Professional Documents
Culture Documents
PCIe Data Sheet
Uploaded by
daniel_vp21Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
PCIe Data Sheet
Uploaded by
daniel_vp21Copyright:
Available Formats
Use the IBM® hardware security module (HSM) to
provide a flexible solution to your high-security
cryptographic processing needs.
IBM 4767-002 PCIe Cryptographic Coprocessor (HSM)
The use of cryptography is a crucial
element of modern business
applications. Applications use
cryptography in a variety of ways to
protect the privacy and confidentiality
of data, ensure its integrity, and
provide user accountability through
digital signature techniques.
The IBM 4767 PCIe Cryptographic
Coprocessor is an HSM. This HSM is
a programmable PCIe card that
offloads computationally intensive
cryptographic processes from the
hosting server and performs sensitive
tasks unsuitable for less secure
general-purpose computers. It is a
Highlights key product for enabling secure
Internet business transactions and is
• A high-end secure HSM • Scaling is supported through suited for a wide variety of secure
implemented on a PCIe card with a bundling of multiple adapters to cryptographic applications.
multi-chip embedded module meet the highest throughput
• Foundation for secure applications, requirements
Certifications
such as high-assurance digital • Secure code loading with
signature generation or financial hardware assisted image The IBM 4767 is validated by NIST
transaction processing verification that enables updating (certificate number 3164) at FIPS
• Custom software options of the functionality while installed 140-2 Level 4, the highest security
in application systems level possible. Referencia 9
• Hardware to perform symmetric and
hashing algorithms, including AES • IBM Common Cryptographic IBM Enterprise PKCS#11 firmware is
(CBC, ECB, GCM, XTS, CMAC, Architecture (CCA) API and Common Criteria EAL4 certified.
others), DES and TDES (CBC, ECB, security architecture The IBM 4767 with CCA firmware is
MAC, EMVMAC, X9.19, X9.9, • IBM Enterprise PKCS #11 (EP11) compliant with the German Banking
others), hashing (SHA-1, SHA-2 • Maximum flexibility and maximum Industry Committee (GBIC) security
(224-512), MD5, RIPEMD-160, trust while operating in physical requirements.
MDC-2, MDC-4, PADMDC-2, environments that have minimum
PADMDC-4) and HMAC Referencia 4 physical security Certification details are on page 7.
• Hardware to support asymmetric • Suitable for high-security
algorithms including large number processing and high-speed
modular math functions for RSA (up cryptographic operations
to 4096-bit) Elliptic Curve (Prime
Curves to 521 and Brainpool Curves • Visa Data Secure Platform (DSP)
up to 512) Referencia 3 Point-to-Point Encryption (P2PE)
including Visa FPE encryption,
• Standards-compliant hardware decryption, and translation
random number generator
• Tamper-responding
• Hardware-based prime number programmable secure hardware
generator meets FIPS 140-2 Level 4, the
highest level of security
IBM 4767 PCIe HSM 1 www.ibm.com/security/cryptocards
The 4767 HSM includes sensors to protect against attacks involving power manipulation, temperature manipulation, and
penetration of the secure module.
Software functionality
The IBM 4767 adapter
provides three modes of
operation:
- Common Cryptographic
Architecture (CCA) Support
Program (financial transaction
focus),
- IBM Enterprise PKCS #11
(internet business application
focus), and
- Accelerator mode for offload
of computer intensive Referencia 7
operations in clear key mode.
These modes are exclusive, so
only one mode can be present
at any time. With CCA, you can
also add custom functions to
the HSM using an available
programming toolkit or through
IBM consulting services.
Typical applications
The IBM 4767 PCIe What is a secure HSM?
Cryptographic Coprocessor A secure HSM is a general-purpose computing environment that
(HSM) is suited to applications withstands both physical and logical attacks. The device must run the
requiring high-speed software that it is supposed to run, with confidence that the software has
not been modified. You must be able to (remotely) distinguish between the
cryptographic functions for
real device and application, and a clever impersonator.
data encryption and digital
signing, secure storage of The HSM must remain secure even if adversaries carry out destructive
signing keys, or custom analysis of one or more devices. Many servers operate in distributed
cryptographic applications. environments where it is difficult or impossible to provide complete physical
These can include financial security for sensitive processing. In some applications, the motivated
applications such as PIN adversary is the end user. You need a device that you can trust even
generation and verification in though you cannot control its environment.
automated teller and point-of-
sale transaction servers, key Cryptography is an essential tool in secure processing. When your
management systems, Internet application must communicate with other distributed elements or assert or
business and Web-serving ascertain the validity of data that it is processing, you will find cryptography
applications, Public Key an essential tool.
