Professional Documents
Culture Documents
Ah en Trusted Wireless Coexistence 106903 en 00
Uploaded by
marcelop5Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Ah en Trusted Wireless Coexistence 106903 en 00
Uploaded by
marcelop5Copyright:
Available Formats
TRUSTED WIRELESS
COEXISTENCE
Coexistence of Trusted Wireless 2.0 and WLAN
Application note
106903_en_00 © PHOENIX CONTACT 2016-01-07
Table of contents
1 Wireless systems in parallel operation........................................................................................ 2
2 Planning coexistence.................................................................................................................. 2
2.1 Avoiding radio-frequency interference by decoupling the frequency range .................................................... 4
3 Coexistence of Trusted Wireless 2.0 and WLAN ........................................................................................ 4
3.1 Investigation into coexistence ........................................................................................................................ 5
3.2 Test set-up ..................................................................................................................................................... 5
3.3 Measurement results...................................................................................................................................... 6
3.4 Conclusion of the investigation....................................................................................................................... 8
WARNING:
This application note does not replace the device-specific documents.
Please follow the safety notes in the associated package slips and data sheets.
Make sure you always use the latest documentation.
It can be downloaded at phoenixcontact.net/products.
TRUSTED WIRELESS COEXISTENCE
1 Wireless systems in parallel operation
If wireless systems are operated in close proximity, there is a chance that they will have a negative impact on one another.
Radio-frequency interference can only occur if the following three factors apply:
– Same place
– Same time
– Same frequency
With radio-frequency interference, it can take longer to transmit a data telegram fully and correctly. This transmission time is
measured by interfaces, e.g., from the moment a sensor triggers to the time the telegram becomes available in a fieldbus.
By measuring over a long period of time, you can assess whether the radio-frequency interference is still permissible. The
tolerable transmission times depend on the application. When sending sensor measurement data, a longer transmission
time can be tolerated. However, when controlling a machine, the transmission time must be very short.
Coexistence is a state in which several wireless systems can operate without trouble despite radio-frequency in-
terference. Coexistence depends on the level of interference immunity of the wireless systems used and the fre-
quencies that they use.
Also observe the following documents on the subject of coexistence:
– IEC 62657-2: Industrial communication networks – Wireless communication networks, part 2: Coexistence
management
– VDI/VDE directive 2185: Radio based communication in industrial automation
2 Planning coexistence
The license-free, globally available 2.4 GHz ISM band has a high bandwidth and is not affected by typical industrial sources
of interference. It is therefore not just used for domestic and office applications, but also increasingly in automation technol-
ogy. Different standards, such as WLAN and Bluetooth, as well as proprietary solutions such as Trusted Wireless 2.0 use
the 2.4 GHz band.
As wireless solutions are being used more and more frequently, radio frequencies are falling into short supply, particularly in
large companies. For this reason, their use must be planned professionally. To do this, different departments have to work
together closely.
Figure 1 Wireless systems in factory automation
106903_en_00 PHOENIX CONTACT 2/7
TRUSTED WIRELESS COEXISTENCE
2.1 Avoiding radio-frequency interference by 3 Coexistence of
decoupling the frequency range
Trusted Wireless 2.0 and WLAN
The assigned frequency is dictated by the wireless technol-
ogy and its settings. Phoenix Contact has developed Trusted Wireless 2.0 tech-
nology specifically for industrial applications.
