Professional Documents
Culture Documents
FortiAnalyzer Admin Guide 05-30003-0082-20060925
FortiAnalyzer Admin Guide 05-30003-0082-20060925
Uploaded by
Pablo Fuentes SanchezOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
FortiAnalyzer Admin Guide 05-30003-0082-20060925
FortiAnalyzer Admin Guide 05-30003-0082-20060925
Uploaded by
Pablo Fuentes SanchezCopyright:
Available Formats
www.fortinet.
com
FortiAnalyzer
Version 3.0 MR3
A D M I N I S T R A T I O N G U I D E
FortiAnalyzer Administration Guide
Version 3.0 MR3
25 September 2006
05-30003-0082-20060925
Copyright 2006 Fortinet, Inc. All rights reserved. No part of this
publication including text, examples, diagrams or illustrations may be
reproduced, transmitted, or translated in any form or by any means,
electronic, mechanical, manual, optical or otherwise, for any purpose,
without prior written permission of Fortinet, Inc.
Trademarks
ABACAS, APSecure, FortiASIC, FortiBIOS, FortiBridge, FortiClient,
FortiGate, FortiGuard, FortiGuard-Antispam, FortiGuard-Antivirus,
FortiGuard-Intrusion, FortiGuard-Web, FortiLog, FortiAnalyzer,
FortiManager, Fortinet, FortiOS, FortiPartner, FortiProtect, FortiReporter,
FortiResponse, FortiShield, FortiVoIP, and FortiWiFi are trademarks of
Fortinet, Inc. in the United States and/or other countries. The names of
actual companies and products mentioned herein may be the trademarks
of their respective owners.
Regulatory compliance
FCC Class A Part 15 CSA/CUS
!
Caution: If you install a battery that is not the correct type, it could
explode. Dispose of used batteries according to local regulations.
Contents
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 3
Contents
Introduction...................................................................................... 11
The FortiAnalyzer Unit .................................................................................... 11
FortiAnalyzer-100A/100B............................................................................ 11
FortiAnalyzer-400........................................................................................ 12
FortiAnalyzer-800........................................................................................ 12
FortiAnalyzer-2000...................................................................................... 13
FortiAnalyzer-4000...................................................................................... 13
FortiAnalyzer-4000A ................................................................................... 13
FortiAnalyzer features..................................................................................... 14
Reporting..................................................................................................... 14
Data mining................................................................................................. 14
Network analyzer ........................................................................................ 14
Log viewer................................................................................................... 15
Real-time log viewing.................................................................................. 15
Log Aggregation.......................................................................................... 15
Quarantine .................................................................................................. 15
Network Attached Storage .......................................................................... 15
About this guide .............................................................................................. 15
FortiAnalyzer documentation......................................................................... 16
Fortinet Tools and Documentation CD........................................................ 17
Fortinet Knowledge Center ......................................................................... 17
Comments on Fortinet technical documentation......................................... 17
Customer service and technical support ...................................................... 17
Installing the FortiAnalyzer unit ..................................................... 19
Planning the installation ................................................................................. 19
Connecting the FortiAnalyzer unit ................................................................. 20
Environmental specifications....................................................................... 20
Air flow ........................................................................................................ 20
Mechanical loading ..................................................................................... 20
Connecting to the network .......................................................................... 20
Configuring the FortiAnalyzer unit ................................................................ 21
Using the web-based manager ................................................................... 23
Using the command line interface............................................................... 24
Using the front panel buttons and LCD....................................................... 25
Upgrading the FortiAnalyzer firmware .......................................................... 25
Backing up the FortiAnalyzer hard disk........................................................ 26
Shutting down the FortiAnalyzer unit............................................................ 26
FortiAnalyzer Version 3.0 MR3 Administration Guide
4 05-30003-0082-20060925
Contents
Configure the FortiAnalyzer unit .................................................... 27
Dashboard........................................................................................................ 27
System Information..................................................................................... 28
System Resources...................................................................................... 28
License Information..................................................................................... 29
Alert Message Console............................................................................... 29
Statistics...................................................................................................... 29
Report Engine............................................................................................. 29
Automatic Refresh Interval.......................................................................... 29
System Operation ....................................................................................... 29
Viewing operational history ......................................................................... 30
Viewing Session information....................................................................... 30
Filtering session information................................................................. 31
Viewing Alert messages.............................................................................. 31
Setting the time........................................................................................... 32
Restore factory default system settings ...................................................... 32
Format the log disks.................................................................................... 33
Restoring a FortiAnalyzer unit..................................................................... 33
Restoring a FortiAnalyzer-100 or FortiAnalyzer-400 ............................ 33
Restoring a FortiAnalyzer-100A/100B, 800, 2000 and 4000/4000A..... 34
Changing the firmware................................................................................ 35
Changing the host name............................................................................. 36
Network settings.............................................................................................. 36
Interface...................................................................................................... 36
Changing the interface settings............................................................ 37
About FortiDiscovery ............................................................................ 37
DNS ............................................................................................................ 38
Routing........................................................................................................ 38
Adding a route ...................................................................................... 38
Administrator settings .................................................................................... 39
Adding a new administrator ........................................................................ 39
Changing the administrator password.................................................. 40
Access Profile ............................................................................................. 40
Auth Groups................................................................................................ 41
RADIUS Server ........................................................................................... 42
Administrator Settings................................................................................. 42
Monitor ........................................................................................................ 42
Administrative domains.................................................................................. 43
Enabling administrative domains ................................................................ 43
Disabling administrative domains ............................................................... 44
Configuring ADOM settings ........................................................................ 44
Creating a new ADOM................................................................................ 45
Adding a device to an ADOM...................................................................... 45
Contents
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 5
Network sharing............................................................................................... 45
Adding users ............................................................................................... 46
Adding groups ............................................................................................. 46
Configuring Windows shares ...................................................................... 46
Assigning user access ................................................................................ 47
Configuring NFS shares.............................................................................. 48
Setting folder and file privileges .................................................................. 49
Configuring the FortiAnalyzer unit ................................................................ 49
Log Settings ................................................................................................ 50
Log Aggregation.......................................................................................... 51
Configuring an aggregation client ......................................................... 52
Configuring an aggregation server ....................................................... 53
IP Aliases .................................................................................................... 53
Importing an IP alias list file.................................................................. 53
IP alias ranges...................................................................................... 54
RAID............................................................................................................ 54
Configuring RAID on the FortiAnalyzer-400 and FortiAnalyzer-800..... 54
Configuring RAID on the FortiAnalyzer-2000 and FortiAnalyz-
er-4000/4000A ................................................................................... 55
Maintenance..................................................................................................... 57
Backup & Restore ....................................................................................... 57
Update center.............................................................................................. 58
RAID levels....................................................................................................... 59
Linear .......................................................................................................... 60
RAID 0......................................................................................................... 60
RAID 1......................................................................................................... 60
RAID 5......................................................................................................... 60
RAID 10....................................................................................................... 61
RAID 50....................................................................................................... 61
RAID 5 and RAID 10 with hot spare............................................................ 61
Hot swapping hard disks ............................................................................. 61
Hot swapping in the FortiAnalyzer-400 and FortiAnalyzer-800 ............ 61
Hot swapping the FortiAnalyzer-2000 and FortiAnalyzer-4000/4000A. 62
Devices.............................................................................................. 65
Devices List...................................................................................................... 65
Device interaction with a FortiAnalyzer unit ................................................ 66
Maximum allowed devices .......................................................................... 66
Unregistered device options........................................................................ 67
FortiGate units connecting with FortiDiscovery........................................... 67
Unknown devices connecting to the FortiAnalyzer unit............................... 68
Adding a FortiGate unit................................................................................... 68
Defining FortiGate port interfaces ............................................................... 70
Adding an HA cluster .................................................................................. 70
Adding FortiClient installations ..................................................................... 71
FortiAnalyzer Version 3.0 MR3 Administration Guide
6 05-30003-0082-20060925
Contents
Adding a FortiManager unit............................................................................ 72
Adding a Syslog server................................................................................... 73
Device Groups ................................................................................................. 74
Blocked Devices.............................................................................................. 74
Viewing blocked devices............................................................................. 75
Logs .................................................................................................. 77
Log Viewer ....................................................................................................... 77
Real-time log viewer ................................................................................... 77
Historical log viewer .................................................................................... 78
Browse.............................................................................................................. 80
Browsing log files ........................................................................................ 81
Importing a log file....................................................................................... 82
Downloading a log file................................................................................. 82
Customizing the log view ............................................................................... 83
Customizing the log column views.............................................................. 83
Filtering logs................................................................................................ 84
Filtering tip............................................................................................ 84
Search the logs................................................................................................ 84
Basic search ............................................................................................... 85
Advanced search ........................................................................................ 85
Search tips .................................................................................................. 86
Printing the search results .......................................................................... 86
Log rolling........................................................................................................ 86
Content archive................................................................................ 89
Content viewer................................................................................................. 89
Customizing the content log view ................................................................. 90
Customizing the log column views.............................................................. 90
Filtering content logs................................................................................... 91
Filtering tip............................................................................................ 91
Log rolling........................................................................................................ 91
Quarantine........................................................................................ 95
Configuring quarantine settings.................................................................... 95
Viewing the quarantined files list................................................................... 96
Forensic Analysis ............................................................................ 97
Users and groups............................................................................................ 97
Adding users ............................................................................................... 97
Creating groups .......................................................................................... 98
Lookup ........................................................................................................ 98
Where does FortiAnalyzer get this information?................................... 99
Contents
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 7
Searching user data ...................................................................................... 100
Saving search results................................................................................ 100
Local archive ............................................................................................ 101
Forensic Reports ........................................................................................... 101
Configuring reports.................................................................................... 101
Customizing the report properties....................................................... 102
Configuring the report criteria ............................................................. 102
Configuring the time period................................................................. 104
Configuring the report types ............................................................... 104
Configuring the report output .............................................................. 104
Viewing Forensic Reports ......................................................................... 106
Traffic summary and security events........................................... 107
Traffic Summaries ......................................................................................... 107
Top Users.................................................................................................. 107
Viewing Web traffic............................................................................. 107
Viewing Email traffic ........................................................................... 108
Viewing FTP traffic.............................................................................. 109
Viewing Instant Messaging and P2P traffic ........................................ 109
Filtering traffic summaries ......................................................................... 110
Filtering tip .......................................................................................... 111
Device Summary....................................................................................... 111
Traffic Report ............................................................................................ 112
Configuring a traffic report .................................................................. 112
Viewing traffic summary reports ......................................................... 112
Security event summaries ............................................................................ 113
Adding a security event report .................................................................. 113
Viewing the security event reports ............................................................ 113
Viewing virus activity ................................................................................. 114
Viewing Intrusion activity........................................................................... 115
Viewing Suspicious activity ....................................................................... 116
Viewing administrative activities................................................................ 117
Reports............................................................................................ 119
Configuring reports....................................................................................... 119
Configuring a report profile........................................................................ 120
Customizing the report properties....................................................... 121
Configuring the report devices............................................................ 122
Configuring the report scope .............................................................. 122
Configuring the report types ............................................................... 124
Configuring the report Format............................................................. 124
Configuring the report schedule.......................................................... 125
Configuring the report output .............................................................. 125
FortiAnalyzer Version 3.0 MR3 Administration Guide
8 05-30003-0082-20060925
Contents
Browsing reports........................................................................................... 127
Viewing reports ......................................................................................... 128
Default reports .......................................................................................... 128
Report types.............................................................................................. 129
Roll up report ...................................................................................... 129
Individual reports ................................................................................ 129
Event activity codes............................................................................ 129
Alerts............................................................................................... 131
Alert Events.................................................................................................... 131
Adding an alert event ................................................................................ 131
Output............................................................................................................. 132
Mail server ................................................................................................ 133
Testing the Mail server configuration.................................................. 133
SNMP access ........................................................................................... 133
Adding an SNMP server ..................................................................... 134
Syslog Servers.......................................................................................... 134
Adding a Syslog server....................................................................... 135
FortiAnalyzer SNMP support .............................................................. 135
FortiAnalyzer traps.................................................................................... 136
FortiGate MIB System Traps.............................................................. 136
FortiGate MIB Logging Traps ............................................................. 136
FortiGate MIB VPN Traps................................................................... 136
Fortinet MIB System fields.................................................................. 136
Fortinet Administrator Accounts ......................................................... 136
Fortinet Options.................................................................................. 136
Fortinet Active IP Sessions................................................................. 137
RFC-1213 (MIB II) .............................................................................. 137
RFC-2665 (Ethernet-like MIB) ............................................................ 137
Network Analyzer........................................................................... 139
Connecting the FortiAnalyzer for analyzing network traffic ..................... 139
Traffic viewer ................................................................................................. 140
Real-time traffic viewer ............................................................................. 140
Historical traffic viewer .............................................................................. 141
Changing the historical view criteria................................................... 142
Browsing network traffic logs...................................................................... 142
Browsing network traffic log files............................................................... 143
Downloading a network traffic log file ....................................................... 144
Customizing the traffic analyzer log view................................................... 145
Customizing the log column views............................................................ 145
Filtering network traffic logs ...................................................................... 145
Filtering tip.......................................................................................... 146
Contents
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 9
Search the network traffic logs .................................................................... 146
Basic search.............................................................................................. 146
Advanced search ...................................................................................... 146
Search tips ................................................................................................ 147
Printing the search results......................................................................... 147
Log rolling...................................................................................................... 147
Vulnerability scan .......................................................................... 151
Modules .......................................................................................................... 151
Jobs ................................................................................................................ 152
Adding a new vulnerability scan job.......................................................... 153
Reports ........................................................................................................... 155
Index................................................................................................ 157
FortiAnalyzer Version 3.0 MR3 Administration Guide
10 05-30003-0082-20060925
Contents
Introduction The FortiAnalyzer Unit
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 11
Introduction
FortiAnalyzer units are network appliances that provides robust reporting, data
analysis and integrated log collection tools. Detailed log reports provide historical
as well as current analysis of network traffic, such as email, FTP and web
browsing activity, to help identify security issues and reduce network misuse and
abuse.
The FortiAnalyzer unit provides a robust selection of reporting tools from detailed
reports that can be scheduled or generated on demand, to basic traffic sniffing
and real-time network monitoring.
This section introduces you to the FortiAnalyzer appliance and includes the
following topics:
The FortiAnalyzer Unit
About this guide
FortiAnalyzer documentation
Customer service and technical support
The FortiAnalyzer Unit
The FortiAnalyzer family includes the following models:
FortiAnalyzer-100A/100B
Ports 4 10/100 Ethernet ports
Memory 256 MB
Disk Drives 1
Disk Drive Capacity 120 GB
FortiGate Devices Supported 10 FortiGate devices or VDOM licenses.
Supports FortiGate-50A to FortiGate-100A
only.
FortiClient installations Supported None
AC Input Voltage 100-240V 0.8Amp Max
POWER
STATUS
4 3 2 1
LINK / ACT
10/100
FortiAnalyzer Version 3.0 MR3 Administration Guide
12 05-30003-0082-20060925
The FortiAnalyzer Unit Introduction
FortiAnalyzer-400
FortiAnalyzer-800
Ports 3 10/100 Ethernet ports
Memory 256 MB
Disk Drives 4 x 120MB hot-swappable (3.0 MR1)
Disk Drive Capacity 480 GB
FortiGate Devices Supported 200 FortiGate units or VDOM licenses.
Supports FortiGate-50A to FortiGate-800 only.
FortiClient installations Supported 2000
AC Input Voltage 100-240V 4Amp Max
Ports 2 10/100 Ethernet ports
Memory 512 MB
Disk Drives 4 x 120MB hot-swappable (3.0 MR1)
Disk Drive Capacity 480 GB
FortiGate Devices Supported 250 FortiGate units or VDOM licenses.
Supports FortiGate-50A to FortiGate-800 only.
FortiClient installations Supported 2500
AC Input Voltage 100-240V 04Amp Max
Introduction The FortiAnalyzer Unit
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 13
FortiAnalyzer-2000
FortiAnalyzer-4000
FortiAnalyzer-4000A
Ports 4 gigabit Ethernet ports
Memory 2 GB
Disk Drives 6 x 400GB hot-swappable
Disk Drive Capacity 2.4 TB
FortiGate Devices Supported 500 FortiGate units or VDOM licenses.
Supports all FortiGate models.
FortiClient installations Supported 5000
AC Input Voltage 100-240V 9Amp Max
Ports 2 gigabit ethernet ports
Memory 1 GB
Disk Drives 12 x 250GB - hot-swappable
Disk Drive Capacity 3 TB
FortiGate Devices Supported 500 FortiGate units or VDOM licenses.
Supports all FortiGate models.
FortiClient installations Supported 5000
AC Input Voltage 100-240V 9Amp Max
Ports 2 gigabit ethernet ports
Memory 1 GB
Disk Drives 12 x 250GB - hot-swappable
Disk Drive Capacity 3 TB
1
2
A
FortiAnalyzer Version 3.0 MR3 Administration Guide
14 05-30003-0082-20060925
FortiAnalyzer features Introduction
FortiAnalyzer features
The FortiAnalyzer unit receives log files from multiple FortiGate and syslog
devices. Using the FortiAnalyzer units robust reporting capabilities, you can
monitor the traffic, attacks, and misuses from network users. The FortiAnalyzer
unit includes the following features:
Reporting
The FortiAnalyzer reporting includes:
Log analysis and reporting
Analyze logs submitted from multiple devices and generate a variety of reports
that enables you to proactively secure networks as threats arise, avoid network
abuses, manage bandwidth requirements, monitor Web site visits, and ensure
appropriate usage of the network. Analysis includes by firewall and by user or
group of users.
Vulnerability reports
Vulnerability reports show potential weaknesses to attacks that may exist for a
selected device. The FortiAnalyzer unit queries for open ports, and where
possible, gathers information about the running services. Known vulnerabilities
that exist for a service or version of the service is included in the report.
Data mining
The FortiAnalyzer unit provides data mining features that enables you to easily
access simple reports to obtain information on the intrusion attempts on your
network as well as the types of traffic occurring on your network. Security event
summaries provide a snapshot of what unwanted traffic is attempting to breach
the firewall and the top traffic producers on the network, while traffic summaries
provide a snapshot of the traffic passing through the firewall on your network.
These reports can help you identify the high volume users, or attack events that
may be slowing down overall network traffic.
Network analyzer
The FortiAnalyzer network analyzer enables you to reach areas of the network
where FortiGate firewalls are not employed, or if you do not have a FortiGate unit
as a firewall. The FortiAnalyzer network analyzer functions as a sniffer to capture
traffic data, save it to the FortiAnalyzer hard disk, and display it or generate
reports using the data.
FortiGate Devices Supported 500 FortiGate units or VDOM licenses.
Supports all FortiGate models.
FortiClient installations Supported 5000
AC Input Voltage 100-240V 9Amp Max
Note: Vulnerability reports are not available on the FortiAnalyzer-100.
Note: The network analyzer is not available on the FortiAnalyzer-100.
Introduction About this guide
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 15
Log viewer
The log browser, enables you to view the log messages sent to the FortiAnalyzer
unit from registered devices. With the log viewer you can view any log file and
messages saved on the FortiAnalyzer hard disk. All log files and messages are
searchable and can be filtered to drill down and locate specific information.
Real-time log viewing
The FortiAnalyzer unit provides real-time logging of web, FTP and email traffic
through content logs.The content viewer provides a real-time display of
meta-information from registered devices. Meta-information includes where the
information is coming from and going to. For example, HTTP content includes the
source IP address and the destination URL to allow you to follow real-time trends
in network usage.
Log Aggregation
Log aggregation is a method of collating log data from remote FortiAnalyzer units
or other third party network devices that support the syslog format to a central
FortiAnalyzer unit. For example, a company may have a headquarters and a
number of branch offices. Each branch office has a FortiGate unit and a
FortiAnalyzer-100A/100B to collect local log information. The headquarters has a
FortiAnalyzer-2000 as the central log aggregator.
Quarantine
For FortiGate units that do not have a hard disk, the FortiAnalyzer unit offers the
ability to quarantine infected or suspicious files entering your network
environment. Use the quarantine browser on the FortiAnalyzer unit to view the
files to determine whether they are dangerous or not. Set the option on the
FortiGate unit to send the quarantined files to the FortiAnalyzer unit.
Network Attached Storage
The FortiAnalyzer unit also acts as a Network Attached Storage (NAS) device.
Use the FortiAnalyzer unit as a means of backing up or storing important
information or using the extra hard disk space as a file server or repository. Any
computer using NFS or Windows sharing can mount the FortiAnalyzer hard drive
to save and retrieve files.
About this guide
This guide describes how to set up, configure and use the FortiAnalyzer unit to
collect logs and generate reports on network use.
This guide has the following sections:
Installing the FortiAnalyzer unit describes how to set up and install the
FortiAnalyzer unit in your network environment.
Configure the FortiAnalyzer unit describes how to configure the FortiAnalyzer
system settings, such as system time, session information, and user
management.
FortiAnalyzer Version 3.0 MR3 Administration Guide
16 05-30003-0082-20060925
FortiAnalyzer documentation Introduction
Devices describes how to add and configure FortiGate, FortiManager units and
Syslog servers so that the FortiAnalyzer unit can maintain a connection with
the device.
Alerts describes how to set up alert messages and configure the FortiAnalyzer
unit to send messages via email through a mail server, to a syslog server or
using SNMP traps. This chapter also lists the SNMP traps supported by the
FortiAnalyzer unit.
Traffic summary and security events describes how to configure and view
reports on intrusion attempts against your network as well as viewing the types
of traffic occurring on your network.
Content archive describes how to monitor metadata content for all users using
email, FTP, Instant Messages and web browsing.
Logs describes how to select and view device and FortiAnalyzer log files. It
also describes customizing the log views using filters and columns settings to
find information in the logs easier, as well as watch logs in real time.
Quarantine describes how to configure the FortiAnalyzer unit to receive
quarantined files from a FortiGate unit and view them on the FortiAnalyzer
hard disk.
Vulnerability scan describes how to set up vulnerability scans and view the
generated reports.
Reports describes how to create report profiles for running regular reports on
the log information collected by the FortiAnalyzer unit. It also describes how to
view the generated reports.
Network Analyzer describes how to connect the FortiAnalyzer unit to a SPAN
or mirror port on a network switch to analyze, or sniff, the network traffic
passing through it.
Forensic Analysis describes how to view and report on an individuals network
habits and activities and generate reports for analysis.
FortiAnalyzer documentation
FortiAnalyzer Administration Guide
Describes how to install and configure a FortiAnalyzer unit to collect FortiGate,
and Syslog log files, and connect to a FortiManager device for management
purposes. It also describes how to view log files, generate and view reports on
various network activities, and use the FortiAnalyzer unit as a NAS server.
FortiAnalyzer CLI Reference
Describes how to use the command line interface of the FortiAnalyzer unit, and
describes all the commands available.
FortiAnalyzer online help
Provides a searchable version of the Administration Guide in HTML format.
You can access online help from the web-based manager as you work.
FortiAnalyzer QuickStart Guides
Explains how to install and set up the FortiAnalyzer unit.
Introduction Customer service and technical support
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 17
Fortinet Tools and Documentation CD
All Fortinet documentation is available from the Fortinet Tools and Documentation
CD shipped with your Fortinet product. The documents on this CD are current at
shipping time. For up-to-date versions of Fortinet documentation see the Fortinet
Technical Documentation web site at http://docs.forticare.com.
Fortinet Knowledge Center
The knowledge center contains short how-to articles, FAQs, technical notes,
product and feature guides, and much more. Visit the Fortinet Knowledge Center
at http://kc.forticare.com.
Comments on Fortinet technical documentation
Please send information about any errors or omissions in this document, or any
Fortinet technical documentation, to techdoc@fortinet.com.
Customer service and technical support
Fortinet Technical Support provides services designed to make sure that your
Fortinet systems install quickly, configure easily, and operate reliably in your
network.
Please visit the Fortinet Technical Support web site at http://support.fortinet.com
to learn about the technical support services that Fortinet provides.
FortiAnalyzer Version 3.0 MR3 Administration Guide
18 05-30003-0082-20060925
Customer service and technical support Introduction
Installing the FortiAnalyzer unit Planning the installation
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 19
Installing the FortiAnalyzer unit
This section describes the FortiAnalyzer hardware and how to connect the
FortiAnalyzer unit to the network. This section includes the following topics:
Planning the installation
Connecting the FortiAnalyzer unit
Configuring the FortiAnalyzer unit
Upgrading the FortiAnalyzer firmware
Backing up the FortiAnalyzer hard disk
Shutting down the FortiAnalyzer unit
Planning the installation
You can add the FortiAnalyzer unit to your local network to receive log message
packets from FortiGate and Syslog devices.
You can connect the FortiAnalyzer unit locally or remotely through the Internet. To
connect the FortiAnalyzer unit to devices remotely, you must configure the DNS
server and the default gateway. To manage the FortiAnalyzer unit, you can use a
computer within the local network or over the Internet.
Figure 1: FortiAnalyzer connection option
Internet
FortiAnalyzer Version 3.0 MR3 Administration Guide
20 05-30003-0082-20060925
Connecting the FortiAnalyzer unit Installing the FortiAnalyzer unit
Connecting the FortiAnalyzer unit
You can install the FortiAnalyzer unit as a free-standing appliance on any stable
surface. You can also mount the FortiAnalyzer-800, FortiAnalyzer-2000 and
FortiAnalyzer-4000/4000A onto a rack unit.
Environmental specifications
Operating temperature: 41 to 95F (5 to 35C)
If you install the FortiAnalyzer unit in a closed or multi-unit rack assembly, the
operating ambient temperature of the rack environment may be greater than
room ambient temperature. Therefore, make sure to install the equipment in an
environment compatible with the manufacturer's maximum rated ambient
temperature.
Storage temperature: -4 to 176F (-20 to 80C)
Humidity: 10 to 90% non-condensing
Air flow
For rack installation, make sure that the amount of air flow required for safe
operation of the equipment is not compromised.
For free-standing installation, make sure that the appliance has at least 1.5 in.
(3.75 cm) of clearance on each side to allow for adequate air flow and cooling.
Mechanical loading
You can mount the FortiAnalyzer-800, FortiAnalyzer-2000 and
FortiAnalyzer-4000/4000A units in a standard 19-inch rack. The FortiAnalyzer-800
requires 1U of vertical space and the FortiAnalyzer-2000 and
FortiAnalyzer-4000/4000A requires 2U of vertical space in the rack.
For rack installation, ensure an even mechanical loading of the FortiAnalyzer-800,
FortiAnalyzer-2000 and FortiAnalyzer-4000/4000A to avoid a hazardous
condition.
Connecting to the network
To connect the FortiAnalyzer unit to the network
1 Place the unit on a stable surface, or in a 19-inch rack unit.
2 Make sure the power of the unit is turned off.
3 Connect the network cable to the LAN or Port 1 interface.
4 Connect the power cable to a power outlet.
5 Turn on the power switch.
Note: The FortiAnalyzer unit may overload your supply circuit and impact your surge
protection and supply wiring. Use appropriate equipment nameplate ratings to address this
concern.
Make sure that the FortiAnalyzer unit has reliable grounding. Fortinet recommends direct
connections to the branch circuit.
Installing the FortiAnalyzer unit Configuring the FortiAnalyzer unit
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 21
Configuring the FortiAnalyzer unit
Use the web-based manager or the Command Line Interface (CLI) to configure the
FortiAnalyzer unit IP address, netmask, DNS server IP address, and default gateway IP
address.
Table 1: FortiAnalyzer-100A and FortiAnalyzer-100B factory defaults
Administrator
account
User name: admin
Password: (none)
Port 1
IP: 192.168.1.99
Netmask: 255.255.255.0
Management Access: HTTP, HTTPS, PING, SSH
Port 2
IP: 192.168.2.99
Netmask: 255.255.255.0
Management Access: HTTP, HTTPS, PING, SSH
Port 3
IP: 192.168.3.99
Netmask: 255.255.255.0
Management Access: HTTP, HTTPS, PING, SSH
Port 4
IP: 192.168.4.99
Netmask: 255.255.255.0
Management Access: HTTP, HTTPS, PING, SSH
Table 2: FortiAnalyzer-400 factory defaults
Administrator
account
User name: admin
Password: (none)
Port 1
IP: 192.168.1.99
Netmask: 255.255.255.0
Management Access: HTTP, HTTPS, PING, SSH
Port 2
IP: 192.168.2.99
Netmask: 255.255.255.0
Management Access: HTTP, HTTPS, PING, SSH
Port 3
IP: 192.168.3.99
Netmask: 255.255.255.0
Management Access: HTTP, HTTPS, PING, SSH
FortiAnalyzer Version 3.0 MR3 Administration Guide
22 05-30003-0082-20060925
Configuring the FortiAnalyzer unit Installing the FortiAnalyzer unit
Table 3: FortiAnalyzer-800 factory defaults
Administrator
account
User name: admin
Password: (none)
Port 1
IP: 192.168.1.99
Netmask: 255.255.255.0
Management Access: HTTP, HTTPS, PING, SSH
Port 2
IP: 192.168.2.99
Netmask: 255.255.255.0
Management Access: HTTP, HTTPS, PING, SSH
Table 4: FortiAnalyzer-2000 factory defaults
Administrator
account
User name: admin
Password: (none)
Port 1
IP: 192.168.1.99
Netmask: 255.255.255.0
Management Access: HTTP, HTTPS, PING, SSH
Port 2
IP: 192.168.2.99
Netmask: 255.255.255.0
Management Access: HTTP, HTTPS, PING, SSH
Port 3
IP: 192.168.3.99
Netmask: 255.255.255.0
Management Access: HTTP, HTTPS, PING, SSH
Port 4
IP: 192.168.4.99
Netmask: 255.255.255.0
Management Access: HTTP, HTTPS, PING, SSH
Table 5: FortiAnalyzer-4000/4000A factory defaults
Administrator
account
User name: admin
Password: (none)
Port 1
IP: 192.168.1.99
Netmask: 255.255.255.0
Management Access: HTTP, HTTPS, PING, SSH
Port 2
IP: 192.168.2.99
Netmask: 255.255.255.0
Management Access: HTTP, HTTPS, PING, SSH
Installing the FortiAnalyzer unit Configuring the FortiAnalyzer unit
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 23
Using the web-based manager
The web-based manager provides a GUI interface to configure and administer the
FortiAnalyzer unit.
Use the web-based manager to:
configure most FortiAnalyzer settings
monitor the status of the FortiAnalyzer unit
configure and view reports
view log files and messages
administer users, groups and set access rights.
You can configure and manage the FortiAnalyzer unit using a secure HTTPS
connection from any computer running Internet Explorer 6.0 or other current
browser.
Configuration changes made using the web-based manager are effective
immediately without resetting the firewall or interrupting service.For all
FortiAnalyzer models, use the following procedure to connect to the web-based
manager for the first time.
To connect to the web-based manager, you need:
An Ethernet connection between the FortiAnalyzer unit and management
computer.
