Professional Documents
Culture Documents
Microsoft Incident Response Playbook
Microsoft Incident Response Playbook
Uploaded by
Zubair RahimCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Microsoft Incident Response Playbook
Microsoft Incident Response Playbook
Uploaded by
Zubair RahimCopyright:
Available Formats
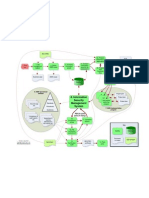
Incident response playbook:
Phishing investigation (part 1)
Start with
initial phishing email / Subject /
email address(es)
Get the list of users /
identities who got the email
Who else got/read the same
email?
Get timestamp when the
Is there delegated Is there a forwarding List of users / user / identity had access to
access to the mailbox? rule for the mailbox? identities the mailbox
Yes
Yes Investigate sign-in
To which user(s) is it events for the identity
delegated /
forwarded?
Stop / Remove the user /
Did the user read the
No identity off the potential
email? list
Did the email
Was there payload in Record hash
contain an Yes Yes
the attachment? / iOC
attachment?
No
A No
May 2021 © 2021 Microsoft Corporation. All rights reserved.
Incident response playbook:
Phishing investigation (part 2)
Check email header for
Record the source IP Verify IP addresses to
the true source of the
address attackers/campaigns
sender
Record destination IP
Did the user click the
Yes address /
link in the email?
destination URL
No
On what endpoint(s) For each
Get Device ID
was the email opened? endpoint
Attachment was Get device
Yes Process creation event?
executed? investigation package
No
Perform device forensics
Was code Yes
Was the dest IP / URL
Yes downloaded /
touched/opened?
executed?
No
Investigate sign-in
events for the identity
Record time stamps, devices,
Investigate source IP
source IP addresses, app IDs, user- Identify device
address
agent string
Investigate each App ID App Investigation flow
May 2021 © 2021 Microsoft Corporation. All rights reserved.
Incident response playbook:
Password spray
Check ADFS for an increase Note
Yes * Must locate successful password attempts
Incident trigger Are you federated? in failed passwod attempts
and/or extranet lockouts even if the "complete" login was unsuccessful.
For example, password was correct but MFA
challenge failed.
** Potential business impact
No
Check Azure AD sign-in for failed
password attempts, extranet Collect any successful sign-
lockout, authentication protocol ins, IP addresses and
and identity protection for authentication protocols
password spray alert used during the attack time
Is the IP address a
Is password spray No known address or Yes Troubleshoot as per
attack confimed? another explanation for operational process
the alert?
Yes
No
Collect any successful sign-ins
during this time and attacker IP
addresses*
Mitigation
Is the compromised Yes Change user s password and Has the attacker
Follow procedure for
password or mark as compromised in successfully
data loss
account identified? identity protection accessed data?
Block IP address of attack on
Firewall, Azure AD and ADFS
Is legacy No Block legacy
authentication
authentication **
blocked?
Yes
No
Is MFA enabled? Enable MFA
Yes
IP policies No Enable IP policies and
enabled? risk-based CA
Yes
Enable extranet lockout.
Is extranet No
Threshold must be less than
lockout enabled?
on-prem
Enable longer term
protections
May 2021 © 2021 Microsoft Corporation. All rights reserved.
Incident response playbook:
App consent grant
S igns of an Inventory apps with
application consent access using of these
grant attack three methods
Users enumerate
Azure AD poral PowerShell
their app access
The AllPrincipals look for
AzureADPSPermissions.ps1 high-risk impact
script output file permissions. See
aka.ms/consentperms
Run AzureADPSPermissions
script
Filter the results
on ConsentType (column
G)
Search for value "All
Search for value "All
Principals" user consent
Principals" admin Yes Yes No Stop
only applicable to the
consent tenant-wide.
user who consented.
Look in column F, review
permissions for each
No delegated application. Look
for review "read", "write",
"*.all" permissions.
Review users that have Review apps with misspelled names, bland names,
consent granted. If high- hacker-sounding names
profile or high-impact users
have inappropriate consents ISP investigation
granted, then investigate - ReplyURL/RedirectURL
further. - Look for suspicious URLs ( Is the URL hosted on a
suspicious domain? Is the URL compromised, is it
recently registered? Is it a temporary domain?
