Professional Documents
Culture Documents
Media Access Control
Uploaded by
Aryan Rathore0 ratings0% found this document useful (0 votes)
18 views34 pagesOriginal Title
Media_Access_Control
Copyright
© © All Rights Reserved
Available Formats
PPT, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
© All Rights Reserved
Available Formats
Download as PPT, PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
18 views34 pagesMedia Access Control
Uploaded by
Aryan RathoreCopyright:
© All Rights Reserved
Available Formats
Download as PPT, PDF, TXT or read online from Scribd
You are on page 1of 34
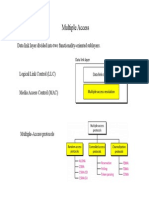
Multiple Access
McGraw-Hill ©The McGraw-Hill Companies, Inc., 2000
Data link layer divided into two functionality-oriented sublayers
Taxonomy of multiple-access protocols discussed in this chapter
ANDOM ACCESS
In random access or contention methods, no station is
superior to another station and none is assigned the
control over another. No station permits, or does not
permit, another station to send. At each instance, a
station that has data to send uses a procedure defined
by the protocol to make a decision on whether or not to
send.
Topics discussed in this section:
ALOHA
Carrier Sense Multiple Access
Carrier Sense Multiple Access with Collision Detection
Carrier Sense Multiple Access with Collision Avoidance
Additive Links On-line Hawaii Area (ALOHA)
Frames in a pure ALOHA network
Procedure for pure ALOHA protocol
Vulnerable time for pure ALOHA protocol
Frames in a slotted ALOHA network
Vulnerable time for slotted ALOHA protocol
Vulnerable time in CSMA
CSMA/CD
McGraw-Hill ©The McGraw-Hill Companies, Inc., 2000
Carrier sense multiple access with collision detection
(CSMA/CD) is a computer networking access method
in which:
a carrier sensing scheme is used.
a transmitting data station that detects another signal while
transmitting a frame,
stops transmitting that frame,
transmits a jam signal, and then waits for a random time
interval before trying to send that frame again.
CSMA/CD is a modification of pure carrier sense multiple
access (CSMA).
CSMA/CD is used to improve CSMA performance by
terminating transmission as soon as a collision is detected,
thus reducing the probability of a second collision on retry.
CSMA/CD is a layer 2 access method, not a protocol of
the OSI model.
When a station wants to send some information, it
uses the following algorithm:
Main procedure:
Frame ready for transmission.
Is medium idle? If not, wait until it becomes ready
Start transmitting.
Did a collision occur? If so, go to collision detected
procedure.
Reset retransmission counters and end frame
transmission.
Example:
This can be likened to what happens at a dinner
party, where all the guests talk to each other
through a common medium (the air). Before
speaking, each guest politely waits for the current
speaker to finish. If two guests start speaking at
the same time, both stop and wait for short,
random periods of time (in Ethernet, this time is
measured in microseconds). The hope is that by
each choosing a random period of time, both
guests will not choose the same time to try to
speak again, thus avoiding another collision.
Example:
Imagine a very simple Ethernet network with
only two nodes.
Each node, independently, decides to send
an Ethernet frame to the other node.
Both nodes listen to the Ethernet wire and
sense that no carrier is present.
Both nodes transmit simultaneously, causing
a collision.
Both nodes detect the collision and each
node waits a random amount of time before
transmitting again.
Behavior of three persistence methods
Flow diagram for three persistence methods
Collision of the first bit in CSMA/CD
Collision and abortion in CSMA/CD
Flow diagram for the CSMA/CD
Energy level during transmission, idleness, or collision
CSMA/CA
Carrier sense multiple access with collision avoidance
(CSMA/CA), in computer networking, is a wireless
network multiple access method in which:
a carrier sensing scheme is used.
a node wishing to transmit data has to first listen to the
channel for a predetermined amount of time to determine
whether or not another node is transmitting on the channel
within the wireless range.
If the channel is sensed "idle," then the node is permitted to
begin the transmission process.
If the channel is sensed as "busy," the node defers its
transmission for a random period of time.
Once the transmission process begins, it is still possible for
the actual transmission of application data to not occur.
Timing in CSMA/CA
Inter−frame spaces (IFS) are waiting periods between
transmission of frames operating in the medium access control
(MAC) sublayer where carrier-sense multiple access with
collision avoidance (CSMA/CA) is used. These are techniques
used to prevent collisions as defined in IEEE 802.11-based
WLAN standard (Wi-Fi)
1.InterFrame Space (IFS): When a station finds the channel busy it senses the
channel again, when the station finds a channel to be idle it waits for a period of
time called IFS time. IFS can also be used to define the priority of a station or a
frame. Higher the IFS lower is the priority.
