Professional Documents
Culture Documents
Self-Quiz Unit 4 Attempt Review Home5
Uploaded by
habupazelOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Self-Quiz Unit 4 Attempt Review Home5
Uploaded by
habupazelCopyright:
Available Formats
Wednesday, 28 February 2024, 8:24 AM
Finished
Wednesday, 28 February 2024, 8:24 AM
7 secs
out of 10.00 ( %)
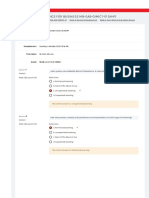
What happens if you turn on Native Audit for databases?
Not answered Select one:
Marked out of a. Security may be reduced but performance is enhanced.
1.00
b. Performance may be reduced but security is enhanced.
c. Security and performance are both enhanced.
d. Security and performance are both reduced.
e. None of the above.
Your answer is incorrect.
The correct answer is: Performance may be reduced but security is enhanced.
In a three-tier application model, which level is responsible for authentication?
Not answered
Marked out of
Select one:
1.00
a. Web server
b. Application server
c. Database server
d. All of the above
e. None of the above
Your answer is incorrect.
The correct answer is: Application server
What do you need to do the following operation: create database.
Not answered Select one:
Marked out of a. Object Privileges
1.00
b. Data Privileges
c. System Privileges
d. Subject Privileges
e. Phantom Privileges
Your answer is incorrect.
The correct answer is: System Privileges
What are the three primary rules for RBAC?
Not answered Select one:
Marked out of a. Role assignment, role authorization, permission authorization
1.00
b. Role assignment, role authentication, permission assignment
c. Role authorization, database authorization, permission authorization
d. Role assignment, role revocation, permission recovery
e. Role auditing, data prioritization, permission prioritization
Your answer is incorrect.
The correct answer is: Role assignment, role authorization, permission authorization
What kind of Access Control method can be used instead of RBAC without losing any functionality?
Not answered Select one:
Marked out of a. Mnemonic Access Control
1.00
b. Mannerism Access Control
c. Manifested Access Control
d. Mandatory Access Control
e. Maximal Access Control
Maximal Access Control
Your answer is incorrect.
The correct answer is: Mandatory Access Control
What needs to be done with respect to personnel getting access to the database
Not answered Select one:
Marked out of a. Performance monitoring
1.00
b. Privacy and Protection
c. Data integrity routines
d. Authorization and Authentication
e. Data Normalization
Your answer is incorrect.
The correct answer is: Authorization and Authentication
What needs to happen as �rst step to connect to a database?
Not answered
Marked out of
Select one:
1.00
a. Automatization
b. Authentication
c. Authorization
d. Data Dumping
e. Enhancement
Your answer is incorrect.
The correct answer is: Authentication
When speaking of Role-based Access Control, which Acronym is typically used?
Not answered
Marked out of
Select one:
1.00
a. ROBAC
b. ROLAC
c. RBAC
d. ROLBAC
Your answer is incorrect.
The correct answer is: RBAC
What is the most important thing necessary for a successful disaster recovery (with respect to
databases).
Not answered
Marked out of
Select one:
1.00
a. Insurance
b. Manpower
c. Emergency power for Electricity
d. Oxygen Supply
e. Backup
Your answer is incorrect.
The correct answer is: Backup
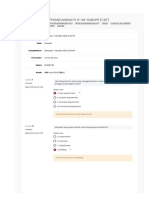
What is the meaning of the acronym LBAC?
Not answered Select one:
Marked out of a. Logic Based Access Control
1.00
b. Logic Bound Access Control
c. List Based Access Control
d. List Bound Access Control
e. Label Based Access Control
Your answer is incorrect.
