Professional Documents
Culture Documents
Windows Matrix
Uploaded by
folalikCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Windows Matrix
Uploaded by
folalikCopyright:
Available Formats
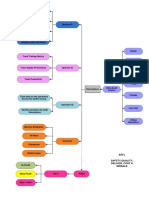
Domain Controller Authentication
Password Filter DLL
Reversible Encryption
Multi-Factor Authentication
T1112 - Modify Registry Hybrid Identity
Binary Padding T1556 - Modify Authentication Process
Software Packing Invalid Code Signature
Steganography Right-to-Left Override
Compile After Delivery Rename System Utilities
Indicator Removal from Tools Masquerade Task or Service
HTML Smuggling Match Legitimate Name or Location
Dynamic API Resolution Double File Extension
Stripped Payloads T1036 - Masquerading
Embedded Payloads T1202 - Indirect Command Execution
T1027 - Obfuscated Files or Information Clear Windows Event Logs
System Firmware Clear Command History
Component Firmware File Deletion
Bootkit Network Share Connection Removal
T1542 - Pre-OS Boot Timestomp
Dynamic-link Library Injection Clear Network Connection History and Configurations
Portable Executable Injection Clear Mailbox Data
Thread Execution Hijacking Clear Persistence
Asynchronous Procedure Call T1070 - Indicator Removal
Thread Local Storage Disable or Modify Tools
Extra Window Memory Injection Disable Windows Event Logging
Process Hollowing Impair Command History Logging
Process Doppelgänging Disable or Modify System Firewall
ListPlanting Indicator Blocking
T1055 - Process Injection Safe Mode Boot
T1620 - Reflective Code Loading Downgrade Attack
T1207 - Rogue Domain Controller T1562 - Impair Defenses
T1014 - Rootkit DLL Search Order Hijacking
Code Signing DLL Side-Loading
SIP and Trust Provider Hijacking Executable Installer File Permissions Weakness
Install Root Certificate Path Interception by PATH Environment Variable
Mark-of-the-Web Bypass Path Interception by Search Order Hijacking
Code Signing Policy Modification Path Interception by Unquoted Path
T1553 - Subvert Trust Controls Services File Permissions Weakness
Compiled HTML File Services Registry Permissions Weakness
@hackinarticles
Control Panel COR_PROFILER
CMSTP KernelCallbackTable
https://github.com/Ignitetechnologies
InstallUtil T1574 - Hijack Execution Flow
Mshta Hidden Files and Directories
https://in.linkedin.com/company/hackingarticles
Msiexec Hidden Users
Odbcconf Hidden Window
Regsvcs/Regasm NTFS File Attributes
Regsvr32 Hidden File System
Rundll32 Run Virtual Instance
Domain Controller Authentication
Verclsid VBA Stomping
Password Filter DLL
Mavinject Email Hiding Rules
Reversible Encryption
MMC Process Argument Spoofing
Multi-Factor Authentication
T1218 - System Binary Proxy Execution T1564 - Hide Artifacts
Hybrid Identity
PubPrn Windows File and Directory Permissions Modification
T1556 - Modify Authentication Process
T1216 - System Script Proxy Execution T1222 - File and Directory Permissions Modification
Keylogging
T1221 - Template Injection T1211 - Exploitation for Defense Evasion
T1111 - Multi-Factor Authentication Interception GUI Input Capture
Port Knocking Environmental Keying
T1621 - Multi-Factor Authentication Request Generation Web Portal Capture
Socket Filters T1480 - Execution Guardrails
T1040 - Network Sniffing Credential API Hooking
T1205 - Traffic Signaling Group Policy Modification
LSASS Memory T1056 - Input Capture
MSBuild Domain Trust Modification
Security Account Manager Web Cookies
T1127 - Trusted Developer Utilities Proxy Execution T1484 - Domain Policy Modification
NTDS SAML Tokens
Pass the Hash T1006 - Direct Volume Access
LSA Secrets T1606 - Forge Web Credentials