2.Contention Window: It is the amount of time divided into slots. A station that
is ready to send frames chooses a random number of slots as wait time.
3.Acknowledgments: The positive acknowledgments and time-out timer can help
guarantee a successful transmission of the frame.
Note
In CSMA/CA, if the station finds the
channel busy, it does not restart the
timer of the contention window;
it stops the timer and restarts it when
the channel becomes idle.
Flow diagram for CSMA/CA
S.NO CSMA/CD CSMA/CA
Whereas CSMA / CA is effective
1. CSMA / CD is effective after a collision. before a collision.
Whereas CSMA / CA is commonly
2. CSMA / CD is used in wired networks. used in wireless networks.
Whereas CSMA/ CA minimizes the
3. It only reduces the recovery time. possibility of collision.
Whereas CSMA / CA will first
CSMA / CD resends the data frame transmit the intent to send for data
4. whenever a conflict occurs. transmission.
While CSMA / CA is used in 802.11
5. CSMA / CD is used in 802.3 standard. standard.
While it is similar to simple
It is more efficient than simple CSMA(Carrier Sense Multiple
6. CSMA(Carrier Sense Multiple Access). Access).
12-2 CONTROLLED ACCESS
In controlled access, the stations consult one another
to find which station has the right to send. A station
cannot send unless it has been authorized by other
stations. We discuss three popular controlled-access
methods.
Topics discussed in this section:
Reservation
Polling
Token Passing
Reservation access method
Select and poll functions in polling access method
Logical ring and physical topology in token-passing access method
You might also like
- Media Access ControlDocument34 pagesMedia Access ControlPrem KumarNo ratings yet
- Report On CSMADocument12 pagesReport On CSMAUtkarsh HathiNo ratings yet
- Csma CDDocument3 pagesCsma CDAashu RajputNo ratings yet
- Lec4 WWW Cs Sjtu Edu CNDocument134 pagesLec4 WWW Cs Sjtu Edu CNAUSTIN ALTONNo ratings yet
- Csma CaDocument4 pagesCsma Cakurib38No ratings yet
- Computer Networks and SecurityDocument26 pagesComputer Networks and SecurityKamal ThelagaNo ratings yet
- Unit2 1.MAC ProtocolDocument40 pagesUnit2 1.MAC Protocolharsharewards1No ratings yet
- DCN Unit4 Media Access ControlDocument19 pagesDCN Unit4 Media Access ControlNamrathaNo ratings yet
- Click To Edit Master Subtitle StyleDocument11 pagesClick To Edit Master Subtitle StyleNavin BarathwajNo ratings yet
- Understand MAC Protocols CSMA/CD, CSMA/CA and Token PassingDocument19 pagesUnderstand MAC Protocols CSMA/CD, CSMA/CA and Token PassingNorila Mat ZanNo ratings yet
- Medium Access Control Sub Layer ProtocolDocument8 pagesMedium Access Control Sub Layer Protocol1NC21IS038 POLATHALA MOUNIKANo ratings yet
- Module2 2Document27 pagesModule2 2Anurag DavesarNo ratings yet
- ALOHA: ALOHA Is A System For Coordinating and Arbitrating Access To A SharedDocument10 pagesALOHA: ALOHA Is A System For Coordinating and Arbitrating Access To A SharedabhiuimNo ratings yet
- Multiple Access Protocols - ALOHA, CSMA, CSMA - CA and CSMA - CD - JavatpointDocument19 pagesMultiple Access Protocols - ALOHA, CSMA, CSMA - CA and CSMA - CD - JavatpointsrjaswarNo ratings yet
- CsmaDocument5 pagesCsmajohndoeNo ratings yet
- Csma OfdmDocument35 pagesCsma OfdmDARRYL IVAN BODOLLONo ratings yet
- 11 Data Link LayerMultiple Access ControlDocument42 pages11 Data Link LayerMultiple Access Controlrafaqathussainc077No ratings yet
- Data Link Layer Protocols - ALOHA, CSMA, CSMA/CA and CSMA/CDDocument9 pagesData Link Layer Protocols - ALOHA, CSMA, CSMA/CA and CSMA/CDYashaswi BhaskarlaNo ratings yet