Internet Explorer version 6.0 or higher or other current popular web browser on
the management computer.
To connect to the web-based manager
1 Connect the Port1 interface of the FortiAnalyzer unit to the Ethernet port of the
management computer.
2 Use a cross-over Ethernet cable to connect the devices directly. Use
straight-through Ethernet cables to connect the devices through a hub or switch.
3 Configure the management computer to be on the same subnet as the
FortiAnalyzer LAN interface.
4 To do this, change the IP address of the management computer to 192.168.1.2
and the netmask to 255.255.255.0.
5 To access the FortiAnalyzer web-based manager, start your browser and browse
to https://192.168.1.99 (remember to include the s in https://).
6 Type admin in the Name field and select Login.
After connecting to the Web-based manager, you can configure the FortiAnalyzer
unit IP address, DNS server IP address, and default gateway to connect the
FortiAnalyzer unit to the network.
To configure the FortiAnalyzer unit using the web-based manager
1 In the web-based manager, go to System > Network > Interface.
2 Select Edit for Port1.
3 Enter the IP address and netmask and select OK.
If the FortiAnalyzer unit will be connected to the internet:
4 Go to System > Network > DNS.
FortiAnalyzer Version 3.0 MR3 Administration Guide
24 05-30003-0082-20060925
Configuring the FortiAnalyzer unit Installing the FortiAnalyzer unit
5 Enter the, primary DNS server IP address, secondary DNS server IP address
(optional).
6 Select Apply.
7 Got to System > Network > Routing.
8 Select Create New and add the default gateway IP address and any other routes
as required.
9 Select OK.
Using the command line interface
You can also use terminal emulation software to connect to the command line
interface (CLI) from any network that is connected to the FortiAnalyzer unit,
including the Internet. This applies to all FortiAnalyzer models.
You can also access the FortiAnalyzer-100A/100B, FortiAnalyzer-800 and
FortiAnalyzer-4000/4000A CLI by using the null-modem cable provided to connect
to the units console port.
The CLI supports the same configuration and monitoring functionality as the
web-based manager.
To connect to the FortiAnalyzer unit through the console
1 Use a null-modem cable to connect the serial port on the
FortiAnalyzer-100A/100B, FortiAnalyzer-800 and FortiAnalyzer-4000/4000A to
the management computer serial port.
2 Start a terminal emulation program (such as HyperTerminal) on the management
computer. Use these settings:
Baud Rate (bps) 9600
Data bits 8
Parity None
Stop bits 1
Flow Control None.
3 At the login: prompt, type admin and press Enter twice.
4 (The login prompt is preceded by the server IP address.)
After connecting to the CLI, you can configure the unit IP address, DNS server IP
address, and default gateway to connect the FortiAnalyzer unit to the network.
To configure the FortiAnalyzer unit using the CLI
1 Set the IP address and netmask of the LAN interface:
config system interface
edit port1
set ip <ip_address><netmask>
end
2 Confirm that the address is correct:
get system interface
Installing the FortiAnalyzer unit Upgrading the FortiAnalyzer firmware
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 25
3 Set the primary and optionally the secondary DNS server IP address:
config system dns
set primary <dns-server_ip>
set secondary <dns-server_ip>
end
4 Set the default gateway:
config system route
edit 1
set device port1
set dst <destination_ip><netmask>
set gateway <gateway_ip>
end
Using the front panel buttons and LCD
You can use the front panel buttons on the FortiAnalyzer-400 and
FortiAnalyzer-800 to set up the units IP address, netmask, and default gateway.
On the FortiAnalyzer-2000, use the up and down arrow buttons to cycle through
the options and enter the IP address information, and select Enter to select a
menu option or number in the IP address.
Upgrading the FortiAnalyzer firmware
Upgrade the FortiAnalyzer firmware using the instructions in the topic Changing
the firmware on page 35. Ensure you backup all configuration settings and log
files before upgrading the firmware.
Press the cycle button to cycle through options and select the IP
address information.
Press the enter button to select a menu option or number in the IP
address.
Note: If you are upgrading from FortiAnalyzer firmware version 0.8, the file system has
changed. After upgrading the firmware, all log data will be destroyed. Ensure you backup all
log information before proceeding with the upgrade. When upgrading from FortiLog 0.8 to
FortiAnalyzer 3.0, the FortiAnalyzer hard disks must be reformatted.
To format the hard disk, go to System > Dashboard. Select Format Log Disks for the
System Operation.
FortiAnalyzer Version 3.0 MR3 Administration Guide
26 05-30003-0082-20060925
Backing up the FortiAnalyzer hard disk Installing the FortiAnalyzer unit
Backing up the FortiAnalyzer hard disk
Before upgrading the FortiAnalyzer firmware, formatting the log disk or changing
the RAID configuration (on a FortiAnalyzer-400, FortiAnalyzer-800,
FortiAnalyzer-2000 and FortiAnalyzer-4000/4000A), it is extremely important that
you back up the log data first. Using the CLI, you can perform a global backup of
all log information to an FTP server.
To backup the log information on the FortiAnalyzer hard disk, use the CLI to enter
the following command:
execute backup logs <ftp_ip_address> <ftp_username>
<ftp_password> <ftp_dir>
Once the firmware upgrade or the RAID configuration is complete, you can restore
the log information to the FortiAnalyzer hard disk.
execute restore logs <device> <ftp_ip_address>
<ftp_username> <ftp_password> <ftp_dir>
Shutting down the FortiAnalyzer unit
When powering off the FortiAnalyzer unit, always shut down the unit using the
following procedures before disconnecting the power supply. By not following this
procedure you risk damaging the FortiAnalyzer hard disk.
To power off the FortiAnalyzer unit
1 From the web-based manager, go to System > Dashboard.
2 In the System Operation list, select Shut Down and select Go.
OR
from the CLI, enter:
execute shutdown
3 Disconnect the power supply.
Note: In the case of changing RAID configurations and formatting log disks, this command
is designed to backup and restore all logs from the FTP server.
Note: Before using the restore CLI command, ensure you add the devices for the logs first.
The command will not function without the devices to associate with the logs. For details on
adding devices, see the chapter Devices on page 65.
Configure the FortiAnalyzer unit Dashboard
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 27
Configure the FortiAnalyzer unit
The FortiAnalyzer unit provides a number of configuration options to customize
the FortiAnalyzer unit using the System settings.
This section describes the configuration settings you can apply to use the
FortiAnalyzer in your network environment.
This section includes the following topics:
Dashboard
Network settings
Administrator settings
Network sharing
Configuring the FortiAnalyzer unit
Maintenance
RAID levels
Dashboard
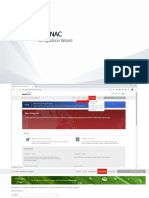
The system dashboard provides a view of the current operating status of the
FortiAnalyzer unit. All FortiAnalyzer administrators with read access to system
configuration can view system status information.
Figure 2: FortiAnalyzer-400 dashboard
Connect to the web-based manager to view the current system status of the
FortiAnalyzer unit, and modify the system information. The status information that
appears includes the system information, alert messages, system resources,
license information and session statistics.
FortiAnalyzer Version 3.0 MR3 Administration Guide
28 05-30003-0082-20060925
Dashboard Configure the FortiAnalyzer unit
System Information
The System Information area of the Dashboard displays the current state of the
FortiAnalyzer unit. The System Status area includes the following information:
System Resources
The system resources displays how the FortiAnalyzer units resources are being
used. You can monitor the CPU, memory and hard disk use and quickly see at
what capacity the FortiAnalyzer unit is running. System resources includes the
following information:
Serial Number The serial number of the FortiAnalyzer unit. The serial number is
unique to the FortiAnalyzer unit and does not change with
firmware updates. Use this number when registering your
FortiAnalyzer unit with Fortinet.
Uptime The time in days, hours and minutes since the FortiAnalyzer was
started or last rebooted.
System Time The current time according to the FortiAnalyzer internal clock.
Select Change to change the time or configure the FortiAnalyzer
unit to obtain the time from an NTP server. For details see Setting
the time on page 32.
Host Name The name of the FortiAnalyzer unit. For details on changing the
name see Changing the host name on page 36.
Firmware Version The version of the firmware installed on the FortiAnalyzer unit.
Select Update to upload a new version of the firmware. For details
on updating the firmware see Changing the firmware on
page 35.
CPU Usage The current CPU status. The web-based manager displays CPU
usage for core processes only. CPU usage for management
processes (for example, for HTTPS connections to the web-based
manager) is excluded.
Memory Usage The current memory status. The web-based manager displays
memory usage for core processes only. Memory usage for
management processes (for example, for HTTPS connections to
the web-based manager) is excluded.
Hard Disk Usage /
RAID status
For the FortiAnalyzer-100 and FortiAnalyzer-100A/100B, the
current status of the hard disk. The web-based manager displays
the amount of hard disk space used.
For the FortiAnalyzer-400, FortiAnalyzer-800, FortiAnalyzer-2000
and FortiAnalyzer-4000/4000A, the current RAID status of the
hard disks. Each circle indicates the status of a hard disk. Green
indicates the hard disk is functioning normally. If the disk is
flashing red and yellow, there is a problem with the hard disk.
The hard disks on the FortiAnalyzer-2000 and
FortiAnalyzer-4000/4000A are hot swappable. For details see Hot
swapping the FortiAnalyzer-2000 and FortiAnalyzer-4000/4000A
on page 62.
History icon Select History to view a graphical representation of the last minute
of CPU, memory, sessions, and network usage. For more
information see Viewing operational history on page 30.
Configure the FortiAnalyzer unit Dashboard
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 29
License Information
Alert Message Console
The Alert display shows alert messages for the FortiAnalyzer and connected
FortiGate units. The Alerts display shows hard disk failure messages, virus
outbreak, or suspicious event warnings. To view all the alert messages recorded
by the FortiAnalyzer unit, select More Alerts. For details on viewing alert
messages see Viewing Alert messages on page 31.
Statistics
Report Engine
The Report Engine display shows the FortiAnalyzer report generation activity. The
report engine activity information includes whether the report engine is active or
inactive, what reports are running when active and the percentage completed.
Select the Generate report button to create a new report profile.
Automatic Refresh Interval
Select how often the Status page automatically updates. Select Refresh Now to
update the status page immediately.
System Operation
Perform the following operations from the Status page. These options are not
available if your access privileges include write permissions.
Support Contract The support contract number and expiry date.
RVS Engine The version of the RVS engine. Select Update to upload a new
version of the engine.
This feature is not available on the FortiAnalyzer-100.
RVS Plug-ins The version of the RVS plug-in.
This feature is not available on the FortiAnalyzer-100.
Device License A listing of the number of devices connected to the FortiAnalyzer
unit.
Registered is the number of devices added to the FortiAnalyzer
unit.
Unregistered is the number of devices attempting to connect to
the FortiAnalyzer unit that need configuring. To configure the
FortiAnalyzer unit to accept logs from a device see Devices List
on page 65.
Since The date and time when the statistics were last reset.
Connections The number of communication sessions occurring on the
FortiAnalyzer unit. Select Details for more information on the
connections. For details on the session information, see Viewing
Session information on page 30.
Logs & Reports A display of the log file activity and volume delivered to the
FortiAnalyzer unit.
Reboot Restart the FortiAnalyzer unit.
ShutDown Shut down the FortiAnalyzer unit. You can only restart the
FortiAnalyzer unit by turning the power off and then on again.
FortiAnalyzer Version 3.0 MR3 Administration Guide
30 05-30003-0082-20060925
Dashboard Configure the FortiAnalyzer unit
Viewing operational history
The System resource history page displays four graphs representing system
resources and network utilization history, updated every three seconds.
To view the FortiAnalyzer operational history
1 Go to System > Dashboard.
2 Select History in the upper right corner of the System Resources area.
Viewing Session information
Session information displays information about the current communication
sessions on the FortiAnalyzer unit.
To view the session information
1 Go to System > Dashboard.
2 In the Statistics area, select Details for the Connection information.
Format log disks Format the FortiAnalyzer hard disk. Selecting this option will
delete all log files and reports from the hard disk. Ensure that you
back up all information before selecting this option. Formatting the
hard disk will also interrupt FortiAnalyzer operations for several
minutes.
Reset to factory
default
Restart the FortiAnalyzer unit with its original configuration when it
was initially powered on. This will delete all configuration changes
you have made, but does not changes the firmware version. This
also includes resetting the IP address and netmask. You will need
to reconnect to the FortiAnalyzer device using the default IP
address of 192.168.1.99.
CPU Usage The CPU usages for the previous minute.
Memory Usage The memory usages for the previous minute.
Session The session history for the previous minute.
Network utilization The network use for the last minute.
Resolve Host Name Select to display host names by a recognizable name rather than
IP addresses. For details on configuring IP address host names
see IP Aliases on page 53.
Resolve Service Select to display network service names rather than port numbers.
For example, HTTP rather than port 80.
Refresh Time Select the frequency of the refresh of the Connections page to
view the connection activity.
Stop Refresh Select to stop the refreshing of the connections page. To start the
refresh, select a refresh time.
View per page Select the number of rows to display per page.
Page n of n Enter a page number to jump to and press Enter.
Search Enter a keyword to perform a simple search on the session
information available. Select Go to begin the search. The number
of matches appears above the Search field.
Protocol The service protocol of the connection. For example, udp and tcp.
From IP The source IP address of the connection.
From Port The source port of the connection.
To IP The destination IP address of the connection.
Configure the FortiAnalyzer unit Dashboard
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 31
Filtering session information
You can filter the contents to find specific content. Each column of data includes a
gray filter icon. Select the icon to filter the contents of the column.
When applying a column filter, the filter icon appears green.
To turn off the filter, select the filter icon for the column, and select Clear all Filters.
Viewing Alert messages
Alert messages provides a window on what is occurring on the FortiAnalyzer and
other FortiGate devices. It enables you to view issues on your network, including
network attacks and virus warnings. The Alert messages window provides a
complete list of alert messages. You can view the alert messages by level and
delete the messages as required.
To view the alert messages
1 Go to System > Dashboard.
2 Select More Alerts in the upper right corner of the Alert Message Console area.
Figure 3: Alert messages
To Port The destination port of the connection.
Expires (Secs) The time in seconds remaining before the connection terminates.
Page Select the page of alerts to view. Use the arrows to move forward
and back through the pages or enter a page number and press
Enter.
Include...and higher
in alerts
Select an alert level to view. The level you select and those alert
messages higher than selected will appear in the alert list.
Keep
unacknowledged
alerts for
Select the number of previous days of alert messages to display.
Selecting a number of days lower than what you are currently
viewing deletes the older alerts. For example, if you are viewing
alerts for seven days, and change the alerts to two days, the
FortiAnalyzer unit deletes the other five days of alert messages.
Formatted | Raw Select to view the alert messages in a formatted or raw format.
Device The device where the alert message is originating.
Event Details of the event causing the alert message.
Severity The level of the alert message.
Time The date and time of the alert message.
FortiAnalyzer Version 3.0 MR3 Administration Guide
32 05-30003-0082-20060925
Dashboard Configure the FortiAnalyzer unit
Clicking the column headers sorts the information in ascending or descending
order for that column.
Setting the time
Set the system time to ensure effective scheduling and accurate logging of
information. You can either manually set the FortiAnalyzer system time or you can
configure the FortiAnalyzer unit to automatically keep its system time correct by
synchronizing with a Network Time Protocol (NTP) server.
To set the system time, go to System > Dashboard and select Change for the
System Time.
Figure 4: Time Settings
Restore factory default system settings
You can restore the FortiAnalyzer unit to its factory default. This procedure does
not change the firmware version.
Counter The number of occurrences of the alert event.
Delete icon Select the check box for alert messages you want to delete and
select the delete icon.
System Time The current FortiAnalyzer system date and time.
Refresh Update the display of the current FortiAnalyzer system date and
time.
Time Zone Select the current FortiAnalyzer system time zone.
Set Time Select to set the FortiAnalyzer system date and time to the values
you set in the Year, Month, Day, Hour, Minute and Second fields.
Synchronize with
NTP Server
Select to use an NTP server to automatically set the system date
and time. You must specify the server and synchronization interval.
Server Enter the IP address or domain name of an NTP server. To find an
NTP server that you can use, see http://www.ntp.org.
Sync Interval Specify how often the FortiAnalyzer unit should synchronize its time
with the NTP server. For example, a setting of 1440 minutes causes
the FortiAnalyzer unit to synchronize its time once a day.
!
Caution: This procedure deletes all changes you have made to the FortiAnalyzer
configuration and reverts the system to its original configuration, including resetting
interface addresses.
Configure the FortiAnalyzer unit Dashboard
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 33
To restore system settings to factory defaults
1 Go to System > Dashboard.
2 In the System Operations area, select Reset to Factory Default and select Go.
3 Select OK to confirm.
The FortiAnalyzer unit restarts with the configuration it had when it was first
powered on.
Format the log disks
Use the system dashboard to format the FortiAnalyzer log disks. Remember to
back up and log data before formatting the hard disks. The FortiAnalyzer unit is
unavailable for the duration of the format process.
To format the log disks
1 Go to System > Dashboard.
2 In the Systems Operations area, select Format Log Disks and select Go.
3 Select OK to begin the format.
Restoring a FortiAnalyzer unit
Use the following procedure if the FortiAnalyzer unit cannot complete the startup
procedure. When this event occurs, the FortiAnalyzer unit is unresponsive to the
web-based manager or the CLI. The cause may be a corrupted firmware image.
Restoring a FortiAnalyzer-100 or FortiAnalyzer-400
To use the following procedure you must have a TFTP server that the
FortiAnalyzer unit can connect to. The TFTP server IP address must be set to
192.168.1.168.
To upload the firmware image to the FortiAnalyzer unit
1 Make sure the TFTP server is running.
2 Copy the firmware image file to the root directory of the TFTP server. Ensure the
file name is image.out.
3 Start the FortiAnalyzer unit.
As the FortiAnalyzer unit starts, the following message appears on the LCD:
Press any key to begin download.....
4 Immediately press any key to begin the automatic download.
The FortiAnalyzer unit connects to the TFTP server and begins downloading the
firmware image. Once downloaded, the FortiAnalyzer unit loads the firmware and
proceeds with the system startup.
!
Caution: This procedure resets all FortiAnalyzer settings to their default state. This
includes the interface IP addresses, as well as HTTP, HTTPS, SSH, and telnet access.
See Configuring the FortiAnalyzer unit on page 21.
FortiAnalyzer Version 3.0 MR3 Administration Guide
34 05-30003-0082-20060925
Dashboard Configure the FortiAnalyzer unit
Restoring a FortiAnalyzer-100A/100B, 800, 2000 and
4000/4000A
To upload a firmware image to the FortiAnalyzer unit
1 Connect to the CLI using the null-modem cable and FortiAnalyzer console port.
2 Make sure the TFTP server is running.
3 Copy the new firmware image file to the root directory of the TFTP server.
4 To confirm the FortiAnalyzer unit can connect to the TFTP server, use the
following command to ping the computer running the TFTP server. For example, if
the IP address of the TFTP server is 192.168.1.168, enter:
execute ping 192.168.1.168
5 Enter the following command to restart the FortiAnalyzer unit:
execute reboot
As the FortiAnalyzer units starts, a series of system startup messages is
displayed.
When one of the following messages appears:
Press any key to display configuration menu...
Immediately press any key to interrupt the system startup.
If you successfully interrupt the startup process, the following messages appears:
[G]: Get firmware image from TFTP server.
[F]: Format boot device.
[B]: Boot with backup firmware and set as default.
[Q]: Quit menu and continue to boot with default firmware.
[H]: Display this list of options.
Enter G,F,B,Q,or H:
6 Type G to get the new firmware image from the TFTP server.
The following message appears:
Enter TFTP server address [192.168.1.168]:
7 Type the address of the TFTP server and press Enter.
The following message appears:
Enter Local Address [192.168.1.188]:
8 Type an IP address that the FortiAnalyzer unit can use to connect to the TFTP
server.
!
Caution: This procedure resets all FortiAnalyzer settings to their default state. This
includes the interface IP addresses, as well as HTTP, HTTPS, SSH, and telnet access.
See Configuring the FortiAnalyzer unit on page 21.
Note: When connecting the Ethernet cable to the FortiAnalyzer-800, insert the cable into
the LAN2 port.
Configure the FortiAnalyzer unit Dashboard
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 35
9 The IP address can be any IP address that is valid for the network the interface is
connected to. Make sure you do not enter the IP address of another device on this
network.
The following message appears:
Enter File Name [image.out]:
10 Enter the firmware image file name and press Enter.
The TFTP server uploads the firmware image file to the FortiAnalyzer unit and
displays the following message:
Save as Default firmware/Backup firmware/Run image without
saving:[D/B/R]
11 Type D.
The FortiAnalyzer unit installs the new firmware image and restarts.
Changing the firmware
Use the following procedure to upgrade the FortiAnalyzer unit to a newer firmware
version or revert to a previous firmware version.
If you are reverting to a previous firmware version, the procedure reverts the
FortiAnalyzer unit to its factory default configuration.
When you upgrade the firmware, the FortiAnalyzer unit maintains the your
configuration settings.
Back up the FortiAnalyzer unit configuration before beginning this procedure. For
information, see Backup & Restore on page 57.
To change the firmware using the web-based manager
1 Copy the firmware image file to your management computer.
2 Log on to the web-based manager as the administrative user.
3 Go to System > Dashboard.
4 Select Update in the System Information area.
5 Type the path and file name of the firmware image file, or select Browse and
locate the firmware image file.
6 Select OK.
If you are reverting to a previous version of the firmware, a message appears
informing you the system configuration will be set to default and all the original
configuration will be lost.
7 Select OK.
If you upgrade the firmware, the FortiAnalyzer unit uploads the firmware image
file, upgrades to the new firmware version, restarts, and displays the
FortiAnalyzer login. This process takes a few minutes.
Note: If you revert to a previous firmware version, because the configuration is reset, you
will need to reconfigure the IP address from the front panel of the FortiAnalyzer-100 and
FortiAnalyzer-400, and the console for the FortiAnalyzer-800 and
FortiAnalyzer-100A/100B.
FortiAnalyzer Version 3.0 MR3 Administration Guide
36 05-30003-0082-20060925
Network settings Configure the FortiAnalyzer unit
If you revert to a previous firmware version, the FortiAnalyzer unit uploads the
firmware image file, reverts to the old firmware version, resets the
configuration, restarts, and displays the FortiAnalyzer unit login. This process
takes a few minutes.
8 Restore your configuration. See Backup & Restore on page 57.
9 Enter the file name or select Browse to locate the signature file and select OK.
Changing the host name
Change the FortiAnalyzer host name to differentiate the FortiAnalyzer from other
FortiAnalyzer units or other devices on your network.
To change the host name
1 Go to System > Dashboard.
2 In the System Information area, select Change for the Host Name.
3 Enter a new name for the FortiAnalyzer unit and select OK. A host name can be
up to 20 characters long.
Network settings
Use the network settings to configure the FortiAnalyzer unit to operate in your
network. Basic network settings include configuring FortiAnalyzer interfaces, DNS
settings and static routes.
Interface
Use the interface configuration to set up the ports on your FortiAnalyzer unit. This
includes the IP address, administrator access and Maximum Transmission Unit
(MTU) settings.
To configure the interfaces of the FortiAnalyzer unit, go to System > Network >
Interface.
Figure 5: FortiAnalyzer-400 interface list
Name The name of the physical port on the FortiAnalyzer unit.
IP/Netmask The IP address and netmask configured for the interface.
Access A list of the administrative access available to the interface.
FDP FortiDiscovery protocol indicator. When FortiDiscovery is enabled
for a port, a green check appears.
Status The status of the port:
a green arrow indicates the port is up. Select Bring Down to
close the port.
a red arrow indicates the port is down. Select Bring up ot open
the port.
Modify Select Modify to change the interface settings.
Configure the FortiAnalyzer unit Network settings
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 37
Changing the interface settings
To change the interface settings
1 Go to System > Network > Interface.
2 Select Modify for the port.
3 Set the following options and select OK:
About FortiDiscovery
FortiDiscovery is a method of FortiGate units running FortiOS 3.0 establishing a
connection to a FortiAnalyzer unit. When a FortiGate administrator selects
Automatic Discovery, the FortiGate unit uses HELLO packets to locate any
FortiAnalyzer units on the network within the same subnet. Once the FortiGate
unit discovers the FortiAnalyzer unit, the fortigate unit automatically enables
logging to the FortiAnalyzer and begins sending log data.
The FortiGate unit will only find the FortiAnalyzer unit when the FortiDiscovery is
enabled on a port on the FortiAnalyzer unit.
Interface name The interface name is hard coded and cannot be changed.
FortiDiscovery
Protocol
Select Enable to use the FortiDiscovery Protocol for the port to
enable FortiGate devices to find the FortiAnalyzer unit
automatically and establish a connection for sending log packets.
See About FortiDiscovery on page 37 for more information.
IP/Netmask Enter an IP address and netmask.
Administrative
Access
Configure administrative access to an interface to control how
administrators access the FortiAnalyzer unit and the FortiAnalyzer
interfaces that administrators can connect to. Select from the
following administrative access options:
HTTPS to allow secure HTTPS connections to the web-based
manager through this interface.
PING to enable the interface to respond to pings. Use this
setting to verify your installation and for testing.
HTTP to allow HTTP connections to the web-based manager
through this interface. HTTP connections are not secure and
can be intercepted by a third party.
SSH to allow SSH connections to the CLI through this
interface.
TELNET to allow Telnet connections to the CLI through this
interface. Telnet connections are not secure and can be
intercepted by a third party.
AGREGGATOR to set the port to be the sender or receiver of
log aggregation transmissions. For more information on
aggregation see Log Aggregation on page 51.
MTU To improve network performance, you can change the maximum
transmission unit (MTU) of the packets that the FortiAnalyzer unit
transmits from any physical interface. Ideally, this MTU should be
the same as the smallest MTU of all the networks between the
FortiAnalyzer unit and the destination of the packets. If the
packets that the FortiAnalyzer unit sends are larger, they are
broken up or fragmented, which slows down transmission.
Experiment by lowering the MTU to find an MTU size for best
network performance.
To change the MTU, select Override default MTU value (1500)
and enter the maximum packet size.
FortiAnalyzer Version 3.0 MR3 Administration Guide
38 05-30003-0082-20060925
Network settings Configure the FortiAnalyzer unit
DNS
Configure the primary and secondary DNS settings.
To configure network settings, go to System > Network > DNS.
Routing
The Route list displays information that the FortiAnalyzer unit compares to
packets headers in order to route packets, and enables you to add static routes to
the FortiAnalyzer unit.
To view the routing list, go to System > Network > Routing.
Figure 6: FortiAnalyzer routing list
Adding a route
A static route provides the FortiAnalyzer unit with the information it needs to
forward a packet to a particular destination other than the default gateway.
To add a static route
1 Go to System > Network > Routing.
2 Select Create New.
3 Set the following options and select OK:
Primary DNS Server Enter the primary DNS server IP address that the FortiAnalyzer
unit can connect to. Several of the FortiAnalyzer functions use
DNS.
Secondary DNS
Server
Enter a secondary DNS server IP address.
Destination
IP/Netmask
The destination IP address and netmask of packets that the
FortiAnalyzer unit wants to send to.
Gateway The IP addresses of a router where the FortiAnalyzer unit
forwards the packet.
Interface The names of the FortiAnalyzer interfaces through which
intercepted packets are received and sent.
Modify Select to change the route configuration settings.
Create New Add a route to the route list.
Destination IP Enter the destination IP address network mask of packets that the
FortiAnalyzer unit has to intercept.
Mask Enter a netmask to associate with the IP address.
Gateway Enter the IP address of the gateway where the FortiAnalyzer unit
will forward intercepted packets.
Interface Select a port from the list of available ports.
Configure the FortiAnalyzer unit Administrator settings
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 39
Administrator settings
Use the Admin option to configure and maintain FortiAnalyzer administrators,
administrator domains (ADOMs), set a users administrative access and maintain
passwords.
When the FortiAnalyzer unit is initially installed, it is configured with a single
master administrator account with the user name of admin. From this account,
you can add and edit administrator accounts, control the access level of each
administrator account and control the IP address for connecting to the
FortiAnalyzer unit. This account is permanent, and cannot be deleted from the
FortiAnalyzer unit.
Adding a new administrator
To view a list of administrators for the FortiAnalyzer unit, go to System > Admin >
Administrators.
Figure 7: Listing of FortiAnalyzer administrators
To add a new administrator
1 Go to System > Admin > Administrators.
2 Select Create New.
3 Configure the following options and select OK
Name The assigned name for the administrator.
Trusted Hosts The IP address where the administrator can log into the
FortiAnalyzer unit. Using an IP address and netmask of 0.0.0.0
enables the administrator to access the FortiAnalyzer unit from
any address.
Profile The access profile assigned to the administrator.
Type Type can be either local, as a configured administrator on the
FortiAnalyzer unit or Radius if you are using a Radius server on
your network.
Delete icon Select to remove the administrator entry. You cannot delete the
admin account.
Edit icon Select to modify the Administration information.
Change Password
icon
Select to change the administrator password. For more
information, see Changing the administrator password on
page 40.
Delete
Edit
Change Password
Administrator Enter the administrator name.
Remote Auth Select if you are using a Radius server group on your network.
Password Enter a password. For security reasons, a password should be a
mixture of letters and numbers and is longer than six characters.
Confirm Password Re-enter the password.
FortiAnalyzer Version 3.0 MR3 Administration Guide
40 05-30003-0082-20060925
Administrator settings Configure the FortiAnalyzer unit
Changing the administrator password
The admin administrator and administrators with read and write permissions can
change their administrator account passwords. Administrators with read only
permissions must get their passwords changed by the admin administrator.
To change the administrator account password
1 Go to System > Admin > Administrators.
2 Select the Change Password Icon in the Action column.
3 Enter the old password for confirmation.
4 Enter the new password and confirm it by entering it again.
5 Select OK.
Access Profile
An Access Profile is the group of access rights assigned to an administrator. You
can create any number of access profiles that you assign to administrators. For
each profile, you can define what access privileges are granted. For example, you
can have a profile where the administrator only has read and write access to the
reports, or assign read-only access to the content archive logs. Only one access
profile can by assigned to any given administrator.
User information Enter the administrator name, email and other contact
information.
Trusted Host Enter the IP address where the administrator can log into the
FortiAnalyzer unit.
If you want the administrator to be able to access the
FortiAnalyzer unit from any address, use the IP address 0.0.0.0
and netmask 0.0.0.0. To limit the administrator to only access the
FortiAnalyzer unit from a specific network, enter that networks IP
and netmask.
Access Profile Select an access profile from the list. You define the administrative
access permissions and save them as access profiles. For more
information, see Access Profile on page 40.
Configure the FortiAnalyzer unit Administrator settings
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 41
Figure 8: FortiAnalyzer access privileges
Only the admin administrator has access to the Global Configuration of a
FortiAnalyzer unit. Every other administrator must be assigned an access profile.