Pass the Ticket T1140 - Deobfuscate/Decode Files or Information
Cached Domain Credentials T1187 - Forced Authentication
T1550 - Use Alternate Authentication Material T1622 - Debugger Evasion
DCSync T1212 - Exploitation for Credential Access
Default Accounts T1197 - BITS Jobs
T1003 - OS Credential Dumping Credentials from Web Browsers
Domain Accounts Token Impersonation/Theft
T1649 - Steal or Forge Authentication Certificates Windows Credential Manager
Local Accounts Create Process with Token
Golden Ticket Password Managers
T1078 - Valid Accounts Make and Impersonate Token
Silver Ticket T1555 - Credentials from Password Stores
System Checks Parent PID Spoofing
Kerberoasting Password Guessing
User Activity Based Checks SID-History Injection
AS-REP Roasting Password Cracking
Time Based Evasion T1134 - Access Token Manipulation
T1558 - Steal or Forge Kerberos Tickets Password Spraying
T1497 - Virtualization/Sandbox Evasion Bypass User Account Control
T1539 - Steal Web Session Cookie Credential Stuffing
T1220 - XSL Script Processing T1548 - Abuse Elevation Control Mechanism
Credentials In Files T1110 - Brute Force
Defense Evasion
Credentials in Registry LLMNR/NBT-NS Poisoning and SMB Relay
Private Keys ARP Cache Poisoning
Change Default File Association
Group Policy Preferences DHCP Spoofing
Screensaver
T1552 - Unsecured Credentials T1157 - Adversary-in-the-Middle
Windows Management Instrumentation Event Subscription
Credential Access Netsh Helper DLL
Accessibility Features
AppCert DLLs
AppInit DLLs T1611 - Escape to Host
Application Shimming Default Accounts
Image File Execution Options Injection Domain Accounts
PowerShell Profile Local Accounts
T1057 - Process Discovery Local Groups Component Object Model Hijacking T1078 - Valid Accounts
T1012 - Query Registry Domain Groups Installer Packages Group Policy Modification
T1018 - Remote System Discovery T1069 - Permission Groups Discovery T1546 - Event Triggered Execution Domain Trust Modification
Security Software Discovery T1120 - Peripheral Device Discovery T1068 - Exploitation for Privilege Escalation T1484 - Domain Policy Modification
T1518 - Software Discovery T1201 - Password Policy Discovery DLL Search Order Hijacking Windows Service
T1082 - System Information Discovery T1040 - Network Sniffing DLL Side-Loading T1543 - Create or Modify System Process
System Language Discovery T1135 - Network Share Discovery Executable Installer File Permissions Weakness Logon Script (Windows)
T1614 - System Location Discovery T1046 - Network Service Discovery Path Interception by PATH Environment Variable Network Logon Script
Internet Connection Discovery T1615 - Group Policy Discovery Path Interception by Search Order Hijacking T1037 - Boot or Logon Initialization Scripts
T1016 - System Network Configuration Discovery T1083 - File and Directory Discovery Path Interception by Unquoted Path Registry Run Keys / Startup Folder
T1049 - System Network Connections Discovery T1482 - Domain Trust Discovery Services File Permissions Weakness Authentication Package
T1033 - System Owner/User Discovery T1622 - Debugger Evasion Services Registry Permissions Weakness Time Providers
T1007 - System Service Discovery T1217 - Browser Bookmark Discovery COR_PROFILER Winlogon Helper DLL
T1124 - System Time Discovery T1010 - Application Window Discovery KernelCallbackTable Security Support Provider
System Checks Local Account T1574 - Hijack Execution Flow LSASS Driver
User Activity Based Checks Domain Account Dynamic-link Library Injection Shortcut Modification
Time Based Evasion Email Account Portable Executable Injection Port Monitors