Static frequency systems have an allocated
frequency range (e.g., WLAN, channels 1 ... 13). Features
Dynamic frequency systems occupy the entire – Frequency ranges:
frequency band uniformly (e.g., Bluetooth, – 2400 MHz ... 2483.5 MHz
Trusted Wireless 2.0). – 869.4 MHz ... 869.65 MHz
– Static frequency systems can easily be decoupled from – 902 MHz ... 928 MHz
one another in that it is possible to assign different fre- – Transmission power: 0 dBm ... 20 dBm, depends on
quency ranges. the data rate, can be set via software (in Europe
– Dynamic frequency systems must not be decoupled 0 dBm ... 19 dBm)
from one another. They constantly hop between the fre- – Possible data rates:
quencies in different patterns. In the event of a collision, 16 kbps, 125 kbps, 250 kbps
transmission is repeated on another frequency. – Robust communication thanks to the frequency-hop-
– If static frequency and dynamic frequency systems are ping spread spectrum with up to 127 channels
used at the same time, a blacklist can be defined for the – Automatic and manual mechanisms for coexistence
dynamic frequency systems. The dynamic frequency with other systems transmitting in the same frequency
systems then avoid the frequencies occupied by the band
static system. – Secure data encryption and authentication
For WLAN networks with large quantities of data and high – Long range thanks to high receiver sensitivity and vari-
temporal allocation, it is advisable to avoid the 5 GHz band. able data transmission speed
– Flexible network structure with automatic connection
management
– Distributed network management
– Comprehensive diagnostics options
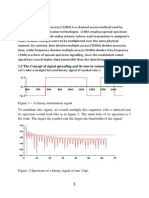
Frequency-hopping spread spectrum (FHSS) method
In the license-free 2.4 GHz frequency band, Trusted Wire-
less 2.0 uses the frequency-hopping spread spectrum
(FHSS) method. This method uses a selection of up to 127
channels from the entire spectrum of the frequency band.
The wireless module “hops” between these channels on the
basis of a pseudo-random pattern. This results in more ro-
bust and more reliable communication.
Figure 2 Radio-frequency interference
Blacklisting
Blacklisting means that certain frequencies can be hidden
selectively. This method allows you to operate several
WLAN systems in parallel with Trusted Wireless 2.0 sys-
tems without any interference or performance limitations.
106903_en_00 PHOENIX CONTACT 3/7
TRUSTED WIRELESS COEXISTENCE
3.1 Investigation into coexistence 3.2 Test set-up
In 2014, the Institut für Automation und Kommunikation Two wireless systems were operated in parallel on the
(ikaf) in Madgeburg, Germany looked at how 2.4 GHz ISM band in a hall. The institute looked at the fol-
Trusted Wireless 2.0 and WLAN affect one another. In addi- lowing:
tion, it recorded spectrograms of the frequency band as well – Influence of a WLAN system on a Trusted Wireless sys-
as histograms of the packet runtime. tem
Procedure: – Influence of a Trusted Wireless system on a WLAN sys-
1. Both wireless systems were operated individually. tem
2. The wireless systems were operated in parallel with The operating behavior was examined based on the trans-
their respective factory settings. mission times. The 95th percentile (P95) was used for the
3. The coexistence mechanisms were set in the most ef- statistical analysis of the measurement results. 95% of all
fective way possible using wireless network planning. measured values are smaller than or the same as the P95
value.
These observations were implemented both with the WLAN
system as the interferer and with the Trusted Wireless 2.0
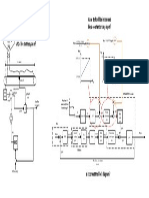
Distances (see Figure 3):
system as the interferer.
WLAN access point (AP) ... WLAN clients (Cl) 8 meters
WLAN access point (AP) ... Consumer 01 1 meter
WLAN client 01 ... Producer 3 meters
WLAN clients 02, 03, 04 (Cl) ... Consumer 01 7.8 meters
In the test set-up, the distances are small, as a set-up of this
type is most critical with respect to coexistence. The level of
performance drops quadratically with the distance.
Star Tree WLAN
Figure 3 Test set-up
106903_en_00 PHOENIX CONTACT 4/7
TRUSTED WIRELESS COEXISTENCE
3.3 Measurement results
Influence of a WLAN system on a Trusted Wireless 2.0 system
– The narrow-band input filter of the Trusted Wireless system filters the interference signal and therefore reduces radio-
frequency interference.
– The transmission time remains constant.
– The Trusted Wireless network is not affected by WLAN.