Infrastructure applications,
smart card applications, PKCS
#11 applications in general, Relevant Cryptographic Standards Supported by the IBM 4767
and custom proprietary FIPS 140 X9.8 / ISO 9564 GBIC (DK)
solutions. Applications can Common Criteria TR-31 NIST SP 800-90A
benefit from the strong security X9.24 Parts 1, 2, and 3 X9.97 / ISO 13491 PKCS #1
characteristics of the HSM and X9.102 PKCS #11
the opportunity to offload
computationally intensive
cryptographic processing.
IBM 4767 PCIe HSM 2 www.ibm.com/security/cryptocards
IBM 4767 hardware Embedded certificate possible attack, all critical keys and
The IBM 4767 hardware During the final manufacturing step, the other sensitive data are immediately
provides significant HSM generates a unique public/private destroyed and the HSM is rendered
performance and architectural key pair which is stored in the device. permanently inoperable. Note therefore
improvements over its The tamper detection circuitry is that the 4767 HSM must be maintained
predecessor while enabling activated at this time and remains active at all times within the temperature,
future growth. The secure throughout the useful life of the HSM, humidity, and barometric pressure
module contains redundant protecting this private key as well as ranges specified. Refer to the
IBM PowerPC 476 processors, other keys and sensitive data. The environmental requirements section of
custom symmetric key and public key of the HSM is certified at the the technical references table on the
hashing engines to perform factory by an IBM private key and the last page.
AES, DES, TDES, SHA-1 and certificate is retained in the HSM.
A pair of batteries mounted on the HSM
SHA-2, MD5 and HMAC, and Subsequently, the private key of the
board provides backup power when the
custom public key HSM is used to sign the HSM status
4767 HSM is not in a powered-on
cryptographic algorithm responses which, in conjunction with a
machine. These batteries must only be
engines to support for RSA series of public key certificates,
removed according to the documented
and Elliptic Curve Crypto- demonstrate that the HSM remains
battery replacement procedure to avoid
graphy (ECC). Other hardware intact and is genuine.
Referencia 6 zeroizing the HSM and rendering it
support includes a secure real-
permanently inoperable. A battery
time clock, hardware random Tamper responding design
replacement kit can be obtained from
number generator and a prime The 4767 HSM has been certified to
IBM (Part Number 45D5803).
number generator. The secure meet the FIPS 140-2 Level 4
module is protected by a requirements by protecting against 4767 technology in IBM servers
tamper responding design that attacks that include penetration of
protects against a wide variety the secure module, side-channel The following IBM server families support
of attacks against the system attacks, and environmental failure 4767 technology, either directly or as
and immediately destroys all protection (power or temperature orderable features.
• x86 — the IBM 4767 can be ordered and
keys and sensitive data if manipulation). From the time of
installed. CCA support program for each
tampering is detected. manufacture, the hardware is fully self- supported operating system can be
protecting. If tamper sensors detect a downloaded from the IBM CryptoCards
Reliability, Availability, and product website.
Serviceability (RAS) • IBM Power® Systems – selected models
Hardware has also been offer an optional cryptographic coprocessor
designed to support the feature, supported on IBM AIX®, IBM i®,
highest level of RAS and selected Linux® distributions.
requirements that enable the • IBM Z® — selected models offer an
secure module to self-check at optional Crypto Express5S (CEX5S)
all times. This is achieved by feature. On z/OS®, support is provided by
running a pair of PowerPC ICSF cryptographic services. On Linux on
processors in lock step and IBM Z, support for the CEX5S is provided
comparing the result from each by the CCA for Linux on Z package or the
EP11 host package, available from the
cycle by cycle. Also, all
IBM CEX5S Linux on IBM Z software
interfaces, registers, memory, page.
cryptographic engines, and
buses are protected at all times IBM 4767 software
using parity, ECC, or CRC. • IBM-supplied IBM Common
Power on self-tests that are Cryptographic Architecture (CCA)
securely stored in the secure
• IBM-supplied IBM Enterprise PKCS
module verify the hardware
#11 (EP11)
and firmware loaded on the
Both come as a no-charge support
module is secure and reliable
program feature.
at every power on. Then, built-
• Or choose customization options:
in RAS features check it
— IBM custom development to your
continuously in real time.
specification.
— Toolkit under custom contracts
and export control.
IBM 4767 PCIe HSM 3 www.ibm.com/security/cryptocards
CCA highlights
CCA includes these capabilities:
• Data confidentiality using AES, DES, and TDES.
• Message integrity using AES, DES and TDES MAC,
CMAC, and HMAC.
• Digital signature generation and verification using RSA or
ECC with formatting according to PKCS #1, RSA-PSS,
ISO 9796-1, and ANSI X9.31. RSA keys up to 4096 bits.
