100% found this document useful (3 votes)
3K views13 pagesICT IGCSE Theory - Revision Presentation: 10. Communication
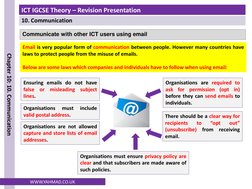
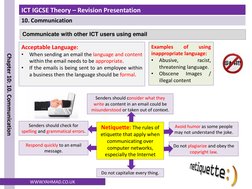
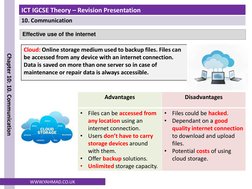
The document discusses communication using email and the internet. It covers laws around email use, appropriate email content and language, copyright, and preventing spam email. It also discusses using groups in email and the effective use of the internet including browsing, social networking, online shopping and banking, and file transfers.
Uploaded by
Jane ChangCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
100% found this document useful (3 votes)
3K views13 pagesICT IGCSE Theory - Revision Presentation: 10. Communication
The document discusses communication using email and the internet. It covers laws around email use, appropriate email content and language, copyright, and preventing spam email. It also discusses using groups in email and the effective use of the internet including browsing, social networking, online shopping and banking, and file transfers.
Uploaded by
Jane ChangCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd