Professional Documents
Culture Documents
Elasticsearch - HTTPS and TLS Security
Uploaded by
brunoapollo5Original Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Elasticsearch - HTTPS and TLS Security
Uploaded by
brunoapollo5Copyright:
Available Formats
ELASTICSEARCH CLUSTER - HTTPS and TLS Security
Nodes IP Addresses:
Node1 - 192.168.56.111
Node2 - 192.168.56.112
Node3 - 192.168.56.113
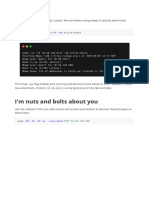
curl -X GET "localhost:9200/_cluster/health?pretty"
.::On Node 1::.
sudo su
cd /usr/share/elasticsearch
bin/elasticsearch-certutil ca
Enter
Enter
bin/elasticsearch-certutil cert --ca elastic-stack-ca.p12
Enter
Enter
Enter
mv elastic-certificates.p12 /etc/elasticsearch/
cd /etc/elasticsearch/
ls -ltr
nano /etc/elasticsearch/elasticsearch.yml
- Copy and paste following 5 lines in elasticsearch.yml file
xpack.security.enabled: true
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.verification_mode: certificate
xpack.security.transport.ssl.keystore.path: elastic-certificates.p12
xpack.security.transport.ssl.truststore.path: elastic-certificates.p12
chown root:elasticsearch /etc/elasticsearch/elastic-certificates.p12
chmod 660 /etc/elasticsearch/elastic-certificates.p12
Copy certificate to the other hosts
scp /etc/elasticsearch/elastic-certificates.p12
vagrant@192.168.56.112:/home/vagrant/
scp /etc/elasticsearch/elastic-certificates.p12
vagrant@192.168.56.113:/home/vagrant/
systemctl restart elasticsearch
.::On Node 2::.
sudo su
cp /home/vagrant/elastic-certificates.p12 /etc/elasticsearch/
nano /etc/elasticsearch/elasticsearch.yml
- Copy and paste following 5 lines in elasticsearch.yml file
xpack.security.enabled: true
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.verification_mode: certificate
xpack.security.transport.ssl.keystore.path: elastic-certificates.p12
xpack.security.transport.ssl.truststore.path: elastic-certificates.p12
chown root:elasticsearch /etc/elasticsearch/elastic-certificates.p12
chmod 660 /etc/elasticsearch/elastic-certificates.p12
systemctl restart elasticsearch
.::On Node 3::.
sudo su
cp /home/vagrant/elastic-certificates.p12 /etc/elasticsearch/
nano /etc/elasticsearch/elasticsearch.yml
- Copy and paste following 5 lines in elasticsearch.yml file
xpack.security.enabled: true
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.verification_mode: certificate
xpack.security.transport.ssl.keystore.path: elastic-certificates.p12
xpack.security.transport.ssl.truststore.path: elastic-certificates.p12
chown root:elasticsearch /etc/elasticsearch/elastic-certificates.p12
chmod 660 /etc/elasticsearch/elastic-certificates.p12
systemctl restart elasticsearch
- Set passwords for default users
cd /usr/share/elasticsearch
bin/elasticsearch-setup-passwords interactive
demo passwords:
elastic:elastic
apm_system:apmsystem
kibana:kibana
logstash_system:logstash
beats_system:beatssystem
remote_monitoring_user:remotemonitoring
- you can generate random passwords automatic using following command
bin/elasticsearch-setup-passwords auto
- be sure that you will remember them
Test cluster health:
curl -u elastic:elastic -X GET "localhost:9200/_cluster/health?pretty"
Enter this ADDITIONAL 4 lines in elasticsearch.yml file on every node to eneble
HTTPS:
nano /etc/elasticsearch/elasticsearch.yml
xpack.security.http.ssl.enabled: true
xpack.security.http.ssl.keystore.path: elastic-certificates.p12
xpack.security.http.ssl.truststore.path: elastic-certificates.p12
xpack.security.http.ssl.client_authentication: optional
systemctl restart elasticsearch
Configure Kibana on Node 3
cd /etc/elasticsearch/
openssl pkcs12 -in elastic-certificates.p12 -out newfile.crt.pem -clcerts -nokeys
Enter
openssl pkcs12 -in elastic-certificates.p12 -out newfile.key.pem -nocerts -nodes
Enter
mv newfile.* /etc/kibana
cd /etc/kibana
ls -ltr
chown root:kibana /etc/kibana/newfile*
