Professional Documents
Culture Documents
Nmap Commands
Nmap Commands
Uploaded by
Ronak Makwana0 ratings0% found this document useful (0 votes)
7 views2 pagesThe document provides instructions for using Nmap to perform various discovery and bypass scans against IP addresses, including port scanning, OS detection, service version detection, and techniques for bypassing firewalls and IDS systems such as packet fragmentation and source address manipulation. It also describes using the Nmap Scripting Engine and Zenmap for additional scanning functionality and creating a network diagram.
Original Description:
Original Title
nmap commands
Copyright
© © All Rights Reserved
Available Formats
TXT, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentThe document provides instructions for using Nmap to perform various discovery and bypass scans against IP addresses, including port scanning, OS detection, service version detection, and techniques for bypassing firewalls and IDS systems such as packet fragmentation and source address manipulation. It also describes using the Nmap Scripting Engine and Zenmap for additional scanning functionality and creating a network diagram.
Copyright:
© All Rights Reserved
Available Formats
Download as TXT, PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
7 views2 pagesNmap Commands
Nmap Commands
Uploaded by
Ronak MakwanaThe document provides instructions for using Nmap to perform various discovery and bypass scans against IP addresses, including port scanning, OS detection, service version detection, and techniques for bypassing firewalls and IDS systems such as packet fragmentation and source address manipulation. It also describes using the Nmap Scripting Engine and Zenmap for additional scanning functionality and creating a network diagram.
Copyright:
© All Rights Reserved
Available Formats
Download as TXT, PDF, TXT or read online from Scribd
You are on page 1of 2
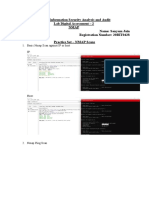
(1)itmbu.ac.in : 108.167.146.
199
(2)scanme.org : 45.33.32.156
Host Discovery:
ARP Ping Scan : nmap -sP -PR 108.167.146.199
UDP Ping Scan : nmap -sP -PU 108.167.146.199
ICMP Ping Scan(Echo) : nmap -sP -PE 108.167.146.199
ICMP Ping Scan(Timestamp) : nmap -sP -PP 108.167.146.199
ICMP Ping Scan(Address mask) : nmap -sP -PM 108.167.146.199
TCP Ping Scan(SYN) : nmap -sP -PS 108.167.146.199
TCP Ping Scan(ACK) : nmap -sP -PA 108.167.146.199
IP Protocol Scan : nmap -sP -PO 108.167.146.199
Port and Service Discovery:
TCP connect/Full Open scan : nmap -sT 108.167.146.199
Stealth Scan/TCP Half Open scan : nmap -sS 108.167.146.199
Xmas Scan : nmap -sX 108.167.146.199
TCP Maimon scan : nmap -sM 108.167.146.199
ACK Flag prob scan : nmap -sA 108.167.146.199
UDP Scan : nmap -sU 108.167.146.199
Service Version Discovery Scan : nmap -sV 108.167.146.199
Scan whole subnet using Aggressive Scan : nmap -A 108.167.146.199
OS Discovery : nmap -sV -O 108.167.146.199
TTL & Window Size :
Nmap Script Engine (NSE) : nmap -sC 108.167.146.199
IDS/Firewall Bypass:
Scan Beyond IDS/Firewall using various Evason Techniques:
1. Packet fragmentation : nmap -f 108.167.146.199
2. source port manipulation : nmap -g 80 108.167.146.199
3. source address manipulation : nmap -S 108.167.146.199
