Professional Documents
Culture Documents
Windows Servers: The NT Security Model
Windows Servers: The NT Security Model
Uploaded by
Jeslam0 ratings0% found this document useful (0 votes)
5 views16 pagesOriginal Title
class06.ppt
Copyright
© © All Rights Reserved
Available Formats
PPT, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
© All Rights Reserved
Available Formats
Download as PPT, PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
5 views16 pagesWindows Servers: The NT Security Model
Windows Servers: The NT Security Model
Uploaded by
JeslamCopyright:
© All Rights Reserved
Available Formats
Download as PPT, PDF, TXT or read online from Scribd
You are on page 1of 16
Windows servers
The NT security model
Breno de Medeiros Florida State University
Fall 2005
NT networks
• Networked NT machines can be:
– Primary Domain controller
• Centralizes user database/authentication
– Backup Domain controller
– Domain member
– Non-domain member
• Trusted domains
• Trusting resources
Breno de Medeiros Florida State University
Fall 2005
Architecture
• Modular
• OS interface (system
calls) are available
at:
– Integral subsystems
– Environment
subsystems
• Both run in the “user
mode” protection
space
Source: http://en.wikipedia.org/wiki/Image:Windows_2000_architecture.PNG
Breno de Medeiros Florida State University
Fall 2005
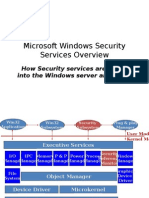
Security viewpoint
• Four main components:
– Executive (kernel mode)
– Protected Servers (user mode)
– Network Subsystem (both kernel and user
modes)
– Administrator tools (user mode)
Breno de Medeiros Florida State University
Fall 2005
Handle tables
• Each process has a table of “object handles” which
enable the process to access those resources
– Maintained by object manager
– Each handle describes the type of access the process has to
the object (read, write, etc)
– The object manager ensures that access is only granted if
compatible with the handle
• When a process requests a new resource for the first
time, the Object Manager asks the Security
Reference Monitor to decide if the process may
acquire the handle.
Breno de Medeiros Florida State University
Fall 2005
File system protection
• Windows NT systems support many file systems,
including:
– File Allocation Table (FAT) FS
– NTFS
– CD-ROM FS (CDFS)
– Named Pipe File System (NPFS)
– Mailslot File System (MSFS)
• Only the NTFS is protected by the access control
system.
• Use FAT only in diskettes
Breno de Medeiros Florida State University
Fall 2005
Configuration Manager
• Keeps the configuration registry
• Stores system configuration information,
including the password database
(SAM), hardware and initialization
information, and OS configuration
information
• Entries in the registry are called keys
Breno de Medeiros Florida State University
Fall 2005
Security-related servers
• Winlogon
• Session Manager
• Local Security Authority
• Security Accounts Manager (SAM)
• Service Controller
• Event Logger
Breno de Medeiros Florida State University
Fall 2005
Local Security Authority
• Local Security Authority Subsystem Service
(LSASS)
– Invoked at login time, it verifies the user
authentication and grants the system access
token (SAT), which is used to start the initial shell
and is inherited by all programs spawned during
this login session
– Performs audit functions
– Operates in user mode
Breno de Medeiros Florida State University
Fall 2005
Security Account Manager
(SAM)
• User mode component
• Maintains the user account database
required by the LSA
• Therefore the login sequence requires
the following intermediation by security-
related services:
– Winlogon LSA SAM
Breno de Medeiros Florida State University
Fall 2005
SAM and authentication
• It is possible to configure a special computer called a
domain controller to consolidate the SAM database in
a single server.