T1497 - Virtualization/Sandbox Evasion T1087 - Account Discovery Thread Execution Hijacking Print Processors
Discovery Asynchronous Procedure Call Active Setup
Thread Local Storage T1547 - Boot or Logon Autostart Execution
Remote Desktop Protocol Extra Window Memory Injection Token Impersonation/Theft
SMB/Windows Admin Shares Process Hollowing Create Process with Token
Distributed Component Object Model Process Doppelgänging Make and Impersonate Token
VNC ListPlanting Parent PID Spoofing
Windows Remote Management T1055 - Process Injection SID-History Injection
T1091 - Replication Through Removable Media T1021 - Remote Services At T1134 - Access Token Manipulation
T1072 - Software Deployment Tools RDP Hijacking Scheduled Task Bypass User Account Control
T1080 - Taint Shared Content T1563 - Remote Service Session Hijacking T1053 - Scheduled Task/Job T1548 - Abuse Elevation Control Mechanism
Pass the Hash T1570 - Lateral Tool Transfer
Privilege Escalation
Pass the Ticket T1534 - Internal Spearphishing
T1550 - Use Alternate Authentication Material T1210 - Exploitation of Remote Services T1133 - External Remote Services
Lateral Movement DLL Search Order Hijacking
DLL Side-Loading
T1039 - Data from Network Shared Drive Executable Installer File Permissions Weakness
T1025 - Data from Removable Media T1005 - Data from Local System Path Interception by PATH Environment Variable
Local Data Staging Sharepoint Path Interception by Search Order Hijacking
Remote Data Staging T1213 - Data from Information Repositories Path Interception by Unquoted Path
T1074 - Data Staged T1115 - Clipboard Data Services File Permissions Weakness Change Default File Association
Local Email Collection T1185 - Browser Session Hijacking Services Registry Permissions Weakness Screensaver
Remote Email Collection T1119 - Automated Collection COR_PROFILER Windows Management Instrumentation Event Subscription
Email Forwarding Rule T1123 - Audio Capture KernelCallbackTable Netsh Helper DLL
T1114 - Email Collection Archive via Utility T1574 - Hijack Execution Flow Accessibility Features
Keylogging Archive via Library Domain Controller Authentication AppCert DLLs
GUI Input Capture Archive via Custom Method Password Filter DLL AppInit DLLs
Web Portal Capture T1560 - Archive Collected Data Reversible Encryption Application Shimming
Credential API Hooking LLMNR/NBT-NS Poisoning and SMB Relay Multi-Factor Authentication Image File Execution Options Injection
T1056 - Input Capture ARP Cache Poisoning Hybrid Identity PowerShell Profile
T1113 - Screen Capture DHCP Spoofing T1556 - Modify Authentication Process Component Object Model Hijacking
T1125 - Video Capture T1557 - Adversary-in-the-Middle Office Template Macros Installer Packages
Collection Office Test T1546 - Event Triggered Execution
Outlook Forms Windows Service
T1105 - Ingress Tool Transfer Outlook Home Page T1543 - Create or Modify System Process
T1008 - Fallback Channels Outlook Rules Local Account
Symmetric Cryptography Add-ins Domain Account
Asymmetric Cryptography T1137 - Office Application Startup T1136 - Create Account
T1573 - Encrypted Channel System Firmware T1554 - Compromise Client Software Binary
T1104 - Multi-Stage Channels Fast Flux DNS Component Firmware T1176 - Browser Extensions
T1095 - Non-Application Layer Protocol Domain Generation Algorithms Bootkit Logon Script (Windows)
T1571 - Non-Standard Port DNS Calculation T1542 - Pre-OS Boot Network Logon Script
T1572 - Protocol Tunneling T1568 - Dynamic Resolution At T1037 - Boot or Logon Initialization Scripts
Internal Proxy Junk Data Scheduled Task Registry Run Keys / Startup Folder
