Professional Documents
Culture Documents
An Integrated Approach For Malicious Tweets Detection Using NLP
Uploaded by
Tech NestOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
An Integrated Approach For Malicious Tweets Detection Using NLP
Uploaded by
Tech NestCopyright:
Available Formats
International Conference on Inventive Communication and Computational Technologies
(ICICCT 2017)
An Integrated approach for Malicious Tweets
detection using NLP
Sagar Gharge Mr. Manik Chavan
Dept. of Computer Science and Engineering, Dept. of Computer Science and Engineering,
Walchand College of Engineering, Walchand College of Engineering,
Sangli, India, Sangli, India,
email: sagar.gharge@walchandsangli.ac.in email: manik.chavan@walchandsangli.ac.in
Abstract— Many previous works have focused on detection information and can use that information against you with a
of malicious user accounts. Detecting spams or spammers on malicious intension. There are many people who share their
twitter has become a recent area of research in social network. personal information on social networking sites daily and such
However, we present a method based on two new aspects: the people fall prey to some or the other malicious activities and
identification of spam-tweets without knowing previous
their personal information is misused
background of the user; and the other based on analysis of
language for detecting spam on twitter in such topics that are in Now-s-days, social networking sites are a medium of
trending at that time. Trending topics are the topics of discussion analytics on a large amount of user data for many companies
that are popular at that time. This growing micro blogging based on which many prediction models are being built, and
phenomenon therefore benefits spammers. Our work tries to recommended systems are been prepared for end users. But
detect spam tweets in based on language tools. We first collected this is only the single side of a coin. On the other side there are
the tweets related to many trending topics, labelling them on the many such people who are waiting for just a single chance of a
basis of their content which is either malicious or safe. After a single wrong step by the user. Social networking sites have
labelling process we extracted a many features based on the become a platform for the promotion of businesses, classes
language models using language as a tool. We also evaluate the
and may more activities, but some people are using it in a very
performance and classify tweets as spam or not spam. Thus our
system can be applied for detecting spam on Twitter, focusing wrong way. They provide the users with links in a promotional
mainly on analysing of tweets instead of the user accounts. form and redirect them to many misleading and misguiding
sites where, the content is either malicious or in such a way
Keywords— Spam detection, Social network, Statistical that it will change their thoughts negatively. The main
natural language processing, Machine Learning. problem which comes as “spam” is here, “spam” is a form of
content which is irrelevant or unsolicited message which is
I. INTRODUCTION sent with a purpose of advertising, phishing, spreading
malware etc. There arises a big threat of malware. Many
Social networking sites now-a-days have become the most people fall prey to spams and are redirected to sites from
popular medium for people to spend their time and make more where a malware is been downloaded to their personal
friends. Online Social networks (OSNs), such as Twitter, machines, which is continuously sending their valuable
Facebook, and many enterprise social networks, have become information to an unknown server.
very much popular in the last few years. People are spending a Twitter is a place where more such spammers are active
huge amount of time on OSNs making friends, with people and they are circulating spams continuously. Hence, there is a
whom they know or with people they are interested in. Twitter, need to detect such spams, which contain URLs and are
which came into existence in 2006, became one of the most redirecting people to different locations. The work in this
popular site. Now-a-days, over 300 million Twitter users create paper deals with detecting such spam tweets and many new
around 600 million new micro blogs which are called as features based on language models that help to improve spam
“tweets” per day. Twitter now has become the most popular detection. The underlying idea of the paper is as follows: we
online micro blogging service, that encourages its users to send analyse the use of languages in the tweets and the page of
and read image based and text based posts of up to 140 where the URL is linked to it. In the scenario of spam the
characters. Now-a-days, billions of users use Twitter to be in language models differ from each other. Hence, the role of the
contact with their friends and followings. On social networking person posting the spam i.e. “spammer”, is to divert people to
sites, people share and spread a lot of knowledge and another content which is totally irrelevant. We analyse the
information which proves beneficial to others and help them in divergence ratio between the language models in order to
many ways. But you never know who is keeping track of your classify the models as spam or not spam.
978-1-5090-5297-4/17/$31.00 ©2017 IEEE 435
International Conference on Inventive Communication and Computational Technologies
(ICICCT 2017)
The remaining of the paper proceeds as follows: Section 2 III. ARCHITECTURE
presents the previous works in the spam detection research
area; Section 3 shows the architecture of the system; Section 4
is devoted to the proposed methodology; Section 5 describes
the observation and analysis; Finally, Section 6 draws the
conclusions.