chmod 660 /etc/kibana/newfile*
nano /etc/kibana/kibana.yml
Put this lines into the file
elasticsearch.hosts: ["https://localhost:9200"]
elasticsearch.username: "kibana"
elasticsearch.password: "kibana"
server.ssl.enabled: true
server.ssl.certificate: /etc/kibana/newfile.crt.pem
server.ssl.key: /etc/kibana/newfile.key.pem
elasticsearch.ssl.verificationMode: none
systemctl restart kibana
https://192.168.56.113:5601/
Logstash on Node 3
cd /home/vagrant/
curl https://artifacts.elastic.co/downloads/logstash/logstash-7.9.0.rpm -o
logstash-7.9.0.rpm
yum -y install java
rpm -i logstash-7.9.0.rpm
cp /etc/kibana/newfile.crt.pem /etc/logstash/newfile.crt.pem
chown root:logstash /etc/logstash/newfile.crt.pem
chmod 660 /etc/logstash/newfile.crt.pem
nano /etc/logstash/pipelines.yml
Replace default pipeline:
- pipeline.id: test
path.config: "/etc/logstash/conf.d/testpipe.conf"
Create conf file for the pipeline:
nano /etc/logstash/conf.d/testpipe.conf
Put these lines on it:
==========================================================================
input {
beats {
host => "192.168.56.113"
port => "5033"
}
}
#filter {
#}
output {
elasticsearch {
hosts => "https://localhost:9200"
index => "estack-test-pipeline-index"
user => "elastic"
password => "elastic"
cacert => "/etc/logstash/newfile.crt.pem"
ssl_certificate_verification => false
}
}
==========================================================================
systemctl start logstash
Check the log file to see that everything looks good maybe it will take a while
for logstash to create the file(depending on VM resources)
tail -f /var/log/logstash/logstash-plain.log
Filebeat Configuration(Windows)
Download this example apachelogs.log file
Link - https://mega.nz/file/jGJDEQjZ#sceYkyaCo7GXiw2ncK3xVLBdfCP1OSXzqKkFTWC8--A
Download ready for using filebeat.zip file.
Link - https://mega.nz/file/ODQnGajR#1jgjFVqn5Z_hPOTTO7NXKqQ8n8NNouLhbr2otTYfR8Q
Create "logs" folder on your desktop and change the path in the filebeat.yml file
with your username.
ex: - C:\Users\YourUsername\Desktop\logs\*.log
Open PowerShell like an administrator and execute following commands:
cd 'C:\Program Files\filebeat\' - or your filebeat installation directory
.\filebeat.exe -c filebeat.yml -e -d "*"
You might also like
- Wazuh With ELK GuideDocument11 pagesWazuh With ELK Guidelets testNo ratings yet
- Configuring Transparent Web Proxy Using Squid 2Document4 pagesConfiguring Transparent Web Proxy Using Squid 2agunggumilarNo ratings yet
- OffshoreDocument8 pagesOffshoreMatthias100% (1)
- Database Cache: Hazelcast Rediscache RabbitmqDocument16 pagesDatabase Cache: Hazelcast Rediscache RabbitmqDoNo ratings yet
- Server SetupDocument6 pagesServer SetupSahil ThakurNo ratings yet
- Documentasi Mail OpsDocument29 pagesDocumentasi Mail OpsKemal Rizky WahyudiNo ratings yet
- CBIS OverCloud Deploy MOPDocument37 pagesCBIS OverCloud Deploy MOPBABA ROSHAN0% (1)
- Croossclue Ster SSLDocument2 pagesCroossclue Ster SSLKupluk KesonoNo ratings yet
- Install Squid Proxy Server On CentOSDocument5 pagesInstall Squid Proxy Server On CentOSMir Farhan Ali AbediNo ratings yet
- WazuhDocument28 pagesWazuhencryptedsideNo ratings yet
- STB After InstallDocument4 pagesSTB After Installsusantostarcom03No ratings yet
- Nouveau Document TexteDocument14 pagesNouveau Document TexteMANAÏ BelighNo ratings yet
- Attackive DirectoryDocument6 pagesAttackive Directorypikafou34No ratings yet
- Broker MachineDocument7 pagesBroker Machinelorenpato08No ratings yet
- Cara Install Lusca - Head r14809 Ubuntu 11.10-OkDocument13 pagesCara Install Lusca - Head r14809 Ubuntu 11.10-OkHos NetNo ratings yet
- Installing On CentOS 7Document10 pagesInstalling On CentOS 7leandroNo ratings yet
- Steps To Add A Node in Oracle RAC 19cDocument35 pagesSteps To Add A Node in Oracle RAC 19cgeteagletNo ratings yet
- Rhce7 3Document13 pagesRhce7 3Harshal Tapadiya100% (3)
