Professional Documents
Culture Documents
Ilovepdf Merged
Uploaded by
Payal KhuspeOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Ilovepdf Merged
Uploaded by
Payal KhuspeCopyright:
Available Formats
Vishwaniketan's Institute of Management Entrepreneurship and Engineering
Technology (ViMEET)
INDEX
Sr. No. Name of Experiments Marks DOP DOS Sign
1 Design and Implementation of a product
cipher using Substitution and Transposition
ciphers.
2 Implementation and analysis of RSA
cryptosystem and Digital signature scheme
using RSA/El Gamal.
3 Implementation of Diffie Hellman Key
exchange algorithm
4 For varying message sizes, test integrity of
message using MD-5, SHA-1, and analyse
the performance of the two protocols. Use
crypt APIs.
5 Exploring wireless security tools like
Kismet, NetStumbler etc.
6 Study the use of network reconnaissance
tools like WHOIS, dig,traceroute, nslookup
to gather information about networks and
domain registrars.
7 Study of packet sniffer tools wireshark, :-
1. Observer performance in promiscuous as
well as non-promiscuous mode. 2. Show
the packets can be traced based on different
filters.
8 Download and install nmap. Use it with
different options to scan open ports,
perform OS fingerprinting, do a ping scan,
tcp port scan, udp port scan, etc. .
9 Detect ARP spoofing using nmap and/or
open source tool ARPWATCH and
wireshark
10 Use the NESSUS/ISO Kaali Linux tool to
scan the network for vulnerabilities
11 Set up IPSEC under LINUX. b) Set up
Snort and study the logs. c) Explore the
GPG tool of linux to implement email
security.
Total Marks
Prof. Snehal Raskar CSS
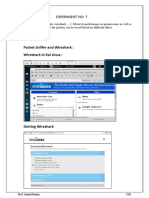
EXPERIMENT NO: 7
AIM: Study of packet sniffer tools wireshark, :- 1. Observer performance in promiscuous as well as
non-promiscuous mode. 2. Show the packets can be traced based on different filters.
IMPLEMENTATION:
Packet Sniffer and Wireshark :
Wireshark in Kai Linux :
Getting Wireshark
Prof. Snehal Raskar CSS
Starting Wireshark :
Prof. Snehal Raskar CSS
Capturing Packets :
Test Run :
Prof. Snehal Raskar CSS
Prof. Snehal Raskar CSS
EXPERIMENT NO: 8
AIM: Download and install nmap. Use it with different options to scan open ports, perform OS
fingerprinting, do a ping scan, tcp port scan, udp port scan, etc. .
Implementation of Nmap :
$ sudo apt-get install Nmap
Prof. Snehal Raskar CSS
EXPERIMENT NO: 9
AIM: Detect ARP spoofing using nmap and/or open source tool ARPWATCH and wireshark
IMPLEMENTATION:
ARP Spoofing using Nmap :
If you suspect you may be suffering from an ARP poisoning attack, you can
check in Command Prompt. First, open Command Prompt as an administrator.
The easiest way is to press the Windows key to open the start menu. Type in
“cmd”, then press Crtl, Shift and Enter at the same time.
This will bring up Command Prompt, although you may have to click Yes to give
the app permission to make changes. In the command line, enter:
arp -a
This will give the ARP table:
Navaneeth
Navaneeth
Prof. Snehal Raskar CSS
EXPERIMENT NO: 10
AIM: Use the NESSUS/ISO Kaali Linux tool to scan the network for vulnerabilities
IMPLEMENTATION:
Output:
● Click the ‘New Scan’.
● Click ‘Basic Network Scan’.
● Name your scan and add a description.
● In the “Targets” field, you’ll want to enter IP scanning details about your home
network. For example, if your router is at 192.168.0.1, you’d want to enter
192.168.0.1/24. This will make it so Nessus scans all the devices on your
network.
Prof. Snehal Raskar CSS
● Click ‘Save’.
● On the next screen, click the play icon to launch the scan.
Prof. Snehal Raskar CSS
Prof. Snehal Raskar CSS
Your results should include all the devices on your local network, from your router to
your Wi-Fi enabled printer. Click the Vulnerabilites tab to see an overview of all the
potential vulnerabilities on the network as a whole.