II. RELATED WORK
The work in [1] focuses on the streaming data on
twitter which is classified as spam or not. Twitter APIs which
are available are used to collect data from twitter and then
analyses it based on the machine learning methods. The work
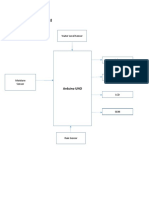
in [2] focuses on the use of enterprise social networks. The use Fig 1. Architecture of the proposed system.
of enterprise social media by the employee is analyse
according to the fact that, what is beneficial to employee and This section consists of the architecture of our
what is not. The paper focuses on the factors influencing the proposed system to detect spam tweets. Fig. 1 shows the
decision of employee to use the social networks for their work proposed model.
purpose. Work in [3] shows the detailing of analysing the The system comprises of the following five
information related to the sentiments of people which is processes:
captured during the twitter data gathering. The twitter data has A. Tweets Collection
become the area of wide research through which the people First the system retrieves a set of tweets based on the
can analyse the sentiments of the user. It proposed many given topic which is the trending one on twitter. The tweets
algorithms that classify the sentiments from the tweets into a are captured and stored in a specific file format and then they
data stream and to decide whether the tweet specifically is are all set to be analysed. Trending topics can also be retrieved
subjective or objective, that is positive or negative sentiments from twitter separately and based on that other tweets are
are classified. collected to analyse.
For a given set of documents it becomes very
difficult to find similar kinds of sentences and key concepts B. Spam labelling
within the sentences. The work in [5] focuses on such analysis The second process is the labelling process where the
of documents, which crawls through the document and then system checks through all the available datasets to detect
analyses and identifies the type of sentences within it and then malicious URLs. The label sets obtained will be used to detect
the way in which sentences show their uniqueness. The spams by training the system accordingly.
problem of spam on web is growing day by day. The paper [6]
focuses on scenarios of such spam detection based on various C. Feature extraction
classifiers, which analyse the URLs in the content and crawls In the third step, the labelled tweets are matched
the pages associated to URLs to identify the divergence ratio against certain language based features, which will help us to
from the original content to the content on the page where the calculate the divergence ratio and decide whether the tweets
URL redirects you to. are spam or not. Each tweet will be represented using natural
The researches on smoothing techniques are very language processing and content analysis technique.
less. The technique focuses on analysing the various factors of
D. Classification
the data being used. Paper [7] analyses the factors such as
training data size, test data size etc. It calculates the variations The prepared dataset consisting of shortlisted set of
in the existing methods. Cyber bots are increasing day by day twees where each tweet is represented by a set of features are
as the world is moving towards automation in social media given to the classifier to train the model and to gain necessary
too. Some bots which are reliable and legitimate, they focus knowledge to detect spams.
on doing the daily task for which they are programmed to but E. Spam Detection
some bots designed by humans who are ready to violate the
The classification algorithm takes a tweet form the
privacy of some users, are used to peep into other users data
user as input and reply back to the user whether it is spam or
and secretly retrieve the information. The analysis and
not. If any miss classification is been noticed by the
difference between these two types of bots is shown in [8]. By
supervisor, then the supervisor reports to the system about the
referring [9] we get to know the concept of relativity between
corrections, which results in updating the dataset from time to
contents and events. Event relatedness is analysed and the
time and the classifier goes through a continuous training
differences between events are presented.
process.
978-1-5090-5297-4/17/$31.00 ©2017 IEEE 436
International Conference on Inventive Communication and Computational Technologies
(ICICCT 2017)
IV. METHODOLOGY core classification. The features are not just limited to the one
mentioned. The text separated from the URL of the suspicious
A. Tweets collection and labelling tweets and other features extracted from the tweet. These
For the evaluation of our approach to detect spams in features are languages based features. Here the natural
the tweets, we need a pre-classified collection of tweets as language processing part comes into picture. The text is
spam or not spam. Such collection is publically available. We processed by removing the stop words and finding the
then designed a system which can browse through Twitter meaning of each separated word. He words are stored in
using Twitter APIs and methods to collect different trending dictionary. There are many other features through the text
topics and tweets associated to it. We collected the trending such as retweet count, number of #hashtags per tweet, number
topics from the English speaking countries (US, England, of followers of user and relative posts.