- Mop ZTSDocument7 pagesMop ZTSManoj KumarNo ratings yet
- Yum Install Glibc.i686 Yum Install XauthDocument43 pagesYum Install Glibc.i686 Yum Install XauthPavankumar BollaNo ratings yet
- OSCP NotesDocument78 pagesOSCP Notesralikdgp100% (3)
- Cloudera Installation - 5.11.1 (Using Parcels)Document18 pagesCloudera Installation - 5.11.1 (Using Parcels)JENIFA JEYAKUMARNo ratings yet
- Team BasicsforEngineer 220920 0333 1720 PDFDocument13 pagesTeam BasicsforEngineer 220920 0333 1720 PDFarunasirigereNo ratings yet
- OSCP NotesDocument78 pagesOSCP NotesRocKet100% (1)
- 389 Directory ServerDocument24 pages389 Directory ServerRajMohenNo ratings yet
- Squid Installation & ConfigurationDocument6 pagesSquid Installation & ConfigurationSunil KumarNo ratings yet
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityFrom EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityNo ratings yet
- Cara Install Lusca - Head r14809 Ubuntu 11.10-OkDocument13 pagesCara Install Lusca - Head r14809 Ubuntu 11.10-OkvictriciaNo ratings yet
- Cacti Install CentosDocument16 pagesCacti Install Centosmilos_arNo ratings yet
- UbuntuserverDocument3 pagesUbuntuserverNurul MuhlisinNo ratings yet
- Component Pack 6.0.0.6 Installation Guide: Martti Garden - IBM Roberto Boccadoro - ELD EngineeringDocument11 pagesComponent Pack 6.0.0.6 Installation Guide: Martti Garden - IBM Roberto Boccadoro - ELD Engineeringabdul1982No ratings yet
- Install SSL On Ubuntu and Enable HTTPSDocument3 pagesInstall SSL On Ubuntu and Enable HTTPSkomarudin.sNo ratings yet
- SONARQUBE52 RunningSonarQubeOverHTTPS 230220 0034 26589Document3 pagesSONARQUBE52 RunningSonarQubeOverHTTPS 230220 0034 26589Warren AroniNo ratings yet
- Workshop Openstack 15 April 2015Document27 pagesWorkshop Openstack 15 April 2015Ady SaputraNo ratings yet
- Panduan Install Security Mail Server KasperskyDocument7 pagesPanduan Install Security Mail Server KasperskyAhmad MaulanaNo ratings yet
- Devops FilesDocument9 pagesDevops Filessweetha sweethaNo ratings yet
- Continuous Kubernetes Security PDFDocument113 pagesContinuous Kubernetes Security PDFtanmayNo ratings yet
- Enable SSL LabDocument3 pagesEnable SSL Labbenben08No ratings yet
- OscpDocument3 pagesOscpbxx31426No ratings yet
- Encrypting Voice Calls in Elastix and Fail2banDocument8 pagesEncrypting Voice Calls in Elastix and Fail2banGodspower InibuNo ratings yet
- Matrix Synapse-4-6Document3 pagesMatrix Synapse-4-6Andrey QuesadaNo ratings yet
- Practicals 3Document5 pagesPracticals 3Tarik AmezianeNo ratings yet
- Note D Án 1Document792 pagesNote D Án 1thaingochieuNo ratings yet
- 11g Rac InstallationDocument63 pages11g Rac Installationjay karandikarNo ratings yet
- Google Code Archive - Long-Term Storage For Google Code Project HostingDocument33 pagesGoogle Code Archive - Long-Term Storage For Google Code Project HostingOsmanNo ratings yet
- 5 Labs Certificado SSL ResolucionDocument3 pages5 Labs Certificado SSL ResolucionGuillermo WilliamsNo ratings yet
- MapR InstallationDocument6 pagesMapR InstallationKali VaraprasadNo ratings yet
- RastaDocument7 pagesRastawhateverNo ratings yet
- ConfigurationDocument7 pagesConfigurationPratik SanasNo ratings yet
- Lsa Sle ProjDocument41 pagesLsa Sle Projjaygautam1710No ratings yet
- MPDFDocument91 pagesMPDFBøù HóúNo ratings yet
- HOW TO INSTALL ASTERISK On Debian 8.1Document15 pagesHOW TO INSTALL ASTERISK On Debian 8.1enamul whabNo ratings yet
- EX294Document16 pagesEX294Deniz YaşarNo ratings yet
- Setting Up An SSL Server With Apache2Document4 pagesSetting Up An SSL Server With Apache2mathyieNo ratings yet
- Oracle Database WebLogic IDM JasperReports HowtoDocument21 pagesOracle Database WebLogic IDM JasperReports HowtoAlma BasicNo ratings yet
- Sette Opp OpenVPN - ECU-1051TLDocument7 pagesSette Opp OpenVPN - ECU-1051TLNguyễn Văn TânNo ratings yet