Prof. Snehal Raskar CSS
You might also like
- Evaluation of Some Intrusion Detection and Vulnerability Assessment ToolsFrom EverandEvaluation of Some Intrusion Detection and Vulnerability Assessment ToolsNo ratings yet
- Evaluation of Some Windows and Linux Intrusion Detection ToolsFrom EverandEvaluation of Some Windows and Linux Intrusion Detection ToolsNo ratings yet
- CSS Lab Manual - 17-26Document10 pagesCSS Lab Manual - 17-26Payal KhuspeNo ratings yet
- CSS Lab Manual - 3Document1 pageCSS Lab Manual - 3Payal KhuspeNo ratings yet
- Network Security Lab Manual DraftDocument29 pagesNetwork Security Lab Manual DraftShraddha PatilNo ratings yet
- Laboratory Setup: Step 1: Download Metasploitable, Which Is A Linux Machine. It Can Be Downloaded FromDocument13 pagesLaboratory Setup: Step 1: Download Metasploitable, Which Is A Linux Machine. It Can Be Downloaded FromTajria SultanaNo ratings yet
- Network Security Lab ManualDocument71 pagesNetwork Security Lab ManualSankalp Balannavar100% (1)
- CSS Lab SyllabusDocument2 pagesCSS Lab Syllabus48Nara Amit GopalNo ratings yet
- Lab 06 TaskDocument2 pagesLab 06 TaskZuraiz QureshiNo ratings yet
- Scanning Phase 2 Eh 4Document25 pagesScanning Phase 2 Eh 4api-224615605No ratings yet
- 3 NmapDocument6 pages3 NmapJohn WickNo ratings yet
- Lab-M04-02 Team 6Document10 pagesLab-M04-02 Team 6api-377949857No ratings yet
- Security & Ethical Hacking p2Document29 pagesSecurity & Ethical Hacking p2Vipin NarangNo ratings yet
- 03 - Performing Security AssessmentsDocument78 pages03 - Performing Security AssessmentsDoraemonNo ratings yet
- CN - Exp-4Document4 pagesCN - Exp-4FLICKA 69No ratings yet
- CIT 480: Securing Computer Systems Lab #7: Network Scanning NameDocument4 pagesCIT 480: Securing Computer Systems Lab #7: Network Scanning NameManzu PokharelNo ratings yet
- 3 NetworkSecurity LABManualDocument33 pages3 NetworkSecurity LABManualdahiyalkNo ratings yet
- CS - ALL - Practical FileDocument34 pagesCS - ALL - Practical FilebrijeshNo ratings yet
- Top 16 Nmap Commands To Scan Remote HostsDocument10 pagesTop 16 Nmap Commands To Scan Remote Hostsmindhackers161No ratings yet
- Practicals 2Document3 pagesPracticals 2Tarik AmezianeNo ratings yet
- Name: Pradeep Gupta Roll No: 112 Div: ADocument3 pagesName: Pradeep Gupta Roll No: 112 Div: APradeep GuptaNo ratings yet
- 03 - Performing Security AssessmentsDocument78 pages03 - Performing Security Assessmentsتيمور الجبورNo ratings yet
- CSS List of ExpsDocument1 pageCSS List of ExpsGanesh PanigrahiNo ratings yet
- VaptDocument21 pagesVaptSri GouriNo ratings yet
- Isaa Ass5Document7 pagesIsaa Ass5Akash SharmaNo ratings yet
- Experiment - 3: Advanced Cyber Security - 4028Document12 pagesExperiment - 3: Advanced Cyber Security - 4028JITESH SINGHNo ratings yet
- Advanced Nmap Command Line OptionsDocument4 pagesAdvanced Nmap Command Line Optionsksenthil77No ratings yet
- 3.3.1.9 Lab - Detecting Threats and VulnerabilitiesDocument5 pages3.3.1.9 Lab - Detecting Threats and Vulnerabilitieskarenozelleb88No ratings yet
- NetworkSecurity LABManualDocument33 pagesNetworkSecurity LABManualvenkatdhanNo ratings yet
- 4.2.2.5 Lab - Port Scanning An IoT DeviceDocument6 pages4.2.2.5 Lab - Port Scanning An IoT Devicemahin BhuiyanNo ratings yet