4. IP Adress Decoy : nmap -D RND:10 108.167.146.199
nmap -D 108.167.146.199,108.167.146.200,108.167.146.198
Scan Beyond IDS/Firewall using Nmap by creating custom packets
1. creating custom packets by appending custom binary data:
nmap 108.167.146.199 --data 0xdeadbeef
2. creating custom packets by appending custom strings:
nmap 108.167.146.199 --data-string "D0nt G1v3 UP"
3. creating custom packets by appending random data:
nmap 108.167.146.199 --data-length 4
Network Diagram using Network topology Mapper
using zenmap
You might also like
- Wireless and Mobile Hacking and Sniffing TechniquesFrom EverandWireless and Mobile Hacking and Sniffing TechniquesNo ratings yet
- Nmap Cheat SheetDocument16 pagesNmap Cheat SheetHarshitaBhatiaNo ratings yet
- NMap - Network MappingDocument35 pagesNMap - Network MappingFaisal AR100% (4)
- Nmap Cheat SheetDocument9 pagesNmap Cheat SheetDraKon GamingNo ratings yet
- Cyber Security For Beginners PDFDocument28 pagesCyber Security For Beginners PDFVenkat KarthikNo ratings yet
- Nmap Cheet Sheet PDFDocument4 pagesNmap Cheet Sheet PDFnomo100% (1)
- Ana Chanaba Robert HuyloDocument18 pagesAna Chanaba Robert HuyloAkshay ChoudharyNo ratings yet
- Nmap For Packet TracingDocument19 pagesNmap For Packet TracingFaizan Ul HaqNo ratings yet
- Nmap:The Network MapperDocument13 pagesNmap:The Network MapperNahid MajumderNo ratings yet
- NMAP Command Guide SheetDocument5 pagesNMAP Command Guide SheetRafoo MG100% (1)
- SQL Injection Attack DemonstrationDocument9 pagesSQL Injection Attack DemonstrationRonak MakwanaNo ratings yet
- Complete Guide To NMAPDocument7 pagesComplete Guide To NMAPPulkit R AggarwalNo ratings yet
- ELearnSecurity ECPPT Notes ExamDocument157 pagesELearnSecurity ECPPT Notes ExamAngel CabralesNo ratings yet
- Nmap Cheat Sheet: Target Specification Scan TechniquesDocument6 pagesNmap Cheat Sheet: Target Specification Scan TechniquesAmeur HedNo ratings yet
- Packet AnalyzerDocument9 pagesPacket AnalyzerHarinisanthoshNo ratings yet
- Cyber Security Lab ManualDocument19 pagesCyber Security Lab ManualadiradityasinghNo ratings yet
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkFrom EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo ratings yet
- Nmap CommandsDocument21 pagesNmap Commandsramya.gNo ratings yet
- Lab Experiment #08 - Network & Host Detection ScansDocument3 pagesLab Experiment #08 - Network & Host Detection ScansAnoop DasNo ratings yet
- CEH CommandsDocument2 pagesCEH CommandsHelen Tseggai100% (1)
- Wireless and Mobile Network Security 9780070700246 0070700249 - Compress PDFDocument244 pagesWireless and Mobile Network Security 9780070700246 0070700249 - Compress PDFRonak MakwanaNo ratings yet
- Comptia Netplusn10008 5 1 Information - Gathering - CommandsDocument1 pageComptia Netplusn10008 5 1 Information - Gathering - CommandsYassine BenzaâzaâNo ratings yet
- Experiment - 1: #1: Scan A Single Host or An Ip Address (Ipv4)Document17 pagesExperiment - 1: #1: Scan A Single Host or An Ip Address (Ipv4)Hardik MehtaNo ratings yet
- ScanningDocument15 pagesScanningtestetesteciteNo ratings yet
- Module-3 ScanningDocument99 pagesModule-3 Scanningposici1542No ratings yet
