0% found this document useful (0 votes)
224 views19 pagesAWS S3 Storage: Features & Use Cases
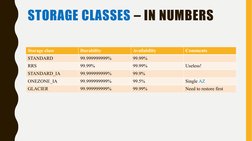
S3 is AWS's object storage service that provides scalable, durable storage for any type of data. It offers 99.999999999% durability and supports unlimited storage. Data is stored in buckets which contain objects. Objects have keys and values, and can have metadata and versions associated with them. Different storage classes like STANDARD, IA, and Glacier are available at different costs and performance levels. Access Control Lists and policies can be used to manage permissions on buckets and objects.
Uploaded by
dushantha madurangaCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PPTX, PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
224 views19 pagesAWS S3 Storage: Features & Use Cases
S3 is AWS's object storage service that provides scalable, durable storage for any type of data. It offers 99.999999999% durability and supports unlimited storage. Data is stored in buckets which contain objects. Objects have keys and values, and can have metadata and versions associated with them. Different storage classes like STANDARD, IA, and Glacier are available at different costs and performance levels. Access Control Lists and policies can be used to manage permissions on buckets and objects.
Uploaded by
dushantha madurangaCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PPTX, PDF, TXT or read online on Scribd