ECC keys using NIST prime curves up to 521 bits and
Brainpool curves up to 512 bits.
• Hashing using SHA-1, SHA-2, MD5, and RIPEMD-160.
• PIN processing—several generation and verification
processes, many PIN block formats, PIN translation to
change keys or formats. DUKPT key management is
supported.
• Support for German Banking Industry Committee, Die
Deutsch Kreditwirtschaft (DK), financial services.
• Variable-length symmetric key-token that meets key
bundling requirements, enforces key usage, and tracks a
key's lifecycle events and pedigree. Referencia 8
• Key distribution based on AES, DES, and RSA. Key
agreement using Elliptic Curve Diffie-Hellman (ECDH).
• Secure generation of symmetric and asymmetric keys,
including AES, DES, and TDES, RSA (up to 4096 bits),
and ECC (Prime curves up to 521 bits and Brainpool
curves up to 512 bits).
• Support for smart card applications using the EMV®
specifications.
• HSM initialization options, a wide variety of backup capabilities for the HSM, and the ability to clone to another HSM.
• Administrative commands digitally signed by administrators and verified in the HSM.
• User Defined Extension (UDX) facility can be used to add custom functions to the standard CCA command set. Custom functions
execute inside the secure module of the IBM 4767, with the same security as the other CCA functions.
• Generation of high-quality random numbers.
• Refined key typing to block attacks through misuse of the key-management functions.
• Secrets stored externally are cryptographically protected against disclosure or modification.
• Secure public key infrastructure: native X.509 certificate support including PKCS #10 certificate request generation through a
new PKI hosted from the HSM.
• Assistance for planning the migration to PCI-HSM compliance mode using run-time analysis and reporting by the HSM.
• Certain classes of HSM-protected AES and TDES keys can be securely exported to CPACF.
If you have additional questions about the IBM 4767 or about CCA, please contact crypto@us.ibm.com.
Custom software support
It is possible to implement custom functions in the 4767 to meet specialized needs. Two options are available. User Defined
Extensions (UDX) use CCA as a starting point and add new functions to the standard CCA API set. This is the approach that is
most commonly used. However, when your application is substantially different from CCA, a complete custom application can be
built on top of the HSM's embedded Linux environment. With this method, you can implement very different approaches to
cryptographic applications, or even non-cryptographic applications that benefit from running in a secure processing environment.
The internal environment of the 4767 consists of an embedded Linux operating system and associated device drivers for the
HSM's specialized hardware. IBM provides documented API functions that custom software can use to perform cryptographic
operations or to assist their applications in other ways. Your custom application is digitally signed using a key that you generate
yourself, and the application is securely loaded to the HSM using the same FIPS 140-2 certified processes that are used to protect
IBM-provided HSM code.
Programming custom applications
IBM offers custom programming services through an experienced IBM team that is familiar with the 4767’s specialized
programming environment, tools, debug aids, and code release procedures. Customers can obtain custom programming services
through an experienced IBM services team or through selected contractors. IBM is pleased to jointly develop specifications and
provide quotes on custom solutions.
IBM 4767 PCIe HSM 4 www.ibm.com/security/cryptocards
Custom software toolkit
Alternatively, IBM offers a toolkit that you can use to create and debug custom applications yourself. Toolkit documentation can be
obtained from the IBM CryptoCards product website. Because this is a specialized programming environment and there are special
considerations related to the export and import of cryptographic implementations, the toolkit is available only under special
contracts. Generally, in addition to the actual toolkit, customers will need to purchase consulting time for education and ongoing
support. Any export or import considerations will be part of this contract.
Education
Courses are held periodically to provide education about the IBM 4767 and CCA. The courses can also be taught at your location,
worldwide. These courses cover programming for the CCA API and the IBM 4767 installation and configuration.
In addition, custom courses can be arranged to cover other topics including programming and debugging applications that operate
within the IBM 4767.
If you have questions about custom applications, the developer’s toolkit, or education, please contact crypto@us.ibm.com.
IBM 4767 PCIe HSM 5 www.ibm.com/security/cryptocards
EP11 highlights
EP11 includes these capabilities:
Referencia 2
• Support for PKCS #11 version 2.20.
• Data confidentiality using AES and TDES.
• Message integrity using AES and TDES
MAC, CMAC, and HMAC.
• Digital signature generation and verification
using RSA or ECC with formatting according
to PKCS #1 and RSA-PSS. RSA keys up to
4096 bits. ECC keys using NIST Prime
curves up to 521 bits and Brainpool curves
up to 512 bits.
• Hashing using SHA-1 and SHA-2.