- DJF EnumerationDocument2 pagesDJF EnumerationElyar SafarovNo ratings yet
- The New Nmap: Gordon "Fyodor" LyonDocument32 pagesThe New Nmap: Gordon "Fyodor" LyonGiselle GirondinNo ratings yet
- NmapDocument5 pagesNmapPriyanshu UpadhyayNo ratings yet
- FortinetDocument3 pagesFortinetAbhishek gargNo ratings yet
- Nmap KomandeDocument1 pageNmap KomandeEmir HasanbegovićNo ratings yet
- Nmap Cheat SheetDocument8 pagesNmap Cheat SheetPauloNo ratings yet
- Nmap Commands CollectionDocument7 pagesNmap Commands Collectionhammad.khan.4440kNo ratings yet
- Nmap CommandsDocument2 pagesNmap Commandsaniket kasturiNo ratings yet
- Nmap Cheat SheetDocument8 pagesNmap Cheat Sheetkalesh shaikNo ratings yet
- Switch Example Description: Target SpecificationDocument3 pagesSwitch Example Description: Target SpecificationKD TricksNo ratings yet
- 20bit0428 VL2022230101456 Ast02Document19 pages20bit0428 VL2022230101456 Ast02Kumar RajaNo ratings yet
- Lab Hacking1 10Document21 pagesLab Hacking1 10tvm1318022002No ratings yet
- Nmap Cheat SheetDocument43 pagesNmap Cheat SheetsolicitadasenhaNo ratings yet
- 1: Scan A Single Host or An Ip Address (Ipv4) : Nmap 192.168.1.1 192.168.1.2 192.168.1.3 Nmap 192.168.1.1,2,3Document4 pages1: Scan A Single Host or An Ip Address (Ipv4) : Nmap 192.168.1.1 192.168.1.2 192.168.1.3 Nmap 192.168.1.1,2,3fallliNo ratings yet
- Port Scanning Technique OSCPDocument17 pagesPort Scanning Technique OSCPLieu Dinh PhungNo ratings yet
- Nmap Cheat Sheet 2023Document11 pagesNmap Cheat Sheet 2023ketix20201No ratings yet
- NpingDocument29 pagesNpingJonathan ThompsonNo ratings yet
- 20BDS0318 Da4 ISM (Nmap)Document12 pages20BDS0318 Da4 ISM (Nmap)Shivam UpadhyayNo ratings yet
- Da 02Document18 pagesDa 02Kumar RajaNo ratings yet
- Ethical HackingDocument3 pagesEthical HackingSathish kumarNo ratings yet
- Nmap CommandDocument11 pagesNmap Commandiffishah170No ratings yet
- 6 T 7 y 7 y 7 y 8Document3 pages6 T 7 y 7 y 7 y 8govebNo ratings yet
- CS - Pr2Document24 pagesCS - Pr2muskanbandariaNo ratings yet
- TCP Port Scan With NmapDocument2 pagesTCP Port Scan With NmapMario Luis LOPEZNo ratings yet
- CIT 480: Securing Computer Systems Lab #7: Network Scanning NameDocument4 pagesCIT 480: Securing Computer Systems Lab #7: Network Scanning NameManzu PokharelNo ratings yet
- NmapcommandsDocument10 pagesNmapcommandsTaseenNo ratings yet
- Nmap Cheat SheetDocument9 pagesNmap Cheat Sheetrivigan888No ratings yet
- Smartdefend: Intelligent Attack Detection and ProtectionDocument18 pagesSmartdefend: Intelligent Attack Detection and ProtectionChinmay GhateNo ratings yet
- TP 1 (Part 2) NMAP Scan Using SnortDocument10 pagesTP 1 (Part 2) NMAP Scan Using Snortismail elmaghNo ratings yet
- Config VPNDocument28 pagesConfig VPNAureo Miraval BravoNo ratings yet
- Fire Up Cpan On UbuntuDocument17 pagesFire Up Cpan On UbuntuHarguilar NhangaNo ratings yet
- 9 Network Discovery and Network SecurityDocument24 pages9 Network Discovery and Network SecurityNaveen KumarNo ratings yet
- By Gopalsamy RajendranDocument19 pagesBy Gopalsamy RajendranrmknecNo ratings yet
- GSM Architecture 1Document8 pagesGSM Architecture 1Ronak MakwanaNo ratings yet
- Heterogeneous Network PDFDocument3 pagesHeterogeneous Network PDFRonak MakwanaNo ratings yet