External Proxy Steganography T1053 - Scheduled Task/Job Authentication Package
Multi-hop Proxy Protocol Impersonation SQL Stored Procedures Time Providers
Domain Fronting T1001 - Data Obfuscation Transport Agent Winlogon Helper DLL
T1090 - Proxy Standard Encoding Web Shell Security Support Provider
T1219 - Remote Access Software Non-Standard Encoding IIS Components LSASS Driver
Port Knocking T1132 - Data Encoding Terminal Services DLL Shortcut Modification
Socket Filters T1092 - Communication Through Removable Media T1505 - Server Software Component Port Monitors
T1205 - Traffic Signaling Web Protocols Port Knocking Print Processors
Dead Drop Resolver File Transfer Protocols Socket Filters Active Setup
Bidirectional Communication Mail Protocols T1205 - Traffic Signaling T1547 - Boot or Logon Autostart Execution
One-Way Communication DNS Default Accounts T1197 - BITS Jobs
T1102 - Web Service T1071 - Application Layer Protocol Domain Accounts Additional Email Delegate Permissions
Local Accounts Device Registration
Command and Control
T1078 - Valid Accounts T1098 - Account Manipulation
Exfiltration Over Bluetooth
Persistence
T1011 - Exfiltration Over Other Network Medium T1041 - Exfiltration Over C2 Channel
Exfiltration over USB Exfiltration Over Symmetric Encrypted Non-C2 Protocol At
T1052 - Exfiltration Over Physical Medium Exfiltration Over Asymmetric Encrypted Non-C2 Protocol Scheduled Task
Exfiltration to Code Repository Exfiltration Over Unencrypted Non-C2 Protocol T1053 - Scheduled Task/Job
Exfiltration to Cloud Storage T1048 - Exfiltration Over Alternative Protocol T1106 - Native API
T1567 - Exfiltration Over Web Service T1030 - Data Transfer Size Limits Component Object Model
T1029 -Scheduled Transfer T1020 - Automated Exfiltration Dynamic Data Exchange
T1129 - Shared Modules T1559 - Inter-Process Communication
Exfiltration
T1072 - Software Deployment Tools T1203 - Exploitation for Client Execution
OS Exhaustion Flood Service Execution PowerShell
Service Exhaustion Flood T1569 - System Services Windows Command Shell
Application Exhaustion Flood Malicious Link Visual Basic
Application or System Exploitation Malicious File Python
T1499 - Endpoint Denial of Service T1204 - User Execution JavaScript
Disk Content Wipe T1047 - Windows Management Instrumentation T1059 - Command and Scripting Interpreter
Disk Structure Wipe Execution
T1561 - Disk Wipe
Internal Defacement T1091 - Replication Through Removable Media
External Defacement Compromise Software Dependencies and Development Tools
T1495 - Firmware Corruption T1491 - Defacement Compromise Software Supply Chain Spearphishing Attachment
T1490 - Inhibit System Recovery Stored Data Manipulation Compromise Hardware Supply Chain Spearphishing Link
Direct Network Flood Transmitted Data Manipulation T1195 - Supply Chain Compromise Spearphishing via Service
Reflection Amplification Runtime Data Manipulation T1199 - Trusted Relationship T1566 - Phishing
T1498 - Network Denial of Service T1565 - Data Manipulation Default Accounts T1200 - Hardware Additions
T1496 - Resource Hijacking T1486 - Data Encrypted for Impact Domain Accounts T1133 - External Remote Services
T1489 - Service Stop T1485 - Data Destruction Local Accounts T1190 - Exploit Public-Facing Application
T1529 - System Shutdown/Reboot T1531 - Account Access Removal T1078 - Valid Accounts T1189 - Drive-by Compromise
Impact Initial Access
MITRE Windows
ATT&CK Tree
You might also like
- CWS-313-2I 09 TroubleshootDeliveryControllerIssues V2.00Document18 pagesCWS-313-2I 09 TroubleshootDeliveryControllerIssues V2.00Onurcan YahyaoğluNo ratings yet
- Crypto Map Version 1.0Document1 pageCrypto Map Version 1.0SylasMendesNo ratings yet