Influence of a WLAN system on a Trusted Wireless 2.0 system Transmission time [ms]
Test system Interferer (WLAN) Mini- Maxi- P95
(Trusted Wireless) mum mum
Without interferer
61.6 91.5 76.3
Number of packets
Transmission time [ms]
With interferer, without blacklisting
61.6 92.3 76.4
Number of packets
Transmission time [ms]
With interferer, with blacklisting
61.6 92.3 76.3
Number of packets
Transmission time [ms]
106903_en_00 PHOENIX CONTACT 5/7
TRUSTED WIRELESS COEXISTENCE
Influence of a Trusted Wireless 2.0 system on a WLAN system
– The wide-band WLAN receiver processes the energy from the Trusted Wireless interferer.
– Without blacklisting, the interference is clearly noticeable.
– If blacklisting is active, the transmission time remains more or less constant.
– Frequency planning with blacklisting prevents interference from Trusted Wireless 2.0.
Influence of a Trusted Wireless 2.0 system on a WLAN system Transmission time [ms]
Test system Interferer Mini- Maxi- P95
(WLAN) (Trusted Wireless) mum mum
Without interferer
0.5 9.7 0.9
Number of packets
Transmission time [ms]
With interferer, without blacklisting
0.5 16.1 2.8
Number of packets
Transmission time [ms]
With interferer, with blacklisting
0.5 8.9 1.2
Number of packets
Transmission time [ms]
106903_en_00 PHOENIX CONTACT 6/7
TRUSTED WIRELESS COEXISTENCE
3.4 Conclusion of the investigation
The measurement results show that it is possible to operate
different wireless systems on the 2.4 GHz band in parallel
without any problems. The narrow-band radio technology
Trusted Wireless 2.0 is highly insensitive to interference. It
is not affected by WLAN.
Wireless network planning in line with IEC 62657-2 and VDI/
VDE directive 2185 prevents other wireless systems from
affecting the WLAN system. If blacklisting is activated in the
Trusted Wireless devices, the wide-band WLAN system is
also not affected.
If you plan the wireless network accordingly and
use the coexistence mechanisms available, you
can be sure that different wireless systems will be
able to operate in harmony.
You can find more information on the ZVEI
homepage by searching for “wireless system
coexistence in automation technology”.
106903_en_00 PHOENIX CONTACT GmbH & Co. KG • Flachsmarktstraße 8 • 32825 Blomberg • Germany 7/7
phoenixcontact.com
You might also like
- Rockwell Software Rslogix5 Plc-5 ProgrammingDocument19 pagesRockwell Software Rslogix5 Plc-5 ProgrammingJesus GarciaNo ratings yet
- Bill of Materials and Cost Estimates Description QTY Unit Unit Cost Total Cost Site Works PHP 17,854.77Document8 pagesBill of Materials and Cost Estimates Description QTY Unit Unit Cost Total Cost Site Works PHP 17,854.77RavNo ratings yet
- Digital Strategy Executive Summary VisualDocument3 pagesDigital Strategy Executive Summary VisualfahdlyNo ratings yet
- Advances in Analog and RF IC Design for Wireless Communication SystemsFrom EverandAdvances in Analog and RF IC Design for Wireless Communication SystemsGabriele ManganaroRating: 1 out of 5 stars1/5 (1)
- Wireless SecurityDocument15 pagesWireless SecurityJagruti BorasteNo ratings yet
- It Era Final ModuleDocument103 pagesIt Era Final ModuleLeonso Visto JrNo ratings yet
