Manual All in One PDFАлексейNo ratings yet
- Textbook Ebook Multivariate Data Analysis 8Th Edition Edition Joseph F Hair All Chapter PDFDocument43 pagesTextbook Ebook Multivariate Data Analysis 8Th Edition Edition Joseph F Hair All Chapter PDFkenna.lackey995100% (13)
- Chapter 1 - Intro To Data ScienceDocument24 pagesChapter 1 - Intro To Data ScienceDr. Sanjay GuptaNo ratings yet
- Learning AIDocument27 pagesLearning AIShankerNo ratings yet
- DB2 12 For z/OS Technical Overview - IBM ITSO Redbooks - 2016-12Document300 pagesDB2 12 For z/OS Technical Overview - IBM ITSO Redbooks - 2016-12Nicholas VanHaiVuNo ratings yet
- Part - A: Database Management System LabDocument26 pagesPart - A: Database Management System LabDevonne BestNo ratings yet