Professional Documents
Culture Documents
Wireshark Tutorial Materi
Uploaded by
Nurhidayat DiatOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Wireshark Tutorial Materi
Uploaded by
Nurhidayat DiatCopyright:
Available Formats
James Won-Ki Hong
Department of Computer Science and Engineering
POSTECH, Korea
jwkhong@postech.ac.kr
POSTECH CSED702D: Internet Traffic Monitoring and Analysis 1/39
Outline
What is Wireshark?
Capturing Packets
Analyzing Packets
Filtering Packets
Saving and Manipulating Packets
Packet Statistics
Colorizing Specific Packets
References
UNJ MJK- Internet Traffic Monitoring and Analysis 2/39
Scan Me with Your Phone
UNJ MJK- Internet Traffic Monitoring and Analysis 3/39
What is Wireshark?
The De-Facto Network Protocol Analyzer
Open-Source (GNU Public License)
Multi-platform (Windows, Linux, OS X, Solaris, FreeBSD,
NetBSD, and others)
Easily extensible
Large development group
Previously Named “Ethereal”
UNJ MJK- Internet Traffic Monitoring and Analysis 4/39
What is Wireshark?
Features
Deep inspection of thousands of protocols
Live capture and offline analysis
Standard three-pane packet browser
Captured network data can be browsed via a GUI, or via
the TTY-mode TShark utility
The most powerful display filters in the industry
Rich VoIP analysis
Live data can be read from Ethernet, IEEE 802.11,
PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame
Relay, FDDI, and others
Coloring rules can be applied to the packet list for quick,
intuitive analysis
Output can be exported to XML, PostScript®, CSV, or
plain text
UNJ MJK- Internet Traffic Monitoring and Analysis 5/39
What is Wireshark?
What we can:
Capture network traffic
Decode packet protocols using dissectors
Define filters – capture and display
Watch smart statistics
Analyze problems
Interactively browse that traffic
Some examples people use Wireshark for:
Network administrators: troubleshoot network problems
Network security engineers: examine security problems
Developers: debug protocol implementations
People: learn network protocol internals
UNJ MJK- Internet Traffic Monitoring and Analysis 6/39
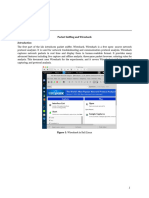
Interfaces
Packet
List
Packet
Details
Packet
Bytes
UNJ MJK- Internet Traffic Monitoring and Analysis 7/39
Capturing Packets (1/3)
UNJ MJK- Internet Traffic Monitoring and Analysis 8/39
Capturing Packets (2/3)
Capture all packets on the
network
Buffer size – in order not
to fill your laptop disk
Capture filter
Display
options
Capture in Name
multiple files resolution
options
When to
automatically
stop the
capture
UNJ MJK- Internet Traffic Monitoring and Analysis 9/39
Capturing Packets (3/3)
Example (W-LAN):
Received Signal Strength
Indication (RSSI) and Link
speed (BW)
UNJ MJK- Internet Traffic Monitoring and Analysis 10/39
Analyzing Packets (1/9)
Ethernet Frame Example
UNJ MJK- Internet Traffic Monitoring and Analysis 11/39
Analyzing Packets (2/9)
IP Packet Example
UNJ MJK- Internet Traffic Monitoring and Analysis 12/39
Analyzing Packets (3/9)
TCP Packet Example
UNJ MJK- Internet Traffic Monitoring and Analysis 13/39
Analyzing Packets (4/9)
TCP 3-way Handshake
UNJ MJK- Internet Traffic Monitoring and Analysis 14/39
Analyzing Packets (5/9)
Flow Graph
Giving us a graphical flow, for better understanding of
what we see
UNJ MJK- Internet Traffic Monitoring and Analysis 15/39
Analyzing Packets (6/9)
Flow Graph
UNJ MJK- Internet Traffic Monitoring and Analysis 16/39
Analyzing Packets (7/9)
Filtering Specific TCP Stream
UNJ MJK- Internet Traffic Monitoring and Analysis 17/39
Analyzing Packets (8/9)
Filtering Specific TCP Stream