Canada, Australia). Trending topics were collected within a One of our features works on divergence ratio
five minutes time interval, there were around 15 K trending between two separated part. The divergence between the
topics. A total of approx. 70 K tweets based on English meaning of text and the page found by visiting and exploring
language were collected, from which almost 25 K tweets were the associated URL. Both of their types are checked and the
containing URLs whereas 8 K tweets were labelled as divergence between them is calculated which is counted as our
malicious. next feature. Spammers now a days are more clever, they
The above mentioned tweets were labelled as spams know what keywords can be suspicious and what cannot be
but it cannot be said that the remaining tweets are not spam, determined easily. Hence they are also using the most
perhaps, for proving our model they will be considered as common keywords to carry out their tasks. However on the
reliable tweets. Hence the remaining tweets need to be other side there isn’t any connection between the adjacent
analysed again as there may exist another technique through posts. The purpose of this feature is to analyze the tweets
which some of the tweets between them can be detected as relative to that, to know the divergence point. With the help of
spam. the divergence points we are able to build new language
model. The cost of computation for extracting these features is
B. Feature Extraction very low but they are not effective as expected.
In this section we will look forward for various new Considering all such scenarios we were able
language based features to improve spam detection. These to shortlist all the above mentioned features and we are
features play an important role, as here are not many previous looking for ten more features which will help us to classify the
works in statistical analysis of language for spam tweets tweets as spam or not, based on the content and the context of
identification up till now. The result of feature extraction is the tweet.
our final dataset used by classifier. This dataset will contain
two sets of tweets, which will be labeled as spam or not spam C. Classification
and it will also contain the tweets which are related to. In the If the datasets are pre-defined properly on which the
case that a user determines that a tweet has been misclassified, classification process is to be carried out, then the
all tweets affected by the same URL may be re-labeled and classification can be performed. The classification process can
updated in the dataset. either be performed using the programming method or it can
The language model is based on analysis of txt in the also be done through existing set of tools. We have prepared a
tweet and its associate language. It works over the slices of the setup of Weka (Whitten and Frank 2005) as it contains almost
text identifying of the probability distribution into it. each and every algorithm for machine learning and to carry
Generally the original and legitimate language is unknown and out data mining tasks. The prepared dataset is evaluated
is identified based on a sample of text representing that against many of the machine learning algorithms in the Weka
language. The probability distribution can then be identified tool. The main classifier we followed was the Support vector
and known by estimation of different models for each of machine. In previous works this algorithm was used with the
different texts. The method for extracting such language based default options, it was seen that the algorithm gave the
features is given as follows. accurate results as compared to other existing classifiers. As
The first step is to get each trending topic and then the results are not still up-to the mark and the evaluation has to
one by one the tweets associated to the topic. The tweets be carried out more precisely modifying the datasets and
found are divided into two categories, one those are not preparing them according to the requirements
containing any kind of links and the other that contain atleast
one URL. The tweets that does not contain any kind of links V. OBSERVATION AND RESULTS
are separated and are labeled as harmless. Rest of which We prepared an experimental setup of machine
contain any URL are proven as suspicious. Such tweets are learning tool “Weka”, which performs analysis based on many
sent for further process. The further evaluation of suspicious of the machine learning algorithms. As we have chosen SVM
tweets is done in two ways, first the tweets are partitioned in a as our main classifier, the results are based on those
way such that the text is separated and after that the URL experiments. For determining the accuracy of the system we
associated to the text is separated. The ULR are analyzed worked on a random set of sample 1000 tweets, from which
whether they are malicious or not, this becomes one of our 60% were legitimate and the rest were malicious. As the
feature to analyze the tweets. These tweets will be consider for
978-1-5090-5297-4/17/$31.00 ©2017 IEEE 437
International Conference on Inventive Communication and Computational Technologies
(ICICCT 2017)
classes for these users were known already, out of those 1000 informaion retrieval. SIGIR ’03.(pp. 314–321). New York, NY, USA:
ACM. http://dx.doi.org/10.1145/860435.860493.
tweets 95-97% were classified without mistake.
[6] Araujo, L., & Martinez-Romo, J. (2010). Web spam detection: new
classification features based on qualified link analysis and language
Confusion Matrix models. IEEE Transactions on Information Forensics and Security, 5(3),
581–590.
Spam Legitimate [7] Chen, S. F., & Goodman, J., 1996. An empirical study of smoothing
techniques for language modeling. In Proceedings of the 34th annual
Spam 38% 2% meeting on Association for Computational Linguistics. ACL ’96.
Association for Computational Linguistics, Stroudsburg, PA, USA (pp.
Legitimate 2% 58% 310–318). http://dx.doi.org/10.3115/981863.981904.
