0% found this document useful (0 votes)
443 views20 pagesBluejacking (PP, P4)
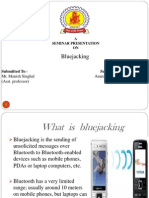
Bluejacking involves sending unsolicited messages to Bluetooth-enabled devices. It exploits the Bluetooth feature that allows discovery and connection between devices within range of each other. Bluejacking originated after an IT consultant named Ajack demonstrated sending messages to Ericsson cellphones. It uses Bluetooth technology, vCards to send messages, and the OBEX protocol. The document discusses the process, software tools, usage scenarios, merits and demerits of bluejacking.
Uploaded by
Harshada KoliCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PPTX, PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
443 views20 pagesBluejacking (PP, P4)
Bluejacking involves sending unsolicited messages to Bluetooth-enabled devices. It exploits the Bluetooth feature that allows discovery and connection between devices within range of each other. Bluejacking originated after an IT consultant named Ajack demonstrated sending messages to Ericsson cellphones. It uses Bluetooth technology, vCards to send messages, and the OBEX protocol. The document discusses the process, software tools, usage scenarios, merits and demerits of bluejacking.
Uploaded by
Harshada KoliCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PPTX, PDF, TXT or read online on Scribd
- What is Bluejacking Technology?
- Origin of Bluejacking
- Technology Used
- Requirements
- Architecture of Bluejacking
- Process of Bluejacking
- Software Tools for Bluejacking
- Usage
- Merits & Demerits
- Related Concepts
- Code of Ethics
- Future Aspects
- Conclusion
- Thank You