Professional Documents
Culture Documents
Tutorial: Valgrind: CS447/CS647/ECE453/ECE653/SE465 Lei Zhang 2014-2-14
Tutorial: Valgrind: CS447/CS647/ECE453/ECE653/SE465 Lei Zhang 2014-2-14
Uploaded by
Nishank ModiOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Tutorial: Valgrind: CS447/CS647/ECE453/ECE653/SE465 Lei Zhang 2014-2-14
Tutorial: Valgrind: CS447/CS647/ECE453/ECE653/SE465 Lei Zhang 2014-2-14
Uploaded by
Nishank ModiCopyright:
Available Formats
Tutorial: Valgrind
CS447/CS647/ECE453/ECE653/SE465
Lei Zhang
lei.zhang@uwaterloo.ca
2014-2-14
What is Valgrind
Valgrind is a GPL'd system for debugging and
profiling Linux programs. With Valgrind's tool
suite you can automatically detect many
memory management and threading bugs,
avoiding hours of frustrating bug-hunting,
making your programs more stable. You can also
perform detailed profiling to help speed up your
programs.
-- http://valgrind.org/info/
Valgrind Tool Suite
An instrumentation framework for building
dynamic analysis tools
Memcheck: memory error detector
Cachegrind: cache profiler
Helgrind, DRD: thread error detectors
Massif: heap profiler
...
Memcheck
Intercept calls to malloc/new/free/delete
Check all reads and writes of memory
Detect memory-management problems
buffer overflow
memory leak
allocation/deallocation mismatch
R/W via dangling pointer
use uninitialized memory
...
A Bit of Internals
Valgrind is essentially a virtual machine
Translate machine code into an architecture-
independent intermediate representation
Insert instrumentation code around the IR
(depending on the tool)
Translating back into machine code and run
on a simulated CPU
Memcheck: every register/memory value has a
shadow value containing information about it
Get Valgrind
Install Valgrind
ecelinux has Valgrind pre-installed
Ubuntu: apt-get install valgrind
Archlinux: pacman -S valgrind
General: ./configure & make & make install
Use Memcheck to Debug
Compile your program
$ gcc -g example.c -o example
-g: include debug info. so Valgrind knows line #
-O: optimization, -O2 and above can screw up
Valgrind report, not recommended
Run Valgrind
$ valgrind ./exmaple
Memcheck is the default tool invoked
--leak-check=full: list details of each leak
--track-origins=yes: track the origin of
uninitialized values
others via valgrind --help
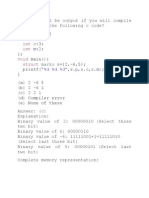
Buffer Overflow (Eg.1)
1 #include <stdio.h>
2 #include <stdlib.h>
3 int main()
4 {
5 int *b = calloc(
6 4, sizeof(int));
7 printf("%d\n", b[4]);
8 free(b);
9 return 0;
10 }
==31015== Invalid read of size 4
==31015== at 0x4005B0: main
(e1.c:7)
==31015== Address 0x51dc050 is 0
bytes after a block of
size 16 alloc'd
==31015== at 0x4C29860: calloc(in
/usr/lib/valgrind/
vgpreload_memcheck-
amd64-linux.so)
==31015== by 0x4005A3: main
(e1.c:5)
Memory Leak (Eg.2)
1 #include <stdio.h>
2 #include <stdlib.h>
3 int main()
4 {
5 int *b = calloc(
6 4, sizeof(int));
7 printf("%d\n", b[3]);
8 return 0;
9 }
==32266== 16 bytes in 1 blocks are
definitely lost in loss
record 1 of 1
==32266== at 0x4C29860: calloc
(in /usr/lib/valgrind/
vgpreload_memcheck-
amd64-linux.so)
==32266== by 0x400553: main
(e2.c:5)
==32266== LEAK SUMMARY:
==32266== definitely lost: 16
bytes in 1 blocks
...