• Secure Attention Sequence: <CTRL> + <ALT> +
<DEL> cannot be captured by user-level programs
– The system invokes Winlogon, which starts a graphical
application (GINA), to handle local and remote connection
requests (via the LSA and SAM)
Breno de Medeiros Florida State University
Fall 2005
Protection (Access Control)
• Windows NT and later provide discretionary access control (DAC). The
unit of control is called an ACE (access control entry). The format of
ACEs is as follows:
ACE Field Description
Inheritance Control Flags •OBJECT_INHERIT ACE
(Boolean flags) •CONTAINER_INHERIT_ACE
•NO_PROPAGATE_INHERIT_ACE
•INHERIT_ONLY_ACE
ACE Type •ACCESS_ALLOWED_ACE
• ACCESS_DENIED_ACE
•SYSTEM_AUDIT_ACE
ACE Type-Specific •SUCCESSFUL_ACCESS_ACE_FLAG
•FAILED_ACCESS_ACE_FLAG
•Access Mask
•SID
Breno de Medeiros Florida State University
Fall 2005
Picture from Final Evaluation of Windows NT Workstations
by Science Applications International Corp./ Ctr. for Information Security
Breno de Medeiros Florida State University
Fall 2005
Windows passwords
• Password policies can be • Better password protection is
established using the offered through passfilt.dll:
UserManager administration • Passwords must be at least six
tool, which supports the characters long
following: • Passwords must contain at least
three of the following four classes of
• Password aging characters:
• Minimum password length – Upper case letters
• Password uniqueness – Lower case letters
– Numbers
• Account lockout features
– Non-alphanumeric characters
– Number of failed logon attempts (punctuation symbols)
– How long to lockout an account • Passwords can not match your
username or part of your full name
listed for the account.
Breno de Medeiros Florida State University
Fall 2005
Windows passwords
• The original Windows password hashing scheme (LM):
– Up to 14-character long passwords (all uppercase).
– Computed as two independent hashes on 7-character values
– Highly vulnerable to dictionary based attacks, such as L0phtrack
• NTLM uses 14 characters for a single hash
• LM hash still exported by default for compatibility with older machines
in same network (i.e., placed in the SAM).
• NTLMv2 accepts longer than 14 characters, and in that case the
exported values for LanManager are incorrect (backward
incompatibility).
– Encrypts password hashes before storing them in the SAM
• Enforce 15 characters as minimum password length and disable LAM
authentication
Breno de Medeiros Florida State University
Fall 2005
Password hash challenge-
and-response
• Windows machines use hash-based challenge and
response mechanisms
• This implies that while passwords are required for
local login, password hashes can be used for remote
authentication
• It also means that, by eavesdropping the network and
capturing challenge/response pairs, an adversary can
collect information to perform dictionary and/or brute-
force attacks on the password.
Breno de Medeiros Florida State University
Fall 2005
You might also like
- Introduction To Memory ForensicsDocument47 pagesIntroduction To Memory Forensicsit20250560 Rajapaksha R.M.P.SNo ratings yet
- Malware-Analysis With HBgary Respender ProfesionalDocument273 pagesMalware-Analysis With HBgary Respender ProfesionalAamir HussainNo ratings yet
- Protecting Confidential Information: How to Securely Store Sensitive DataFrom EverandProtecting Confidential Information: How to Securely Store Sensitive DataNo ratings yet