• EP11 login sessions – bind objects to a
specific user to allow for fine-grained usage
control of objects.
• Attribute-bound keys – transport secrets
securely without losing attributes between
different systems.
• Secure Wrapping Key (WK) cloning and
domain or card state export and import.
• Enforcing usage policies and support for
binding objects to specific operational
modes.
• Secure audit facility.
• Generation of high-quality random numbers.
• Trustable public keys through integrity-
protected SPKIs with MAC.
• Secrets stored externally are
cryptographically protected against
disclosure or modification.
• Wrapped content is authenticated with a
MAC key that is derived from the WK.
• Wrapping keys can only be loaded encrypted using importer keys.
• Administrative commands are signed by M-of-N administrators before the command is accepted by the HSM.
• Allows binding of objects to specific operational modes enforcing using objects only on backends where specific policies are
activated.
• The system is stateless, keeping most of the secrets outside the HSM in wrapped and MACed form, allowing maximizing
throughput and a potential unlimited number of users.
• The transport protocol that is used between the backend and the host library is documented and published.
• Secure generation of symmetric and asymmetric keys for AES, TDES, DH, DSA, RSA (up to 4096 bits), and ECC (Prime curves
up to 521 bits and Brainpool curves up to 512 bits).
• Key distribution based on AES, DES, and RSA. Key agreement using Diffie-Hellman (DH) and ECDH.
If you have additional questions about EP11, please contact EP11SUPP@de.ibm.com.
IBM 4767 PCIe HSM 6 www.ibm.com/security/cryptocards
Certification Information
This section discusses the various certifications that the IBM 4767 has achieved.
The IBM 4767 is validated by NIST (certificate number 3164) at FIPS 140-2 Level 4, the highest
security level possible.
EP11 in version 4.18 (BSI-DSZ-CC-1002), running on the IBM 4767, has been certified to meet the
requirements of the BSI (Federal Office for Information Security in Germany) for conformance with
Common Criteria in version 3.1 (rev. 4) with Evaluation Assurance Level (EAL) 4.
The evaluation has been conducted in accordance with the provisions of the
certification scheme of the German Federal Office for Information Security
(BSI) and the conclusions of the evaluation facility in the evaluation technical
report are consistent with the evidence adduced.
The IBM 4767-002 with CCA version 5.3 firmware fulfills the security requirements of the German Banking Industry Committee
(GBIC). The report is listed under number 3299.
The CCA release 5.3 provides sophisticated state-of-the-art protections for
handling sensitive information like PIN data, cryptographic key data and
account data.
The HSM IBM Model 4767-002 CCA Release 5.3 implementation is compliant
with GBIC’s security requirements.
IBM 4767 PCIe HSM 7 www.ibm.com/security/cryptocards
HSM technical specifications:
IBM 4767 PCIe Cryptographic Coprocessor
© Copyright IBM Corporation 2016, 2019
Physical characteristics
Card type: Half-length PCIe x4 card IBM Corporation
Integrated Marketing Communications,
PCI Local Bus Specification 2.2 Server Group
PCIe specification 1.1 Route 100
Somers, NY 10589
Voltage / Power consumed: +3.3 VDC ± 10% 23.44 W max
Required: 25 W min Referencia 5 Produced in the United States of America
April 2019
System requirements References in this publication to IBM products or
services do not imply that IBM intends to make them
This section describes requirements for the system in which the 4767 is installed. available in every country in which IBM operates.
Consult your local IBM business contact for information
Software (downloadable from IBM CCA Support Program for use on Linux, on the products, features, and services available in your
HSM 4767 download software Windows, or AIX. See the operating system area.
link of the IBM CryptoCards reference chart for a list of supported operating
product website): systems. IBM, the IBM logo, ibm.com, IBM Z, System z, Power
Referencia 1 Systems, and z/OS are trademarks or registered
trademarks of IBM Corporation in the United States,
The coprocessor can be installed in selected IBM Z other countries or both.
models and selected IBM Power servers as a
Hardware feature, as well as in x86 servers that meet the Linux is a registered trademark of Linus Torvalds in the
environmental requirements listed below. For details, United States, other countries, or both.
see IBM 4767 x86 servers. EMV is a trademark owned by EMVCo LLC.
Other trademarks and registered trademarks are the
Environmental requirements From the time of manufacture, the IBM 4767 PCIe properties of their respective companies.
Cryptographic Coprocessor card must be shipped, IBM hardware products are manufactured from new
stored, and used within the following environmental parts, or new and used parts. Regardless, our warranty
specifications. Outside of these specifications, the terms apply.
IBM 4767 tamper sensors can be activated and
render the IBM 4767 permanently inoperable. Photographs shown are of engineering prototypes.