- Media Access MethodDocument4 pagesMedia Access MethodYolanda Konde100% (1)
- Eeswar Babu Banala: Associate Professor Vidya Jyothi Institute of Technology Hyderabad TelanganaDocument77 pagesEeswar Babu Banala: Associate Professor Vidya Jyothi Institute of Technology Hyderabad Telanganakarna_lokeshNo ratings yet
- Multiple Access ProtocolsDocument43 pagesMultiple Access ProtocolsSahilPrabhakarNo ratings yet
- 11 Data Link LayerMultiple Access ControlDocument44 pages11 Data Link LayerMultiple Access Controlanushka aroraNo ratings yet
- Medium Access ControlDocument44 pagesMedium Access Controlvishnu Prasad GoranthalaNo ratings yet
- Chapter 12: Media Access Control (MAC)Document21 pagesChapter 12: Media Access Control (MAC)Selvakrishnan SekarNo ratings yet
- CN U3Document106 pagesCN U3NAMAN JAISWALNo ratings yet
- The MAC Layer: Jean-Yves Le Boudec Fall 2009Document52 pagesThe MAC Layer: Jean-Yves Le Boudec Fall 2009Diangarti TariangNo ratings yet
- Cn-Unit Ii-NotesDocument42 pagesCn-Unit Ii-NotesRobin RobinNo ratings yet
- 9 Multiple AccessDocument16 pages9 Multiple AccessHasan AhmadNo ratings yet
- CN UNIT III Part 1Document19 pagesCN UNIT III Part 1vijayNo ratings yet
- CE257 Data Communication and Networking: By: Dr. Ritesh Patel Ce Dept, Cspit, Charusat Riteshpatel - Ce@charusat - Ac.inDocument71 pagesCE257 Data Communication and Networking: By: Dr. Ritesh Patel Ce Dept, Cspit, Charusat Riteshpatel - Ce@charusat - Ac.inDHRUVNo ratings yet
- Lecture06 Mac CsmaDocument12 pagesLecture06 Mac CsmaDr. Pallabi SaikiaNo ratings yet
- Why CSMA/CD cannot be used in wireless LANDocument17 pagesWhy CSMA/CD cannot be used in wireless LAN054 Jaiganesh MNo ratings yet
- MAC ProtocolDocument36 pagesMAC ProtocolHrithik ReignsNo ratings yet
- WSN Unit-3Document89 pagesWSN Unit-3mr8566No ratings yet
- C-OFDMA: Improved Throughput For Next Generation WLAN Systems Based On Ofdma and Csma/CaDocument6 pagesC-OFDMA: Improved Throughput For Next Generation WLAN Systems Based On Ofdma and Csma/CafakeNo ratings yet
- Mobile Communications Chapter 3: Media AccessDocument23 pagesMobile Communications Chapter 3: Media AccessNischala RaoNo ratings yet
- Ch12 Multiple AccessDocument42 pagesCh12 Multiple AccessShubham JainNo ratings yet
- CSMA/CA Network Protocol ExplainedDocument2 pagesCSMA/CA Network Protocol ExplainedDragan StančevNo ratings yet
- CN Unit-IIIDocument14 pagesCN Unit-IIIAb VNo ratings yet
- Chapter 11Document14 pagesChapter 11Suvo IslamNo ratings yet
- Csma/Cd: Carrier Sense Multiple Access With Collision DetectionDocument24 pagesCsma/Cd: Carrier Sense Multiple Access With Collision Detectionpradeep singhNo ratings yet
- What Is A MAC Address?Document20 pagesWhat Is A MAC Address?peeyushNo ratings yet
- Ethernet and Multiple Access Protocols GuideDocument4 pagesEthernet and Multiple Access Protocols Guidemc210202582 MUEEN HASANNo ratings yet
- Access Media in Mobile ComputingDocument27 pagesAccess Media in Mobile Computingislamia collegeNo ratings yet
- A Multichannel CSMA MAC Protocol For Multihop Wireless NetworksDocument5 pagesA Multichannel CSMA MAC Protocol For Multihop Wireless Networksashish88bhardwaj_314No ratings yet
- Multiple Access protocol-ALOHA, CSMA, CSMA/CA and Csma/CdDocument11 pagesMultiple Access protocol-ALOHA, CSMA, CSMA/CA and Csma/CdDr. Km. Sucheta Singh (SET Assistant Professor)No ratings yet
- DCN Unit 5Document62 pagesDCN Unit 5RazinNo ratings yet
- CH 12Document55 pagesCH 12rawda.2419117No ratings yet
- Data Link MAC LayerDocument23 pagesData Link MAC Layerprishasingh1104No ratings yet