Dangling Pointer (Eg.3)
1 #include <stdio.h>
2 #include <stdlib.h>
3 int main()
4 {
5 int *b = calloc(
6 4, sizeof(int));
7 b[2] = 1;
8 free(b);
9 printf("%d\n", b[2]);
10 return 0;
11 }
==5021== Invalid read of size 4
==5021== at 0x4005CA: main
(e3.c:9)
==5021== Address 0x51dc048 is 8
bytes inside a block of
size 16 free'd
==5021== at 0x4C289DC: free (in
/usr/lib/valgrind/
vgpreload_memcheck-
amd64-linux.so)
==5021== by 0x4005C1: main
(e3.c:8)
Double Free (Eg.4)
1 #include <stdio.h>
2 #include <stdlib.h>
3 int main()
4 {
5 int *b = malloc(
6 4 * sizeof(int));
7 b[2] = 1;
8 free(b);
9 free(b);
10 return 0;
11 }
==2819== Invalid free() / delete /
delete[] / realloc()
==2819== at 0x4C289DC: free (in
/usr/lib/valgrind/
vgpreload_memcheck-
amd64-linux.so)
==2819== by 0x400578: main (e4.c:9)
==2819== Address 0x51dc040 is 0 bytes
inside a block of size 16
free'd
==2819== at 0x4C289DC: free (in
/usr/lib/valgrind/
vgpreload_memcheck-
amd64-linux.so)
Uninitialized Memory (Eg.5)
1 #include <stdio.h>
2 #include <stdlib.h>
3 int main()
4 {
5 int ret;
6 int *b = malloc(
7 4 * sizeof(int));
8 ret = b[2];
9 free(b);
10 return ret;
11 }
==3911== Syscall param
exit_group(status) contains
uninitialised byte(s)
...
==3911== Uninitialised value was
created by a heap allocation
==3911== at 0x4C27730: malloc
(in /usr/lib/valgrind/
vgpreload_memcheck-
amd64-linux.so)
==3911== by 0x40054E: main
(e5.c:6)
Caveats
No bound checking on stack-allocated arrays
int main() {
int a[10];
a[11] = 42;
}
More time (20x-30x), more memory (2x)
Reveal problem only when input triggering it
is provided
Useful Links
Valgrind Quick Start Guide
http://valgrind.org/docs/manual/quick-start.
html#quick-start.intro
Valgrind Memcheck Manual
http://valgrind.org/docs/manual/mc-manual.html
Design and Architecture of Valgrind
Nicholas Nethercote & Julian Seward, Valgrind: A
Framework for Heavyweight Dynamic Binary
Instrumentation, PLDI07
You might also like
- CIS 2107 Computer Systems and Low-Level Programming Fall 2011 FinalDocument18 pagesCIS 2107 Computer Systems and Low-Level Programming Fall 2011 FinalLimSiEianNo ratings yet
- Gordon Fyodor Lyon-Nmap Network Scanning - The Official Nmap Project Guide To Network Discovery and Security Scanning-Nmap Project (2009) PDFDocument467 pagesGordon Fyodor Lyon-Nmap Network Scanning - The Official Nmap Project Guide To Network Discovery and Security Scanning-Nmap Project (2009) PDFSri PraKrije100% (3)
- Using Valgrind:: Detecting Memory ErrorsDocument11 pagesUsing Valgrind:: Detecting Memory ErrorsGiridhar AddepalliNo ratings yet
- Exam2b s11Document13 pagesExam2b s11serhatandic42No ratings yet
- 03B+04A Dynamic Memory Allocation Memory LeaksDocument53 pages03B+04A Dynamic Memory Allocation Memory Leaksmoamin.shikhaNo ratings yet
- Exam2 f10 PDFDocument15 pagesExam2 f10 PDFajgeminiNo ratings yet
- Debugging Tools Intro - DWARF, ELF, GDB:Binutils, Build-IdDocument33 pagesDebugging Tools Intro - DWARF, ELF, GDB:Binutils, Build-IdergodicNo ratings yet
- IT215: Systems Software, Winter 2015-16 Second In-Sem Exam (1 Hour 30 Minutes)Document8 pagesIT215: Systems Software, Winter 2015-16 Second In-Sem Exam (1 Hour 30 Minutes)Mettl SupportNo ratings yet
- Java Error in Datagrip 794Document77 pagesJava Error in Datagrip 794aslNo ratings yet
- Global Edge C ProgramDocument14 pagesGlobal Edge C ProgramAbhishek Ek100% (1)
- What Is The Output of This ProgramDocument5 pagesWhat Is The Output of This ProgramJasleen KaurNo ratings yet
- Dynamic Memory AllocationDocument14 pagesDynamic Memory AllocationHemesh Jain SuranaNo ratings yet
- Exam2 s09 v2Document10 pagesExam2 s09 v2serhatandic42No ratings yet
- Memory AllocationDocument21 pagesMemory Allocationvikram_srit9342No ratings yet
- GettingStartedCpp PDFDocument236 pagesGettingStartedCpp PDFHữu QuânNo ratings yet
