Professional Documents
Culture Documents
IT Proposal Document To Tech Linx No2-Rmy
Uploaded by
Rahiman Mat YassimOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
IT Proposal Document To Tech Linx No2-Rmy
Uploaded by
Rahiman Mat YassimCopyright:
Available Formats
Table of Contents
Abbreviations
1.0 Introduction
1.1 Purpose
1.2 The Project
1.3 Development Design Philosophy
1.4 Design Criteria
1.5 General Scope
1.6 This Report
2.0 Information Communication Technology (ICT)
2.1 Information Communication Technology Concept
2.1.1 Flexible and Cost Effective
2.1.2 Efficiency of Systems
2.1.3 Simplicity
2.1.4 Reliability
2.1.5 Services at Hand
2.1.6 Information Communication Technology
2.2 Horizontal Cabling System
2.2.1 Background
2.2.2 Information Outlet and Workstation Connectivity
2.2.3 Horizontal Cables and Distribution
2.2.4 Cable Termination Panels
2.3 Voice Backbone Cabling System
2.4 Data Network Backbone Cabling System
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 1 of 90
2.5 Networking Equipment and Software
2.5.1 Routers
2.5.2 Switches
2.5.3 Modems
2.5.4 Server and Softwares
2.6 Wide Area Network (WAN) Access System
2.7 Private Communication Exchange (PCX) System
2.7.1 PCX Components
2.7.2 PCX Main Equipment
2.7.3 Proprietary Public Branch Exchange (PBX)
2.7.4 Computer Telephony (CT) Technology
2.8 Network Security System
2.8.1 Introduction
2.8.2 Internet Access Security
2.8.3 LAN Security
2.8.4 Screening Router
2.8.5 Firewall Deployment
2.8.6 Network Monitoring and Intrusion Detection
2.8.7 Vulnerability Scanner
2.8.8 User Authentication
2.8.9 Virus Protection
2.8.10 Encrypted Links
2.8.11 Server / System Security
2.8.12 SNMP and Network Managament
2.8.13 High Availability
2.8.14 Tenant VLANs
2.8.15 Security Policy
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 2 of 90
3.0 Integrated Building Management System (IBMS)
3.1 Background Information
3.1.1 Intelligent Building and Information Communication Technology System
3.1.2 Flexibility for the Future
3.1.3 System Integration
3.1.4 Interaction Between Intelligent Building Systems
3.1.4.1 Building Automation System
3.1.4.2 Building Integrated Security System
3.1.4.3 Intelligent Fire Alarm System
3.2 Intelligent Building Management System (IBMS) Equipment
3.2.1 Integration LAN
3.2.2 Operation Workstations
3.2.3 Power Line Filtering
3.2.4 Uninterruptible Power Supply (UPS)
3.2.5 Remote Operator’s Workstation (ROW)
3.2.6 Lobby Security / Information Desk
3.2.7 Operator Interface
3.2.8 Application Software Packages
3.2.9 Reports
3.2.10 Point Database
3.2.11 Maintenance Management and Inventory Control (MMIC) Workstation
3.2.12 Response Time
3.3 Building Automation System (BAS)
3.3.1 BAS Functions
3.3.2 Proposed System Topology
3.3.3 Proposed Application Software Packages
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 3 of 90
3.4 Air Conditioning and Lighting Control
3.4.1 Air Conditioning Control General
3.4.2 Modes of Operation
3.4.3 Determination of the Occupied / Unoccupied Mode
3.4.4 Lighting Control
3.5 Building Security System (BSS)
3.5.1 Overview
3.5.2 Tenant and on Floor Spaces
3.5.3 Normal Hours Access
3.5.4 Lighting
3.5.5 System Components
3.5.6 Access Control and Monitoring System (ACMS)
3.5.7 Access Controller
3.5.8 Sensors
3.5.9 Voice Intercom System (VIS)
3.5.10 Closed Circuit Television System (CCTV)
3.5.11 Interior Fixed Cameras
3.5.12 Exterior Fixed Cameras
3.5.13 Pan-Tilt-Zoom Cameras with Exterior Housing
3.5.14 Video Motion Detection
3.5.15 Digital Image Storage
3.5.16 Sound Masking
3.5.17 Letter Bomb Detector
3.5.18 Interaction with other Security Devices
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 4 of 90
4.0 General Considerations
4.1 Operational Considerations
4.1.1 Surge Voltage Protection System
4.1.2 Earthing Protection System
4.1.3 Fire Protection System
4.1.4 Electro Magnetic Interference Protection System
4.1.5 Protection Against Vandalism
4.1.6 Uninterrupted Power Supply (UPS) System
4.2 Preparatory Base Building Works
4.2.1 Electrical Works
4.2.2 Mechanical Works
4.2.3 Architectural Works
4.3 IBMS Contract and Potential Sub Contractors
4.3.1 IBMS Contract Document
4.3.2 Potential IBMS Contractor
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 5 of 90
Appendices
Appendix A Proposal 1
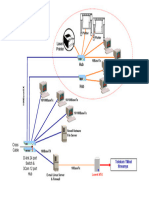
Information Outlet User Matrix for Data and Voice
Appendix B Proposal 1
Data & Voice Connection to Workstation for Open Plan Area with Access Flooring System
Appendix C Proposal 1
Data & Voice Connection to Workstation for Area without Access Flooring System
Appendix D Proposal 1
Data & Voice Horizontal Cabling Distribution for Open Plan Area with Access Flooring System
Appendix E Proposal 1
Data & Voice Main Feeder Cabling System Schematic (Type A)
Appendix F Proposal 1
Data & Voice Main Feeder Cabling System (Type A)
Appendix G Proposal 1
Data & Voice Main Feeder Cabling System Schematic (Type B)
Appendix H Proposal 1
Data & Voice Main Feeder Cabling System (Type B)
Appendix I Proposal 1
Data & Voice Main Feeder Cabling System (Type B)
Appendix J Proposal 1
Data & Voice Main Feeder Cabling System (Type B)
Appendix K Proposal 1
Proposed Telecommunication Raceways at Basement Level
Appendix L Proposal 1
Proposed Telecommunication Raceways at Level 1
Appendix M Proposal 1
Proposed Telecommunication Raceways at Level 2
Appendix N Proposal 1
Proposed Telecommunication Raceways at Level 3
Appendix O Proposal 1
Proposed Telecommunication Raceways at Level 4
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 6 of 90
Appendix P Proposal 1
Proposed Communication and Telephone Closet Arrangement
And Typical Main Raceways Cross Section
Appendix Q Proposal 1
Proposed Networking Switches
Appendix R Proposal 1
Proposed Networking Security System Installation
Appendix S Proposal 1
Proposed Interactions Between Intelligent Building Systems
Appendix T Proposal 1
Proposed IBMS Topology
Appendix U Proposal 1
Proposed BAS Topology
Appendix V Proposal 1
Proposed Integrated Security System
Appendix W Proposal 1
Proposed Central Command Room Layout
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 7 of 90
ABBREVIATIONS I.D. - Identification PSTN - Private Service Telephone Network
I/O - Input / Output ROW - Remote Operator’s Workstation
A/C - Air Conditioning
IBMS - Intelligent Building Management System SNMP - Simple Network Management Protocol
AA - Automated Attendant
IDS - Intrusion detection System SSH - Secure Shell
AAS - Audio Alarm System
IO - Information Outlets SSL - Secure Socket layer
ACD - Automated Call Distribution
IP - Internet Protocol TCP/IP - Transmission Control Protocol/Internet
ACMS - Access Control and Monitoring System
ISDN - Integrated Service Digital Network Protocol
AHU - Air Handler Unit
ISP - Internet Service Provider TP - Terminal Portability
AI/AO - Analog Input / Analog Output
IT - Information Technology UC - Unitary Controllers
Apps Server - Application Server
IVR - Interactive Voice Response USB - Universal Serial Bus
ASCII - American Standard Character Set II
LAN - Local Area Networks, UTP - Unshielded Twisted Pair cable
ATM - Asychronous Transfer Mode
LAN - Local Area Network VLAN - Virtual LAN
BAS - Building Automation System
LCD - Liquid Crystal Display VOIP - Voice Over IP
BRI - Basic Rate Interface
LCMS - Lift Control and Monitoring System WAN - Wide Area Network
BSS - Building Integrated Security System
LCS - Lighting Control System
CCD - Charge Coupled Device
LED - Light Emitting Diode
CCR - Central Control Room
LIU - Lightguide Interconnect Unit
CCTV - Closed Circuit Television
Mbps - Mega bits per second
CLIP - Caller Line Identification Presentation
MEP - Mechanical Electrical Plumbing
CRM - Customer Relationship Management
mm - Millimeters
CT - Computer Telephony
MMI - Man Machine Interfaces
DAT - Digital Audio Tape
MMIC - Maintenance management and inventory
DB Server - Database Server
control
DCP - Distributed Control Panels
MSN - Multiple Subscriber Number
DD - Design Development
NT - Network Termination Unit
DDI - Direct Dialling In
OS - Operating System
DI/DO - Digital Input / Digital Output
PABX - Private Access Branch Exchange
DMZ - De Militarized Zone
PC - Personal Computer
ELV - Extra Low Voltage
PCS - Parking Control System
FAS - Building Intelligent Fire Alarm System
PCX - Private Communication Exchange
FPTU - Fan Powered Terminal Unit
POS - Point of Sale system
Gbs - Giga bits per second
PRI - Primary Rate Interface
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 8 of 90
1.0 INTRODUCTION
1.1 Purpose
This Initial Concept Report has been undertaken by BK Consulting (BKC) at the request of Tech-Linx and is the
first stage of the design process for the Intelligent Building Systems and their integration with one another and
with the Information Communication Technology (ICT) systems. In addition to the technical requirements, this
report also addresses certain operational and architectural issues and is intended to be a discussion document
in order to obtain Tech-Linx’s feedback on their aspiration and requirements prior to BKC completing the
Schematic Designs.
Once the feedback on this report has been obtained the schematic designs will be further progressed and it is
proposed that in late February / early March that the Schematic Designs are presented to the Owner,
potentially at their headquarters in Dresden.
1.2 The Project
Tech-Linx is developing a state of the art technology park at Cyberjaya in the Multi-Media Super Corridor that
extends from Kuala Lumpur City Centre to the new airport. The new development will comprise five office
buildings and an auditorium building together with a 1,300m 2 car park. Total net sq. ft. of the office buildings
is 22,210 m2. Tech-Linx will relocate the present offices of Net-Linx from the Petronas Towers in Kuala Lumpur
City Centre to the new development and will create modern office space for other leading technology based
companies.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 9 of 90
1.3 Development Design Philosophy
We see that there are two fundamental objectives for the development of Tech-Linx Technology Park at
Cyberjaya.
To create an excellent working environment for the employees of Tech-Linx’s associated
companies and hence maximise the productivity and creativity of the employees resulting in
increased profitability; and
As a result of creating an excellent working environment it will attract high-class companies to
be tenants paying goods rentals, thus maximising Tech-Linx’s return on investment.
In this modern world it is therefore not only necessary to have Architecture of the highest quality, but also the
building must provide the best possible communication, controls and security systems to create an excellent
and efficient working environment.
Hence as part of the state of the art Technology Park, Tech-Linx require that there should be substantial
integration of the microprocessor based building control system in such a way that meet the needs of the
Owner and their tenants in the present and have the built in flexibility to accommodate future changes in both
building use and technology.
In this report we have therefore covered a vast spectrum of potential systems that could be installed to meet
this objective.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 10 of 90
However, to ensure that the capital cost of these systems is efficiently invested, before finalising the designs it
must always remembered that:
The system must be practical and relevant
That there are, a far as possible, expandable / adaptable to accommodate future technology:
and
That the operators and end users are trained properly to use them
Unfortunately, in the past, there have been too many examples where ay only 10% of the available features
are used which has resulted from either over specification or lack of training.
The ultimate gauge of the success of the technology systems being designed and installed will be the amount
and effectiveness of their usage.
1.4 Design Criteria
In line with the Development Design Philosophy when formulating the overall program for Tech-Linx
Technology Park, the following design criteria are considered applicable:
The computer based building monitoring and control systems will be designed in accordance
with generally accepted “Intelligent Building” concepts.
The systems facilities will be modular, flexible and expandable such that they may be readily
enhanced or modified as may be required in the future.
All installations will be made in a neat and workmanlike manner giving due consideration to the
character, use and architectural aesthetics of the complex.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 11 of 90
The installations will be planned with a view to optimising the effective use of personnel by
functionally integrating systems operations.
Individual elements of the installations will be, as far as reasonably possible, contractor
independent such that they may be multi-sourced in the future.
Energy conservation will be a major aspect of the systems designs.
The operator interfaces with the systems will be "user friendly" and will be such as to simplify, as
far as reasonably possible, the task of operator training and acceptance.
Individual installations will be functionally engineered and, installed using premium commercial
grade components so as to minimize their associated potential long-term maintenance cost
implications.
A single BAS will serve all five buildings and auditorium.
A single BSS will serve all five buildings and auditorium. The major components of the BSS will
be the Voice Intercom System (VIS), the Access Control and Monitoring System (ACMS), the
Closed Circuit Television (CCTV) system and the Parking Control System (PCS).
A single parking system will be provided as part of the BSS. We have assumed that this will not
be a revenue system and that access will be restricted to tenants.
Lift control will be via the ACMS component of the BSS. We have assumed that a separate lift
control system will be provided for each building.
A single Central Control Room (CCR), located in the Net-Linx building, will serve the entire
complex for the functions performed by the IBMS.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 12 of 90
1.5 General Scope
BKC will be responsible for the design of the Building Automation System (BAS), the Building Security System
(BSS), the ICT systems and the integration of various extra low voltage systems. Norman Disney Young (NDY)
will undertake the design of the electrical and mechanical systems and the Fire Alarm System (FAS). BKC will
also be responsible for the production of the performance specifications for the audiovisual equipment.
We will coordinate with NDY to ensure FAS specification which is being prepared by them will be compatible
with the requirements for integration with other extra low voltage systems. The communication between the
FAS and other extra low voltage systems will be unidirectional with all data transmission emanating from the
FAS.
The lift control system will be specified by NDY and will be coordinated with BKC to ensure that the lifts are
designed to accommodate an access control system.
1.6 This Report
In the following sections of this report we describe the concepts and initial ideas for
The Integrated Building Management System
The Information Communication Technology Systems
Some General Considerations
The report does not cover the performance specification for the Audio Visual Equipment nor the details of the
Net-Linx occupied space, which shall be subsequently developed once the requirement’s become more clearly
defined.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 13 of 90
2.0 INFORMATION COMMUNICATION TECHNOLOGY
2.1 Information Communication Technology Concept
2.1.1 Flexible and Cost Effective
The building systems are adaptable to different technologies and user needs without incurring too much
difficulty and cost
2.1.2 Efficiency of Systems
Management, maintenance, operation and services of the building systems are cost effective, efficient, reliable
and environment-friendly. From the high efficiency of system it will create a productive work. This will reduce
the cost of operation. Indirectly it will save company expenses. This will give high output to the production and
at the same time give a good input to the production capabilities. This factor needs to be synchronized with
the human factor. All the systems are tools to make life easier.
2.1.3 Simplicity
This is the key factor to make sure the system is adopted and utilized to its fullest extent. This is a human
factor people always want something simple & effective.
2.1.4 Reliability
The design of the system should have an element of redundancy to create reliability. A stable system will
ensure that daily operations are running without disruption. In another words ZERO DOWNTIME. Unstable
systems are the single biggest contributor to lost production. It is essential that the networks employed on this
installation are certified and managed properly.
2.1.5 Services at Hand
Users anywhere, internal or external to the building, can access any of the services on-line which are provided
from within or outside the building, observing all access and security restrictions.
2.1.6 Information Communication Technology
Most organisations are moving towards ICT. Information delivery is the key to making the right decisions with
the highly informative data and the latest update now available all over the world.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 14 of 90
ICT needs the right infrastructure. The infrastructure consists of: -
Circuit connectivity
Network Equipment (Active Equipment)
Hardware
Software
Information System Management
System Administrator
2.1.6.1 Circuit connectivity
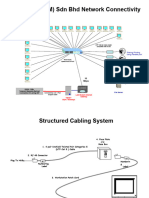
The Physical layer which is the structured cabling system. The main medium is copper cable and the Fiber
Optic cable. All the building will be wired with Fiber Optic Cable for the Backbone. For the workstation outlets it
will be copper cable. The copper cabling is referred to as the Horizontal cabling system.
2.1.6.2 Network Equipment (Active Equipment)
Network Equipment is the sharing device in between the all workstations or the device sensor. All the data
from the outlet will interconnect and flow into the network equipment, which is called a switch. This data is in a
packet format. This packet will travel from one point to another point. This switch needs to have the capability
to handle the amount of data generated on the site. The volume of data transfer is measured in bits per
second. 10mbps / 100mbps/1Gbps are the most popular bandwidths available in the telecommunication
industry today. Most of the Closed Circuit Television (CCTV), Personal Communication Exchange (PCX),
Computer System, Door Access Control System, Fire Alarm, Air-Con system and Building Automation System
(BAS) are based on Ethernet Switching Technology to communicate and transfer data for monitoring,
controlling and management of the system.