The correct answer is: Label Based Access Control
You might also like
- Pedia Idiot NotesDocument18 pagesPedia Idiot Noteswiljamesclim100% (8)
- DP 900 TestPrep - CloudthatDocument13 pagesDP 900 TestPrep - CloudthatIct lab67% (3)
- Walking The Talk Duponts Untold Safety FailuresDocument28 pagesWalking The Talk Duponts Untold Safety Failuressl1828No ratings yet
- Dashboard Software Engineering Concepts Software Maintenance Pre-QuizDocument2 pagesDashboard Software Engineering Concepts Software Maintenance Pre-QuizPrakash Hegde67% (3)
- NCD Proof PDFDocument2 pagesNCD Proof PDFAnonymous TDzUwCg67% (3)
- Facility Management Plan (FMP) Facilities Health, Safety & Environmental (Hse) ManagementDocument35 pagesFacility Management Plan (FMP) Facilities Health, Safety & Environmental (Hse) ManagementAhmad Saiful Ridzwan Jaharuddin100% (2)
- CIVREV!!!!Document5 pagesCIVREV!!!!aypod100% (1)
- UGRD-CS6306 Unified Functional TestingDocument71 pagesUGRD-CS6306 Unified Functional TestingApril John BurgosNo ratings yet
- NCM 113 Course OutlineDocument3 pagesNCM 113 Course OutlineJennifer Solano Cruel100% (2)
- MFD Part2 Pastpapers According To SubjectsDocument255 pagesMFD Part2 Pastpapers According To SubjectsEnea Nastri100% (3)
- Self-Quiz Unit 4 Attempt Review HomeDocument4 pagesSelf-Quiz Unit 4 Attempt Review HomehabupazelNo ratings yet
- Self-Quiz Unit 4 Attempt Review Home3Document4 pagesSelf-Quiz Unit 4 Attempt Review Home3habupazelNo ratings yet
- Self-Quiz Unit 4 Attempt Review Home4Document4 pagesSelf-Quiz Unit 4 Attempt Review Home4habupazelNo ratings yet
- Self-Quiz Unit 4 Attempt Review Home2Document4 pagesSelf-Quiz Unit 4 Attempt Review Home2habupazelNo ratings yet
- Key IIS Final VIP David Hai 1Document443 pagesKey IIS Final VIP David Hai 1Hi LightNo ratings yet
- Câu hỏiontapatttDocument117 pagesCâu hỏiontapatttnguyen toanNo ratings yet
- Day 5 Quiz - Attempt ReviewDocument7 pagesDay 5 Quiz - Attempt ReviewĐỗ Đức AnhNo ratings yet
- Prelim Exam - Attempt Review 2Document6 pagesPrelim Exam - Attempt Review 2Jomer LunarNo ratings yet
- (Update) Post Test Week 7 - Attempt ReviewDocument5 pages(Update) Post Test Week 7 - Attempt ReviewDita NoviyantiNo ratings yet
- UntitledDocument46 pagesUntitledNguyen Duc TaiNo ratings yet
- Quiz 1 - Attempt ReviewDocument7 pagesQuiz 1 - Attempt ReviewAditya SinghNo ratings yet
- Model Exam 2 Click Here To Attempt - Attempt ReviewDocument51 pagesModel Exam 2 Click Here To Attempt - Attempt RevieworsangobirukNo ratings yet
- Artificial Intelligence MCQSDocument22 pagesArtificial Intelligence MCQSMUHAMMAD KHUBAIBNo ratings yet
- Prelim Exam - Principles of Operating SystemDocument12 pagesPrelim Exam - Principles of Operating SystemYolanda RiguerNo ratings yet
- IT MTU Model ExamDocument181 pagesIT MTU Model Examaschalew tsehomeNo ratings yet
- Day 4 Quiz - Attempt ReviewDocument8 pagesDay 4 Quiz - Attempt ReviewĐỗ Đức AnhNo ratings yet
- Database MGT System Prelim ExamDocument12 pagesDatabase MGT System Prelim Examjulius obregonNo ratings yet
- CS6303 - Load Testing - Prelim Lab Quiz 1 - Attempt ReviewDocument3 pagesCS6303 - Load Testing - Prelim Lab Quiz 1 - Attempt ReviewLolita CrebilloNo ratings yet
- Kuis - Pertemuan 1 - Attempt ReviewDocument6 pagesKuis - Pertemuan 1 - Attempt ReviewLukdalam 0No ratings yet
- Review Quiz - Attempt Review-1Document12 pagesReview Quiz - Attempt Review-1Z MO4s ZNo ratings yet