- CDIS CV PL.2 ScoutingDocument33 pagesCDIS CV PL.2 ScoutingIvanildo CostaNo ratings yet
- Ceh NS NTP JanDocument18 pagesCeh NS NTP JanA F M BakabillahNo ratings yet
- Cyber Security Lab ManualDocument19 pagesCyber Security Lab ManualadiradityasinghNo ratings yet
- Network Security LAB Manual For DiplomaDocument31 pagesNetwork Security LAB Manual For DiplomaIrshad Khan50% (2)
- NMap - Network MappingDocument35 pagesNMap - Network MappingFaisal AR100% (3)
- What Is NmapDocument5 pagesWhat Is Nmapramya.gNo ratings yet
- Lecture 8Document24 pagesLecture 8Alhussain DarbiNo ratings yet
- Defcon 18 Fyodor Fifield NmapDocument4 pagesDefcon 18 Fyodor Fifield NmapcokebottleNo ratings yet
- Lab 5 InstructionsDocument6 pagesLab 5 InstructionsGrace MwendeNo ratings yet
- Lab 6 - NmapDocument4 pagesLab 6 - NmapAbhi NairNo ratings yet
- CEH ToolsDocument7 pagesCEH ToolsLordWaderNo ratings yet
- Lab IiiDocument14 pagesLab IiiKumar JiNo ratings yet
- Lab Experiment #08 - Network & Host Detection ScansDocument3 pagesLab Experiment #08 - Network & Host Detection ScansAnoop DasNo ratings yet
- 1.host Discovery: Ping&Ping SweepDocument5 pages1.host Discovery: Ping&Ping SweepRafael DalboniNo ratings yet
- Lab 13Document4 pagesLab 13Сейфолла БаяндыNo ratings yet
- SnortDocument5 pagesSnortduccsgo312No ratings yet
- Lecture 4Document22 pagesLecture 4Arwa Juma Al BusaidiNo ratings yet
- 1,2 CSCLDocument15 pages1,2 CSCL20DCS138 MEET VAGAHNINo ratings yet
- Top 4 Packet Crafting ToolsDocument2 pagesTop 4 Packet Crafting ToolsRoger ChangNo ratings yet
- University of Petroleum and Energy Studies Assignment-1Document6 pagesUniversity of Petroleum and Energy Studies Assignment-1khatNo ratings yet
- © 2018 Caendra, Inc. - Hera For PTP - SNMP AnalysisDocument13 pages© 2018 Caendra, Inc. - Hera For PTP - SNMP AnalysisSaw GyiNo ratings yet
- NmapDocument14 pagesNmapamird12No ratings yet
- Attack and PenetrationDocument44 pagesAttack and PenetrationAchmad Hidayat100% (1)
- Nmap Cheat SheetDocument8 pagesNmap Cheat SheetJABERO861108No ratings yet
- NMap Tutorial For Beginners PDFDocument7 pagesNMap Tutorial For Beginners PDFzarakighostNo ratings yet
- Top 32 Nmap Command Examples For SysNetwork AdminsDocument16 pagesTop 32 Nmap Command Examples For SysNetwork AdminswizunuNo ratings yet
- ISL Lab ManualDocument78 pagesISL Lab ManualAbhijeet MoharkarNo ratings yet
- Using Nmap On WindowsDocument7 pagesUsing Nmap On WindowsThando MalazaNo ratings yet
- NMap Usage and Examples ScriptingDocument7 pagesNMap Usage and Examples ScriptingMichel CameloNo ratings yet
- NMAP - Information GatheringDocument6 pagesNMAP - Information GatheringRockstar GmailNo ratings yet
- Ferrography AnalysisDocument34 pagesFerrography Analysistribo technicalNo ratings yet
- HBSC1203 V2Document6 pagesHBSC1203 V2TAY JIUN HOANG MoeNo ratings yet
- Examination of Nutrition Knowledge, Attitude, and Dietary Behaviors of College Student Vegetarians, Semi-Vegetarians, and Non-VegestariansDocument11 pagesExamination of Nutrition Knowledge, Attitude, and Dietary Behaviors of College Student Vegetarians, Semi-Vegetarians, and Non-VegestariansMeilindaNo ratings yet
- Capacity and Facilities DesignDocument59 pagesCapacity and Facilities DesignAnshikaNo ratings yet