2.1.6.3 Hardware
Hardware is the devices such as Personal Computer, Server for Database, Printer, Scanner, Personal Digital
Assistant (PDA) and Video Conference Camera. All hardware will have their own software to operate, which are
known as drivers. These drivers will communicate with the device in order to get the input & output that is
needed by the users.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 15 of 90
2.1.6.4 Software
Software is the Programme for the application such as word processing for letter and documents, Spread
Sheets for data calculation, Database Systems, Accounting Software, Payroll for Human Resource. Basic Office
applications come in Packages such as Microsoft Office 2000 and Lotus Smart Suite.
The Network Monitoring system is a part of the software. This application monitosr the traffic, connectivity in
between the devices and the load of the traffic in the system. The purpose of this software is to monitor the
system and alert the system administrator to take the necessary action. By having this it will reduce the
downtime as much as possible.
2.1.6.5 Information Management System (IMS)
The Information Management System function is to maintain, monitor and manage the Information
Communication Technology in the organization. This Unit or Department will be the Team to manage, make
sure the policies of the company will be followed by the users. This team will be responsible to determine the
ICT Road Map for future requirements. A part of that team need to support the users in terms of training,
troubleshooting and operational procedures.
2.1.6.6 System Administrator (SA)
The System Administrator is the person who is in charge of the IMS. The Administrator has to protect and
maintain all the information in systems. They need to take the necessary action to avoid breakdown of the
network. The SA should have a sound knowledge of networking and recognise the threat posed by virus attach
and hackers which is becoming more prevalent today.
The following ICT sub-systems will be described in this report.
Horizontal cabling system using copper solution
Data network backbone cabling system using fiber optic solution
Voice backbone cabling system using copper cables
Networking equipments and softwares
Wide Area Network (WAN) connectivity
Private Communication Exchange (PCX) and telecommunication equipment.
Network Security System
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 16 of 90
2.2 Horizontal Cabling System
2.2.1 Background
Horizontal Cabling system is the connectivity from the Centre sharing device (Switch/Hub) to each computer
called a workstation. The length of the cable (channel length inclusive of patch cords at both ends) must be
equal or less than 100 meter according to ISO 11801, TIA/EIA 586 standard.
The proposed horizontal cabling system shall comply with the enhanced Category 5 channel requirement and
be tested to minimum 250MHz bandwidth using a copper solution and shall be able to support future Gigabit
Ethernet applications to the desktop with possible zero bit error. The horizontal copper cable shall be limited to
90 meter running distance for basic link. All components shall use single manufacturer approved and tested
products to facilitate in getting full certification and multi-years warranty.
Since the standards for Category 6 channel requirement is yet to be established, the proposal is based on the
current market approved available products.
The horizontal cabling system shall comprise of the following components.
Information outlets and workstation connectivity
Horizontal cables and distribution
Cable termination panels
All of the Landlord areas i.e. Management Offices, all floors of Block A and B, Utility Building and rooms, shall
be fully wired. Whereas for the tenanted areas or floors at Block C, D, E and F shall be decided by taking
consideration of the following.
Possibility to have multi-tenant at the same Block at the same floor. Individual tenants may not want to
share the same wiring closet. Currently only one communication closet is provided for that purpose at
each floor. Multiple wiring closets may be required for multi-tenanted floors.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 17 of 90
It is in the tenant’s interest to have total control of their LAN installation. This could be achieved by
having a totally separated Computer room within the tenanted area and/or by employing logical
networking security systems between the Landlord and Tenant in case of possible physical connection
The horizontal cabling system if provided at the tenanted area shall be robust and flexible enough to
cope with any possible office layout designed by the tenant. The flexibility will be achieved by having an
access flooring system where the I/O point location could be adjusted to suit the final location of the
workstations.
On the other hand, the horizontal cable system could be planned and put in place for known tenant on
site (example Net-Linx) provided that the layout design is developed at the right time during the
construction stage.
2.2.1 Information Outlet and Workstation Connectivity
The quantity of the information outlets (data and voice) to be provided per area would be based on the
following assumption. However, I/O points for interface to other system installation are not included in this
assumption.
Average Distribution Density Area to be Served
1. 3nos I/O per 10sq.m area Office area
2. 2nos I/O per 10sq.mm area Meeting, Conference,
3. 3nos I/O per 9sq.mm area Exhibition Center, Knowledge factor, IT & Multimedia Center
4. 1nos I/O per seat Auditorium
5. 2nos I/O per room AHU, Water Tank, Lift Motor and Utility rooms except Toilets
6. 2nos I/O per 20meter length Public circulation area and limited 1nos I/O for lift lobby
7. 1nos I/O per booth Public telephone
Refer to Appendix A for the Information Outlet User Matrix for Data and Voice I/O point distribution based on
the above I/O point average density.
The proposed connection to the desk or workstation is differentiated between area with and without access
flooring system. Refer to Appendix B and C for the proposal workstation connectivity.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 18 of 90
For areas with access flooring system, Type B connectivity is preferred where there is no need for the end user
to access the floor void to get into the information outlet location. Some difficulty maybe encountered if the
carpet is lay overlapping the floor panel.
Areas without access flooring system would depend on the area to be served i.e. open plan or cellular. The
information outlet could be located on the wall with a pre-agreed installation height or on the floor service
boxes. In any case, its location shall be fully coordinated with the proposed Interior Design because it not
flexible enough to be relocated.
The preferred type of user or workstation connectivity would determine on the horizontal cable distribution
system.
2.2.2 Horizontal Cables and Distribution
All horizontal cables shall originate from the communication closet or newly proposed equipment room at the
same floor in order to maintain 90 meter horizontal cable distance limitation. Four pair unshielded twisted pairs
(UTP) copper cables would be used as horizontal cables.
The horizontal cable distribution, which is determined by the selection of the workstation connectivity, could be
either one of the following.
Dropped point from high level trunking to wall mounted IO points.
Employing underflooor trunking system either comb, fishbone or grid system, for open area without
access flooring system.
Employing access floor trunking system or open basket in comb, fishbone or grid system, for open area
with access flooring system.
The first and second methods of distribution system are not flexible and subject to full coordination. Whereas
the third option could be further categorized either to serve single or multi-users (refer to Appendix D for
typical horizontal cabling distribution scheme for area with access flooring system). However, in order to
maintain easy cable management single location per user is preferred.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 19 of 90
2.2.3 Cable termination panels
Horizontal cable in the communication closet of equipment room shall be terminated either using one of the
following components.
Rack or wall mounted UTP patch panels.
Wall mounted 8 pairs disconnection modules.
However, the final selection shall be based on
Location of the termination unit i.e. either at communication closet or floor standing rack.
Flexibility of UTP patching between the termination units and networking switches. It is much easier
and cheaper to patch between RJ45 to RJ45 outlets. compare with RJ45 to connection or disconnection
module.
Location of the proposed networking switches, which may be provided by the Tenant in their new
proposed Server room within tenant demises.
In this design proposal, the following provision are considered,
Area to be served Horizontal Cable Termination Type Remarks
Management office (part 24-ports patch panel on floor New Equipment Room (Landlord’s
of Block A & F, level 1) standing racks area) to be proposed at Landscape
- Landlord area area directly accessible from the
Management Office
Block A 24-ports patch panel on wall mounted Communication closet already
- Landlord area rack or frame provided at each level accessible
from Lift Lobby
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 20 of 90
Block B 24-ports patch panel on wall mounted New Communication closet to be
- Landlord area rack or frame provided at Block B i.e. at Store
room and accessible from Lift
Lobby
Fire Control Room at 24-ports patch panel on floor Room already provided with access
Utility Building standing or wall mounted rack flooring system (architect to
- Landlord area depending on the room layout confirm)
Tenanted floor at Block Preferred on 24-port patch panel on Horizontal cables may be planned
C, D, E & F at each level floor standing racks at Tenant’s upon confirmation of tenant layout
- Tenant area selected equipment room location. design to void unnecessary work
2.3 Voice Backbone Cabling System
The voice backbone cabling system is proposed employing Category 3 copper telephone cables for connection
between Main Distribution Frame (MDF) to Subscriber Distribution Frame (SDF) room and to every level of
each block. Refer to appendix showing two different options of the copper voice backbone cabling system.
The voice backbone is proposed in consideration of the following.
As provision for analogue Private Service Telecommunication Network (PSTN) from the Service Provider
as possibly required by small scale tenants or by the Landlord for public telephone booths, fax machines
or direct line telephone handset connection.
As provision for separate or back-up cabling requirement for connection to Private Communication
Exchange (PCX) equipment to provide voice communication to all of the Landlord areas i.e. AHU room,
lift motor room, water tank room and lift lobby at the tenanted blocks. This shall ensure that the voice
communication is independent of the network switches availability. Fireman Intercom System if
provided shall be considered as a separate wiring system designed by the M&E Engineer.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 21 of 90
As provision for a possibility of small scale tenant to share common PCX equipment facility belonging to
the Landlord subject to expandability of the selected PCX equipment and incoming trunk line i.e. ISDN
PRI for Direct Dialing Inwards (DDI) facility.
As provision for a single tenant occupying the whole block or several floors in different blocks, to use
the same voice backbone for their voice communication connection between floors or between
buildings. This could be achieved by making voice cross-connections at the Basement riser of the
individual block and at SDF room.
As provision for video teleconference connectivity using ISDN BRI or PRI over copper cables.
Based on the above consideration, Proposal 2 for Voice Backbone Cabling System is preferred as shown in
Appendix G and H. The number of pairs of the copper cables shall be at least equal to the number of voice
points allocated per floor inclusive of 20% spare capacity.
However, there is possibility that the above provision is only applicable for the Landlord areas or blocks.
Whereas for the tenanted floors the copper backbone requirement should be finalized base on commercial
factors.
2.4 Data Backbone Cabling System
The proposed data backbone cabling system shall be designed to carry Gigabit bandwidth for possible Gigabit
Ethernet and Asynchronous Transfer Mode (ATM) applications. The campus would be wired using fiber optic
cables connecting all six blocks and to all floors. There are two types of fiber optic cables, Singlemode and
Multimode. Singlemode fiber of 10 microns wavelength is ideal for long distance gigabits data transmission up
to 20km depending on the switch fiber port connection capability. Multimode Fiber of 50 micron and 62.5
micron wavelength is capable for short distance gigabit data transmission up to 250 meter. However, under
current research and development, singlemode fiber could have the potential to carry data transmission up to 1
terabit.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 22 of 90
It is assume that the fiber backbone cabling system would be originated from the SDF room at Basement. Mesh
topology or a combination of STAR and LOOP distribution would be adopted to ensure full redundancy to each
block floors to be served. Refer to Appendix G and H of the proposed Fiber Backbone Cabling System.
Fiber cable of 24 core, 62.5/125 micro multimode fiber outdoor/armoured would be used for interbuilding
cabling (STAR and LOOP/RING) except only 12 core to Utility Building and 12-core indoor for interfloor cabling.
The SC type connectors and couplers together with the LIU units, installed on wall or floor standing racks
would be used for fiber cables termination. The loop or ring interbuilding fiber cables are the proposed
redundancy, which would be laid in alternative routing.
The backbone cabling system is designed to allow provision for patching between LIU to networking switches
or direct patching between horizontal and vertical cable LIUs at equipment room at Basement level. It is
assume that fiber patch cords would be provided correspond to the quantity of fiber core for each fiber at both
ends.
2.5 Networking Equipment and Software
2.5.1 Router
The Router is a device to translate from one protocol to another protocol. It is an IP converter device and at
the same time it can be the Proxy between the LAN and WAN. It controls the access between internal and
external communication. The router also functions as the main Address or the Post Office for an internal
Networks system. The distribution of the data will routed to the different segments of IP addresses.
The router can support high-speed serial connections up to 2 mbps. The standard of router shall support IEEE
802.3 Ethernet and 802.3U Fast Ethernet for the internal connection to switch. For internal connections, it can
be the X.35, E1, ISDN, Point to Point Protocol (PPP), Frame Relay and Asynchronous Transfer Mode (ATM).
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 23 of 90
2.5.2 Switches
Switches are the main sharing devices from one point to multipoint or multipoint to multipoint. Each device will
take one UTP or fiber port available at the switch. The data transmission for Ethernet Port is 10 Mega bit Per
Second (10 Million bit per second). For Fast Ethernet the transmission is at 100 Mbps. The function of a switch
is to carry data and distribute it around the LAN. The Main Switch is multiple trunk to deliver Gigabit
transmission capabilities to each block. The typical tenanted floor would have transmission capabilities of
10Mbps/100Mbps. However, 1000Mbps/1Gbps transmission bandwidth could also been provided to specific
user.
There would be proposed two Main Enterprise Switches for redundancy, fault tolerance and for backup
purposes. The Main Switches would be located at the Tech Linx Main Server room or Equipment Room.
Individual blocks would also be provided with Enterprise Switches located at the proposed Equipment Rooms at
the Basement Level of each block. These Enterprise switches are interconnected to each other using the
proposed data fiber backbone cabling system as described earlier. It is assumed that small-scale switches
would be provided at each floor of Block A and B. Whereas for Office blocks it is assume as part of the tenant
fit-out.
The proposed enterprise switches would support the following connection.
Gigabit connection for internal link between switches at individual block and main switches.
Lease line point to point connection or ATM 155/622Mbps WAN connection for main switches only.
The proposed switches should have the intelligent Ethernet Switch capability that allow easy configuration and
support multiple network segment within a single Chassis with 10/100/1000mbps connectivity. They also
should support Simple Network Management Protocol (SNMP) and be able to integrate with servers and
routers.
The proposed switches also should have capabilities for wireless solutions for small bandwidth usage such as
application for presentations in the meeting rooms, conference rooms or mobile users with notebook
computers. However, in the current market wireless LAN is limited to 10 – 11Mbps connection with limited
coverage dependent on environment and signal coverage.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 24 of 90
2.5.3 Modem
Modem or Network Terminal Unit (NTU) is the device that modulates and demodulates the signal from carrier
(Telco Company). It is capable of receiving and transmitting data up to 2 Mbps. It also supports point-to-point
connections. It could be used as the remote access point from a user dial-up connection to system. The
proposed modem should support DTE interface conform to standard such V.24, V.35, V.36, and V.90.
2.5.4 Server and Software
The Server is a computer that running a specific application, database storage, system monitoring or main
access point from a user with the right authority. It should have the capabilities of serving the user
simultaneously at one time. The basic requirement for server is a highly scalable microprocessor, memory, disk
storage space, communication bandwidth and physical connections.
Bespoke servers will run specific applications such as, Firewall for Security of the network, Mail server to handle
all e-mail communication. The server can also be the data storage space for video streaming of CCTV, Video &
Audio application or smart board or public information kiosk. For IBMS the servers require to monitor the signal
from each device. A server running the monitoring software will detect the fault signal and will give an alert
signal to system administrator.
The Specification of the server and application softwares will be determined by the application and the
requirement of the system that being install at the building. The requirement will be developed after getting
further feedback from Tech-Linx of the building operation and business.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 25 of 90
2.6 Wide Area Network (WAN) Access System
WAN is the connection from one LAN to another LAN, which is separated by the geographical area. WAN
connection could be Point-to-Point, Central or Multipoint to multipoint connection. The connection in between
the LAN is using the Teleco Company infrastructure. Most of the Telco company is using the ATM as the
standard media to carry the data or voice packet.
The proposed WAN connectivity for Tech-Linx building will be developed when the end user requirement for
data transfer, usage, traffic, location of data to be transferred are available. The WAN connection could be
between one organization to the same organization (intranets) or to different organization (extranets) with
certain limitation and authority level
The WAN infrastructure will require heavy investment and depending on the end user requirements and
business strategy, we would study the various options for WAN access and recommend accordingly.
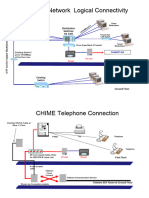
2.7 Private Communication Exchange (PCX) System
2.7.1 PCX Components
The Private Communication Exchange (PCX) system should comprise the following components.
PCX main equipment
Telecommunication equipment i.e. operator consoles and handsets
Voicemail system
Call Billing system
Administration terminals for local and remote maintenance purposes
Other accessories i.e. telephone frames and modules, lightning arrestor, back-up battery or UPS
Other necessary items for system maintenance
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 26 of 90
2.7.2 PCX Main Equipment
The PCX main equipment shall be decided from either one of the following equipment to provide voice
communication system for the Landlord.
Proprietary Public Branch Exchange (PBX)
Computer Telephony (CT) Technology
Voice over Internet Protocol (VoIP)
The selection of the main equipment should consider its compatibility and integration capabilities to serve the
whole complex for a single user or a possible multi user environment. The selected equipment should be future
proof.
2.7.3 Proprietary Public Branch Exchange (PBX)
The older version of monolithic proprietary Public Branch Exchange equipment with its closed architecture with
less compatibility and integration capabilities makes the PBX equipment less favorable to be used. However,
the new models with enhanced features, capabilities and low entry price make it suitable to be used. However
Voice Over IP (VOIP) is taking hold in this market.