- Quiz 001 - Attempt Review PDFDocument6 pagesQuiz 001 - Attempt Review PDFPeter Eclevia100% (1)
- SE Quiz 3 - Attempt ReviewDocument5 pagesSE Quiz 3 - Attempt ReviewHansu MalviyaNo ratings yet
- Prelim Lab Exam - Attempt Review 1Document5 pagesPrelim Lab Exam - Attempt Review 1Jomer LunarNo ratings yet
- Quiz 001 Software Engineering 1 PDFDocument6 pagesQuiz 001 Software Engineering 1 PDFPeter EcleviaNo ratings yet
- Midterm Test 1 (Page 1 of 4)Document1 pageMidterm Test 1 (Page 1 of 4)nhox sokNo ratings yet
- Pre Test 1 - Attempt ReviewDocument4 pagesPre Test 1 - Attempt ReviewNovia PutriNo ratings yet
- Artificial Intelligence For Business Mb-Gab-Oimict-01 (Ahp) : Started On Tuesday, 5 October 2021, 12:00 PMDocument5 pagesArtificial Intelligence For Business Mb-Gab-Oimict-01 (Ahp) : Started On Tuesday, 5 October 2021, 12:00 PMZaenal HediansahNo ratings yet
- Artificial Intelligence For Business Mb-Gab-Oimict-01 (Ahp) : The Correct Answer Is: Free From ErrorsDocument8 pagesArtificial Intelligence For Business Mb-Gab-Oimict-01 (Ahp) : The Correct Answer Is: Free From ErrorsZaenal HediansahNo ratings yet
- Kuis 01 - Attempt ReviewDocument10 pagesKuis 01 - Attempt ReviewAdinda MaharaniNo ratings yet
- Information Assurance and Security 1 MIdtermDocument23 pagesInformation Assurance and Security 1 MIdtermjusipragasNo ratings yet
- Prelim Exam - Attempt Review 1Document6 pagesPrelim Exam - Attempt Review 1Jomer LunarNo ratings yet
- IT Application Tools in Business Prelim Qiuz 2.2Document4 pagesIT Application Tools in Business Prelim Qiuz 2.2lj parrenoNo ratings yet
- F1 System IntegDocument7 pagesF1 System IntegJohn Kelly BarrogoNo ratings yet
- Artificial Intelligence McqsDocument173 pagesArtificial Intelligence McqsMUHAMMAD KHUBAIBNo ratings yet
- 2-3system Integ Prelim Quiz 2 and Exam 47 Score PDFDocument13 pages2-3system Integ Prelim Quiz 2 and Exam 47 Score PDFNicoco LocoNo ratings yet
- Quiz 1 Ais 2 - Group Ac 20 & 40Document7 pagesQuiz 1 Ais 2 - Group Ac 20 & 40Good PersonNo ratings yet
- Final Lab Exam - UGRD-IT6201C Principles of Operating SystemsDocument30 pagesFinal Lab Exam - UGRD-IT6201C Principles of Operating Systemsyhu FULNo ratings yet
- Final Exam - Attempt Review IntegDocument25 pagesFinal Exam - Attempt Review IntegTon LazaroNo ratings yet
- c12 Quiz - Attempt ReviewDocument4 pagesc12 Quiz - Attempt ReviewTestya RamadhinNo ratings yet
- Self-Quiz Unit 3 - Attempt Review5Document6 pagesSelf-Quiz Unit 3 - Attempt Review5Reem Reem (Reem Castro)No ratings yet
- Quizz DBiDocument9 pagesQuizz DBiDuyệt NguyễnNo ratings yet
- Quiz 4 - Attempt ReviewDocument5 pagesQuiz 4 - Attempt ReviewHansu MalviyaNo ratings yet
- Midterm Exam - Attempt Review CS6303Document7 pagesMidterm Exam - Attempt Review CS6303Ton LazaroNo ratings yet
- QUIZ #3 - Attempt Review2Document5 pagesQUIZ #3 - Attempt Review2m.amerhadafiNo ratings yet
- Application Development and Emerging Technologies PrelimDocument9 pagesApplication Development and Emerging Technologies PrelimretiredxajiNo ratings yet
- Progress Test 2 - Attempt ReviewDocument23 pagesProgress Test 2 - Attempt ReviewVĩnh TrungNo ratings yet
- UGRD-ITE6300 Cloud Computing and Internet of ThingsDocument17 pagesUGRD-ITE6300 Cloud Computing and Internet of ThingsJuan miguel Sta CruzNo ratings yet
- Database Mid ExamDocument26 pagesDatabase Mid ExamGian Sonny ObraNo ratings yet
- Senior - DT - Quiz 2Document4 pagesSenior - DT - Quiz 2Amlan GainNo ratings yet