UNJ MJK- Internet Traffic Monitoring and Analysis 18/39
Analyzing Packets (9/9)
RTP Stream Analysis
Stable
stream BW
UNJ MJK- Internet Traffic Monitoring and Analysis 19/39
Filtering Packets (1/4)
Applying Filter when Capturing Packets
Capture Interfaces Options:
UNJ MJK- Internet Traffic Monitoring and Analysis 20/39
Filtering Packets (2/4)
Applying Filter when Analyzing Packets
UNJ MJK- Internet Traffic Monitoring and Analysis 21/39
Filtering Packets (3/4)
Examples:
Capture only traffic to or from IP address 172.18.5.4
• host 172.18.5.4
Capture traffic to or from a range of IP addresses
• net 192.168.0.0/24
• net 192.168.0.0 mask 255.255.255.0
Capture traffic from a range of IP addresses
• src net 192.168.0.0/24
• src net 192.168.0.0 mask 255.255.255.0
Capture traffic to a range of IP addresses
• dst net 192.168.0.0/24
• dst net 192.168.0.0 mask 255.255.255.0
Capture only DNS (port 53) traffic
• port 53
Capture non-HTTP and non-SMTP traffic on your server
• host www.example.com and not (port 80 or port 25)
• host www.example.com and not port 80 and not port 25
UNJ MJK- Internet Traffic Monitoring and Analysis 22/39
Filtering Packets (4/4)
Examples:
Capture except all ARP and DNS traffic
• port not 53 and not arp
Capture traffic within a range of ports
• (tcp[2:2] > 1500 and tcp[2:2] < 1550) or (tcp[4:2] > 1500 and
tcp[4:2] < 1550)
• tcp portrange 1501-1549
Capture only Ethernet type EAPOL
• ether proto 0x888e
Capture only IP traffic
(the shortest filter, but sometimes very useful to get rid of lower layer
protocols like ARP and STP)
• ip
Capture only unicast traffic
(useful to get rid of noise on the network if you only want to see traffic
to and from your machine, not, for example, broadcast and multicast
announcements)
• not broadcast and not multicast
UNJ MJK- Internet Traffic Monitoring and Analysis 23/39
Saving and Manipulating Packets (1/3)
Save only displayed packets
UNJ MJK- Internet Traffic Monitoring and Analysis 24/39
Saving and Manipulating Packets (2/3)
Export to CSV file
UNJ MJK- Internet Traffic Monitoring and Analysis 25/39
Saving and Manipulating Packets (3/3)
Exported CSV File
UNJ MJK- Internet Traffic Monitoring and Analysis 26/39
Packet Statistics (1/8)
Protocol Hierarchy
UNJ MJK- Internet Traffic Monitoring and Analysis 27/39
Packet Statistics (2/8)
Conversation
Traffic between two specific endpoints
With some manipulation
UNJ MJK- Internet Traffic Monitoring and Analysis 28/39
Packet Statistics (3/8)
I/O Graph
UNJ MJK- Internet Traffic Monitoring and Analysis 29/39
Packet Statistics (4/8)
Configurable Options
I/O Graphs
• Graph 1-5: enable the specific graph 1-5 (graph 1 by default)
• Filter: a display filter for this graph (only the packets that pass
this filter will be taken into account for this graph)
• Style: the style of the graph (Line/Impulse/FBar/Dot)
X Axis
• Tick interval: an interval in x direction lasts
(10/1 minutes or 10/1/0.1/0.01/0.001 seconds)
• Pixels per tick: use 10/5/2/1 pixels per tick interval
• View as time of day: option to view x direction labels as time of
day instead of seconds or minutes since beginning of capture
Y Axis
• Unit: the unit for the y direction
(Packets/Tick, Bytes/Tick, Bits/Tick, Advanced...)
• Scale: the scale for the y unit
(Logarithmic,Auto,10,20,50,100,200,...)
UNJ MJK- Internet Traffic Monitoring and Analysis 30/39
Packet Statistics (5/8)
TCP Stream Graph
UNJ MJK- Internet Traffic Monitoring and Analysis 31/39
Packet Statistics (6/8)
Round-Trip Time Graph
RTT Vs. Sequence numbers gives us the time that take
to Ack every packet.