- Cloud - AWS PentestDocument55 pagesCloud - AWS PentestkhlifiNo ratings yet
- Docker ComposeDocument3 pagesDocker ComposeAlvian RizaldiNo ratings yet
- Check Proxy Will Be Working or NotDocument5 pagesCheck Proxy Will Be Working or NotRamesh VankaNo ratings yet
- Dante HTB This One Is Documentation of Pro Labs HTBDocument131 pagesDante HTB This One Is Documentation of Pro Labs HTBkhocchonguoithuong9999100% (2)
- Data Security Best PracticesDocument20 pagesData Security Best Practiceshim2000himNo ratings yet
- Translation Quality Assessment: Joss Moorkens Sheila Castilho Federico Gaspari Stephen Doherty EditorsDocument292 pagesTranslation Quality Assessment: Joss Moorkens Sheila Castilho Federico Gaspari Stephen Doherty EditorsTaha AkdağNo ratings yet
- Felix Mabanta: Executive SummaryDocument4 pagesFelix Mabanta: Executive SummaryFelix MabantaNo ratings yet
- Diagrama Motor c9Document2 pagesDiagrama Motor c9Juan Pablo Leon Ruales83% (6)
- Fyp 1Document26 pagesFyp 1Taha RahatNo ratings yet
- Ehealth Standards and Profiles in For Europe and BeyondDocument60 pagesEhealth Standards and Profiles in For Europe and BeyondAntónio FerreiraNo ratings yet
- Smartstep Full User Guide v4Document38 pagesSmartstep Full User Guide v4Erick MendezNo ratings yet
- Commvault Scaleprotect WPDocument138 pagesCommvault Scaleprotect WPhherNo ratings yet
- Docker Trusted RegistryDocument4 pagesDocker Trusted RegistryNagasiva Manohar ReddyNo ratings yet
- General Specifications - YTA110 Temperature Transmitter HART Communication PDFDocument2 pagesGeneral Specifications - YTA110 Temperature Transmitter HART Communication PDFcbaliveNo ratings yet
- Installation Guide: What You Need To Get StartedDocument12 pagesInstallation Guide: What You Need To Get StartedKapila WijayaratneNo ratings yet
- Bucket Hydraulic System: Operación de SistemasDocument4 pagesBucket Hydraulic System: Operación de SistemasvidalNo ratings yet
- ManojDocument2 pagesManojgarapati anilkumar garapati anilkumarNo ratings yet
- Vinay Front-Converted (1) - MergedDocument46 pagesVinay Front-Converted (1) - MergedSGVU UniversityNo ratings yet
- Central - South - Amer - Base Plus HW - Shade - 007 - 012019Document441 pagesCentral - South - Amer - Base Plus HW - Shade - 007 - 012019David OsorioNo ratings yet
- A Survey On Real Time Bus Monitoring SystemDocument4 pagesA Survey On Real Time Bus Monitoring SystemAnonymous CUPykm6DZNo ratings yet
- Cách Cài Di ToolDocument22 pagesCách Cài Di ToolVĩ ĐặngNo ratings yet
- Trimurti Fabricators PVT LTD.: Monsoon Protection PlanDocument4 pagesTrimurti Fabricators PVT LTD.: Monsoon Protection Planalla malikNo ratings yet
- Service Support Quick ReferenceDocument3 pagesService Support Quick ReferencemrcyberNo ratings yet
- cdd124674-PLANO ELECTRICO D6N XLDocument4 pagescdd124674-PLANO ELECTRICO D6N XLPaola MuñozNo ratings yet
- iSWACO ARGUSDocument4 pagesiSWACO ARGUSfahmi1987No ratings yet
- Computer Studies 2ND Term Lesson NoteDocument11 pagesComputer Studies 2ND Term Lesson NotelordsenoxNo ratings yet
- Manual Fanuc LTD Serie 21 y 210 Modelo BDocument416 pagesManual Fanuc LTD Serie 21 y 210 Modelo BEmmanuel MontemayorNo ratings yet
- IMsbUserGuide PDFDocument41 pagesIMsbUserGuide PDFAnonymous 271ZkAHXXNo ratings yet
- SFF ListDocument46 pagesSFF ListBruno Pérez GarcíaNo ratings yet
- 1 - PAN Terminal Server Agent Install StepsDocument6 pages1 - PAN Terminal Server Agent Install StepsMaciej WaliszkoNo ratings yet
- CM400DX1-24A: Details PDFDocument1 pageCM400DX1-24A: Details PDFSergio MuriloNo ratings yet
- Air - Fuel Ratio Tuning - Rich Vs Lean - TurbobygarrettDocument2 pagesAir - Fuel Ratio Tuning - Rich Vs Lean - TurbobygarrettDhirendra DubeyNo ratings yet
- Global Positioning System (GPS)Document34 pagesGlobal Positioning System (GPS)Samir2020No ratings yet
- 3 Axis Milling Machine PDFDocument5 pages3 Axis Milling Machine PDFAnuj MathurNo ratings yet