- CH - 12 MACDocument55 pagesCH - 12 MACsonyNo ratings yet
- MODEL HOME WORK --- 3: CSMA/CA AdvantagesDocument6 pagesMODEL HOME WORK --- 3: CSMA/CA AdvantagesKritesh ThakurNo ratings yet
- Csma CaDocument10 pagesCsma Caashish_jaywant1283No ratings yet
- Unit 3 - Computer Networks - WWW - Rgpvnotes.inDocument18 pagesUnit 3 - Computer Networks - WWW - Rgpvnotes.inROHIT MISHRANo ratings yet
- Media Access ControlDocument26 pagesMedia Access Controlgadhela saiNo ratings yet
- Media Access ControlDocument26 pagesMedia Access ControlRohit SinghNo ratings yet
- Chapter6MAC LayerDocument35 pagesChapter6MAC LayerMd NehalNo ratings yet
- Multiple-Access Protocols: Done By: Sana'a Al-Qaralleh Presented To: Dr. Ibrahim Al-QatawnehDocument40 pagesMultiple-Access Protocols: Done By: Sana'a Al-Qaralleh Presented To: Dr. Ibrahim Al-QatawnehMhmd NeamatNo ratings yet
- Medium Access ControlDocument10 pagesMedium Access ControlVijay ParuchuriNo ratings yet
- CCNA Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesFrom EverandCCNA Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesNo ratings yet
- Unit3JSPSingh (1)Document55 pagesUnit3JSPSingh (1)Aryan RathoreNo ratings yet
- Lecture18Blood RelationDocument30 pagesLecture18Blood RelationAryan RathoreNo ratings yet
- Lecture17Direction senseDocument33 pagesLecture17Direction senseAryan RathoreNo ratings yet
- Lecture16ProbabilityFinalDocument49 pagesLecture16ProbabilityFinalAryan RathoreNo ratings yet
- Unit1_P2JSPSinghDocument62 pagesUnit1_P2JSPSinghAryan RathoreNo ratings yet
- UNIT 5 Part1Document90 pagesUNIT 5 Part1Abhishek KumarNo ratings yet
- Unit 1 Pea306Document118 pagesUnit 1 Pea306Aryan RathoreNo ratings yet
- Unit 3 Pea306Document103 pagesUnit 3 Pea306Aryan RathoreNo ratings yet
- Lecture15PCFinalDocument58 pagesLecture15PCFinalAryan RathoreNo ratings yet
- Unit 4 Pea306Document127 pagesUnit 4 Pea306Aryan Rathore100% (1)
- Agile ModelDocument16 pagesAgile ModelAryan RathoreNo ratings yet
- UNIT 6 DEVOPSDocument50 pagesUNIT 6 DEVOPSAryan RathoreNo ratings yet
- CB - Doubly LL 1Document14 pagesCB - Doubly LL 1Aryan RathoreNo ratings yet
- SDLCDocument30 pagesSDLCAryan RathoreNo ratings yet
- On SDLC ModelsDocument52 pagesOn SDLC ModelsVenkatesh.R97% (32)
- CB - Linked ListDocument44 pagesCB - Linked ListAryan RathoreNo ratings yet
- HeNe LaserDocument2 pagesHeNe LaserAryan RathoreNo ratings yet
- Data Structures Lecture: Header Linked ListDocument11 pagesData Structures Lecture: Header Linked ListAryan RathoreNo ratings yet
- SelectionSortDocument34 pagesSelectionSortAryan RathoreNo ratings yet
- Ethernet Frame FormatDocument10 pagesEthernet Frame FormatAryan RathoreNo ratings yet
- NormalizationDocument71 pagesNormalizationAnmol OmarNo ratings yet
- Lect 22 To 26 Testing - BB Testing and LevelsDocument105 pagesLect 22 To 26 Testing - BB Testing and LevelsPenugonda PranavNo ratings yet
- 2 DMLDocument43 pages2 DMLAnmol OmarNo ratings yet
- Quantum Mechanics Recap: Key ConceptsDocument16 pagesQuantum Mechanics Recap: Key ConceptsAryan RathoreNo ratings yet
- Practice QDocument12 pagesPractice QNiraj TabdarNo ratings yet
- TestingDocument78 pagesTestingChanchal AlamNo ratings yet
- Practice Questions2 MTH401Document12 pagesPractice Questions2 MTH401Ravindra VishnoiNo ratings yet
- Modulo Ethernet - Ifbd-He0506 - SPC - enDocument35 pagesModulo Ethernet - Ifbd-He0506 - SPC - enE Moy LandaNo ratings yet
- SmartLogger3000 Quick GuideDocument18 pagesSmartLogger3000 Quick GuideYeison Steven HernanadezNo ratings yet