- Computer Security: Principles and Practice: Chapter 3: User AuthenticationDocument41 pagesComputer Security: Principles and Practice: Chapter 3: User AuthenticationHarihara Gopalan SNo ratings yet
- Fundamentals of Pipeline Engineering, Construction & OperationsDocument4 pagesFundamentals of Pipeline Engineering, Construction & OperationsMehedi HasanNo ratings yet
- Mobius Training Cat IIDocument10 pagesMobius Training Cat IISuhartomt33% (3)
- CEH Lesson 3 - Enumeration and System HackingDocument36 pagesCEH Lesson 3 - Enumeration and System HackingLouise RealNo ratings yet
- CH 11Document37 pagesCH 11Raj ChauhanNo ratings yet
- CH 8 - Desktop and Server OS VulnerabilitesDocument69 pagesCH 8 - Desktop and Server OS VulnerabilitescoderNo ratings yet
- CH 8Document67 pagesCH 8ÇHTØUKÎ RËBÉLSSNo ratings yet
- Cisco Secure Endpoint - Intro and Access - Deployment - Stage 3 FY22Document39 pagesCisco Secure Endpoint - Intro and Access - Deployment - Stage 3 FY22mos changNo ratings yet
- CH 04Document16 pagesCH 04andrewiles88No ratings yet
- 09 - LECTURE Security Testing For Mobile and Web AppsDocument36 pages09 - LECTURE Security Testing For Mobile and Web AppsTeng Jun tehNo ratings yet
- Operating System SecurityDocument10 pagesOperating System SecuritynegashNo ratings yet
- Operating System ServicesDocument23 pagesOperating System ServicesdMAX GamingNo ratings yet
- Silberschatz and Galvin: SecurityDocument16 pagesSilberschatz and Galvin: SecurityFyruz FyFiveNo ratings yet
- OS ServicesDocument56 pagesOS Servicespramod rockzNo ratings yet
- ch02 OSDocument25 pagesch02 OSNam NguyenNo ratings yet
- Audit of Operating System NetworksDocument47 pagesAudit of Operating System Networksmaria avia kimNo ratings yet
- IT Controls Part II: Security and AccessDocument42 pagesIT Controls Part II: Security and AccessToxy KayzNo ratings yet
- 14malware Behavior and AntiReverse EngineeringDocument27 pages14malware Behavior and AntiReverse EngineeringPrestaNo ratings yet
- Operating System Security: Mike Swift CSE 451 Autumn 2003Document23 pagesOperating System Security: Mike Swift CSE 451 Autumn 2003Moayead MahdiNo ratings yet
- Software and Mobile Apps: Teori Sistem Informasi-2023Document37 pagesSoftware and Mobile Apps: Teori Sistem Informasi-2023Intan Imarmas Nababan578No ratings yet
- Chapter 2 System StructuresDocument27 pagesChapter 2 System StructuresAmisha SharmaNo ratings yet
- Day12 Client Side AttacksDocument65 pagesDay12 Client Side AttacksSheharyar AwanNo ratings yet
- SecurityDocument23 pagesSecurityZainab HameedNo ratings yet
- Chapter-1 Part 2Document64 pagesChapter-1 Part 2Yasar KhatibNo ratings yet
- Chapter 8-Operating System Notes 2Document44 pagesChapter 8-Operating System Notes 2Zilly cocoNo ratings yet
- SecurityDocument17 pagesSecurityFarooq ShadNo ratings yet
- Cyber - Security - Module 4 - 1Document29 pagesCyber - Security - Module 4 - 1KuNdAn DeOrENo ratings yet
- Linux LoggingDocument39 pagesLinux LoggingeranNo ratings yet
- B Tech CSE - V Sem - TCS 501 System Software - Final - To - Study - All CombinedDocument167 pagesB Tech CSE - V Sem - TCS 501 System Software - Final - To - Study - All Combinedtamannasharma1848No ratings yet
- 1 IntroductionDocument50 pages1 IntroductionakiraNo ratings yet
- Hacking Windows: Last Modified: 2-5-09Document91 pagesHacking Windows: Last Modified: 2-5-09andrewiles88No ratings yet