In case of variations, it can cause DUPACKs and even
Retransmissions
Usually will happen on communications lines:
Over the Internet
Over cellular networks
UNJ MJK- Internet Traffic Monitoring and Analysis 32/39
Packet Statistics (7/8)
Time / Sequence Graph
Seq No [B]
Time / Sequence representes how sequence numbers
advances with time
In a good connection (like in the example), the line will
be linear
The angle of the line indicates the speed of the
connection. In this example – fast connection
Time [Sec]
UNJ MJK- Internet Traffic Monitoring and Analysis 33/39
Packet Statistics (8/8)
Time / Sequence Graph
Seq No [B]
In this case, we see a non-
contiguous graph
Can be due to:
Severe packet loss
Server response (processing)
time
Time [Sec]
UNJ MJK- Internet Traffic Monitoring and Analysis 34/39
Colorizing Specific Packets (1/4)
Packet Colorization
Colorize packets according to a filter
Allow to emphasize the packets interested in
A lot of Coloring Rule examples at the Wireshark Wiki
Coloring Rules page at We want to watch a
http://wiki.wireshark.org/ColoringRules specific protocol through
out the capture file
UNJ MJK- Internet Traffic Monitoring and Analysis 35/39
Colorizing Specific Packets (2/4)
UNJ MJK- Internet Traffic Monitoring and Analysis 36/39
Colorizing Specific Packets (3/4)
UNJ MJK- Internet Traffic Monitoring and Analysis 37/39
Colorizing Specific Packets (4/4)
TLS Connection Establishment
UNJ MJK- Internet Traffic Monitoring and Analysis 38/39
References
Wireshark Website
http://www.wireshark.org
Wireshark Documentation
http://www.wireshark.org/docs/
Wireshark Wiki
http://wiki.wireshark.org
Network analysis Using Wireshark Cookbook
http://www.amazon.com/Network-Analysis-Using-Wiresh
ark-Cookbook/dp/1849517649
UNJ MJK- Internet Traffic Monitoring and Analysis 39/39
Q&A
UNJ MJK- Internet Traffic Monitoring and Analysis 40/39
You might also like
- James Won-Ki Hong: Department of Computer Science and Engineering POSTECH, KoreaDocument39 pagesJames Won-Ki Hong: Department of Computer Science and Engineering POSTECH, KoreasyedpandtNo ratings yet
- Ping WiresharkDocument15 pagesPing WiresharkSneha KanwadeNo ratings yet
- Finding An IP Address With Wireshark Using ARP Requests: Generate ARP Traffic Upon StartupDocument4 pagesFinding An IP Address With Wireshark Using ARP Requests: Generate ARP Traffic Upon StartupNguyen BuiNo ratings yet
- Linux Administration and OS File Systems ManagementDocument21 pagesLinux Administration and OS File Systems ManagementsreenathonwebNo ratings yet
- 49 WiresharkDocument8 pages49 Wiresharkalguacil2013No ratings yet
- Wireshark Cheat SheetDocument2 pagesWireshark Cheat SheetCarlos LozanoNo ratings yet
- Managing and Securing a Cisco Structured Wireless-Aware NetworkFrom EverandManaging and Securing a Cisco Structured Wireless-Aware NetworkRating: 3 out of 5 stars3/5 (1)
- Commands For VLAN and MAC Address ConfigurationDocument39 pagesCommands For VLAN and MAC Address ConfigurationPhạm Văn ThuânNo ratings yet
- Packet Sniffing: - by Aarti DhoneDocument13 pagesPacket Sniffing: - by Aarti Dhonejaveeed0401No ratings yet
- Apponix Technologies: Powershell-Scripting in ChennaiDocument5 pagesApponix Technologies: Powershell-Scripting in ChennaiHarshavardhan ReddyNo ratings yet
- Linux File SystemDocument24 pagesLinux File SystemRaj ShekarNo ratings yet
- Snort 2.1 Intrusion Detection, Second EditionFrom EverandSnort 2.1 Intrusion Detection, Second EditionRating: 4 out of 5 stars4/5 (6)
- Wireshak TutorialDocument7 pagesWireshak Tutorialhafiz0007No ratings yet
- Ghidra Cheat SheetDocument2 pagesGhidra Cheat SheetLungu Bogdan AlexandruNo ratings yet