Changes may be incorporated in production models.
This equipment is subject to all applicable FCC rules
IBM 4767 and will comply with them upon delivery.
Shipping: Card should be shipped in original IBM packaging (electrostatic discharge bag Information concerning non-IBM products was obtained
with desiccant and thermally insulated box with gel packs). from the suppliers of those products. Questions
concerning those products should be directed to those
Temp shipping -34°C to +60°C
suppliers.
Pressure shipping min 550 mbar
Humidity shipping 5% to 100% RH All customer examples described are presented as
illustrations of how those customers have used IBM
Storage: Card should be stored in electrostatic discharge bag with desiccant. products and the results they may have achieved.
Temp storage +1°C to +60°C Actual environmental costs and performance
Pressure storage min 700 mbar characteristics may vary by customer.
Humidity storage 5% to 80% RH
Operation (ambient in system)
Temp operating +10°C to +35°C
Humidity operating 8% to 80% RH
Operating altitude (max) 10 000 ft equivalent to 700 mbar min
For more information
Documentation and publications, ordering procedures, and news concerning the
IBM 4767 PCIe Cryptographic Coprocessor can be found at the IBM
CryptoCards product website. You can also call IBM DIRECT at 1-800-IBM-
CALL, contact your IBM representative, or visit the IBM Marketplace.
IBM 4767 PCIe HSM 8 www.ibm.com/security/cryptocards
You might also like
- Buffer Overflow Attacks: Detect, Exploit, PreventFrom EverandBuffer Overflow Attacks: Detect, Exploit, PreventRating: 3.5 out of 5 stars3.5/5 (3)
- Ibm 4767-002 Pcie Cryptographic Coprocessor (HSM)Document6 pagesIbm 4767-002 Pcie Cryptographic Coprocessor (HSM)rgarcp2348No ratings yet
- Safenet Protectserver Pcie HSM PB v7Document3 pagesSafenet Protectserver Pcie HSM PB v7Huong NguyenNo ratings yet
- Key Protection Technology PaperDocument7 pagesKey Protection Technology Paperpauloco123No ratings yet
- Safenet Protectserver Network HSMDocument2 pagesSafenet Protectserver Network HSMferchovacaNo ratings yet
- 01 ProtectServer - Part I - Product OverviewDocument20 pages01 ProtectServer - Part I - Product OverviewmasanjayaNo ratings yet
- Hardware Security ModuleDocument2 pagesHardware Security ModuleSuresh100% (3)
- Thales ProtectServer Network HSM2 PBDocument2 pagesThales ProtectServer Network HSM2 PBTrầnTuấnThànhNhânNo ratings yet
- Thales Protect Server 3 Network Hsms PBDocument3 pagesThales Protect Server 3 Network Hsms PBTrầnTuấnThànhNhânNo ratings yet
- Entrust Nshield Edge DsDocument2 pagesEntrust Nshield Edge Dslo faszNo ratings yet
- Fortanix SDKMS DatasheetDocument4 pagesFortanix SDKMS Datasheetvlado.vajdicNo ratings yet
- Luna PCI E PB EN A4 v7 JUN052014 Web PDFDocument2 pagesLuna PCI E PB EN A4 v7 JUN052014 Web PDFمحمد زكريNo ratings yet
- Securing Cyberark Privileged Access Manager Using Securosys Cloudshsm or Primus HSMDocument2 pagesSecuring Cyberark Privileged Access Manager Using Securosys Cloudshsm or Primus HSMIT JPTOKNo ratings yet
- Safenet Protectserver Network HSM PB v11Document2 pagesSafenet Protectserver Network HSM PB v11Minh TranNo ratings yet
- NGSCB Provides Secure Computing PlatformDocument28 pagesNGSCB Provides Secure Computing PlatformAjay Nandakumar100% (1)
- Thales HSM BR v9Document4 pagesThales HSM BR v9Aung Kyaw ThuNo ratings yet
- Safenet Luna Network HSM v5 v6 PDFDocument2 pagesSafenet Luna Network HSM v5 v6 PDFHau Phuc TongNo ratings yet
- CCSP Exam Cram DOMAIN 5 HandoutDocument183 pagesCCSP Exam Cram DOMAIN 5 HandouttrojanbayaNo ratings yet
- Crypto ProcessorDocument16 pagesCrypto ProcessorYarlagadda Venkatesh ChowdaryNo ratings yet
- Secure Embedded ProcessorsDocument17 pagesSecure Embedded ProcessorsSimmi JoshiNo ratings yet