To create an access profile
1 Go to System > Admin > Access Profile.
2 Select Create New.
3 Enter a name for the profile.
4 Select a filter for each option:
Auth Groups
The Auth Groups page enables you to group RADIUS servers in to logical
arrangements. To add a group you must first have at least one RADIUS server
configured.
To add a group
1 Go to System > Admin > Auth Groups.
2 Select Create New.
3 Select the servers to add to the group and select the right arrow.
4 Select OK.
None The administrator has no access to the function.
Read Only The administrator can view pages, menus and information, but
cannot modify any settings.
Read-Write The administrator can view pages, menus and information as well
as change configurations.
FortiAnalyzer Version 3.0 MR3 Administration Guide
42 05-30003-0082-20060925
Administrator settings Configure the FortiAnalyzer unit
RADIUS Server
Add RADIUS servers to the FortiAnalyzer unit for administrator authorization.
To add a RADIUS server
1 Go to System > Admin > RADIUS Servers.
2 Select Create New.
3 Configure the following and select OK:
Administrator Settings
Administrator settings enable you to configure the idle time when the
FortiAnalyzer unit logs out an administrator, the language for the web-based
manager and to enable administrative domains.
To configure administrators, go to System > Admin.
Figure 9: Administrators settings
Monitor
The Monitor page enables the admin account to view other administrators
currently logged in to the FortiAnalyzer unit. The admin account can disconnect
other administrators, should the need arise.
To monitor current administrators go to System > Admin > Monitor.
Name Enter a name to identify the server.
Server IP/Name Enter the IP address for the server.
Shared Secret Enter the password for the server.
Note: Only the admin user can add or change administrator account information.
Idle Timeout Set the idle timeout to control the amount of inactive time before
the administrator must log in again. To improve security keep the
idle timeout to a low value, for example five minutes.
Web Administration
Language
Set the language for the web-based manager.
Admin Domain
Configuration
Select to enable administrative domains (ADOMs). For more
information on ADOMs, see Administrative domains on page 43.
If you want to disable the ADOM feature, you must first delete all
ADOM entries from the FortiAnalyzer unit. Until you do this, the
Admin Domain Configuration option will not appear in this window.
Note that the Admin Domain Configuration option is not available
on the FortiAnalyzer-100 or FortiAnalyzer-100A/100B.
Configure the FortiAnalyzer unit Administrative domains
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 43
To disconnect an administrator, select a check box next to the administrator name
and selecting Disconnect.
Administrative domains
Administrative Domains (ADOMs) enable the FortiAnalyzer administrator to
create and manage access for multiple domains, and can comprise multiple
devices on a single device. The admin administrator can configure administrative
profiles to grant administrators access to specific log data, reports, alerts, and
options and menus in the web-based manager.
Each ADOM is independent of other domains in the system. When the
FortiAnalyzer administrator assigns customers separate and unique ADOMs,
administrators or users on each ADOM will not be aware of other devices or
ADOMs on the FortiAnalyzer unit.
Similar to the web-based manager, users who access the CLI for their ADOM are
not able to see data or configuration settings for other ADOMs.
Enabling administrative domains
Using the default admin account, you can enable multiple ADOM operation on the
FortiAnalyzer unit.
To enable administrative domains
1 Go to System > Admin > Settings.
2 Select Admin Domain Configuration.
3 Select OK.
The FortiAnalyzer logs you out. You can now log in again as admin. When you log
in as admin with Admin Domain Configuration enabled, you see the Administrative
Domain Configuration page.
The default domain is the Global Configuration, which grants access to all
devices, data and reports on the FortiAnalyzer unit. You must enable
administrative domains to configure access privileges for ADOMs.
Figure 10: The Administrative Domain Configuration page
Note: Administrative Domains are not available on the FortiAnalyzer-100 or
FortiAnalyzer-100A/100B.
FortiAnalyzer Version 3.0 MR3 Administration Guide
44 05-30003-0082-20060925
Administrative domains Configure the FortiAnalyzer unit
After enabling the Admin Domain Configuration, the web-based manager and CLI
display the following changes:
Global and ADOM configurations are separated
Only the admin administrator has access to the Global Configuration
The admin account can configure all ADOM configurations
Administrators can see and configure only options defined in their
administrative profiles
Disabling administrative domains
Should you decide to turn off the ADOM setting, you must first remove any
ADOMs created. If any ADOMs, excluding the root domain, remain, the option to
unset the ADOM option will not appear.
To disable the ADOM feature
1 Go to System > Admin > Settings.
2 Select Admin Domain Configuration to clear the check box.
3 Select OK.
Configuring ADOM settings
The default configuration of a FortiAnalyzer contains only the Global
Configuration. You must create and configure new ADOMs.
When Admin Domain Configuration is enabled, only the default admin
administrator account can:
configure global settings
create or delete ADOMs
configure multiple ADOMs
assign interfaces to ADOMs
assign an administrator to an ADOM
Configuring ADOM settings includes the following steps:
Creating a new ADOM
Creating an Access Profile
Adding a new administrator and assigning an ADOM and access profile to the
administrator
Adding a device to an ADOM
Global Configuration The admin administrator can access the global configuration.
Select Main Menu to return to the Admin Domain Configuration
page.
Create New Create a new ADOM.
Delete Delete the selected ADOM.
Selection Enable to select the ADOM for deletion.
Name The name of the ADOM.
Select the name to configure the ADOM.
Select Main Menu item to return to the Admin Domain
Configuration page.
Configure the FortiAnalyzer unit Network sharing
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 45
Creating a new ADOM
Creating a new ADOM will enable the FortiAnalyzer administrator to configure
access privileges for a group of administrators and users.
To create a new ADOM
1 Select Main Menu.
2 Select Create New.
3 Enter a name for the new ADOM.
4 Select OK.
Adding a device to an ADOM
An ADOM can include multiple devices. Users of an ADOM can access
information such as logs and alerts, and change configurations for devices on
their ADOM according to their access profile.
To add a device to an ADOM
1 Go to Device > All > Device.
2 Select Edit for the device you want to add to the ADOM.
3 Select the Administrative Domain.
Network sharing
Users can save, store and access information on the FortiAnalyzer hard disk as
an alternate means of storing important files and work. Users can also access the
reports and logs saved on the FortiAnalyzer hard disk.
Use network sharing to configure users and user access to the FortiAnalyzer
folders and files on its hard disk and set file properties.
When users connect to the FortiAnalyzer unit, consider the following:
Microsoft Windows users connect to the FortiAnalyzer hard disk by mapping a
drive letter to a network folder.
For Macintosh users, enable the FortiAnalyzer Windows networking selection.
Macintosh users can use the SMB sharing protocol to connect to the
FortiAnalyzer unit.
UNIX or Linux users:
mount the FortiAnalyzer hard disk as smbfs if you are using Windows
Networking.
mount the FortiAnalyzer hard disk as nfs if you select Network File System.
Before a user can access files on the FortiAnalyzer hard disk, create user and
group accounts and set their access permissions.
FortiAnalyzer Version 3.0 MR3 Administration Guide
46 05-30003-0082-20060925
Network sharing Configure the FortiAnalyzer unit
Adding users
Create user accounts to give users access to the log, reports and hard disk
storage of the FortiAnalyzer unit. Users added will not have administrative access
to the FortiAnalyzer hard disk or FortiAnalyzer unit. To add administrative users
see Administrator settings on page 39.
To add a user account
1 Go to System > Network Sharing > User.
2 Select Create New.
3 Enter the following information for the user account and select OK:
Adding groups
Create user groups to maintain directory access to a large number of users at
once.
To add a user group
1 Go to System > Network Sharing > Group.
2 Select Create New.
3 Enter the following information for the group account:
4 Select the users from the Available Users area and select the Right arrow to add
them to the group.
To remove a user, select a user from the Members area and select the Left arrow.
5 Select OK.
Configuring Windows shares
Configure the FortiAnalyzer unit to provide folder and file sharing using Windows
sharing. To view users with Windows share access to the FortiAnalyzer unit, go to
System > Network Sharing > Windows Share.
User name Enter a user name. For example, twhite. The name cannot include
spaces.
UID (NFS only) Enter a user ID.
Use this field only if you are using the NFS protocol. The NFS protocol
uses the UID to determine the permissions on files and folders.
Password Enter a password for the user.
Description Enter a description of the user. For example, the users name or a position
such as IT Manager.
Group Enter a user name. For example, Finance. The name cannot include
spaces.
GID (NFS only) Enter a Group ID. Use this field if you are using Network File System.
Configure the FortiAnalyzer unit Network sharing
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 47
Figure 11: Viewing user access
To configure windows shares
1 Go to System > Network Sharing > Windows Share.
2 Select Enable Windows Network Sharing.
3 Enter a Workgroup name.
4 Select Apply.
Assigning user access
After configuring users and user groups, configure the files and folders the users
can access, and their read and read/write access privileges.
Figure 12: Windows sharing configuration
Local Path The path the user has permission to connect to.
Share as The name of the shared folder or file.
User/Group A list of users or groups that have access to the folder or files.
Permissions Permissions for the user or groups. This can be either Read Only
or Read Write.
Modify Select Edit to change any of the options for file sharing.
Select Delete to remove the file sharing permissions.
Edit
Delete
Local Path
Button
FortiAnalyzer Version 3.0 MR3 Administration Guide
48 05-30003-0082-20060925
Network sharing Configure the FortiAnalyzer unit
To add a new Windows share configuration
1 Go to System > Network Sharing > Windows Share.
2 Select Create New.
3 Select the Local Path button to select the folder for the users or groups to access.
4 Select OK.
5 Enter the Share Name to describe the shared folder.
6 Select user and group names from the Available Users & Groups box. Hold the
Ctrl key to select multiple users or groups.
7 Select the type of access rights the users and groups will have and select the
appropriate right arrow to move the user or group name to the Read-Only Access
or Read-Write Access boxes.
8 Select Ok.
Configuring NFS shares
Configure the FortiAnalyzer unit to provide folder and file sharing using Windows
sharing.
To view a list of users with NFS share access to the FortiAnalyzer unit, including
access privileges, go to System > Network Sharing > NFS Export.
Figure 13: Viewing user access
To add a new NFS share configuration
1 Go to System > Network Sharing > NFS Export.
2 Select Enable NFS Exports and select Apply.
3 Select Create New.
Note: The default permissions for files and folders is read and execute privileges. The
owner of the document also has write privileges. To enable write permissions for users and
groups, you must select the write permission for the folder and for the user and the group.
For details see Setting folder and file privileges on page 49.
Local Path The path the user has permission to connect to.
Remote Clients A list of users that have access to the folder or files.
Permissions Permissions for the user. This can be either Read Only or Read
Write.
Modify Select Edit to change any of the options for file sharing.
Select Delete to remove the file sharing permissions.
Edit
Delete
Configure the FortiAnalyzer unit Configuring the FortiAnalyzer unit
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 49
Figure 14: NFS share configuration
4 Select the Local Path button to select the folder for the users or groups to access.
5 Select OK.
6 Enter the IP address of the remote system or user ID.
7 Select the type of access rights required and select Add.
8 Select OK.
Setting folder and file privileges
By default, when a user adds a new file or folder, the access rights are Read,
Write, Execute for the owner (user), and Read and Execute for the Admin group
and Others.
The FortiAnalyzer unit enables you to administer the folders and files on the
FortiAnalyzer hard disk as you are setting the access rights. These options are set
in the CLI. For more information, see the config nas share command in the
FortiAnalyzer CLI Reference.
Configuring the FortiAnalyzer unit
Use the system config to setup and maintain the FortiAnalyzer units internal
system configuration.
This section includes the following topics:
Log Settings
Log Aggregation
IP Aliases
RAID
Local Path
Button
Note: The default permissions for files and folders is read and execute privileges. The
owner of the document also has write privileges. To enable write permissions for users and
groups, you must select the write permission for the folder and for the user and the group.
For details see Setting folder and file privileges on page 49.
Note: When sharing a file or folder using NFS, and the user attempts to mount the
FortiAnalyzer hard disk on UNIX, the mount operation may fail. If this occurs, rebooting the
UNIX system corrects this, and the system can mount the FortiAnalyzer hard disk.
FortiAnalyzer Version 3.0 MR3 Administration Guide
50 05-30003-0082-20060925
Configuring the FortiAnalyzer unit Configure the FortiAnalyzer unit
Log Settings
The FortiAnalyzer unit creates its own system log messages to provide
information on system events occurring on the unit, such as system activity,
administration events and IPSec negotiations for secure transfers of log message
packets.
To configure where the FortiAnalyzer unit saves its own log messages, go to
System > Config > Log Setting.
Figure 15: System settings
Log Locally Select this option to save the FortiAnalyzer log messages on the
FortiAnalyzer hard disk.
Log Level Select the severity level for the log messages recorded to the
FortiAnalyzer hard disk. The FortiAnalyzer unit logs all levels of
severity down to, but not lower than, the level you select. For
example, if you want to record emergency, critical, and error
messages, select Error.
Config Policy Select to configure the events the FortiAnalyzer unit records to the
log.
Allocated Disk
Space (MB)
The maximum size of the FortiAnalyzer log file that the FortiAnalyzer
unit saves to the hard disk.
When the log file reaches the specified maximum size, the
FortiAnalyzer unit saves current network traffic log file with an
incremental number and starts a new active log file.
Log options when
log disk is full
The policy to follow for saving the current log and starting a new
active log when the FortiAnalyzer disk is full.
Select Overwrite oldest logs to delete the oldest log entry when the
disk is full. Select Do not log to stop logging messages when the disk
is full.
Configure the FortiAnalyzer unit Configuring the FortiAnalyzer unit
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 51
Log Aggregation
Log aggregation is a method of collating log data from remote FortiAnalyzer units
to a central FortiAnalyzer unit.
For example, a company may have a headquarters and a number of branch
offices. Each branch office has a FortiGate unit and a FortiAnalyzer-100A/100B to
collect local log information. The headquarters has a FortiAnalyzer-2000 as the
central log aggregator.
You can also use the FortiAnalyzer unit to aggregate logs for third party network
devices or server/work stations that supports syslog log messaging.
Reuse Settings
from Standard
Logs
Select to use configured options for device logs settings. See Log
rolling on page 86.
Log file should not
exceed
The maximum size of the current log file that the FortiAnalyzer unit
saves to the disk. When the log file reaches the specified maximum
size, the FortiAnalyzer unit saves the current log file and starts a new
active log file.
When a log file reaches its maximum size, the FortiAnalyzer unit
saves the log files with an incremental number, and starts a new log
file with the same name.
Log file should be
rolled
Set the frequency of when the FortiAnalyzer unit saves the current
log file and starts a new active log file. Select this option if you want to
start new log files even if the maximum log file size has not been
reached. For example, you want to roll a daily log on a FortiAnalyzer
unit that does not see a lot of activity.
Log to Host Select to send FortiAnalyzer log messages to a Syslog server.
IP Enter the IP address of the Syslog server.
Port Enter the Syslog port. The default port is 514.
Log Level Select the severity level for the log messages recorded to the Syslog
server. The FortiAnalyzer unit logs all levels of severity down to, but
not lower than, the level you select. For example, if you want to
record emergency, critical, and error messages, select Error.
CSV format Enable CSV format to record log messages in comma-separated
value (CSV) formatted files. Log message fields are separated by
commas.
Event Log Select to configure the events the FortiAnalyzer unit records to the
log.
Automatcially
Delete
Select the age unit for the specific log or report files. Select from
hours, weeks, days or months, and enter the value for the age unit.
FortiAnalyzer Version 3.0 MR3 Administration Guide
52 05-30003-0082-20060925
Configuring the FortiAnalyzer unit Configure the FortiAnalyzer unit
Figure 16: Log aggregation diagram
Log aggregation enables the branch office FortiAnalyzer units to send or upload
their logs at regular intervals to the headquarter FortiAnalyzer unit. This provides a
central storage location as well as a method of running reports that include data
from all branch offices in a single report.
Log aggregation involves an aggregation client (branch office) and an aggregation
server (headquarters). The aggregation client sends all log information for the
registered devices using SSH on port 22. This does not include quarantined files.
It does include the active log to the point of aggregation (tlog.log for example) and
all rolled logs available on the client hard disk (tlog.1.log, tlog.2.log, etc.).
Subsequent log uploads will only include the most recent updates. The
FortiAnalyzer unit will not resend all logs again.
On the aggregation server, additional devices will appear in the devices list. You
can easily identify these devices as the Rx and Tx icons are empty.
Configuring an aggregation client
The aggregation client is the FortiAnalyzer unit that sends logs to a aggregation
server. These would include units such as the FortiAnalyzer-100A/100B or
FortiAnalyzer-400.
To configure the aggregation client
1 Go to System > Config > Log Aggregation.
2 Select Enable log aggregation TO remote FortiAnalyzer
Configure the FortiAnalyzer unit Configuring the FortiAnalyzer unit
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 53
3 Set the following settings and select OK:
Configuring an aggregation server
The aggregation server is the FortiAnalyzer unit that receives the logs sent from
an aggregation client. FortiAnalyzer units such as the FortiAnalyzer-800 and
higher can be configured as aggregation servers.
To configure the aggregation client
1 Go to System > Config > Log Aggregation.
2 Select Enable log aggregation TO this FortiAnalyzer
3 Set the following settings and select OK:
IP Aliases
Use IP Aliases to assign a meaningful name to IP addresses. When configuring
reports, and viewing logs and content archives, select Resolve Host Name to view
the alias name rather than the IP address.
To define IP aliases
1 Go to System > Config > IP Aliases.
2 Select Create New.
3 Enter a name for the IP address in the Alias box.
4 Enter the IP address and select OK.
Importing an IP alias list file
For large listings of IP address and names, you can also import a text file
containing this information. This facilitates easier updating of large lists.
The contents of the text file should be in the format:
<ip address> <alias_name>
For example:
10.10.10.1 User_1
There should only be one IP address/user name entry per line.
Remote FortiAnalyzer IP Enter the IP address of the FortiAnalyzer unit acting as the
aggregation server.
Password Enter the password for the aggregation server.
Confirm Password Enter the password again for the aggregation server.
Aggregation daily at Select the time of the day when the aggregation client uploads
the logs to the aggregation server.
Aggregate now Select to send the logs to the aggregation server immediately.
Use this when you want to create a report on the server with the
most current log data.
Password Enter the password for the aggregation server.
Confirm Password Enter the password again for the aggregation server.
FortiAnalyzer Version 3.0 MR3 Administration Guide
54 05-30003-0082-20060925
Configuring the FortiAnalyzer unit Configure the FortiAnalyzer unit
To import the alias file
1 Go to System > Config > IP Aliases.
2 Select Import.
3 Enter the path and file name or select Browse to locate the file.
4 Select OK.
IP alias ranges
When adding an IP alias you can include an IP address range as well as individual
addresses. The range can include an address range and wild cards. For example:
10.10.10.1 - 10.10.10.50
10.10.10.1 - 10.10.20.100
10.10.10.*
RAID
Configuring RAID on the FortiAnalyzer-400 and
FortiAnalyzer-800
The FortiAnalyzer-400 and FortiAnalyzer-800 have four hot swappable hard disks.
Hot swapping is available when running the FortiAnalyzer unit with RAID level 1
and 5.
To set the RAID level, go to System > Config > RAID.
For details on the different RAID levels, see RAID levels on page 59.
Figure 17: FortiAnalyzer-400 RAID settings
!
Caution: Note that if you change RAID levels, the FortiAnalyzer unit reformats the hard
disks to support the new setting. It is extremely important that you back up all information
before changing the RAID level.
Configure the FortiAnalyzer unit Configuring the FortiAnalyzer unit
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 55
Configuring RAID on the FortiAnalyzer-2000 and
FortiAnalyzer-4000/4000A
The FortiAnalyzer-2000 has six hard disks and the FortiAnalyzer-4000/4000A has
12 hard disks. For both units, the disks are hot-swappable. This provides
additional RAID options for greater flexibility for data recovery, should a hard disk
fail.
To set the RAID level, go to System > Config > RAID.
RAID Level Select a RAID level and select Apply.
Free Disk Space The amount of free disk space.
Total Disk Space The amount of disk space available within the RAID array. This
value will change depending on the RAID type selected.
Type The setting for the unit. When employing a RAID level that
includes a hot spare, the hard disk assigned as a hot spare
appears as a separate unit.
Status The status of the RAID. For example, when starting a RAID array,
Initializing appears. When the RAID disk is functioning normally,
OK appears.
Size The total size of the unit for the RAID level or the size of the spare
hard disk.
No. The hard disk number.
Member of RAID Indicates if the hard disk is a part of the RAID array.
Status The current state of the hard disk.
Size (GB) The size of the hard disk.
Action Action icons appear when the FortiAnalyzer unit detects a faulty
hard disk.
To change a failed hard disk, select Remove to inform the
FortiAnalyzer unit that the hard disk will be removed. After
removing, the selection will become Add. Once the hard disk is
replaced, select Add.
For details on swapping hard disks, see Hot swapping in the
FortiAnalyzer-400 and FortiAnalyzer-800 on page 61.
!
Caution: It is important to note that if you change RAID levels, the FortiAnalyzer unit
reformats the hard disks to support the new setting. It is extremely important that you back
up all information before changing the RAID level.
FortiAnalyzer Version 3.0 MR3 Administration Guide
56 05-30003-0082-20060925
Configuring the FortiAnalyzer unit Configure the FortiAnalyzer unit
Figure 18: FortiAnalyzer-2000 RAID settings
Enable RAID Select to enable RAID 5. To enable other RAID levels, use the
command line interface. For command details see the
FortiAnalyzer CLI Reference.
Enable Hot Spare Select to enable the use of a hot spare with the RAID array.
Additional RAID levels are set in the CLI.
Total Disk Space The amount of disk space available within the RAID array.
Available Disk Space The amount of free disk space.
Click to start
controller rescan
Select after removing or adding a hard disk to the unit. This
enables the FortiAnalyzer unit to update the status of the hard disk
configurations.
Unit The hard disk grouping.
Type The setting for the unit. When employing a RAID level that
includes a hot spare, the hard disk assigned as a hot spare
appears as a separate unit.
Status The status of the unit. For example, when starting a RAID array,
Initializing appears. When the hard disk if functioning normally,
OK appears.
Size The total size of the unit for the RAID level or the size of the spare
hard disk.
Port The hard disk number.
Part of Unit Indicates if the hard disk is a part of the RAID array.
Status The current state of the hard disk.
Size (GB) The size of the hard disk.
Remove / Add To change a failed hard disk, select Remove to inform the
FortiAnalyzer unit that the hard disk will be removed. After
removing, the selection will become Add. Once the hard disk is
replaced, select Add.
For details on hot swapping hard disks, see Hot swapping the
FortiAnalyzer-2000 and FortiAnalyzer-4000/4000A on page 62.
Configure the FortiAnalyzer unit Maintenance
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 57
Maintenance
The maintenance page enables you to backup and restore configuration files and
maintain and review FortiGuard information for the FortiAnalyzer unit.
Backup & Restore
Go to System > Maintenance > Backup & Restore to back up and restore the
system configuration and to manage firmware.
You can back up the system configuration and also restore the system
configuration from previously downloaded backup files. This page also displays
the last backup and firmware upgrade time and date.
Figure 19: Backup and restore options
Last Backup The date and time of the last backup to local PC
Backup Back up the current configuration.
Backup configuration to: Currently, the only option is to back up to your local PC.
Encrypt configuration
file
Select to encrypt the backup file. Enter a password in the
Password field and enter it again in the Confirm field. You
will need this password to restore the file.
You must encrypt the backup file if you are using a
secure connection to a FortiGate or FortiManager device.
Backup Select to back up the configuration.
Restore Restore the configuration from a file.
Restore configuration
from:
Currently the only option is to restore from a PC.
Filename Enter the configuration file name or use the Browse
button if you are restoring the configuration from a file on
the management. computer.
Password Enter the password if the backup file is encrypted.
Restore Select to restore the configuration from the selected file.
Firmware
Partition A partition can contain one version of the firmware and
the system configuration.
FortiAnalyzer Version 3.0 MR3 Administration Guide
58 05-30003-0082-20060925
Maintenance Configure the FortiAnalyzer unit
Update center
You can configure the FortiAnalyzer unit to connect to the FortiProtect Distribution
Network (FDN) to update the IPS attack definitions for the vulnerability scanner.
The FDN is a world-wide network of FortiProtect Distribution Servers (FDSs).
When the FortiAnalyzer unit connects to the FDN it connects to the nearest FDS.
To do this, all FortiAnalyzer units are programmed with a list of FDS addresses
sorted by nearest time zone according to the time zone configured for the
FortiAnalyzer unit.
The FortiAnalyzer unit supports the following definition update features:
User-initiated updates from the FDN,
Hourly, daily, or weekly scheduled antivirus and attack definition updates from
the FDN,
Update status including version numbers, expiry dates, and update dates and
times,
To receive scheduled updates and push updates, you must register the
FortiAnalyzer unit on the Fortinet support web page.
Figure 20: Update center
Active A green check mark indicates which partition contains
the firmware and configuration currently in use.
Last Upgrade The date and time of the last update to this partition.
Firmware Version The version and build number of the FortiAnalyzer
firmware. On the backup partition, you can:
Select Upload to replace with firmware from the
management computer.
Select Upload and Reboot to replace the firmware.
Configure the FortiAnalyzer unit RAID levels
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 59
RAID levels
FortiAnalyzer units containing multiple hard disks can store log data using a RAID
array to provide redundant storage, data protection, faster hard disk access or a
larger storage capacity.
FortiProtect
Distribution
Network
The status of the connection to the FortiProtect Distribution Network
(FDN).
A green indicator means that the FortiAnalyzer unit can connect to the
FDN. You can configure the FortiAnalyzer unit for scheduled updates.
A red-yellow flashing indicator means that the FortiAnalyzer unit cannot
connect to the FDN. Check your configuration. For example, you may
need to add routes to the FortiAnalyzer routing table. To set the routing
see Routing on page 38.
Refresh Select Refresh, to test the FortiAnalyzer unit connection to the FDN. The
test results are displayed at the top of the System Update page.
Use override
server address
If you cannot connect to the FDN or if your organization provides attack
updates using their own FortiProtect server, you can configure an
override server.
Select the Use override server address check box and enter the IP
address of a FortiProtect server.
If after applying the override server address, the FortiProtect Distribution
Network setting changes to available, the FortiAnalyzer unit has
successfully connected to the override server. If the FortiProtect
Distribution Network stays set to not available, the FortiAnalyzer unit
cannot connect to the override server. Check the FortiAnalyzer
configuration and the network configuration to make sure you can
connect to the override FortiProtect server from the FortiAnalyzer unit.
Update The RVS engine and plug-in definitions for which update information is
displayed.
Version The version numbers of the files currently installed on the FortiAnalyzer
unit.
Expiry date The expiry date of your license for RVS engine updates.
Last update
attempt
The date and time on which the FortiAnalyzer unit last attempted to
download the updates.
Last update
status
The result of the last update attempt. No updates means the last update
attempt was successful but no new updates were available. Update
succeeded or similar messages mean the last update attempt was
successful and new updates were installed. Other messages can
indicate that the FortiAnalyzer was not able to connect to the FDN and
other error conditions.
Scheduled
Update
Select this check box to enable scheduled updates.
Every Attempt to update once every 1 to 23 hours. Select the number of hours
between each update request.
Daily Attempt to update once a day. You can specify the hour of the day to
check for updates. The update attempt occurs at a randomly determined
time within the selected hour.
Weekly Attempt to update once a week. You can specify the day of the week and
the hour of the day to check for updates. The update attempt occurs at a
randomly determined time within the selected hour.
Update Now Select Update Now to manually initiate an update.
Apply Select Apply to save update settings.
FortiAnalyzer Version 3.0 MR3 Administration Guide
60 05-30003-0082-20060925
RAID levels Configure the FortiAnalyzer unit
To configure the RAID settings, go to System > Config > RAID.
The FortiAnalyzer unit support standard RAID levels linear, 0, 1 and 5. The
FortiAnalyzer-2000 and FortiAnalyzer-4000/4000A supports additional RAID level
10 (1+0), and 50 (5+0), as well as 5 +hot spare and 10 + hot spare.
Linear
A linear RAID level combines all hard disks into one large virtual disk. It is also
known as concatenation or JBOD (Just a Bunch of Disks). The total space
available in this option is the capacity of all disks used. There is very little
performance changes when using this RAID format, including any redundancy
available at this level. If any of the drives fails, the entire set of drives is unusable
until the faulty drive is replaced. All data will be lost.
RAID 0
A RAID 0 array is also referred to as striping. The FortiAnalyzer unit writes
information evenly across all hard disks. The total space available is that of all the
disks in the RAID array. There is no redundancy available. If any of the drives fail,
the data cannot be recovered. This RAID level is beneficial because it provides
better performance, since the FortiAnalyzer unit can distribute disk writing across
multiple disks.
RAID 1
A RAID 1 array is also referred to as mirroring. The FortiAnalyzer unit writes
information to one hard disk, and writes a copy (a mirror image) of all information
to all other hard disks. The total disk space available is that of only one hard disk,
as the others are solely used for mirroring. This provides redundant data storage
with no single point of failure. Should any of the hard disks fail, there are several
backup hard disks available. With a FortiAnalyzer-400 for example, if one disk
fails, there are still three other hard disks the FortiAnalyzer unit can access and
continue functioning.
RAID 5
A RAID 5 array employs striping with a parity check. The FortiAnalyzer unit writes
information evenly across all drives. Additional parity blocks are written on the
same stripes. The parity block is staggered for each stripe. The total disk space is
the total number of disks in the array, minus one disk for parity storage. For
example, on a FortiAnalyzer-400 with four hard disks, the total capacity available
is actually the total for three hard disks. RAID 5 performance is typically better with
reading than writing, although performance is degraded when one disk has failed
or is missing. RAID 5 also ensures no data loss. If a drive fails, it can be replaced
and the FortiAnalyzer unit will restore the data on the new disk using reference
information from the parity volume.
Note: RAID functionality is only available on the FortiAnalyzer-400, FortiAnalyzer-800,
FortiAnalyzer-2000 and FortiAnalyzer-4000/4000A. These units include multiple hard disks
for RAID support.
Note: This RAID level is not available on the FortiAnalyzer-2000 and
FortiAnalyzer-4000/4000A.
Configure the FortiAnalyzer unit RAID levels
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 61
RAID 10
RAID 10 is only available on the FortiAnalyzer-2000. RAID 10 (or 1+0), includes
nested RAID levels 1 and 0, or a stripe (RAID 0) of mirrors (RAID 1). The total disk
space available is the total number of disks in the array (a minimum of 4) divided
by 2. Any drive from a RAID 1 array can fail without loss of data. However, should
the other drive in the RAID 1 array fail, all data will be lost. In this situation, it is
important to replace a failed drive as quickly as possible.
RAID 50
RAID 50 is only available on the FortiAnalyzer-2000. RAID 50 (or 5+0) includes
nested RAID levels 5 and 0, or a stripe (RAID 0) and stripe with parity (RAID 5).