[8] Chu, Z., Gianvecchio, S., Wang, H., & Jajodia, S. (2012). Detecting
automation of twitter accounts: are you a human, bot, or cyborg? IEEE
Accuracy Transactions on Dependable and Secure Computing, 9(6), 811–824.
[9] Lee, C.-H. (2012). Unsupervised and supervised learning to evaluate
Accuracy True Positive False Positive event relatedness based on content mining from social-media streams.
Expert Systems with Applications, 39(18), 13338–13356.
93% 0.975 0.05 <http://www.sciencedirect.com/science/article/pii/S0957417412007841
>.
[10] Nishanth, K. J., Ravi, V., Ankaiah, N., & Bose, I. (2012). Soft
computing based imputation and hybrid data and text mining: The case
VI. CONCLUSION of predicting the severity of phishing alerts. Expert Systems with
Applications, 39(12), 10583–10589.
The main objective of the paper was to analyze the
[11] K. Kandasamy, P. Koroth, “An Integrated Approach to Spam
tweets on twitter by applying the mentioned classification Classification on Twitter Using URL Analysis, Natural Language
algorithms. The SVM classifier gives the standard results. The Processing and Machine Learning Techniques”, IEEE Students’
paper presented a new methodology for detecting spam tweets Conference on Electrical, Electronics and Computer Science 2014.
from twitter which was different from the previous works [12] Mochamad Vicky Ghani Aziz, Ary Setijadi Prihatmanto, “Design and
Implementation of Natural Language Processing with Syntax and
which only focused on detecting spam accounts. The use of Semantic Analysis for Extract Traffic Conditions from Social Media
language models were with the purpose to detect the Data”, IEEE 5th International Conference on System Engineering and
divergence from one place to another, from which some of Technology, Aug. 10 - 11, 2015.
them further proved to be malicious.
ACKNOWLEDGMENT
I would like to thank my Guide Mr. M.K. Chavan for
their continuous help and encouragement. Also a word of
appreciation for Department of CSE, Walchand College for
providing useful resources.
REFERENCES
[1] Chao Chen, Jun Zhang, Member, IEEE, “A Performance Evaluation of
Machine Learning-Based Streaming Spam Tweets Detection”, IEEE
Transactions on Computational social systems, vol. 2, no. 3, september
2015.
[2] C. P.-Y. Chin, N. Evans, and K.-K. R. Choo, “Exploring factors
influencing the use of enterprise social networks in multinational
professional service firms,” J. Organizat. Comput. Electron. Commerce,
vol. 25, no. 3, pp. 289–315, 2015.
[3] Z. Miller, B. Dickinson, W. Deitrick, W. Hu, and A. H. Wang, “Twitter
spammer detection using data stream clustering,” Inf. Sci., vol. 260, pp.
64–73, Mar. 2014.
[4] Juan Martinez-Romo, Lourdes Araujo, “Detecting malicious tweets in
trending topics using a statistical analysis of language”, Expert Systems
with Applications 40 (2013) 2992–3000.
[5] Allan, J., Wade, C., & Bolivar, A. (2003). Retrieval and novelty
detection at the sentence level. In Proceedings of the 26th annual
international ACM SIGIR conference on Research and development in
978-1-5090-5297-4/17/$31.00 ©2017 IEEE 438
You might also like
- Cyberspace News Prediction of Text and ImageDocument53 pagesCyberspace News Prediction of Text and ImagecityNo ratings yet
- Improving Spam Detection in Online Social Networks: Arushi Gupta Rishabh KaushalDocument6 pagesImproving Spam Detection in Online Social Networks: Arushi Gupta Rishabh KaushalShifanaNo ratings yet
- Spam Detection in Social Media Using Machine Learning AlgorithmDocument10 pagesSpam Detection in Social Media Using Machine Learning AlgorithmIJRASETPublicationsNo ratings yet
- Spammer Detect Project DocumentDocument45 pagesSpammer Detect Project Documentsainadh upputhollaNo ratings yet