- Techniques - For - Precise - Interference Measurements in The Field - AgilentDocument14 pagesTechniques - For - Precise - Interference Measurements in The Field - AgilentPedro PrietoNo ratings yet
- WSN Unit 2Document14 pagesWSN Unit 2Sandeep Kumar MekapothulaNo ratings yet
- Page - 1Document24 pagesPage - 1karthik_ktnkNo ratings yet
- Patton Aukerman ShorterDocument7 pagesPatton Aukerman ShorterHermandeep KaurNo ratings yet
- CIR 209 (Lecture 9) - Wireless Network Design & ImplementationDocument15 pagesCIR 209 (Lecture 9) - Wireless Network Design & Implementationdancanongori9No ratings yet
- Sensus+White+Paper Mesh+vs+PTMP+NetworksDocument8 pagesSensus+White+Paper Mesh+vs+PTMP+Networksharoldc4No ratings yet
- Reliable Smart Multihop Wireless Sensor Networks: Communication and NetworkingDocument12 pagesReliable Smart Multihop Wireless Sensor Networks: Communication and Networkingajay 235No ratings yet
- SIBA Wireless and Mobile Communication AssignmentDocument12 pagesSIBA Wireless and Mobile Communication AssignmentShahzad Raza JalbaniNo ratings yet
- Mobile Wi Max TestingDocument2 pagesMobile Wi Max Testingbulli babuNo ratings yet
- Chapter 3Document26 pagesChapter 3tzsami591No ratings yet
- Frequency Hopping Spread Spectrum (FHSS) vs. Direct Sequence Spread Spectrum (DSSS) by SorinM - SCHWARTZDocument16 pagesFrequency Hopping Spread Spectrum (FHSS) vs. Direct Sequence Spread Spectrum (DSSS) by SorinM - SCHWARTZRakesh RtNo ratings yet
- Explanation: Frequency Hopping Spread Spectrum (FHSS) Systems Use Frequency Diversity (ChangingDocument28 pagesExplanation: Frequency Hopping Spread Spectrum (FHSS) Systems Use Frequency Diversity (Changingyerima1No ratings yet
- WMN Prilim Sample paper 1Document11 pagesWMN Prilim Sample paper 1baxadi8221No ratings yet
- A Survey On Cross-Layer Optimization in Wireless Networks: Bindeshwar Singh Kushwaha, Pramod Kumar MishraDocument9 pagesA Survey On Cross-Layer Optimization in Wireless Networks: Bindeshwar Singh Kushwaha, Pramod Kumar MishraBindeshwarNo ratings yet
- Wireless Security An OverviewDocument16 pagesWireless Security An OverviewMervis EncelanNo ratings yet
- Wireless Lans and Ieee 802.11 Mac: Cse 6590 Winter 2012Document59 pagesWireless Lans and Ieee 802.11 Mac: Cse 6590 Winter 2012nksarathyNo ratings yet
- E3sconf Ses18 03013Document4 pagesE3sconf Ses18 03013feibulaliNo ratings yet
- 5990 9074en PDFDocument30 pages5990 9074en PDFCarlos Alberto Ortiz MoraNo ratings yet
- ""Seminar On Wi-Fi Communication"": Department of Electronics EngineeringDocument14 pages""Seminar On Wi-Fi Communication"": Department of Electronics EngineeringViral111No ratings yet
- Border Security Using Wireless Integrated Network Sensors (Wins)Document10 pagesBorder Security Using Wireless Integrated Network Sensors (Wins)Vijaykumar BonagiriNo ratings yet
- EC8004-Wireless Networks-NotesDocument364 pagesEC8004-Wireless Networks-NotesGtecEceNo ratings yet
- Entirety Brazil SEI ANATEL 6600480 ActDocument5 pagesEntirety Brazil SEI ANATEL 6600480 ActLuiz WinterNo ratings yet
- Introduction To Wireless Systems-CH 3Document99 pagesIntroduction To Wireless Systems-CH 3George maksoudNo ratings yet