Apps with - Is there a terms of service/agreement link in the
misspelled names, Check ClientDisplayName app registration? Is the content unique and
bland names, or (column C) for apps that specific to the application/publisher?
hacker-sounding seem suspicious. - Is the tenant that registered the application
names newly created or compromised? (for example, is
the app registered by an at-risk user?)
Confirmed attack No
Yes
Completed
investigation
Revoke application's
permissions using one of
these methods:
Navigate to the Use PowerShell to revoke OAuth Use PowerShell to revoke Disable sign-in for the account, Disable integrated
affected user in the consent grant. Follow the steps Service AppRole Assignment. which will disable app access to applications for your
Azure AD portal. in Remove AzureAD Follow the steps in data in that account. Not ideal for tenancy (Not
OAuth2PermissionGrant RemoveAzureADServiceAppRole user, but useful for short-term recommended)
cmdlets. Assignment. remediation.
Navigate to Admin
Select Applications > In the Azure AD portal,
Remove AzureADOAuth2Permissi Remove AzureADServiceAppRole Center>Settings>Org
the suspicious app select User > Profile > Settings,
onsGrant -ObjectId <string> Assignment -ObjectId <string> settings>Services page,
> Remove. and block sign-in.
select UserConsent to apps.
May 2021 © 2021 Microsoft Corporation. All rights reserved.
You might also like
- Lab 1 Foot Printing and ReconnaissanceDocument220 pagesLab 1 Foot Printing and Reconnaissancefawas hamdi50% (2)
- Example of SOC RACI With Both Internal Resources of A Given Organization and Pure-Player MSSPDocument2 pagesExample of SOC RACI With Both Internal Resources of A Given Organization and Pure-Player MSSPJames LeeNo ratings yet
- OWASP Security Culture-1.0Document26 pagesOWASP Security Culture-1.0Luiz Henrique CustódioNo ratings yet
- Lab 4 Vulnerability AnalysisDocument98 pagesLab 4 Vulnerability Analysisfawas hamdiNo ratings yet
- Pentest ReportDocument19 pagesPentest ReportMuhammad Awais100% (1)
- Lab 2 Scanning NetworksDocument143 pagesLab 2 Scanning Networksfawas hamdi100% (1)
- Certified Secure Web Application Engineer (CSWAE) Course Outline - Rev.2.1Document4 pagesCertified Secure Web Application Engineer (CSWAE) Course Outline - Rev.2.1Zidane LanceNo ratings yet
- Hooli Phishing Simulation Report v1.0Document13 pagesHooli Phishing Simulation Report v1.0JordanNo ratings yet
- Ey How Do You Protect Robots From Cyber AttackDocument17 pagesEy How Do You Protect Robots From Cyber AttackabgmNo ratings yet
- Foundations of Breach & Attack Simulation: Student GuideDocument26 pagesFoundations of Breach & Attack Simulation: Student GuideJonathan GillNo ratings yet
- TR18 AD MSFT Defence at ScaleDocument31 pagesTR18 AD MSFT Defence at ScalekeepzthebeezNo ratings yet
- Tounsi - Threat IntelligenceDocument22 pagesTounsi - Threat IntelligenceRafael PaimNo ratings yet
- Lab 3 EnumerationDocument121 pagesLab 3 Enumerationfawas hamdi100% (1)
- The Threat Environment: Attackers and Their AttacksDocument8 pagesThe Threat Environment: Attackers and Their AttacksbseosNo ratings yet
- Pentesting PresentationDocument99 pagesPentesting PresentationMaqsood AlamNo ratings yet
- Cyber ScapeDocument1 pageCyber Scapemirza sharifNo ratings yet
- List of Confidence TricksDocument23 pagesList of Confidence TricksRichard0% (1)
- Absolute Beginner's Guide To Security, Spam, Spyware & Viruses-Walker PDFDocument585 pagesAbsolute Beginner's Guide To Security, Spam, Spyware & Viruses-Walker PDFGireesh Chowdary GarikapatiNo ratings yet