- Xlathlete Wingate Pro Hockey Combine Prep WorkoutDocument5 pagesXlathlete Wingate Pro Hockey Combine Prep WorkoutNigel MH Adrian ManobandaNo ratings yet
- Question Text: Answer Saved Marked Out of 1.00Document13 pagesQuestion Text: Answer Saved Marked Out of 1.00Brush & BlushNo ratings yet
- (TP) Chapter 10 - Sound in DuctsDocument9 pages(TP) Chapter 10 - Sound in Ductsagung_123123No ratings yet
- SPE-195122-MS Smart Dual ESP Completion To Develop Stacked ReservoirsDocument13 pagesSPE-195122-MS Smart Dual ESP Completion To Develop Stacked Reservoirsosama aldresyNo ratings yet
- TFT Proto Manual v200Document4 pagesTFT Proto Manual v200albertNo ratings yet
- Cuttack and BhubaneshwarDocument43 pagesCuttack and BhubaneshwarShatabdi SinhaNo ratings yet
- Compressed Natural Gas - WikipediaDocument1 pageCompressed Natural Gas - WikipediaEkampreet KaurNo ratings yet
- Us Navy Flight Test ManualDocument881 pagesUs Navy Flight Test ManualDavid Russo100% (8)
- Cover Letter For Cashier Job With No ExperienceDocument6 pagesCover Letter For Cashier Job With No Experienceplpymkzcf100% (2)
- Dream DeferredDocument10 pagesDream DeferredJayesh JainNo ratings yet
- 03 - Leviticus PDFDocument162 pages03 - Leviticus PDFGuZsolNo ratings yet
- Applied Partial Differential Equations - J. David Logan-1998Document2 pagesApplied Partial Differential Equations - J. David Logan-1998Jeremy Mac LeanNo ratings yet
- Industrial Gases - PPTDocument48 pagesIndustrial Gases - PPTParul Saxena100% (2)
- Series QCT and QCB Cylinders With Integrated Guide: Double-Acting, Magnetic Piston, Guided Ø 20, 25, 32, 40, 50, 63 MMDocument5 pagesSeries QCT and QCB Cylinders With Integrated Guide: Double-Acting, Magnetic Piston, Guided Ø 20, 25, 32, 40, 50, 63 MMVanesaNo ratings yet
- TXDVXX 12Document7 pagesTXDVXX 12Pedro RochaNo ratings yet
- Central Venous Access Device (CVAD) ManagementDocument77 pagesCentral Venous Access Device (CVAD) ManagementEvaG2012No ratings yet
- Servo Cn1 - Chân Để Hàn - CncDocument1 pageServo Cn1 - Chân Để Hàn - CncTrí ChốtNo ratings yet
- Unilever Centralized & Decentralized.Document19 pagesUnilever Centralized & Decentralized.Melody Merry0% (1)
- SS ZG653 (RL1.2) : Software Architecture: BITS PilaniDocument12 pagesSS ZG653 (RL1.2) : Software Architecture: BITS PilaniAditya AggarwalNo ratings yet
- Wiring Diagram HFM-SFI Sequential Multiport Fuel Injection - Ignition System2 w202Document4 pagesWiring Diagram HFM-SFI Sequential Multiport Fuel Injection - Ignition System2 w202mathexscribdNo ratings yet
- Subsurface Investigation For Foundations - Code of Practice: Indian StandardDocument52 pagesSubsurface Investigation For Foundations - Code of Practice: Indian StandardBodhraj singh solanki50% (2)
- Numerology Along With JyotishDocument11 pagesNumerology Along With JyotishAnonymous jGdHMEODVmNo ratings yet
- Technovate Refrigeración y Aire AcondicionadoDocument34 pagesTechnovate Refrigeración y Aire Acondicionadojpg60No ratings yet
- 4 I&m Roadshow Otn v1.2Document47 pages4 I&m Roadshow Otn v1.2vairaveleceNo ratings yet
- High Performance SeriesDocument8 pagesHigh Performance SeriesRonCarNo ratings yet
- GIC TestDocument5 pagesGIC TestRishabh AgarwalNo ratings yet