- Lab C4 Wireless WorksheetDocument2 pagesLab C4 Wireless WorksheetCameron HulseNo ratings yet
- A Study of RF Link and Coverage in ZigBee PDFDocument6 pagesA Study of RF Link and Coverage in ZigBee PDFWided AhmadiNo ratings yet
- CDMA and Spread Spectrum Techniques ExplainedDocument33 pagesCDMA and Spread Spectrum Techniques ExplainedAnkita SharmaNo ratings yet
- EC8004-Wireless Networks-NotesDocument100 pagesEC8004-Wireless Networks-NotesGtecEceNo ratings yet
- WINS Node Architecture for Border SecurityDocument35 pagesWINS Node Architecture for Border Securitydugulamsushma8951No ratings yet
- Cognitive Wireless Sensor Networks: Emerging Topics and Recent ChallengesDocument4 pagesCognitive Wireless Sensor Networks: Emerging Topics and Recent ChallengesTenda TiyNo ratings yet
- A Study of Wireless Networks: Wlans, Wpans, Wmans, and Wwans With ComparisonDocument4 pagesA Study of Wireless Networks: Wlans, Wpans, Wmans, and Wwans With ComparisonWissem HammoudaNo ratings yet
- Chapter 1Document36 pagesChapter 1LeowNo ratings yet
- UNIT I NotesDocument20 pagesUNIT I Notes6041 Gowardhanan100% (1)
- Ref 92-2015Document16 pagesRef 92-2015Long HoangNo ratings yet
- Alcatel-Lucent Enterprise Omniaccess 310 Series Access PointsDocument5 pagesAlcatel-Lucent Enterprise Omniaccess 310 Series Access PointsJose Miguel GarcíaNo ratings yet
- FreeLinc NFMI Technology for Short Range CommunicationDocument5 pagesFreeLinc NFMI Technology for Short Range CommunicationAmethist ChanNo ratings yet
- MC Answer Key 1Document47 pagesMC Answer Key 1Neeraj SinghNo ratings yet
- Computer Networking Fundamentals Chapter 4Document95 pagesComputer Networking Fundamentals Chapter 4wfidayuNo ratings yet
- What Does Extended Service Set MeanDocument7 pagesWhat Does Extended Service Set MeanIT Hub SLNo ratings yet
- WC 8Document1 pageWC 8api-3761679No ratings yet
- 128 1498039059 - 21-06-2017 PDFDocument4 pages128 1498039059 - 21-06-2017 PDFEditor IJRITCCNo ratings yet
- Schematic of OFDM SystemDocument13 pagesSchematic of OFDM SystemakhilaNo ratings yet
- Wireless Sensor Network GuideDocument7 pagesWireless Sensor Network GuideMaleeha SabirNo ratings yet
- On Covert Acoustical Mesh Networks in AirDocument10 pagesOn Covert Acoustical Mesh Networks in AirKLKTZNo ratings yet
- Fhss DsssDocument5 pagesFhss DsssAhmed IbraheemNo ratings yet
- Encoding and v.24Document6 pagesEncoding and v.24gangsterworld000No ratings yet
- 4 WirelessDocument11 pages4 WirelessChis LebroNo ratings yet
- WCMC - CH - 3Document42 pagesWCMC - CH - 3birukNo ratings yet
- 1 Network Systems and New TechDocument46 pages1 Network Systems and New TechAbegail QuindozaNo ratings yet
- I. About DOCSIS 3.0: 1. Better SecurityDocument5 pagesI. About DOCSIS 3.0: 1. Better SecurityHuy BùiNo ratings yet
- The Wireless JungleDocument13 pagesThe Wireless Junglemzungo1972No ratings yet
- an9804Document8 pagesan9804sumitstop2No ratings yet
- Jagadeeshchandra R.BDocument192 pagesJagadeeshchandra R.BShivaram NagarajanNo ratings yet
- Ijaiem 2013 04 27 078Document7 pagesIjaiem 2013 04 27 078International Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Common Telecommunications DevicesDocument5 pagesCommon Telecommunications DevicesHeidi Joy JameroNo ratings yet