2.7.4 Computer Telephony (CT) Technology
The Computer Telephony (CT) technology is the technology that merges two disparate fields, namely computer
and telephones, to provide a communication solution that improves not only corporate efficiency but also
customer services. The CT products and solutions can be categorised as,
Communication servers
Unified messaging system (UMS) involving voice-mail, e-mail and fax-mail
Interactive voice response system (IVR)
Internet protocol (IP) telephony products
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 27 of 90
Voice Over IP has taken hold in the telecommunications market recently. This development has been driven
directly by the increase in available bandwidth on the Internet. Companies such as Tech-Linx and Net linx
already employ Virtual Private Networks (VPN). By increasing the bandwidth available to these networks it is
possible to deliver telecommunications via the Internet to remote offices within the group of companies. This
effectively makes use of the leased lines, which have already been budgeted for within an organisation. The
added benefits of this are that the transfers of a local call in say Edmonton to Dresden or Malaysia are done
within the Tech-Linx VPN and are therefore transparent to the customer. Similarly Inter-Office voice traffic is
carried out on the Wide Area Network at a fixed cost.
There are drawbacks however; currently in Malaysia bandwidth is 10 to 20 times the cost of North America and
Voice Over IP Europe. This does not help the fiscal argument for implementing VOIP however the operational efficiencies and
integrated benefits of the system and the fact that bandwidth costs are dropping globally should make this a
viable option.
Local Telco
The proposed PCX equipment should have a full PBX features capability together with following enhanced
Internet capabilities.
ISDN PRI
Router
2.7.4.1 Least cost routing with outbound call translation
This is the system ability to choose the best Service Provider to make an outbound call. The SP may be
chosen based on either the trunk group, or by call translation to access the desired carrier, or by a
combination of trunk group selection and call translation.
PCX Workstation Router 2.7.4.2 Hard Multi-Tenancy
With this feature, the system should be able to support multiple companies which the system could
have virtual companies where physical lines are partitioned and allocated to these companies. Each
company appears to have its own private PBX and all settings that are available in a standalone PBX is
Local Call will be Local Telco Company
Telephone PCX Switch available to the system administrator of each company
International Call will use the lease Line to ISP via the
Internet
2.7.4.3 WEB based system configurator
Workstation
The system configuration tool should be web-based and allows configuration via LAN point-to-point dial
up and leased line network configuration, via the TCP/IP protocol.
ISDN PRI Local Telco
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 28 of 90
The web based Configurator allows three types of logins, each with different configurations screens that
Telephone may be viewed and modified:
System Administrator login. This login is meant for the system wide administrator and he has
essentially the permission to assign the hardware resources.
Company Administrator login. This login is for the individual company’s administrator and he has
permission to change settings specific to his company.
User login. This login is for the individual users. An user can only change settings specific to
himself.
2.7.4.4.Soft Multi-Tenancy
Like the (hard) multi-tenancy, the soft multi-tenancy enables multiple companies to share the resources
of a single communication server. In the case of soft multi-tenancy, for 2 or more companies sharing
the same PCX resource, an extension from one company can intercom or transfer calls to an extension
of the other company internally within PCX without having to make a physical outbound call, thus not
incurring an outbound call charge.
2.7.4.5 Unified Messaging Features
With the appropriate Unified Message System (UMS) server, the PCX system should be able to integrate
voicemail, e-mail and fax mail using the standards MS Outlook Express, MS Outlook, CC Mail, Navigator
or any of industry standard pop3 and imap clients. The PCX equipment should been provided with
digital trunking (ISDN PRI) lines to be able to have DID extension lines in order to perform these
functions.
2.7.4.6 Smart Book
This is an intelligent Phone Directory and personal aid to the User. From the Smart Book, the User is
able to initiate a call, and transfer a call just by clicking with the mouse. The User is also able to search
for a phone number by keying in the person’s name. The Smart Book supports the User’s personal
phone book, the company’s internal extension list, and a company global list of defined external
numbers.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 29 of 90
2.7.4.7 PC-USB Telephone Equipment
The USB telephone set is a full functioned digital feature unit, which is connected to the USB port of the
desktop PC. As the USB phone is connected to the desktop PC, it utilizes the LAN cable infrastructure of
the PC LAN and does not utilize the traditional phone cable infrastructure. Therefore, the voice IO point
provision under the horizontal cabling system could be deleted or being used as data IO point.
2.7.4.8 Call Center and Interactive Voice Response (IVR)
This features would allowed end user to set-up their fully integrated call center for their customer with
automated call distribution (ACD) system, IVR and open interface to link up with hose database for e-
commerce link and customer relationship management (CRM) system.
The system should allowed intelligent conversation with a machine. It should answers calls, reads out
menu selection, and responses to touch-tone digits keyed in by the caller for round the clock operation.
2.7.4.9 Expandability
The system should be future proof with no integration issue when adding more CT functionalities as
they are developed and available in the future.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 30 of 90
2.8 Network Security System
2.8.1 Introduction
In view of Tech-Linx’s plans of having a technology park campus of intelligent buildings within a web based
Intranet for their tenants together with providing LAN/Internet infrastructure for tenants, the issues in regard
to the security profile of its facilities essential.
Ensuring infrastructure provided at the Data Centres is actually secure
SWITCH
Demonstrate visible due diligence in regard to IT Security to customers (tenants) and other
PABX FILE SERVER DB SERVER
stakeholders
TENANTS NETWORK
Provide a demonstrable ‘value added’ security solution for current and new customers
Ensure the effectiveness and efficiency of the IT Security spend
APPS SERVER
DB
Ensure Privacy and Security for Tenants data and systems if common infrastructure is utilized
PUBLIC SERVER
Confidence/Assurance for Tenants to use LAN/Internet infrastructure backed up with international IT
DB SERVER
SWITCH
FIREWALL
SWITCH security standards and certification
ROUTER
INTERNET WEB SERVER
Ensure Privacy and Security for Tech-Linx servers, systems and its LAN users.
FIREWALL
PUBLIC SERVER FILE SERVER
IDS
In general, the architecture for the building management system relies on firewalls as the primary security
IDS
mechanism. Accordingly, the architecture reflects standard firewall practises with proper implementation in
PUBLIC NETWORK (DMZ) TECH-LINX INTERNAL NETWORK
this respect.
Primarily, the risks addressed are,
The architecture protects against internal risk from tenants
The architecture protects against external risk from the Internet.
The architecture separates public servers from the internal LAN such that any compromise in the DMZ will not
affect critical internal systems of Tech-Linx
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 31 of 90
2.8.2 Internet Access security
The Internet being the largest network in the world today is also the most dangerous to Tech-Linx and their
tenants. The connection to the Internet will be open to all hackers and would be hackers. Careful consideration
must be taken to ensure that this access point is protected thoroughly. The following measures are suggested
to thwart hackers:
Inserting a screening router between the Internet and the Internal network (see discussion below on Screening
router).
Inserting a multilevel firewall between the Internet and Internal network (see discussion below on Firewall
Implementation strategy).
Utilizing Vulnerability Scanner tools to probe hosts, network devices and workstations to detect and plug
vulnerabilities in systems. (see discussion below on Vulnerability scanners).
Utilizing Network Monitoring Tools to scan all critical segments. Configure the systems to alert administrators if
probes are detected (see discussion on IDS below).
Inserting Internet Virus Scanner Tools.
2.8.3 LAN Security
The tenants network is considered as an external network and not under the direct control of Tech-Linx. As
such, there is an unknown risk and must be considered as high. Any attacks on the tenants network could
easily spread to Tech-linx network if it is not protected.
Industry best practise recommends controlling the access from this segment with a firewall. The segmentation
of the tenants network from Tech-linx’s network ensure that tenants have controlled authorized access to IBS
systems and other related servers.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 32 of 90
2.8.4 Screening Router
The screening router provides the capability to screen packets based on criteria such as type of protocol, the
source address and destination address fields for a particular type of protocol, and control fields that are part
of the protocol. In this way the router provides a powerful mechanism to control the type of network traffic
that can exist on any network segment. Services that can compromise the network security can therefore be
restricted. Screening routers by themselves might not be able to eliminate all risks but are extremely effective
in reducing the zone of risk.
With the use of the screening router we will be able to prevent the following kinds of attack
IP spoofing where the hacker tries to impersonate a local host.
IP source routing where the hacker tries to divert packets to his machine by specifying an explicit route to the
destination, overriding the usual route selection process.
2.8.5 Firewall Deployment
The firewalls acts as a choke point that monitors and rejects application level network traffic. Because the
firewall does not forward any TCP/IP traffic, it completely blocks any IP traffic between the internal and
external network. Only authorized traffic will be allowed to pass.
High risk environments such as the Internal Accounting System and Databases of a major organization are
often advised to segment the network with firewalls from different vendors, operating on different platforms.
Although a single firewall and OS greatly simplifies the administration and maintenance, relying on one
platform and single OS may offer easy entry to malicious outsiders to exploit a single vulnerability associated
with this platform or firewall (e.g. the ftp vulnerability on a popular firewall product alerted recently).
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 33 of 90
2.8.6 Network Monitoring and Intrusion Detection
Monitoring is a key security activity that allows the early detection of intrusions and allows timely response.
Without effective monitoring, intruders are able to work for extended periods of time and can therefore
compromise practically any system.
There are many potential actions that can be taken here.
A general monitoring policy should be put in place
Implementation of log monitoring tools to consolidate and assist system administrators to examine logs.
Implementation of IDS systems on key segments is suggested both to support International Security
Certification Requirements and to provide improved early warning of attacks.
We recommend the following placements of IDS sensors.
Sensor on the DMZ
Sensor on the internal LAN
2.8.7 Vulnerability Scanner
A security scanner to identify vulnerabilities in servers and applications is proposed. The scanner aids system
administrators in verifying firewall and server configurations have been done properly by highlighting open
ports and weaknesses in implementation.
The vulnerability scanner should be on a laptop to allow checking of all segments and also used to view service
visibility from different segments.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 34 of 90
2.8.8 User Authentication
Current methods of authentication relies solely on fixed userids and passwords. This poses a high risk as it is
easily vulnerable to compromises such as password guessing, userid and password interception, brute force
password attacks and others. Anyone possessing the correct userid and password has complete access to the
system.
A stronger authentication mechanism needs to be put in place. Solutions to consider include secure tokens and
digital certificates. The authentication scheme implemented for such deployments must be both manageable
and easily deployed for large numbers of individual users.
2.8.9 Virus Protection
Virus attacks are extremely common in today’s Internet and can cause a great deal of effort and resources to
resolve once an organization of the size of Tech-linx is infected. Prevention is the cure. Normally the policy on
virus protection is dependent on individual users installing the latest signature update themselves. This heavy
reliance on users is seen as a potential risk as over time users will tend to ignore update directives.
A central anti-virus management and distribution system that is automated, is necessary to ensure that all
connected systems have the latest updates. All incoming and outgoing Internet mail should pass through an
Internet email virus scan system.
2.8.10 Encrypted links
All internal and external sensitive or potentially sensitive network traffic inside and outside of the network
should be encrypted. Implementations of secure protocols such as SSH and SSL needs to be deployed
throughout the Tech-linx Internet/Intranet/Extranet network. The security requirements of confidentiality,
privacy and integrity are therefore well respected.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 35 of 90
2.8.11 Server/Systems Security
Servers that have not been properly configured and hardened provide hackers with easy paths to internal
systems. Most compromises/hacking that takes place is due to improper configuration and unpatched bugs of
Operating Systems and applications.
All critical servers have to be properly patched, configured and hardened before being exposed to internal and
external networks. The hardening of OS and applications should be carried out by experienced security experts.
2.8.12 SNMP and Network Management
Simple Network Management Protocol (SNMP) is the most widely-used network management protocol on
TCP/IP-based networks. The functionality of SNMP was enhanced with the publication of SNMPv2. However,
both these versions of SNMP lack security features, notably authentication and privacy.
SNMPv3, corrects this deficiency. SNMPv3 defines a framework for incorporating security features into an
overall capability that includes either SNMPv1 or SNMPv2 functionality. SNMPv3 specifies MD5 for digital signing
of SNMP datagrams and DES for symmetrical encryption of transactions.
It is recommended not to employ earlier unsafe versions of SNMP without careful consideration of the security
implications. Wherever possible Tech-Linx should deploy management components that are SNMPv3 compliant,
although it may not be widely available in product offerings yet.
2.8.13 High Availability
The firewalls, Internet router and the ISP link are single points of failures to the infrastructure. Internet
blackouts are highly possible and will affect customer (tenants) confidence in services provided.
It is recommended that Tech-Linx design a high-availability architecture with back-up and load-balancing
equipment integrated in the network infrastructure. This will need a careful consideration and cost/benefit
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 36 of 90
analysis in terms of network equipment selection and requirements analysis (based on Internet traffic load
analysis, risk tolerance, security budget). In addition, a second Internet link to a different ISP should be
deployed to avoid dependency on one ISP.
2.8.14 Tenant VLANs
Protecting the privacy of tenant networks and servers from others can be provided at the infrastructure level
via the use of VLAN features of today’s LAN switches. VLAN ensures that data remains within the organization.
In addition tenants can deploy their own firewalls for added protection.
2.8.15 Security Policy
The key to successful security implementation starts with a good corporate security policy. Effective policies
ultimately result in the development and implementation of a better computer security program and better
protection of systems and information.
Information security policies and enforcement are necessary in all organisations with or without firewalls. The
implementation of firewall systems cannot properly proceed without organisational involvement and policy
development.
In making these choices, policy is established for an organisation and is then used as the basis for protecting
resources, both information and technology, and guiding employee behavior.
The security policy of an organisation is a set of rules that say how the organisation responds to the threats
presented to its information and strengthens vulnerable parts of its operation. The objective of the security
policy is to define principles and guidelines, which govern the procurement and implementation of systems. It
should not contain unnecessary implementation details.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 37 of 90
The policy must describe in high level terms the measures to be adopted to protect the organisation's
information. When the security policy has been defined, the implementation can be initiated.
A firewall, as an example, puts the organisational security policy into action. The agreements and
understandings a security policy defines become the rules base that will be coded on the firewall by your
installer. With this in mind, writing the requirements for a firewall really starts with writing an organisational
security policy.
Tech-Linx needs to develop a security policy that will meet its business objective. In order to have an effective
set of policies and procedures, Tech-Linx will have to make many decisions, gain agreement, and then
communicate and implement the policies. A committee should be set up to formulate the policies and
procedures and should consist of system administrators and decision makers in Tech-Linx.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 38 of 90
3.0 INTEGRATED BUILDING MANAGEMENT SYSTEM (IBMS)
3.1 Background Information
This section is presented to outline information relevant to the design of the new Tech-Linx Technology Park as
a state-of-the-art complex. This involves answering a series of questions, the first of which is: “What makes
this a state-of-the-art complex?” We believe that the state-of-the-art building is one that has been designed to
meet the needs of the Owner, Occupant and Operator today and has the built-in flexibility to meet the
changing technology and the changing needs of the Owner, Occupant and Operator in the future. This
definition will form the basis of the BKC design at all stages from scheme design through to the preparation of
the Contract Documents.
3.1.1 Intelligent Building and Information Communications Technology Systems:
The following are the primary microprocessor based building and information communication technology
systems that we anticipate will be in the new Tech-Linx Technology Park:
Building Automation System
Intelligent/addressable Fire Alarm System (to be designed by NDY)
Building Integrated Security System
Lift control and monitoring system (to be designed by NDY)
Maintenance management and inventory control
Electrical metering system (to be designed by NDY)
Lighting control system
Parking Control (This will be part of the BSS)
Point of sales system (This will require a “smart card”)
Public Address System Ito be designed by NDY)
Audio visual systems
Data networks and computer/telephony integration
Multimedia systems
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 39 of 90
In this report we use the term “Intelligent Building Management System (IBMS)” to refer to the total network
of integrated Intelligent Building and Information Technology systems and the associated Local Area Networks.
The last three items on the above list are covered in Section 2 of this report.
3.1.2 Flexibility for the future:
How do we ensure flexibility when we have no certain knowledge of future developments? We cannot
guarantee that future developments in the technology and the requirements of the Owner, Occupants and
Operators will be readily accommodated by our design today but we can take some steps to mitigate against
this happening such as:
Ensuring that all systems are expandable. The systems as installed shall be expandable to incorporate,
at minimum, a 100 percent increase in monitoring and control capability with the addition of hardware
and software. Subsequent to this potential expansion the Intelligent Building performance shall not be
degraded in any manner and shall meet all previously required performance criteria. Additionally,
equipment initially installed shall not become redundant as a result of implementing the potential
expansion requirements.
Installing a judicious amount of spare capacity. This is particularly applicable to the cabling where the
incremental cost of installing redundant cables is reasonably low. For example, the cost of the labour to
install a six strand multimode fibre optic backbone does not increase that much for a twelve strand
cable and whatever cost increases there maybe are low compared with the cost of pulling cable in the
future.
Only purchasing equipment from vendors that have displayed a history of ongoing support and of
providing upgrades and interfaces to their existing systems as they bring new, more technically
advanced, systems into the market place.
Ensuring where possible that the cabling systems that are used by the Intelligent Building Systems are
designed in such a manner that they provide a pathway for the transfer of information from any point in
the building to any other point in the building without the requirement to significantly disrupt the
operation of the building with the installation of additional cable. In this particular project we are
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 40 of 90
proposing the use of bandwidth on the structured cabling vertical runs and then dedicated horizontal
cabling as necessary to meet the specific requirements of the IBMS.
Ensuring, where possible, that equipment specified and purchased employs technology which in that
particular industry is state-of-the-art and is not about to be superseded by a new generation that is
more technically advanced.
Ensuring, where possible, that an adequate supply of spare parts is available from more than one
source and that there is also more than one source of maintenance services. This can be aided to some
extent by using components, including software, that meets widely accepted national and international
standards.