RAID 50 provides increased performance and also ensures no data loss for the
same reasons as RAID 5. Data can be recovered even when up to four drives fail.
RAID 5 and RAID 10 with hot spare
The FortiAnalyzer-2000 and FortiAnalyzer-4000/4000A enables hot spare of hard
disk drives automatically by using one drive as a stand-by unit. When you select
one of these two options, the FortiAnalyzer unit uses five hard disks in the RAID
array, and the sixth hard disk is used as a spare, should any of the other five fail.
In the event that a hard disk fails, within a minute of the failure, the FortiAnalyzer
unit automatically substitutes the hot spared disk drive and rebuilds the data to
integrate the hard disk into the RAID array.
When you replace the hard disk with a new one, the FortiAnalyzer unit keeps the
new hard disk as the hot spare.
The FortiAnalyzer-2000 and FortiAnalyzer-4000/4000A also supports the hot
swapping of hard disks during operation. For details see Hot swapping the
FortiAnalyzer-2000 and FortiAnalyzer-4000/4000A on page 62.
Hot swapping hard disks
The hard disks on the FortiAnalyzer-400 and higher are hot swappable. Hot
swapping refers to removing a failed hard disk and replacing it with a new one
while the FortiAnalyzer unit remains in operation.
The FortiAnalyzer-100A/100B and FortiAnalyzer-100 units each have a single
hard disk. Hot swapping is not available on these units.
Hot swapping in the FortiAnalyzer-400 and FortiAnalyzer-800
The following diagram indicates the drive number and their location in the
FortiAnalyzer unit when you are looking at the front of the unit. Refer to this
diagram before removing the disk drive to ensure you remove the correct one.
Note: RAID 10 requires an even number of disks. For example, on the FortiAnalyzer-2000,
when selecting RAID 10 with hot spare, the FortiAnalyzer unit will use four of the six disks
in the RAID 10 array, keeping one as a hot spare. The additional hard disk will be defined
as idle. The total disk space available is 240 GB.
FortiAnalyzer Version 3.0 MR3 Administration Guide
62 05-30003-0082-20060925
RAID levels Configure the FortiAnalyzer unit
You can use any brand of hard disk to replace a failed hard disk. However, you
must ensure that the hard disk size is the same size as the remaining working
drives. Using a smaller drive will affect the RAID setup. The FortiAnalyzer unit will
reconfigure the RAID to the smaller drive, potentially causing data loss.
Table 6: FortiAnalyzer-400 disk drive configuration.
Table 7: FortiAnalyzer-800 disk drive configuration.
To swap a FortiAnalyzer-400 or FortiAnalyzer-800 hard disk
1 Go to System > Config > RAID.
The web-based manager displays which hard disk has failed. A trash can icon
appears next to the failed disk drive.
2 Select Remove for the failed hard disk.
A message displays indicating it is safe to remove the disk from the drive.
3 Remove the hard disk from the drive bay on the FortiAnalyzer unit
On the FortiAnalyzer-400, open the faceplate, remove the screws for the drive
and pull out the drive.
On the FortiAnalyzer-800, pull open the face place, unlock the drive and pull
out the drive.
4 Insert the new hard disk into the empty drive bay on the FortiAnalyzer unit,
reversing the steps above.
5 Select Return from the web-based manager.
The FortiAnalyzer disk controller will scan the available hard disks and update its
information with the new hard disk.
6 Select Add to add the hard disk to the RAID array.
The FortiAnalyzer unit rebuilds the RAID array with the new hard disk.
Hot swapping the FortiAnalyzer-2000 and
FortiAnalyzer-4000/4000A
The following diagram indicates the drive number and their location in the
FortiAnalyzer unit when you are looking at the front of the unit. Refer to this
diagram before removing the disk drive to ensure you remove the correct one.
You can use any brand of hard disk to replace a failed hard disk. However, you
must ensure that the hard disk size is the same size as the remaining working
drives. Using a smaller drive will affect the RAID setup. The FortiAnalyzer unit will
reconfigure the RAID to the smaller drive, potentially causing data loss.
Note: Only perform a hot swap with a RAID setting of either 1 or 5. Hot swapping on any
other RAID settings will result in data loss.
Drive 1 (p1)
Drive 2 (p2)
Drive 3 (p3)
Drive 4 (p4)
Drive 1 Drive 2 Drive 3 Drive 4
Configure the FortiAnalyzer unit RAID levels
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 63
Table 8: FortiAnalyzer-2000 disk drive configuration
Table 9: FortiAnalyzer-4000/4000A disk drive configuration
To swap a FortiAnalyzer-2000 or FortiAnalyzer-4000 hard disk
1 Go to System > Config > RAID.
The web-based manager displays which hard disk has failed.
2 Select Remove for the failed hard disk.
3 Remove the hard disk from the drive bay on the FortiAnalyzer unit
On the FortiAnalyzer-2000, press in the tab and pull the drive handle to
remove the dive.
On the FortiAnalyzer-4000/4000A, using a screw driver, turn the handle lock
so it is horizontal. Push the blue latch right and pull the drive handle to remove
the drive.
4 Select Click to start controller rescan.
The FortiAnalyzer disk controller scans the available hard disks and updates the
RAID array for the remaining hard disks. The RAID array status will be
Degraded.
5 Insert the new hard disk into the empty drive bay on the FortiAnalyzer unit.
6 Select Click to start controller rescan.
The FortiAnalyzer disk controller will scan the available hard disks and update its
information with the new hard disk.
7 Select Add to add the hard disk to the RAID array.
The FortiAnalyzer unit rebuilds the RAID array with the new hard disk.
The options available here will depend on the RAID level selected. For most RAID
levels, you can only add the new hard disk back into the RAID array. If you are
running a RAID level with hot spare, you can also add the new hard disk as the
hot spare.
Drive 1 (p1) Drive 4 (p4)
Drive 2 (p2) Drive 5 (p5)
Drive 3 (p3) Drive 6 (p6)
Drive 1 (p1) Drive 4 (p4) Drive 7 (p7) Drive 10 (p10)
Drive 2 (p2) Drive 5 (p5) Drive 8 (p8) Drive 11 (p11)
Drive 3 (p3) Drive 6 (p6) Drive 9 (p9) Drive 12 (p12)
FortiAnalyzer Version 3.0 MR3 Administration Guide
64 05-30003-0082-20060925
RAID levels Configure the FortiAnalyzer unit
Devices Devices List
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 65
Devices
The power of the FortiAnalyzer centers on reporting, data and network analysis
capability. The FortiAnalyzer unit collects log messages from multiple FortiGate
devices and Syslog servers, which it then uses for generating many different
report types.
This section describes how to add and configure FortiGate, FortiManager units
and Syslog servers so they can communicate with the FortiAnalyzer unit
This section includes the following topics
Devices List
Adding a FortiGate unit
Adding a FortiManager unit
Adding a Syslog server
Device Groups
Blocked Devices
Devices List
The devices list displays a listing of devices configured to connect and send log
packets, or messages, to the FortiAnalyzer unit.
Figure 21: Devices list
Note: The device administrator must also configure the device to send log messages and
other logging information to the FortiAnalyzer unit.
Page Enter a page number press Enter when you have multiple pages
of devices.
Show Select the type of devices to display in the list. You can select
devices by type or by group.
Unregistered Device
Options
Set the options to instruct the FortiAnalyzer unit what to do when
encountering an unregistered device attempting to connect to the
unit. For details see Unregistered device options on page 67.
Add Device Select to add and configure a new device to the list.
Edit
Delete
FortiAnalyzer Version 3.0 MR3 Administration Guide
66 05-30003-0082-20060925
Devices List Devices
Device interaction with a FortiAnalyzer unit
FortiGate, FortiManager and Syslog devices use the syslog protocol, sending log
packets using udp port 514,when sending log packets to the FortiAnalyzer unit.
When the FortiAnalyzer unit receives the packet, the FortiAnalyzer unit adds the
device to the list of unregistered devices.
Maximum allowed devices
Each FortiAnalyzerunit has a maximum number of device licenses it can support
and still provide effective logging and reporting capabilities. The following table
details these maximums.
Table 10: FortiAnalyzer Maximum supported devices
Name The name of the device.
Hardware The model of the device. For example, FortiGate-300A appears as
FGT300A.
IP Address The IP address of the device.
Administrative
Domains
The ADOM configured for the device.
Log Tx Rx
Report Tx Rx
Content Tx Rx
Quar Tx Rx
Displays the permissions that each device has for sending and
viewing logs and reports when connected to the FortiAnalyzer
unit.
Tx indicates the device is configured to transmit log packets to
the FortiAnalyzer unit.
Rx indicates the device is allowed to view reports and logs
stored on the FortiAnalyzer unit directly from the device. This
feature is only available on FortiGate units running FortiOS
3.0. This permission will appear red (unavailable) for Syslog
devices by default.
For a FortiManager unit, Tx indicates full access for all devices
managed by the FortiManager unit; Rx indicates that the
FortiManager unit can configure the FortiAnalyzer unit.
Secure Connection Indicates there is an IPSec tunnel connection between the device
and the FortiAnalyzer unit for the transmission of logs, content and
quarantined files. For details on creating a secure connection, see
Adding a FortiGate unit on page 68.
Disk Space (MB)
Used/Allocated
Displays the amount of the FortiAnalyzer disk space is allocated
for the device and how much of that space is used.
Action Select Edit to edit the device configuration.
Select Delete to remove a device from the list.
Select to add register an unregistered device so the FortiAnalyzer
unit can begin receiving the devices log messages.
For an unregistered device, select Block to stop the device from
attempting to connect to the FortiAnalyzer unit to send log
messages. For details on blocking a device see Blocked Devices
on page 74.
FortiGate and/or Syslog FortiManager FortiClient
FortiAnalyzer-100 10 (FortiGate-50A to
FortiGate-100A only)
1 None
FortiAnalyzer-100A/100B 10 (FortiGate-50A to
FortiGate-100A only)
1 None
FortiAnalyzer-400 200 (FortiGate-50A to
FortiGate-800 only)
1 2000
Devices Devices List
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 67
The maximums indicate a combined total of added and unregistered devices. If
there are more than the maximum allowed, the FortiAnalyzer unit will not allow
you to add more devices. You must either remove or block some devices.
When new devices attempt to connect to a FortiAnalyzer unit at its maximum
allowed devices, the FortiAnalyzer unit will reject the attempt by the device to
connect and automatically add the device to the list of blocked devices.
For details on blocked devices see Blocked Devices on page 74.
Unregistered device options
As devices are configured to send log packets to the FortiAnalyzer unit, you can
configure how the FortiAnalyzer unit handles the connection requests until you
can verify that they should be accepted. You can define what the FortiAnalyzer
unit does when it receives a request for a connection from a device.
Unregistered devices are included in the maximum devices available for a
FortiAnalyzer unit. Too many unregistered devices may prevent you from adding
a specific device. For details see Maximum allowed devices on page 66.
There are two options when configuring the unregistered device options:
known devices
unknown devices.
FortiGate units connecting with FortiDiscovery
FortiDiscovery is a feature within FortiOS 3.0 for all FortiGate units. It is a protocol
where a FortiGate unit and a FortiAnalyzer unit are able to discover one another
and configure themselves automatically.
On the FortiGate unit, the FortiGate administrator sets the option to use automatic
discovery to connect and send log packets to the FortiAnalyzer unit. On the
FortiAnalyzer unit, you configure the FortiAnalyzer unit to accept the connection
request. Once configured, the FortiGate unit automatically sets up the
FortiAnalyzer connection and begin sending log data and other FortiAnalyzer
reports and log files. For details see Unregistered device options on page 67.
To configure unregistered FortiGate units with FortiDiscovery
1 Go to Device > All.
2 Select Unregistered Device Options.
3 Select from the following options in the Unregistered FortiGates (connect via
Auto-Discovery area:
FortiAnalyzer-800 250 (FortiGate-50A to
FortiGate-800 only)
1 2500
FortiAnalyzer-2000 500 (All FortiGate models) 1 5000
FortiAnalyzer-4000/4000A 500 (All FortiGate models) 1 5000
Ignore Connection and Log Data All incoming FortiGate requests are not
accepted and the FortiAnalyzer will not add
them to the registered devices list.
Allow connection, add to unregistered
table, but ignore the data
Add the device to the list of unregistered device
list but do not store log data.
Allow connection, register
automatically, and store up to N MB of
data
Add the device to the registered devices list,
and save the log packets to the hard disk, using
the defined amount of disk space.
FortiAnalyzer Version 3.0 MR3 Administration Guide
68 05-30003-0082-20060925
Adding a FortiGate unit Devices
Unknown devices connecting to the FortiAnalyzer unit
Select what the FortiAnalyzer unit should do with the connection request for an
unknown device. These devices include FortiGate units running FortiOS 2.8 or
lower, FortiManager or Syslog servers.
To configure unregistered device options
1 Go to Device > All.
2 Select Unregistered Device Options.
3 Select from the following options for either known devices (FortiGate 2.8,
FortiManager) or unknown devices (syslog):
Adding a FortiGate unit
Before adding a FortiGate unit to the FortiAnalyzer unit, you must first configure
the FortiGate unit to send log packets to the FortiAnalyzer unit. To configure the
FortiGate unit to send log packets to the FortiAnalyzer unit, on the FortiGate unit
go to Log&Report > Log Config.
For full details on configuring a FortiGate unit, see the Log&Report chapter of the
FortiGate Administration Guide or the FortiGate Online Help.
When the FortiAnalyzer unit initially receives message packets from a FortiGate
unit, the FortiAnalyzer unit adds the FortiGate unit to the list of unregistered
devices.
To register a FortiGate unit to send log messages to the FortiAnalyzer unit
1 Go to Device > All
2 Select Unregistered from the Show list, and select Add from the Action column.
or
Select Add Device.
3 Set the following options.
Ignore all unknown unregistered
devices
All incoming device requests are not accepted and
the FortiAnalyzer will not add them to the
unregistered devices list.
Add unknown unregistered device
to unregistered table, but ignore
data
Add the device to the unregistered devices list for
future configuration and addition to the FortiAnalyzer
unit, but do not save the incoming log packets to the
hard disk.
Add unknown unregistered
devices to unregistered table, and
store up to N MB of data
Add the device to the unregistered devices list for
future configuration and addition to the FortiAnalyzer
unit, and save the log packets to the hard disk, but
only to a defined amount of disk space.
Device Type Select FortiGate from the device list. It is selected by default when
selecting a FortiGate unit from the unregistered list.
Device Name Enter a name to represent the FortiGate unit. For example,
FortiGate-300A.
Devices Adding a FortiGate unit
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 69
4 Expand the Devices Privileges settings.
5 Set the privileges the FortiGate unit has when sending and viewing log files,
archived content and quarantined files.
6 Expand the Group Membership settings.
7 Select the group where you want to include the FortiGate unit, and select the right
arrow button to add the FortiGate unit to the group. A FortiGate unit can belong to
multiple groups.
You can also add the FortiGate unit to a group later or change the group you
assigned. For details see Device Groups on page 74.
8 Expand the FortiGate Interface Specification settings.
Device ID When selecting a FortiGate unit from the unregistered list, the
FortiAnalyzer unit automatically adds the FortiGate units serial
number. If you are adding a new FortiGate unit that is not already
in the unregistered list, enter the FortiGate units serial number.
The FortiGate units serial number is available on the System
menu in the Web-based GUI.
Mode Select the mode of the FortiGate unit. Leave the selection as
Standalone when adding a single unit. If you are adding an HA
cluster, select HA. For more details on adding an HA cluster see
Adding an HA cluster on page 70.
Description Enter additional information for the FortiGate unit up to 128
characters long. Description information appears when you hover
the mouse over the FortiGate units name in the devices list.
Administrative
Domain
Select the administrative domain (ADOM) that the device will be
associated with. This selection is visible when using the ADOM
feature. For more information on ADOMs, see Administrator
settings on page 39.
Secure Connection Select this option to set up a secure connection between the
FortiAnalyzer unit and the FortiGate unit.
To ensure a correct secure connection, the Device Name entered
above and the Local ID setting on the FortiGate unit must match
exactly. You set this in the FortiGate CLI in config system
fortianalyzer.
You must also enter a pre-shared key that matches the pre-shared
key entered on the FortiGate unit.
By Key Enter a pre-shared key for the secure connection when you select
Secure Connection. You must select the Secure Connection check
box to enable this option. The key you enter must match the key
set on the FortiGate unit to ensure the logs and files are sent over
a secure connection.
Allocated Disk Space
(MB)
Set the allocated amount of the FortiAnalyzer hard disk to log and
content messages for the device. The amount allocated will also
include disk space set aside for quarantined files. For details on
quarantine file disk allocation, see Configuring quarantine
settings on page 95.
A disk space setting of zero is unlimited.
When Allocated Disk
Space is All Used
Select what the FortiAnalyzer unit should do when the allocated
disk space has been reached. Select either overwriting older files
or stop logging.
Note: Accessing logs, content logs and quarantined files is available on FortiGate units
running firmware version 3.0 or later.
FortiAnalyzer Version 3.0 MR3 Administration Guide
70 05-30003-0082-20060925
Adding a FortiGate unit Devices
9 Define the port interface options using the arrow buttons. For details on port
interface settings see Defining FortiGate port interfaces on page 70.
If you want to add a VLAN or other interface, type the name of the interface and
select Add.
10 Select OK.
Defining FortiGate port interfaces
FortiAnalyzer Network activity reports include information on inbound and
outbound traffic flow. Traffic flow information is based on the source and
destination interfaces of the device and how they are configured to send and
receive information.
To ensure that the traffic information is represented correctly in these reports, you
need to assign the FortiGate interfaces to an interface type. The device interface
can include an interface name or a defined VLAN on the device.
You can classify the device interfaces as one of None, LAN, WAN or DMZ to
match the type of traffic the interface will process. When the FortiAnalyzer unit
generates the traffic log report, the FortiAnalyzer unit compares the source and
destination interface classifications and determines the traffic direction. The traffic
direction is one of:
Incoming
Outgoing
Internal
External
Unclassified.
The table below illustrates how the source and destination interface types are
represented in the log report as traffic direction.
Adding an HA cluster
Adding an High Availability (HA) cluster enables you to enable an HA cluster to
send log packets to the FortiAnalyzer unit. The log messages sent are maintained
as a cluster rather than a number of individual log files for each unit in the cluster.
This also enables you to view the cluster traffic and run reports on the cluster.
When adding an HA cluster, add the primary device.
Table 11: Log report traffic direction identification
Source Destination Traffic Direction
None All types Unclassified
All types None Unclassified
WAN LAN, DMZ Incoming
WAN WAN External
LAN, DMZ LAN, DMZ Internal
LAN, DMZ WAN Outgoing
Devices Adding FortiClient installations
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 71
To add an HA cluster
1 Go to Device > All
2 Select Unregistered from the Show list, and select Add from the Action column.
or
Select Add Device.
3 Configure the same settings as indicated in the section Adding a FortiGate unit
on page 68, using the information for the primary unit, with the following
exceptions:
Set the Mode to HA.
Enter the device IDs (serial numbers) for each subordinate unit in the cluster
and select Add.
Adding FortiClient installations
The FortiAnalyzer unit can store FortiClient log messages for reporting purposes.
Unlike logging FortiGate units, you configure the FortiAnalyzer unit to accept all
FortiClient log messages, rather than individual users. To obtain network histories
for individual users, use the FortiAnalyzer reporting features.
To register a FortiClient installation to send log messages to the
FortiAnalyzer unit
1 Go to Device > All.
2 Select Unregistered from the Show list, and select Add from the Action column.
or
Select Add Device.
3 Set the following options and select OK.
Unlike other devices, a FortiClient connection can only send log messages to the
FortiAnalyzer unit. You cannot configure it so that a user can view their log
messages or specific reports.
Device Type Select FortiClient from the device list. It is selected by default
when selecting a FortiClient installation from the unregistered list.
Device Name The default selection is for all FortiClients.
Description by default, the description indicates that the FortiClient selection is
for all connected FortiClient installations.
Administrative
Domain
Select the administrative domain (ADOM) that the device will be
associated with. This selection is visible when using the ADOM
feature. For more information on ADOMs, see Administrator
settings on page 39.
Allocated Disk Space
(MB)
Set the allocated amount of the FortiAnalyzer hard disk to log and
content messages for the device. The amount allocated will also
include disk space set aside for quarantined files. For details on
quarantine file disk allocation, see Configuring quarantine
settings on page 95.
A disk space setting of zero is unlimited.
When Allocated Disk
Space is All Used
Select what the FortiAnalyzer unit should do when the allocated
disk space has been reached. Select either overwriting older files
or stop logging.
FortiAnalyzer Version 3.0 MR3 Administration Guide
72 05-30003-0082-20060925
Adding a FortiManager unit Devices
Adding a FortiManager unit
Before adding a FortiManager unit to the FortiAnalyzer, you must first configure
the FortiManager to connect to the FortiAnalyzer unit.
To configure the FortiManager unit
1 On the FortiManager unit, select System Settings from the Dashboard.
2 Go to Local Logs > Log Config.
For details on configuring the FortiManager, see the FortiManager Administration
Guide or the FortiManager Online Help.
When the FortiManager connects to the FortiAnalyzer unit, the FortiAnalyzer unit
adds the FortiManager to the list of unregistered devices. The FortiAnalyzer unit
does not actually receive any log packets from the FortiManager device. The
connection is for management purposes only.
To register a FortiManager unit
1 Go to Device > All.
2 Select Unregistered from the Show list, and select Add from the Action column for
the FortiManager unit.
or
Select Add Device.
3 Set the following options.
Device Type Select FortiManager from the device list. It is selected by default
when selecting a FortiManager unit from the unregistered list.
Device Name Enter a name to represent the device.
Device ID When selecting a FortiManager unit from the unregistered list, the
FortiAnalyzer unit automatically adds the FortiManager units
serial number. If you are adding a new FortiManager unit that is
not already in the unregistered list, enter the FortiManager units
serial number. The FortiManager units serial number is available
on the System menu in the web-based manager.
Description Enter additional information for the FortiManager unit up to 128
characters long. Description information appears when you hover
the mouse over the FortiManager units name in the devices list.
Administrative
Domain
Select the administrative domain (ADOM) that the device will be
associated with. This selection is visible when using the ADOM
feature. For more information on ADOMs, see Administrator
settings on page 39.
Secure Connection Select this option to set up a secure connection between the
FortiAnalyzer unit and the FortiManager unit.
To ensure a correct secure connection, the Device ID entered
above and the Local ID setting must match exactly
By Key Enter a preshared key for the secure connection. You must select
the Secure Connection check box to select this option. The key
you enter must match the key set on the FortiManager unit to
ensure the log files are send over a secure connection.
Allocated Disk Space
(MB)
Set the amount of the FortiAnalyzer hard disk is allocated to log
and content files for the device. A disk space setting of zero is
unlimited.
When Allocated Disk
Space is All Used
Select what the FortiAnalyzer unit should do once the allocated
disk space has been reached. Select from overwriting older files or
stop logging.
Devices Adding a Syslog server
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 73
4 Expand the Devices Privileges settings.
5 Set the privileges the FortiManager unit has to the FortiAnalyzer unit.
Select Allow all devices managed by FortiManager to have full access to the
FortiAnalyzer unit and to Allow the FortiManager to configure the FortiAnalyzer
unit.
6 Expand the Group Membership settings.
7 Select the group or groups where you want to include the FortiManager unit, and
select the right arrow button to add the FortiManager unit to the group.
8 Select OK.
Adding a Syslog server
Before adding a syslog server to the FortiAnalyzer unit, you must first configure
the server to send log packets to the FortiAnalyzer unit. See your syslog server
documentation for information on directing log packets.
The FortiAnalyzer unit adds the syslog server to the list of unregistered devices.
The FortiAnalyzer unit will not accept the log packets until you configure the
FortiAnalyzer unit to accept the connection form the server.
To add a syslog server to the FortiAnalyzer
1 Go to Device > All.
2 Select Unregistered from the Show list, and select Add from the Action column for
the syslog device.
or
Select Add Device.
3 Set the following options.
Device Type Select Syslog from the device list. It is selected by default when
selecting a syslog server from the unregistered list.
Device Name Enter a name to represent the Syslog server.
IP Address Enter the IP address of the Syslog server. The IP address will
already appear when selecting a syslog server from the
unregistered list.
Description Enter additional information for the Syslog server up to 128
characters long. Description information appears when you hover
the mouse over the Syslog servers name in the devices list.
Administrative
Domain
Select the administrative domain (ADOM) that the device will be
associated with. This selection is visible when using the ADOM
feature. For more information on ADOMs, see Administrator
settings on page 39.
Allocated Disk Space
(MB)
Set the amount of the FortiAnalyzer hard disk is allocated to log
and content files for the device. A disk space setting of zero is
unlimited.
When Allocated Disk
Space is All Used
Select what the FortiAnalyzer unit should do once the allocated
disk space has been reached. Select from overwriting older files or
stop logging.
FortiAnalyzer Version 3.0 MR3 Administration Guide
74 05-30003-0082-20060925
Device Groups Devices
4 Expand the Group Membership settings.
5 Select the group or groups where you want to include the Syslog server, and
select the right arrow button to add the Syslog servers to the group.
6 Select OK.
Device Groups
When you have multiple devices belonging to a department or section of the
company, you can create groups to keep the devices together for easier
monitoring. A device can belong to multiple groups. Once you create a group you
can add or remove devices as required.
To add a device group and add devices
1 Go to Device > Groups.
2 Select Create New.
3 Enter a name for the group.
4 Select the devices to include in the group from the list of Available Devices and
select the right-pointing arrow.
5 Select OK.
Blocked Devices
Blocking devices are a way to control the number of device licenses available on
the FortiAnalyzer unit. The FortiAnalyzer unit supports a maximum number of
devices. To free up license spots, you can block devices that you do not want in
the FortiAnalyzer devices lists.
To block a device
1 Go to Device > All.
2 Select Unregistered from the Show list.
3 Select Block from the Action column.
Note: You can delete groups without removing devices from the group. When adding a
device to a group, it is like a Windows shortcut. Removing a group will not remove the
device configuration from the FortiAnalyzer unit.
Devices Blocked Devices
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 75
Viewing blocked devices
To view blocked devices on the FortiAnalyzer unit, go to Device > All > Blocked
Devices.
Figure 22: List of blocked devices
Device ID The name or serial number of the blocked device.
Hardware Model The type of device, for example FortiGate, FortiManager or Syslog
server.
IP Address The IP Address of the blocked device.
Action Select Delete to remove access from the device from the
FortiAnalyzer unit.
Select Unblock to add the device to the FortiAnalyzer unit.
FortiAnalyzer Version 3.0 MR3 Administration Guide
76 05-30003-0082-20060925
Blocked Devices Devices
Logs Log Viewer
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 77
Logs
The FortiAnalyzer unit collects log message packets from FortiGate,
FortiManager, FortiClient and Syslog devices. Using the log browser, you can
view device and FortiAnalyzer log files and log messages. The FortiAnalyzer unit
can also view device logs in real-time, enabling you to see events and traffic
occurring on a device as it happens.
This section includes the following topics:
Log Viewer
Browse
Customizing the log view
Search the logs
Log rolling
Log Viewer
The log viewer enables you to view logs from registered devices. The Log Viewer
has two types of log viewing options:
Real-time logs display log message updates as the log message packets are
sent to the FortiAnalyzer unit. The display refreshes every 10 seconds to
display the most current entries.
Historical logs provides a method of viewing log messages by focusing on
specific log types and time frames.
To view real-time logs, go to Log > Log Viewer.
Real-time log viewer
Real-time logs display log information and updates continually, to provide the
most recent updates and events occurring on a selected device.
To view real-time logs, go to Log > Log Viewer > Real-time, select a device and
log type and select OK.
FortiAnalyzer Version 3.0 MR3 Administration Guide
78 05-30003-0082-20060925
Log Viewer Logs
Figure 23: Viewing logs in real time
For information about log messages, see the FortiGate Log Message Reference.
Historical log viewer
The Historical log viewer enables you to view log information for a selected device
and log type for a specific time range. When viewing log messages, you can filter
the information to find specific event information.
To select a historical log to view
1 Go to Log > Log Viewer > Historical.
2 Select a device. All registered devices appear in the list.
3 Select the log type.
4 Set the Start time by selecting the following:
Type The log type you are viewing and the device where it is originating
from.
Change Select to change the log type to view or the device.
Stop Select to stop the FortiAnalyzer unit from refreshing the log view.
Column Settings Select to change the columns to view and the order they appear
on the page. For details see Customizing the log column views
on page 83.
Formatted | Raw Select a view of the log file. Selecting Formatted (the default)
displays the log files in columnar format. Selecting Raw, displays
the log information as it actually appears in the log file.
Resolve Host Name Select to display host names by a recognizable name rather than
IP addresses. For details on configuring IP address host names
see IP Aliases on page 53.
Resolve Service Select to display the network service names rather than the port
numbers. For example, HTTP rather than port 80. This option
does not appear when the logs do not have service information to
display. For example, the event log.
Column Settings
Unspecified Select to view log messages from the earliest date and time
available in the logs.
Specified Select to set a specific start date and time for the log messages.
Date Enter a start date. Use the format YYYY/MM/DD. Alternatively,
select the Calendar icon and select a start date.
Time Select a starting time for the log messages. Leave the time at
00:00 to view log messages starting at 12:00 midnight for the
selected date.
Logs Log Viewer
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 79
5 Select the End time by selecting the following:
6 Select OK.
Figure 24: Viewing historical log data
Current Select to include up to the minute log messages.
Specified Select to set a specific end date and time for the log messages.
Date Enter an end date. Use the format DD/MM/YYYY. Alternatively,
select the Calendar icon and select a start date.
Time Select a ending time for the log messages. Leave the time at
00:00 to view log messages ending at 12:00 midnight for the
selected date.
Type The type of log you are viewing and the device where it originated.
Change Select to change the log, time frame or a different device.
Formatted | Raw Select a view of the log file. Selecting Formatted (the default)
displays the log files in columnar format. Selecting Raw, displays
the log information as it actually appears in the log file.
Resolve Host Name Select to display host names by a recognizable name rather than
IP addresses. For details on configuring IP address host names
see IP Aliases on page 53.
Resolve Service Select to display the network service names rather than the port
numbers. For example, HTTP rather than port 80. This option
does not appear when the logs do not have service information to
display. For example, the event log.
View per page Select the number of rows of log entries to display per page.
Page n of n Enter a page number to jump to in the log information. Press Enter
to jump to the page.
Column Settings Select to change the columns to view and the order they appear
on the page. For details see Customizing the log column views
on page 83.
Column Settings
FortiAnalyzer Version 3.0 MR3 Administration Guide
80 05-30003-0082-20060925
Browse Logs
For information about log messages, see the FortiGate Log Message Reference.