- Webinar Presentation Cybersecurity4ProtectionEngineersDocument81 pagesWebinar Presentation Cybersecurity4ProtectionEngineersthanh tranNo ratings yet
- Panos London 01 Who Rules The InternetDocument6 pagesPanos London 01 Who Rules The InternetMurali ShanmugavelanNo ratings yet
- Azure Storage - ThreatModelDocument135 pagesAzure Storage - ThreatModelMateuszNo ratings yet
- Transforming Security Through Visibility: Name TitleDocument16 pagesTransforming Security Through Visibility: Name TitleThiên HoàngNo ratings yet
- Customer-Partners - WINDOW-POC GUIDE Harmony EndPoint EPM R81.10 - Step by Step Version FinalDocument39 pagesCustomer-Partners - WINDOW-POC GUIDE Harmony EndPoint EPM R81.10 - Step by Step Version Finalgarytj210% (1)
- Pcnsa V17.95Document72 pagesPcnsa V17.95Clever Romani AyalaNo ratings yet
- DevOps Ecosystem v2Document1 pageDevOps Ecosystem v2nitindograNo ratings yet
- Bank Management System Report PDFDocument142 pagesBank Management System Report PDFSheetal Rana60% (10)
- Object Detection Using Deep LearningDocument45 pagesObject Detection Using Deep LearningOrthi GanguliNo ratings yet
- Defense EvasionDocument1 pageDefense EvasionrakivanatanNo ratings yet
- Mitre Att&Ck Enterprise Framework: Solving Problems For A Safer WorldDocument1 pageMitre Att&Ck Enterprise Framework: Solving Problems For A Safer WorldSeguridad InformaticaNo ratings yet
- NSA Sharkseer PDFDocument12 pagesNSA Sharkseer PDFJuan100% (1)
- Apt Attacks Map Government 2019Document1 pageApt Attacks Map Government 2019spamstopsNo ratings yet
- Fleury - MITRE KILL CHAINDocument1 pageFleury - MITRE KILL CHAINVinicius CaldiniNo ratings yet
- Defend MitreDocument1 pageDefend MitrerakivanatanNo ratings yet
- SD Blueprint MergedDocument160 pagesSD Blueprint MergedHrithik VemparalaNo ratings yet
- Hikvision Product Security White PaperDocument28 pagesHikvision Product Security White PaperEl Kader SurveillanceNo ratings yet
- Access ControlDocument1 pageAccess Controlulhaqz2No ratings yet
- SDA Mind Map PDFDocument1 pageSDA Mind Map PDFbest0806No ratings yet
- 11 Measuring and Data Transmission: Software Documentation Page 11-1 EDC7 Keyword Protocol 2000Document20 pages11 Measuring and Data Transmission: Software Documentation Page 11-1 EDC7 Keyword Protocol 2000Lucía jandigNo ratings yet
- Cysemol Manual ShortDocument59 pagesCysemol Manual ShortSrikanth S.No ratings yet
- Iot Platform ArchitectureDocument3 pagesIot Platform ArchitectureKirubagaran TNo ratings yet
- Document Automation Pitch DeckDocument33 pagesDocument Automation Pitch Deckrobot.azure.2No ratings yet
- CyberSecurity WhitePaper en PDFDocument45 pagesCyberSecurity WhitePaper en PDFruben sandovalNo ratings yet
- OSS - Basic Training On Operation of TopEng Mediation V1.0-20070516-BDocument13 pagesOSS - Basic Training On Operation of TopEng Mediation V1.0-20070516-BShonam NarayanNo ratings yet
- Arquitetura GCP Pos GraduaçãoDocument2 pagesArquitetura GCP Pos GraduaçãoNicolas FontalvaNo ratings yet
- Arquitetura GCP Pos GraduaçãoDocument2 pagesArquitetura GCP Pos GraduaçãoNicolas FontalvaNo ratings yet
- Process Flow For Label PrintingDocument1 pageProcess Flow For Label PrintingRecardo FreddyNo ratings yet
- System Design BlueprintDocument1 pageSystem Design BlueprintSathiamoorthy DuraisamyNo ratings yet
- Dark Trace - Mapping To MITREDocument19 pagesDark Trace - Mapping To MITREDonghan KimNo ratings yet
- ScanViS Camguard 2Document2 pagesScanViS Camguard 2Bruno MarceloNo ratings yet
- Senhasegura Datasheet How Pam Works Atualizado enDocument5 pagesSenhasegura Datasheet How Pam Works Atualizado enandini eldanantyNo ratings yet