- 9 Simple Steps To Secure Your Wi-Fi NetworkDocument8 pages9 Simple Steps To Secure Your Wi-Fi NetworkRajpreet OberoiNo ratings yet
- USB BasicsDocument15 pagesUSB Basicspsrao.bangalore4407No ratings yet
- Adv Routing Traffic ShapingDocument77 pagesAdv Routing Traffic ShapingzobdasNo ratings yet
- Linux Networking Commands NewDocument18 pagesLinux Networking Commands NewFrancis Densil RajNo ratings yet
- Filesystem PDFDocument50 pagesFilesystem PDFRaja Shahbaz KhalidNo ratings yet
- Towers of Power Class 2 - 2015Document32 pagesTowers of Power Class 2 - 2015mochodog100% (1)
- Nmap:The Network MapperDocument13 pagesNmap:The Network MapperNahid MajumderNo ratings yet
- How To Use Wireshark To Capture, Filter and Inspect PacketsDocument8 pagesHow To Use Wireshark To Capture, Filter and Inspect PacketsShibu NairNo ratings yet
- Juniper(r) Networks Secure Access SSL VPN Configuration GuideFrom EverandJuniper(r) Networks Secure Access SSL VPN Configuration GuideRating: 5 out of 5 stars5/5 (1)
- 802.11ah - OverviewDocument67 pages802.11ah - Overviewdatuan100% (1)
- WiresharkDocument4 pagesWiresharkSunil Joseph ChunkapuraNo ratings yet
- Ping and Traceroute UnderstandingDocument22 pagesPing and Traceroute Understandingdavekrunal46No ratings yet
- WiFi TechnologyDocument37 pagesWiFi Technologyfeku feku100% (1)
- Forensics Tutorial 12 - Network Forensics With WiresharkDocument20 pagesForensics Tutorial 12 - Network Forensics With WiresharkMary Amirtha Sagayee. GNo ratings yet
- MPLS-Enabled Applications: Emerging Developments and New TechnologiesFrom EverandMPLS-Enabled Applications: Emerging Developments and New TechnologiesRating: 4 out of 5 stars4/5 (4)
- Voice Over IP - Security PitfallsDocument4 pagesVoice Over IP - Security PitfallsLucas Giovane ZanetteNo ratings yet
- 802 11ah Overview Comm Soc r1Document15 pages802 11ah Overview Comm Soc r1l386543No ratings yet
- Case Project 3Document2 pagesCase Project 3QomindawoNo ratings yet
- Hands-On Lab: Lab 1: Capture Traffic To/from Your Hardware AddressDocument65 pagesHands-On Lab: Lab 1: Capture Traffic To/from Your Hardware Addressjohnbohn100% (1)
- Linux SecurityDocument2 pagesLinux Securityapi-37049880% (1)
- Technical Seminar On Packet Sniffing: Sailatha.SDocument15 pagesTechnical Seminar On Packet Sniffing: Sailatha.SAnonymous ty7mAZNo ratings yet
- Submitted By-Anurag Deyasi Information Technology SSEC, BhilaiDocument39 pagesSubmitted By-Anurag Deyasi Information Technology SSEC, BhilaiAnonymous kbmKQLe0JNo ratings yet
- SSH TunnelingDocument6 pagesSSH Tunnelingedwinrosario05No ratings yet
- Answer:: Networking Interview QuestionsDocument10 pagesAnswer:: Networking Interview QuestionsramNo ratings yet
- Ccna I Exploration Lab 2 - Intro To Packet Tracer Lab Required Materials - Data File Lsg01-Ptskills1.PkaDocument4 pagesCcna I Exploration Lab 2 - Intro To Packet Tracer Lab Required Materials - Data File Lsg01-Ptskills1.PkaElizabeth NewmanNo ratings yet
- 5.2.1.4 Configuring SSH InstructionDocument4 pages5.2.1.4 Configuring SSH InstructionJohan JV BasukiNo ratings yet
- Wireless Captive PortalsDocument16 pagesWireless Captive PortalsLuka O TonyNo ratings yet
- Mobile Radio Network Design in the VHF and UHF Bands: A Practical ApproachFrom EverandMobile Radio Network Design in the VHF and UHF Bands: A Practical ApproachNo ratings yet
- Ip Nat Guide CiscoDocument418 pagesIp Nat Guide CiscoAnirudhaNo ratings yet
- VPN With SocatDocument1 pageVPN With SocatzennroNo ratings yet
- Implementing Always On VPN: Modern Mobility with Microsoft Windows 10 and Windows Server 2022From EverandImplementing Always On VPN: Modern Mobility with Microsoft Windows 10 and Windows Server 2022No ratings yet