- M04 - Part 2 Case Project - Lake Point Security Consulting-Shaker MohammadtomDocument12 pagesM04 - Part 2 Case Project - Lake Point Security Consulting-Shaker MohammadtomShakerNo ratings yet
- Netwrix SY0 501 StudyGuide PDFDocument154 pagesNetwrix SY0 501 StudyGuide PDFvenky_akella100% (4)
- Rank Software - Threat Hunting PlaybookDocument31 pagesRank Software - Threat Hunting PlaybookDrake von Duck100% (1)
- Rsa Sans Roadmap To Creating A World Class SocDocument1 pageRsa Sans Roadmap To Creating A World Class SocRoot100% (1)
- CISO RoadmapDocument4 pagesCISO Roadmapcyberlearnhub24No ratings yet
- Ransomware Executive One-Pager and Technical Document-FINAL PDFDocument10 pagesRansomware Executive One-Pager and Technical Document-FINAL PDFNeenu SukumaranNo ratings yet
- Risk Assessment Process Nist 80030 7383Document20 pagesRisk Assessment Process Nist 80030 7383datadinkNo ratings yet
- An Approach To Vulnerability Management: by Umesh Chavan, CISSPDocument3 pagesAn Approach To Vulnerability Management: by Umesh Chavan, CISSPRaju PatleNo ratings yet
- Privacy Standards and FrameworksDocument2 pagesPrivacy Standards and FrameworksSaldovNo ratings yet
- OWASP Vulnerability Management Guide (OVMG)Document20 pagesOWASP Vulnerability Management Guide (OVMG)rajularNo ratings yet
- DFIRDocument26 pagesDFIRAndrei StefanNo ratings yet
- IoT Security Checklist Web 10 17 r1Document39 pagesIoT Security Checklist Web 10 17 r1SubinNo ratings yet
- FFIEC CAT App B Map To NIST CSF June 2015 PDF4 PDFDocument24 pagesFFIEC CAT App B Map To NIST CSF June 2015 PDF4 PDFyaya yahuNo ratings yet
- Threat Hunting With Cortex XDR: Jani Haapio Channel SEDocument32 pagesThreat Hunting With Cortex XDR: Jani Haapio Channel SEep230842No ratings yet
- TATA Communications VAPT Service OverviewDocument20 pagesTATA Communications VAPT Service Overviewnidelel214No ratings yet
- ACSC Cyber Incident Response Plan Guidance - A4Document56 pagesACSC Cyber Incident Response Plan Guidance - A4Elena VaciagoNo ratings yet
- User + Entity Behavior Analytics (Ueba) : The Heart of Next-Generation Threat HuntingDocument19 pagesUser + Entity Behavior Analytics (Ueba) : The Heart of Next-Generation Threat HuntingShuichi SakaiNo ratings yet
- Hunting On The Endpoint PDFDocument30 pagesHunting On The Endpoint PDFMondher SmiiNo ratings yet
- Insident ResponseDocument8 pagesInsident Responseraghuram medapatiNo ratings yet
- CIS IBM DB2 9 Benchmark v3.0.1Document206 pagesCIS IBM DB2 9 Benchmark v3.0.1Andrei SandulescuNo ratings yet
- Mandiant - Company - Presentation - SHORT - V0.1 MASTERDocument38 pagesMandiant - Company - Presentation - SHORT - V0.1 MASTERuakarsuNo ratings yet
- Problems of Business Cyber-Risk EstimationDocument21 pagesProblems of Business Cyber-Risk EstimationRezwan Hassan RashedNo ratings yet
- Content Analysis Techniques Once The Content Is Accessed, There Are Seven Major Analysis TechniquesDocument2 pagesContent Analysis Techniques Once The Content Is Accessed, There Are Seven Major Analysis Techniquesamitdhawan1No ratings yet
- Playbooks-Mitigation of Phishing CampaignsDocument6 pagesPlaybooks-Mitigation of Phishing CampaignsLudwig Geoffrey100% (1)
- How To Mitigate Cyber RisksDocument10 pagesHow To Mitigate Cyber Riskstoanquoc.doanNo ratings yet
- Security Orchestration, Automation, and Response (SOAR)Document21 pagesSecurity Orchestration, Automation, and Response (SOAR)Widie AozoraNo ratings yet
- Cybersecurity Incident Response - How To Survive An AttackDocument26 pagesCybersecurity Incident Response - How To Survive An Attacka50% (2)