- Kernel Debug Series Part6 Understand Kernel OopsDocument27 pagesKernel Debug Series Part6 Understand Kernel Oopssnehadhar39No ratings yet
- How To Check Export Functions of Windows 8 NT Kernel by Using WindbgDocument7 pagesHow To Check Export Functions of Windows 8 NT Kernel by Using WindbgchuiyewleongNo ratings yet
- R5F21548GDocument5 pagesR5F21548Gสุขสันต์ วงค์คำชาวNo ratings yet
- Memory AllocationDocument21 pagesMemory AllocationshonatajNo ratings yet
- Computer Architecture Lab 5aDocument9 pagesComputer Architecture Lab 5aHasan IqbalNo ratings yet
- OOP1 Lab8Document12 pagesOOP1 Lab8asdfghkl3232No ratings yet
- Java Error in Datagrip 22903Document61 pagesJava Error in Datagrip 22903aslNo ratings yet
- 123654789632587410Document20 pages123654789632587410hanandkumarNo ratings yet
- 1 Lab ExerciseDocument25 pages1 Lab ExerciseJohn AraojoNo ratings yet
- Dynamic MemoryDocument28 pagesDynamic Memorysubbaiyal6No ratings yet
- Programming in C and C++: 4. Misc. Library Features, Gotchas, Hints and TipsDocument24 pagesProgramming in C and C++: 4. Misc. Library Features, Gotchas, Hints and TipsJohn PinchosNo ratings yet
- Tcs Placement Paper Technical 07Document3 pagesTcs Placement Paper Technical 07kanthigaduNo ratings yet
- Clang Linux Fosdem 19 PDFDocument13 pagesClang Linux Fosdem 19 PDFCristianNo ratings yet
- Answer Sheet Template: Part - A (One Exercise) Ans. 1: C Code For Exercise 1 - Symbol Table Creation (35 Marks)Document4 pagesAnswer Sheet Template: Part - A (One Exercise) Ans. 1: C Code For Exercise 1 - Symbol Table Creation (35 Marks)Shubham TiwariNo ratings yet
- Kernel Hacking: Introduction To Linux Kernel 2.6 How To Write A RootkitDocument28 pagesKernel Hacking: Introduction To Linux Kernel 2.6 How To Write A RootkitRAVICHANDRA VNo ratings yet
- Linux Kernel Debugging Going Beyond Printk MessagesDocument65 pagesLinux Kernel Debugging Going Beyond Printk MessagesالمتمردفكرياNo ratings yet
- 01 IntroductionDocument31 pages01 IntroductionMourad El HassouniNo ratings yet
- C QuestionsDocument57 pagesC QuestionsSuman RavuriNo ratings yet
- C Faq2Document65 pagesC Faq2ShaaahidNo ratings yet
- Tricky C QuestionsDocument24 pagesTricky C QuestionshonalemangeshNo ratings yet
- Week8 WDocument10 pagesWeek8 WleishNo ratings yet
- 21-CP-6 (Report12) DLDDocument18 pages21-CP-6 (Report12) DLDAlmaas ChaudryNo ratings yet
- IT215: Systems Software, Winter 2014-15 First In-Sem Exam (2 Hours)Document9 pagesIT215: Systems Software, Winter 2014-15 First In-Sem Exam (2 Hours)Mettl SupportNo ratings yet
- MCQ'sDocument10 pagesMCQ'ssjprabakarsathyNo ratings yet
- C Quiz Questions With AnswersDocument22 pagesC Quiz Questions With AnswersvanithaarivuNo ratings yet
- CCS CodeDocument3 pagesCCS CodesuyashNo ratings yet
- Emu LogDocument253 pagesEmu LogCopito Max GarciaCastroNo ratings yet
- C Faq3Document83 pagesC Faq3ShaaahidNo ratings yet
- C Language Quiz Questions and Answers With ExplanationDocument47 pagesC Language Quiz Questions and Answers With ExplanationarunNo ratings yet
- End Solution 2023 (Autumn)Document10 pagesEnd Solution 2023 (Autumn)Arman PaniNo ratings yet
- Structures, Unions & BitwiseDocument14 pagesStructures, Unions & BitwiseKetan Fakeer100% (1)
- DXC Tech 1 PDFDocument16 pagesDXC Tech 1 PDFBhavana IttigoniNo ratings yet
- Dynamic Memory Allocation in C: (Reek, Ch. 11)Document21 pagesDynamic Memory Allocation in C: (Reek, Ch. 11)Mukul ThakurNo ratings yet
- CSCPAPERSDocument54 pagesCSCPAPERSABHISHEK ANANDNo ratings yet
- Wipro 5Document183 pagesWipro 5SanthoshiniRajanNo ratings yet
- Functions: CSIS1117 Computer ProgrammingDocument52 pagesFunctions: CSIS1117 Computer Programmingjulianli0220No ratings yet
- Embedded Sample PaperDocument11 pagesEmbedded Sample PaperShashi KanthNo ratings yet
- How To Develop An Operating System UsingDocument14 pagesHow To Develop An Operating System UsingSarkarsoft SarkarNo ratings yet