- A Comprehensive Review On Twitter Spam DetectionDocument13 pagesA Comprehensive Review On Twitter Spam DetectionHamza MunirNo ratings yet
- Cybercrime Profiling: Text Mining Techniques To Detect and Predict Criminal Activities in Microblog PostsDocument5 pagesCybercrime Profiling: Text Mining Techniques To Detect and Predict Criminal Activities in Microblog Postsbin.kdsnokiaNo ratings yet
- Semi-Supervised Spam Detection in Twitter StreamDocument7 pagesSemi-Supervised Spam Detection in Twitter Streamkaran kallaNo ratings yet
- A Content Filtering Scheme in Social SitesDocument8 pagesA Content Filtering Scheme in Social SitesEDUARDO FELIPE RAMIREZ INFANTESNo ratings yet
- Social Network Shaming Text: Identification, Inspection, ReductionDocument12 pagesSocial Network Shaming Text: Identification, Inspection, ReductionHetNo ratings yet
- Cyberbullying Detection Using Machine LearningDocument6 pagesCyberbullying Detection Using Machine LearningthomaslusiferNo ratings yet
- 3216avc01 PDFDocument10 pages3216avc01 PDFavcjournalNo ratings yet
- Spammer Detection and Fake User Identification On Social NetworksDocument9 pagesSpammer Detection and Fake User Identification On Social NetworksTech NestNo ratings yet
- Opinion Mining On Social Media Data: 2013 IEEE 14th International Conference On Mobile Data ManagementDocument6 pagesOpinion Mining On Social Media Data: 2013 IEEE 14th International Conference On Mobile Data ManagementsenthilnathanNo ratings yet
- Statistical Twitter Spam Detection Demystified: Performance, Stability and ScalabilityDocument13 pagesStatistical Twitter Spam Detection Demystified: Performance, Stability and ScalabilityAakash GargNo ratings yet
- Fake Profile IdentificationDocument51 pagesFake Profile IdentificationRohini ChinthalaNo ratings yet
- Sentiment Analysis On TwitterDocument8 pagesSentiment Analysis On TwitterIJRISE Journal100% (2)
- NLP and Machine Learning Techniques For Detecting Insulting Comments On Social Networking PlatformsDocument8 pagesNLP and Machine Learning Techniques For Detecting Insulting Comments On Social Networking Platformsit's ARKNo ratings yet
- IRJET_FAKE_NEWS_PREDICTION_USING_MACHINEDocument5 pagesIRJET_FAKE_NEWS_PREDICTION_USING_MACHINEalperen.unal89No ratings yet
- Classification and Analysis On Fake News in Social Media Using Machine LearningDocument10 pagesClassification and Analysis On Fake News in Social Media Using Machine LearningInternational Journal of Innovative Science and Research TechnologyNo ratings yet
- Fake News Synopsis 1Document6 pagesFake News Synopsis 1VAIBHAV SRIVASTAVANo ratings yet
- Rumour Detection from Social MediaDocument19 pagesRumour Detection from Social Mediachirag0% (1)
- Cyberbullying IPRDocument25 pagesCyberbullying IPRSajid MdNo ratings yet
- Research Paper On Spam DetectionDocument5 pagesResearch Paper On Spam Detectionhbkgbsund100% (1)
- Bot FinderDocument16 pagesBot FinderSamuelNo ratings yet
- (IJCST-V10I5P20) :MR D.Purushothaman, K PavanDocument9 pages(IJCST-V10I5P20) :MR D.Purushothaman, K PavanEighthSenseGroupNo ratings yet
- Sentiment Analysis For Promotional Campaigns: 1 Sameer Mulani 2 Nikhat PathanDocument3 pagesSentiment Analysis For Promotional Campaigns: 1 Sameer Mulani 2 Nikhat PathanSameer MulaniNo ratings yet
- Email Spam PDFDocument5 pagesEmail Spam PDFOmer ErçelNo ratings yet
- A Batch Based Approach For Tweeting Geotags of Social Media AttributesDocument13 pagesA Batch Based Approach For Tweeting Geotags of Social Media AttributesIJRASETPublicationsNo ratings yet
- Article 13Document7 pagesArticle 13Siddhant MhaskeNo ratings yet
- S U R J S S: Indh Niversity Esearch Ournal (Cience Eries)Document6 pagesS U R J S S: Indh Niversity Esearch Ournal (Cience Eries)adsNo ratings yet
- News Summarization and AuthenticationDocument3 pagesNews Summarization and AuthenticationShashaNo ratings yet