- OS PPTDocument36 pagesOS PPTVatsal GhoghariNo ratings yet
- Windows Security ArchitectureDocument19 pagesWindows Security ArchitectureAkash BoazNo ratings yet
- Chapter - 5 Information SecurityDocument23 pagesChapter - 5 Information SecurityJebesaNo ratings yet
- Software L2 OperatingsystemsDocument29 pagesSoftware L2 OperatingsystemsShakila ShakiNo ratings yet
- CH 16Document34 pagesCH 16Enock DarkohNo ratings yet
- Week003 PresentationDocument54 pagesWeek003 PresentationMichael Angelo MallariNo ratings yet
- IT Controls Part II: Security and Access: Accounting Information Systems, 5Document39 pagesIT Controls Part II: Security and Access: Accounting Information Systems, 5Glazerie Quijano GalabinNo ratings yet
- Bai 2-2 OS SecurityDocument36 pagesBai 2-2 OS Securitylevietkhanh189No ratings yet
- 2.operating System Structures wKlQ5ifo7P PDFDocument43 pages2.operating System Structures wKlQ5ifo7P PDFShivam mishraNo ratings yet
- BH 2012 Duckwall-Campbell SlidesDocument54 pagesBH 2012 Duckwall-Campbell SlidesCrazy JackNo ratings yet
- CH 2Document25 pagesCH 2rahulNo ratings yet
- Server SecurityDocument62 pagesServer SecurityEddie PeterNo ratings yet
- Module 1 System CallsDocument22 pagesModule 1 System CallsJoseph PrasanthNo ratings yet
- Windows Essentials - 1Document39 pagesWindows Essentials - 1Battle Royale ClipsNo ratings yet
- Windows XP Video NotesDocument32 pagesWindows XP Video NotesMani KhanNo ratings yet
- Hands-On Ethical Hacking and Network Defense, 3rd Edition: Desktop and Server OS VulnerabilitiesDocument54 pagesHands-On Ethical Hacking and Network Defense, 3rd Edition: Desktop and Server OS VulnerabilitiesSiddhartha Bikram KarkiNo ratings yet
- Bài 3- Bảo mật HDHDocument34 pagesBài 3- Bảo mật HDHAnh Phú NguyễnNo ratings yet
- Operating System & Data Storage Lec 2Document79 pagesOperating System & Data Storage Lec 2vantom85No ratings yet
- Computer Security and Penetration Testing: Windows VulnerabilitiesDocument34 pagesComputer Security and Penetration Testing: Windows VulnerabilitiesOsei SylvesterNo ratings yet
- PM Android SecurityDocument36 pagesPM Android Securityమనోహర్ రెడ్డిNo ratings yet
- Chapter 7 CEH v8 Gaining Access To A SystemDocument16 pagesChapter 7 CEH v8 Gaining Access To A SystemLeroy SerepeNo ratings yet
- 2677x CH09 NAGINPPTDocument26 pages2677x CH09 NAGINPPTnelsondarla12No ratings yet
- Auditing Operating System and Databases PDFDocument45 pagesAuditing Operating System and Databases PDFdhaval kulkarniNo ratings yet
- System Structure PDFDocument23 pagesSystem Structure PDFh4nnrtmNo ratings yet
- Computer Softwares: - System Software Servers As Intermediary Between Hardware and Functional ApplicationDocument9 pagesComputer Softwares: - System Software Servers As Intermediary Between Hardware and Functional Applicationprv3No ratings yet
- Chapter 4 - Operation System Security - 1Document46 pagesChapter 4 - Operation System Security - 1Lâm NguyễnNo ratings yet
- Chuong3 QuanTriNguoiDungDocument30 pagesChuong3 QuanTriNguoiDungToa ĐỗNo ratings yet
- Chapter 2Document54 pagesChapter 2bu.patil25No ratings yet
- Don Bosco Splendid Home 1 Terminal Examination-2017 Class-VII English IDocument2 pagesDon Bosco Splendid Home 1 Terminal Examination-2017 Class-VII English IproodootNo ratings yet
- Research Paper On Language TranslatorDocument8 pagesResearch Paper On Language Translatorafeavbpwg100% (1)