Browse
The log browser enables you to see all stored log files for all devices and
FortiAnalyzer logs. In this window, you can view the log information, download log
files to your hard disk or delete unneeded files.
To browse the log files, go to Log > Browse.
Figure 25: Browsing log files
Search Enter a keyword to perform a simple search on the log information
available. Select Go to begin the search. The number of matches
appears above the Search field.
The FortiAnalyzer unit will search the entire log file for the keyword
you enter.
Printable Version Select to generate a report that captures the current log
messages. The web browser prompts you to save the report file
for viewing or printing. The report saved is in HTML format. Note
that large log messages can take a long time to load.
The printable version takes all filter settings into account when
generating a printable version.
Note: Searches using characters will not include results from the Traffic logs. Traffic logs
include information for source and destination IP addresses and ports which is strictly
numerical information.
For example, if you are searching on User1, you may get results for User1, however, none
of the results will include entries from the Traffic log. To get results from the traffic log, you
must search on the IP address of User1. For example, 10.10.10.1.
Device Type Select a device category to view its related log files.
Import Select to import older log files to view and run log reports. For details on
importing log files see Importing a log file on page 82.
Log files A list of available log files. Any device groups you create also appear
here. Select the group name to expand the list of devices within the
group.
The current, or active, log file appears as well as rolled log files. Rolled
log files include a number in the file name. For example, alog.2.log. If
you configure the FortiAnalyzer unit to upload rolled logs to an FTP site,
only the current log will appear in the log browser.
# The number of devices in a group, and the number of logs for a device.
Delete
Download
Display
Logs Browse
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 81
When a log file reaches its maximum size, the FortiAnalyzer unit saves the log
files with an incremental number, and starts a new log file with the same name.
For example, the current attack log is alog.log. Any subsequent saved logs
appear as alog.n.log, where n is the number of rolled logs.
For details on setting the maximum file size and log rolling options, see Log
rolling on page 86.
Browsing log files
The log viewer enables you to view log information for a selected devices log file.
This enables you to view all traffic that occurred on a device. You can also filter
the information to see specific event information.
To view a log file
1 Go to Log > Browse.
2 Expand the group name and device name to see the list of available logs.
3 In the Action column, select Display for the desired log file.
Figure 26: Viewing log data
Last Modified The last time the log was updated from the device.
Size (bytes) The size of the log file.
Action Select Delete to remove the log file from the FortiAnalyzer hard disk.
Select Download to save the log file to your local hard disk.
Select Display to view the contents of the log file.
Type The type of log you are viewing and the device where it originated.
Change Select to view a different log file.
Formatted | Raw Select a view of the log file. Selecting Formatted (the default)
displays the log files in columnar format. Selecting Raw, displays
the log information as it actually appears in the log file.
Resolve Host Name Select to display host names by a recognizable name rather than
IP addresses. For details on configuring IP address host names
see IP Aliases on page 53.
Resolve Service Select to display the network service names rather than the port
numbers. For example, HTTP rather than port 80. This option
does not appear when the logs do not have service information to
display. For example, the event log.
View per page Select the number of rows of log entries to display per page.
Page n of n Enter a page number to jump to in the log information. Press Enter
to jump to the page.
Column Settings
FortiAnalyzer Version 3.0 MR3 Administration Guide
82 05-30003-0082-20060925
Browse Logs
For information about log messages, see the FortiGate Log Message Reference.
Importing a log file
If you have older log files from a device, you can import these logs onto the
FortiAnalyzer unit for generating log reports.
Importing log files is also useful when changing your RAID configuration (for the
FortiAnalyzer-400, 800, 2000 and 4000/4000A). Changing your RAID
configuration wipes the hard disk. If you backup your FortiAnalyzer log, you can
import the FortiAnalyzer log onto the device.
You can also import normal Fortinet logs or logs in CSV format.
To import a log file
1 Go to Log > Browse.
2 Select Import.
3 Select the device from the Device list that the log file is associated with.
4 Enter the path and file name of the log file, or select Browse.
5 Select OK.
Downloading a log file
Download a log file to save it as a backup or for use outside the FortiAnalyzer unit.
To download a log file
1 Go to Log > Browse.
2 In the Log Files column, locate a device and log type.
3 In the Action column, select Download.
Column Settings Select to change the columns to view and the order they appear
on the page. For details see Customizing the log column views
on page 83.
Search Enter a keyword to perform a simple search on the log information
available. Select Go to begin the search. The number of matches
appears above the Search field.
The FortiAnalyzer unit will search the entire log file for the keyword
you enter.
Printable Version Select to generate a report that captures the current log
messages. The web browser prompts you to save the report file
for viewing or printing. The report saved is in HTML format. Note
that large log messages can take a long time to load.
The printable version takes all filter settings into account when
generating a printable version.
Note: Searches using characters will not include results from the Traffic logs. Traffic logs
include information for source and destination IP addresses and ports which is strictly
numerical information.
For example, if you are searching on User1, you may get results for User1, however, none
of the results will include entries from the Traffic log. To get results from the traffic log, you
must search on the IP address of User1. For example, 10.10.10.1.
Logs Customizing the log view
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 83
4 Select one of the following and select OK.
5 The web browser prompts you for a location to save the file.
Customizing the log view
The FortiAnalyzer unit enables you to customize the way you view the logs to
enable you to narrow down the information to exactly what you want to see.
Customizing the log column views
Customize the columns to view only the information relevant to you. You can add,
remove and change the position of each column.
Figure 27: Customizing the columns
To add or remove columns
1 When viewing a log file, select Column Settings.
A list of columns available for the log type appears.
2 In the Available Fields area, select a column name and select the right arrow to
move the column name into the Display Fields area.
To change the positioning of the columns
1 When viewing a log file, select Column Settings.
A list of columns available for the log type appears.
2 Select a column name.
3 Select the up and down arrows to change the position of the column in the list.
Convert to CSV
format
Downloads the log format as a commas separated file with an
extension of .csv. Each data element is separated by a comma.
Compress with gzip Download the log file in its native format with gzip compression.
Note: You must be viewing the log contents in the formatted view to use the filters.
FortiAnalyzer Version 3.0 MR3 Administration Guide
84 05-30003-0082-20060925
Search the logs Logs
Filtering logs
When viewing log files both real-time and historical, you can filter the contents to
find specific content. Log filters appear when you are viewing real-time and
historical data in the Log Viewer or when browsing log files on the FortiAnalyzer
hard disk.
Figure 28: Filter icons for logs
Each column of data includes a gray filter icon. Select the icon to filter the
contents of the column.
When applying a column filter, the filter icon appears green.
To turn off the filter, select the filter icon for the column, and select Reset Filter.
Filtering tip
When filtering by source or destination IP, you can use the following in the filtering
criteria:
a single address (2.2.2.2)
an address range using a wild card (1.2.2.*)
an address range (1.2.2.1-1.2.2.100)
You can also use the boolean operator "or" to indicate multiple choices:
1.1.1.1 or 2.2.2.2
1.1.1.1 or 2.2.2.*
1.1.1.1 or 2.2.2.1-2.2.2.10
Search the logs
The FortiAnalyzerunit provides search capabilities for locating specific information
within the stored log files. The FortiAnalyzer unit provides two log searches:
Basic search
Advanced search
Note: You must be viewing the log contents in the formatted view to use the filters.
Filter icon Filter in use
Note: When viewing real-time logs, you cannot filter the time column because the time will
always be the current time.
Logs Search the logs
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 85
Basic search
The basic search performs a simple search of all log files on the FortiAnalyzer
unit. The FortiAnalyzer unit maintains a search history for reference should you
need to use the search keywords again. The FortiAnalyzer searches all log files
and data for matches.
To perform a search, go to Log > Search. Enter the keywords for the search.
Separate multiple keywords with a space.
Search results appear below the search entry fields.
Advanced search
The advanced search provides more options to narrow your search criteria.
To perform an advanced search, go to Log > Search, and select Advanced
search.
Figure 29: FortiAnalyzer advanced search
Note: Searches using characters will not include results from the Traffic logs. Traffic logs
include information for source and destination IP addresses and ports which is strictly
numerical information.
For example, if you are searching on User1, you may get results for User1, however, none
of the results will include entries from the Traffic log. To get results from the traffic log, you
must search on the IP address of User1. For example, 10.10.10.1.
Search Select to begin searching the logs.
Basic search Select to perform a basic search.
Find results with all
of the words
Enter all the keywords you want to use in your search. The
FortiAnalyzer search engine will return all log entries that contain
all keywords entered. Separate keywords with a space.
Find results with at
least one of the
words
Enter all the keywords you want to use in your search. The
FortiAnalyzer search engine will return all log entries that contain
one or more of the keywords. Separate keywords with a space.
Find results without
the words
Enter the keywords that you do not want included in your search
results. If a log entry contains the keywords you are searching on
and includes a keyword from this field, the log entry will not be
included in the search results.
Log types Select the log types that you want to search. Hold the CTRL or
SHIFT keys to select multiple log types.
Devices Select the devices logs to search. Hold the CTRL or SHIFT keys
to select multiple devices.
Dated within Select a time frame of the log entries to search within.
FortiAnalyzer Version 3.0 MR3 Administration Guide
86 05-30003-0082-20060925
Log rolling Logs
Search tips
The FortiAnalyzer search feature includes a robust search index that enables you
to find any information by including specific information in your search criteria.
Consider the following when searching the logs:
The search is case-insensitive.
Use the * character as a wild card. For any partial term or IP address, enter
as much as you can and use the * to search all terms related to what you
entered.
To find how often an IP address is attacked, enter the IP and the attack type.
For example 10.10.10.1 slammer. Or, to see how often a user logs into the
FortiGate unit, enter 10.10.10.1 login.
You can search for IP ranges, including subnets. For example:
172.20.110.0-255 matches all IP addresses in the
172.20.110.0/255.255.255.0 or 172.20.110.0/24 subnet
172.20.110.0-140.255 matches all IP addresses from 172.20.110.0 to
172.20.140.255
172.16.0.0-20.255.255 matches all IP addresses from 172.16.0.0 to
172.20.255.255)
Printing the search results
The FortiAnalyzer unit enables you to produce a hard copy of the results of a
search, which you can email, save to a local hard disk or print.
After completing a search, the results include a Printable Version link. Select the
link to create an HTML version of the results.
Log rolling
Log rolling is a way to control the log file size and manage the FortiAnalyzer. You
can configure the frequency of the log rolling and what to do with the log file when
rolled.
When a log file reaches its maximum size, the FortiAnalyzer unit saves the log
files with an incremental number, and starts a new log file with the same name.
For example, the current attack log is alog.log. Any subsequent saved logs appear
as alog.n.log, where n is the number of rolled logs.
To enable log rolling, go to Log > Config.
Note: Searches using characters will not include results from the Traffic logs. Traffic logs
include information for source and destination IP addresses and ports which is strictly
numerical information.
For example, if you are searching on User1, you may get results for User1, however, none
of the results will include entries from the Traffic log. To get results from the traffic log, you
must search on the IP address of User1. For example, 10.10.10.1.
Logs Log rolling
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 87
Figure 30: Log rolling settings
Log file should not
exceed
The maximum size of a log file that the FortiAnalyzer unit saves to
the hard disk.
When the log file reaches the specified maximum size, the
FortiAnalyzer unit saves the current log file with an incremental
number and starts a new active log file.
Log file should be
rolled
Set the time of day, when the FortiAnalyzer unit saves the current
log file and starts a new active log file. Select either Daily or
Weekly. If you only want the FortiAnalyzer unit to roll log files
when the file size is reached, select Optional.
Enable log uploading Select to upload log files to an FTP server when a log file rolls.
Server type Select the type of uploading server. Select from:
File Transfer Protocol (FTP)
Secure File Transfer Protocol (SFTP)
Secure Copy Protocol (SCP)
Server IP address Enter the IP address of the FTP server.
Username Enter the user name to connect to the FTP server. The user name
has a default of anonymous.
Password Enter the password required to connect to the FTP server.
Confirm Password Re-enter the password to ensure it is entered correctly.
Directory Enter a specific directory on the FTP server to save the log file.
Upload Log files Select when the FortiAnalyzer unit uploads files to the FTP server.
Select When rolled to upload as soon as the FortiAnalyzer unit
rolls the log file, based on the settings above.
Select a specific time of the day when the FortiAnalyzer unit
rolls the log file. The FortiAnalyzer unit will upload at the
configured time no matter what the size of the log file is or
when it may be configured to roll to a new file.
Upload rolled files in
gzipped format
Select to compress the content log files in gzipped format before
uploading to the FTP server.
Delete files after
uploading
Select to remove the log file from the FortiAnalyzer hard disk once
the FortiAnalyzer unit completes the upload.
FortiAnalyzer Version 3.0 MR3 Administration Guide
88 05-30003-0082-20060925
Log rolling Logs
Content archive Content viewer
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 89
Content archive
A FortiGate unit can monitor and log metadata content for all users using email,
FTP and Instant Messages. The metadata content includes information such as
the senders and recipients of email and instant messages and the content of
those messages.
Using standard data filtering, you can track and locate specific email or
messaging communications occurring on your network.
For details on how to configure the FortiGate unit to send content archive
information to the FortiAnalyzer unit, see the FortiGate Administration Guide.
This section includes the following topics:
Content viewer
Customizing the content log view
Log rolling
Content viewer
The content viewer displays metadata from devices connected to the
FortiAnalyzer unit. Metadata includes where the information is coming from and
going to.
The content viewer enables you to view and filter on three content types:
email
FTP
Instant Messaging conversations
To view content archive log information, go to the Content Archive menu, select
the content to view. Each log type has a similar viewing controls.
Figure 31: Viewing file transfer logs
Show Select the FortiGate device from the list.
Timeframe Select the time span for the log data you want to view.
Column Settings
FortiAnalyzer Version 3.0 MR3 Administration Guide
90 05-30003-0082-20060925
Customizing the content log view Content archive
Customizing the content log view
The FortiAnalyzer unit enables you to customize the way you view the content
logs to enable you to narrow down the information to exactly what you want to
see.
Customizing the log column views
When viewing log information in formatted view, customize the columns to fit your
requirements. You can add, remove and change the position of each column.
Figure 32: Customizing the column view
To add or remove columns
1 When viewing a historical content log file, select Column Settings.
A list of available columns for the log type appears.
2 In the Show column, select or clear the check boxes for your column selections.
To change the positioning of the columns
1 When viewing a historical content log file, select Column Settings.
A list of available columns for the log type appears.
Resolve Host Name Select to view the client IP address as a real name. You must
configure the IP aliases on the FortiAnalyzer for this setting to be
effective. For details see IP Aliases on page 53.
Note this option is not available when viewing the email content
archive.
Formatted | Raw Select a view of the content log file. Selecting Formatted (the
default) displays the content log files in columnar format. Selecting
Raw, displays the content log information as it actually appears in
the content log file.
View per page Select the number of rows of log entries to display per page.
Page n of n Enter a page number to jump to in the log information. Press Enter
to jump to the page.
Column Settings Select to change the columns to view and the order they appear
on the page. For details see Customizing the log column views
on page 90.
Search Enter a keyword to perform a simple search on the available log
information. Select Go to begin the search. The number of
matches appears above the Search field.
Content archive Log rolling
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 91
2 Select a column name.
3 Select the up and down arrows to change the position of the column in the list.
Filtering content logs
When looking at content logs for both real-time and historical, you can filter the
information to find specific information. Filters are available when you are viewing
historical data in the Content Viewer or when browsing content log files on the
FortiAnalyzer hard disk.
Figure 33: Filter icons in the Historical content logs
Each column of data includes a gray filter icon. Select the icon to filter the
contents of the column. Enter the information you are looking for in the field
provided and select OK.When a filter is applied to a column, the filter icon appears
green.
To turn off the filter, select the filter icon and select Reset Filter. When viewing
real-time logs, you cannot filter on the time column because the time will always
be the current time.
Filtering tip
When filtering by source or destination IP, you can use the following in the filtering
criteria:
a single address (2.2.2.2)
an address range using a wild card (1.2.2.*)
an address range (1.2.2.1-1.2.2.100)
You can also use the boolean operator "or" to indicate multiple choices:
1.1.1.1 or 2.2.2.2
1.1.1.1 or 2.2.2.*
1.1.1.1 or 2.2.2.1-2.2.2.10
Log rolling
Log rolling is a way to control the content log file size and space used on the
FortiAnalyzer hard disk. You can configure the frequency of the log rolling and
what to do with the content log file when rolled.
As the FortiAnalyzer unit receives log messages, it performs the following tasks:
verifies whether the log file has exceeded its file size limit
if the file size is not exceeded, checks to see if it is time to roll the log file
Note: You must be viewing the log contents in the formatted view to use the filters.
Filter icon Filter in use
FortiAnalyzer Version 3.0 MR3 Administration Guide
92 05-30003-0082-20060925
Log rolling Content archive
When a content log file reaches its maximum size, or reaches the scheduled log
rolling time, the FortiAnalyzer unit saves the content log files with an incremental
number, and starts a new content log file with the same name. For example, the
current content log is clog.log. Any subsequent saved content logs appear as
clog.n.log, where n is the number of rolled logs. For example, clog.4.log.
To enable log rolling, go to Content Archive > Config.
Figure 34: Log rolling settings
Reuse Settings from
Standard Logs
Select to use the same settings that you set for standard log files,
set in Log > Config.
Log file should not
exceed
The maximum size of a content log file that the FortiAnalyzer unit
saves to the hard disk.
When the content log file reaches the specified maximum size, the
FortiAnalyzer unit saves current content log file with an
incremental number and starts a new active log file.
Log file should be
rolled
Set the time of day, when the FortiAnalyzer unit saves the current
content log file and starts a new active log file. Select Optional if
you do not want to use this option.
Enable log uploading Select to upload content log files to an FTP server whenever a
content log file rolls.
Server type Select the type of uploading server. Select from:
File Transfer Protocol (FTP)
Secure File Transfer Protocol (SFTP)
Secure Copy Protocol (SCP)
Server IP address Enter the IP address of the FTP server.
Username Enter the user name required to connect to the FTP server. The
user name has a default of anonymous. Click the field to enter a
different user name.
Password Enter the password required to connect to the FTP server.
Confirm Password Re-enter the password to ensure it is entered correctly.
Directory Enter a specific directory on the FTP server to save the log file.
Content archive Log rolling
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 93
Upload Log files Select when the FortiAnalyzer unit should upload files to the FTP
server.
Select When rolled to upload as soon as the FortiAnalyzer unit
rolls the content log file, based on the settings above.
Select a specific time of the day when the FortiAnalyzer unit
rolls the content log file. The FortiAnalyzer unit will upload at
the configured time no matter what the size of the log file is or
when it may be configured to roll to a new file.
Upload rolled files in
gzipped format
Select to compress the content log files in gzipped format before
uploading to the FTP server.
Delete files after
uploading
Select to remove the content log file from the FortiAnalyzer hard
disk once the FortiAnalyzer unit completes the upload.
FortiAnalyzer Version 3.0 MR3 Administration Guide
94 05-30003-0082-20060925
Log rolling Content archive
Quarantine Configuring quarantine settings
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 95
Quarantine
The FortiAnalyzer unit provides a repository for files quarantined by a FortiGate
unit. These files are considered a threat to the network, suspicious or of a
questionable nature. You can use the FortiAnalyzer quarantine support as a
central management location for all suspicious files under quarantine.The
communication between the two units is the same IPSec tunnel a FortiGate unit
uses when sending log files.
This section describes how to configure the FortiAnalyzer unit to receive these
quarantined files and view them on the FortiAnalyzer hard disk.
For details on configuring the FortiGate unit to send quarantined files to the
FortiAnalyzer unit, see the FortiGate Administration Guide.
This section includes the following topics:
Configuring quarantine settings
Viewing the quarantined files list
Configuring quarantine settings
Configure the quarantine settings to define the amount of hard disk space
allocated on the FortiAnalyzer unit for suspicious files.
To set the quarantine options, go to Quarantine > Config, and enter the amount
of disk space to allocate for storing quarantine files sent from the FortiGate units.
The FortiAnalyzer unit divides the amount of disk space you allocated for files
evenly between all registered FortiGate devices. For example, if you allocate 500
MB to quarantine files and you have five registered FortiGate units, each
FortiGate unit has 100 MB of space available for quarantined files. If you add
another FortiGate unit, each FortiGate unit will have less space available because
the allocated amount is now divided between more units.
The amount of disk space for quarantine files is allotted from the total disk space
allocated for the device. For example, if you allocate 500 MB for a FortiGate unit,
and 100 MB is allocated for quarantined files, the total space available for log files
is 400MB. For details see Adding a FortiGate unit on page 68.
Note: Sending quarantine files to the FortiAnalyzer unit is only available on FortiGate units
running FortiOS 3.0.
Note: The FortiAnalyzer unit is simply a recipient, or holding place of quarantined files from
the FortiGate unit. You need to configure the action the FortiGate unit performs when the
allocated disk space is filled with quarantined files. You can choose to overwrite older files
or drop the new quarantine files. For details on configuring the quarantine options, see the
FortiGate Administration Guide.
FortiAnalyzer Version 3.0 MR3 Administration Guide
96 05-30003-0082-20060925
Viewing the quarantined files list Quarantine
Viewing the quarantined files list
The quarantined files repository displays a list of quarantined files on the
FortiAnalyzer hard disk and information about each quarantined file.
To view quarantined files, go to Quarantine > Repository.
Figure 35: Viewing quarantined files
Show Select a device from the list of available devices to display the list
of quarantined files for a specific device, and select Go.
Time frame Select a span of time when quarantined files were sent to the
FortiAnalyzer unit and select Go.
Automatic Refresh
Interval
Select how often the quarantine page automatically updates.
Select Refresh Now to update the status page immediately.
Delete Select a file from the list by selecting the check box next to the
name and select Delete to remove the quarantined file from the
FortiAnalyzer hard disk.
Page n of n Select a page number x from the list of pages y and press Enter to
see the page.
View..per page Select the number of quarantined files to view on a single page.
From Device The name of the device where the quarantined file originated.
File Name The processed file name of the quarantined file.
Date & Time The date and time the FortiGate quarantined the file, in the format
yyyy/mm/dd hh:mm:ss. The time and date indicates the time that
the first file was quarantined, if duplicate files are quarantined.
Service The service where the file was quarantined (HTTP, FTP, IMAP,
POP3, SMTP).
Ticket # A 32-bit checksum the FortiGate unit performed on the file.
Status Description A short description of the reason why the FortiGate unit
quarantined the file.
DC Duplicate count. A count of how many duplicates of the same file
were quarantined. A rapidly increasing number can indicate a
virus outbreak.
Size (Bytes) The file size of the quarantined file.
Action Select Delete to remove the quarantined file from the
FortiAnalyzer hard disk.
Select Download to save the file to another location when it is
deemed safe for the recipient to collect.
Select Detail to view more information about the file including the
date and time of the quarantine and the sender and intended
recipient of the file.
Forensic Analysis Users and groups
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 97
Forensic Analysis
Forensic analysis provides a method of monitoring and reporting on individuals or
groups of individuals on their internet traffic, email and Instant Messaging (IM)
patterns within an organization.
While the Reports and other log data also provide this information, the forensic
analysis enables the administrator to narrow the information to specific individuals
or groups of individuals.
This section describes how to set up users and groups, search logs for user
activity and how to generate and view analysis reports.
This section includes the following topics:
Users and groups
Searching user data
Forensic Reports
Users and groups
Use forensic analysis to view the network and Internet usage habits of individual
users or groups of users. To do this, you must first add a list of users and their
network information. This includes the users IP address, user name, IM name(s)
and email address(es).
Adding users
Add users to the FortiAnalyzer analysis list for tracking. When adding a user, you
include their username, IP address, email address and IM names (if applicable). If
you only know part of the information you want to add, use Lookup to find
additional user information. For details on finding additional user information, see
Lookup on page 98.
To add a user to the forensic analysis list
1 Go to Forensic Analysis > Lookup > User.
2 Select Create New.
3 Enter the following information and select OK:
Note: The forensic analysis feature is not available on the FortiAnalyzer-100.
Name Enter the name of the user. The name cannot include spaces.
Username (in Logs) Enter the username as it will appear in the logs.
IP Address Enter the IP address of the user.
Email Address(es) Enter the email address for the user and select Add. For
completeness of the reports, add all known email addresses for
the user.
IM Name(s) Enter the instant message name for the user if applicable and
select Add. For completeness of the reports, add all known IM
names.
FortiAnalyzer Version 3.0 MR3 Administration Guide
98 05-30003-0082-20060925
Users and groups Forensic Analysis
Creating groups
Create user groups to obtain analysis information for a selection of users, rather
than running reports for a number of individuals. You must add individual users
before you can add them to a group.
To add a forensic analysis group
1 Go to Forensic Analysis > Lookup > Group.
2 Select Create New.
3 Enter the name of the group.
4 Select the users from the Available Users list, and select the right arrow to add
them to the group.
To remove a member, select a user from the Members list on the right and select
the left arrow.
5 Select OK.
Lookup
The Lookup provides a method of finding additional user information. For
example, if you know the users email address, you can use the lookup to find the
IP address or instant message user names. The User Lookup enables you to
have a complete user information base for forensic analysis reports.
To perform a user lookup, go to Forensic Analysis > Lookup > Lookup.
The following table describes what information you can find when you have partial
information.
Table 12: User lookup matrix
Lookup Using Result
IP address Username Returns all IP addresses where defined username
logged on.
Username IP address Returns all user names that logged on at the
defined address.
Email address IP address Returns all email originating from a defined
address.
IM name IP address Returns all IM names that logged on at a defined
IP address.
Forensic Analysis Users and groups
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 99
Figure 36: Lookup user information
Where does FortiAnalyzer get this information?
The FortiAnalyzer unit obtains user information from the FortiGate logs. The
following table outlines what logs the FortiAnalyzer refers to when retrieving user
information.
Lookup Select the information to look for in the log data.
Username / IP
Address
Depending on the Lookup selection, enter either the username or
IP address to find the associated information.
Time frame Select the time range in the logs that the FortiAnalyzer unit
searches.
All xx logged on yy
within the last zz
A visual indication of what you have selected and its relationship
to each other. Below this statement a list of available data will
appear. Select the check box beside each entry to add the data to
the user information.
User Select to add any of the results to an existing user in the forensic
analysis user table.
Create User / Add to
user
This button selection depends on whether you select a user from
the list.
Select Add to User when you select a user from the User list. The
FortiAnalyzer unit adds the information selected from the results to
the selected user information.
Select Create User to use the information entered above and
selected from the results, to create a new forensic analysis user
entry.
User Name Web filter log
IP Address Web filter log
Email address Email filter log. If not found, the FortiAnalyzer unit uses the content
logs.
IM name IM log. If not found, the FortiAnalyzer unit uses the content logs.
FortiAnalyzer Version 3.0 MR3 Administration Guide
100 05-30003-0082-20060925
Searching user data Forensic Analysis
To enable these log types on the FortiGate unit
1 Go to Firewall > Protection Profile
2 Select a protection profile.
3 Select Logging.
4 Select the activities to log and select OK.
Searching user data
The user data search enables you to perform a quick search on selected activity
of a specific user. Use the search to quickly see a users email, IM chat, FTP and
HTML activities for a selected time period.
To perform a user data search
1 Go to Forensic Analysis > Search > Search.
2 Set the following options and select Search:
After selecting Search, the FortiAnalyzer unit scans the content log data (data
from the Content Archive from a FortiGate unit) on its hard disk for all information
based on the criteria entered, and displays the number if results for each criteria.
Figure 37: Search results
Select View for the log information you want to view in detail. The search results
open in a new browser window.
Select download to save a specific log result to your local hard disk.
Saving search results
If you want to save these results for future reference, you can save the results to
the FortiAnalyzer hard disk. You can view the saved search results by selecting
Local Archive. For details see Local archive on page 101.
Search based on Select a search based on the user name or the IP address.
User / IP Address Select the search criteria. Depending on your search selection,
enter a user name or an IP address.
Time frame Select the span of time to view for the users activity.
Search for Select the information on the user or IP address that you want to
search for.
Forensic Analysis Forensic Reports
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 101
To save the results
1 Select Save Archive.
2 Enter a name for the search results. The name cannot include spaces.
3 Enter a Description to identify what was included in the search results.
4 Select Save.
Local archive
The local archive provides easy access to the forensic analysis searches that are
saved on the FortiAnalyzer unit.
To view the saved searches, go to Forensic Analysis > Search > Local Archive.
Select the Archive file name to view the search results.
Select Edit to change the archive name or description.
Select Delete to remove the search archive from the FortiAnalyzer hard disk.
Forensic Reports
The FortiAnalyzer unit collates information collected from device log files and
enables you to run reports for specific users or groups of user in tabular and
graphical reports, similar to the network reporting functionality. The reports
provide detailed information on a users website access, blocked web access,
email and FTP and IM usage during a specific period on your network.
Configuring reports
Create a report configuration profile that defines what information appears on a
report. Select the type of report, devices to include in the report, time frames to
provide specialized reports.
To configure a forensic analysis report profile
1 Go to Forensic Analysis > Report > Config.
2 Select Create New.
3 Enter a Report Name.
The report name cannot include spaces.
4 Enter a title and a description of what the report includes.
5 Select the blue arrow next to the options you need to configure:
6 Select OK.
Properties Select to add logos, headers, footers and company information to
customize the report.
Report Criteria Select the information you want to include in the report.
Time Period Select the filtering information and time range for the reporting
period.
Forensic Report
Type(s)
Select the reports to include.
Output Select the file format for the reports.
FortiAnalyzer Version 3.0 MR3 Administration Guide
102 05-30003-0082-20060925
Forensic Reports Forensic Analysis
Customizing the report properties
Customize the report with company or branch information and logos to create a
professional report.
Figure 38: Customizing the report properties
When adding a logo to the report, consider the following table to ensure you select
the correct logo format for the report created. If you select a logo that is not
supported for a report format, the logo will not appear in the report.
Table 13: Report formats and supported logo formats
Configuring the report criteria
Select the type of results you would like to include in the report.
Company Name Enter the name of your company, department or branch.
Header Comment Enter a title or information to include in the header of the report.
Footer Comment Select the information to include in the footer of the report:
Select Report Title to use the title of the report entered in the
first step of creating a new report profile.
Select Custom to add your own information.
Title Page Logo Add a company logo to the title page of the report. Select Custom
to locate the logo and select Upload to save it to the FortiAnalyzer
hard disk for use in the report.
Header Logo Add a smaller company logo to the headers of the report. Select
Custom to locate the logo and select Upload to save it to the
FortiAnalyzer hard disk for use in the report.
PDF Reports PNG
RTF Reports JPG, PNG, GIF and WMF
HTML Reports All formats supported.
Forensic Analysis Forensic Reports
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 103
Figure 39: Configuring the forensic analysis report criteria
Report Profile Select to save the report profile for future reports or On Demand
to use the report profile once. Once the FortiAnalyzer unit runs the
report, the profile created is removed from the system.
Report Category Select the type of analysis to include in the report, either user or
device.