- Wireless Macs GummallaDocument14 pagesWireless Macs GummallaGK SrinivasaNo ratings yet
- 3G Training For FM by Ahmed Abd El MageeddddDocument103 pages3G Training For FM by Ahmed Abd El MageeddddAhmed AliNo ratings yet
- Frequency Hopping Vs Direct SequenceDocument17 pagesFrequency Hopping Vs Direct SequenceAsaelCocomNo ratings yet
- Refer 1Document4 pagesRefer 1Pandimadevi GanesanNo ratings yet
- Equalizer 4.0 PSS English 2935006221Document2 pagesEqualizer 4.0 PSS English 2935006221marcelop5No ratings yet
- CR200 Renewable 331043E LowresDocument2 pagesCR200 Renewable 331043E Lowresmarcelop5No ratings yet
- Rad 900 IfsDocument22 pagesRad 900 Ifsmarcelop5No ratings yet
- Act 7-5larsDocument1 pageAct 7-5larsmarcelop5No ratings yet
- Troubleshooting Profibus Pa - A Practical Example: © Siemens AG 2008Document30 pagesTroubleshooting Profibus Pa - A Practical Example: © Siemens AG 2008marcelop5No ratings yet
- Probe control system upgradeDocument6 pagesProbe control system upgrademarcelop5No ratings yet
- Adding The GW PL ETH/UNI-BUS To PC WORX As A Profinet I/ODocument4 pagesAdding The GW PL ETH/UNI-BUS To PC WORX As A Profinet I/Omarcelop5No ratings yet
- A and B Should Be Introduced Like A Constant or Step Input? How Could I Integrate The Rotary Feeder Adding A New VFD Drive To The System?Document1 pageA and B Should Be Introduced Like A Constant or Step Input? How Could I Integrate The Rotary Feeder Adding A New VFD Drive To The System?marcelo penafielNo ratings yet
- STEP7 ErrorCode EnglDocument31 pagesSTEP7 ErrorCode EnglVoicu StaneseNo ratings yet
- Analog ModuleDocument15 pagesAnalog ModuleBin MulyadinNo ratings yet
- Frequency Transducer - MCR-F-UI-DC - 2814605: Key Commercial DataDocument7 pagesFrequency Transducer - MCR-F-UI-DC - 2814605: Key Commercial Datamarcelop5No ratings yet
- Data Sheet 6ES7331-1KF02-0AB0: Input CurrentDocument5 pagesData Sheet 6ES7331-1KF02-0AB0: Input CurrentRodrigo DonizeteNo ratings yet
- Data Sheet 6GK7342-5DA03-0XE0: Transmission RateDocument4 pagesData Sheet 6GK7342-5DA03-0XE0: Transmission Ratemarcelop5No ratings yet
- Data Sheet 6ES7315-2EH14-0AB0: General InformationDocument13 pagesData Sheet 6ES7315-2EH14-0AB0: General Informationmarcelop5No ratings yet
- Data Sheet 6GK7343-1CX10-0XE0: Transmission RateDocument5 pagesData Sheet 6GK7343-1CX10-0XE0: Transmission Ratemarcelop5No ratings yet
- KepSever WinCC Connectivity Guide PDFDocument17 pagesKepSever WinCC Connectivity Guide PDFJess GlezNo ratings yet
- ASEE 2012 Twin Tank Paper FinalDocument16 pagesASEE 2012 Twin Tank Paper Finalmarcelop5No ratings yet
- STEP7 ErrorCode EnglDocument31 pagesSTEP7 ErrorCode EnglVoicu StaneseNo ratings yet
- Howtoretrievea Logix 5000 PLCprogramDocument8 pagesHowtoretrievea Logix 5000 PLCprogrammarcelop5No ratings yet
- Analog ModuleDocument15 pagesAnalog ModuleBin MulyadinNo ratings yet
- Belt ScalesDocument14 pagesBelt Scalesmarcelop5No ratings yet
- PasterDocument9 pagesPastermarcelop5No ratings yet
- Altivar 31Document96 pagesAltivar 31Leyre Marcilla MartínezNo ratings yet
- Inst Guide Profibus PADocument55 pagesInst Guide Profibus PAMpho MathubaNo ratings yet