Providing, where possible, Intelligent Building Systems that can be interfaced to other systems, even if
there is no immediate requirement or no immediate economic justification for the integration of the
systems into the Intelligent Building network.
It is proposed to incorporate all of the above philosophies into the Intelligent Building Systems design for the
Tech-Linx Technology Park project.
3.1.3 Systems Integration:
In the foregoing definition of the state-of-the-art building there is no mention of systems integration but in
today’s marketplace this inevitably becomes a requirement for the building. Why should Tech-Linx integrate
the Intelligent Building Systems and the Information Technology systems? The following are some reasons for
systems integration in a building of the type that Tech-Linx will be developing:
Information available at one system can be used to affect the actions of another system to the benefit
of the building and its occupants.
A limited common operator interface - This can reduce manpower requirements.
Saves control room and cabling riser space.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 41 of 90
The activities of separate systems can be monitored from a single location and there is a single point for
receiving alarms.
Can reduce manpower requirements OR can allow manpower to perform additional tasks, such as
increased maintenance of equipment, which have cost benefits.
May have lower capital costs depending on the approach adopted toward the integration.
Marketability. The buildings will be more marketable to tenants and if Tech-Linx wishes to sell it in the
future.
Flexibility - A standard protocol will enable a wide range of vendors to compete for expansions and
replacement of components.
Brings control of the local environment to the desktop computer.
We consider the first item on this list, viz. the information available at one system can be used to affect the
actions of another system to the benefit of the building and its occupants, provides the greatest benefit to the
Owner. The following is a list of potential interactions between the systems that we believe may be
appropriate for the Tech-Linx Technology Park.
3.1.4 Interactions Between Intelligent Building Systems:
The interfaces proposed for the Intelligent Building Systems are illustrated diagrammatically in Appendix S of
the “Proposed Interactions Between Intelligent Building Systems”, and are discussed briefly below:
3.1.4.1 Building Automation System:
The proposed interaction between the BAS and the other extra low voltage building systems is as follows:
Building Integrated Security System:
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 42 of 90
The interface between the BSS and the BAS will enable the start up of the air conditioning and the switching on
of lights in the appropriate zone when a person enters the building either via a perimeter door or via the car
park. Similarly it will discontinue lighting and air conditioning when the person leaves the building.
In areas where lighting is reduced or turned off on a scheduled basis during non-normal hours of building
operation the occurrence of a security alarm will cause the BAS to initiate lighting in the applicable area.
Whenever the CCTV camera system is activated because motion has been sensed in a zone, the lighting will be
automatically switched on by the BAS for the appropriate zone.
Intelligent Fire Alarm System:
The FAS will override BAS control whenever there is a fire alarm. The FAS will shut down or start up air
handling units and other mechanical equipment regardless of the BAS control requirements. This will be done
via relays that are controlled solely by the FAS.
There will also be a digital interface between the BAS and the FAS so that the FAS can communicate the
occurrence of an alarm situation to the BAS. This will enable the BAS to anticipate the action of the FAS with
regard to the start/stop of equipment. In this manner the BAS exercises an oversight role and does not
generate alarms because equipment has been started or stopped without BAS intervention. At the time of a
fire alarm the operations staff are busy and do not require the aggravation of unnecessary alarm messages.
Past experience has shown that the stop/start of equipment by the FAS can cause the BAS to be tied up
outputting alarm messages at a time when it is most required. The fire alarm is a true alarm condition; the
resulting actions of starting and stopping equipment are not alarm conditions as they are supposed to happen.
The BAS should only generate an alarm when a piece of equipment that should have started or stopped does
not do so. In order to cater for time delays between FAS action and communication of the fire alarm to the
IBMS network and the subsequent message arrival at the BAS, a time delay will be available on all alarm
annunciations at the BAS. This is further discussed below.
Lift Control and Monitoring System:
The BAS will switch on lighting in the destination lobby during non-normal hours of operation.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 43 of 90
IT System:
We envisage the IT desktop monitors will have an icon that will permit a person with the appropriate password
to change the set point for the temperature in his/her zone. In zones with more than one person, the control
of this function should probably be restricted to one individual. We would anticipate a limit of say 2 degrees
Celsius about the general building set point. For example, if the policy for the building is to have a
temperature set point of 23 degrees Celsius, then the zone occupants would be restricted to varying the set
point from their desktop systems between 21 and 25 degrees Celsius. We would recommend that clicking on
the icon will bring up an easy to use template showing the present temperature and the present set point and
having increase and decrease set point buttons.
If Tech-Linx installs meters for chilled water and/or electricity in tenant areas, the BAS monitoring of these
meters will enable the data to be communicated to the accounts department. This data can then be used in
the preparation of tenant invoices.
Maintenance Management and Inventory Control System:
The BAS will send all cumulative run time data to the MMIC. This will become the basis, along with calendar
time for the maintenance schedules.
3.1.4.2 Building Integrated Security System:
The BSS comprises the access control and monitoring system (ACMS),the Closed Circuit Television (CCTV)
system, Audio Alarm System, the Voice Intercom System (VIS) and the Parking Control System (PCS) which are
integrated with one another. This integration will be totally independent of the status of the IBMS integration
LAN. The BSS will be integrated with the IBMS from the point of view of the interactions between the systems
but the access of the BSS functions at the IBMS operations workstation will be limited primarily to the status of
monitored and controlled doors and the status of BSS equipment. It will be seen in Figure 2 that the digital
communications involving the BSS are primarily from the BSS to the other IBMS subsystems. The primary
interface for the BSS functions will be the BSS workstation rather than the IBMS operations workstation. In the
case of the latter, the BSS as a whole is also integrated with the IBMS as a node on the integration LAN. The
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 44 of 90
integration of the BSS components is detailed in a following section. The proposed interaction between the
BSS and the other IBS is as follows:
Intelligent Fire Alarm System:
The FAS will override the BSS in the event of a fire alarm. Via hard-wired relays, the FAS will remove electrical
service to all BSS controlled doors designated as fire exits so that they unlatch and can be opened by anyone.
The FAS also communicates the occurrence of a fire alarm to the BSS via the IBMS network in order that the
BSS does not issue unnecessary security violation messages. As detailed above for the BAS interaction with
the FAS, the releasing of the doors is an expected occurrence and not an alarm and the shunting of alarms
removes the unnecessary aggravation.
The FAS also interfaces with the BSS so that in the event of a fire alarm, if there is a camera covering the
location of the fire alarm, the image from that CCTV camera will automatically be displayed on the CCTV
monitors in the CCR.
IT System:
The BSS can be the basis of a time card system for calculation of payroll and the preparation of employee
attendance records.
Maintenance Management and Inventory Control System:
The BSS will send frequency and duration of usage data to the MMIC. This will become the basis, along with
calendar time for the maintenance schedules.
Lift Control and Monitoring System:
The BSS will control usage of the lifts via the access controllers in the cabs.
Point of Sale System:
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 45 of 90
It is proposed to have a “smart chip” in the access cards. The cards will probably be of the proximity type and
the “smart chip” will not be used for access control, but it will be used for tracking sales at any retail outlets
and other tasks that Tech-Linx may wish to monitor in this manner. We are reviewing the possibility of using
the “smart” chip for access control as well as for the point of sales function.
PABX:
When the PABX receives incoming calls it will re-route the calls to the last location at which the person was
detected by the BSS
3.1.4.3 Intelligent Fire Alarm System:
The communications between the FAS and the other IBMS systems are unidirectional. Codes do not permit the
transfer of information to the FAS from another system.
IT System:
It is proposed to have a pop-up window on the IT system monitors that will provide access to instructions from
the FAS in the event of a fire. It is anticipated that the instructions will vary depending on the location of the
fire alarm. This is not a substitute for the FAS generated voice message system.
Maintenance Management and Inventory Control System:
The MMIC will be maintain data on the frequency and duration of use for the mechanical equipment which is
controlled only by the FAS such as the lobby and stairwell pressurisation fans and the fire pumps. Additionally
the MMIC will maintain maintenance schedules for the FAS equipment, including sensors, fire extinguishers,
etc.
Lift Control and Monitoring System:
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 46 of 90
There will be a hard-wired interface between the LCMS and the FAS that will send the lifts to the ground floor
in the event of a fire alarm and restrict their use to Bomba. This work will be outside the scope of the IBMS
subcontractor
3.2 Intelligent Building Management System (IBMS) Equipment
The term Intelligent Building Management System (IBMS) is used to refer to the network of integrated
Intelligent Building Systems. Appendix T “Proposed IBMS Topology”, represents a generic IBMS and is
provided solely for the purposes of illustrating the requirements for this project. Each vendor will have a
different approach to the IBMS architecture and where possible these have been illustrated in the appendices.
It is proposed that the Intelligent Building Systems be functionally integrated on an “integration LAN” with a
single operator interface and that there also be an interface to the IT systems. This will allow access to the
building automation, building security, intelligent fire alarm from a single operator interface and also can allow
limited access to these systems from selected Tech-Linx and other tenants’ desktop PCs.
3.2.1 Integration LAN:
The integration LAN shall be:
Peer-to-peer.
10 Mbps, 100Mbps or 1Gbps Ethernet TCP/IP or 25Mbps or 155Mbps ATM TCP/IP network.
Only standard, approved connectors shall be used.
Intelligent switches and associated hardware and software together with bridges and gateways shall be
provided as necessary.
There will be a network data server that will perform the following functions:
The storage, analysis and retrieval of data and information in addition to that stored at the individual
Intelligent Building Systems.
The storage of copies of BAS software, including schedules and databases. The network data computer will
downline load software to the BAS panels in the event of failure and loss of data.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 47 of 90
The supervision of connected operator terminals and other peripheral devices.
The NDS shall have a Microsoft Windows NT or Windows 2000 operating system.
3.2.2 Operations Workstations:
It is proposed that two operations workstations be provided at the Central Control Room. Each of the
workstations would comprise a VDU, keyboard, mouse, and printer. The functions of the operations
workstation shall be:
The storage, analysis and retrieval of data and information in addition to that stored at the individual
Intelligent Building Systems.
The primary function of the operations workstation is providing a “window” into the individual systems.
It is proposed that the workstation will be based on the most advanced technology available for Personal
Computers at the time of purchase by the vendor.
At minimum, it will be required that the PC have similar specifications to those detailed above for the Network
Data Server.
The operations workstations will have the following associated I/O devices:
Video Display Unit (VDU) with a minimum screen diagonal measurement of 432mm (17 inch) and a minimum
resolution of .28 pitch, 1024 by 768 pixels. The unit will be capable of displaying both schematic and
alphanumeric data at the same time. A minimum of 256 discrete colours will be available for display selection.
A touch screen is not recommended.
Printers: The two operations workstations will share two printers that will be configured such that one is used
for the hard copy output of alarms, event messages and other system generated messages. The other printer
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 48 of 90
shall be used for the output of reports and other data as requested by the operator. The printers shall be
housed in silent enclosures.
The failure of a workstation, hub, router or the integration LAN shall in no way affect the operation of the
individual Intelligent Building Systems.
3.2.3 Power Line Filtering:
The IBMS subcontractor shall provide power line filtering equipment that will provide appropriate protection for
all equipment furnished at the operations workstations. The IBMS shall operate satisfactorily without any
degradation in performance when connected to the building electrical power distribution system. The IBMS
equipment should be powered from the same power source as the equipment it controls.
3.2.4 Uninterruptible Power Supply (UPS):
A UPS unit shall be provided to meet the entire requirements of the CCR. The UPS shall be of the no-break
type and shall be capable of maintaining all CCR equipment functioning for a minimum period of 30 minutes.
3.2.5 Remote Operator’s Workstation (ROW):
It is proposed to have two (2) ROW. These will be laptop PCs which will be plug connectable at all BSS remote
field panels, BAS controllers and at all FAS fire control panels. The operator shall also be able to dial into the
IBMS network from a remote location using a standard telephone connection. Two telephone lines will be
required at the Central Control Room to support the modems used by the ROW to communicate with the IBMS
Network. When connected to the IBMS network the operator interface at these devices shall be substantially
the same as that at the operations workstations. The ROW shall meet the following specifications, at
minimum:
Output display shall be on a backlit active VGA (800 x 600 pixel display) screen.
Integral QWERTY keyboard with full ASCII character set.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 49 of 90
Weight, including carrying case, not to exceed 3.5 kg
There shall be a carrying case designed specifically for the ROW which ensures adequate protection.
ROW shall be powered by a rechargeable battery and shall also be powered by a 240 Vac, nominal 50
Hz, source. The IBMS subcontractor shall provide batteries adequate for a minimum of 4 hours of
operation.
The operator interface at the ROW shall be the same as that at the operations workstations at the CCR.
The operator shall also be able to access the individual distributed control panels on the BAS, BSS and
FAS networks.
3.2.6 Lobby Security/ Information Desk:
A remote audible alarm shall be provided at the security desk. This will annunciate operator selected alarms
when there is no operator at the CCR. When the operator is present in the control room the alarms shall not
be annunciated at the lobby desk. The alarm annunciation shall be via a horn located in the desk. An
acknowledge switch shall silence the alarm and a blue LED shall remain illuminated until the alarm condition is
removed. There is no requirement for a PC at this location.
3.2.7 Operator Interface:
The operator interface will have appropriate functions based on authorization levels that will provide the
operator with monitoring and control capabilities for all systems served by the integration LAN. The operator
interface will, at minimum, serve all of the BAS functions and will be able to access the status of any BSS, FAS
or LCMS points. The operator interface will be English language. The IBMS shall use a Pentium computer
based, software programmable, true multitasking operating system and integrated monitoring and control
operator interface. The network operating system shall be Windows NT or Windows 2000. The network
database shall be SQL or approved equal. Log-ins with unique passwords shall be required. A graphical
interface shall be provided based on the standard building automation system graphical users interface or it
shall be based on a third party software package such as Intellution or WonderWare.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 50 of 90
Log-ins and changes made to the system shall be identified through the printer and stored electronically for
review by authorized personnel. There shall be a minimum of 750,000 password combinations. The operator
interfaces will be "user friendly" and will be such as to simplify, as far as reasonably possible, the task of
operator training and acceptance. There shall be multiple authorization levels within the system. Lower levels
will allow viewing of alarms and/or set points only. Higher levels will allow changing of set points and other
operator changeable values. Even higher levels shall be used for management reporting. The operator shall be
able, at minimum, to perform the following functions from the operations workstation, subject to password
access restrictions:
Observe the current value of any parameter monitored by the BSS, FAS, BAS, the electrical metering
systems, lighting control systems and the lift control and monitoring systems.
Initiate any control action that can be undertaken by the BSS, FAS, BAS, lighting control systems and
the lift control and monitoring systems.
Acknowledge alarms.
Request hard copy or soft copy reports incorporating any monitored or controlled parameter.
Add, delete and change schedules.
3.2.8 Applications Software Packages:
The following software applications packages, at minimum, will be provided for the IBMS and will be resident at
the operations workstation:
VDU system display package: This software package enables the operator to configure, modify and delete
system diagrams. Real-time data shall be superimposed on the system diagrams and shall be updated at
intervals between 10 and 20 seconds. The data shall be positioned on the display at points indicative of the
instrumentation locations on the system.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 51 of 90
Historical data recording: This is a software facility for the collection and storage of data and its subsequent
retrieval and display in tabular and graphical form as selected by the operator.
Energy usage: The energy usage software monitors and reports electrical energy usage and instantaneous
energy demand. This feature will also store data for recall via the historical data trend package.
Real-time plotting: This software package emulates a strip chart recorder. This program will concurrently
display between three(3) and six (6) plots of variables in a graphical format. The graphs will be plotted as the
values are sampled in a similar fashion to a chart recorder and when the plot reaches the right hand side of the
X-axis, the X-axis shall scroll to the left so as to accommodate newly sampled data.
Equipment run time summaries: This software package accumulates the operating times for motors as selected
by the operator using an interactive procedure. Any piece of equipment that has its status monitored by the
BAS will be selectable for inclusion in this feature. It shall be possible to concurrently monitor the accumulated
operating time for every item of equipment monitored and/or controlled by the BAS.
3.2.9 Reports:
It will be required that there is flexibility in the compilation of reports for outputting at the operations
workstations. Operators will be able to call upon a series of standard and customised reports. The standard
reports typically available from the BAS, BSS and FAS will be available at the operations workstation on the
following basis:
A single point.
A single item of mechanical/electrical equipment.
Specific floor.
All equipment serving a particular floor.
Total building basis.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 52 of 90
Reports will be output in hard or soft copy, as determined by the operator, and will include:
Historical data
Energy usage
Equipment run times
Alarms conditions detected by the BAS, BSS and FAS
Present status of any monitored point associated with the BAS (including the York chillers), BSS or FAS.
Reports customised by the operator to include points from different systems on the same report.
3.2.10 Point Databases:
It is anticipated that, for the integrated building management systems from the potential vendors for the Tech-
Linx project, many of the functions associated with the databases for the individual systems, such as adding,
deleting and changing card access information or fire alarm monitoring points will have to be undertaken
directly from the respective subsystem server and will not be possible through the operations workstations.
Similarly it is anticipated that operations sequences which reside at the individual systems will generally require
a direct connection by an I/O device, such as the remote operator’s workstation, to the appropriate system for
implementing changes. We would expect that sequences associated with the interactions between systems
would reside in the initiating system. For example, in the case of the interaction between the BSS and BAS
whereby the use of the access card to enter the building triggers the start up of the air conditioning and
lighting in the appropriate location, the software will reside at the initiating device, i.e. the BSS, which will issue
a command to the BAS for execution.