- 3RD YEAR Network SecurityDocument53 pages3RD YEAR Network SecurityMelanie BuñalesNo ratings yet
- Mis Final Exam (None Exam Center) - Attempt ReviewDocument15 pagesMis Final Exam (None Exam Center) - Attempt ReviewYe Ab FekaduNo ratings yet
- Pre Test - Attempt ReviewDocument12 pagesPre Test - Attempt ReviewKetut Vera Budi LesmanaNo ratings yet
- Review Quiz - Attempt Review3Document11 pagesReview Quiz - Attempt Review3Z MO4s ZNo ratings yet
- QUIZ #3 - Attempt ReviewDocument5 pagesQUIZ #3 - Attempt Reviewm.amerhadafiNo ratings yet
- Blue Prism Professional Developer Certification Case Based Practice Questions - Latest Edition 2023From EverandBlue Prism Professional Developer Certification Case Based Practice Questions - Latest Edition 2023No ratings yet
- Starters: Please Ask Our Waiting Staff For Our Today'S Special MenuDocument2 pagesStarters: Please Ask Our Waiting Staff For Our Today'S Special MenuAdrian HartantoNo ratings yet
- Service: ManualDocument103 pagesService: ManualSaulvcr64 PorleyNo ratings yet
- Cylinder Head, Pressure Test (First), D7CDocument4 pagesCylinder Head, Pressure Test (First), D7CAl BimaNo ratings yet
- Group - 6 Positive PhychologyDocument57 pagesGroup - 6 Positive PhychologyIamLNo ratings yet
- NTE123AP Silicon NPN Transistor Audio Amplifier, Switch (Compl To NTE159)Document3 pagesNTE123AP Silicon NPN Transistor Audio Amplifier, Switch (Compl To NTE159)Didier DoradoNo ratings yet
- For Each Animal, Circle Left or Right For The Direction It Is FacingDocument1 pageFor Each Animal, Circle Left or Right For The Direction It Is FacingMaria PahomeNo ratings yet
- Energy Changes OL NotesDocument4 pagesEnergy Changes OL NotesHooria AminNo ratings yet
- Stuffed PeppersDocument2 pagesStuffed PeppersDewayne AginNo ratings yet
- Itc Maurya: (Luxury Hotel Collection)Document31 pagesItc Maurya: (Luxury Hotel Collection)Gopi KrishnaNo ratings yet
- Anatomi BBB: Hilmi Adyatma 1710211069Document13 pagesAnatomi BBB: Hilmi Adyatma 1710211069Hilmi AdyatmaNo ratings yet
- Zimwnt-Ufc01 - WNTP236 - 4097 - 001 (00000002) PDFDocument71 pagesZimwnt-Ufc01 - WNTP236 - 4097 - 001 (00000002) PDFNatasa RalicNo ratings yet
- Land Surface Temp and Disease - PPTDocument28 pagesLand Surface Temp and Disease - PPTGOSPEL FACTORYNo ratings yet
- Declaration: Document Updated 9 June 2011Document16 pagesDeclaration: Document Updated 9 June 2011Pippa McFallNo ratings yet
- BASF Rheology Modifiers Product Recomendation (AP)Document1 pageBASF Rheology Modifiers Product Recomendation (AP)nastitimustika100% (1)
- Amber Brochure 9 Apr 2021Document2 pagesAmber Brochure 9 Apr 2021Lalet BistNo ratings yet
- Xyr 5000 Wt530Document9 pagesXyr 5000 Wt530murali52100% (1)
- The Persons With Disabilities 1995Document27 pagesThe Persons With Disabilities 1995siva ramanNo ratings yet
- Mineral Resources and Food ResourcesDocument31 pagesMineral Resources and Food Resourcesvaishali TMU studentNo ratings yet
- Case Study Strategic Nurul Syahira Binti Johari (H19a0721)Document7 pagesCase Study Strategic Nurul Syahira Binti Johari (H19a0721)Nurul SyahiraNo ratings yet
- GeoCon DavaodelEq Jsperez 02dec2020Document22 pagesGeoCon DavaodelEq Jsperez 02dec2020Kym Buena-RegadoNo ratings yet
- LD Flow ChartDocument1 pageLD Flow Chartapi-222173654No ratings yet
- Pre Ut U11sDocument2 pagesPre Ut U11sSvetlanaNo ratings yet
- Freeman Aortic RegurgitationDocument102 pagesFreeman Aortic RegurgitationJose Ignacio Tarton SisimitNo ratings yet