- Netstat Command and Its UsageDocument10 pagesNetstat Command and Its Usageveera42No ratings yet
- A Step-By-Step Guide To Setting Up A Home NetworkDocument3 pagesA Step-By-Step Guide To Setting Up A Home NetworkBilal SalamNo ratings yet
- Keystone Account Opening FormDocument6 pagesKeystone Account Opening Formenumah francisNo ratings yet
- (Your Business Name Here) - Safe Work Procedure Metal LatheDocument1 page(Your Business Name Here) - Safe Work Procedure Metal LatheSafety DeptNo ratings yet
- Trade Secrets Lawsuit V ReebokDocument17 pagesTrade Secrets Lawsuit V ReebokDarren Adam HeitnerNo ratings yet
- Crime MappingDocument13 pagesCrime MappingRea Claire QuimnoNo ratings yet
- Truman Show EssayDocument3 pagesTruman Show EssayJess FongNo ratings yet
- EE 4702 Take-Home Pre-Final Questions: SolutionDocument11 pagesEE 4702 Take-Home Pre-Final Questions: SolutionmoienNo ratings yet
- Plaxis Products 2010 EngDocument20 pagesPlaxis Products 2010 EngAri SentaniNo ratings yet
- Nipcib 000036Document273 pagesNipcib 000036AlfoFS0% (1)
- Rtcclient Tool Quick Guide: Date Jan. 25, 2011Document3 pagesRtcclient Tool Quick Guide: Date Jan. 25, 2011curzNo ratings yet
- SWVA Second Harvest Food Bank Spring Newsletter 09Document12 pagesSWVA Second Harvest Food Bank Spring Newsletter 09egeistNo ratings yet
- Affidavit of WaiverDocument1 pageAffidavit of Waivergelbert palomarNo ratings yet
- The Object-Z Specification Language: Software Verification Research Centre University of QueenslandDocument155 pagesThe Object-Z Specification Language: Software Verification Research Centre University of QueenslandJulian Garcia TalanconNo ratings yet
- TD 3.6 L4 TCD 3.6 L4: Operation ManualDocument72 pagesTD 3.6 L4 TCD 3.6 L4: Operation ManualMajd50% (2)
- Ease Us Fix ToolDocument7 pagesEase Us Fix ToolGregorio TironaNo ratings yet
- LECTURE 11-Microalgal Biotechnology-Biofuels N BioproductsDocument16 pagesLECTURE 11-Microalgal Biotechnology-Biofuels N BioproductsIntan Lestari DewiNo ratings yet
- SEBI Circular On Online Processing of Investor Service Requests and Complaints by RTAs - June 8, 2023Document5 pagesSEBI Circular On Online Processing of Investor Service Requests and Complaints by RTAs - June 8, 2023Diya PandeNo ratings yet
- Pre Int Work Book Unit 9Document8 pagesPre Int Work Book Unit 9Maria Andreina Diaz SantanaNo ratings yet
- Norma MAT2004Document12 pagesNorma MAT2004Marcelo Carvalho100% (1)
- Ergonomics InvestmentDocument4 pagesErgonomics InvestmentLiliana Alejandra Rodriguez ZamoraNo ratings yet
- Yrc1000 Options InstructionsDocument36 pagesYrc1000 Options Instructionshanh nguyenNo ratings yet
- BBA - Study On Gold As A Safer Investment CommodityDocument94 pagesBBA - Study On Gold As A Safer Investment CommoditySANJU GNo ratings yet
- Kaizenvest Education Report IndiaDocument62 pagesKaizenvest Education Report IndiaSakshi SodhiNo ratings yet
- 7diesel 2016Document118 pages7diesel 2016JoãoCarlosDaSilvaBrancoNo ratings yet
- Handling and Working With Analytical StandardsDocument6 pagesHandling and Working With Analytical StandardsPreuz100% (1)
- (2022) 5 SCC 661Document43 pages(2022) 5 SCC 661Swati PandaNo ratings yet
- Sexual Hazartment of Women at OfficeDocument3 pagesSexual Hazartment of Women at OfficeMohandas PeriyasamyNo ratings yet
- Stanley Diamond Toward A Marxist AnthropologyDocument504 pagesStanley Diamond Toward A Marxist AnthropologyZachNo ratings yet
- Least Used ProtocolsDocument3 pagesLeast Used ProtocolsJohn Britto0% (1)
- Summer Internship Project On: "Basics of PHP"Document45 pagesSummer Internship Project On: "Basics of PHP"its me Deepak yadav100% (1)