3.2.11 Maintenance Management and Inventory Control (MMIC) Workstation:
The MMIC workstation shall be PC based. The PC shall have substantially the same specifications as detailed
above for the operations workstations. Preferably the MMIC workstation should reside on the integration LAN
as it will serve all systems rather than be incorporated into any one particular system. The MMIC shall
schedule maintenance on the basis of:
Calendar time.
Accumulated operating time.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 53 of 90
Frequency of use.
Frequency of alarms associated with an item of equipment.
The MMIC software shall produce work orders, maintain records of inventory, advise on economic order
quantities and perform other tasks normally associated with MMIC programmes such as maintaining cost
records.
3.2.12 Response Times:
The response times of the IBMS and the individual components must meet strict performance criteria. The
following is the suggested response times that should be required from the system:
All BAS, FAS and BSS monitored alarms should be annunciated at the appropriate workstation at the
CCR within 4 seconds of their occurrence.
All outputs of information requested by the operator should be displayed on the appropriate VDU within
5 seconds or, if directed to a printer, should commence printing within 5 seconds and should be output
at a rate of no less than half that of the printer specified rate.
Commands entered by the operator should be implemented within 2 seconds of the entry being made
regardless of which IBMS component system the command is directed to.
A request from one IBMS integrated system for action by another system must be implemented by the
appropriate system within 5 seconds of the request.
The coordinated actions of the BSS components must be such that the response actions commence within 2
seconds of the initiating action
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 54 of 90
3.3 BUILDING AUTOMATION SYSTEM (BAS)
3.3.1 BAS Functions:
It is proposed that the Building Automation System will fulfil the following monitoring and control functions:
Monitor and control the chilled water distribution (chilled water is provided by the district cooling plant).
Monitor and control the air distribution systems including the air handling units and the VAV terminal
units.
Monitor the open status, closed status and trip status of major electrical system distribution breakers.
Monitor electrical usage and demand.
RS232
MASTER VOICE
INTERCOM
STATION Monitor the emergency generators and the associated fuel oil systems.
Monitor the sprinkler, cold water, hose reel and other storage tanks.
SECURITY
MONITORING
CCTV
STATION
CPU VOICE
INTERCOM
CCTV MONITORS
SYSTEM
NETWORK Monitor the domestic water pumps, fire pumps, sump pumps, etc.
SWITCH
IBMS
INTERFACE Monitor and control other mechanical, electrical and sanitary systems as appropriate.
CAMERA
SWITCHER
AND GATEWAY
CONTROL
3.3.2 Proposed System Topology:
COMMON BISS BACKBONE / PATHWAY
The BAS shall meet the following general criteria:
INTERCOMS
GATEWAY GATEWAY
ALARMS
SMART ACCESS INTERCOMS - Computer based.
CARD CONTROL
- Fully networked
READERS PANEL
CCTV CAMERAS
ACCESS
- Real time.
DOOR AUDIBLE
CONTROLS CONTROL ANNUNCIATORS
PANEL
- Distributed processing.
Appendix U “ proposed BAS Topology”, illustrates a possible BAS topology. The following describes, in very
general terms, a relationship between the various components of the BAS that would be acceptable. Other BAS
topologies would be acceptable if they meet or exceed the intent and performance requirements.
The BAS shall be configured to ensure reliability of systems operation. Each air handling unit, air distribution
terminal unit and other major component of the mechanical systems shall have a dedicated microprocessor
based control panel.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 55 of 90
Local area networks, including peripheral LAN devices such as hubs, switches, routers and gateways shall
enable communications between the operator workstations and control panels so as to achieve the monitoring
and control detailed in these specifications.
The Operator Interface Workstations (OIW) shall incorporate, at minimum, Personal Computers (PC) and
Operator terminals. The OIW shall reside on the primary “peer-to-peer” LAN and shall provide the Operator
with a "window" into the BAS for the accessing of data, the changing of database parameters and the
execution of manually entered commands. The OIW shall also provide additional facilities in addition to those
available at the control panels for the storage, analysis and retrieval of data and for the storage and down line
loading of software to the control panels. The primary communication LAN shall be an Ethernet TCP/IP
network, an ATM TCP/IP network or a network with equivalent capabilities.
The Network Data Server (NDS) shall provide facilities in addition to those available at the CCP, DCP, and UC
for the storage, analysis and retrieval of data and for the storage and down line loading of software to the CCP,
DCP and UC. The NDS shall also perform similar functions for the other extra low voltage building systems
such as the BSS.
The Communications Control Panels (CCP) shall be capable of “peer-to-peer communication and shall reside as
nodes on the primary LAN. CCP shall be fully programmable control panels. CCP shall provide communication
coordination with the DCP, interface to the secondary LAN, and/or shall provide a gateway to third party
systems such as the lighting control system and the Maintenance Management and Inventory Control system.
The Distributed Control Panel (DCP) shall reside as nodes on the secondary LAN. DCP shall be fully
programmable control panels. DCP shall provide an interface to the field instrumentation and final control
elements. Each air handling unit shall have a dedicated DCP.
UC shall reside as nodes on the secondary LAN. UC shall be applications specific type controllers. Control and
monitoring using UC shall be limited to unitary equipment such as VAV terminal units, exhaust air fans,
electrical breaker position monitoring, etc. UC shall provide an interface to the field instrumentation and final
control elements for specified items of equipment.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 56 of 90
The Remote Operator Terminal (ROW) shall provide the Operator with an interface to the BAS at each DCP
location and at each mechanical room regardless of whether there is a DCP at that location or not. The ROW
shall also provide the Operator with remote access to the Intelligent Building Management System (IBMS) via
auto-dial/auto-answer modems. The ROW shall be a portable PC such as a laptop, notebook or sub-notebook
PC. The ROW shall also enable the Operator to access each UC or if such is not possible then the BAS
subcontractor shall provide a separate portable Operator interface device that shall enable the Operator to
access data, change database parameters and execute manually entered commands at the UC to which it is
connected.
The failure of a BAS component shall not cause the subsequent failure of any mechanical or electrical system
or any other BAS component. The failure of a BAS unitary controller or a DCP shall not cause the loss of
monitoring and control at the Operations Workstation of more than one VAV terminal unit or one AHU or one
substation/switchboard or any other major item of equipment. The loss of a BAS component shall not cause
the loss of monitoring and control at the CCR.
3.3.3 Proposed Applications Software Packages:
The Applications Software Packages shall reside at the DCP or UC at which they are used. It is proposed to
provide the following application software packages:
Programs for the optimisation of energy usage:
Equipment scheduling:
This program will enable the BCS to automatically schedule an item of equipment on and off.
Optimised scheduling:
This is an adaptive software program that will:
Start AC equipment at the latest possible time while ensuring that space in the building reaches
set point conditions by the time occupancy commences.
Stop AC equipment at the earliest possible time while ensuring that space in the building shall
still be within the set point deadband at the scheduled end of occupancy.
Peak electrical demand control:
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 57 of 90
This is a software package that predicts the peak demand in accordance with the Utility company's
standard procedure and initiates action as necessary to maintain the peak demand within the operator
assigned limit.
Equipment cycling:
This is a program that will cycle equipment usage in a manner that conserves energy.
Supply duct static pressure optimisation:
This facility will decrease the static pressure set point and, consequently, the energy usage while at the
same time ensuring that all cooling requirements are met.
Chilled water supply temperature set point reset:
This programme monitors the valve positions on the chilled water supply line and adjusts the chilled
water supply temperature so as to minimise energy usage.
Miscellaneous programmes:
Indoor air quality control:
This programme overrides energy optimisation programmes to ensure that satisfactory air quality is
maintained.
Psychometric properties calculations: This software will enable the calculation of any of the following ambient
air parameters based on the monitoring of any two of them:
Wet bulb temperature.
Dew point temperature.
Dry bulb temperature
Relative humidity
Programs for the restart of building mechanical systems:
Equipment restart following a fire alarm:
Following a return to normal, this program will restart equipment shut down as the result of a fire alarm
Equipment restart following a power failure:
Following a return to normal, this program will restart equipment shut down as the result of a fire alarm
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 58 of 90
3.4 AIR CONDITIONING AND LIGHTING CONTROL
The logic used by the BAS to control the air conditioning and lighting greatly influences the energy efficiency of
the building. The logic for a continuously occupied zone differs significantly from that for a zone that has
unoccupied periods. The major challenge, therefore, is in the use of the BAS to minimise energy usage during
the unoccupied periods. Two primary questions have to be resolved: how does the BAS know when the zone
is unoccupied and to what extent is it prudent to reduce air conditioning in an unoccupied zone? The following
discussion addresses these two questions.
3.4.1 Air Conditioning Control-General:
The air conditioning will be under the control of the BAS and each zone within the building has to be reviewed
to determine which BAS control approach is appropriate. In equipment rooms, for example, it may be
necessary to maintain air conditioning at all times but in some office areas which have periods of non-
occupancy it will be possible to conserve energy by adopting different control strategies for occupied and
unoccupied periods. The following discussion is primarily applicable to the Net-Linx office areas.
We propose that the operation of the A/C in the office areas be based on the following three modes:
Occupied mode:
In this mode the air conditioning maintains space conditions that are comfortable for the occupants. A
typical occupied temperature setpoint would be 23 Deg.C.
Intermediate mode:
This mode may not be employed in all instances. Typically this mode would be used following the start
of the designated building occupancy time up to the time of the arrival of the occupant. This mode may
also be implemented during periods when only cleaning staff are in the zone or during periods when the
occupants are likely to be out of the space such as lunchtime. The space temperature setpoint during
this mode would be intermediate between that of the occupied and unoccupied modes, say 3 Deg. C.
above the occupied mode setpoint, i.e. an intermediate mode space temperature setpoint might be 26
Deg. C.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 59 of 90
Unoccupied mode:
In this mode the space temperature is allowed to drift up by an operator determined amount above the
normal occupied mode setpoint. The temperature setpoint in this mode might, for example, be 7 Deg.
C. above the normal occupied setpoint, i.e. an unoccupied space temperature setpoint might be 30 Deg.
C.
3.4.2 Modes of Operation:
We have made the assumption in the following descriptions of the possible modes of operation that there will be
a building operator on duty at the complex during the normal building occupied periods but that there will be no
building operator on site when the building is scheduled to be unoccupied. We have also assumed that at least
one security guard will be in the complex at all times. We have assumed that there will be additional charges to
tenants who require cooling during periods designated as unoccupied.
The following are the alternative approaches to the control of the air conditioning for the office areas:
Scheduled start/stop: A/C is controlled based on operator determined schedules. Different schedules can be
selected for each day of the week and holidays and generally it is possible to have at least 4 “START” and 4
“STOP” scheduled times each day for each item of equipment. This approach activates the air conditioning
based on schedules regardless of whether or not the zone is occupied. There is no intermediate mode in the
morning between the end of the unoccupied mode and the start of the occupied mode but the intermediate
mode may be implemented during, for example, the lunchtime period.
With this approach a means is required to set the space temperature setpoint to the occupied value during
periods scheduled as unoccupied. This is discussed further below.
Optimised start/stop: A/C is controlled by the optimised start/stop program that calculates the latest time at
which the A/C can be started in order to attain the required space temperature by the time of scheduled
occupancy and calculates the earliest time that the A/C can be stopped without going outside acceptable space
temperatures. This approach activates the air conditioning regardless of whether or not the zone is occupied.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 60 of 90
There is no intermediate mode in the morning between the end of the unoccupied mode and the start of the
occupied mode but the intermediate mode may be implemented during, for example, the lunchtime period.
The alternative methods by which the setpoint is adjusted to the occupied value during the unoccupied or
intermediate periods are the same as detailed above for the scheduled start/stop control.
Motion detectors: The BAS monitoring of motion detectors to determine occupancy and initiate start-up and
shutdown of air conditioning is not recommended as the sole basis for A/C control. It may be a consideration,
however, when combined with, for example, scheduled or optimised start stop. Using the combined approach
the space is placed into the intermediate mode and the space temperature is brought down to, say, 26 Deg. C.
by the scheduled or optimised start/stop program when the building is scheduled for occupancy and is
maintained at that temperature until the space is determined by the motion sensor to be occupied and the
setpoint is dropped to the occupied setpoint, say 23 Deg. C. This approach can generate significant savings
relative to the previous two approaches.
To ensure that the occupied mode is not initiated unnecessarily, it is usual to have a time delay that defers the
start of the occupied period until motion within the space has been detected continuously for a minimum
period and to ensure that the unoccupied mode is not initiated unnecessarily, it is usual to have a time delay
that defers the start of the unoccupied period until no motion has been detected within the space continuously
for a minimum period. One drawback to this approach is that the space temperature may take some time to
reach a reasonable comfort level once the after-hours occupant has arrived and it may not be easy to control
who initiates this additional cooling.
Building security system interface: This approach is the same as that detailed above for the motion detectors
but the access control system determines when an employee is in the space rather than the motion detector.
The assumption is made that when an employee enters the building, as detected by the access control system,
the employee will require the occupied space setpoint to be in effect in his/her space. Depending on the
number of office zones in each building, this may be a less costly approach than the installation of motion
detectors. Where an employee has access to more than one zone the access control system initiates the start
of the occupied mode in the primary zone. If A/C is required in additional zone(s) then this could be
accomplished via the desktop PCs as detailed above.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 61 of 90
3.4.3 Determination of the Occupied/Unoccupied Mode:
There are several ways that the BAS can be the occupie/unoccupied mode of a space:
Contact building operator: A tenant contacts the building operator in person or by telephone and arranges for
a temporary adjustment to the occupied schedules for the space. This approach has the drawback that it
cannot be implemented when the building operator is not on-site unless a contact telephone number is
available for the duty operator who can then make the schedule changes remotely via the Remote Operator’s
Workstation (ROW). A means has to be put in place that enables the operator to know that the person he is
talking to has the authority to incur the additional cooling costs and a means has to be implemented for
tracking the requests so that the Owner can invoice for the additional cooling costs. This approach is generally
not popular with the building operators. An alternative approach is to let the security guard initiate the
occupied setpoint when the building operator is not on-site but this is often not practical.
Occupancy button: The unitary controller that monitors and controls the VAV terminal unit serving the space
monitors a button on the space temperature sensor housing. The button is only active during scheduled
unoccupied or intermediate periods. One drawback to this approach is that the space temperature may take
some time to reach a reasonable comfort level once the after-hours occupant has arrived and it may not be
easy to control who initiates this additional cooling, particularly in zones with more than one employee. The
time of the additional cooling periods can be communicated by the BAS to the Owner’s IT system and that
system can then invoice the tenant accordingly.
Telephone interface: A modem at one of the BAS components permits the occupant who wishes to be in the
building during a scheduled unoccupied or intermediate period to access the BAS from a remote location and
enter a temporary adjustment to the schedule. This function is password protected and is an interactive
procedure whereby the person making the phone call responds to a series of pre-recorded questions such as
password, time for the new occupancy period to commence and time for the new occupied period to end. The
occupant’s responses are entered via the telephone keypad. A simple look-up table at the BAS enables the
BAS to determine which space to put into the occupied mode based on the password. The same procedure is
adopted for extending the scheduled occupancy period when an employee is working late. The telephone
interface approach has the following advantages relative to the occupancy button approach:
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 62 of 90
It is limited to employees with the required level of password
It is easier to track for billing purposes, as the identity of the person making the request is known.
The A/C commences cool-down of the space ahead of the new occupancy period and may be able to
achieve the required space temperature setpoint prior to the commencement of the new occupied
period.
It is probably a lower cost approach than the occupancy button and it is less cumbersome than the
operator contact approach.
One disadvantage of this approach is that multiple passwords are required for employees with access to more
than one A/C zone.
IT system interface: Access to the A/C schedules is granted to employees with the appropriate password level
via the desktop PCs. This approach has the advantage that employees have access to the control of the A/C in
each zone that they are permitted to access. A simple interactive procedure is used by the employee to
change the occupancy schedules.
3.4.4 Lighting Control:
It has yet to be determined approach will be used for the control of the lighting. There are several choices:
Lighting switches:
The main drawback to lighting switches in the office areas is that employees and cleaners forget to turn
lighting off when they leave. Lighting in general areas such as the ground floor lobby, lift lobbies,
parking garages and the building exterior cannot be left to tenants to control, particularly in a multi-
tenant building. Often the ON/OFF control of the general area lighting is by the security guard and
sometimes it is placed on a timer.
Direct BAS control of lighting relays:
Each VAV box will have a microprocessor based controller which usually will have sufficient spare
capacity to enable the BAS control of a relay. The relay replaces the light switch. The BAS determines
the mode of operation using one of the approaches detailed above for the A/C, viz. motion detector,
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 63 of 90
occupancy button, access control and monitoring system interface or pre-programmed schedules.
Lighting is ON during the occupied mode and OFF during the intermediate and unoccupied modes.
Stand-alone motion detector:
The stand-alone motion detector replaces the light switch. The detection of motion closes a relay within
the motion detector and this switches on the lighting. A time delay relay in the motion detector
switches off the lights when occupancy has not been detected by the motion detector for a continuous
period, the length of which would be of the order of 5 to 15 minutes depending on space usage. This
form of lighting control is independent of the BAS.