- Ems E3Document1 pageEms E3andini eldanantyNo ratings yet
- Processing Integrity and Availability ControlsDocument1 pageProcessing Integrity and Availability ControlsDiyah FebriNo ratings yet
- Overview of Payroll IntegrationsDocument10 pagesOverview of Payroll IntegrationsrifkiNo ratings yet
- Mobile Soft Token Implementation - For Nam A Bank 2019: Christabel Koh Technical Account ManagerDocument23 pagesMobile Soft Token Implementation - For Nam A Bank 2019: Christabel Koh Technical Account ManagerDang TrieuhaiNo ratings yet
- Ciclo de Vida Del RansomwareDocument1 pageCiclo de Vida Del RansomwarerodrigoduocNo ratings yet
- BRKSEC-2691 Identity Based Networking IEEE 802.1X and BeyondDocument83 pagesBRKSEC-2691 Identity Based Networking IEEE 802.1X and BeyondNguyen LeNo ratings yet
- ARX Presenation PDFDocument10 pagesARX Presenation PDFintellectdesignNo ratings yet
- Palo Alto Networks - Content-ID Tech BriefDocument5 pagesPalo Alto Networks - Content-ID Tech BriefEduardo Vilchez RoncalNo ratings yet
- Process ControllerDocument8 pagesProcess ControllerSergio LunaNo ratings yet
- Hacking AvanzadoDocument17 pagesHacking AvanzadoevilrunNo ratings yet
- Fortanix DSM OnePage DatasheetDocument2 pagesFortanix DSM OnePage Datasheetvlado.vajdicNo ratings yet
- Overview of System Architecture For Platform 2023Document1 pageOverview of System Architecture For Platform 2023Work ConNo ratings yet
- Credential AccessDocument1 pageCredential AccessNuryadin Usman Abdurrahim AsSampiti IINo ratings yet
- Security Empowers Business: How It Works 2Document11 pagesSecurity Empowers Business: How It Works 2Rafiai KhalidNo ratings yet
- Organization: Cisco SD-WAN ArchitectureDocument5 pagesOrganization: Cisco SD-WAN ArchitectureAhmed HamadaNo ratings yet
- DME IQ Intelligent Cloud O&M Platform Quick Deployment Guide (Connecting Storage Using DME IQ Client)Document2 pagesDME IQ Intelligent Cloud O&M Platform Quick Deployment Guide (Connecting Storage Using DME IQ Client)Mpho MpyaNo ratings yet
- Cheetah Functional ArchitectureDocument2 pagesCheetah Functional ArchitectureADITYA DUBEYNo ratings yet
- Windows Log-Md Att&Ck Cheat Sheet - Win 7 - Win 2012: DefinitionsDocument17 pagesWindows Log-Md Att&Ck Cheat Sheet - Win 7 - Win 2012: DefinitionsJWilhNo ratings yet
- Chapter 9 & 10: Is Controls For System Reliabilities: - Confidentiality, Privacy, Processing Integrity & AvaiabilityDocument7 pagesChapter 9 & 10: Is Controls For System Reliabilities: - Confidentiality, Privacy, Processing Integrity & AvaiabilityNik Nur Azmina AzharNo ratings yet
- Rsa Netwitness PlatformDocument7 pagesRsa Netwitness Platformdoan nguyenNo ratings yet
- #Fastsecure: Технический Директор Fortinet В России И Странах СнгDocument23 pages#Fastsecure: Технический Директор Fortinet В России И Странах Снгhabib kamaieNo ratings yet
- Comarch Fault ManagementDocument5 pagesComarch Fault ManagementJoaquinNo ratings yet
- 1 ATA StandardsBlockchain - SITADocument35 pages1 ATA StandardsBlockchain - SITAaccendoNo ratings yet
- AIR Deep Dive - Nplus1Document29 pagesAIR Deep Dive - Nplus1cctv cydNo ratings yet
- Simplify Your StreamingDocument27 pagesSimplify Your StreamingPrasenjit PatnaikNo ratings yet
- Vehicle Database Management System (VDMS)Document18 pagesVehicle Database Management System (VDMS)ghayyourNo ratings yet
- KPI's Safety, Quality, Deliver, Cost & MoraleDocument1 pageKPI's Safety, Quality, Deliver, Cost & MoraleCHAITANYA SAHUNo ratings yet
- Du CVMDocument6 pagesDu CVM1977amNo ratings yet
- OLD AWS Core Products and ServicesDocument54 pagesOLD AWS Core Products and ServicesashishscribdNo ratings yet