- CISM Model QuestionsDocument12 pagesCISM Model QuestionsKumar0% (1)
- OSSIM ComponentsDocument8 pagesOSSIM Componentsbad3106No ratings yet
- Incident Response PlanDocument7 pagesIncident Response Plandss777No ratings yet
- Ransomware Readiness GuideDocument15 pagesRansomware Readiness GuideadminakNo ratings yet
- Advanced APT Hunting Workshop 26012021 ReduxDocument136 pagesAdvanced APT Hunting Workshop 26012021 ReduxGenestapowerNo ratings yet
- Course: Information Security Management in E-GovernanceDocument53 pagesCourse: Information Security Management in E-GovernancehNo ratings yet
- Mobile Application Security Review ChecklistDocument2 pagesMobile Application Security Review Checklistbudi.hw748No ratings yet
- Thread ModelingDocument41 pagesThread ModelingMervNo ratings yet
- Risk Identification ProcessDocument1 pageRisk Identification ProcessВіталій ІванюкNo ratings yet
- IPD - Malware ResponseDocument28 pagesIPD - Malware ResponseshuvoNo ratings yet
- ISO27k ISMS Implementation and Certification ProcessDocument1 pageISO27k ISMS Implementation and Certification Processvishnukesarwani100% (2)
- Cloud SecurityDocument4 pagesCloud SecurityPrince Kumar BhatiaNo ratings yet
- ISO-IEC 27001 Self Assessment FormDocument3 pagesISO-IEC 27001 Self Assessment FormAlea Consulting100% (1)
- CSSLP Brochure ForPDFDocument6 pagesCSSLP Brochure ForPDFjoekkuNo ratings yet
- Least Privilege CybersecurityDocument21 pagesLeast Privilege CybersecurityjuanNo ratings yet
- Misp Book PDFDocument391 pagesMisp Book PDFStewart GarzonNo ratings yet
- Web PEN Test ReportDocument8 pagesWeb PEN Test ReportRahul BhangaleNo ratings yet
- Cybersecurity Roadmap For PPT DownloadDocument7 pagesCybersecurity Roadmap For PPT DownloadDawood lifeNo ratings yet
- Cyber Security QuestionnaireDocument18 pagesCyber Security QuestionnaireDheer Shreyhan PuddooNo ratings yet
- Pentesting ReportDocument3 pagesPentesting ReportLovepreetSidhu100% (1)
- Cyber EthicsDocument16 pagesCyber Ethicsnavinnaithani100% (2)
- Cyber Security Incident Response A Complete Guide - 2020 EditionFrom EverandCyber Security Incident Response A Complete Guide - 2020 EditionNo ratings yet
- Dynamic Application Security Testing A Complete Guide - 2019 EditionFrom EverandDynamic Application Security Testing A Complete Guide - 2019 EditionNo ratings yet
- AS HB171 - Guidelines For The Management of of EvidenceDocument42 pagesAS HB171 - Guidelines For The Management of of Evidencefawas hamdiNo ratings yet
- Sample TicketDocument4 pagesSample Ticketfawas hamdiNo ratings yet
- 2019 ITEC854 Security Management - Week 13Document12 pages2019 ITEC854 Security Management - Week 13fawas hamdiNo ratings yet
- 2019 ITEC854 Security Management - Week 08Document27 pages2019 ITEC854 Security Management - Week 08fawas hamdiNo ratings yet
- 2019 ITEC854 Security Management - Week 10Document34 pages2019 ITEC854 Security Management - Week 10fawas hamdiNo ratings yet
- OSSTMM 3.0.: The Open Source Security Testing Methodology ManualDocument30 pagesOSSTMM 3.0.: The Open Source Security Testing Methodology Manualfawas hamdi100% (1)
- 2019 ITEC854 Security Management - Week 11Document61 pages2019 ITEC854 Security Management - Week 11fawas hamdiNo ratings yet
- Scenario-Based (IT) Risk Assessment & Management: Peter R. Bitterli, CISA, CISM, CGEITDocument106 pagesScenario-Based (IT) Risk Assessment & Management: Peter R. Bitterli, CISA, CISM, CGEITfawas hamdi100% (1)