- EUD SecurityDocument20 pagesEUD SecurityDJMASSNo ratings yet
- See Enc PB101Document2 pagesSee Enc PB101ahmed gaafarNo ratings yet
- Thales Luna Network HSMDocument3 pagesThales Luna Network HSManlemacoNo ratings yet
- TCT - Vormetric Data Security Platform 12.18.19Document20 pagesTCT - Vormetric Data Security Platform 12.18.19tekena.alaminaNo ratings yet
- PCI-DSS and Crypto Key Management:: White PaperDocument10 pagesPCI-DSS and Crypto Key Management:: White PaperPramavNo ratings yet
- Safenet Keysecure PB v17Document3 pagesSafenet Keysecure PB v17Mert DayanirNo ratings yet
- Embedded High Assurance Computing Using The Freescale Trust ArchitectureDocument8 pagesEmbedded High Assurance Computing Using The Freescale Trust ArchitectureLuckySharma SharmaNo ratings yet
- HSM Design Principles v5 1Document6 pagesHSM Design Principles v5 1vvNo ratings yet
- NetHSM CurvesDocument2 pagesNetHSM CurvesTany Villalba VillalNo ratings yet
- Data Sheete Rubrik Encryption at Rest PDFDocument2 pagesData Sheete Rubrik Encryption at Rest PDFAdam VielbaumNo ratings yet
- Fs12-3113-002 Safenethsms Ds HRDocument2 pagesFs12-3113-002 Safenethsms Ds HRYandra Dhamma RakkhitoNo ratings yet
- FPGA-based High-Performance Parallel Architecture For Homomorphic Computing On Encrypted DataDocument12 pagesFPGA-based High-Performance Parallel Architecture For Homomorphic Computing On Encrypted DataMamal EtiNo ratings yet
- SC400Document2 pagesSC400lakbabi1035No ratings yet
- mchp001 Iiot Ebook FinalDocument43 pagesmchp001 Iiot Ebook Finalauerg1No ratings yet
- Cryptosec RKL Executive SummaryDocument14 pagesCryptosec RKL Executive SummaryRohit SinghNo ratings yet
- ArcSight ExpressDocument2 pagesArcSight Expressuwb_groupNo ratings yet
- Big Ip Platforms DatasheetDocument24 pagesBig Ip Platforms Datasheetspada1975No ratings yet
- Dspic™ Asymmetric Key Embedded Encryption Library: Execution TimeDocument2 pagesDspic™ Asymmetric Key Embedded Encryption Library: Execution TimeДрагиша Небитни ТрифуновићNo ratings yet
- Thales Host SecurityDocument6 pagesThales Host Securitysambasivam_saNo ratings yet
- Whitepaper - Vormetric Data Security PlatformDocument8 pagesWhitepaper - Vormetric Data Security PlatformgastonpantanaNo ratings yet
- 25j.rsa Public Key Cryptography Algorithm A ReviewDocument6 pages25j.rsa Public Key Cryptography Algorithm A ReviewAnousouya DeviNo ratings yet
- Fortanix DSM OnePage DatasheetDocument2 pagesFortanix DSM OnePage Datasheetvlado.vajdicNo ratings yet
- Deepcover Embedded Security SolutionsDocument11 pagesDeepcover Embedded Security SolutionsSteveliNo ratings yet
- Data Sheet: Security SoftwareDocument2 pagesData Sheet: Security Softwarealyson.balbinoNo ratings yet
- Li Rhel 8 Security Technology Brief f17208 201905 enDocument2 pagesLi Rhel 8 Security Technology Brief f17208 201905 ententNo ratings yet
- Secure Application Access HS5020 BrochureDocument5 pagesSecure Application Access HS5020 BrochureAjit Pratap KundanNo ratings yet
- Pay ShieldDocument2 pagesPay ShieldsdadsdNo ratings yet
- The Second Generation of IBM Hyper Protect PlatformDocument40 pagesThe Second Generation of IBM Hyper Protect PlatformYilma AbiyNo ratings yet
- Big-Ip System: Gain Agility With The Most Programmable Cloud-Ready AdcDocument18 pagesBig-Ip System: Gain Agility With The Most Programmable Cloud-Ready Adcm1gcrzNo ratings yet
- Sherwood-Gallo1990 Chapter TheApplicationOfSmartCardsForRDocument13 pagesSherwood-Gallo1990 Chapter TheApplicationOfSmartCardsForRRathnamNo ratings yet
- Sid800 DS 1109Document2 pagesSid800 DS 1109mbaezasotoNo ratings yet
- Thales PayShield 9000Document2 pagesThales PayShield 9000ramagimaNo ratings yet
- Excrypt SSP9000: FuturexDocument2 pagesExcrypt SSP9000: FuturexLee Chee SoonNo ratings yet