- MCA-108 Object Oriented Programming Using C++ L-T-P: 3-1-0Document91 pagesMCA-108 Object Oriented Programming Using C++ L-T-P: 3-1-0Sankari SoniNo ratings yet
- Arma Server Web Admin - ARMA 3 - COMMUNITY MADE UTILITIES - Bohemia Interactive Forums PDFDocument1 pageArma Server Web Admin - ARMA 3 - COMMUNITY MADE UTILITIES - Bohemia Interactive Forums PDFBMikeNo ratings yet
- Agilent FieldFox All Models Programming GuideDocument339 pagesAgilent FieldFox All Models Programming GuideAchmad Arizki KosasihNo ratings yet
- Nandha Engineering College (Autonomous) Department of Ece Batch No:21Document3 pagesNandha Engineering College (Autonomous) Department of Ece Batch No:21monishabe23No ratings yet
- Black Spot Identification: Sensitivity: InternalDocument8 pagesBlack Spot Identification: Sensitivity: InternalShain SalimNo ratings yet
- C03 User's InterfaceDocument52 pagesC03 User's InterfaceFIVE MEDIA SOCIALNo ratings yet
- Promoting Effective Communication: Chapter SixteenDocument15 pagesPromoting Effective Communication: Chapter SixteenWazeeer AhmadNo ratings yet
- In Situ Adaptive TabulationDocument2 pagesIn Situ Adaptive Tabulationjoseph458No ratings yet
- 2 - Difference Between Incident, Problem, Change and Asset ManagementDocument14 pages2 - Difference Between Incident, Problem, Change and Asset Managementelisa navesNo ratings yet
- 10-1 Intro To Conic Sections - ClassDocument29 pages10-1 Intro To Conic Sections - Classalvin ubasNo ratings yet
- System Specifications: Vocabulary 2Document4 pagesSystem Specifications: Vocabulary 2silvioney backes vogadoNo ratings yet
- S S S S: 2. Suppliers of Admiralty Charts and PublicationsDocument2 pagesS S S S: 2. Suppliers of Admiralty Charts and PublicationsFachrul Hokus FokusNo ratings yet
- Settop Box ManualDocument6 pagesSettop Box ManualamindurNo ratings yet
- Talend ESBDocument114 pagesTalend ESBNguyen Duc TungNo ratings yet
- Application Form For Wi-Fi ConnectionDocument1 pageApplication Form For Wi-Fi ConnectionProgramming vidNo ratings yet
- Take Home Assignment - Beer Production - V2.3Document3 pagesTake Home Assignment - Beer Production - V2.3Abhishek koteNo ratings yet
- Clickshare Cse-200+: Wireless Collaboration Solution For Creative Content-Sharing Fit For Enterprise Roll-OutsDocument2 pagesClickshare Cse-200+: Wireless Collaboration Solution For Creative Content-Sharing Fit For Enterprise Roll-OutsWilmer ProcontNo ratings yet
- Management Information Systems Research Center, University of Minnesota MIS QuarterlyDocument6 pagesManagement Information Systems Research Center, University of Minnesota MIS QuarterlyCon BibsNo ratings yet
- How To Manage Inbound Outbound Route On UCMDocument23 pagesHow To Manage Inbound Outbound Route On UCMEmilio I WildeNo ratings yet
- Autonomous Driving With Deep Learning: A Survey of State-of-Art TechnologiesDocument33 pagesAutonomous Driving With Deep Learning: A Survey of State-of-Art TechnologiestilahunNo ratings yet
- Email Basics: by Pa Ali NyangDocument24 pagesEmail Basics: by Pa Ali Nyangpan111No ratings yet
- MOA For TABLET 2023Document2 pagesMOA For TABLET 2023Phoeza Espinosa VillanuevaNo ratings yet
- BIT 282 Java Programming Lab: Course ObjectivesDocument1 pageBIT 282 Java Programming Lab: Course ObjectivesPalanikumarNo ratings yet
- User Manual: VDH-NKDocument41 pagesUser Manual: VDH-NKMohamed Ibrahim AhamedRasmiNo ratings yet
- Led TV : Owner'S ManualDocument52 pagesLed TV : Owner'S ManualLucille Isidro CruzNo ratings yet
- Actuators: Version 2 EE IIT, Kharagpur 1Document29 pagesActuators: Version 2 EE IIT, Kharagpur 1Khaled MahranNo ratings yet