User Select a user from the list. Alternatively, select Specify and select
an option from the Specify list.
This setting is available when using the User Analysis Report
Category.
Specify Select to generate a report based on a specific user name or IP
address. This option becomes available when selecting Specify
from the User selection.
This setting is available when using the User Analysis Report
Category.
Source IP Address
Username (in logs)
Depending on the selection from the Specify list, enter the
appropriate information.
This setting is available when using the User Analysis Report
Category.
Group Select to generate a report on a specific user group.
This setting is available when using the User Analysis Report
Category.
Group Name (in logs) Enter a specific group name. This option becomes available when
selecting Specify from the Group selection.
This setting is available when using the User Analysis Report
Category.
Report Granularity Select the number of results for the report.
This setting is available when using the User Analysis and Device
Analysis Report Categories.
Device(s) Select a device or device group.
This setting is available when using the User Analysis and Device
Analysis Report Categories.
Virtual Domains Enter a virtual domain name for the report.
This setting is available when using the Device Analysis Report
Category.
Resolve Host Names Select to display host names by a recognizable name rather than
IP addresses. For details on configuring IP address host names,
see IP Aliases on page 53.
Resolve Service
Names
Select to display network service names rather than port numbers.
For example, HTTP rather than port 80.
FortiAnalyzer Version 3.0 MR3 Administration Guide
104 05-30003-0082-20060925
Forensic Reports Forensic Analysis
Configuring the time period
Select a time span for the report period or select a specific time frame. When the
FortiAnalyzer unit generates the report, it uses the log data found within the
specified time period only.
Figure 40: Report configuration time period options
Configuring the report types
Select the type of information you want to include in the report. Select the blue
arrow to expand the report categories and select individual reports.
Configuring the report output
Select destination and format for the report. Configure the FortiAnalyzer unit to
either save the reports to the FortiAnalyzer hard disk or email the report to any
number of recipients or both.
When configuring the FortiAnalyzer unit to email a report, you must configure the
mail server on the FortiAnalyzer unit. For details see Mail server on page 133.
Include Summary
Information
Select to include a roll up of the report contents.
Include Table of
Contents
Select to include a table of contents for the report.
Time Period Select a time range the report will be focused on.
From: Select the beginning date and time for the report.
To: Select the ending date and time for the report.
Note: If you are emailing HTML reports to a user, and their email client does not support
HTML, they will see the HTML code for each report in the message body.
Forensic Analysis Forensic Reports
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 105
Figure 41: Forensic analysis report output configuration
File output Select the file format for the generated reports that are saved to
the FortiAnalyzer hard disk. To access the reports on the hard
disk, see Viewing Forensic Reports on page 106.
Select from the following:
HTML
Adobe PDF
MS Word format (RTF)
ASCII Text
Multi purpose Internet Mail Extension HTML format (MHT)
Email output Select the file formats for the generated reports that the
FortiAnalyzer unit sends as an email attachment.
Select from the following:
HTML
Adobe PDF
MS Word format (RTF)
ASCII Text
Multi purpose Internet Mail Extension HTML format (MHT)
Email subject Enter a subject to the email FortiAnalyzer sends. When not
selected, the subject line is the name of the report.
To select the Customize subject check box, you must select a file
format from the Email output list.
Email Attachment
name
Enter the name for the report files included in the email. When you
select multiple reports for the report profile, the FortiAnalyzer unit
compresses all reports into a zip file. This option enables you to
select the name for the zip file.
Email Body Enter the text to include in the body of the email message.
Email from Enter an email address for the FortiAnalyzer unit or administrator
requesting the report.
FortiAnalyzer Version 3.0 MR3 Administration Guide
106 05-30003-0082-20060925
Forensic Reports Forensic Analysis
Viewing Forensic Reports
Use the FortiAnalyzer web-based manager to view a list of the generated forensic
analysis reports. To view generated forensic analysis reports, go to Forensic
Analysis > Reports > Browse.
Figure 42: Browse generated reports
Email server Select the email server to use when the FortiAnalyzer unit sends
the reports as an email attachment.
Email to Enter the email addresses of the recipients of the report. Add
multiple recipients by pressing Enter after each email address.
Addresses appear in the Email List.
Upload Report to FTP
Server
Select to upload completed report files to an FTP server.
Server type Select the type of uploading server. Select from:
File Transfer Protocol (FTP)
Secure File Transfer Protocol (SFTP)
Secure Copy Protocol (SCP)
IP address Enter the IP address of the FTP server.
Username Enter the user name to log onto the FTP server.
Password Enter the password to log onto the FTP server.
Directory Enter the directory on the FTP server where the FortiAnalyzer unit
saves the report files.
Upload report(s) in
gzipped format
Select to compress the report files as gzip files before uploading
to the FTP server.
Delete file(s) after
uploading
Select to delete the report files from the FortiAnalyzer hard disk
once the FortiAnalyzer unit completes the upload to the FTP
server.
Delete Select to remove multiple reports. Before selecting Delete, select the
check boxes for the reports you want to remove.
Page n of n Enter a page number to jump to. Press Enter to jump to the page.
Report Files Displays the generated reports.Select the report name to view a the
report in HTML format.
Start Time indicates the date and time when the FortiAnalyzer unit generated
the report.
End Time Indicates the date and time when the FortiAnalyzer unit completed
the report. If the FortiAnalyzer unit is in the process of generating a
report, a progress bar will appear in this column.
Size (bytes) The file size of the report.
Other Formats By default, the FortiAnalyzer unit create the report in HTML format. If
you selected other formats when creating the report profile, they
appear in this column.
Action Select Delete to remove the report from the FortiAnalyzer hard disk.
Select Rename to change the name of the report from the default
created by the FortiAnalyzer unit.
Delete
Rename
Traffic summary and security events Traffic Summaries
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 107
Traffic summary and security events
Using the submitted log messages from registered devices, the FortiAnalyzer unit
provides data mining features that enables you to access simple reports on a
number of different intrusion attempts against your network as well as the types of
traffic occurring on your network.
This section includes the following topics
Traffic Summaries
Security event summaries
Traffic Summaries
Traffic summaries are pre-defined reports that provide a snapshot of the traffic
passing through the firewall on your network. The reports can help you identify
who the high volume users and FortiGate units are that may be affecting overall
network traffic. Hourly reports are updated every ten minutes, weekly, daily and
monthly reports are updated every hour.
These reports can help you in determining traffic flow issues and provide a basis
for configuring traffic shaping on a FortiGate unit to better control traffic flow
throughout the day. For details on traffic shaping, see the FortiGate
Administration Guide.
This section includes the following topics:
Top Users
Device Summary
Traffic Report
Top Users
Top users enables you to view the users that create the most traffic for each
service including web, email, FTP and IM/P2P. The tabular data presented shows
the user, which firewall they are using and the amount of data traffic created.
Viewing Web traffic
The Web Traffic page provides a summary of the HTTP and HTTPS usage per
user on the network.
To view the web traffic, go to Network Summary > Top Users > Web Traffic.
Figure 43: Viewing web traffic
FortiAnalyzer Version 3.0 MR3 Administration Guide
108 05-30003-0082-20060925
Traffic Summaries Traffic summary and security events
Clicking the column headers sorts the information in ascending or descending
order for that column.
Viewing Email traffic
The Email Traffic page provides a summary of the email usage per user on the
network.
To view the web traffic, go to Network Summary > Top Users > Email Traffic.
Figure 44: Viewing email traffic
Web activity within
the last
Select a time frame for viewing the web traffic.
View Select a device or group of devices.
Total Web activity for
the period
An overview of the amount of data, in megabytes, transferred via
the web.
View per page Select the number of log messages displayed on each page.
Page n of n Enter the page number you want to display and press Enter.
Search Enter a search criteria and select Go. Log entries with the search
results appear in the list.
Resolve Host Name Select to view a real name for the Host column rather than an IP
address. For this feature to work correctly, you must set the IP
aliases. For details see IP Aliases on page 53.
Firewall The name of the FortiGate unit.
Host (Source) The IP address of the FortiGate unit.
Traffic The amount of data transferred through HTTP and HTTPS within
the period.
Last Activity The date and time of the last email message.
Downloads The number of downloads that occurred within the period.
Uploads The number of uploads that occurred within the period.
Email activity within
the last
Select a time frame for viewing the web traffic.
View Select a device or group of devices.
View per page Select the number of log messages displayed on each page.
Page n of n Enter the page number you want to display and press Enter.
Search Enter a search criteria and select Go. Log entries with the search
results appear in the list.
Resolve Host Name Select to view a real name for the Host column rather than an IP
address. For this feature to work correctly, you must set the IP
aliases. For details see IP Aliases on page 53.
Total Email activity
for the period
An overview of the amount of data, in megabytes, sent and
received through email.
Firewall The name of the FortiGate unit.
Host (Source) The IP address of the FortiGate unit.
Traffic summary and security events Traffic Summaries
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 109
Clicking the column headers sorts the information in ascending or descending
order for that column.
Viewing FTP traffic
The FTP Traffic page provides a summary of the FTP usage per user on the
network.
To view the web traffic, go to Network Summary> Top Users > FTP Traffic.
Figure 45: Viewing FTP traffic
Clicking the column headers sorts the information in ascending or descending
order for that column.
Viewing Instant Messaging and P2P traffic
The Instant Messaging (IM) and P2P Traffic page provides a summary of the IM
usage per user on the network.
To view the web traffic, go to Network Summary > Top Users > IM/P2P Traffic.
Traffic The amount of data transferred through sent and received within
the period.
Last Activity The date and time of the last email message.
Upload The number of outgoing email messages that occurred within the
period.
download The number of incoming email messages that occurred within the
period.
FTP activity within
the last
Select a time frame for viewing the FTP traffic.
View Select a device or group of devices.
View per page Select the number of log messages displayed on each page.
Page Enter the page number you want to display and press Enter.
Search Enter a search criteria and select Go. Log entries with the search
results appear in the list.
Resolve Host Name Select to view a real name for the Host column rather than an IP
address. For this feature to work correctly, you must set the IP
aliases. For details see IP Aliases on page 53.
Total FTP activity for
the period
An overview of the amount of data, in megabytes, transferred.
Firewall The name of the firewall.
Host (Source) The IP address of the firewall.
Traffic (MB) The amount of data transferred within the period.
Last Activity The date and time of the last FTP transfer.
Uploads The number of uploads that occurred within the period.
Downloads The number of downloads that occurred within the period.
FortiAnalyzer Version 3.0 MR3 Administration Guide
110 05-30003-0082-20060925
Traffic Summaries Traffic summary and security events
Figure 46: Viewing IM/P2P traffic
Clicking the column headers sorts the information in ascending or descending
order for that column.
Filtering traffic summaries
When looking at user traffic summaries, you can filter the information to find
specific information.
Figure 47: Filter icons in the User web activity
Each column of data includes a gray filter icon. Select the icon to filter the
contents of the column. Enter the information you are looking for in the field
provided and select OK.
When a filter is applied to a column, the filter icon appears green.
To turn off the filter, select the filter icon and select Reset Filter.
IM activity within the
last
Select a time frame for viewing the IM traffic.
View Select a device or group of devices.
View per page Select the number of log messages displayed on each page.
Page Enter the page number you want to display and press Enter.
Search Enter a search criteria and select Go. Log entries with the search
results appear in the list.
Resolve Host Name Select to view a real name for the Host column rather than an IP
address. For this feature to work correctly, you must set the IP
aliases. For details see IP Aliases on page 53.
Total IM activity for
the period
An overview of the amount of data, in megabytes, transferred by
IM. This includes messages and file transfers.
Firewall The name of the firewall.
Host (Source) The IP address of the firewall.
Traffic (MB) The amount of data transferred with IM within the period.
Last Activity The date and time of the last instant message.
Messages The number of messages that were sent and received within the
period.
File Transfers The number of file transfers that occurred within the period.
Filter icon Filter in use
Traffic summary and security events Traffic Summaries
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 111
When viewing real-time logs, you cannot filter on the time column because the
time will always be the current time.
Filtering tip
When filtering by source or destination IP, you can use the following in the filtering
criteria:
a single address (2.2.2.2)
an address range using a wild card (1.2.2.*)
an address range (1.2.2.1-1.2.2.100)
You can also use the boolean operator "or" to indicate multiple choices:
1.1.1.1 or 2.2.2.2
1.1.1.1 or 2.2.2.*
1.1.1.1 or 2.2.2.1-2.2.2.10
Device Summary
The device summary provides a graphical analysis of the network traffic by
FortiGate unit. The summary provides graphical details in real-time for all
FortiGate units, by group or individually. All FortiGate units appearing must be
properly registered with the FortiAnalyzer unit.
The device summaries include:
Protocol distribution - the overall protocol traffic and breakdown by upload and
download traffic.
Web and FTP - traffic by host, top FTP and web server and volume.
Email - top SMTP, POP3 and IMAP servers and top email sender activity.
Multimedia - top RTSP and MMS server activity.
To view the device summary graphs, go to Network Summary > Device
Summary.
Figure 48: Viewing protocol distribution
FortiAnalyzer Version 3.0 MR3 Administration Guide
112 05-30003-0082-20060925
Traffic Summaries Traffic summary and security events
Traffic Report
The traffic report enables you to generate a report to aggregate all the traffic
summary information rather than viewing the pages in Realtime Analysis > Top
Users individually. Similar to the log reports and forensic analysis, the
FortiAnalyzer unit generates a report and saves it on the FortiAnalyzer hard disk
for viewing and distribution.
Configuring a traffic report
Create a report configuration profile that defines what information appears on a
report. Select the type of report, devices to include in the report, time frame to
provide specialized reports.
To configure a traffic report
1 Go to Network Summary > Traffic Report > Config.
2 Set the following options and select Generate Now:
Viewing traffic summary reports
Use the FortiAnalyzer web-based manager to view a list of the generated traffic
summary reports. To view generated the reports, go to Network Summary >
Traffic Report > Browse.
Figure 49: Browse generated traffic summary reports
Device Select a device or device group.
Time frame Select the time span to display on the graphs.
Name Enter a name for the traffic summary report.
Time Period Select the span of time the report will encompass.
Include Top Users
Summary
Select to include a roll-up of the most active network users.
Device Selection Select the device or group of devices to include.
Report Output Select the file type for the report. Select from PDF or Microsoft
Word (RTF) formats.
Name Displays the generated reports.
Start Time indicates the date and time when the FortiAnalyzer unit generated
the report.
End Time Indicates the date and time when the FortiAnalyzer unit completed
the report. If the FortiAnalyzer unit is in the process of generating
a report, a progress bar will appear in this column.
Formats Displays the report formats available, based on the selection from
the report configuration. Select the format to view the report.
Action Select Delete to remove the report from the FortiAnalyzer hard
disk.
Traffic summary and security events Security event summaries
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 113
Security event summaries
Security event summaries are reports that provide a snapshot of unwanted traffic
that is attempting to breach the firewall. The FortiAnalyzer unit has four default
event reports that are updated daily:
Virus
Intrusion
Suspicious
Administrative.
Adding a security event report
The FortiAnalyzer unit includes default security event reports for virus, intrusion
and suspicious activity events. You can add customized event correlation reports
to configure when the FortiAnalyzer unit generates the reports and what device
logs the FortiAnalyzer uses in compiling the report.
To configure an event correlation
1 Go to Network Summary > Config > Event Correlation.
2 Select Create new.
3 Complete the following options and select OK:
Viewing the security event reports
To view the event correlations report details, go to Network Summary > Config >
Event Correlation.
Name Enter a name for the event correlation report.
Devices/Groups Select a device or group of devices that the FortiAnalyzer unit runs
the report against. The FortiAnalyzer unit uses the logs for the
selected device(s).
Run Engine Select to generate either a daily report or a weekly report of event
activity.
Time Select the time of day when the FortiAnalyzer unit runs the report.
Select Daily and select the time of the day to run the report each
day.
Select Weekly, and select the days of the week when the
FortiAnalyzer unit runs the report each week.
Engine Type Select the type of event correlation report to run.
Ignore hosts that
have less than n
incidents
Select to set a threshold for the number of incidents occurring
from an individual source, and set the threshold value. For
example, if a single source tries to send multiple viruses more
than the set threshold, then the FortiAnalyzer unit considers it one
virus event.
Ignore hosts whose
traffic is less than n
MB
This option appears only when configuring a Suspicious report.
Select to set a threshold for the minimum acceptable amount of
traffic occurring from an individual source, and set the threshold
value. For example, if a single source tries to send multiple
viruses or attacks more than the set threshold for content traffic,
then the FortiAnalyzer unit considers it one virus event.
FortiAnalyzer Version 3.0 MR3 Administration Guide
114 05-30003-0082-20060925
Security event summaries Traffic summary and security events
Figure 50: Viewing event correlation report list
Viewing virus activity
The Virus Activity page correlates all virus logs stored on the FortiAnalyzer unit
and produces a report of the overall virus activity on the network. The
FortiAnalyzer unit reviews the virus logs at a scheduled interval, providing access
to the virus activity on your network. For details on configuring the virus event
correlation, Adding a security event report on page 113.
To view virus activity, go to Network Summary > Virus Activities.
Figure 51: Viewing Virus activity
Report Engine The name of the report. The FortiAnalyzer unit includes three
default report engines for Virus, Intrusion and Suspicious.
Frequency The time when the FortiAnalyzer unit runs a report.
Devices/Groups The device or group of device logs the FortiAnalyzer unit uses
when generating the report.
Threshold Indicates the maximum number of times a host has attempted to
attack or infect users on the network before it is included in the
report. For a virus event, it also indicates the amount of traffic in
megabytes that is acceptable from a single source before it is
considered a virus event. The Traffic threshold is only available on
Suspicious event reports.
Action Select Delete to remove the report name. Note that the Virus,
Intrusion and Suspicious reports are included by default. You
cannot delete these reports from the FortiAnalyzer unit.
Select Edit to modify the configuration of the report.
Select Go to run the report immediately.
Select View to view the report results.
Create New Select to add a new event correlation report.
Delete
Edit
Run report
View report
Details
Acknowledge
Traffic summary and security events Security event summaries
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 115
Viewing Intrusion activity
The Intrusion Activity page correlates all intrusion logs stored on the FortiAnalyzer
unit and produces a report of the overall intrusion activity on the network. The
FortiAnalyzer unit reviews the intrusion logs at a scheduled interval, providing you
with easy access to the intrusion activity on your network. For details on
configuring the intrusion activity correlation, see Adding a security event report
on page 113.
To view intrusion activity, go to Network Summary > Intrusion Activities.
Figure 52: Viewing Intrusion activity
Virus activity within
the last
Select the time frame to view the virus activity.
View Select a device or group of devices.
Firewall The name of the firewall.
Host (Source) The source IP address of the firewall.
Virus The name of the virus.
Last Activity The date and time of the last incident of the virus.
Count The number of incidents made by the virus on the network.
Action Select Details to display additional information for the entry. The
details window displays further details of the virus incidents
including time and date, target and protocol attempt.
Select Acknowledge to reset the attack count to zero for the virus.
This enables you to verify if the firewall has new virus incidents, as
well as watch the number of incidents occurring.
Intrusion activity
within the last
Select the time frame to view the virus activity.
View Select a device or group of devices.
Firewall The name of the firewall.
Host (Source) The source IP address of the firewall.
Attack Name The name of the intrusion event The attack name is a link to the
FortiGuard Center. Selecting the link opens the FortiGuard web
site and displays information on the attack from the FortiGuard
database.
Last Activity The date and time of the last intrusion incident.
Details
Acknowledge
FortiAnalyzer Version 3.0 MR3 Administration Guide
116 05-30003-0082-20060925
Security event summaries Traffic summary and security events
Viewing Suspicious activity
The Suspicious Activity page displays any activity that may be considered
suspicious or unusual network traffic.
The FortiAnalyzer unit reviews the Traffic and Session information of the selected
FortiGate units to see the average traffic pattern. The top 30 IP addresses with
traffic that is above average will be considered under suspicion of being viral, and
are included in the report. This can include a high number of sessions to a device,
or the sending of unusually high quantity of email traffic. The report provides you
with easy access to the state of the traffic usage on the network. For details on
configuring the suspicious activity correlation, see Adding a security event report
on page 113.
To view intrusion activity, go to Network Summary> Suspicious Activities.
Figure 53: Viewing Suspicious activity
Count The number of intrusion incidents on the network.
Action Select Details to display any additional information for the entry.
The details window displays further details of the virus incidents
including time and date, target and protocol attempt.
Select Acknowledge to reset the attack count to zero for the
intrusion counter. This enables you to verify if the firewall has new
intrusion incidents as well as watch the number of incidents
occurring.
Note: The Suspicious activity reports do not display information on the Suspicious virus.
To view virus activity, see Viewing virus activity on page 114.
Intrusion activity
within the last
Select the time frame to view the virus activity.
View Select a device or group of devices.
Traffic Usage Enter the top number of firewall devices to include in the traffic
usage report. The FortiAnalyzer will report on up to 30 addresses.
Total traffic The total amount of data travelling through all firewalls listed.
Firewall The name of the firewall.
Host (Source) The source IP address of the firewall.
Usage (MB) The amount of data in megabytes travelling through the firewall.
Details
Acknowledge
Traffic summary and security events Security event summaries
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 117
Viewing administrative activities
The Administration Activity page correlates all administration log entries from the
event logs stored on the FortiAnalyzer unit and produces a report of the overall
administrative activity occurring on the FortiGate units on the network.
To view administrative activity, go to Network Summary > Administrative
Activities.
Figure 54: Viewing Administration activity
Last Activity The date and time of the last incident of the virus.
Number of Sessions The number of incidents made by the virus on the network.
Action Select Acknowledge to reset the session count to zero.
Select Details to display the traffic generated by the IP address.
Session Usage Enter the top number of firewall devices to include in the session
usage report. The FortiAnalyzer will report on up to 30 addresses.
Firewall The name of the firewall.
Host (Source) The source IP address of the firewall.
Last Activity The date and time of the last high session activity.
Number of Sessions The number of incidents made by the virus on the network.
Action Select Acknowledge to reset the session count to zero.
Select Details to display further details regarding the IP address
use.
Administrative
activity within the last
Select the time frame to view the administrative activity.
View Select a device or group of devices.
Firewall The name or serial number of the FortiGate unit.
User The user name of the last administrative user to perform an
administrative task on the unit.
Last Action The administrative function performed by the user.
Last Activity The date and time when the user performed the administrative
action.
Count The number of administrative activities logged for the FortiGate
unit.
Action Select Details to display any additional information for the entry.
The details window displays further details of the administrative
events.
Select Acknowledge to reset the attack count to zero for the
administrative activities. This enables you to monitor events on a
regular basis if required.
Details
Acknowledge
FortiAnalyzer Version 3.0 MR3 Administration Guide
118 05-30003-0082-20060925
Security event summaries Traffic summary and security events
Reports Configuring reports
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 119
Reports
The FortiAnalyzer unit collates information collected from device log files and
presents the information in tabular and graphical reports. The reports provide
detailed information on the type of traffic, attacks and preventative actions that
occurred during a specific period on your network.
Using reports you can:
manage your network more effectively and to make informed decisions
view network usage and patterns
discover and address vulnerabilities across dispersed device installations
minimize the effort required to monitor and maintain acceptable user policies,
identify attack patterns and prevent attacks
monitor Internet surfing patterns for compliance with company policy
identify visitors to your web site for potential customers
This section includes the following topics:
Configuring reports
Browsing reports
Configuring reports
Create a report configuration profile that defines what information appears on a
report. Select the type of report, devices to include in the report and time frames
to provide specialized reports.
To configure a report profile, go to Report > Config.
FortiAnalyzer Version 3.0 MR3 Administration Guide
120 05-30003-0082-20060925
Configuring reports Reports
Figure 55: Viewing report profiles
Configuring a report profile
To enable the FortiAnalyzer unit to run a report, you need to configure the report
profile options on the focus of the report.
To configure a report profile
1 Go to Report > Config.
2 Select Create New.
3 Enter a Report Name. The report name cannot include spaces.
Create New Select to create a new report profile and configure its settings and
schedule.
# The number of report profiles on the FortiAnalyzer unit.
Report The name of the report profile.
Device(s) The device or device group included in the configured report
profile.
Schedule The scheduled frequency when the FortiAnalyzer unit generates
the report.
Action Select Delete to remove the configured report.
Select Edit to modify the report configuration.
Select Clone to create a duplicate of a report to use as a starting
point for a new report profile.
Select Go to run a report profile at any time (on demand). Select
Go when you do not have a scheduled time for the FortiAnalyzer
unit to run a report.
Delete
Edit
Clone
Run Report
Reports Configuring reports
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 121
4 Select to run the report immediately after configuration (on demand) or run the
report at configured intervals.
When selecting an on demand report, the FortiAnalyzer unit does not save the
report profile after the generating the report.
5 Enter a Report Title and Description.
6 Select the blue arrow next to the options you need to configure:
7 Select OK.
Customizing the report properties
Customize the report with company or branch information and logos to create a
professional report.
Figure 56: Customizing the report properties
When adding a logo to the report, consider the following table to ensure you
select the correct logo format for the report created. If you select a logo that is not
supported for a report format, the logo will not appear in the report.
Properties Select to add logos, headers, footers and company information to
customize the report.
Devices Select the devices or groups of devices to include in the report.
Report Scope Select the filtering information and time range for the reporting
period.
FortiGate Report
Type(s)
Select the reports to include.
Report Format Select how the report information is displayed in the report, by
device or for all devices.
Schedule Configure when the FortiAnalyzer unit runs the report, for
example, weekly, or monthly.
Output Select the file format for the reports.
Company Name Enter the name of your company, department or branch.
Header Comment Enter a title or information to include in the header of the report.
Footer Comment Select the information to include in the footer of the report:
Select Report Title to use the title of the report entered in the
first step of creating a new report profile.
Select Custom to add your own information.
Title Page Logo Add a company logo to the title page of the report. Select Custom
to locate the logo and select Upload to save it to the FortiAnalyzer
hard disk for use in the report.
Header Logo Add a smaller company logo to the headers of the report. Select
Custom to locate the logo and select Upload to save it to the
FortiAnalyzer hard disk for use in the report.
FortiAnalyzer Version 3.0 MR3 Administration Guide
122 05-30003-0082-20060925
Configuring reports Reports
Table 14: Report formats and supported logo formats
Configuring the report devices
Select the device or device groups you want to include in the reports from the list.
All registered devices and groups appear in the list.
If you want a report on multiple devices, create a group and add the devices to the
group. For details on creating a group, see Device Groups on page 74.
Configuring the report scope
The report scope includes the data inclusion options. Select the time span and
filter information for the data to include in the reports.
Select the blue arrow to expand the Time Period options. Select a time span
for the report period or select a specific time frame. When the FortiAnalyzer
unit generates the report, it uses the log data found within the specified time
period only.
Figure 57: Report configuration time period options
Select the blue arrow to expand the Data Filter options. Filtering enables you
to view or remove information from a report to provide a more concise report.
For example, you only want reports on specific error messages, or you do not
want include certain IP address destinations.
Figure 58: Report configuration log filter
PDF Reports PNG
RTF Reports JPG, PNG, GIF and WMF
HTML Reports All formats supported.
Time Period Select a time range the report will be focused on.
From: Select the beginning date and time for the report.
To: Select the ending date and time for the report.
Reports Configuring reports
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 123
Filter logs Select None to not apply a filter to the logs in the report.
Select Include logs that match of the following criteria to
customize the filtering.
Include logs that
match
Select the matching criteria for the filter.
Select all to include logs in the report that match all filter settings.
If information within a log does not match all the criteria, the
FortiAnalyzer unit will not include the log in the report.
Select any to include logs in the report that match any of the filter
settings. If any of the filter content, even one filter setting, matches
information in a log file, the FortiAnalyzer unit includes the log in
the report.
Priority Select the check box to enable the priority level filter options.
Set the priority level to look for in the logs and set whether the
information should be less than, greater than or equal to the
priority level.
Source(s) Enter the source IP address for the matching criteria. Use the
Alias list to select sources by name. For details on adding IP
Aliases, see IP Aliases on page 53. Use a comma to separate
multiple sources.
Select Not to exclude the source IP address from the report. For
example, do not include any information from a specific source IP
address in the log report.
Destination(s) Enter the destination IP address for the matching criteria. Use the
Alias list to select sources by name. For details on adding IP
Aliases, see IP Aliases on page 53. Use a comma to separate
multiple sources.
Select Not to exclude the destination IP address from the report.
For example, do not include any information from a specific
destination IP address in the log report.
You can filter on IP ranges, including subnets to report on groups
within the company. For example:
172.20.110.0-255 filters all IP addresses in the
172.20.110.0/255.255.255.0 or 172.20.110.0/24 subnet
172.20.110.0-140.255 filters all IP addresses from
172.20.110.0 to 172.20.140.255
172.16.0.0-20.255.255 filters all IP addresses from 172.16.0.0
to 172.20.255.255)
Interface(s) Enter the FortiGate interface you want to include in the report.
Separate multiple interface names with a comma.
Select Not to exclude the interface information from the report. For
example, do not include any information from a specific interface
in the log report.
User(s) Enter the user names to include in the report. Separate multiple
user names with a comma.
Group(s) Enter the user groups to include in the report. Separate multiple
groups with a comma. User groups are configured on the
FortiGate unit.
Virtual Domain(s) Enter the virtual domains (VDOM) to include in the report.
Separate multiple VDOMs with a comma.
Select Not to exclude the VDOM from the report. For example, do
not include any information from a specific VDOM in the log
report.
Policy ID(s) Enter the firewall policy ID numbers to include in the report. The
report will include the traffic information from the FortiGate firewall
policies in the logs. Separate multiple policy IDs with a comma.
FortiAnalyzer Version 3.0 MR3 Administration Guide
124 05-30003-0082-20060925
Configuring reports Reports
Configuring the report types
Select the type of information you want to include in the report:
Select Basic to include the most common report types.
Select All to include all report types. If data does not exist for a report type, that
report will appear with the message No matching log data for this report.
Select Custom to select the reports you want to include. Select the blue arrow
to expand the report categories and select individual reports.
Configuring the report Format
Select the type of results you would like to include in the report.
Figure 59: Report configuration report format
Select the blue arrow to expand the Advanced options.
Service(s) Enter specific services to include in the report. Separate multiple
services with a comma.
Select Not to exclude the service from the report. For example, do
not include any information from a specific service in the log
report.
Message(s) Enter specific email messages you want the report to include from
the email reports. Separate multiple messages with a comma.
Day of the Week Select the days of the week that the information is pulled from the
log files to include in the report.
Report Results Select how the data for the report will be presented. Select to
have the data appear collectively for all devices or for each device
separately. If no selection is made, the FortiAnalyzer will generate
reports for all devices by default.
Resolve Host Names Select to display host names by a recognizable name rather than
IP addresses. For details on configuring IP address host names,
see IP Aliases on page 53.
Resolve Service
Names
Select to display network service names rather than port numbers.
For example, HTTP rather than port 80.