- Senior Executives Commitment To Information Security - From Motivation To ResponsibilityDocument4 pagesSenior Executives Commitment To Information Security - From Motivation To Responsibilityfawas hamdiNo ratings yet
- This Study Resource Was: ISO 27001 Documentation ToolkitDocument6 pagesThis Study Resource Was: ISO 27001 Documentation Toolkitfawas hamdiNo ratings yet
- Sample Asset Register/Inventory List: Additional Information That May Help You Track E-Rate Program Supported EquipmentDocument1 pageSample Asset Register/Inventory List: Additional Information That May Help You Track E-Rate Program Supported Equipmentfawas hamdiNo ratings yet
- ITEC854 Consequence and WWMD MatrixDocument8 pagesITEC854 Consequence and WWMD Matrixfawas hamdiNo ratings yet
- Y10 05 P30 Assessment v2Document7 pagesY10 05 P30 Assessment v2ayten.sherifNo ratings yet
- Day 1 PCD CYBERSEC Cybersecurity Day 1Document186 pagesDay 1 PCD CYBERSEC Cybersecurity Day 1Gabriel OdunugaNo ratings yet
- q1 EmptechDocument91 pagesq1 EmptechKrizford CervantesNo ratings yet
- Kunal & Divya-Surana College Main Paper PresentationDocument30 pagesKunal & Divya-Surana College Main Paper PresentationKunal ChauhanNo ratings yet
- SOALDocument7 pagesSOALMahar Catur FernizaNo ratings yet
- Etech ReviewerDocument10 pagesEtech ReviewerAlysson Patoc SolarNo ratings yet
- Security Awareness TrainingDocument25 pagesSecurity Awareness TrainingDaniel IdongesitNo ratings yet
- XII Networking Notes 2021-22 PDFDocument11 pagesXII Networking Notes 2021-22 PDFVishalvsNo ratings yet
- Cyber Crime - ReportDocument21 pagesCyber Crime - ReportSayan Mitra1No ratings yet
- Lecture 7b CybercrimeDocument20 pagesLecture 7b CybercrimecrossgNo ratings yet
- Difference Between Old and New Syllabus-IPDocument5 pagesDifference Between Old and New Syllabus-IPHwnmNo ratings yet
- What Is Computer SecurityDocument5 pagesWhat Is Computer SecurityiamvishalNo ratings yet
- Cybercrime: - Kristyn Vaz and Riva TalwarDocument7 pagesCybercrime: - Kristyn Vaz and Riva TalwarMiaNo ratings yet
- PGDC Syllabus - 19102022 - 221105 - 133044Document27 pagesPGDC Syllabus - 19102022 - 221105 - 133044Arjun ManeNo ratings yet
- Week 12 ModuleDocument15 pagesWeek 12 ModuleWawi Dela RosaNo ratings yet
- Mock Test (2018-19) For Clerical To Trainee Officer and JMGS-IDocument15 pagesMock Test (2018-19) For Clerical To Trainee Officer and JMGS-IRamachandran MNo ratings yet
- Cambridge IGCSEDocument7 pagesCambridge IGCSEJessica AureliaNo ratings yet
- Cisco - Testinises.350 701.free - pdf.2021 Mar 12.by - Gary.145q.vceDocument15 pagesCisco - Testinises.350 701.free - pdf.2021 Mar 12.by - Gary.145q.vcedropboxNo ratings yet
- Cyber Security Unit 1Document20 pagesCyber Security Unit 1jai100% (1)
- ENISA Threat Landscape 2023Document161 pagesENISA Threat Landscape 2023imad bsd100% (1)
- (September-2021) New Braindump2go 312-50v11 PDF and 312-50v11 VCE Dumps (946-978)Document8 pages(September-2021) New Braindump2go 312-50v11 PDF and 312-50v11 VCE Dumps (946-978)Lê Huyền MyNo ratings yet
- ICDL IT Security 2.0 - Institute of Advanced Technology - NairobiDocument110 pagesICDL IT Security 2.0 - Institute of Advanced Technology - NairobiGraphic Design IATNo ratings yet
- Fake ScribdDocument5 pagesFake ScribdHANSNo ratings yet
- Traffic LogsDocument7 pagesTraffic LogsPkumarNo ratings yet
- Internet ThreatsDocument47 pagesInternet ThreatsAlbert FalsarioNo ratings yet
- Information Assurance and Security (COMPUTER CRIMES Module 8)Document7 pagesInformation Assurance and Security (COMPUTER CRIMES Module 8)Marneil Allen SanchezNo ratings yet