- Retrieving Hidden Friends A Collusion Privacy Attack Against Online Friend Search EngineDocument5 pagesRetrieving Hidden Friends A Collusion Privacy Attack Against Online Friend Search EngineEditor IJTSRDNo ratings yet
- Cyber Bullying Detection Using Machine Learning-IJRASETDocument10 pagesCyber Bullying Detection Using Machine Learning-IJRASETIJRASETPublicationsNo ratings yet
- Detecting Malicious Facebook Applications Using Classification TechniqueDocument3 pagesDetecting Malicious Facebook Applications Using Classification TechniqueSameerSinghNo ratings yet
- Fake News Detection Using Machine Learning: A ReviewDocument6 pagesFake News Detection Using Machine Learning: A ReviewIjaems JournalNo ratings yet
- Karthik.S-Spammer Detection and Fake User Identification On Social NetworksDocument5 pagesKarthik.S-Spammer Detection and Fake User Identification On Social NetworksAnil KumarNo ratings yet
- Machine Learning Approach To Classify Twitter Hate SpeechDocument5 pagesMachine Learning Approach To Classify Twitter Hate SpeechEditor IJTSRDNo ratings yet
- Detection of Cyberbullying On Social Media Using Machine LearningDocument6 pagesDetection of Cyberbullying On Social Media Using Machine LearningSLDFLAGNo ratings yet
- Twitter Bullying DetectionDocument7 pagesTwitter Bullying Detectionkarishma patilNo ratings yet
- Detect Cyberbullying in Hindi and Marathi Using Machine LearningDocument6 pagesDetect Cyberbullying in Hindi and Marathi Using Machine Learningmubeen naeemNo ratings yet
- Data Mining To Track Suspicious Discussions On Online ForumsDocument6 pagesData Mining To Track Suspicious Discussions On Online ForumsSANDYA DUMPANo ratings yet
- Survey On Spam Filtering in Text Analysis: Saksham Sharma, Rabi Raj YadavDocument7 pagesSurvey On Spam Filtering in Text Analysis: Saksham Sharma, Rabi Raj YadavAnonymous TpYSenLO8aNo ratings yet
- Spam Detection Framework For Android Twitter Application Using Naïve Bayes and K-Nearest Neighbor ClassifiersDocument6 pagesSpam Detection Framework For Android Twitter Application Using Naïve Bayes and K-Nearest Neighbor ClassifiersHaniAzzahraNo ratings yet
- Multi-Purpose Chat Bot: Team Formation Team MembersDocument15 pagesMulti-Purpose Chat Bot: Team Formation Team MembersShubham ChaudharyNo ratings yet
- The Spammer Detection and Fake User Identification On Social NetworksDocument8 pagesThe Spammer Detection and Fake User Identification On Social NetworksIJRASETPublicationsNo ratings yet
- Twitter Data Preprocessing For Spam Detection: Myungsook KlassenDocument6 pagesTwitter Data Preprocessing For Spam Detection: Myungsook KlassenSupportGameNo ratings yet
- Detecting Indonesian Spammer On Twitter: Erwin B. Setiawan, Dwi H. Widyantoro, Kridanto SurendroDocument5 pagesDetecting Indonesian Spammer On Twitter: Erwin B. Setiawan, Dwi H. Widyantoro, Kridanto SurendroTech NestNo ratings yet
- Paper 1304079 FahimAbrarDocument8 pagesPaper 1304079 FahimAbraralifNo ratings yet
- (IJCST-V3I6P14) : Ritu Kumari, Utkarsha Mamidwar, Sanjoli Kapoor, Kritika Sharma, Mrs - Deepali GothawalDocument5 pages(IJCST-V3I6P14) : Ritu Kumari, Utkarsha Mamidwar, Sanjoli Kapoor, Kritika Sharma, Mrs - Deepali GothawalEighthSenseGroupNo ratings yet
- 17581556-026 RM (It-403) Mid Paper Spring 2020Document6 pages17581556-026 RM (It-403) Mid Paper Spring 2020Abdullah AbbasNo ratings yet
- 17581556-026 RM (It-403) Mid Paper Spring 2020Document6 pages17581556-026 RM (It-403) Mid Paper Spring 2020Abdullah AbbasNo ratings yet
- Research PAPER ML ABHIMANYUDocument2 pagesResearch PAPER ML ABHIMANYUnowaynora2No ratings yet
- Monitoring of Suspicious Discussions On Online Forums Using Data MiningDocument7 pagesMonitoring of Suspicious Discussions On Online Forums Using Data MiningSANDYA DUMPANo ratings yet