Include Summary
Information
Select to include a roll up of the report contents.
Include Table of
Contents
Select to include a table of contents for the report.
Reports Configuring reports
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 125
For some report types, you can set the top ranked items for the report. These
reports have Top in their name, and will always display only the top n entries. For
example, report on the most active mail clients within the organization rather than
all mail clients.
Reports that do not include Top in their name will always display all information.
Changing the values for top field will not affect these reports.
Configuring the report schedule
Set a schedule when the FortiAnalyzer unit generates the reports. Choose a
recurring schedule. For example, to generate weekly reports on mail traffic.
Figure 60: Report configuration schedule
Configuring the report output
Select destination and format for the report. Configure the FortiAnalyzer unit to
either save the reports to the FortiAnalyzer hard disk or email the report to any
number of recipients or both.
When configuring the FortiAnalyzer unit to email a report, you must configure the
mail server on the FortiAnalyzer unit. For details see Mail server on page 133.
Not Scheduled Select to not generate a daily report. Use this setting when you
only want to run the reports as needed.
Daily Select to generate the report every day at the same time.
These Days Select specific days of the week to generate the report.
These Dates Select specific days of the month to generate the report. For
example, to generate the report on the first and fifteenth of every
month, enter 1,15.
Time Select the time of the day when the FortiAnalyzer generates the
report.
Note: If you are emailing HTML reports to a user, and their email client does not support
HTML, they will see the HTML code for each report in the message body.
FortiAnalyzer Version 3.0 MR3 Administration Guide
126 05-30003-0082-20060925
Configuring reports Reports
Figure 61: Report output configuration
File output Select the file format for the generated reports that are saved to
the FortiAnalyzer hard disk. To access the reports on the hard
disk, see Viewing reports on page 128.
Select from the following:
HTML
Adobe PDF
MS Word format (RTF)
ASCII Text
Multi purpose Internet Mail Extension HTML format (MHT)
Email output Select the file formats for the generated reports that the
FortiAnalyzer unit sends as an email attachment.
Select from the following:
HTML
Adobe PDF
MS Word format (RTF)
ASCII Text
Multi purpose Internet Mail Extension HTML format (MHT)
Email subject Enter a subject to the email FortiAnalyzer sends. When not
selected, the subject line is the name of the report.
To select the Customize subject check box, you must select a file
format from the Email output list.
Email Attachment
name
Enter the name for the report files included in the email. When you
select multiple reports for the report profile, the FortiAnalyzer unit
compresses all reports into a zip file. This option enables you to
select the name for the zip file.
Email Body Enter the text to include in the body of the email message.
Reports Browsing reports
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 127
Browsing reports
Use the FortiAnalyzer web-based manager to view a list of the generated reports.
To view generated reports, go to Report > Browse.
Figure 62: Browse generated reports
Email from Enter an email address for the FortiAnalyzer unit or administrator
requesting the report.
Email server Select the email server to use when the FortiAnalyzer unit sends
the reports as an email attachment.
Email to Enter the email addresses of the recipients of the report. Add
multiple recipients by pressing Enter after each email address.
The addresses appear in the Email list box.
Upload Report to FTP
Server
Select to upload completed report files to an FTP server.
Server type Select the type of uploading server. Select from:
File Transfer Protocol (FTP)
Secure File Transfer Protocol (SFTP)
Secure Copy Protocol (SCP)
IP address Enter the IP address of the FTP server.
Username Enter the user name to log onto the FTP server.
Password Enter the password to log onto the FTP server.
Directory Enter the directory on the FTP server where the FortiAnalyzer unit
saves the report files.
Upload report(s) in
gzipped format
Select to compress the report files as gzip files before uploading
to the FTP server.
Delete file(s) after
uploading
Select to delete the report files from the FortiAnalyzer hard disk
once the FortiAnalyzer unit completes the upload to the FTP
server.
Refresh Select to refresh the list. If the FortiAnalyzer unit is in the process
of generating a report, use Refresh to update the status of the
report generation.
Delete Select the reports from the listing by selecting the check box next
to the report name.
Device Type Select the reports based on the type of device included in the
report.
FortiAnalyzer Version 3.0 MR3 Administration Guide
128 05-30003-0082-20060925
Browsing reports Reports
Viewing reports
To view a generated report
1 Go to Report > Browse.
2 In the Report files column, select a report group from the list and do one of the
following:
Select the report name to view a roll up report of all individual reports.
Select the blue triangle to expand the individual report list, and select to view
an individual report.
In the Other Formats column, select a file format for a report from the list.
Default reports
When registering a FortiGate unit that is running firmware version 3.0 or higher, a
default report profile will automatically be created. This version of the firmware
enables the FortiGate administrator to view all reports created by the
FortiAnalyzer unit for the FortiGate unit, as well as modify and update the default
report profile. The default profile uses the naming convention of
Default_<FortiGate Serial Number>.
You cannot delete the default report profiles.
You are also unable to modify the default report profile. Only the FortiGate
administrator can modify this type of report profile. The FortiGate administrator
has limited capabilities when a updating report profile. For example, they cannot
customize the header and footer information, or add logos to the reports.
Page Navigation Enter a page number to display reports when a report list spans
multiple pages. Select Go to move to the page.
Use the page forward and page back arrows to navigate through
individual pages.
Sample Reports Select to view an example of a report generated by the
FortiAnalyzer unit.
Report Files Displays the generated reports. Select the report name to view a
roll up of all reports in HTML format.
The report appears in the reports list with the report name, date
and time the report was generated.
For example, a report name of Report 1-2006-03-31-2112, is a
report called Report 1, generated on March 31, 2006 at 9:12pm.
Select the blue arrow to expand the report to view the individual
reports in HTML format.
Started Indicates the date and time when the FortiAnalyzer unit generated
the report.
Finished Indicates the date and time when the FortiAnalyzer unit completed
the report. If the FortiAnalyzer unit is in the process of generating
a report, a progress bar will appear in this column.
Size (bytes) The file size of the report in HTML format. The generated reports
are available in HTML, PDF, RTF and ASCII text formats,
depending on the output configuration. For details on setting
output options, see Configuring the report output on page 125.
Other Formats Select a file format to view the generated report.
Action Select Edit to rename the roll up report.
Select Delete to remove the report from the FortiAnalyzer hard
disk.
Reports Browsing reports
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 129
For details on report customization within the FortiGate unit, see the Log&Report
chapter in the FortiGate Administrators Guide.
Report types
There are two types of the report that you can browse and view:
Roll up report
Individual reports
Roll up report
The roll up report contains all reports that you selected for the FortiAnalyzer unit to
generate and presents it as a roll up report with all individual reports included.
To view a roll up report
1 Go to Report > Browse and select a report name.
2 Select a report category to expand the list of report sub-categories. Selecting a
report name in the left frame displays the report in the right frame.
Roll up reports are only available in HTML format.
Individual reports
Individual reports have the same look and functionality as the roll up reports when
viewing the HTML file format. When you view the report in one of the alternate
formats, only the right frame with the report information is included.
To view individual reports
1 Go to Report > Browse.
2 Select the blue arrow for a report name to view the individual reports.
3 Select the report you want to view in HTML format, or select a file format in the
Other Formats column.
Event activity codes
The report for the Event Activity includes a table column called Event Code.
These codes are the log message ID numbers from the FortiGate unit. The log
message ID is a ten digit number. The first two digits (01) represent the log type,
and is an event log in this case. The following two digits represent the subtype
(see Table 15 on page 129). The remaining five digits are the message ID. For
details see the FortiGate Log Message Reference.
Table 15: FortiGate 2.8 log subtypes
Subtype
number
Subtype
00 system System activity event
01 ipsec IPSec negotiation event
02 dhcp DHCP service event
03 ppp L2TP/PPTP/PPPoE service event
04 admin admin event
05 ha HA activity event
FortiAnalyzer Version 3.0 MR3 Administration Guide
130 05-30003-0082-20060925
Browsing reports Reports
Table 16: FortiGate 3.0 log subtypes
06 auth Firewall authentication event
07 pattern Pattern update event
30 chassis FortiGate-4000 and FortiGate-5000 series chassis event
Subtype number Subtype
00 system System activity event
01 ipsec IPSec negotiation event
02 dhcp DHCP service event
03 ppp L2TP/PPTP/PPPoE service event
04 admin admin event
05 ha HA activity event
06 auth Firewall authentication event
07 pattern Pattern update event
23 alert email Alert email notifications
29 chassis FortiGate-4000 and FortiGate-5000 series chassis
event
32 sslvpn user - ssl vpn user event
33 sslvpn admin - ssl vpn administrator event
34 sslvpn session - ssl vpn session event
Alerts Alert Events
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 131
Alerts
Alerts provide a method of informing you of issues arising on a FortiGate unit on
your network or the FortiAnalyzer unit itself, such as system failures or network
attacks, enabling you to react in a timely manner to the event.
You configure the FortiAnalyzer unit alert conditions, instructing the FortiAnalyzer
unit what devices and what log messages to monitor, and what to do in the event
a log message appears meeting the alert conditions.
Alert Events
Alert events are the definitions the FortiAnalyzer unit monitors for when receiving
log message packets from registered devices. Configure the alert events that the
FortiAnalyzer unit monitors for and what it should do when encountering the alert.
To view configured alert events, go to Alert > Alert Event.
Figure 63: Alert events list
Adding an alert event
To add a new alert event
1 Go to Alert > Alert Event.
2 Select Create New.
Create New Select to add a new alert event.
Delete Select to remove multiple alert events from the table. To do this,
select the check box next to the alert events and select Delete.
Name The name given to the alert event.
Devices The devices the FortiAnalyzer unit is monitoring for the alert event.
Triggers The log message packets the FortiAnalyzer unit is monitoring for
the alert event.
Destination The location where the FortiAnalyzer unit sends the alert
message. This can be an email address, SNMP Trap or syslog
server.
Action Select Delete to remove the alert event.
Select Edit to change the alert event configuration.
Delete
Edit
FortiAnalyzer Version 3.0 MR3 Administration Guide
132 05-30003-0082-20060925
Output Alerts
3 Configure the following options and select OK.
Output
When the FortiAnalyzer unit receives a log messages meeting the alert event
conditions, it sends an alert message as an email, syslog message or SNMP
Trap, informing an administrator of the issue and where it is occurring.
The FortiAnalyzer unit enables you to configure where it sends the alert message.
The FortiAnalyzer unit can send an alert message to an email address via SMTP,
a Syslog server or as an SNMP Trap.
Alert Name Enter a name indicating the type of alert the FortiAnalyzer is
monitoring for.
Device Selection Select the devices the FortiAnalyzer unit monitors for the alert
event. Select from the Available Devices list and select the
right-arrow to move the device name to the Selected Devices list.
Hold the SHIFT or CTRL keys to select multiple devices.
Trigger(s) Select the triggers that the FortiAnalyzer unit uses to indicate
when to send an alert message. Select the following:
a log type to monitor
the event level to monitor for within the log messages.
the relation to the level. For example, selecting >= Warning,
the FortiAnalyzer unit will send alerts when a log message has
a level of Warning, Error, Critical, Alert and Emergency.
Generic Text Select to add a standard text response for the alert notification.
Threshold Set the threshold or log message level frequency that the
FortiAnalyzer unit monitors for before sending an alert message.
For example, set the FortiAnalyzer unit to send an alert only after
it receives five emergency messages in an hour.
Destination(s) Select where the FortiAnalyzer unit sends the alert message.
Send alert to Select an email address, SNMP trap or Syslog server from the list.
You must configure the SNMP traps or Syslog server, before you
can select them from the list.
For the FortiAnalyzer unit to send an email message, you must
configure a DNS server and mail server account. For details see
Mail server on page 133.
For details on configuring SNMP traps, see SNMP access on
page 133.
For details on configuring Syslog servers, see Syslog Servers on
page 134.
From Email Address When configuring the FortiAnalyzer unit to send an email address,
enter an originator email address.
To Email Address When configuring the FortiAnalyzer unit to send an email alert
message, enter the recipients of the email message.
Add Select Add to add the destination for the alert message. Add as
many recipients as required.
Delete Select a recipient from the Destination list and select Delete to
remove a recipient.
Include Alert Severity Select the alert severity value to include in the outgoing alert
message information.
Alerts Output
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 133
Mail server
When configuring the FortiAnalyzer unit to send email alert messages, you need
to configure a DNS server and an SMTP server. The FortiAnalyzer unit uses the
SMTP server name to connect to the mail server, and must look up this name on
your DNS server. To configure a DNS server, see DNS on page 38.
Figure 64: Mail server list
To configure mail server
1 Go to Alert > Output > Mail Server.
2 Select Create New.
3 Set the following options and select Apply.
Testing the Mail server configuration
To verify that the mail server configuration is working correctly
1 Go to Alert > Output > Mail Server.
2 Select Test.
3 Enter an email address and select Test.
SNMP access
Configure the SNMP server where the FortiAnalyzer unit sends SNMP traps when
encountering an alert. You must add the SNMP server before you can select it as
a way for the FortiAnalyzer unit to communicate an alert. For a list of supported
MIBs and traps see FortiAnalyzer traps on page 136.
To view the SNMP servers, go to Alert > Output > SNMP Access List.
Note: When smtp send mail fails, the FortiAnalyzer unit will attempt to send a message
every ten seconds and never stop until it succeeds in sending the message or the
administrator reboots the unit.
Delete
Edit
Test
Enable
Authentication
Select the Authentication Enable check box to enable SMTP
authentication. When set, you must enter a email user name and
password for the FortiAnalyzer to send an email with the account.
SMTP Server The name/address of the SMTP email server.
Email Account Enter the user name for logging on to the SMTP server to send alert
mails. You only need to do this if you have enabled the SMTP
authentication. The account name must be in the form of an email
address. For example, fortianalyzer@company.com.
Password Enter the password for logging on to the SMTP server to send alert
email. You only need to do this if you selected SMTP authentication.
FortiAnalyzer Version 3.0 MR3 Administration Guide
134 05-30003-0082-20060925
Output Alerts
Figure 65: SNMP servers list
Use the Access List to identify where the SNMP server is located and the
administrator for the server.
Adding an SNMP server
To add a new SNMP server
1 Go to Alert > Output > SNMP Access List.
2 Select Create New.
3 Configure the following options, and select OK.
Syslog Servers
Configure the syslog servers where the FortiAnalyzer unit sends log
messages.You must add the syslog server before you can select it as a way for
the FortiAnalyzer unit to communicate an alert.
To view the SNMP servers, go to Alert > Output > Syslog Server.
Create New Select to add a new SNMP server.
Name The name given to the SNMP server.
Community Name The community name for the SNMP server.
IP or FQDN The IP address or fully qualified domain name for the SNMP
server.
Send system traps to Select an inputted trap from SNMP server from the list.
Action Select Delete to remove the SNMP server configuration.
Select Edit to change the SNMP server configuration.
Select Test to verify the SNMP server configuration.
Delete
Edit
Test
Name Enter a name for the SNMP server.
Community Name Enter a community name for the SNMP server.
IP address (or FQDN) Enter the IP address or fully qualified domain name for the SNMP
server.
Alerts Output
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 135
Figure 66: Syslog server list
Adding a Syslog server
To add a new Syslog server
1 Go to Alert > Output > Syslog Server.
2 Select Create New.
3 Configure the following options, and select OK.
FortiAnalyzer SNMP support
You can configure the FortiAnalyzer unit to report system information and send
traps (alarms or event messages) to SNMP managers. Using an SNMP manager,
you can access SNMP traps and data from the FortiAnalyzer unit.
The FortiAnalyzer SNMP implementation is read-only. SNMP v1 and v2c
compliant SNMP managers have read-only access to FortiAnalyzer system
information and can receive FortiAnalyzer traps. To monitor FortiAnalyzer system
information and receive FortiAnalyzer traps you must compile Fortinet proprietary
MIBs as well as Fortinet-supported standard MIBs into your SNMP manager.
RFC support includes support for most of RFC 2665 (Ethernet-like MIB) and most
of RFC 1213 (MIB II)
The FortiAnalyzer unit uses the FortiGate MIB for object identifiers. You can
obtain the MIB files from Fortinet technical support. To be able to communicate
with the SNMP agent, you must compile all of these MIBs into your SNMP
manager.
Create New Select to add a new Syslog server.
Name The name given to the Syslog server.
IP or FQDN: Port The IP address or fully qualified domain name for the SNMP
server, and port number.
Action Select Delete to remove the Syslog server configuration.
Select Edit to change the Syslog server configuration.
Select Test to verify the Syslog server configuration.
Delete
Edit
Test
Name Enter a name for the SNMP server.
IP address (or FQDN) Enter the IP address or fully qualified domain name for the SNMP
server.
Port Enter the Syslog server port number. The default Syslog port is
514.
FortiAnalyzer Version 3.0 MR3 Administration Guide
136 05-30003-0082-20060925
Output Alerts
Your SNMP manager might already include standard and private MIBs in a
compiled database that is ready to use. You must add the Fortinet proprietary MIB
to this database. If the standard MIBs used by the Fortinet SNMP agent are
already compiled into your SNMP manager you do not have to compile them
again.
FortiAnalyzer traps
The FortiAnalyzer unit can send traps to SNMP managers that you have added to
SNMP communities. To receive traps, you must load and compile the Fortinet 3.0
MIB into the SNMP manager.
The FortiAnalyzer unit supports the following MIBs and traps:
FortiGate MIB System Traps
fnTrapCpuHigh
fnTrapMemLow
fnTrapIpChange
FortiGate MIB Logging Traps
fnTrapLogFull
FortiGate MIB VPN Traps
fnTrapVpnTunUp
fnTrapVpnTunDown
fnTrapFlgEventCount
Fortinet MIB System fields
fnSysModel
fnSysSerial
fnSysVersion
fnSysCpuUsage
fnSysMemUsage
fnSysSesCount
fnSysDiskCapacity
fnSysDiskUsage
fnSysMemCapacity
Fortinet Administrator Accounts
fnAdminNumber
fnAdminIndex
fnAdminName
fnAdminAddr
Fortinet Options
fnOptIdleTimeout
fnOptLanguage
Alerts Output
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 137
Fortinet Active IP Sessions
fnIpSessIndex
fnIpSessProto
fnIpSessFromAddr
fnIpSessFromPort
fnIpSessToAddr
fnIpSessToPort
fnIpSessExp
RFC-1213 (MIB II)
mib-2.system
mib-2.interface
mib-2.at
mib-2.ip
mib-2.icmp
mib-2.tcp
mib-2.udp
mib-2.ifMIB
RFC-2665 (Ethernet-like MIB)
.dot3StatsTable
.dot3CollTable
.dot3ControlTable
.dot3PauseTable
FortiAnalyzer Version 3.0 MR3 Administration Guide
138 05-30003-0082-20060925
Output Alerts
Network Analyzer Connecting the FortiAnalyzer for analyzing network traffic
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 139
Network Analyzer
The FortiAnalyzer unit extends its log and report functionality with a network traffic
sniffer that captures activity occurring on your network, using a dedicated port on
the FortiAnalyzer unit.
The FortiAnalyzer network analyzer enables you to reach areas of the network
where FortiGate firewalls are not employed, or if you do not have a FortiGate unit
as a firewall. The FortiAnalyzer network analyzer functions as a sniffer to capture
traffic data, save it to the FortiAnalyzer hard disk and display it or generate reports
using the data.
This section describes how to enable and view network activity in real time as well
as view historical logs of network traffic activity. It also describes log storage
configuration options.
This section includes the following topics:
Connecting the FortiAnalyzer for analyzing network traffic
Traffic viewer
Browsing network traffic logs
Customizing the traffic analyzer log view
Search the network traffic logs
Log rolling
Connecting the FortiAnalyzer for analyzing network traffic
To use the FortiAnalyzer unit for traffic sniffing, connect the FortiAnalyzer unit to
the SPAN, or mirroring port of the Ethernet switch. Both the management and
sniffing ports can be connected to the same switch.
To connect the FortiAnalyzer unit
1 Connect an Ethernet cable to a port on the FortiAnalyzer unit other than the
existing Ethernet port used to connect to the network to collect device logs. For
example, port 2.
2 Connect the other end of the Ethernet cable to the SPAN or mirroring port of an
Ethernet switch.
3 In the web-based manager, go to Tools > Network Analyzer > Config.
4 Select Enable Network Analyzer on, and select a port from the list. Do not select
the port you are using for management and log message collecting activities.
5 Select Apply.
Note: The network analyzer feature is not available on the FortiAnalyzer-100. The network
analyzer feature requires a dedicated port to connect to the span or mirror port of a network
switch.
FortiAnalyzer Version 3.0 MR3 Administration Guide
140 05-30003-0082-20060925
Traffic viewer Network Analyzer
Traffic viewer
The traffic viewer provides a real-time and historical display of network activity
when connected to a network switch.
The Traffic Viewer has two types of viewing options:
Real-time view displays traffic packets as the traffic packets are sent through
the switch. The display refreshes every 10 seconds to display the most current
activity.
Historical view provides a way to view network traffic logs by focusing on
specific time frames.
Real-time traffic viewer
The real-time traffic viewer displays traffic information and updates continually, to
provide the most recent updates and events occurring on the network.
To view real-time network activity, go to Tools > Network Analyzer > Real-time.
Figure 67: Viewing real-time traffic
Stop Select to stop the traffic sniffing. When selected, Stop changes to
Start. Select Start to continue the real-time traffic viewing.
Column Settings Select to change the columns to view and the order they appear
on the page. For details see Customizing the log column views
on page 145.
Formatted | Raw Select a view of the network traffic log file. Selecting Formatted
(the default) displays the network traffic log files in columnar
format. Selecting Raw, displays the network traffic log information
as it actually appears in the log file.
Resolve Host Names Select to display host names by a recognizable name rather than
IP addresses. For details on configuring IP address host names
see IP Aliases on page 53.
Resolve Service
Names
Select to display network service names rather than port numbers.
For example, HTTP rather than port 80.
Log Time The date and time the packet was transmitted.
Source The IP address of the sender of the packet.
Destination The IP address of the recipient of the packet.
Destination Port The port a UDP or TCP packet was being sent to.
Protocol The protocol used when sending the packet.
Message Information on the packet sent through the switch.
Network Analyzer Traffic viewer
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 141
Historical traffic viewer
The Historical traffic viewer enables you to view network traffic logs stored on the
FortiAnalyzer hard disk. Use the network traffic history to identify trends and any
network issues. When viewing network traffic log messages, you can filter the
information to find specific event information.
To select a historical network traffic log to view, go to Tools > Network Analyzer
> Historical.
Figure 68: Viewing historical network traffic log
Type The type of log you are viewing.
Change Select to change the log time frame.
Formatted | Raw Select a view of the network traffic log file. Selecting Formatted
(the default) displays the network traffic log files in columnar
format. Selecting Raw, displays the network traffic log information
as it actually appears in the log file.
Resolve Host Names Select to display host names by a recognizable name rather than
IP addresses. For details on configuring IP address host names
see IP Aliases on page 53.
Resolve Service
Names
Select to display network service names rather than port numbers.
For example, HTTP rather than port 80.
View per page Select the number of rows of log entries to display per page.
Page n of n Enter a page number to jump to in the log information. Select Go
to jump to the page.
Column Settings Select to change the columns to view and the order they appear
on the page. For details see Customizing the log column views
on page 145.
Search Enter a keyword to perform a simple search on the log information
available. Select Go to begin the search. The number of matches
appears above the Search field.
Column Settings
FortiAnalyzer Version 3.0 MR3 Administration Guide
142 05-30003-0082-20060925
Browsing network traffic logs Network Analyzer
Changing the historical view criteria
When viewing the historical network traffic log, you can define the time range to
review. This enables you to easily focus on a time frame when questionable
activity may have occurred on your network.
To select a historical network traffic log criteria
1 Go to Tools > Network Analyzer > Historical.
2 Select Change.
3 Set the Start time by selecting the following:
4 Select the End time by selecting the following:
5 Select OK.
Browsing network traffic logs
The network traffic log browser enables you to see all stored network traffic log
files. In this window, you can view the network traffic logs, download log files to
your hard disk or delete unneeded files.
To browse the log files, go to Tools > Network Analyzer > Browse.
Printable Version Select to generate a report that captures the current log
messages. The web browser prompts you to save the report file
for viewing or printing. The report saved is in HTML format. Note
that large log messages can take a long time to load.
The printable version takes all filter settings into account when
generating a printable version.
Log Time The date and time the packet transmitted.
Source The IP address of the sender of the packet.
Destination The IP address of the recipient of the packet.
Destination Port The destination port for the packet.
Protocol The protocol used when sending the packet.
Message Information on the packet sent through the switch.
Unspecified Select to view network traffic log information from the earliest date
and time available in the logs.
Specified Select to set a specific start date and time for the log information.
Date Enter a start date. Use the format YYYY/MM/DD. Alternatively,
select the Calendar icon and select a start date.
Time Select a starting time for the log information. Leave the time at
00:00 to view log information starting at 12:00 midnight for the
selected date.
Current Select to include up to the minute network traffic log information.
Specified Select to set a specific end date and time for the log information.
Date Enter an end date. Use the format YYYY/MM/DD. Alternatively,
select the Calendar icon and select a start date.
Time Select a ending time for the log information. Leave the time at
00:00 to view log information ending at 12:00 midnight for the
selected date.
Network Analyzer Browsing network traffic logs
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 143
Figure 69: Browsing network log files
Browsing network traffic log files
The network traffic log viewer enables you to view network traffic information
occurring on your network that is otherwise not logged by a FortiGate unit. You
can also filter the content to see specific traffic information.
To view a log file
1 Go to Tools > Network Analyzer > Browse.
2 In the Action column, select Display for a content log file.
Figure 70: Viewing log data
Log files A list of log files on the FortiAnalyzer unit.
Last Modified The last time the log was updated from the device.
Size (bytes) The size of the log file.
Action Select Delete to remove the log file from the FortiAnalyzer hard disk.
Select Download to save the log file to your local hard disk.
Select Display to view the contents of the log file.
Delete
Download
Display
Type The type of log you are viewing.
Change Select to view a different log.
Formatted | Raw Select a view of the network traffic log file. Selecting Formatted
(the default) displays the network traffic log files in columnar
format. Selecting Raw, displays the network traffic log information
as it actually appears in the log file.
Column Settings
FortiAnalyzer Version 3.0 MR3 Administration Guide
144 05-30003-0082-20060925
Browsing network traffic logs Network Analyzer
Downloading a network traffic log file
Download a network traffic log file to save it as a backup or for use outside the
FortiAnalyzer unit.
To download a content log file
1 Go to Tools > Network Analyzer > Browse.
2 In the Log Files column, locate a log file.
3 In the Action column, select Download.
4 Select one of the following and select OK.
5 The web browser prompts you for a location to save the file.
Resolve Host Names Select to display host names by a recognizable name rather than
IP addresses. For details on configuring IP address host names,
see IP Aliases on page 53.
Resolve Service
Names
Select to display network service names rather than port numbers.
For example, HTTP rather than port 80.
Previous/Next icons Select to move to the next or previous displayed page in the log
information.
View per page Select the number of rows of log entries to display per page.
Page n of n Enter a page number to jump to in the log information. Select Go
to jump to the page.
Column Settings Select to change the columns to view and the order they appear
on the page. For details, see Customizing the log column views
on page 145.
Search Enter a keyword to perform a simple search on the log information
available. Select Go to begin the search. The number of matches
appears above the Search field.
Printable Version Select to generate a report that captures the current log
messages. The web browser prompts you to save the report file
for viewing or printing. The report saved is in HTML format. Note
that large log messages can take a long time to load.
The printable version takes all filter settings into account when
generating a printable version.
Log Time The date and time the packet was transmitted.
Source Port The port number where the packet originated.
Destination The IP address of the recipient of the packet.
Destination Port The destination port for the packet.
Protocol The protocol used when sending the packet.
Message Information on the packet sent through the switch.
Convert to CSV
format
Downloads the log format as a commas separated file with an
extension of .csv. Each data element is separated by a comma.
Compress with gzip Download the log file in its native format with gzip compression.
Network Analyzer Customizing the traffic analyzer log view
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 145
Customizing the traffic analyzer log view
The FortiAnalyzer unit enables you to customize the way you view the logs to
enable you to narrow down the information to exactly what you want to see.
Customizing the log column views
When viewing network traffic information in formatted view, customize the
columns to suit your requirements. You can add, remove and change the position
of each column.
To add or remove columns
1 When viewing an historical network traffic log file, select Column Settings.
A list of columns available for the log appears.
2 In the Available Fields area, select a column name and select the right arrow to
move the column name into the Display Fields area.
To change the positioning of the columns
1 When viewing a historical network traffic log file, select Column Settings.
A list of columns available for the log type appears.
2 Select a column name.
3 Select the up and down arrows to change the position of the column in the list.
Filtering network traffic logs
When looking at network traffic log files, you can filter the information to find
specific traffic information. Filters are available when you are viewing historical
data in the Log Viewer or browsing network traffic log files on the FortiAnalyzer
hard disk.
Figure 71: Filter icons for network analyzer logs
Each column of data includes a gray filter icon. Select the icon to filter the
contents of the column. Enter the information you are looking for in the field
provided and select OK.
When a filter is applied to a column, the filter icon appears green.
To turn off the filter, select the filter icon and select Reset Filter.
When viewing real-time logs, you cannot filter on the time column because the
time will always be the current time.
Filter icon
FortiAnalyzer Version 3.0 MR3 Administration Guide
146 05-30003-0082-20060925
Search the network traffic logs Network Analyzer
Filtering tip
When filtering by source or destination IP, you can use the following in the filtering
criteria:
a single address (2.2.2.2)
an address range using a wild card (1.2.2.*)
an address range (1.2.2.1-1.2.2.100)
You can also use the boolean operator "or" to indicate multiple choices:
1.1.1.1 or 2.2.2.2
1.1.1.1 or 2.2.2.*
1.1.1.1 or 2.2.2.1-2.2.2.10
Search the network traffic logs
The FortiAnalyzerunit provides search capabilities to help you locate specific
information within the stored network traffic log files. The FortiAnalyzer interface
provides two searches:
Basic search
Advanced search
Basic search
The basic search performs a simple search of the network traffic log files on the
FortiAnalyzer unit. The FortiAnalyzer unit maintains a search history for reference
should you need to use the search keywords again.
To perform a search, go to Tools > Network Analyzer > Search. Enter the
keywords for the search and select Search. Separate multiple keywords with a
space.
For example:
Search results appear below the search entry fields.
Advanced search
The advanced search provides a more robust search facility, with more options to
narrow your search criteria.
To perform an advanced search, go to Tools > Network Analyzer > Search, and
select Advanced search.
The search is case-insensitive. Use the * character as a wild card.
Figure 72: FortiAnalyzer advanced search
Search for IP address 10.10.10.1
Search for Information arp who-has 10.10.10.1
Network Analyzer Log rolling
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 147
Search tips
The FortiAnalyzer search feature includes a robust search index that enables you
to find any information by including specific information in your search criteria.