- Forti SIEMDocument13 pagesForti SIEMsteveNo ratings yet
- Forti SIEMDocument13 pagesForti SIEMAlex GranadosNo ratings yet
- FortiSIEM Series DatasheetDocument13 pagesFortiSIEM Series DatasheetmagnusfischerNo ratings yet
- Big Ip Platforms DatasheetDocument24 pagesBig Ip Platforms DatasheetFelipe Andres Palma BarrientosNo ratings yet
- SecureDongle - Software Protection DongleDocument4 pagesSecureDongle - Software Protection Donglecjsio100% (2)
- Thales Luna Pcie HSM 7 PBDocument3 pagesThales Luna Pcie HSM 7 PBAung Kyaw ThuNo ratings yet
- Network Engineer/security ArchitectDocument2 pagesNetwork Engineer/security Architectaami6No ratings yet
- IBM Spectrum Scale: Transparent Cloud Tiering Deep DiveDocument14 pagesIBM Spectrum Scale: Transparent Cloud Tiering Deep Divedaniel_vp21No ratings yet
- IBM Spectrum Scale Security - Firewall Overview - Storage SolutionsDocument14 pagesIBM Spectrum Scale Security - Firewall Overview - Storage Solutionsdaniel_vp21No ratings yet
- Ansible Automation SA Technical Deck Q2FY19Document43 pagesAnsible Automation SA Technical Deck Q2FY19daniel_vp21No ratings yet
- 08 ScaleCloudDeploymentsDocument37 pages08 ScaleCloudDeploymentsdaniel_vp21No ratings yet
- Transparent Cloud Tiering With Ibm Spectrum Scale: Proof of ConceptDocument12 pagesTransparent Cloud Tiering With Ibm Spectrum Scale: Proof of Conceptdaniel_vp21No ratings yet
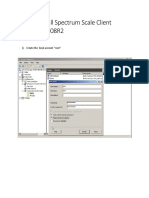
- Spectrum Scale Client Windows 2008R2Document36 pagesSpectrum Scale Client Windows 2008R2daniel_vp21No ratings yet
- DESY: Transparent Cloud Tiering Proof-of-ConceptDocument8 pagesDESY: Transparent Cloud Tiering Proof-of-Conceptdaniel_vp21No ratings yet
- System Health Monitoring and Problem DetectionDocument48 pagesSystem Health Monitoring and Problem Detectiondaniel_vp21No ratings yet
- Spectrum Scale Expert Talks: Episode 3Document30 pagesSpectrum Scale Expert Talks: Episode 3daniel_vp21No ratings yet
- SAS0569-2017 Shared File Systems - Determining The Best Choice For Your SAS Foundation - Has Spectrum Scale ChapterDocument11 pagesSAS0569-2017 Shared File Systems - Determining The Best Choice For Your SAS Foundation - Has Spectrum Scale Chapterdaniel_vp21No ratings yet
- 001 What Is New in IBM Spectrum Scale 5.0.5Document44 pages001 What Is New in IBM Spectrum Scale 5.0.5daniel_vp21No ratings yet
- SAS0569-2017 Shared File Systems - Determining The Best Choice For Your SAS Foundation - Has Spectrum Scale ChapterDocument11 pagesSAS0569-2017 Shared File Systems - Determining The Best Choice For Your SAS Foundation - Has Spectrum Scale Chapterdaniel_vp21No ratings yet
- Accelerate Insights With Sas 9.4 Deployed On Ibm Power9 and Ibm Flashsystem 9150Document9 pagesAccelerate Insights With Sas 9.4 Deployed On Ibm Power9 and Ibm Flashsystem 9150daniel_vp21No ratings yet
- SAS 9.3 Grid Deployment On IBM Power Servers With IBM XIV Storage System and IBM GPFSDocument40 pagesSAS 9.3 Grid Deployment On IBM Power Servers With IBM XIV Storage System and IBM GPFSdaniel_vp21No ratings yet
- SAS On IBM ESS Solution Brief Software Defined StorageDocument9 pagesSAS On IBM ESS Solution Brief Software Defined Storagedaniel_vp21No ratings yet
- Quick Reference Guide SAS With ESS: Unique Capability Main BenefitsDocument2 pagesQuick Reference Guide SAS With ESS: Unique Capability Main Benefitsdaniel_vp21No ratings yet
- SSUG19UK Day 2 02 Migrating Spectrum Scale Filesystems With Minimal DowntimeDocument24 pagesSSUG19UK Day 2 02 Migrating Spectrum Scale Filesystems With Minimal Downtimedaniel_vp21No ratings yet
- ALEX GpfsDocument33 pagesALEX Gpfsdaniel_vp21No ratings yet
- Power8 Technology Workshop: Daniel Villacorta Power Systems Consultant Ibm Systems Lab ServicesDocument45 pagesPower8 Technology Workshop: Daniel Villacorta Power Systems Consultant Ibm Systems Lab Servicesdaniel_vp21No ratings yet