- Edge Router Lite PerformanceDocument7 pagesEdge Router Lite PerformanceAlecsandruNeacsuNo ratings yet
- Packet Switching ConcetpsDocument38 pagesPacket Switching ConcetpsKhaled GamalNo ratings yet
- Comandos EricssonDocument6 pagesComandos Ericssonpedro balbuenaNo ratings yet
- Frequency Division and Synchronous Time Division MultiplexingDocument6 pagesFrequency Division and Synchronous Time Division MultiplexingMurthyNo ratings yet
- Top 5 Free AWS Courses for BeginnersDocument8 pagesTop 5 Free AWS Courses for BeginnersminalNo ratings yet
- Chapter 3 Solutions: Activity Questions, Lab 3-1Document3 pagesChapter 3 Solutions: Activity Questions, Lab 3-1Andrew JonesNo ratings yet
- Installing and Configuring Atlassian SoftwareDocument19 pagesInstalling and Configuring Atlassian Softwarekourosh nosrati heraviNo ratings yet
- MiCOM H - 2146enDocument4 pagesMiCOM H - 2146enSerge RinaudoNo ratings yet
- Securing Public Key Infrastructure (PKI)Document128 pagesSecuring Public Key Infrastructure (PKI)Edin HadziahmetovicNo ratings yet
- ApplianX IP Gateway Quick Start GuideDocument1 pageApplianX IP Gateway Quick Start Guidedavid grantNo ratings yet
- 1 - STP VLAN VTP EtherChannel Threat Mitigation - TermDocument1 page1 - STP VLAN VTP EtherChannel Threat Mitigation - TermOlga BradyNo ratings yet
- AuditFlow User ManualDocument634 pagesAuditFlow User ManualDona RosadoNo ratings yet
- Intelligent Traffic System Using IoT and AgentsDocument7 pagesIntelligent Traffic System Using IoT and AgentsakashNo ratings yet
- Site Specifications For The DRX-Revolution Mobile X-Ray SystemDocument18 pagesSite Specifications For The DRX-Revolution Mobile X-Ray Systemtha_ansNo ratings yet
- Interface GSM Module with PIC MicrocontrollerDocument7 pagesInterface GSM Module with PIC Microcontrollerahmad_wazierNo ratings yet
- PC Zone Computer TradingDocument5 pagesPC Zone Computer TradingLam Chun YienNo ratings yet
- Ieee Projects Final Year Projects Mca Me Be Java Dot Net Projects Micans InfotechDocument7 pagesIeee Projects Final Year Projects Mca Me Be Java Dot Net Projects Micans InfotechgingeevimalNo ratings yet
- IP addresses, ISPs, locations and other metadataDocument2 pagesIP addresses, ISPs, locations and other metadataDaoud AlaliNo ratings yet
- Guia de Usuario - Modem e Roteador Archer VR900Document122 pagesGuia de Usuario - Modem e Roteador Archer VR900Felipe SantosNo ratings yet
- Network Subnetting and IP Address AssignmentDocument3 pagesNetwork Subnetting and IP Address Assignmentkashi nath DebNo ratings yet
- Ingenico Move5000 Quick Start Guide ENDocument9 pagesIngenico Move5000 Quick Start Guide ENMary GomezNo ratings yet
- Silo - Tips Universal Power Line CarrierDocument8 pagesSilo - Tips Universal Power Line CarrierSUBSTATION TOSYALINo ratings yet
- Amazon Simple Storage Service: User Guide API Version 2006-03-01Document1,069 pagesAmazon Simple Storage Service: User Guide API Version 2006-03-01teo2005No ratings yet
- 0.0.0.0 Lab - Configuring Devices For Use With Cisco Configuration Professional (CCP) 2.5 - InstructorDocument12 pages0.0.0.0 Lab - Configuring Devices For Use With Cisco Configuration Professional (CCP) 2.5 - InstructorSalem TrabelsiNo ratings yet
- Business Data Communications and Networking: Jerry Fitzgerald and Alan DennisDocument48 pagesBusiness Data Communications and Networking: Jerry Fitzgerald and Alan Denniseffective leaderNo ratings yet
- Delta Opti Datasheet IPC T22APDocument2 pagesDelta Opti Datasheet IPC T22APWisma SantikaNo ratings yet
- Activation of Network LicenseDocument10 pagesActivation of Network LicenseJosé GarcíaNo ratings yet