- Identifying & Mitigating Phone Number Abuse on Social MediaDocument159 pagesIdentifying & Mitigating Phone Number Abuse on Social MediaWendyNo ratings yet
- Analysis of Rumour Detection Using Deep Learning Methods On Social MediaDocument10 pagesAnalysis of Rumour Detection Using Deep Learning Methods On Social MediaInternational Journal of Innovative Science and Research TechnologyNo ratings yet
- Comparative Study of RumourDocument25 pagesComparative Study of RumourkritheedeviNo ratings yet
- Thesis On Spam DetectionDocument4 pagesThesis On Spam Detectionalisoncariassiouxfalls100% (2)
- Capstone Project Proposal: SurakshaDocument12 pagesCapstone Project Proposal: SurakshaShubhanshu KhirwarNo ratings yet
- SSRN Id3972525Document7 pagesSSRN Id3972525tvnijeeshNo ratings yet
- FFFDocument3 pagesFFFTech NestNo ratings yet
- 12th Maths Vol.2 Model Question Paper Tamil MediumDocument6 pages12th Maths Vol.2 Model Question Paper Tamil MediumTech NestNo ratings yet
- B.E./B.Tech. Degree Examinations Question PaperDocument3 pagesB.E./B.Tech. Degree Examinations Question PaperTech NestNo ratings yet
- A Study On Brand Preference of Soft Drinks at Madurai CityDocument13 pagesA Study On Brand Preference of Soft Drinks at Madurai CityTech NestNo ratings yet
- Block Diagram: Water Level SensorDocument1 pageBlock Diagram: Water Level SensorTech NestNo ratings yet
- 05 - Chapter 2Document28 pages05 - Chapter 2Tech NestNo ratings yet
- GOVERNMENT POLYTECHNIC COLLEGE VeeraDocument2 pagesGOVERNMENT POLYTECHNIC COLLEGE VeeraTech NestNo ratings yet
- Government Polytechnic College: Bonafide CertificateDocument2 pagesGovernment Polytechnic College: Bonafide CertificateTech NestNo ratings yet
- Factors Influencing Consumer Preference of Branded Soft Drinks in Tamil NaduDocument20 pagesFactors Influencing Consumer Preference of Branded Soft Drinks in Tamil NaduTech NestNo ratings yet
- Government Polytechnic CollegeDocument1 pageGovernment Polytechnic CollegeTech NestNo ratings yet
- 26Document1 page26Tech NestNo ratings yet
- Power System Protection and SwitchgearDocument96 pagesPower System Protection and SwitchgearjonatasNo ratings yet
- Detecting Indonesian Spammer On Twitter: Erwin B. Setiawan, Dwi H. Widyantoro, Kridanto SurendroDocument5 pagesDetecting Indonesian Spammer On Twitter: Erwin B. Setiawan, Dwi H. Widyantoro, Kridanto SurendroTech NestNo ratings yet
- Factors Influencing Branded Soft Drinks Among The People of Salem, Tamil NaduDocument6 pagesFactors Influencing Branded Soft Drinks Among The People of Salem, Tamil NaduTech NestNo ratings yet
- Consumer Preferences for Branded Soft Drinks in Tamil Nadu CitiesDocument28 pagesConsumer Preferences for Branded Soft Drinks in Tamil Nadu CitiesTech NestNo ratings yet
- Spammer Detection and Fake User Identification On Social NetworksDocument9 pagesSpammer Detection and Fake User Identification On Social NetworksTech NestNo ratings yet
- Secure Data Sharing in Cloud Computing Using Revocable StorageDocument13 pagesSecure Data Sharing in Cloud Computing Using Revocable StorageAmit PandeyNo ratings yet
- EliminationDocument2 pagesEliminationTech NestNo ratings yet
- Cloud BasepaperDocument13 pagesCloud BasepaperTech NestNo ratings yet
- Customer Perceived Value - and Risk-AwareDocument15 pagesCustomer Perceived Value - and Risk-AwareTech NestNo ratings yet
- Table of Content PDFDocument5 pagesTable of Content PDFTech NestNo ratings yet
- 9Document12 pages9Tech NestNo ratings yet
- AGREEMENTDocument1 pageAGREEMENTTech NestNo ratings yet
- Profit Maximization Strategy With Spot AllocationDocument6 pagesProfit Maximization Strategy With Spot AllocationTech NestNo ratings yet
- ReportDocument67 pagesReportTech NestNo ratings yet
- Table of Content PDFDocument5 pagesTable of Content PDFTech NestNo ratings yet