- Celdas de CargaDocument3 pagesCeldas de Cargamarcelop5No ratings yet
- Selecting ProxDocument6 pagesSelecting Proxmarcelop5No ratings yet
- Electronics Engg - SEDocument48 pagesElectronics Engg - SEnirajthakkarNo ratings yet
- Computer Science: Jump To Navigationjump To SearchDocument6 pagesComputer Science: Jump To Navigationjump To SearchLawrence DecanoNo ratings yet
- Holiday HomeworkDocument7 pagesHoliday Homeworkapi-236861282No ratings yet
- Ch4 OS BasicsDocument41 pagesCh4 OS Basicspimat40375No ratings yet
- Scc-1 Smartcraft Connect Gateway Installation Manual: Components in KitDocument23 pagesScc-1 Smartcraft Connect Gateway Installation Manual: Components in KitJosh WolfeNo ratings yet
- Challenge1 50Document7 pagesChallenge1 50qweertyNo ratings yet
- Shivaji Maharaj's Respect for WomenDocument12 pagesShivaji Maharaj's Respect for WomenCristi RonnieNo ratings yet
- ACC200 Tuturial Sem 3 2019 PDFDocument74 pagesACC200 Tuturial Sem 3 2019 PDFanon_255678422100% (1)
- Streaming TV Channels & Radio Stations from Around the WorldDocument16 pagesStreaming TV Channels & Radio Stations from Around the WorldTimothy BarnesNo ratings yet
- Evaluating The Thermal Stability of Manual Transmission Lubricants in A Cyclic Durability TestDocument19 pagesEvaluating The Thermal Stability of Manual Transmission Lubricants in A Cyclic Durability TestsamehNo ratings yet
- Board Resolution No 1 For ECT 2011Document21 pagesBoard Resolution No 1 For ECT 2011Reygie Bulanon MoconNo ratings yet
- Promis User ManualDocument56 pagesPromis User ManualErnest V SNo ratings yet
- Phoenix SIL2 RelayDocument5 pagesPhoenix SIL2 Relaysteam100deg1658No ratings yet
- Kongsberg PulSAR ApplicationsDocument2 pagesKongsberg PulSAR ApplicationsReynaldo PulidoNo ratings yet
- 3ds Max TipsDocument6 pages3ds Max Tipsez1010100% (1)
- MIT2 14S14 Prob Archive PDFDocument674 pagesMIT2 14S14 Prob Archive PDFKamal PatelNo ratings yet
- Online MetroCard Recharge - TutorialsDuniyaDocument36 pagesOnline MetroCard Recharge - TutorialsDuniyaGurkirat SinghNo ratings yet
- Whats New NanoCADDocument19 pagesWhats New NanoCADHaytham ZaghloulNo ratings yet
- 7.2.3.1.4 Block Waiting Time: ETSI TS 102 221 V17.1.0 (2022-02) 44Document3 pages7.2.3.1.4 Block Waiting Time: ETSI TS 102 221 V17.1.0 (2022-02) 44sdfksd iroroooNo ratings yet
- Safety Manual Sec B1 BBSMDocument2 pagesSafety Manual Sec B1 BBSMTanko RichardsNo ratings yet
- Ielts Reading Test 10 - PassagesDocument9 pagesIelts Reading Test 10 - PassagesĐinh Quốc LiêmNo ratings yet
- Mobile Computing Course PlanDocument7 pagesMobile Computing Course PlanPragya ChakshooNo ratings yet
- The Importance of Additive ManufacturingDocument9 pagesThe Importance of Additive ManufacturingraviNo ratings yet
- 20 G 1 Anc 140 Aa 0 NNNNNDocument12 pages20 G 1 Anc 140 Aa 0 NNNNNWriterNo ratings yet
- Checklist - SRS Review.1.0Document5 pagesChecklist - SRS Review.1.0Trung Thành NguyễnNo ratings yet
- Gate Controller Manual: AAD03010 Frequency Control SystemDocument17 pagesGate Controller Manual: AAD03010 Frequency Control SystemKen LeeNo ratings yet
- Connecting To Linux Using PuttyDocument9 pagesConnecting To Linux Using Puttydilip4682794No ratings yet