- Introduction To The ABAP/4 Development Workbench: Sap AgDocument18 pagesIntroduction To The ABAP/4 Development Workbench: Sap AgandersonjardelNo ratings yet
- A Painless Guide To CRC Error Detection AlgorithmsDocument15 pagesA Painless Guide To CRC Error Detection Algorithmsva3ttnNo ratings yet
- What Is SQL?: Select "Column1" (,"column2",etc) From "Tablename" (Where "Condition") OptionalDocument16 pagesWhat Is SQL?: Select "Column1" (,"column2",etc) From "Tablename" (Where "Condition") OptionalЛенка КалабићNo ratings yet
- BackdoorDocument15 pagesBackdoortechNo ratings yet
- C Program Structure and Basic ElementsDocument12 pagesC Program Structure and Basic ElementsRana Sher AliNo ratings yet
- LP Solving a Linear Programming Model Problem using Excel-SolverDocument7 pagesLP Solving a Linear Programming Model Problem using Excel-SolverMilan LahiruNo ratings yet
- Design and Implementation of A Computerised Stadium Management Information SystemDocument33 pagesDesign and Implementation of A Computerised Stadium Management Information SystemBabatunde Ajibola TaofeekNo ratings yet
- Yozo LogDocument6 pagesYozo Logalim lutfiNo ratings yet
- Alternative SortingDocument9 pagesAlternative SortingpriyanjayNo ratings yet
- RDBMS Concepts and NormalizationDocument18 pagesRDBMS Concepts and NormalizationAlberto HernandezNo ratings yet
- Department of Electronics and Communication EngineeringDocument2 pagesDepartment of Electronics and Communication Engineeringece3a MITMNo ratings yet
- C++ Course WorkDocument10 pagesC++ Course Workishtiaq hussainNo ratings yet
- PCS 7 - Programming Instructions For BlocksDocument220 pagesPCS 7 - Programming Instructions For BlocksLucas Brant33% (3)
- Algorithm For Insertion in A Circular QueueDocument3 pagesAlgorithm For Insertion in A Circular QueuesatNo ratings yet
- Integrator - Workshop - Creating An Item Inbound Interface - UpdatedDocument11 pagesIntegrator - Workshop - Creating An Item Inbound Interface - UpdatedFrancisco MoralesNo ratings yet
- Lab Record StudentsDocument10 pagesLab Record StudentsSneha SruthiNo ratings yet
- 7d0a9ec5cef6b3ca8fc0f5d94f5ac2faDocument1,178 pages7d0a9ec5cef6b3ca8fc0f5d94f5ac2faسيد سعد100% (1)
- DSAP MFG BMBC Batch Information CockpitDocument19 pagesDSAP MFG BMBC Batch Information CockpitDeepak SinghNo ratings yet
- Commonly Asked Python Telephonic Interview QuestionsDocument6 pagesCommonly Asked Python Telephonic Interview Questionsnagub100% (1)
- IAR RefDocument137 pagesIAR RefDamianNo ratings yet
- Hibernate Material PDFDocument137 pagesHibernate Material PDFkasim50% (2)
- Data Types: Data Types Are Always Represent What Type of Data To BeDocument14 pagesData Types: Data Types Are Always Represent What Type of Data To BeNiranjanNo ratings yet
- The Federal Polytechnic, Ede School of Engineering TechnologyDocument2 pagesThe Federal Polytechnic, Ede School of Engineering TechnologyOlopade JohnNo ratings yet
- CME 4456 Reconfigurable Computing: Şerife YILMAZDocument72 pagesCME 4456 Reconfigurable Computing: Şerife YILMAZB. TNo ratings yet
- COAL Final - Fall20 (Solution)Document8 pagesCOAL Final - Fall20 (Solution)K213156 Syed Abdul RehmanNo ratings yet
- Hélder Gonçalves - Software EngineerDocument1 pageHélder Gonçalves - Software EngineerHélder GonçalvesNo ratings yet
- 2 - Process ManagementDocument143 pages2 - Process ManagementThanh HoàngNo ratings yet
- CakePHP Tutorial No. 4 From IBMDocument24 pagesCakePHP Tutorial No. 4 From IBMGerhard Sletten100% (35)
- PSCP MaterialDocument151 pagesPSCP MaterialS SriNo ratings yet
- NUST SMME Lab Report #3 on Fundamentals of ProgrammingDocument9 pagesNUST SMME Lab Report #3 on Fundamentals of ProgrammingAltafNo ratings yet