Stand-alone microprocessor based lighting control system:
This would be a programmable system that would operate independently of the BAS. It would have to
be based on an occupancy sensor of some sort for the control of lighting outside normal hours of
occupancy. This could be achieved by duplication of the means for detecting occupancy for the control
of the A/C or it could be accomplished by a digital communications link between the BAS and the stand-
alone lighting control system.
We make the following recommendation for the consideration of Tech-Linx:
Employees will be required to use the access control and monitoring system when they enter and leave
so that the BSS knows whether a person is in or out of the building. This is discussed further in the
next section.
Air conditioning will be controlled on a zone basis by the BAS directly via microprocessor based unitary
controllers at each VAV terminal unit. Lighting will be controlled by the BAS either directly via relays or
indirectly via a communications interface to a microprocessor based lighting control system. This
decision will be made during the design development phase in conjunction with NDY.
Operator adjustable space temperature setpoints shall be established for the three modes of operation:
occupied, intermediate and unoccupied. Each zone shall have its own setpoints that will be changeable
by the employees who have been assigned a password permitting this function. Changes will be
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 64 of 90
constrained within limits established by Tech-Linx. Setpoints shall be changeable from the employee’s
desktop.
Operator adjustable schedules shall be established for the start of the daily building occupancy. This
shall determine the time at which the unoccupied mode switches to the intermediate mode of operation.
It shall be possible to implement these schedules on a per zone, per tenant and per building basis, as
selected by the building operator. Each zone shall have its own schedule and will be changeable by the
employees who have been assigned a password permitting this function. Changes will be made from
the employee’s desktop PC but will be constrained within limits established by Tech-Linx.
If the zone is in the intermediate mode of operation, the BAS will switch it to the occupied mode when
one person assigned to that zone is detected by the access control and monitoring system entering the
building (includes the parking garage). The occupied mode will only commence if the zone is in the
intermediate mode, i.e. preparing for occupancy. If the zone is in the unoccupied mode the lighting will
be turned ON in the zone but the A/C will not be started automatically. The start up of the A/C will be
via the desktop PC using an interactive procedure that will be limited to employees having a suitable
password level. This will prevent unnecessary energy consumption when an employee returns to their
zone for just a short period of time.
In open office areas, the switch from occupied to unoccupied mode at the end of the working day will
be based on operator entered schedules. It shall be possible to implement these schedules on a per
zone, per tenant and per building basis, as selected by the building operator. Each zone shall have its
own schedule and will be changeable by the employees who have been assigned a password permitting
this function. Changes will be made from the employee’s desktop PC but will be constrained within
limits established by Tech-Linx. The lights will go ON and OFF momentarily 5 minutes before the switch
from the occupied to the unoccupied mode. This will provide employees in the space with sufficient
time to extend the occupied period if they so wish. The time extension will be done from the
employee’s desktop PC and will be password protected. Time extensions shall be constrained to a
maximum of 60 minutes after which the procedure must be repeated if additional occupancy is
required.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 65 of 90
In closed offices, a motion detector shall be used to turn lights OFF if an occupant is away from the
office continuously for more than an operator determined period of time that would typically be of the
order of 5 minutes but would be dependent on the type of lighting. The motion detector will turn lights
on whenever motion is detected. The motion detectors shall not be used to control the A/C.
Consequently, if a secretary enters an executive’s empty office, for example, to put something on the
desk this will turn the lights on but will not cause the A/C to go to the occupied mode.
The detection by the access control and monitoring system that an employee is entering the building
during the unoccupied period will cause the lighting to be turned on as necessary for the employee to
get from the point of entry to the ground floor lift lobby. The lighting in the lift lobby on the lift’s
destination floor will also be turned ON.
3.5. BUILDING SECURITY SYSTEM
3.5.1 Overview:
The installations will be executed such as to provide an appropriate level of physical security for personnel,
property and visitors without unduly impeding staff from going about their normal duties.
The security devices will, in general, not be concealed from the user, except in specific architectural or security
sensitive areas, and the users will be generally aware of the security provisions.
The systems will be installed so as to be compatible with the effective operation of the complex in both normal
and abnormal, emergency situations. Adherence will be maintained with code requirements.
Systems shall be designed for high duty operations, ease of accessibility for maintenance and redundancy of
critical components.
System monitored intrusion detection points shall be four state (active, closed, short and ground) providing
high protection against tampering.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 66 of 90
Tech-Linx Headquarters Offices: Security for the Headquarters Offices has been considered in terms of a
number of security zones or areas having a defined security perimeter. These are illustrated in diagram in this
page. The primary zone types may be categorized as follows:
The “Site” zone: In the case of Tech-Linx the security at the site level is negligible as there is no site perimeter
fencing or any other security measures.
The "building exterior zone": A building exterior zone is created to prevent unauthorized access into the
building during non business hours. TO BE DEVELOPED
The “vertical transportation and stairs” zones: TO BE DEVELOPED
3.5.2 Tenant and on floor spaces:
TO BE DEVELOPED
Each security zone will be defined by means of an actual perimeter consisting of walls, doors, floors, windows,
and other like physical barriers. A summary outline of the planned facilities and operations follows:
3.5.3 Normal Hours Access:
TO BE DEVELOPED
3.5.4 Lighting:
Although lighting is outside the scope of the BSS, it can serve two functional security objectives; illumination of
areas of security interest for human or electronic observation, or a psychological deterrent by leading an
intruder to believe that they will be discovered or observed. Inadequate site and parking lighting is often cited
as the number one factor of liability for losses. Local ordinances usually set guidelines for minimum
illumination requirements for structured and surface parking areas, but the lighting levels required depend on
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 67 of 90
the amount of activity or usage that the property receives. The following should be used as a guideline for
determining minimum lighting standards for the parking and site areas:
Area Minimum Recommended Light Level (LUX)
general parking areas in garage 50 lux
garage ramps and corridors 100 lux
garage entrances 500 lux
surface parking 50 lux
truck docks 300 lux
pedestrian traffic areas 100 lux
plaza areas 30-50 lux
3.5.5 System Components:
The BSS is comprised of the following major integrated components:
Integration: The CCTV, VIS and ACMS shall be integrated to facilitate the coordinated operator
monitoring and response requirements of the BSS. Regardless of the status of the IBMS integration
LAN, the BSS shall be fully integrated so that all of its components interact in a fully coordinated
manner.
Closed Circuit Television (CCTV): A CCTV security surveillance system with monitoring, salvo switching,
real time recording and control equipment will be located at the Central Control Room (CCR). Digital
image storage will be requested as an alternate price to replace the standard VCR approach.
Voice Intercom System (VIS): A two way Security Voice Intercom (VIS) communication system having
master stations at the CCR, a submaster at the security desk, remote intercoms and emergency
assistance intercoms at locations throughout the Facility.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 68 of 90
Audio Alarm System (AAS): A microprocessor, microphone based monitoring system for enclosed spaces
such as stairwells with the ability to monitor remote speaker microphone stations and generate alarms
based on user programmable noise threshold levels. Head end facilities enable operators to “listen-in”
to people at the speaker microphone location. Some manufacturers incorporate the AAS into the VIS.
Access Control and Monitoring System (ACMS): A network computer-based Access Control and
Monitoring System (ACMS) with SQL database, having a monitoring and control computer, operator
workstations and annunciation devices located at the CCR. Access controllers and sensors will be
located throughout the Facility. The sensors shall include door position switches, motion detectors and
duress buttons. We are presently evaluating the use of biometrics, proximity cards and “smart” cards
for access control. A video badging system shall be provided.
Interfaces: Hard-wired interfaces will be provided with the Intelligent Fire Alarm System for positive
door unlocking in the event of a fire alarm. Software interfaces will be provided as detailed in the next
section.
Parking Control: Access controllers with extended read range and VIS slave intercom stations will be
provided for the exit/entry control of the parking. The BSS subcontractor will provide parking control
barriers and associated induction loops but there will be no fee management system. Parking will only
be available to those having a valid access card.
Digital CCTV Image Storage: This is relatively new technology that is still relatively high priced in
comparison to conventional multiplexed analogue video cassette recording (VCR) systems. Because of
the cost, we suggest that an alternate price item be obtained to replace the base bid system VCR with
the digital facilities.
Sound Masking: An alternate price will be obtained for acoustic noise generators to impede
eavesdropping on conversations on the in the boardroom. These systems will protect against both
interior listening devices, such as microphones concealed in ceiling spaces, and exterior laser/microwave
reflections from windows.
3.5.6 Access Control and Monitoring System (ACMS):
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 69 of 90
The ACMS will be a computer based, distributed processing, software programmable, access control and
intrusion alarm monitoring system. The ACMS shall comprise a series of microprocessor based Remote Field
Panels networked together with the IBMS central PC. We anticipate that the network will be a fibre optic cable
Ethernet or ATM TCP/IP LAN. An on-line data base management package will be included to allow for
individual user access privileges and alarm monitoring time schedules to be defined or redefined by Tech-Linx
as requirements change.
The ACMS will be interfaced as required to the Intelligent Building Management System. It is anticipated that
the following security packages will be incorporated into the ACMS:
Time controlled scheduling (time zones) for individual controlled doors, access controllers and
monitored points.
Alarm monitoring and annunciation, complete with the automatic archiving of operator
acknowledgment.
Individual cardholder files, including digital photo I.D.s.
Individual access privilege definition for cardholders.
Historical transaction archiving, reporting and audit trail facilities.
Automatic event/transaction archiving.
On-line data base management with partitioning capabilities.
Power fail-safe/auto-restart facilities.
Operator password access control.
Access controller "on-line" and "degrade" mode operation.
Anti-passback for the parking garage.
Anti-passback for the building.
Guard watch tour.
Time and visitor management.
3.5.7 Access controllers:
TO BE DEVELOPED
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 70 of 90
It is proposed to use the ACMS as the basis of a people registry which will provide a list of all people in the
building at the time of a catastrophe such as a fire or bomb threat. The people registry will also be the basis of
overtime calculations by the payroll department and, if there are any employees in the future who are paid on
a time basis, then this will also form the basis of payroll calculations. The access controllers will also be used
for the guard watch tour function where possible. If the access controller system is unable to fulfil the guard
watch tour function then the IBMS subcontractor will be required to furnish a separate system such as that
manufactured by Morse which requires the guard to read a series of control tags located strategically around
the building via a hand held data recorder. The data recorders shall have LCD and “autopilot” features.
The access controllers will most likely be proximity card readers, biometric readers, smart cards or a
combination. We are presently reviewing the options to determine the appropriate technologies for the Tech-
Linx Technology Park.
The following is an initial list of proposed access controller locations but it should be emphasised that this will
change to some degree as the interior design progresses. The primary purpose of the list at this stage is to
assist in preparing initial cost estimates and for coordination with the interior designers.
TO BE COMPLETED
It is anticipated that the access controllers will be active at all times. We have assumed that the west side
entrance into the ground floor main lobby will be open during normal hours of office and retail use and that
outside those hours the access controller will be active. We propose that all perimeter access controller
controlled doors have electromagnetic locks with an integral door position switch that will be automatically
released by the FAS in the event of a fire alarm. All interior access controller controlled doors should, where
possible, have electric solenoid mortise locks that will where appropriate be automatically released by the FAS
in the event of a fire alarm. All doors with exit access controllers shall have emergency break glasses with
suitable signage that shall release the door when the glass is broken.
3.5.8 Sensors:
Door status:
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 71 of 90
The following sensors are proposed for door status monitoring but it is emphasised that there will almost
certainly change as the interior design evolves:
TO BE DEVELOPED
We have assumed that all doors will be key locked except those on the ground floor that are designated as fire
exits. For the ground floor fire exits, we propose the use of delayed electromagnetic locks with an integral
door position switch, pre-recorded voice announcement in English and Bahasa Malaysia and audible alarm.
These doors would be automatically released by the FAS in the event of a fire alarm.
Break Glass Door Release Units:
Break glass door release units will be provided on all access controller controlled doors to enable emergency
exit from a space. The break glass units will be monitored by the ACMS. An audible alarm will sound locally
when the glass is broken.
Duress Alarms:
It is proposed to have duress alarms at the following locations:
TO BE DEVELOPED
Beam Detectors:
It is proposed to have beam detectors across the parking ramps. The intent is to identify people walking on
the ramp and activate a suitably positioned fixed lens camera. This will be shunted by an induction loop.
Video Badging System (VBS):
The VBS shall include, at minimum, the following:
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 72 of 90
Personal computer with keyboard and VDU with adequate storage for 10,000 video images and data. The PC
shall be identical to the ACMS operator workstation PC, except for the following:
Minimum Processors speed of 1000 MHZ.
20 Gigabyte SCSI hard disk.
128/256 Megabytes full parity EDO RAM memory.
Video Display Unit (VDU) with a minimum screen diagonal measurement of 381mm (15 inches) and
shall have a minimum resolution of .28 pitch, 1024 by 768 pixels and 76 Hz refresh rates.
Table top flat bed colour scanner using SCSI 32 bit interface to the PC.
Colour digital video camera with tripod and light.
VBS software including operator definable fields, company logo, ghosting, selectable type styles, colour and
size of fonts.
Colour printer. Printer shall be capable of printing video images and data directly onto each personnel ID card
along with a UV and tamper protective layer. Printer shall be 300 dpi with 16 million colours and shall have
provisions for single card and batch printing of the I.D. cards. The access control I.D. card shall be dye
sublimation printed on both sides with reference to Tech-Linx, and identifiable only by imprinted code number
on the card. The access control ID card will also serve as the Tech-Linx I.D. card, personal access into the
building and vehicle access into the garage. The ID cards shall have a video image of the staff member
prominently displayed on the card. The I.D. card shall also incorporate a “smart chip” to allow the use of the
card at point of sale facilities. The I.D. card will be worn at all times.
3.5.9 Voice Intercom System (VIS):
It is proposed to provide a commercial quality, two-way microprocessor based voice intercom system. The VIS
master station shall be at the CCR and will have access to all system remote substations. The VIS remotes shall
have push to talk buttons which shall only be used for the initial contact and, thereafter, the operator shall
control the conversation direction from the master station. The principal function of the VIS will be to allow for
two-way voice communication at all times between the operators at the CCR and the intercom substations
located throughout the building. An LED shall illuminate intermittently upon activation of the intercom remote
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 73 of 90
substation and will be steady upon call connection. The proposed locations, which are subject to change as
the interior design changes, for remote voice intercom substations are as follows:
TO BE DEVELOPED
The proposed locations for the voice intercom submaster stations are as follows:
TO BE DEVELOPED
It is proposed to have parkers assist stations at:
TO BE DEVELOPED
Parkers assist stations will comprise a voice intercom substation, high intensity metal halide blue lights on the
east and west sides of the column and signage indicating that the VIS is on the other side. The voice intercom
substations shall automatically activate the CCTV cameras covering the area and the area will be displayed on
the monitor in the CCR. Pan-tilt-zoom cameras shall automatically move to predefined positions to optimise
the operator’s view. The blue lights will go from continuous illumination to flashing/strobing.
It is proposed to have audio alarm stations in each of the stairwells at the following locations:
TO BE DEVELOPED
3.5.10 Closed Circuit Television System (CCTV):
The video surveillance system will be colour, programmable, microprocessor controlled and keyboard operated.
Each of the operator’s workstations will be equipped with a CCTV keyboard for fallback camera display
selection. Camera selection will be both manual, using the keyboards, and semi automatically pre-programmed
through the CCTV controller.
All cameras will be solid-state 1/3 inch format CCD (charge coupled device) colour imaging with auto-iris. The
video transmission medium will be fibre optic cable. In the base bid, Video Cassette Recorders (VCR) of, at
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 74 of 90
minimum, commercial quality, will be provided at the Central Control Room. These will be programmed to
automatically record all cameras in a real time quad mode. Sufficient monitors will be provided such that all
CCTV shall be viewable at one time. Additionally, the operator will be able to record upon demand the input
from any system camera in real time. Video recording playback will be through selected monitors. An
alternate price will be obtained for digital image storage.
Subject to interior design changes, the proposed fields of view for the CCTV cameras are as follows:
3.5.11 Interior fixed cameras:
TO BE DEVELOPED
3.5.12 Exterior fixed cameras:
TO BE DEVELOPED
3.5.13 Pan-Tilt-Zoom Cameras with Exterior Housings:
TO BE DEVELOPED
3.5.14 Video Motion detection:
Video motion detection units shall be provided. Each unit shall be capable of providing video motion detection
on 16 cameras. Cameras to be used for video motion detection shall be operator assignable without removing
or rewiring any harnesses or jumpers. The zones of motion detection shall be definable for each camera by
the operator and the schedules for video motion detection shall also be assignable on an individual camera
basis. It is proposed that provision will be made for all cameras to have video motion detection.
3.5.15 Digital Image Storage:
The base bid system will have VCRs for CCTV camera image storage but an alternate price will be obtained for
digital CCTV image storage. Whichever system is used there shall be the facility for digital zoom. We are
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 75 of 90
aware of two products on the market, Geutebruck and Loronix. We do not know if the latter is available in
Malaysia at this time.
3.5.16 Sound Masking:
An alternate price will be requested for sound masking in sensitive areas such as boardroom. The main
requirement will be for protection from laser/microwave reflections from windows. Portable units weighing less
than 350 gram are available that can be easily moved around the building to areas where sensitive discussions
will be held.
3.5.17 Letter Bomb Detectors:
These are frequently installed in mailrooms to detect letter bombs before letters are opened. They are
relatively compact and inexpensive and it is recommended that all mail be passed through a detector before
opening and distribution within the building.