Consider the following when searching the logs:
The search is case-insensitive, that is, case is not considered.
Use the * character as a wild card. For any partial term or IP address, enter
as much as you can and use the * to search on all terms related to what you
entered.
You can search for IP ranges, including subnets. For example:
172.20.110.0-255 matches all IP addresses in the
172.20.110.0/255.255.255.0 or 172.20.110.0/24 subnet
172.20.110.0-140.255 matches all IP addresses from 172.20.110.0 to
172.20.140.255
172.16.0.0-20.255.255 matches all IP addresses from 172.16.0.0 to
172.20.255.255)
Printing the search results
The FortiAnalyzer unit enables you to produce a hard copy of the results of a
search, which you can email, save to a local hard disk or print.
After completing a search, the results include a Printable Version link. Select the
link to create an HTML version of the results.
Log rolling
Log rolling is a way to control the network traffic log file size and space used on
the FortiAnalyzer hard disk. You can configure the frequency of the log rolling and
what to do with the network traffic log file when rolled.
Search Select to begin searching the logs
Basic search Select to return to the basic search.
Find results with all
of the words
Enter the keywords you want to use in your search. The
FortiAnalyzer search engine will return all network traffic log
entries that contain all keywords entered. Separate keywords with
a space.
Find results with at
least one of the
words
Enter all the keywords you want to use in your search. The
FortiAnalyzer search engine will return all network traffic log
entries that contain one or more of the keywords. Separate
keywords with a space.
Find results without
the words
Enter the keywords that you do not want included in your search
results. If a network traffic log entry contains the keywords you are
searching on and includes a keyword from this field, the log entry
will not be included in the search results.
Return log entries
dated within
Select a time frame of the log entries to search within.
FortiAnalyzer Version 3.0 MR3 Administration Guide
148 05-30003-0082-20060925
Log rolling Network Analyzer
As the FortiAnalyzer unit receives network log records, it performs the following
tasks:
verifies whether the log file has exceeded its file size limit
if the file size is not exceeded, checks to see if it is time to roll the log file. You
configure the time to be either a daily or weekly occurrence, and when the roll
occurs.
When a network traffic log file reaches its maximum size, or reaches the
scheduled log rolling time, the FortiAnalyzer unit saves the network traffic log files
with an incremental number, and starts a new log file with the same name. For
example, the current network traffic log is xlog.log. Any subsequent saved network
traffic logs appear as xlog.n.log, where n is the number of rolled logs. For
example, xlog.4.log
To enable log rolling, go to Tools > Network Analyzer > Config.
Figure 73: Log rolling settings
Enable Network
Analyzer on
Select the port on the FortiAnalyzer unit to use for monitoring
network traffic.
Allocated Disk Space
(MB)
Enter the amount of disk space reserved for network traffic logs.
The dialog also displays the amount used of the allocated space.
When Allocated Disk
Space is All Used
Select what the FortiAnalyzer unit does when the allocated disk
space is filled up. Select to either overwrite the older log file or
stop logging until you can clear some room.
To avoid completely filling the hard disk space, use the log rolling
and uploading options.
Reuse settings from
standard logs
Select to use the same settings that you set for standard logs files
configured in Logs > Config.
Log rolling settings Use this area to define when the FortiAnalyzer unit should roll its
network traffic log files.
Network Analyzer Log rolling
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 149
Log file should not
exceed
The maximum size of a network traffic log file that the
FortiAnalyzer unit saves to the hard disk.
When the network traffic log file reaches the specified maximum
size, the FortiAnalyzer unit saves current network traffic log file
with an incremental number and starts a new active log file.
Log file should be
rolled
Set the time of day, when the FortiAnalyzer unit saves the current
network traffic log file and starts a new active log file. Select
Optional if you do not want to use this option.
Enable log uploading Select to upload network traffic log files to an FTP server
whenever a content log file rolls.
Server type Select the type of uploading server. Select from:
File Transfer Protocol (FTP)
Secure File Transfer Protocol (SFTP)
Secure Copy Protocol (SCP)
Server IP address Enter the IP address of the FTP server.
Username Enter the user name required to connect to the FTP server. The
user name has a default of anonymous. Click the field to enter a
different user name.
Password Enter the password required to connect to the FTP server.
Confirm Password Re-enter the password to ensure it is entered correctly.
Directory Enter a specific directory on the FTP server to save the log file.
Upload Log files Select when the FortiAnalyzer unit should upload files to the FTP
server.
Select When rolled to upload as soon as the FortiAnalyzer unit
rolls the network traffic log file, based on the settings above.
Select a specific time of the day when the FortiAnalyzer unit
rolls the network traffic log file. The FortiAnalyzer unit will
upload at the configured time no matter what the size of the log
file is or when it may be configured to roll to a new file.
Upload rolled files in
gzipped format
Select to compress the log files in gzipped format before
uploading to the FTP server.
Delete files after
uploading
Select to remove the log file from the FortiAnalyzer hard disk once
the FortiAnalyzer unit completes the upload.
FortiAnalyzer Version 3.0 MR3 Administration Guide
150 05-30003-0082-20060925
Log rolling Network Analyzer
Vulnerability scan Modules
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 151
Vulnerability scan
Vulnerability reports enable you to scan vulnerabilities on a device, such as a mail
server, FTP server or other UNIX or Windows host. The FortiAnalyzer unit uses
predefined vulnerability modules to query for open ports and where possible
gathers information about the services running for those ports.
This section describes how to set up vulnerability scans and view the reports
generated by the FortiAnalyzer unit.
This section includes the following topics:
Modules
Jobs
Reports
Modules
The Modules page provides a reference to the types of vulnerability scans the
FortiAnalyzer unit can perform on a host or device.
Use the module list to determine what type of vulnerability scanning you want the
FortiAnalyzer unit to perform, including level of severity.
To view supported vulnerability scan modules, go to Tools > Vulnerability Scan
> Module. Select a blue arrow to expand a module list.
Note: Vulnerability scan is not available on the FortiAnalyzer-100.
FortiAnalyzer Version 3.0 MR3 Administration Guide
152 05-30003-0082-20060925
Jobs Vulnerability scan
Figure 74: Vulnerability scan module list
Jobs
Create a vulnerability scan report job. Select the type of scan, devices to include
in the report, and when the FortiAnalyzer unit will run the report.
To view the list of staged jobs, go to Tools > Vulnerability Scan > Jobs.
Figure 75: List of staged vulnerability scan jobs
View modules with
severity
Select the severity level and a condition for the level of the
severity. Select from the following:
<= less than and equal to
>= greater than and equal to
== equal to
Go Select to view the severity selections.
Name The name of the severity grouping. Select the blue arrow to
expand the list of modules based on the severity option selection.
Severity The severity level of the module.
Description A brief explanation of the vulnerability.
Details Select for more information on the vulnerability.
Delete
Edit
Run Now
Vulnerability scan Jobs
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 153
Adding a new vulnerability scan job
To enable the FortiAnalyzer unit to run a vulnerability report, you need to
configure a report job, indicating the device to scan and what the scan will
encompass.
To add a new vulnerability scan job
1 Go to Tools > Vulnerability Scan > Jobs.
2 Select Create new.
3 Complete the following:
4 Select the blue arrow for Scan options to expand the list.
5 Complete the following:
6 Select the blue arrow for Schedule Option.
Create New Select to add a job to the queue.
Job Name The name of the job you configure.
Target The IP addresses of the device or host that the FortiAnalyzer unit
will scan.
Status The current status of the job in the queue. This can include the
current activity, such as running or waiting to start or it can be the
date the job is set to run in the future.
Action Select Delete to remove the job from the list.
Select Edit to modify the job. You cannot modify a job if it is
currently running.
Select Run Now to initiate a report.
Job Name Enter a name for the vulnerability report.
Scan Targets Enter the IP addresses, or range of addresses, of the device or
hosts you want the FortiAnalyzer to scan and select Add. You can
add as many devices or hosts as required. To remove a device,
select Remove.
Remote
Authentication
Select when the FortiAnalyzer unit needs to log into a remote
system to perform the vulnerability scan.
User Name Enter the user name for a remote scan. This option is only
available when selecting Remote Authentication.
Password Enter the password for the above user name. This option is only
available when selecting Remote Authentication.
Quick Scan Select to run a scan in quick mode. The FortiAnalyzer scans a list
of known ports but will not scan every port ID for every host. It will
only check a list of known ports.
Custom Scan Select to enable the FortiAnalyzer unit to scan specific ports
based on specific severity levels.
Modules Severity Select the condition level and the severity level.
For details on what the FortiAnalyzer scans at any given level, see
Modules on page 151.
TCP Ports Range Enter the port numbers, or port ranges, the FortiAnalyzer scans.
Separate each port number or range of numbers with a comma.
Enable UDP scan Select to run a port scan on UDP ports.
UDP Ports Range Enter the port numbers, or port ranges, the FortiAnalyzer scans.
Separate each port number or range of numbers with a comma.
FortiAnalyzer Version 3.0 MR3 Administration Guide
154 05-30003-0082-20060925
Jobs Vulnerability scan
7 Select when you want the FortiAnalyzer unit to run the vulnerability scan.
Run now starts the scan immediately after you select OK.
Run later enables you to select a date or time when the FortiAnalyzer unit runs the
scan. For example, this can be at night when more cycles are available due to
less logging activity.
8 Select the blue arrow to expand the Output options.
9 Complete the following
File output Select the file format for the generated reports that are saved to
the FortiAnalyzer hard disk. To access the reports on the hard
disk, see Reports on page 155.
Select from the following:
HTML
Adobe PDF
MS Word format (RTF)
Email output Select the file formats for the generated reports that the
FortiAnalyzer unit sends as an email attachment.
Select from the following:
HTML
Adobe PDF
MS Word format (RTF)
Email subject Enter a subject to the email FortiAnalyzer sends. When not
selected, the subject line is the name of the report.
To select the Customize subject check box, you must select a file
format from the Email output list.
Email Attachment
name
Enter the name for the report files included in the email. When you
select multiple reports for the report profile, the FortiAnalyzer unit
compresses all reports into a zip file. This option enables you to
select the name for the zip file.
Email Body Enter the text to include in the body of the email message.
Email from Enter an email address for the FortiAnalyzer unit or administrator
requesting the report.
Email server Select the email server to use when the FortiAnalyzer unit sends
the reports as an email attachment.
Email to Enter the email addresses of the recipients of the report. Add
multiple recipients by pressing Enter after each email address.
The addresses appear in the Email list box.
Vulnerability scan Reports
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 155
Reports
Use the FortiAnalyzer web-based manager to view a list of the generated
vulnerability scan reports. To view generated reports, go to Tools > Vulnerability
Scan > Reports.
Figure 76: Browse generated Vulnerability Scan reports
Job Name The name of the vulnerability scan job entered when setting up
the job.
Start Time The time the scan started.
End Time The time when the scan completed.
Action Select Delete to remove the report.
Formats Select the format of the report to view. Select between PDF and
MS Word (RTF) formats.
FortiAnalyzer Version 3.0 MR3 Administration Guide
156 05-30003-0082-20060925
Reports Vulnerability scan
Index
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 157
Index
A
access
management 39
accounts
administrator 39
users 46
acknowledge alerts 31
admin
idle timeout 42
administrative access 37, 39
alert 131
display on dashboard 29
events 131
mail server 133
sending 132
SNMP traps 133
syslog server 134
threshold 132
triggers 131, 132
alert messages 31
acknowledge 31
alias range 54
allocate disk space 69, 71
attack name 115
auto locate 37
B
backup 26
blocked devices 74
browse
forensic analysis reports 106
logs 80
network traffic 142
reports 112, 127
C
changing firmware 35
CLI 23
column view
content logs 90
logs 83
network traffic 145
command line interface 23, 24
company name 102, 121
config policy 50
configure the FortiGate unit 68
connecting
for analyzing network traffic 139
the FortiAnalyzer unit 20
to the web-based manager 23
connection sessions 29
content archive 89
content logs
delete after upload 93
filter 91
gzip format 93
roll settings 91
correlation report 113
CPU status 28
D
DC (duplicate count) 96
defaults 21
define device port interfaces 70
delete after upload
content log 93
forensic analysis 106
logs 87
network traffic log 149
report 127
delete old logs 50
device
alerts 131
groups 74
device ID
FortiGate unit 69
FortiManager 72
devices
add 68
blocked 74
license 29, 66
maximum allowed 66
unregistered 67
disk controller 61
disk formatting 33
disk space
FortiGate unit 69, 71
FortiManager 72
quarantine 95
syslog server 73
DNS 38, 133
download
logs 82
network traffic logs 144
E
email
alert 132
view traffic 108
email subject 105, 126, 154
enable quick scan 153
environmental specifications 20
FortiAnalyzer Version 3.0 MR3 Administration Guide
158 05-30003-0082-20060925
Index
event
activity 129
log numbers 129
summaries 113
F
factory default 21, 30
FDN
FortiProtect Distribution Network 58
FDS
FortiProtect Distribution Server 58
file
properties 49
filter
content logs 91
for reports 122
logs 84
network traffic 145
user traffic 110
firmware
update 35
upgrade 25
version 28
footer comment 102, 121
forensic analysis
browse 106
delete after upload 106
footer 102
gzip 106
header 102
logo 102
output 104
report types 104
resolve host names 103
resolve service names 103
time 104
upload to FTP 106
format disk 33
format hard disk 30
FortiAnalyzer
family 11
hot swap 61
restore 33
shut down 26
specs 20
FortiAnalyzer MIB 135
FortiAnalyzer traps 136
FortiDiscovery 37
FortiGate unit
groups 69
ID 69
port interfaces 70
pre-shared key 69
FortiManager 72
device ID 72
disk space 72
groups 73
secure connection 72
FortiProtect Distribution Network 58
FortiProtect Distribution Server 58
FortiScan 29
FTP usage 109
fully qualified domain name 134, 135
G
gateway 38
groups 74
FortiGate unit 69
FortiManager 73
syslog server 74
user groups 46
H
hard disk usage 28
header comment 102, 121
HELO packet 37
historical viewer
logs 78
network traffic 141
host name 28
hot swap 61
HTTP 37
HTTP usage 107
HTTPS 37
I
idle timeout 42
IM use 109
import
IP alias file 53
log files 82
individual report 129
installation
planning 19
instant message usage 109
interface
administrator access 37
configuration 36
status 36
intrusion activity report 115
IP alias 53
importing from file 53
ipsec tunnel 66
L
language option 42
LCD panel 25
license information 29
log
level 51
logo formats 102, 122
logos 102, 121
logs
auto delete 50
backup 26
browse 80
column view 83
delete after upload 87
download 82
filter 84
gzip format 87
Index
FortiAnalyzer Version 3.0 MR3 Administration Guide
05-30003-0082-20060925 159
historical viewer 78
import 82
real-time viewer 77
resolve host names 78, 79, 81
restore 26
roll settings 86
search 84
settings 50
M
mail server 133
maximum
allowed devices 66
transmission units 37
memory status 28
MIB 135
models, FortiAnalyzer 20
modules 151
MTU 37
N
network
attached server 45
file system 45
performance 37
time protocol 32
network traffic
browse 142
column view 145
delete after download 149
download logs 144
filter 145
gzip 149
historical viewer 141
log roll settings 147
real-time viewer 140
resolve host names 140, 141, 144
resolve service names 140, 141, 144
search logs 146
NTP 32
null modem 24
O
output for forensic analysis 104
output for report 125
overwrite older files 69, 71
P
password 39
PDF document 104, 125
PING 37
port
514 66
interfaces 70
power down 29
power off 26
pre-shared key
FortiGate unit 69
profile, reports 101, 112, 119
properties 49
protocol, syslog 66
Q
quarantine
disk space 95
duplicate count 96
ticket number 96
R
RAID
status 28
ranges 54
read & write access level
administrator account 57
real-time viewer
logs 77
network traffic 140
reboot 29
report 129
browse 112, 127
customize 102, 121
delete after upload 127
footer 121
gzip 127
header 121
individual 129
logo 121
output 125
results 124
roll up 129
schedule 125
time period 122
types 104, 124
upload to FTP 127
reports
filter for 122
profile 101, 112, 119
resolve host names 124
resolve service names 124
vulnerability 155
reset factory defaults 30
resolve host names 53
forensic analysis 103
logs 78, 79, 81
network traffic 140, 141, 144
reports 124
resolve service names
forensic analysis 103
network traffic 140, 141, 144
reports 124
restart 29
restore 26
defaults 32
the FortiAnalyzer unit 33
RFC 1213 135
RFC 2665 135
roll settings
content logs 91
logs 86
network traffic logs 147
FortiAnalyzer Version 3.0 MR3 Administration Guide
160 05-30003-0082-20060925
Index
roll up report 129
routing 38
RTF document 104, 125
S
scan
report 152
target 153
schedule a report 125
search
logs 84
network traffic logs 146
secure connection 66, 69
FortiManager 72
security
event report 113
summaries 113
security reports 113
selecting devices 122
serial number 28
session information 116
settings
log 50
shut down 26, 29
SMTP 133
sniffer 139
SNMP
traps 136
SNMP manager 135
SNMP server, test 134
SNMP traps 133
SNMP, MIB 135
SNMP, traps 136
SPAN port 139
specifications
environmental 20
FortiAnalyzer 20
SSH 37
stop logging 69, 71
subject 105, 126, 154
suspicious
activity report 116
events 29
sync interval 32
syslog protocol 66
syslog server 73, 134
disk space 73
groups 74
system settings 50
restore default 30, 32
system time 28
T
TELNET 37
test
mail server 133
SNMP server 134
TFTP server 33
threshold 114, 132
ticket number 96
time
NTP server 32
period for report 122
settings 32
sync interval 32
traffic
flow on a FortiGate unit 70
information 116
summaries 107
transmission options 66
traps
SNMP 136
trusted host 39, 40
TXT document 104, 125
U
unregistered device 65, 67
upgrade firmware 25
uptime 28
user
accounts 46
groups 46
user traffic
filter 110
V
virtual domains (VDOM) 123
virus activity report 114
vulnerability
enable quick scan 153
jobs 152
modules 151
reports 155
scan target 153
W
warning 29, 131
web traffic 107
web-based manager 23
connecting 23
windows shares 45
www.fortinet.com
www.fortinet.com
You might also like
- HSGQ EPON OLT Command User Manual (122018)Document41 pagesHSGQ EPON OLT Command User Manual (122018)Kheme Vitoumeta50% (6)
- Networking and TCL Interview QuestionsDocument133 pagesNetworking and TCL Interview Questionsnawrajlekhak100% (4)
- Basic Networking TutorialDocument120 pagesBasic Networking TutorialKshitija Sahani100% (1)
- Fortigate Ipsec VPN 50 PDFDocument228 pagesFortigate Ipsec VPN 50 PDFpesbarcavnNo ratings yet
- g12 Css 1st QTR SLM - EdfDocument64 pagesg12 Css 1st QTR SLM - EdfYaj AnilomNo ratings yet
- Training On Pasolink Network Management System (Java Version)Document64 pagesTraining On Pasolink Network Management System (Java Version)Iftikhar Ahmad AhmadNo ratings yet
- Fortigate Firewall 50 PDFDocument191 pagesFortigate Firewall 50 PDFDroservicio LtdaNo ratings yet
- Fortigate Troubleshooting 56Document64 pagesFortigate Troubleshooting 56Sridhar bvnlNo ratings yet
- FortiSwitch and Security Fabric v2 - Public PDFDocument37 pagesFortiSwitch and Security Fabric v2 - Public PDFDJ JAMNo ratings yet
- Installing The FortiGate UnitDocument17 pagesInstalling The FortiGate Unitmanoj22490No ratings yet
- NSE3 FortiAuthenticator Combined LiteUpdate 20210311Document29 pagesNSE3 FortiAuthenticator Combined LiteUpdate 20210311Bhanuka SenarathnaNo ratings yet
- CCSA R81.10 Student & Lab ManualDocument693 pagesCCSA R81.10 Student & Lab Manualpoyib84365No ratings yet
- PAN-EDU-101 - Lab Manual PAN-OS 6.0 - Rev A PDFDocument48 pagesPAN-EDU-101 - Lab Manual PAN-OS 6.0 - Rev A PDFRuben De Sis Temas0% (2)
- Fortinet NS4 V6.0 2019 Dumps1 PDFDocument24 pagesFortinet NS4 V6.0 2019 Dumps1 PDFCesarNo ratings yet
- E2 Lab 3 5 2 inDocument4 pagesE2 Lab 3 5 2 inAhmad ShNo ratings yet
- Firepower On ASA POV Best Practices Quick Start Guide 6.1Document27 pagesFirepower On ASA POV Best Practices Quick Start Guide 6.1Majnu Sm100% (1)
- AWS Academy Cloud Architecting Module 06 Student Guide: 200-ACACAD-20-EN-SGDocument59 pagesAWS Academy Cloud Architecting Module 06 Student Guide: 200-ACACAD-20-EN-SGM Rizki AsriyandaNo ratings yet
- FortiGate I Student Guide-Online 5-2-1Document478 pagesFortiGate I Student Guide-Online 5-2-1Erick TapiaNo ratings yet
- 3.7.10 Lab - Use Wireshark To View Network TrafficDocument7 pages3.7.10 Lab - Use Wireshark To View Network TrafficPham Quang Huy (K16HL)No ratings yet
- FortiAnalyzer Study Guide OnlineDocument225 pagesFortiAnalyzer Study Guide OnlineFelipe Gabriel Nieto ConchaNo ratings yet
- HPE Compute Solutions, Rev. 21.41 Lab GuideDocument138 pagesHPE Compute Solutions, Rev. 21.41 Lab GuideLucio PastanaNo ratings yet
- Forticlient Admin 52 WindowsDocument183 pagesForticlient Admin 52 WindowswmtNo ratings yet
- Fortigate Infrastructure Lab Guide: Do Not Reprint © FortinetDocument143 pagesFortigate Infrastructure Lab Guide: Do Not Reprint © Fortinetshashi505286No ratings yet
- Fortianalyzer Lab Guide: Do Not Reprint © FortinetDocument90 pagesFortianalyzer Lab Guide: Do Not Reprint © FortinetDarko SpunkyNo ratings yet
- Troubleshooting Tricks and HintsDocument10 pagesTroubleshooting Tricks and HintsAnkur SaxenaNo ratings yet
- Fortigate Advanced Routing 50Document161 pagesFortigate Advanced Routing 50nexrothNo ratings yet
- Fortigate CliDocument854 pagesFortigate Clidoru.aero4738No ratings yet
- Cisco APIC 40 With VMware Admin v1 PDFDocument40 pagesCisco APIC 40 With VMware Admin v1 PDFMahmoud RamadanNo ratings yet
- Troubleshooting PDFDocument96 pagesTroubleshooting PDFJeanNo ratings yet
- Fortigate VDOMDocument120 pagesFortigate VDOMMauricio TorresNo ratings yet
- Basic Fortigate Firewall Configuration: Content at A GlanceDocument17 pagesBasic Fortigate Firewall Configuration: Content at A GlanceDenisa PriftiNo ratings yet
- Palo Alto Networks Edu-210: Document VersionDocument31 pagesPalo Alto Networks Edu-210: Document VersionclaraNo ratings yet
- CNS-223-1I Implement Citrix ADC 13.x: Basic Networking Lab ManualDocument14 pagesCNS-223-1I Implement Citrix ADC 13.x: Basic Networking Lab ManualМаријан СтанићNo ratings yet
- Comandos Esenciales - FORTINETDocument2 pagesComandos Esenciales - FORTINETLuis Gerardo MendozaNo ratings yet
- FortiAnalyzer Best Practices GuideDocument18 pagesFortiAnalyzer Best Practices GuideElbarni MohamedNo ratings yet
- Nse4 Infraestructura 101-150Document50 pagesNse4 Infraestructura 101-150leydis GarciaNo ratings yet
- Do Not Reprint © Fortinet: Fortigate Infrastructure Lab GuideDocument140 pagesDo Not Reprint © Fortinet: Fortigate Infrastructure Lab GuideJoel MazuiNo ratings yet
- FortiNAC - VM RunningDocument22 pagesFortiNAC - VM RunningTestew asaNo ratings yet
- Art-Net II Ethernet Communication StandardDocument40 pagesArt-Net II Ethernet Communication StandardAitor Aloa del TesoNo ratings yet
- FortiOS 6.4.0 Hardening Your FortiGateDocument28 pagesFortiOS 6.4.0 Hardening Your FortiGaterockitNo ratings yet
- BIG-IP Advanced Routing Troubleshooting GuideDocument96 pagesBIG-IP Advanced Routing Troubleshooting Guideปลาชุม ชุมพลNo ratings yet
- Shriram's Fortigate Best PracticesDocument42 pagesShriram's Fortigate Best PracticesShriram Iyer100% (1)
- FortiGate III Student Guide-Online V8Document521 pagesFortiGate III Student Guide-Online V8neoalt100% (1)
- Fortinet ComandosDocument9 pagesFortinet ComandosJuan Jose Ortiz VegaNo ratings yet
- FortiNAC FortiGate VPN IntegrationDocument58 pagesFortiNAC FortiGate VPN IntegrationFrancisco JuniorNo ratings yet
- FortiAnalyzer 5.4.5 CLI ReferenceDocument224 pagesFortiAnalyzer 5.4.5 CLI ReferenceFelipe Gabriel Nieto Concha0% (1)
- FGT1 02 Logging and MonitoringDocument19 pagesFGT1 02 Logging and MonitoringMax Olguin MellaNo ratings yet
- FreePBX Training Neocenter Jun19 23 Pag - 37 170Document134 pagesFreePBX Training Neocenter Jun19 23 Pag - 37 170jose sanchezNo ratings yet
- 201-Fcnsa 5.0.3Document224 pages201-Fcnsa 5.0.3manzo_zeti100% (1)
- BCC Proxy AdminDocument356 pagesBCC Proxy AdminRajesh ChamanthulaNo ratings yet
- Fortianalyzer: Device Registration and CommunicationDocument41 pagesFortianalyzer: Device Registration and CommunicationcrgonzalezfloresNo ratings yet
- Understanding NAT 4.1 RevCDocument30 pagesUnderstanding NAT 4.1 RevCRyanb378No ratings yet
- Fortinac Vmware Install 85Document66 pagesFortinac Vmware Install 85Pradeep KumarNo ratings yet
- Fortigate Infrastructure: Software-Defined WanDocument37 pagesFortigate Infrastructure: Software-Defined Wanrego680No ratings yet
- Redundancy:: o Redundancy, Failover, High Availability, Clustering, RAID and Fault-ToleranceDocument19 pagesRedundancy:: o Redundancy, Failover, High Availability, Clustering, RAID and Fault-ToleranceHai DoNo ratings yet
- XI Manual Installation InstructionsDocument2 pagesXI Manual Installation Instructionswilliam_pNo ratings yet
- Cisco IWAN Lab GuideDocument152 pagesCisco IWAN Lab GuidejoseivanvilelaNo ratings yet
- Palo Alto Networks - Edu-210: Document VersionDocument27 pagesPalo Alto Networks - Edu-210: Document Versionclara0% (1)
- WSA 7.0.0 UserGuideDocument784 pagesWSA 7.0.0 UserGuideLuis JimenezNo ratings yet
- F5 - Getting Started Lab IntroductionDocument15 pagesF5 - Getting Started Lab Introductionyaniss780% (1)
- FortiAnalyzer 05 ReportsDocument59 pagesFortiAnalyzer 05 ReportscrgonzalezfloresNo ratings yet
- Nexus 7000 VPC Role ChangeDocument2 pagesNexus 7000 VPC Role Changea_giri1No ratings yet
- Pan-Os Cli Quick StartDocument44 pagesPan-Os Cli Quick StartdeltacraiovaNo ratings yet
- Secure Access 6.0 Study Guide-Online PDFDocument428 pagesSecure Access 6.0 Study Guide-Online PDFRenato Tarifa DiasNo ratings yet
- Cisco Certified Security Professional A Complete Guide - 2020 EditionFrom EverandCisco Certified Security Professional A Complete Guide - 2020 EditionNo ratings yet
- Pexip Infinity Oracle Deployment Guide V33.aDocument29 pagesPexip Infinity Oracle Deployment Guide V33.albenharzproNo ratings yet
- DatatatadfDocument30 pagesDatatatadfKardinar RudiyantoNo ratings yet
- Ccnav7 Srwe Skills Assessment: TopologyDocument9 pagesCcnav7 Srwe Skills Assessment: TopologyPaul Andres Heredia FerrufinoNo ratings yet
- Chapter Test Css g12Document30 pagesChapter Test Css g12flash driveNo ratings yet
- CX4 Installing Storage-System Hardware - Master 1424705Document58 pagesCX4 Installing Storage-System Hardware - Master 1424705ravimars22No ratings yet
- CCNA 2 Pretest Exam Answers v5Document81 pagesCCNA 2 Pretest Exam Answers v5Pate Ssmma Ikanivoka100% (2)
- Deployment Options PDFDocument25 pagesDeployment Options PDFNebi AriantoNo ratings yet
- Questions Bank1Document11 pagesQuestions Bank1Arian SSNo ratings yet
- Hive Manager Virtual Appliance Quick Start 330029 03 RevADocument7 pagesHive Manager Virtual Appliance Quick Start 330029 03 RevAKen KøbmandNo ratings yet
- CN FINAL Practical - FileDocument45 pagesCN FINAL Practical - FileDHILLON DIGITAL CENTERNo ratings yet
- Installation Guide For Omnivista 2500 Nms Enterprise Version 4.2.1.R01Document51 pagesInstallation Guide For Omnivista 2500 Nms Enterprise Version 4.2.1.R01AadityaIcheNo ratings yet
- IP Address Basics: IP Filtering in CanvasDocument3 pagesIP Address Basics: IP Filtering in CanvasArtur ZbykovskyiNo ratings yet
- Subnetting LabDocument5 pagesSubnetting LabBruno BandinaNo ratings yet
- Enet rm002 - en PDocument106 pagesEnet rm002 - en PbrenbraNo ratings yet
- Answers Unit 2 LabDocument3 pagesAnswers Unit 2 LabBrianna OberfoellNo ratings yet
- Lab Guide - CCNSPDocument6 pagesLab Guide - CCNSPRexford AdjeiNo ratings yet
- 04 Network Layer Protocols and IP AddressingDocument45 pages04 Network Layer Protocols and IP Addressingيوسف الدرسيNo ratings yet
- bài tập ngày 20 09 chia địa chỉ mạngDocument13 pagesbài tập ngày 20 09 chia địa chỉ mạngTrùng Dương NTNo ratings yet
- Manual For NIRS XDS RapidContent Analyzer PDFDocument90 pagesManual For NIRS XDS RapidContent Analyzer PDFAv Raham B. AriasNo ratings yet
- VNet User GuideDocument20 pagesVNet User GuideCsaba LangerNo ratings yet
- EBS Deployment On OCI PDFDocument13 pagesEBS Deployment On OCI PDFsudhirpatil15No ratings yet