- C Programming Basic - Week 2Document55 pagesC Programming Basic - Week 2Tan VuNo ratings yet
- Welcome To Oracle Placement Paper 2010Document15 pagesWelcome To Oracle Placement Paper 20109464No ratings yet
- KTLTR Week03 PublishDocument61 pagesKTLTR Week03 PublishNhat LongNo ratings yet
- C Programming for the Pc the Mac and the Arduino Microcontroller SystemFrom EverandC Programming for the Pc the Mac and the Arduino Microcontroller SystemNo ratings yet
- CRF Design Template v4.0Document28 pagesCRF Design Template v4.0Shalini ShivenNo ratings yet
- Business Units in Project Portfolio ManagementDocument10 pagesBusiness Units in Project Portfolio ManagementAnonymous lP1z1cAgsYNo ratings yet
- Paulwaldmann (Paul Waldmann) - Starred GitHubDocument6 pagesPaulwaldmann (Paul Waldmann) - Starred GitHubAnonymous l0YO1cNo ratings yet
- Routing and SwitchingDocument10 pagesRouting and Switchingsupersaiyan445566No ratings yet
- Byrne, John: Advanced Signaling & Media Management - TelcobridgesDocument3 pagesByrne, John: Advanced Signaling & Media Management - TelcobridgesmsantacruzrNo ratings yet
- Penetration Testing and Network DefenseDocument624 pagesPenetration Testing and Network DefenseAnonymous iNxLvwNo ratings yet
- Computer Networks: Differentiated Services ( 5.4.6)Document14 pagesComputer Networks: Differentiated Services ( 5.4.6)rafael_aNo ratings yet
- PG LabelGallery Programming Guide EngDocument306 pagesPG LabelGallery Programming Guide EngAndresNo ratings yet
- Digital System Design: Verilog HDL Basic ConceptsDocument38 pagesDigital System Design: Verilog HDL Basic Conceptsmahesh24pkNo ratings yet
- Apostila JCLDocument126 pagesApostila JCLFrancisco Junior100% (1)
- MIT6 01SCS11 Ses03 PDFDocument3 pagesMIT6 01SCS11 Ses03 PDFSanjay RaajNo ratings yet
- 3.3 Infrastructure AutomationDocument20 pages3.3 Infrastructure AutomationAtul SharmaNo ratings yet
- Exam Cafe CAD CAM AnswersDocument8 pagesExam Cafe CAD CAM AnswersO OmNo ratings yet
- Lecture 1-3: Cse202: Object Oriented ProgrammingDocument49 pagesLecture 1-3: Cse202: Object Oriented ProgrammingAbhishek KumarNo ratings yet
- Manual For The Sound Card Oscilloscope V1.30: 1 RequirementsDocument11 pagesManual For The Sound Card Oscilloscope V1.30: 1 RequirementsJorge MartinNo ratings yet
- Numerical Analysis - I. Jacques and C. JuddDocument110 pagesNumerical Analysis - I. Jacques and C. Judddeepika snehiNo ratings yet
- Motor Vehicles Department, Government of Maharashtra: Application Reference DetailsDocument3 pagesMotor Vehicles Department, Government of Maharashtra: Application Reference DetailsAshutosh BhosaleNo ratings yet
- FTV - Lab ManualDocument304 pagesFTV - Lab ManualraulcarballedaNo ratings yet
- Assignment 1 OSDocument13 pagesAssignment 1 OSDương Văn ChấnNo ratings yet
- Redux Async - Course Introduction: Let Us First Try To Understand The Asynchronous Behaviour!Document7 pagesRedux Async - Course Introduction: Let Us First Try To Understand The Asynchronous Behaviour!Mahesh VPNo ratings yet
- MIS603 Microservices ArchitectureDocument8 pagesMIS603 Microservices Architecturemian saadNo ratings yet
- PS4 Training GuideDocument35 pagesPS4 Training GuidecatalinccNo ratings yet
- Math/Numeric Functions: - Power /pow - Round - Truncate - Mod - SQRTDocument11 pagesMath/Numeric Functions: - Power /pow - Round - Truncate - Mod - SQRTAvi DahiyaNo ratings yet
- ITWD Syllabus Sp10Document12 pagesITWD Syllabus Sp10Sean LawsonNo ratings yet
- ZedDocument32 pagesZedYared100% (2)
- BSMS API V 0.3 Specs (1) BrandDocument4 pagesBSMS API V 0.3 Specs (1) BrandMuhammad Nadeem ZafarNo ratings yet
- Unit 1-EsiotDocument46 pagesUnit 1-EsiotSonia BajajNo ratings yet
- RAM and ROM AND CPUDocument15 pagesRAM and ROM AND CPUJed SorollaNo ratings yet
- Session Plan 15CS564 Dot Net-2017-2018Document5 pagesSession Plan 15CS564 Dot Net-2017-2018Rashmi HarshaNo ratings yet