3.5.18 Interaction with other security devices:
The VIS, CCTV, AAS and VBS shall be integrated into the ACMS such that they interact in a fully coordinated
fashion as follows:
Data communication transfer shall be provided between the CCTV, VIS, ACMS and VBS to allow the
integrated operation of these systems. This interaction shall be independent of the integration IBMS
LAN.
The operator shall be able to suspend or put the response of a BSS integrated alarm "on hold" to allow
the operator to select another alarm or perform other integrated BSS actions. The automatic display of
the graphics shall be enabled by operator selection.
In integrated security mode all master control keyboard functions will be operable through the
operators computer keyboard. A panel with master control keyboard wire jacks shall be provided to
allow quick plug-in connection for subsystem control when not operating in the integrated mode.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 76 of 90
VIS remote initiated call - VIS remote initiated door/gate call shall require the following integrated BSS
operation:
Remote shall annunciate a tone at the VIS master.
Upon operator acceptance at the VIS master, the location and description of the remote shall be shown
on the BSS workstation.
The associated graphic alarm display map shall be displayed immediately and the remote location shall
be highlighted or change colours.
The associated camera shall be switched to the operators CCTV monitor at full display for viewing. If
the associated camera is pan-tilt-zoom, the associated preset shall be enabled to view the appropriate
area. Recording of the associated camera shall continue.
The operator may grant access by activating the "Door/Gate Grant Access" function by selecting the
ACMS door grant access control via mouse selection or function key selection.
A comment window at the VDU for operator comments as necessary.
Ending the call at the VIS master shall reset the system for the next operator selected event or alarm
occurrence and shall move the CCTV video from the prime alarm video monitor to the secondary video
monitor.
ACMS alarms - ACMS alarms shall require the following integrated BSS operation:
Upon receipt of the ACMS alarm, the BSS VDU shall annunciate the alarm in the alarm queue.
Upon operator acceptance of the alarm at the VDU alarm queue, the location and detailed description
shall be shown on the BSS VDU.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 77 of 90
The associated graphic alarm display map shall be displayed and the end device location shall be
highlighted or change colours.
The associated VIS remote shall be connected.
The associated camera shall be switched to the operators CCTV monitor at full display for viewing. If
the associated camera is pan-tilt-zoom, the associated preset shall be enabled to view the appropriate
area.
The CCTV recording facilities shall provide real-time recording of the event.
A comment window at the VDU shall enable the operator to make comments as necessary.
Operator deselection of the event shall disconnect the VIS remote and reset the system for the next
operator selected event or alarm occurrence and shall move the CCTV video from the prime alarm video
monitor to the secondary video monitor.
Operator BSS device selection - BSS operators shall be able to select any BSS device for control or
viewing by icon selection through the graphic alarm displays, selection via the pull down menus or by
text entry of the device to be controlled. When any device is selected the following shall occur:
The associated camera with pre-set enabled shall be switched to the primary monitor at full display for
viewing.
The associated VIS remote shall be connected.
The associated device shall be highlighted on the associated graphical alarm display.
The associated camera shall be recorded by the CCTV system if so selected by the operator.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 78 of 90
4.0 GENERAL CONSIDERATIONS
4.1 Operational Consideration
In order to ensure uninterrupted services, adequate physical and logical protection systems should be provided
to the wiring system, equipment and equipment rooms. Certain provision should be covered under the other
trades design and installation.
4.1.1 Surge Voltage Protection System
Electronic Surge Protection (ESP) device should be installed to minimize the effect of generated transient over
voltage come in to the building via power, telecommunication and signal cables entering or leaving the building
except for fiber optic cables.
In addition, transient over voltage could be generated within the building due to inductive load, electrical
switching or induced voltage to power lines as the side effect by lightning strike to the building. ESP should be
provided at the following point of installation.
Power Lines (designed by M&E Engineer)
The electrical main switchboard of the incoming feeders (by electrical trade contractor).
Dedicated electrical distribution boards (DB) serving the centralized equipment room (by electrical
trade contractor).
Plug-in type ESP for critical equipment that is not connected to dedicated DB (by electrical trade
contractor).
Telecommunication Lines
PSTN and ISDN incoming telephone lines (by IT trade contractor).
Signal Lines
All signal line from outdoor CCTV cameras (by security trade contractor).
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 79 of 90
4.1.2 Earthing Protection System
To ensure effectiveness of the installed ESP, a comprehensive earthing protection system should be provided.
The installation of the earthing system main components should be covered under the electrical trade
contractor.
A dedicated earthing protection system should be designed for communication system. An earth resistance
value of less than 1 ohm should be achieved at the earth terminal bar installed in the room but not limited to
the following rooms,
1. Communication risers at Block A, B, C, D, E and F at each level.
2. Main Distribution Frame (MDF) room.
3. Subscriber Distribution Frame (SDF) room.
4. Fire Control room
5. Other equipment or computer rooms (yet to be defined) to house equipment racks for networking
equipments.
The earth main terminal bar should be designed (by M&E Engineer) with multiple earth terminal connections
for provision of,
1. Connection of an earth conductor to common earth bed system.
2. Connection of testing terminals in order to facilitate measurement of earth resistance value at the main
terminal bar.
3. Connection of an earth conductor to the equipment to be earthed.
Any area provided with access flooring system, the whole flooring system shall be bonded to earth potential
bar which should be designed by M&E Engineer.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 80 of 90
4.1.3 Fire Protection System
M&E Engineer should provide risk assessment of fire protection system for computer or equipment room.
The construction of the equipment room should comply with the passive and active fire requirement. The room
should be considered to have fire compartmentation with appropriate fire extinguishing system.
Water base or carbon dioxide fire extinguishing system should not be installed at the equipment room. Inergen
or FM200 fire extinguishing agent should be considered (by M&E Engineer).
4.1.4 Electro Magnetic Interference Protection System
Depending on the final location of the equipment room (i.e. MDF, SDF, computer and server room), protection
against electromagnetic interference should be provided for the whole room in order to minimize
electromagnetic interference of the telecommunication signal. M&E Engineer shall carry out the detail design.
Material selection for raceways should be galvanised metal trunking or galvanised iron pipe to minimise EMI
signal from the power cables which may running side by side
4.1.5 Protection Against Vandalism
Physical security of Tech-Linx assets is very important, as it takes only one disgruntled employee to bring down
the entire system. Physical security also ensures that there is no possibility of accidental damage to equipment
or cabling.
All server rooms, network closets and manhole points should be designed to be secured and vandal proof at all
times and only authorised personnel should be allowed access to these locations. All access to these points
should be logged either via secure card access systems or manual log entries.
The ICT Engineer would design additional reinforced security access system. In addition, the routing and
selection of the raceway should be coordinated to ensure the following,
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 81 of 90
Accessibility for maintenance
Alternative routing for back-up purposes
4.1.6 Uninterrupted Power Supply System
In order to safe guard the ICT equipment installation from any possible power failure, the risk assessment for
the electrical power supply should be carried out by the M&E Engineer as the designer of the power distribution
system. However, the following precautions shall be considered but not limited to,
All power outlets to serve all ICT equipment shall be tapped from the building emergency supply
(designed by M&E Engineer) to overcome possible normal power breakdown. This could be involved in
providing emergency power outlets at ICT equipment rooms, communication riser closet, building
security closet, telephone closet or any part of the room where ICT equipments are being installed.
Since there is a possibility of common emergency electrical distribution boards feeding the other area of
installation which may result in power tripping due to other part of installation, additional power back-
up shall be provided by using interrupted power supply (UPS) units with appropriate back-up time. The
UPS units shall provide continuous power supply during transition from normal to emergency power
during normal power breakdown. The UPS could also provide conditioned power to the ICT equipment,
which may be sensitive to dirty power input.
UPS Unit Type Application
1 Rack mount, standalone on-line with 30 All networking equipment, switches, or any
minutes back-up time critical ICT equipment installed on the rack at
communication riser closet or equipment room.
This shall be included in ICT package
2 Floor standing, standalone line –interactive, All user stations. This shall depend on end-user
with 5 minutes back-up time requirement.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 82 of 90
Depending on the criticality of the equipment, redundancy could be provided in the UPS installation due
to possible breakdown or maintenance requirement of the UPS unit. Parallel operation should be
provided for this purpose.
It also possible to provide central UPS system with full redundancy in parallel operation for all the
equipment in the central equipment room, but additional space and appropriate capacity power isolator
or switch should be allocated for the purpose.
A modular hot swappable type UPS could be considered in consideration of its ease of expansion to
higher rating compare with fixed modular type UPS.
The selected UPS units shall have provision for external communication for central monitoring and
controlling together with unattended shutdown software.
4.2 Preparatory Base Building Works
4.2.1 Electrical Works
The electrical trade contractor should include under the electrical scope of works of the following,
Risk assessment for electrical power distribution system to all ICT, Security and IBMS equipment which
required permanent 24hours uninterrupted power supply.
Power supply via dedicated electrical distribution boards to the equipment or computer rooms.
Small power installation using switched socket outlets to all equipment, preferably the source to be
tapped from the emergency supply.
All electronic surge protection devices for power lines.
Lighting system installation.
Earthing protection system.
Protection system against electromagnetic interference.
Refer to other part of section 4.2 for other proposed detail requirement.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 83 of 90
Whereas the IT trade contractor should include in their scope of works data point provision for connection by
Electrical trade contractor to
Administration station for electrical control and monitoring stations.
Other provision spelled out by M&E Engineer
4.2.1.2 Conduit to door security devices
The doors and the door hardware need to be coordinated with the security subcontractor at the earliest
possible opportunity. We propose to make this the number one priority of the DD phase of the project and will
try to have door conduit drawings ready within two weeks of the approval to proceed with the DD phase. With
respect to the door hardware, we will attempt to coordinate that with the Architect within the same time period
and to help us in this matter we request door schedules be sent to us as soon as possible. In particular we
need to know whether the doors are wood, glass or metal and whether they are single leaf or double leaf.
4.2.1.3 BAS power requirements
Power will be required at anticipated control panel locations and at the Central Control Room. We suggest that
a 240Vac, 20 A, circuit be provided by the electrical trade at the Central Control Room. Power should be
provided to the 24Vac transformer in each AHU control panel by the electrical trade. A 240Vac source is
required at each VAV terminal unit location.
4.2.1.4 BAS trunking
Certain trunking runs would be best provided by the electrical subcontractors rather than the BAS and BSS
subcontractors. Our intent is that the BSS and BAS panels will be placed in the AHU rooms and the CCR. We
will provide a firm recommendation on the trunking runs at the beginning of the DD phase when we have
finally located all of the CCTV cameras.
4.2.1.5 Emergency Generator
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 84 of 90
The mimic board for the emergency generator should be located at the emergency generator with a duplicate
at the CCR or with an interface to the BAS. In the case of the latter the generator manufacturer should provide
a terminal strip at the emergency generator with all points wired to it.
4.2.2 Mechanical Works
The mechanical trade contractor should include under the mechanical scope of works of the following,
Risk assessment for mechanical services at equipment or computer rooms, which require permanent
24hour uninterrupted air conditioning systems and free from any possible water leakage.
Air conditioning and ventilation system to the equipment rooms and communication riser closets.
Appropriate fire detection and extinguishing system.
Refer to other part of section 4.2 for other proposed detail requirement.
Whereas the IT trade contractor should include in their scope of works data point provision for connection by
mechanical trade contractor to
1. Administration station for Building Automation System (BAS)
2. Other provision spelled out by M&E Engineer
The IBMS subcontractor will not be appointed until late in the project. In order to expedite matters it is
suggested that the base-building subcontractors can undertake certain preparatory work. This work is detailed
below but it is emphasised that this is preliminary and a more comprehensive set of guidelines will be
developed at the commencement of the design development phase:
4.2.2.1 VAV boxes:
The boxes are available with an exterior controls enclosure and with other options such as a 240Vac to 24Vac
transformer, 24Vac damper actuator and flow cross. These options should all be purchased and the damper
actuator and transformer secondary wiring should be brought to a terminal strip in the enclosure. The tubing
from the flow cross should be terminated on bulkhead fittings on the side of the box. The arrangement of
components within the controls enclosure should be such as to maximise the space available for the VAV box
DDC controller that will be mounted by the BAS subcontractor.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 85 of 90
4.2.2.2 Air handling units:
The AHU have a several monitoring and control functions that can be facilitated by taking appropriate steps at
the factory. We wish to suggest that the following be undertaken by the AHU manufacturer:
Provide a controls enclosure mounted on the side of the AHU near the variable frequency drive
controller. The enclosure should be sufficiently large to house the items detailed below and should, at
minimum, meet IP54 requirements.
Install a 1000 ohm platinum RTD in the supply air outlet. This should be wired back to a terminal strip
in the controls enclosure. The BAS subcontractor will furnish the RTD.
Install a differential pressure switch across the filters and wire to the terminal strip in the controls
enclosure. The BAS subcontractor will furnish the sensor.
The AHU manufacturer should wire the following points to the terminal strip in the controls enclosure
for the monitoring and control of the VFD:
o Fan start/stop: A set of contacts should be available at the VFD and should be wired to
the terminal strip in the controls enclosure such that when the AHU DDC controller closes
a relay across the contacts the fan starts and when the AHU DDC controller relay opens
the fan stops.
o Fan status: A set of contacts should be available at the VFD and should be wired to the
terminal strip in the controls enclosure such that when the AHU DDC controller senses a
closed contact across the terminals the fan is running and when the AHU DDC controller
senses an open contact across the terminals the fan is not running.
o Speed control: A set of terminals should be available in the VFD controller and and
should be wired to the terminal strip in the controls enclosure such that a 4 to 20mA, or
0 to 10V, signal output from the BAS will control fan speed between the locally set
minimum and maximum speeds.
o VFD controller alarm: A set of terminals should be available in the VFD controller and
should be wired to the terminal strip in the controls enclosure such that when the BAS
senses a contact closure across the terminals the VFD controller is in alarm and when the
contact is open across the terminals the VFD controller is not in alarm.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 86 of 90
Install the chilled water coil control valve and wire the actuator to the terminal strip in the controls
enclosure. The BAS subcontractor will furnish the valve.
We would like to suggest that the AHU manufacturer submit drawings to us for the above at the start of the DD
phase.
4.2.2.3 Damper actuators
A terminal strip should be provided at every BAS controlled damper. The terminals should be wired such that
the BAS subcontractor only has to provide a contact closure across a pair of terminals to close the two position
dampers and provide a 4 to 20mA or 0 to 10V signal at the terminal strip for modulating dampers. There
should be no requirement for the BAS subcontractor to access the damper actuator and we would suggest that
the same should be true for the FAS subcontractor for those dampers that are controlled by the FAS. If the
damper terminal strip is designed properly there will be no coordination difficulties between the FAS and BAS
subcontractors, as they will be wiring to separate terminals. The wiring should be such that the FAS always
overrides the BAS control of dampers.
4.2.2.4 Motor Starters
This applies to the motor starters for single speed motors that are monitored and/or controlled by the BAS
and/or FAS. A termination strip should be provided by the trade furnishing the motors to which the BAS
subcontractor and FAS subcontractor can wire to stop/ start the motor, monitor the motor on/off status and
monitor the trip status. There should be no requirement for the IBMS subcontractor to access the motor
starters and we would suggest that the same should be true for the FAS subcontractor for those motors that
are controlled by the FAS. If the motor terminal strip is designed properly there will be no coordination
difficulties between the FAS and IBMS subcontractors, as they will be wiring to separate terminals. The wiring
should be such that the FAS always overrides the BAS control of motors. We would suggest that the applicable
subcontractor submit drawings to us for our review at the beginning of the DD phase.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 87 of 90
4.2.2.5 Sprinkler System
The sprinkler system serving the CCR and the computer room should be changed from a wet pipe system to a
dry pipe preaction system.
4.2.2.6 FAS Mimic Panel
The FAS mimic panel should be located at the CCR by the FAS subcontractor in accordance with the CCR
design.
4.2.3 Architectural Works
CONDUIT/TRUNKING ENTRY SPACE FOR WALL
FROM THIS WALL MOUNTED EQUIPMENT
The architectural requirement for IBMS CCR also applicable for ICT Equipment room proposed at basement
EQUIPMENT ROOM Level at each block.
SPACE FOR UPS
SPACE FOR 8 NOS X 19 INCH 4.2.3.1 Central Control Room (CCR)
RACK UNITS
CENTRAL CONTROL ROOM
SPACE FOR FAS
The Central Control Room should be finished with raised floor and 24 hour air conditioning suitable for the
GRAPHICAL ANNUNCIATOR
PANELS AND LIFT/GENSET PANELS
quantity of equipment and a minimum of four (4) people. A 30KVA electrical service should be brought to the
PASS THROUGH BASED ON EVANS MODULAR CONSOLES PROVIDES
WINDOW 17 NOS X MODULES AS REQUIRED TO ACCOMODATE
BCS/BSS/FAS/LIFT/GEC, EQUIPMENT, GENSET ETC EQUIPMENT
equipment room where it will be connected to the UPS by the IBMS subcontractor. The electrical service for
this location should be from the emergency power panel.
PRINTERS
A proposed layout for the CCR is shown in Appendix Q. The lift mimic board and the FAS mimic board should
PHOTO STUDIO
SPACE FOR DRAWING
RACKS AND/OR be located by the appropriate sub-contractors as shown in CCR proposed layout. This room should be ready
LAYOUT TABLES
SPACE FOR STORAGE/SHELVING/CABINETS
OR FUTURE PRJECTION SCREEN and suitable for housing computer based equipment by the time of IBMS subcontract award.