- Jewel LoanDocument1 pageJewel LoanTech NestNo ratings yet
- AsssDocument1 pageAsssTech NestNo ratings yet
- Abstract PDFDocument1 pageAbstract PDFTech NestNo ratings yet
- BRI Divisions and Branches Level ReportDocument177 pagesBRI Divisions and Branches Level ReportCalvin Watulingas100% (1)
- RVM100 Instruction ManualDocument7 pagesRVM100 Instruction ManualRubénNo ratings yet
- Moot Problem For ICA - NMIMS - June 2021Document3 pagesMoot Problem For ICA - NMIMS - June 2021AayushiNo ratings yet
- 03 IoT Technical Sales Training Industrial Wireless Deep DiveDocument35 pages03 IoT Technical Sales Training Industrial Wireless Deep Divechindi.comNo ratings yet
- Igbe Religion's 21st Century Syncretic Response to ChristianityDocument30 pagesIgbe Religion's 21st Century Syncretic Response to ChristianityFortune AFATAKPANo ratings yet
- BS 07579-1992 (1999) Iso 2194-1991Document10 pagesBS 07579-1992 (1999) Iso 2194-1991matteo_1234No ratings yet
- Teacher Resume Alison KnipferDocument2 pagesTeacher Resume Alison Knipferapi-317249919No ratings yet
- Design Portfolio (Priyal)Document30 pagesDesign Portfolio (Priyal)PRIYAL SINGHALNo ratings yet
- Quality Management and Control in ConstructionDocument22 pagesQuality Management and Control in ConstructionjennyNo ratings yet
- Question 1 - Adjusting EntriesDocument10 pagesQuestion 1 - Adjusting EntriesVyish VyishuNo ratings yet
- UNIX Unbounded 5 Edition: Amir AfzalDocument23 pagesUNIX Unbounded 5 Edition: Amir AfzalOsei BanningNo ratings yet
- Cyber Crime and Law ClassDocument99 pagesCyber Crime and Law ClassMohd ShifanNo ratings yet
- Bankable Project FinalDocument32 pagesBankable Project FinalSanjay Baria0% (1)
- List of MBA Institutes in HyderabadDocument5 pagesList of MBA Institutes in Hyderabadebrandingindia1No ratings yet
- Types of EquityDocument2 pagesTypes of EquityPrasanthNo ratings yet
- Pre Test in Pe 12Document3 pagesPre Test in Pe 12HERMINIA PANCITONo ratings yet
- Facebook Black BookDocument23 pagesFacebook Black Bookwise_man1975100% (1)
- Lipid ChemistryDocument93 pagesLipid ChemistrySanreet RandhawaNo ratings yet
- Manage Vitamin B12 DeficiencyDocument5 pagesManage Vitamin B12 DeficiencyAnca CucuNo ratings yet
- Simulation of Spring: Date: Martes, 25 de Agosto de 2020 Designer: Solidworks Study Name: Resorte 1 Analysis TypeDocument10 pagesSimulation of Spring: Date: Martes, 25 de Agosto de 2020 Designer: Solidworks Study Name: Resorte 1 Analysis TypeIván D. ArdilaNo ratings yet
- LCP4805-mc Mehta Vs Union of IndiaDocument60 pagesLCP4805-mc Mehta Vs Union of Indiatech hutNo ratings yet
- Speidel, M. O. (1981) - Stress Corrosion Cracking of Stainless Steels in NaCl Solutions.Document11 pagesSpeidel, M. O. (1981) - Stress Corrosion Cracking of Stainless Steels in NaCl Solutions.oozdemirNo ratings yet
- 2.3 Stabilized MaterialDocument11 pages2.3 Stabilized MaterialMamush LetaNo ratings yet
- Embedded SQL Into RPGDocument8 pagesEmbedded SQL Into RPGMaran GanapathyNo ratings yet
- 07 - Toshkov (2016) Theory in The Research ProcessDocument29 pages07 - Toshkov (2016) Theory in The Research ProcessFerlanda LunaNo ratings yet
- Arijit Singh Lyrics: "Saawali Si Raat"Document1 pageArijit Singh Lyrics: "Saawali Si Raat"123No ratings yet
- SITXFSA001 - Assessment A - Short Answer - V2-1Document34 pagesSITXFSA001 - Assessment A - Short Answer - V2-1Namwetayeka Richald WanihaNo ratings yet
- Mental Health and Mental Disorder ReportDocument6 pagesMental Health and Mental Disorder ReportBonJovi Mojica ArtistaNo ratings yet
- 47 Syeda Nida Batool Zaidi-1Document10 pages47 Syeda Nida Batool Zaidi-1Eiman ShahzadNo ratings yet
- LTC exemption and tax on retrenchment compensationDocument2 pagesLTC exemption and tax on retrenchment compensationhanumanthaiahgowdaNo ratings yet