- Duke POLSCI 268Document7 pagesDuke POLSCI 268CNo ratings yet
- Elaine Aston, Caryl ChurchillDocument7 pagesElaine Aston, Caryl ChurchillMelissa RinaldiNo ratings yet
- 1.1 Environmental Value Systems Case Study 2Document3 pages1.1 Environmental Value Systems Case Study 2Vedant Patil0% (1)
- Kvs Ro JPR Class10th Science Study Material 2023-24Document98 pagesKvs Ro JPR Class10th Science Study Material 2023-24Avinesh MeenaNo ratings yet
- Community in Paraguay - A Visit To The BruderhofDocument106 pagesCommunity in Paraguay - A Visit To The BruderhofBruderhof100% (2)
- Cinética Química UDocument16 pagesCinética Química UJesus Manuel Yallerco VenegasNo ratings yet
- Presentation Robert Burmanjer 13july11Document10 pagesPresentation Robert Burmanjer 13july11Anonymous kHjswl6No ratings yet
- About Us - Focolare MovementDocument10 pagesAbout Us - Focolare MovementGitauNo ratings yet
- Productive CounterargumentDocument2 pagesProductive Counterargumentapi-322718373No ratings yet
- DOH 2018 Annual Report - Full ReportDocument44 pagesDOH 2018 Annual Report - Full Reportregie cuaresma100% (1)
- Biodegradable PlasticsDocument14 pagesBiodegradable PlasticsWieke SusilawatiNo ratings yet
- Villa - Sensor Install Uac Driver Signature1Document3 pagesVilla - Sensor Install Uac Driver Signature1mrahNo ratings yet
- How To Create A Digital Signature For PDF: (For Adobe Acrobat DC)Document3 pagesHow To Create A Digital Signature For PDF: (For Adobe Acrobat DC)VickyNo ratings yet
- Gas Detector Series Installation ManualDocument12 pagesGas Detector Series Installation Manualhatem hbibiNo ratings yet
- Merrill's First Principles of Instruction: Group 5Document10 pagesMerrill's First Principles of Instruction: Group 5Ma Cecilia TransfiguracionNo ratings yet
- Operation and Maintenance Instructions Manual: DP/DQ/DR/DS/DT Model Engines Fire Pump ApplicationsDocument46 pagesOperation and Maintenance Instructions Manual: DP/DQ/DR/DS/DT Model Engines Fire Pump ApplicationsAlvaro Serna100% (1)
- Mann+Hummel: Filtration Solutions For CompressorsDocument8 pagesMann+Hummel: Filtration Solutions For CompressorsSethuraman Kumarappan (KPCL)No ratings yet
- Block-4 Others American Fiction Old IGNOU DelDocument38 pagesBlock-4 Others American Fiction Old IGNOU Delr kumarNo ratings yet
- Supplier Relationship Managemen Peter KraljicDocument4 pagesSupplier Relationship Managemen Peter KraljicSeemaNo ratings yet
- S861 & S866 Alfa LavalDocument176 pagesS861 & S866 Alfa LavalarmaganNo ratings yet
- Slush (Beverage) : Jump To Navigation Jump To Search Improve This Article Adding Citations To Reliable SourcesDocument7 pagesSlush (Beverage) : Jump To Navigation Jump To Search Improve This Article Adding Citations To Reliable SourcestokagheruNo ratings yet
- Project Proposal For Care and Education For 25 Orphan and Poor Children in HyderabadDocument8 pagesProject Proposal For Care and Education For 25 Orphan and Poor Children in HyderabadIris TierraNo ratings yet
- GMAW Wire Feeders, Welding Guns and Drive RollsDocument8 pagesGMAW Wire Feeders, Welding Guns and Drive Rollsriddhi sarvaiyaNo ratings yet
- Surge Protection Device For Elv: LAN Public Address Telephone CCTV Fire AlarmDocument1 pageSurge Protection Device For Elv: LAN Public Address Telephone CCTV Fire AlarmQuang NguyễnNo ratings yet
- Haemnatopoiesis and CMLDocument8 pagesHaemnatopoiesis and CMLKe XuNo ratings yet