VIDEO IMAGING
CAMERA
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 88 of 90
4.3 IBMS Contract Documents And Potential Subcontractors
4.3.1 IBMS Contract Documents
Primarily because of the tight schedule, we have proposed that a single tender package be prepared and a
single contract be let for the IBMS. The IBMS work will cover the following:
Furnishing and installing a BAS
Furnishing and installing a BSS
Integrating the BAS, BSS, FAS, the lift monitoring and control system, the electrical metering system,
lighting control system (if a stand-alone system is provided) and the maintenance management and
inventory control system.
Providing an interface to the IT (data) system.
We anticipate that the specification will incorporate the following Sections:
IBMS Bid Forms
General Conditions and Supplemental Conditions
Scope of Work
General Requirements
Testing and Inspections
Documentation
Training
Installations – General
Installations – Electrical
IBMS Network and Workstations
BAS Control Panels
BAS Software
BSS CCTV Security Surveillance System
BSS Voice Intercom System
BSS Access Control and Monitoring System
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 89 of 90
BAS Field Termination Schedules
BSS Device Lists
IBMS Drawings
4.3.2 Potential IBMS Subcontractors
We believe that the following are potential IBMS contractors:
Siemens
Honeywell Engineering Sdn. Bhd.
Johnson Controls (Malaysia) Sdn. Bhd.
We are of the opinion that the IBMS subcontractor must meet the following criteria:
Have a local staff in the Kuala Lumpur area of trained personnel capable of giving instructions and
providing routine and emergency maintenance on the IBMS, all components and software/firmware and
all other elements of the IBMS.
Have a proven record of experience in the supply and installation of BAS and BSS over a minimum
period of five (5) years.
Have successfully installed a similar IBMS on a previous project of comparable size and complexity.
Have comprehensive local service and support facilities for the total IBMS as provided.
Maintain local, or have approved local contracted access to, supplies of essential expendable parts.
In some instances, we foresee a potential vendor subcontracting a portion(s) of the work. We suggest that
this is acceptable but the organisation undertaking the systems integration must be the single source of
responsibility and be the one that contracts with Tech-Linx as the IBMS subcontractor.
We strongly recommend that the IBMS subcontractor be required to demonstrate the integrated systems at the
factory prior to being allowed to commence installation on site. Generally the site environment is not
conducive to R and D work or to solving software problems.
We believe that, at this stage, the above listed potential contractors should not be considered as the only viable
potential IBMS subcontractors.
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 90 of 90
End of Report
Initial Concept Report for
Information Communication Technology, Security and IBMS
Page 91 of 90
You might also like
- Inside Bluetooth Low Energy (PDFDrive)Document456 pagesInside Bluetooth Low Energy (PDFDrive)Daniel NazwiskoNo ratings yet
- Optix Metro 100 V100R002 System Description V1 20Document33 pagesOptix Metro 100 V100R002 System Description V1 20Nguyen Minh Tu88% (8)
- SAN Implementation Workshop - StudentGuideDocument934 pagesSAN Implementation Workshop - StudentGuidekarthick100% (2)
- Computer Network Security and Cyber EthicsDocument15 pagesComputer Network Security and Cyber EthicsMaryjade NecesarioNo ratings yet
- FE4Document276 pagesFE4Cuong Le100% (1)
- English Workbook Cloudf 202105Document94 pagesEnglish Workbook Cloudf 202105diegoNo ratings yet
- Implementing Database Security and AuditingFrom EverandImplementing Database Security and AuditingRating: 4.5 out of 5 stars4.5/5 (3)
- Case Study Ministry of Education WifiDocument61 pagesCase Study Ministry of Education WifilololololNo ratings yet
- Telecommunication Networks For The Smart Grid by Alberto Sendin, Miguel A. Sanchez-Fornie, Iñigo Berganza, Javier Simon, Iker UrrutiaDocument361 pagesTelecommunication Networks For The Smart Grid by Alberto Sendin, Miguel A. Sanchez-Fornie, Iñigo Berganza, Javier Simon, Iker UrrutiaAn NguyenNo ratings yet
- Ars Acnps PDFDocument136 pagesArs Acnps PDFDiana GabrielaNo ratings yet
- Service Provision: Technologies for Next Generation CommunicationsFrom EverandService Provision: Technologies for Next Generation CommunicationsNo ratings yet
- The Convergence of Internet of Things and Cloud For Smart ComputingDocument139 pagesThe Convergence of Internet of Things and Cloud For Smart ComputingSasikumar PNo ratings yet
- Indian Telecom Security Assurance Requirements (ITSAR) : 5G Aggregated GNB NSA Option - 3, 7 & 4Document74 pagesIndian Telecom Security Assurance Requirements (ITSAR) : 5G Aggregated GNB NSA Option - 3, 7 & 4Vijju JatNo ratings yet
- Cloud Computing NetworkingDocument515 pagesCloud Computing Networkingnoisi80100% (2)
- ICT Literacy For Secondary SchoolDocument6 pagesICT Literacy For Secondary Schoolnurislah83No ratings yet
- GoBISM Manual for Securing Bangladesh Government InformationDocument143 pagesGoBISM Manual for Securing Bangladesh Government InformationRAJAN DASNo ratings yet
- Internet of Everything PrintableDocument167 pagesInternet of Everything Printableahme imtiazNo ratings yet
- Conettix IP A E Specification enUS 2664119691Document17 pagesConettix IP A E Specification enUS 2664119691Jim TenchNo ratings yet
- Data Communications and Networking For Manufacturing IndustriesDocument12 pagesData Communications and Networking For Manufacturing Industriestruepathfinder23No ratings yet
- Toncich Data Communications and Networking For Manufacturing Industries (2nd Edition) (Chrystobel Engineering)Document348 pagesToncich Data Communications and Networking For Manufacturing Industries (2nd Edition) (Chrystobel Engineering)siritapeNo ratings yet
- ELTE3.1.1 Huawei Technical Proposal Template For Metro V2.0Document77 pagesELTE3.1.1 Huawei Technical Proposal Template For Metro V2.0Desislav Evlogiev Petkov50% (2)
- Computer Networks - RefDocument157 pagesComputer Networks - RefHeman SetiaNo ratings yet
- Wu Mengdi-2017-Wireless Communication Applications in Internet of ThingsDocument57 pagesWu Mengdi-2017-Wireless Communication Applications in Internet of ThingsDen NisNo ratings yet
- Internet of Things (IoT)Document366 pagesInternet of Things (IoT)pittsfr100% (5)
- Cloud Computing BookDocument8 pagesCloud Computing Booklourdesmaryamulu8500No ratings yet
- Veer Narmad South Gujarat University, Surat MCA (5 Semester) Network GroupDocument15 pagesVeer Narmad South Gujarat University, Surat MCA (5 Semester) Network GroupKanhaNo ratings yet
- Mobile Telecommunications Protocols for Data NetworksFrom EverandMobile Telecommunications Protocols for Data NetworksRating: 2.5 out of 5 stars2.5/5 (2)
- 02-sx Toc r2.2.mhtDocument6 pages02-sx Toc r2.2.mhtAhmedNo ratings yet
- Principles of Computer Communication NetworksDocument8 pagesPrinciples of Computer Communication NetworksAngel Acosta - ArnadoNo ratings yet
- IOT For SMEs - HandbookDocument58 pagesIOT For SMEs - HandbookbluesbankyNo ratings yet
- Intelligent Internet Knowledge Networks: Processing of Concepts and WisdomFrom EverandIntelligent Internet Knowledge Networks: Processing of Concepts and WisdomNo ratings yet
- Smart Grid Security by Gilbert N. WWW Pdfbook Co KeDocument308 pagesSmart Grid Security by Gilbert N. WWW Pdfbook Co KeHossam Eldin TalaatNo ratings yet
- IoT Security GuideDocument145 pagesIoT Security GuideAli0% (1)
- Virtualized Software Defined Networks and Services by Mehmet Toy and Qiang DuanDocument328 pagesVirtualized Software Defined Networks and Services by Mehmet Toy and Qiang Duancota_carinhasNo ratings yet
- Towards 4G Technologies: Services with InitiativeFrom EverandTowards 4G Technologies: Services with InitiativeHendrik BerndtNo ratings yet
- Design and Implementation of A Local Area Network Utilizing IntelDocument105 pagesDesign and Implementation of A Local Area Network Utilizing IntelPrince Kennedy Mark OgucheNo ratings yet
- IT Infrastructure Requirements Needed To Run SAP BCM SoftwareDocument76 pagesIT Infrastructure Requirements Needed To Run SAP BCM SoftwareLuis StephlitchNo ratings yet
- Syllabus of Comm NWDocument1 pageSyllabus of Comm NW20ELB355 MOHAMMAD ESAAMNo ratings yet
- How Communication Works in Real-Time ProjectsDocument131 pagesHow Communication Works in Real-Time ProjectsKrishna OodhorahNo ratings yet
- Final ProjectDocument78 pagesFinal ProjectKeertana RNo ratings yet
- Seconet PRJ enDocument42 pagesSeconet PRJ enGelu BordeaNo ratings yet
- MX ML T25MX-Part2 en 20140430Document128 pagesMX ML T25MX-Part2 en 20140430andrius petkusNo ratings yet
- Architectures 15: Preface Xiii List of Abbreviations XV A Guide To The Book Xxiii 1 1Document8 pagesArchitectures 15: Preface Xiii List of Abbreviations XV A Guide To The Book Xxiii 1 1D P TEJASHNo ratings yet
- Identity-Based Networking Services: MAC Security: Deployment GuideDocument32 pagesIdentity-Based Networking Services: MAC Security: Deployment GuidewertreNo ratings yet
- Nrusso Ccie Ccde Evolving Tech 1july2018 PDFDocument173 pagesNrusso Ccie Ccde Evolving Tech 1july2018 PDFThiago SantosNo ratings yet
- Evolved Packet System (EPS): The LTE and SAE Evolution of 3G UMTSFrom EverandEvolved Packet System (EPS): The LTE and SAE Evolution of 3G UMTSNo ratings yet
- Distributed Systems Characterisation and Design: 1DT057 D I SDocument35 pagesDistributed Systems Characterisation and Design: 1DT057 D I SJhen JhenNo ratings yet
- PHP DocDocument192 pagesPHP DocEphrem ChernetNo ratings yet
- B426 Installation Gu Installation ManualDocument38 pagesB426 Installation Gu Installation ManualJose RamirezNo ratings yet
- Ad Hoc Wireless Networks Architectures and Protocols 013147023x 9780131470231Document881 pagesAd Hoc Wireless Networks Architectures and Protocols 013147023x 9780131470231tiyasofficial0099No ratings yet
- Smart HomeDocument5 pagesSmart HomeRahiman Mat YassimNo ratings yet
- Malaysia International Remote Control Car ChampionshipDocument11 pagesMalaysia International Remote Control Car ChampionshipRahiman Mat YassimNo ratings yet
- New Marketing OfficeDocument8 pagesNew Marketing OfficeRahiman Mat YassimNo ratings yet
- Network Design & Telephone SystemDocument1 pageNetwork Design & Telephone SystemRahiman Mat YassimNo ratings yet
- TDCDocument2 pagesTDCRahiman Mat YassimNo ratings yet
- New Marketing OfficeDocument8 pagesNew Marketing OfficeRahiman Mat YassimNo ratings yet
- Silver It AgeDocument13 pagesSilver It AgeRahiman Mat YassimNo ratings yet
- Proposal DiagramDocument4 pagesProposal DiagramRahiman Mat YassimNo ratings yet
- Johnson Matthey SCS 2Document4 pagesJohnson Matthey SCS 2Rahiman Mat YassimNo ratings yet
- Entrutech DocumentationDocument1 pageEntrutech DocumentationRahiman Mat YassimNo ratings yet
- TASB Network Design2Document2 pagesTASB Network Design2Rahiman Mat YassimNo ratings yet
- Chime DesignDocument2 pagesChime DesignRahiman Mat YassimNo ratings yet
- Sample of RackDocument2 pagesSample of RackRahiman Mat YassimNo ratings yet
- LAN System For Precint 10Document6 pagesLAN System For Precint 10Rahiman Mat YassimNo ratings yet
- Fiber Optic Connection PJH To CMCDocument27 pagesFiber Optic Connection PJH To CMCRahiman Mat YassimNo ratings yet
- Record CablingDocument3 pagesRecord CablingRahiman Mat YassimNo ratings yet
- LAN Node & SpecDocument7 pagesLAN Node & SpecRahiman Mat YassimNo ratings yet
- LAN System For Precint 10Document6 pagesLAN System For Precint 10Rahiman Mat YassimNo ratings yet
- Bai1 / PLC - 1 (CPU 1214C DC/DC/DC) : S7-1200 Station - 1Document9 pagesBai1 / PLC - 1 (CPU 1214C DC/DC/DC) : S7-1200 Station - 1Pháp Sư Giấu MặtNo ratings yet
- Ccnas Chp4 Ptactb Cbac InstructorDocument4 pagesCcnas Chp4 Ptactb Cbac InstructorCarlos QuiñonesNo ratings yet
- Lenovo B590-LB59A MB-12209-1 48.4XB01.011 Schematic Diagram PDFDocument102 pagesLenovo B590-LB59A MB-12209-1 48.4XB01.011 Schematic Diagram PDFjimmy tjahyonoNo ratings yet
- Cisco Expansionmodules Datasheet enDocument16 pagesCisco Expansionmodules Datasheet enPrince AttoblaNo ratings yet
- Norsok T 003Document22 pagesNorsok T 003erstendrainNo ratings yet
- Anue Path Delay Product BriefDocument2 pagesAnue Path Delay Product Briefbakh777196No ratings yet
- Guidelines On Connecting GearS2 Device Using WiFi For GWDDocument9 pagesGuidelines On Connecting GearS2 Device Using WiFi For GWDanusprasadNo ratings yet
- CR750, CR751 - Instruction Manual (Ethernet Function) BFP-A3379-0 (03.15)Document82 pagesCR750, CR751 - Instruction Manual (Ethernet Function) BFP-A3379-0 (03.15)ayxworks eurobotsNo ratings yet
- Cortelco 274701-VIP-PAKDocument45 pagesCortelco 274701-VIP-PAKmercadotecnicaNo ratings yet
- Setup Local Yum Repository On CentOS 7Document9 pagesSetup Local Yum Repository On CentOS 7JOHN JAIRO ARGUELLO GODOYNo ratings yet
- TRADXTAPP00215Document79 pagesTRADXTAPP00215Ahmed IsmailNo ratings yet
- Introtociscosafe 2023 PDFDocument50 pagesIntrotociscosafe 2023 PDFMichael O'ConnellNo ratings yet
- Real Estate Management System Design DocumentDocument8 pagesReal Estate Management System Design DocumentjhateshkolipakulaNo ratings yet
- 1 - STP VLAN VTP EtherChannel Threat Mitigation - TermDocument1 page1 - STP VLAN VTP EtherChannel Threat Mitigation - TermOlga BradyNo ratings yet
- RF Optimization Engineer - Google SearchDocument3 pagesRF Optimization Engineer - Google Searchanil kumarNo ratings yet
- Network Management Mod1Document21 pagesNetwork Management Mod1Bharath N ReddyNo ratings yet
- Radio Training LTE2Document30 pagesRadio Training LTE2Roro JNo ratings yet
- Localhost 1947 Int DiagnosticsDocument7 pagesLocalhost 1947 Int DiagnosticsMichael Steinhorst AlcantaraNo ratings yet
- Difference Between OST and PSTDocument4 pagesDifference Between OST and PSTrayar_ramuNo ratings yet
- Apache CloudStack 4.2.0 Release Notes en USDocument39 pagesApache CloudStack 4.2.0 Release Notes en USsgrrscNo ratings yet
- Experiment-2: Aim: Familiarization With Networking Components-Hub Switch Repeater Router GatewayDocument3 pagesExperiment-2: Aim: Familiarization With Networking Components-Hub Switch Repeater Router GatewayKetanNo ratings yet
- HypervisorDocument2 pagesHypervisormadhusudhananNo ratings yet
- Procedure of Network Settings of D9004/D9008/D9216Document5 pagesProcedure of Network Settings of D9004/D9008/D9216adytzuuvNo ratings yet
- Mapping Security Controls Against Security Guidance RecommendationsDocument23 pagesMapping Security Controls Against Security Guidance RecommendationsRuslan SoloviovNo ratings yet
- 2 AT4 Wireless IoT Seminar LTE Rev4Document43 pages2 AT4 Wireless IoT Seminar LTE Rev4Hernan SernaNo ratings yet
- TL-WA855RE (EU) 5.0 DatasheetDocument5 pagesTL-WA855RE (EU) 5.0 DatasheetJohnyNo ratings yet
- Optical EthernetDocument29 pagesOptical EthernetNiharika Madgula100% (1)
- Sigtran-Sctp, M3ua, M2paDocument16 pagesSigtran-Sctp, M3ua, M2paabhishek sinhaNo ratings yet
- Ieee Projects Final Year Projects Mca Me Be Java Dot Net Projects Micans InfotechDocument7 pagesIeee Projects Final Year Projects Mca Me Be Java Dot Net Projects Micans InfotechgingeevimalNo ratings yet